Satellite Encryption
Daniel S. Soper, California State University
For virtually all of human history, the communication of information was relegated to the surface of the Earth. Whether written or spoken, transmitted by land, sea, or air, all messages had one thing in common: They were, like those who created them, inescapably bound to the terrestrial surface.
In February 1945, however, the landscape of human communication was forever altered when an article by the famous science fiction writer Arthur C. Clarke proposed the extraordinary possibility that artificial satellites placed into orbit above the Earth could be used to facilitate mass communication on a global scale. A year later, a Project RAND report concluded that “A satellite vehicle with appropriate instrumentation [could] be expected to be one of the most potent scientific tools of the 20th century,” and that “The achievement of a satellite craft would produce repercussions comparable to the explosion of the atomic bomb.” It was only 12 short years after Clarke’s historic prediction that mankind’s first artificial satellite, Sputnik 1, was transmitting information from orbit back to Earth.
In the decades that followed, satellite technology evolved rapidly from its humble beginnings to become an essential tool for such diverse activities as astronomy, communications, scientific research, defense, navigation, and the monitoring of global weather patterns. In the 21st century, satellites are helping to fuel globalization, and societies are relying heavily on the power of satellite technology to enable the modern lifestyle. It is for these reasons that satellite communications must be protected. Before examining satellite encryption in detail, however, a brief review of satellite communication in general may be useful.
For communications purposes, modern satellites can be classified into two categories: those that communicate exclusively with the surface of the Earth (which will be referred to here as “Type 1” satellites) and those that communicate not only with the surface of the Earth but also with other satellites or spacecraft (referred to here as “Type 2” satellites). The distinction between these two types of satellite communications is depicted in Figure 25.1.
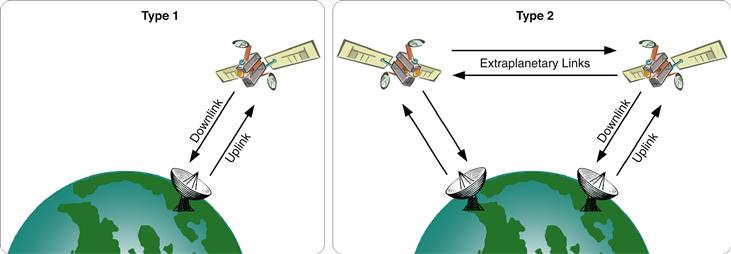
Figure 25.1 Comparison of Type 1 and Type 2 satellite communication capabilities.
As shown in the figure, there are several varieties of communication links that a satellite may support, and the classification of a particular satellite as Type 1 or Type 2 allows us to gain an understanding of its basic communications capabilities as well as insight into the sort of communications links that might need protecting. In the case of Type 1 satellites, the spacecraft may support uplink capabilities, downlink capabilities, or both. An uplink channel is a communications channel through which information is transmitted from the surface of the Earth to an orbiting satellite or other spacecraft. By contrast, a downlink channel is a communications channel through which information is transmitted from an orbiting satellite or other spacecraft to the terrestrial surface. While Type 2 satellites may possess the uplink and downlink capabilities of a Type 1 satellite, they are also capable of establishing links with spacecraft or other Type 2 satellites for purposes of extraplanetary communication. Type 2 satellites that can act as intermediaries between other spacecraft and the ground may be classified as relay satellites. Note that whether a particular link is used for sending or receiving information depends on the perspective of the viewer—from the ground, for example, an uplink channel is used to send information, but from the perspective of the satellite, the uplink channel is used to receive information.
1. The Need for Satellite Encryption
Depending on the type of satellite communications link that needs to be established, substantially different technologies, frequencies, and data encryption techniques might be required. The reasons for this lie as much in the realm of human behavior as they do in the realm of physics. Broadly speaking, it is not unreasonable to conclude that satellite encryption would be entirely unnecessary if every human being were perfectly trustworthy. That is to say, barring a desire to protect our messages from the possibility of extraterrestrial interception, there would be no need to encrypt satellite communications if only those individuals entitled to send or receive a particular satellite transmission actually attempted to do so. In reality, however, human beings, organizations, and governments commonly possess competing or contradictory agendas, thus implying the need to protect the confidentiality, integrity, and availability of information transmitted via satellite.
