Information Technology Security Management
Rahul Bhasker, California State University
Bhushan Kapoor, California State University
Information technology security management can be defined as processes that supported enabling organizational structure and technology to protect an organization’s IT operations and assets against internal and external threats, intentional or otherwise. The principle purpose of IT security management is to ensure confidentiality, integrity, and availability (CIA) of IT systems. Fundamentally, security management is a part of the risk management process and business continuity strategy in an organization.
1. Information Security Management Standards
A range of standards are specified by various industry bodies. Although specific to an industry, these standards can be used by any organization and adapted to its goals. Here we discuss the main organizations that set standards related to information security management.
Federal Information Security Management Act
At the U.S. federal level, the National Institute of Standards and Technology (NIST) has specified guidelines for implementing the Federal Information Security Management Act (FISMA). This act aims to provide the following standards shown in Figure 16.1.

Figure 16.1 Specifications in the Federal Information Security Management Act.1
The “Federal Information Security Management Framework Recommended by NIST”2 sidebar describes the risk management framework as specified in FISMA. The activities specified in this framework are paramount in implementing an IT security management plan. Although specified for the federal government, this framework can be used as a guideline by any organization.
International Standards Organization
Another influential international body, the International Standards Organization and the International Electro Technical Commission, published ISO/IEC 17799:2005.3 These standards establish guidelines and general principles for initiating, implementing, maintaining, and improving information security management in an organization. The objectives outlined provide general guidance on the commonly accepted goals of information security management. The standards consist of best practices of control objectives and controls in the areas of information security management shown in Figure 16.2.
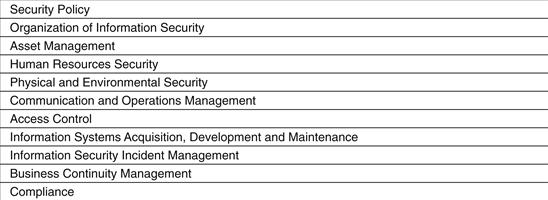
Figure 16.2 International Standards Organization best-practice areas.6
These objectives and controls are intended to be implemented to meet the requirements identified by a risk assessment.
Other Organizations Involved in Standards
Other organizations that are involved in information security management include The Internet Society4 and the Information Security Forum.5 These are professional societies with members in the thousands. The Internet Society is the organization home for the groups responsible for Internet infrastructure standards, including the Internet Engineering Task Force (IETF) and the Internet Architecture Board (IAB). The Information Security Forum is a global nonprofit organization of several hundred leading organizations in financial services, manufacturing, telecommunications, consumer goods, government, and other areas. It provides research into best practices and advice, summarized in its biannual Standard of Good Practice, which incorporates detailed specifications across many areas.
2. Information Technology Security Aspects
The various aspects to IT security in an organization that must be considered include:
• Security policies and procedures
• Security organization structure
– Processes for a business continuity strategy
Security Policies and Procedures
Security policies and procedures constitute the main part of any organization’s security. These steps are essential for implementing IT security management: authorizing security roles and responsibilities to various security personnel; setting rules for expected behavior from users and security role players; setting rules for business continuity plans; and more. The security policy should be generally agreed to by most personnel in the organization and should have the support of the highest-level management. This helps in prioritization at the overall organization level.
The following list, illustrated in Figure 16.3, is a sample of some of the issues an organization is expected to address in its policies.7 Note, however, that the universal list is virtually endless, and each organization’s list will consist of issues based on several factors, including its size and the value and sensitivity of the information it owns or deals with. Some important issues included in most security policies are:
• Access control standards. These are standards on controlling the access to various systems. These include password change standards.
• Accountability. Every user should be responsible for her own accounts. This implies that any activity under a particular user ID should be the responsibility of the user whose ID it is.
• Audit trails. There should be an audit trail recorded of all the activities under a user ID. For example, all the login, log-out activities for 30 days should be recorded. Additionally, all unauthorized attempts to access, read, write, and delete data and execute programs should be logged.
