Computer Forensics
Scott R. Ellis, RGL
This guide is intended to provide in-depth information on computer forensics as a career, a job, and a science. It will help you avoid mistakes and find your way through the many aspects of this diverse and rewarding field.
1. What is Computer Forensics?
Definition: Computer forensics is the acquisition, preservation, and analysis of electronically stored information (ESI) in such a way that ensures its admissibility for use as either evidence, exhibits, or demonstratives in a court of law.
Rather than discussing at great length what computer forensics is (the rest of the chapter will take care of that), let’s, for the sake of clarity, define what computer forensics is not. It is not an arcane ability to tap into a vast, secret repository of information about every single thing that ever happened on, or to, a computer. Often, it involves handling hardware in unique circumstances and doing things with both hardware and software that are not, typically, things that the makers or manufacturers ever intended (see sidebar: “Angular Momentum”).
Not every single thing a user ever did on a computer is 100% knowable beyond a shadow of a doubt or even beyond reasonable doubt. Some things are certainly knowable with varying degrees of certainty. and there is nothing that can happen on a computer through the use of a keyboard and a mouse that cannot be replicated with a software program or macro of some sort. It is fitting, then, that many of the arguments of computer forensics become philosophical, and that degrees of certainty exist and beg definition. Such as: How heavy is the burden of proof? Right away, lest arrogant thoughtlessness prevail, anyone undertaking a study of computer forensics must understand the core principles of what it means to be in a position of authority and to what varying degrees of certainty an examiner may attest to without finding he has overstepped his mandate (see sidebar, “Angular Momentum”). The sections “Testifying in Court” and “Beginning to End in Court” in this chapter, and the article “Computer Forensics and Ethics, Green Home Plate Gallery View,” address these concerns as they relate to ethics and testimonial work.
2. Analysis of Data
Never underestimate the power of a maze. There are two types of mazes that maze experts generally agree on: unicursive and multicursive. In the unicursive maze, the maze has only one answer; you wind along a path and with a little patience you end up at the end. Multicursory mazes, according to the experts, are full of wrong turns and dead ends.
The fact of the matter is, however, when one sets foot into a multicursive maze, one need only recognize that it is, in fact, two unicursory mazes put together, with the path through the maze being the seam. If you take the unicursory tack and simply always stay to the right (or the left, as long as you are consistent), you will traverse the entire maze and have no choice but to traverse and complete it successfully.
This is not a section about mazes, but they are analogous in that there are two approaches to computer forensics: one that churns through every last bit of data and one that takes shortcuts. This is called analysis. Quite often as a forensic analyst, the sheer amount of data that needs to be sifted will seem enormous and unrelenting. But there is a path that, if you know it, you can follow it through to success. Here are a few guidelines on how to go about conducting an investigation. For starters, we talk about a feature that is built into most forensic toolsets. It allows the examiner to “reveal all” in a fashion that can place hundreds of thousands of files at the fingertips for examination. It can also create a bad situation, legally and ethically.
Computer Forensics and Ethics, Green Home Plate Gallery View1
A simplified version of this article was published on the Chicago Bar Association blog in late 2007. This is the original version, unaltered.
EnCase is a commonly used forensic software program that allows a computer forensic technologist to conduct an investigation of a forensic hard disk copy. One of the functions of the software is something known as “green-home-plate-gallery-view.” This function allows the forensic technologist to create, in plain view, a gallery of every single image on the computer.
In EnCase, the entire folder view structure of a computer is laid out just as in Windows Explorer with the exception that to the left of every folder entry are two boxes. One is shaped like a square, and the other like a little “home plate” that turns green when you click on it; hence the “green-home-plate.” The technical name for the home plate box is “Set Included Folders.” With a single click, every single file entry in that folder and its subfolders becomes visible in a table view. An additional option allows the examiner to switch from a table view of entries to a gallery view of thumbnails. Both operations together create the “green-home-plate-gallery-view” action.
With two clicks of the mouse, the licensed EnCase user can gather up every single image that exists on the computer and place it into a single, scrollable, thumbnail gallery. In a court-ordered investigation where the search may be for text-based documents such as correspondence, green-home-plate-gallery-view has the potential of being misused to visually search the computer for imaged/scanned documents. I emphasize misused because, ultimately, this action puts every single image on the computer in plain view. It is akin to policemen showing up for a domestic abuse response with an x-ray machine in tow and x-raying the contents of the whole house.
Because this action enables one to view every single image on a computer, including those that may not have anything to do with the forensic search at hand, it raises a question of ethics, and possibly even legality. Can a forensic examiner green-home-plate-gallery-view without reasonable cause?