With human behavioral considerations in mind, the need for satellite encryption can be evaluated from a physical perspective. Consider, for example, a Type 1 communications satellite that has been placed into orbit above the Equator. Transmissions from the satellite to the terrestrial surface (i.e., the downlink channel) would commonly be made by way of a parabolic antenna. Although such an antenna facilitates focusing the signal, the signal nevertheless disperses in a conical fashion as it departs the spacecraft and approaches the surface of the planet. The result is that the signal may be made available over a wider geographic area than would be optimally desirable for security purposes. As with terrestrial radio, in the absence of encryption anyone within range of the signal who possesses the requisite equipment could receive the message. In this particular example, the geographic area over which the signal would be dispersed would depend on both the focal precision of the parabolic antenna and the altitude of the satellite above the Earth. These concepts are illustrated in Figure 25.2.
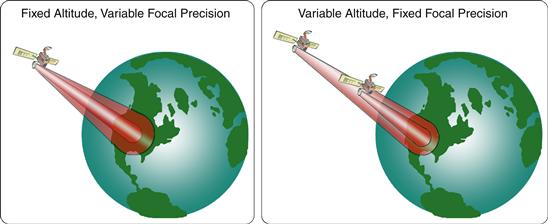
Figure 25.2 Effect of altitude and focal precision on satellite signal dispersion.
Because the sender of a satellite message may have little or no control over to whom the transmission is made available, protecting the message requires that its contents be encrypted. For similar reasons, extraplanetary transmissions sent between Type 2 satellites must also be protected; with thousands of satellites orbiting the planet, the chances of an intersatellite communication being intercepted are quite good!
Aside from these considerations, the sensitivity of the information being transmitted must also be taken into account. Various entities possess different motivations for wanting to ensure the security of messages transmitted via satellite. An individual, for example, might want her private telephone calls or bank transaction details to be protected. Likewise, an organization may want to prevent its proprietary data from falling into the hands of its competition, and a government may want to protect its military communications and national security secrets from being intercepted or compromised by an enemy. As with terrestrial communications, the sensitivity of the data being transmitted via satellite must dictate the extent to which those data are protected. If the emerging global information society is to fully capitalize on the benefits of satellite-based communication, its citizens, organizations, and governments must be assured that their sensitive data are not being exposed to unacceptable risk. In light of these considerations, satellite encryption can be expected to play a key role in the future advancement of mankind.
2. Satellite Encryption Policy
Given the rapid adoption of satellite communications, and the potential security implications associated therewith, many governments and multinational coalitions are increasingly establishing policy instruments with a view toward controlling and regulating the availability and use of satellite encryption in both the public and private sectors. Such policy instruments have wide-reaching economic, political, and cultural implications that commonly extend beyond national boundaries.
One might, for example, consider the export controls placed on satellite encryption technology by the U.S. government, which many consider the most stringent in the world. Broadly, these export controls were established in support of two primary objectives. First, the maintenance of a restrictive export policy allows the government to review and assess the merits of any newly developed satellite encryption technologies that have been proposed for export. If the export of those technologies is ultimately approved, the government will possess a detailed understanding of how the technologies operate, potentially allowing for their encryption schemes to be defeated if deemed necessary. Second, such controls allow the government to prevent satellite encryption technologies of particularly high merit from leaving the country, especially if the utilization of those technologies by foreign entities would interfere with U.S. intelligence-gathering activities. Although these stringent controls may appear to be a legacy of the xenophobic policies of the Cold War, they are nevertheless still seen as prudent measures in a world where information and communication technologies can be readily leveraged to advance extreme agendas. Unfortunately, such controls have potentially negative economic implications insofar as U.S. firms may be barred from competing in the increasingly lucrative global market for satellite communication technologies.