• Backups. There should be a clearly defined backup policy. Any backups should be kept in a secure area. A clear policy on the frequency of the backups and their recovery should be communicated to the appropriate personnel.
• Disposal of media. A clear policy should be defined regarding the disposal of media. This includes a policy on which hardware and storage media, such as disk drives, diskettes, and CD-ROMs, are to be destroyed. The level and method of destruction of business-critical information that is no longer needed should be well defined and documented. Personnel should be trained regularly on the principles to follow.
• Disposal of printed matter. Guidelines as to the disposal of printed matter should be specified and implemented throughout the organization. In particular, business-critical materials should be disposed properly and securely.
• Information ownership. All the data and information available in the organization should have an assigned owner. The owner should be responsible for deciding on access rights to the information for various personnel.
• Managers’ responsibility. Managers at all levels should ensure that their staff understands the security policy and adheres to it continuously. They should be held responsible for recording any deviations from the core policy.
• Equipment. An organization should have specific guidelines about modems, portable storage, and other devices. These devices should be kept in a secured physical environment.
• Communication. Well-defined policy guidelines are needed for communication using corporate information systems. These include communications via emails, instant messaging, and so on.
• Work procedures and processes. Employees of an organization should be trained to secure their workstations when not in use. The policy can impose a procedure of logging off before leaving a workstation. It can also include quarantining any device (such as a laptop) brought from outside the organization before plugging it into the network.
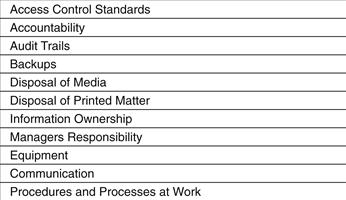
Figure 16.3 Security aspects an organization is expected to address in its policies.
Security Organization Structure
Various security-related roles need to be maintained and well defined. These roles and their brief descriptions are described here.8
End User
End users have a responsibility to protect information assets on a daily basis through adherence to the security policies that have been set and communicated. End-user compliance with security policies is key to maintaining information security in an organization because this group represents the most consistent users of the organization’s information.
Executive Management
Top management plays an important role in protecting the information assets in an organization. Executive management can support the goal of IT security by conveying the extent to which management supports security goals and priorities. Members of the management team should be aware of the risks that they are accepting for the organization through their decisions or failure to make decisions. There are various specific areas on which senior management should focus, but some that are specifically appropriate are user training, inculcating and encouraging a security culture, and identifying the correct policies for IT security governance.
Security Officer
The security officer “directs, coordinates, plans, and organizes information security activities throughout the organization.”9
Data/Information Owners
Every organization should have clearly identified data and information owners. These executives or managers should review the classification and access security policies and procedures. They should also be responsible for periodic audit of the information and data and its continuous security. They may appoint a data custodian in case the work required to secure the information and data is extensive and needs more than one person to complete.
Information System Auditor
Information system auditors are responsible for ensuring that the information security policies and procedures have been adhered to. They are also responsible for establishing the baseline, architecture, management direction, and compliance on a continuous basis. They are an essential part of unbiased information about the state of information security in the organization.
Information Technology Personnel
IT personnel are responsible for building IT security controls into the design and implementations of the systems. They are also responsible for testing these controls periodically or whenever there is a change. They work with the executives and other managers to ensure compliance in all the systems under their responsibility.
Systems Administrator
A systems administrator is responsible for configuring the hardware and the operating system to ensure that the information systems and their contents are available for business as and when needed. These adminstrators are placed ideally in an organization to ensure security of these assets. They play a key role because they own access to the most vulnerable information assets of an organization.
IT Security Processes
To achieve effective IT security requires processes related to security management. These processes include business continuity strategy, processes related to IT security governance planning, and IT security management implementation.
Processes for a Business Continuity Strategy
As is the case with any strategy, the business continuity strategy depends on a commitment from senior management. This can include some of the analysis that is obtained by business impact assessment/risk analysis focused on business value drivers. These business value drivers are determined by the main stakeholders from the organizations. Examples of these value drivers are customer service and intellectual property protection.10
The Disaster Recovery Institute International (DRII) associates eight tasks with the contingency planning process.11 These are as follows:
• Business impact analysis, to analyze the impact of outage on critical business function operations.