In terms of a search where the search or motion specifically authorized searching for text-based “documents,” green-home-plate-gallery-view is not the correct approach, nor is it the most efficient. The action exceeds the scope of the search and it may raise questions regarding the violation of rights and/or privacy. To some inexperienced examiners, it may seem to be the quickest and easiest route to locating all the documents on a computer. More experienced examiners may use it as a quick litmus test to “peek under the hood” to see if there are documents on the computer.
Many documents that are responsive to the search may be in the form of image scans or PDFs. Green-home-plate-gallery-view renders them visible and available, just for the scrolling. Therein lies the problem: If anything incriminating turns up, it also has the ring of truth in a court of law when the examiner suggests that he was innocently searching for financial documents when he inadvertently discovered, in plain view, offensive materials that were outside the scope of his original mandate. But just because something has the ring of truth does not mean that the bell’s been rung.
For inexperienced investigators, green-home-plate-gallery-view (see Figure 19.2) may truly seem to be the only recourse and it may also be the one that has yielded the most convictions. However, because there is a more efficient method to capture and detect text, one that can protect privacy and follows the constraints of the search mandate, it should be used.
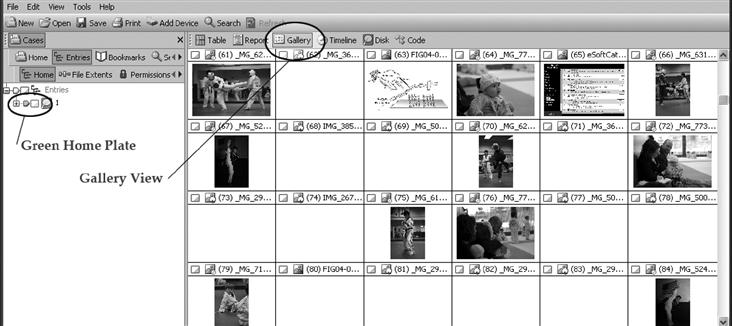
Figure 19.2 Green-home-plate-gallery-view.
Current forensic technology allows us, through electronic file signature analysis, sizing, and typing of images, to capture and export every image from the subject file system. Next, through optical character recognition (OCR), the experienced professional can detect every image that has text and discard those that do not. In this manner, images are protected from being viewed, the subject’s privacy is protected, and all images with text are located efficiently. The resultant set can then be hashed and reintroduced into EnCase as single files, hashed, and indexed so that the notable files can be bookmarked and a report generated.
Technically, this is a more difficult process because it requires extensive knowledge of imaging, electronic file signature analysis, automated OCR discovery techniques, and hash libraries. But to a trained technician, this is actually faster than green-home-plate-gallery-view, which may yield thousands of images and may take hundreds of hours to accurately review.
In practice, the easiest way is seldom the most ethical way to solve a problem; neither is it always the most efficient method of getting a job done. Currently, there are many such similar scenarios that exist within the discipline of computer forensics. As the forensic technology industry grows and evolves, professional organizations may eventually emerge that will provide codes of ethics and some syncretism in regard to these issues. For now, however, it falls on attorneys to retain experienced computer forensic technologists who place importance on developing appropriate ethical protocols. Only when these protocols are in place can we successfully understand the breadth and scope of searches and prevent possible violations of privacy.
Database Reconstruction
A disk that hosts an active database is a very busy place. Again and again throughout this chapter, a single recurring theme will emerge: Data that has been overwritten cannot, by any conventionally known means, be recovered. If it could be, then Kroll Ontrack and every other giant in the forensics business would be shouting this service from the rooftops and charging a premium price for it. Experimentally, accurate statistics on the amount of data that will be overwritten by the seemingly random action of a write head may be available, but most likely it functions by rules that are different for every system based on the amount of usage, the size of the files, and the size of the unallocated clusters. Anecdotally, the formula goes something like this; the rules change under any given circumstances, but this story goes a long way toward telling how much data will be available:
On a server purposed with storing surveillance video, there are three physical hard drives. Drive C serves as the operating system (OS) disk and program files disk; Drives E and F, 350 gigabytes (GB) each, serve as storage disks. When the remote DVR units synchronize each evening, every other file writes to every other disk of the two storage drives. Thirty-day-old files automatically get deleted by the synchronization tool.
After eight months of use, the entire unallocated clusters of each drive, 115 GB on one drive and 123 GB on the other, are completely filled with MPG data. An additional 45 GB of archived deleted files are available to be recovered from each drive.
In this case, the database data were MPG movie files. In many databases, the data, the records (as the database indexes and grows and shrinks and is compacted and optimized), will grow to populate the unallocated clusters. Database records found in the unallocated clusters are not an indicator of deleted records. Database records that exist in the unallocated clusters that don’t exist in the live database are a sign of deleted records.
Lesson learned: Don’t believe everything you see. Check it out and be sure. Get second, third, and fourth opinions when you’re uncertain.