The establishment and maintenance of satellite encryption policy also needs to be considered in the context of satellite systems of global import. Consider, for example, the NAVSTAR global positioning system (GPS), whose constellation of satellites enables anyone with a GPS receiver to accurately determine their current location, time, velocity, and direction of travel anywhere on or near the surface of the Earth. In recent years, GPS capabilities have been incorporated into the navigational systems of automobiles, oceangoing vessels, trains, commercial aircraft, military vehicles, and many other forms of transit all over the world. Despite their worldwide use, the NAVSTAR GPS satellites are currently operated by the 50th Space Wing of the U.S. Air Force, implying that satellite encryption policy decisions related to the GPS are controlled by the U.S. Department of Defense. One of the options available to the U.S. government through this arrangement is the ability to selectively or entirely block the transmission of civilian GPS signals while retaining access to GPS signals for military purposes. Additionally, the U.S. government reserves the right to introduce errors into civilian GPS signals, thus making them less accurate. As the U.S. government exercises exclusive control over the GPS system, users all over the world are forced to place a great deal of trust in the goodwill of its operators and in the integrity of the encryption scheme for the NAVSTAR uplink channel. Given the widespread use of GPS navigation, a global catastrophe could ensue if the encryption scheme used to control the NAVSTAR GPS satellites were to be compromised. Because the GPS system is controlled by the U.S. military, the resiliency and security of this encryption scheme cannot be independently evaluated.
In the reality of a rapidly globalizing and interconnected world, the effectiveness of national satellite encryption policy efforts may not be sustainable in the long run. Satellite encryption policies face the same legal difficulties as so many other intrinsically international issues; outside of international agreements, the ability of a specific country to enforce its laws extends only so far as its geographic boundaries. This problem is particularly relevant in the context of satellite communications because the satellites themselves orbit the Earth and hence do not lie within the geographic boundaries of any nation. Considered in conjunction with governments’ growing need to share intelligence resources and information with their allies, future efforts targeted toward satellite encryption policy making may increasingly fall under the auspices of international organizations and multinational coalitions.
3. Implementing Satellite Encryption
It was noted earlier in this chapter that information can be transmitted to or from satellites using three general types of communication links: surface-to-satellite links (uplinks), satellite-to-surface links (downlinks), and intersatellite or interspacecraft links (extraplanetary links). Technological considerations notwithstanding, the specific encryption mechanism used to secure a transmission depends not only on which of these three types of links is being utilized but also on the nature and purpose of the message being transmitted. For purposes of simplicity, the value of transmitted information can be classified along two dimensions: high value and low value. The decision as to what constitutes high-value and low-value information largely depends on the perspective of the beholder; after all, one man’s trash is another man’s treasure. Nevertheless, establishing this broad distinction allows satellite encryption to be considered in the context of the conceptual model shown in Figure 25.3.
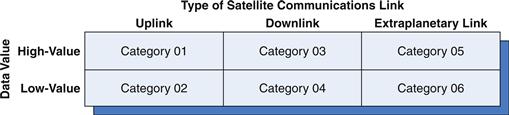
Figure 25.3 Satellite communications categories as a function of data value and type of link.
As shown in the figure, any satellite-based communication can be classified into one of six possible categories. In the subsections that follow, each of these categories will be addressed by considering the encryption of both high-value and low-value data in the context of the three types of satellite communication links. Before we consider the specific facets of encryption pertaining to satellite uplink, extraplanetary, and downlink transmissions, however, an examination of several of the more general issues associated with satellite encryption may be prudent.