• Risk assessment, to assess the risks to the current infrastructure and the incorporation of safeguards to reduce the likelihood and impact of disasters.
• Recovery strategy identification, to develop a variety of disaster scenarios and identify recovery strategies.
• Recovery strategy selection, to select the appropriate recovery strategies based on the perceived threats and the time needed to recover.
• Contingency plan development, to document the processes, equipment, and facilities required to restore the IT assets.
• User training, to develop training programs to enable all affected users to perform their tasks.
• Plan verification, for accuracy and adequacy.
• Plan maintenance, for continuous upkeep of the plan as needs change.
Processes for IT Security Governance Planning
IT security governance planning includes prioritization as its major function. This helps in utilizing the limited sources of the organization. Determining priorities among the potential conflicting interests is the main focus of these processes. This includes budget setting, resource allocation, and, most important, the political process needed to prioritize in an organization.
Rules and Regulations
An organization is influenced by rules and regulations that influence its business. In a business environment marked by globalization, organizations have to be aware of both national and international rules and regulations. From an information security management perspective, various rules and regulations must be considered. These are listed in Figure 16.4.

Figure 16.4 Rules and regulations related to information security management.
We give more details on some rules and regulations here:
• The Health Insurance Portability and Accountability Act (HIPAA) requires the adoption of national standards for electronic healthcare transactions and national identifiers for providers, health insurance plans, and employers. Healthcare providers have to protect the personal medical information of the customer to comply with this law. Similarly, the Gramm-Leach-Bliley Act of 1999 (GLBA), also known as the Financial Services Modernization Act of 1999, requires financial companies to protect the information about individuals that it collects during transactions.
• The Sarbanes-Oxley Act of 2002 (SOX). This law requires companies to protect and audit their financial data. The chief information officer and other senior executives are held responsible for reporting and auditing an organization’s financial information to regulatory and other agencies.
• State Security Breach Notification Laws (California and many others) require businesses, nonprofits, and state institutions to notify consumers when unencrypted “personal information” might have been compromised, lost, or stolen.
• The Personal Information Protection and Electronics Document Act (PIPEDA) supports and promotes electronic commerce by protecting personal information that is collected, used, or disclosed in certain circumstances, by providing for the use of electronic means to communicate or record information or transactions, and by amending the Canada Evidence Act, the Statutory Instruments Act, and the Statute Revision Act that is in fact the case.
• The Computer Fraud and Abuse Act, or CFAA (also known as Fraud and Related Activity in Connection with Computers), is a U.S. law passed in 1986 and intended to reduce computer crimes. It was amended in 1994, 1996, and 2001 by the U.S.A. PATRIOT Act.12
The following sidebar, “Computer Fraud and Abuse Act Criminal Offences,” lists criminal offences covered under this law.13
The U.S.A. PATRIOT Act of 2001 increased the scope and penalties of this act by14:
• Raising the maximum penalty for violations to ten years (from five) for a first offense and 20 years (from ten) for a second offense
• Ensuring that violators only need to intend to cause damage generally, not intend to cause damage or other specified harm over the $5000 statutory damage threshold
• Allowing aggregation of damages to different computers over a year to reach the $5000 threshold
• Enhancing punishment for violations involving any (not just $5000 in) damage to a government computer involved in criminal justice or the military
• Including damage to foreign computers involved in U.S. interstate commerce
• Including state law offenses as priors for sentencing;
• Expanding the definition of loss to expressly include time spent investigating
• Responding (this is why it is important for damage assessment and restoration)
These details are summarized in Figure 16.5.
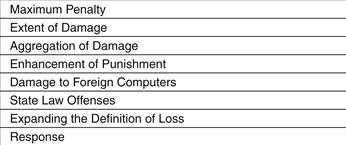
Figure 16.5 U.S.A. PATRIOT Act increase in scope and penalties.