3. Computer Forensics in the Court System
Computer forensics is one of the few computer-related fields in which the practitioner will be found in the courtroom on a given number of days of the year. With that in mind, the following sections are derived from the author’s experiences in the courtroom, the lessons learned there, and the preparation leading up to giving testimony. To most lawyers and judges, computer forensics is a mysterious black art. It is as much a discipline of the art to demystify and explain results in plain English as it is to conduct an examination. It was with special consideration of the growing prevalence of the use of electronically stored information (ESI) in the courtroom, and the general unfamiliarity with how it must be handled as evidence, that spawned the idea for the sidebar “Preserving Digital Evidence in the Age of eDiscovery.”
4. Understanding Internet History
Of the many aspects of user activity, the Internet history is usually of the greatest interest. In most investigations, people such as HR, employers, and law enforcement seek to understand the subject’s use of the Internet. What Web sites did he visit? When did he visit them? Did he visit them more than once? The article “What Have You Been Clicking On” (see sidebar) seeks to demystify the concept of temporary Internet files (TIF).
5. Temporary Restraining Orders and Labor Disputes
A temporary restraining order (TRO) will often be issued in intellectual property or employment contract disputes. The role of the forensic examiner in a TRO may be multifold, or it may be limited to a simple, one-time acquisition of a hard drive. Often when an employee leaves an organization under less than amicable terms, accusations will be fired in both directions and the resulting lawsuit will be a many-headed beast. Attorneys on both sides may file motions that result in forensic analysis of emails, user activity, and possible contract violations as well as extraction of information from financial and customer relationship management (CRM) databases.
Divorce
Typically the forensic work done in a divorce case will involve collecting information about one of the parties to be used to show that trust has been violated. Dating sites, pornography, financial sites, expatriate sites, and email should be collected and reviewed.
Patent Infringement
When one company begins selling a part that is patented by another company, a lawsuit will likely be filed in federal court. Subsequently, the offending company will be required to produce all the invoices relating to sales of that product. This is where a forensic examiner may be required. The infringed-on party may find through their own research that a company has purchased the part from the infringer and that the sale has not been reported. A thorough examination of the financial system will reveal all the sales. It is wise when doing this sort of work to contact the financial system vendor to get a data dictionary that defines all the fields and the purpose of the tables.
Invoice data is easy to collect. It will typically reside in just two tables: a header and a detail table. These tables will contain customer codes that will need to be joined to the customer table, so knowing some SQL will be a great help. Using the database server for the specific database technology of the software is the gold standard for this sort of work. Getting the collection to launch into VMware is the platinum standard, but sometimes an image won’t want to boot. Software utilities such as Live View do a great job of preparing the image for deployment in a virtualized environment.
When to Acquire, When to Capture Acquisition
When a forensics practitioner needs to capture the data on a hard disk, he does so in a way that is forensically sound. This means that, through any actions on the part of the examiner, no data on the hard drive is altered and a complete and total copy of the surface of the hard drive platters is captured. Here are some common terms used to describe this process:
Any of these terms is sufficient to describe the process. The one that attorneys typically use is mirror because they seem to understand it best. A “forensic” acquisition simply means that the drive was write-protected by either a software or hardware write blocker while the acquisition was performed.
Acquisition of an entire hard drive is the standard approach in any case that will require a deep analysis of the behaviors and activities of the user. It is not always the standard procedure. However, most people will agree that a forensic procedure must be used whenever information is copied from a PC. Forensic, enterprise, and ediscovery cases all vary in their requirements for the amount of data that must be captured. In discovery, much of what is located on a computer may be deemed “inaccessible,” which is really just fancy lawyer talk for “it costs too much to get it.” Undeleting data from hundreds of computers in a single discovery action in a civil case would be a very rare thing to happen and would only take place if massive malfeasance was suspected. In these cases, forensic creation of logical evidence files allows the examiner to capture and copy relevant information without altering the data.
Creating Forensic Images Using Software and Hardware Write Blockers
Both software and hardware write blockers are available. Software write blockers are versatile and come in two flavors. One is a module that “plugs” into the forensic software and can generally be used to write block any port on the computer. The other method of software write blocking is to use a forensic boot disk. This will boot the computer from the hard drive. Developing checklists that can be repeatable procedures is an ideal way to ensure solid results in any investigation.
Software write blockers are limited by the port speed of the port they are blocking, plus some overhead for the write-blocking process. But then, all write blockers are limited in this manner.
Hardware write blockers are normally optimized for speed. Forensic copying tools such as Logicube and Tableau are two examples of hardware write blockers, though there are many companies now that make them. LogiCube will both hash and image a drive at a rate of about 3GB a minute. They are small and portable and can replace the need for bulky PCs on a job site. There are also appliances and large enterprise software packages that are designed to automate and alleviate the labor requirements of large discovery/disclosure acquisitions that may span thousands of computers.