General Satellite Encryption Issues
One of the problems common to all forms of satellite encryption relates to signal degradation. Satellite signals are typically sent over long distances using comparatively low-power transmissions and must frequently contend with many forms of interference, including terrestrial weather, solar and cosmic radiation, and many other forms of electromagnetic noise. Such disturbances may result in the introduction of gaps or errors into a satellite transmission. Depending on the encryption algorithm chosen, this situation can be particularly problematic for encrypted satellite transmissions because the entire encrypted message may be irretrievable if even a single bit of data is out of place. To resolve this problem, a checksum or cryptographic hash function may be applied to the encrypted message to allow errors to be identified and reconciled on receipt. This approach comes at a cost, however: Appending checksums or error-correcting code to an encrypted message increases the length of the message and by extension increases the time required for the message to be transmitted and lowers the satellite’s overall communications capacity due to the extra burden placed on its limited resources.
Another common problem associated with satellite encryption relates to establishing the identity of the sender of a message. A satellite, for example, needs to know that the control signals it is receiving from the ground originate from an authorized source. Similarly, an intelligence agency receiving a satellite transmission from one of its operatives needs to establish that the transmission is authentic. To establish the identity of the sender, the message needs to be encrypted in such a way that from the recipient’s perspective, only a legitimate sender could have encoded the message. The sender, of course, also wants to ensure that the message is protected while in transit and thus desires that only an authorized recipient would be able to decode the message on receipt. Both parties to the communication must therefore agree on an encryption algorithm that serves to identify the authenticity of the sender while affording a sufficient level of protection to the message while it is in transit. Although keyless encryption algorithms may satisfy these two criteria, such algorithms are usually avoided in satellite communications, since the satellite may become useless if the keyless encryption algorithm is broken. Instead, keyed encryption algorithms are typically used to protect information transmitted via satellite. Using keyed encryption algorithms can be problematic, however.
To gain insight into the problems associated with keyed encryption, one might first consider the case of a symmetrically keyed encryption algorithm, wherein the same key is used to both encode and decode a message. If party A wants to communicate with party B via satellite using this method, then both A and B must agree on a secret key. As long as the key remains secret, it also serves to authenticate both parties. If party A also wants to communicate with party C, however, A and C must agree on their own unique secret key; otherwise party B could masquerade as A or C, or vice versa. A keyed encryption approach to satellite communication thus requires that each party establish a unique secret key with every other party with whom they would like to communicate. To further compound this problem, each party must obtain all its secret keys in advance because possession of an appropriate key is a necessary prerequisite to establishing a secure communications channel with another party.
To resolve these issues, an asymmetrically keyed encryption algorithm may be adopted wherein the key used to encrypt a message is different from the key used to decrypt the message. Such an approach requires each party to maintain only two keys, one of which is kept private and the other of which is made publicly available. If party A wants to send party B a secure transmission, A first asks B for her public key, which can be transmitted over an unsecured connection. Party A then encodes a secret message using B’s public key. The message is secure because only B’s private key can decode the message. To authenticate herself to B, party A needs only to reencode the entire message using her own private key before transmitting the message to B. On receiving the message, B can establish whether it was sent by A, because only A’s private key could have encoded a message that can be decoded with A’s public key. This process is depicted in Figure 25.4.
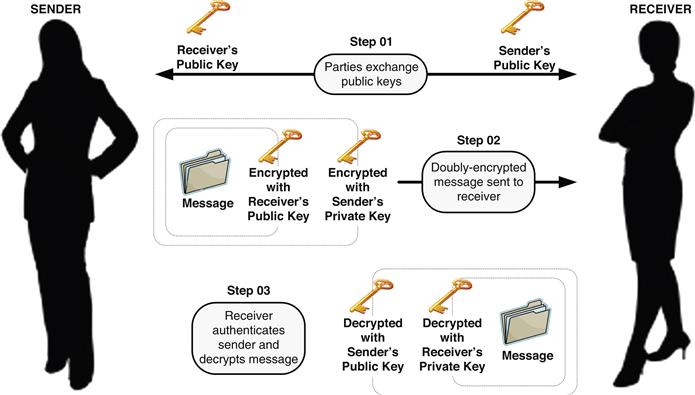
Figure 25.4 Ensuring sender identity and message security with asynchronously-keyed encryption
Unfortunately, even this approach to satellite encryption is not entirely foolproof. To understand why, consider how a malicious party M might interject himself between A and B to intercept the secure communication. To initiate the secure transmission, A must request B’s public key over an unsecured channel. If this request is intercepted by M, M can supply A with his own (that is, M’s) public key. A will then encrypt the message with M’s public key, after which she will reencrypt the result of the first encryption operation with her own private key. A will then transmit the encrypted message to B, which will once again be intercepted by M. Using A’s public key in conjunction with his own private key, M will be able to decrypt and read the message.