The PATRIOT Act of 2001 came under criticism for a number of reasons. There are fears that the Act is an invasion of privacy and infringement on freedom of speech. Critics also feel that the Act unfairly expands the powers of the executive branch and strips away many crucial checks and balances.
The original act has a sunset clause that would have caused many of the law’s provisions to expire in 2005. The Act was reauthorized in early 2006 with some new safeguards and with expiration dates for its two most controversial powers, which authorize roving wiretaps and secret searches of records.
3. Conclusion
Information technology security management consists of processes to enable organizational structure and technology to protect an organization’s IT operations and assets against internal and external threats, intentional or otherwise. These processes are developed to ensure confidentiality, integrity, and availability of IT systems. There are various aspects to the IT security in an organization that need to be considered. These include security policies and procedures, security organization structure, IT security processes, and rules and regulations.
Security policies and procedures are essential for implementing IT security management: authorizing security roles and responsibilities to various security personnel; setting rules for expected behavior from users and security role players; setting rules for business continuity plans; and more. The security policy should be generally agreed to by most personnel in the organization and have support from the highest-level management. This helps in prioritization at the overall organization level. The IT security processes are essentially part of an organization’s risk management processes and business continuity strategies. In a business environment marked by globalization, organizations have to be aware of both national and international rules and regulations. Their information security and privacy policies must conform to these rules and regulations.
1“Federal Information Security Management Act,” National Institute of Standards and Technology, http://csrc.nist.gov/groups/SMA/fisma/index.html, 2008 (downloaded 10/20/2008).
2“Federal Information Security Management Act,” National Institute of Standards and Technology, http://csrc.nist.gov/groups/SMA/fisma/index.html, 2008 (downloaded 10/20/2008).
3“Information technology | Security techniques | Code of practice for information security management, ISO/IEC 17799,” The International Standards Organization and The International Electro Technical Commission, www.iso.org/iso/iso_catalogue/catalogue_tc/catalogue_detail.htm?csnumber=39612, 2005 (downloaded 10/20/2008).
4“ISOC’s Standards and Technology Activities,” Internet Society, www.isoc.org/standards, 2008 (downloaded 10/20/2008).
5“The Standard of Good Practice,” Information Security Forum, https://www.securityforum.org/html/frameset.htm, 2008 (downloaded 10/20/2008).
6“Information technology | Security techniques | Code of practice for information security management, ISO/IEC 17799,” The International Standards Organization and The International Electro Technical Commission, (www.iso.org/iso/support/faqs/faqs_widely_used_standards/widely_used_standards_other/information_security.htm 2005 (downloaded 10/20/2008).
7“Information technology | Security techniques | Code of practice for information security management, ISO/IEC 17799,” The International Standards Organization and The International Electro Technical Commission, www.iso.org/iso (downloaded 10/20/2008).
8Tipton and Krause, “Information Security Governance,” Information Security Management Handbook, Auerbach Publications, 2008.
9Tipton and Krause, “Information Security Governance,” Information Security Management Handbook, Auerbach Publications, 2008.
10C. R. Jackson, “Developing Realistic Continuity Planning Process Metrics,” Information Security Management Handbook, Auerbach Publications, 2008.
11“Contingency Planning Process,” DRII – The Institute for Continuity Management, https://www.drii.org/professional_prac/profprac_appendix.html#BUSINESS_CONTINUITY_PLANNING_INFORMATION, 2008 (downloaded 10/24/2008).
12“Fraud and Related Activities in Relation to the Computers,” U.S. Code Collection, Cornell University Law School, www4.law.cornell.edu/uscode/18/1030.html, 2008 (downloaded 10/24/2008).
13“Fraud and Related Activities in Relation to the Computers,” U.S. Code Collection, Cornell University Law School, www4.law.cornell.edu/uscode/18/1030.html, 2008 (downloaded 10/24/2008).
14“Computer Fraud and Abuse Act,” Wikipedia, http://en.wikipedia.org/wiki/Computer_Fraud_and_Abuse_Act, 2008 (downloaded 10/24/2008).