Live Capture of Relevant Files
Before conducting any sort of a capture, all steps should be documented and reviewed with counsel before proceeding. Preferably, attorneys from both sides on a matter and the judge agree to the procedure before it is enacted. Whenever a new procedure or technique is introduced late on the job site, if there are auditors or observers present, the attorneys will argue, which can delay the work by several hours. Most forensic software can be loaded to a USB drive and launched on a live system with negligible forensic impact to the operating environment. Random Access Memory (RAM) captures are becoming more popular; currently this is the only way to capture an image of physical RAM. Certain companies are rumored to be creating physical RAM write blockers. Launching a forensic application on a running system will destroy a substantial amount of physical RAM as well as the paging file. If either RAM or the paging file is needed, the capture must be done with a write blocker.
Once the forensic tool is launched, either with a write blocker or on a live system, the local drive may be previewed. The examiner may only be interested in Word documents, for example. Signature analysis is a lengthy process in preview mode, as are most searches. A better method, if subterfuge is not expected: Filtering the table pane by extension produces a list of all the docs. “Exporting” them will damage the forensic information, so instead you need to create a logical evidence file (LEF). Using EnCase, a user can create a condition to view all the .DOC files and then dump the files into a logical evidence file in about 30 seconds. Once the logical evidence file is created, it can later be used to create a CD-ROM. There are special modules available that will allow an exact extraction of native files to CD to allow further processing for a review tool.
Redundant Array of Independent (or Inexpensive) Disks (RAID)
Acquiring an entire RAID set disk by disk and then reassembling them in EnCase is probably the easiest way of dealing with a RAID and may be the only way to capture a software RAID. Hardware RAIDs can be most efficiently captured using a boot disk. This allows the capture of a single volume that contains all the unique data in an array. It can be trickier to configure and as with everything, practice makes perfect. Be sure you understand how it works. The worst thing that can happen is that the wrong disk or an unreadable disk gets imaged and the job has to be redone at your expense.
File System Analyses
FAT12, FAT16, and FAT32 are all types of file systems. Special circumstances aside, most forensic examiners will find themselves regularly dealing with either FAT or NTFS file systems. FAT differs from NTFS primarily in the way that it stores information about how it stores information. Largely, from the average forensic examiner’s standpoint, very little about the internal workings of these file systems is relevant. Most modern forensic software will do the work of reconstructing and extracting information from these systems, at the system level, for you. Nonetheless, an understanding of these systems is critical because, at any given time, an examiner just might need to know it. The following are some examples showing where you might need to know about the file system:
• Locating lost or moved partitions
• Discussions of more advanced information that can be gleaned from entries in the MFT or FAT
The difference between FAT12, 16, and 32 is in the size of each item in the File Allocation Table (FAT). Each has a correspondingly sized entry in the FAT. For example, FAT12 has a 12-bit entry in the FAT. Each 12-bit sequence represents a cluster. This places a limitation on the file system regarding the number of file extents available to a file. The FAT stores the following information:
• A list of entries that correspond to each cluster on the partition
Sector information is stored in the directory. In the FAT file system, directories are actually files that contain as many 32-byte slots as there are entries in the folder. This is also where deleted entries from a folder can be discovered. Figure 19.3 shows how the sector view is represented by a common forensic analysis tool.

Figure 19.3 The sector view.
NTFS
NTFS is a significant advancement in terms of data storage. It allows for long filenames, almost unlimited storage, and a more efficient method of accessing information. It also provides for much greater latency in deleted files, that is, deleted files stick around a lot longer in NTFS than they do in FAT. The following items are unique to NTFS. Instead of keeping the filenames in folder files, the entire file structure of NTFS is retained in a flat file database called the Master File Table (MFT):
• Improved support for metadata
• Advanced data structuring improves performance and reliability
• Improved disk space utilization with a maximum disk size of 7.8TB, or 264 sectors; sector sizes can vary in NTFS and are most easily controlled using a third-party partitioning tool such as Partition Magic.
The Role of the Forensic Examiner in Investigations and File Recovery
The forensic examiner is at his best when he is searching for deleted files and attempting to reconstruct a pattern of user behavior. The sidebar “Oops! Did I Delete That?” first appeared in the Chicago Daily Southtown column “Bits You Can Use.” In addition, this section also includes a discussion of data recovery and an insurance investigation article (see sidebar, “Don’t Touch That Computer! Data Recovery Following Fire, Flood, or Storm”).
Password Recovery
The following is a short list of the ways and types of passwords that can be recovered. Many useful tools that can be downloaded from the Internet for free will crack open system files that store passwords. Software programs, such as Peachtree (a financial database), Windows 98, certain FTP programs, and the like all store passwords in a way that allows their easy retrieval.