A will not know that the message has been intercepted, and B will not know that a message was even sent. Note that intercepting a secure communication is particularly easy for M if he owns or controls the satellite through which the message is being routed. In addition to the risk of interception, asynchronously keyed encryption algorithms are typically at least 10,000 times slower than synchronously keyed encryption algorithms—a situation that may place an enormously large burden on a satellite’s limited computational resources. Until a means is developed of dynamically and securely distributing synchronous keys, satellite-based encryption will always require tradeoffs among security, computational complexity, and ease of implementation.
Uplink Encryption
Protecting a transmission that is being sent to a satellite from at or near the surface of the Earth requires much more than just cryptographic techniques—to wit, encrypting the message itself is a necessary but insufficient condition for protecting the transmission. The reason for this is that the actual transmission of the encrypted message to the satellite is but the final step in a long chain of custody that begins when the message is created and ends when the message is successfully received by the satellite. Along the way, the message may pass through many people, systems, or networks, the control of which may or may not reside entirely in the hands of the sender. If one assumes that the confidentiality and integrity of the message have not been compromised as the message has passed through all these intermediaries, then but two primary security concerns remain: the directional accuracy of the transmitting antenna and the method used to encrypt the message. In the case of the former, the transmitting antenna must be sufficiently well focused to allow the signal to be received by—and ideally only by—the target satellite. With thousands of satellites in orbit, a strong potential exists for a poorly focused transmission to be intercepted by another satellite, in which case the only remaining line of defense for a message is the strength of the encryption algorithm with which it was encoded. For this reason, a prudent sender should always assume that her message could be intercepted while in transit to the satellite and should implement message encryption accordingly.
When deciding on which encryption method to use, the sender must simultaneously consider the value of the data being transmitted, the purpose of the transmission, and the technological and computational limitations of the target satellite. A satellite’s computational and technological capabilities are a function of its design specifications, its current workload, and any degradation that has occurred since the satellite was placed into orbit. These properties of the satellite can therefore be considered constraints; any encrypted uplink communications must work within the boundaries of these limitations. That having been said, the purpose of the transmission also features prominently in the choice of which encryption method to use. Here we must distinguish between two types of transmissions: commands, which instruct the satellite to perform one or more specific tasks, and transmissions in transit, which are intended to be retransmitted to the surface or to another satellite or spacecraft. Not only are command instructions of high value, they are also not typically burdened with the same low-latency requirements of transmissions in transit. Command instructions should therefore always be highly encrypted because control of the satellite could be lost if they were to be intercepted and compromised.
What remains, then, are transmissions in transit, which may be of either high value or low value. One of the basic tenants of cryptography states that the value of the data should dictate the extent to which the data are protected. As such, minimal encryption may be acceptable for low-value transmissions in transit. For such transmissions, adding an unnecessarily complex layer of encryption may increase the computational burden on the satellite, which in turn may delay message delivery and limit the satellite’s ability to perform other tasks simultaneously. High-value transmissions in transit should be protected with a robust encryption scheme that reflects the value of the data being transmitted. The extent to which a highly encrypted transmission in transit will negatively impact a satellite’s available resources depends on whether or not the message needs to be processed before being retransmitted. If the message is simply being relayed through the satellite without any additional processing, the burden on the satellite’s resources may be comparatively small. If, however, a highly encrypted message needs to be processed by the satellite prior to retransmission (e.g., if the message needs to be decrypted, processed, and then re-encrypted), the burden on the satellite’s resources may be substantial. Processing high-value, highly encrypted transmissions in transit may therefore vastly reduce a satellite’s throughput capabilities when considered in conjunction with its technological and computational limitations.