Recovering license keys for software is often an important step in reconstructing or virtualizing a disk image. Like passwords, without a valid license key the software won’t work. There are a number of useful programs that can recover software license keys from the registry of a computer that can be found with a quick Google search. Understanding the mind of the user can also be helpful in locating things such as password storage tools or simply thinking to search a computer for the word password. Many, many Web sites will pass the password down to a client machine through the Password field in HTML documents. Some developers have wised up to this “feature” and they strip it out before it comes down, but most of them do it on the client side. This means that with the proper intercepting tool, the password can be captured midstream on its way down to the client, before it gets stripped out.
Password cracking can be achieved with a minimal amount of skill and a great deal of patience. Having some idea of what the password is before cracking it will be helpful. You can also purchase both online services as well as software tools that will strip the password right out of a file, removing it completely. Word documents are particularly vulnerable, and zip files are particularly invulnerable. However, there is a method (and a free download) that can figure out the password of a zip file if a sample of a file that is known to be in the zip can be provided.
File Carving
In most investigations, the very first place a file system examination begins is with live files. Live files are those files that still have MFT entries. Link file, trash bin, Outlook Temporary (OLK) folders, recent items, ISO lists, Internet history, TIF, and thumb databases all constitute a discernible, unique pattern of user activity. As such, they hold particular interest. By exploring these files an examiner can make determinations about file origins, the usage of files, the distribution of files, and of course the current location of the files. But sometimes the subject has been very clever and removed all traces of activity. Or the suspect item may be a server, used merely as a repository for the files. Or maybe someone just wants to recover a file that they deleted a long, long time ago (see sidebar, “Oops, Did I Delete That?”).
When such need arises, the vast graveyard called the unallocated clusters could hold the last hope that the file can be recovered. By searching the unallocated clusters using a search tool designed for such things, and by using a known keyword in the file, one may locate the portion within the unallocated clusters where a file used to reside. Typically, search hits will be stored under a tab or in a particular area of the forensic toolset, and they may be browsed, one by one, along with a small excerpt from the surrounding bits. By clicking on the search hit, another pane of the software window may show a more expanded view of the hit location. If it is a document, with text, then that is great and you may see other words that were also known to have been in the target file. Now, in TV shows like CSI, of course the document is always there, and by running some reverse 128-bit decrytion sequencer to an inverted 12-bit decryption sequencer that reloops the hashing algorithm through a 256-bit decompiler by rethreading it into a multiplexing file marker, they can just right click and say “export this” and the file will print out, even if it’s not even on the computer that is being examined and never was. (Yes, I made all that up.)
In the real world, more often than not we find that our examinations are spurred and motivated and wholly created by someone’s abject paranoia. In these cases, no amount of digging will ever create the evidence that they want to see. That leaves only creative use of time stamps on documents to attempt to create an aroma of guilt about the subject piece. Sometimes we find that even after rooting through 300GB of unallocated clusters, leaving no stone unturned, the file just isn’t there. But sometimes, all pessimism aside, we find little bits and pieces of interesting things all salted around throughout the unallocated clusters.
The first place to turn is the automated carvers. By familiarizing ourselves with the hexadecimal patterns of file signatures (and I’ve provided a nice table for you here), we may view the hex of the unallocated clusters in a hex editor or in the hex pane of the examination tool. Or possibly we already know the type of file. Let’s say that we know the type of file because our client told us that they only use Word as their document editor. We scroll to the beginning of the section of text, which might look like this:
Figure sample file signature
From the text pane view of EnCase:
ĐÏ.ࡱá................>...þÿ .........
From the Hex view:
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 4F 6F 70 73 21 20 20 44 69 64
20 49 20 64 65 6C 65 74 65 20 74 68 61 74 3F 0D 42 79 20 53 63 6F 74 74 20
52 2E 20 45 6C 6C 69 73 0D 73 65 6C 6C 69 73 40 75 73 2E 72 67 6C 2E 63 6F
6D 0D 0D 54 68 65 20 66 69 6C 65 20 69 73 20 67 6F 6E 65 2E 20 20 49 74 92
73 20 6E 6F 74 20 69 6E 20 74 68 65 20 72 65 63 79 63 6C 65 20 62 69 6E 2E
20 59 6F 75 92 76 65 20 64 6F 6E 65 20 61 20 63 6F 6D 70 6C 65 74 65 20 73
Scrolling down in the text pane, we then find the following:
...............Oops! Did I delete that? By Scott R. Ellis The file is gone. It’s not in the recycle bin. You’ve. . . . . . .
By simply visually scanning the unallocated clusters, we can pick up where the file begins and, if the file signature isn’t in the provided list of signatures or if for some reason the carving scripts in the forensic software are incorrectly pulling files, they may need to be manually set up. Truly, for Word files, that is all you need to know. You need to be able to determine the end and the beginning of a file. Some software will ignore data in the file before and after the beginning and end of file signatures. This is true for many, many file types; I can’t tell you which ones because I haven’t tried them all. There are some file types that need a valid end-of-file (EOF) marker, but most don’t. However, if you don’t capture the true EOF (sensible marker or no), the file may look like garbage or all the original formatting will be scrambled or it won’t open. Some JPEG viewers (such as Adobe Photoshop) will throw an error if the EOF is not found. Others, such as Internet Explorer, won’t even notice. Here’s the trick—and it is a trick, and don’t let anyone tell you differently; they might not teach this in your average university computer forensics class: Starting with the file signature, highlight as many of the unallocated clusters after the file signature that you think would possibly be big enough to hold the entire file size. Now double that, and export it as raw data. Give it a .DOC extension and open it in Word. Voilá! The file has been reconstructed. Word will know where the document ends and it will show you that document. If you happen to catch a few extra documents at the end, or a JPG or whatever, Word will ignore them and show only the first document.
Unless some sort of drastic “wiping action” has taken place, as in the use of a third-party utility to delete data, I have almost always found that a great deal of deleted data is immediately available in EnCase (forensic software) within 20–25 minutes after a hard disk image is mounted, simply by running “recover folders” and sitting back and waiting while it runs. This is especially true when the drive has not been used at all since the time the data was deleted. Preferably, counsel will have taken steps to ensure that this is the case when a computer is the prime subject of an investigation. Often this is not the case, however. Many attorneys, IT, and HR directors “poke around” for information all on their own.
It is conceivable that up to 80% of deleted data on a computer may be readily available, without the necessity of carving, for up to two or three years, as long as the computer hasn’t seen extreme use (large amounts of files, or large amounts of copying and moving of very large files) that could conceivably overwrite the data.
Even so, searching unallocated clusters for file types typically does not require the creation of an index. Depending on the size of the drive, it may take four or five hours for the carving process to complete, and it may or may not be entirely successful, depending on the type of files that are being carved. For example, MPEG videos do not carve well at all, but there are ways around that. DOC and XLS files usually carve out quite nicely.
Indexing is something that is done strictly for the purpose of searching massive amounts of files for large numbers of keywords. We rarely use EnCase to search for keywords; we have found it better to use Relativity, our review environment, to allow the people who are interested in the keywords to do the keyword searching themselves as they perform their review. Relativity is built on an SQL platform on which indexing is a known and stable technology.
In other words (as in the bottom line), spending 15 to 25 minutes with a drive, an experienced examiner can provide a very succinct answer as to how long it would take to provide the files that they want. And, very likely, the answer could be, “Another 30 minutes and it will be yours.” Including time to set up, extract, and copy to disk, if everything is in perfect order, two hours is the upper limit. This is based on the foundation that the deleted data they are looking for was deleted in the last couple of weeks of the use of the computer. If they need to go back more than a couple of months, an examiner may end up carving into the unallocated clusters to find “lost” files—these are files for which part of or all of the master file table entry has been obliterated and portions of the files themselves may be overwritten.
Carving is considered one of the consummate forensic skills. Regardless of the few shortcuts that exist, carving requires a deep, disk-level knowledge of how files are stored, and it requires a certain intuition that cannot be “book taught.” Examiners gain this talent from years of looking at raw disk data. Regardless, even the most efficient and skilled of carvers will turn to their automated carving tools. Two things that the carving tools excel at is carving out images and print spool files (EMFs). What are they really bad at? The tools I use don’t even begin to work properly to carve out email files. General regular program (GREP) searching doesn’t provide for branching logic, so you can’t locate a qualified email header, every single time, and capture the end of it. The best you can do is create your own script to carve out the emails. GREP does not allow for any sort of true logic that would be useful or even efficient at capturing something as complex as the many variations of email headers that exist, but it does allow for many alterations of a single search term to be formulated with a single expression. For example, the words house, housing, houses, and housed could all be searched for with a single statement such as “hous[(e)|(es)|(ing)|(ed)]”. GREP can be useful, but it is not really a shortcut. Each option added to a GREP statement doubles the length of time the search will take to run. Searching for house(s) has the same run time as two separate keywords for house and houses. It also allows for efficient pattern matching. For example, if you wanted to find all the phone numbers on a computer for three particular area codes, you could formulate a GREP expression like this. Using a test file and running the search each time, an expression can be built that finds phone numbers in any of three area codes:
(708)|(312)|(847) Checks for the three area codes
[(]?(708)|(312)|(847)[-).]? Checks for parentheses and other formatting
[(]?(708)|(312)|(847)[-).]?###[-.]?#### Checks for the rest of the number
This statement will find any 10-digit string that is formatted like a phone number, as well as any 10-digit string that contains one of the three area codes. This last option, to check for any 10-digit number string, if run against an entire OS, will likely return numerous results that aren’t phone numbers. The question marks render the search for phone number formatting optional.