Extraplanetary Link Encryption
Before a signal is sent to the terrestrial surface, it may need to be transmitted across an extraplanetary link. Telemetry from a remote spacecraft orbiting Mars, for example, may need to be relayed to scientists by way of an Earth-orbiting satellite. Alternatively, a television signal originating in China may need to be relayed around the Earth by several intermediary satellites in order to reach its final destination in the United States. In such circumstances, several unique encryption-related issues may arise, each of which is associated with the routing of an extraplanetary transmission through one or more satellite nodes. Perhaps the most obvious of these issues is the scenario that arises when the signal transmitted from the source satellite or spacecraft is not compatible with the receiving capabilities of the target. For example, the very low-power signals transmitted from a remote exploratory spacecraft may not be detectable by a particular listening station on the planet’s surface, or the data rate or signal modulation with which an extraplanetary transmission is sent may not be supported by the final recipient. In this scenario, the intermediary satellite through which the signal is being routed must act as an interpreter or translator of sorts, a situation illustrated in Figure 25.5.
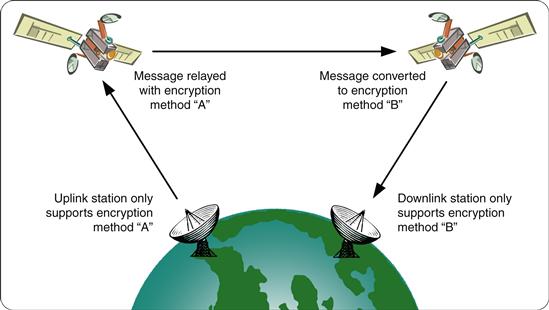
Figure 25.5 In-transit translation of message encryption in satellite communication.
From an encryption perspective, the situation we’ve illustrated implies that the intermediary satellite may need to decrypt the extraplanetary message and re-encrypt it using a different encryption scheme prior to retransmission. A similar issue may arise for legal or political reasons. Consider, for example, a message that is being transmitted from one country to another by way of several intermediary satellites. The first country may have no standing policies regarding the encryption of messages sent via satellite, whereas the second country may have policies that strictly regulate the encryption standards of messages received via satellite. In this case, one or more of the orbiting satellites may need to alter the encryption of a message in transit to satisfy the legal and regulatory guidelines of both countries.
Downlink Encryption
Several issues impact whether OR how? the information is protected as it is transmitted from orbiting satellites to the surface of the Earth. As with uplink encryption, the technological and computational capabilities of the spacecraft may constrain the extent to which a particular message can be protected. If, for example, an older communications satellite does not possess the requisite hardware or software capabilities to support a newly developed downlink encryption scheme, that scheme simply cannot be used with the satellite. Similarly, if the utilization of a particular encryption scheme would reduce the efficiency or message-handling capacity of a satellite to a level that is deemed unacceptable, the satellite’s operators may choose to prioritize capacity over downlink security. The precision with which a satellite is able to focus a downlink transmission may also impact the choice of encryption scheme; as noted earlier in this chapter, a widely dispersed downlink signal can be more readily intercepted than can a signal transmitted with a narrow focus. Though each of these computational and technological limitations must be considered when selecting a downlink encryption scheme, they are by no means the only factors requiring consideration.
Unlike uplink signals, which can only originate from the surface of the planet, messages to be transmitted over a downlink channel can come from one of three sources: the terrestrial surface, another spacecraft, or the satellite itself. The source of the message to be broadcast to the planet’s surface plays a critical role in determining the method of protection for that message. Consider, for example, a message that originates from the planet’s surface or from another spacecraft. In this case, one of two possible scenarios may exist. First, the satellite transmitting the message to Earth may be serving only as a simple signal router or amplifying transmitter; that is to say, the message is already encrypted on receipt, and the satellite is simply relaying the previously encrypted message to the surface. In this case, the satellite transmitting the downlink signal has very little to do with the encryption of the message, and only the integrity of the message and the retransmission capabilities of the satellite at the time the message is received need be considered. In the second scenario, a satellite may need to filter a message or alter its encryption method prior to downlink transmission. For example, a satellite may receive signals that have been optimized for extraplanetary communication from a robotic exploration spacecraft in the far reaches of the solar system. Prior to retransmission, the satellite may need to decrypt the data, process it, and then reencrypt the data using a different encryption scheme more suited to a downlink transmission. In this case, the technological capabilities of the satellite, the timeliness with which the data need to be delivered, and the value of the data themselves dictate the means through which those data are protected prior to downlink transmission.
Finally, one might consider the scenario in which the data being transmitted to the terrestrial surface originate from the satellite itself rather than from the surface or from another spacecraft. Such data can be classified as either telemetry relating to the status of the satellite or as information that the satellite has acquired or produced while performing an assigned task. In the case of the former, telemetry relating to the status of the satellite should always be highly protected, since it may reveal details about the satellite’s capabilities, inner workings, or control systems if it were to be intercepted and compromised. In the case of the latter, however, the value of the data that the satellite has acquired or produced should dictate the extent to which those data are protected. Critical military intelligence, for example, should be subjected to a much higher standard of encryption than data that are comparatively less valuable. In the end, a satellite operator must weigh many factors when deciding on the extent to which a particular downlink transmission should be protected. It is tempting to conclude that the maximum level of encryption should be applied to every downlink transmission. Doing so, however, would unnecessarily burden satellites’ limited resources and would vastly reduce the communications capacity of the global satellite network. Instead, a harmonious balance needs to be sought between a satellite’s technological and computational capabilities, and the source, volume, and value of the data that it is asked to handle. Only by achieving such a balance can the maximum utility of a satellite be realized.
4. The Future of Satellite Encryption
Despite the many challenges faced by satellite encryption, the potential advantages afforded by satellites to mankind are so tantalizing and alluring that the utilization of satellite-based communication can only be expected to grow for the foreseeable future. As globalization continues its indefatigable march across the terrestrial surface, access to secure high-speed communications will be needed from even the most remote and sparsely populated corners of the globe. Satellites by their very nature are well positioned to meet this demand and will therefore play a pivotal role in interconnecting humanity and enabling the forthcoming global information society. Furthermore, recent developments in the area of quantum cryptography promise to further improve the security of satellite-based encryption. This rapidly advancing technology allows the quantum state of photons to be manipulated in such a way that the photons themselves can carry a synchronous cryptographic key. The parties involved in a secure communication can be certain that the cryptographic key has not been intercepted, because eavesdropping on the key would introduce detectable quantum anomalies into the photonic transmission. By using a constellation of satellites in low Earth orbit, synchronous cryptographic keys could be securely distributed via photons to parties that want to communicate, thus resolving the key exchange problem. The parties could then establish secure communications using more traditional satellite channels. The further development and adoption of technologies such as quantum cryptography ensures that satellite-based communication has a bright—and secure—future.
There are, of course, risks to relying heavily on satellite-based communication. Specifically, if the ability to access critical satellite systems fails due to interference or damage to the satellite, disastrous consequences may ensue. What might happen, for example, if interference from a solar flare were to disrupt the constellation of global positioning satellites? What might happen if a micrometeoroid storm were to damage all the weather satellites monitoring the progress of a major hurricane? What might happen to a nation’s ability to make war if antisatellite weapons were deployed to destroy its military communications and intelligence-gathering satellites? Questions such as these highlight the risks of relying too heavily on artificial satellites. Nevertheless, as the costs associated with building, launching, and operating satellites continue to decline, the utilization of satellite technology will, for the foreseeable future, become an increasingly common part of the human experience.