The following are the characters that are used to formulate a GREP expression. Typically, the best use of GREP is its ability to formulate pattern-matching searches. In GREP, the following symbols are used to formulate an expression:
· The period is a wildcard and means a space must be occupied by any character.
∗ The asterisk is a wildcard that means any character or no character. It will match multiple repetitions of the character as well.
? The character preceding the question mark must repeat 0 or 1 times. It provides instructions as to how to search for the character or grouping that precedes it.
+ This is like the question mark, only it must exist at least one or more times.
[·] Matches a list of characters. [hH]i matches hi and Hi (but not hHi!).
∧ This is a “not” and will exclude a part from a string.
[-] A range of characters such as (a-z) will find any single letter, a through z.
This will escape the standard GREP search symbols so that it may be included as part of the search. For example, a search string that has the ( symbol in it (such as a phone number) needs to have the parentheses escaped so that the string can be included as part of the search.
| This is an “or.” See previous sample search for area codes.
By preceding a hex character with x marks the next two characters as hexadecimal characters. Using this to locate a known hex string is more efficient than relying on it to be interpreted from Unicode or UTF.
Most forensic applications have stock scripts included that can carve for you. Many of the popular computer forensics applications can carve for you. They have scripted modules that will run, and all you have to do is select the signature you want and voilá, it carves it right out of the unallocated clusters for you. Sounds pretty slick, and it is slick—when it works. The problem is that some files, such as MPEG video, don’t have a set signature at the beginning and end of each file. So how can we carve them? Running an MPEG carver will make a mess. It’s a far better thing to do a “carve” by locating MPEG data, highlighting it, exporting it to a file, and giving it an MPEG extension.
Things to Know: How Time stamps Work
Let’s take an example: Bob in accounting has been discovered to be pilfering from the cash box. A forensics examiner is called in to examine his computer system to see if he has been engaging in any activities that would be against company policy and to see if he has been accessing areas of the network that he shouldn’t be. They want to know what he has been working on. A quick examination of his PC turns up a very large cache of pornography. A casual glance at the Entry Modified time stamp shows that the images were created nearly one year before Bob’s employment, so automatically the investigator disregards the images and moves onto his search for evidence of copying and deleting sensitive files to his local machine. The investigator begins to look at the deleted files. His view is filtered, so he is not looking at anything but deleted files. He leaves the view in “gallery” view so that he can see telltale images that may give clues as to any Web sites used during the timeframe of the suspected breaches. To his surprise, the investigator begins seeing images from that porn cache. He notices now that when a deleted file is overwritten, in the gallery view of the software the image that overwrote the deleted file is displayed. He makes the logical conclusion that the Entry Modified time stamp is somehow wrong.
On a Windows XP machine, an archive file is extracted. Entry Modified time stamps are xx:xx:xx, even though the archive was extracted to the file system on yy:yy:yy. Normally when a file is created on a system, it takes on the system date as its Date Created time stamp. Such is not the case with zip files.
Entry Modified, in the world of computer forensics, is that illustrious time stamp that has cinched many a case. It is a hidden time stamp that users never see, and few of them actually know about it. As such, they cannot change it. A very little-known fact about the Entry Modified time stamp is that it is constrained. It can be no later than the Date Created time stamp. (This is not true in Vista.)
When a zip file is created, the Date Created and Date Modified time stamps become the same.
Experimental Evidence
Examining and understanding how time stamps behave on individual PCs and operating systems provide some of the greatest challenges facing forensic examiners. This is not due to any great difficulty, but rather because of the difficulty in clearly explaining it to others. This examiner once read a quote from a prosecutor in a local newspaper that said, “We will clearly show that he viewed the image on three separate occasions.” In court the defense’s expert disabused her of the notion she held that Last Written, Last Accessed, Entry Modified, and Date Created time stamps were convenient little recordings of user activity. Rather, they are references mostly used by the operating system for its own arcane purposes. Table 19.1 compares the three known Windows time stamps with the four time stamps in EnCase.
Table 19.1
Comparison of Three Known Windows Time stamps with the Four EnCase Time stamps
| Windows | EnCase | Purpose |
| Date Created | Date Created | Typically this is the first time a file appeared on a system. It is not always accurate. |
| Date Modified | Last Written | Usually this is the time when a system last finished writing or changing information in a file. |
| Last Accessed | Last Accessed | This time stamp can be altered by any number of user and system actions. It should not be interpreted as the file having been opened and viewed. |
| N/A | Entry Modified | This is a system pointer that is inaccessible to users through the Explorer interface. It changes when the file changes size. |
XP
A zip file was created using a file with a Date Created time stamp of 12/23/07 10:40:53AM (see ID 1 in Table 19.2). It was then extracted and the time stamps were examined.
Table 19.2
Date Created Time stamp

Using Windows XP compressed folders, the file was then extracted to a separate file on a different system (ID 2 in Table 19.2). Date Created and Entry Modified time stamps, upon extraction, inherited the original Date Created time stamp of 12/23/07 10:40:53AM and Last Accessed of 04/28/08 01:56:07PM.
The system Entry Modified (not to be confused with Date Modified) became 04/28/08 01:57:12PM.
Various operating systems can perform various operations that will, en masse, alter the Entry Modified time stamp (see Table 19.3). For example, a tape restoration of a series of directories will create a time stamp adjustment in Entry Modified that corresponds to the date of the restoration. The original file is on another system somewhere and is inaccessible to the investigator (because he doesn’t know about it).
Table 19.3
Altering the Entry Modified Time stamp

In Table 19.3, Entry Modified becomes a part of a larger pattern of time stamps after an OS event. On a computer on which most of the time stamps have an Entry Modified time stamp that is sequential to a specific timeframe, it is now more difficult to determine when the file actually arrived on the system. As long as the date stamps are not inherited from the overwriting file by the overwritten file, examining the files that were overwritten by ID2 (Table 19.3), can reveal a No Later Than time. In other words, the file could not have appeared on the system prior to the file that it overwrote.
Vista
A zip file was created using a file with a Date Created time stamp of dd:mm:yyyy(a) and a date modified of dd:mm:yy(a). Using Windows Vista compressed folders, the file was then extracted to a separate file on the same system. Date Modified time stamps, on extraction, inherited the original time stamp of dd:mm:yyyy(a), but the Date Created time stamp reflected the true date. This is a significant change from XP. There are also tools available that will allow a user to mass-edit time stamps. Forensic examiners must always bear in mind that there are some very savvy users who research and understand antiforensics.
Email Headers and Time stamps, Email Receipts, and Bounced Messages
There is much confusion in the ediscovery industry and in computer forensics in general about how best to interpret email time stamps. Though it might not offer the perfect “every case” solution, this section reveals the intricacies of dealing with time stamps and how to interpret them correctly.
Regarding sources of email, SMTP has to relay email to its own domain. Helo/Ehlo allows a user to connect to the SMTP port and send email.
As most of us are aware, in 2007 the U.S. Congress enacted the Energy Policy Act of 2005 (http://www.epa.gov/oust/fedlaws/publ_109-058.pdf, Section 110. Daylight Savings). This act was passed into law by President George W. Bush on August 8, 2005. Among other provisions, such as subsidies for wind energy, reducing air pollution, and providing tax breaks to homeowners for making energy-conserving changes to their homes, it amended the Uniform Time Act of 1966 by changing the start and end dates for Daylight Savings Time (DST) beginning in 2007. Previously, clocks would be set ahead by an hour on the first Sunday of April and set back on the last Sunday of October. The new law changed this as follows: Starting in 2007 clocks were set ahead one hour on the first Sunday of March and then set back on the first Sunday in November. Aside from the additional confusion now facing everyone when we review email and attempt to translate Greenwich Mean Time (GMT) to a sensible local time, probably the only true noteworthy aspect of this new law is the extra daylight time afforded to children trick-or-treating on Halloween. Many observers have questioned whether or not the act actually resulted in a net energy savings.
In a world of remote Web-based email servers, it has been observed that some email sent through a Web mail interface will bear the time stamp of the time zone wherein the server resides. Either your server is in the Central Time zone or the clock on the server is set to the wrong time/time zone. Servers that send email mark the header of the email with the GMT stamp numerical value (noted in bold in the example that follows) as opposed to the actual time zone stamp. For example, instead of saying 08:00 CST, the header will say 08:00 (-0600). The GMT differential is used so that every email client interprets that stamp based on the time zone and time setting of itself and is able to account for things like Daylight Savings Time offsets. This is a dynamic interpretation; if I change the time zone of my computer, it will change the way Outlook shows me the time of each email, but it doesn’t actually physically change the email itself. For example, if an email server is located in Colorado, every email I send appears to have been sent from the Mountain Time zone. My email client interprets the Time Received of an email based on when my server received the mail, not when my email client downloads the email from my server.
If a server is in the Central Time zone and the client is in Mountain Time, the normal Web mail interface will not be cognizant of the client’s time zone. Hence those are the times you’ll see. I checked a Webmail account on a server in California that I use and it does the same thing. Here I’ve broken up the header to show step by step how it moved. Here is, first, the entire header in its original context, followed by a breakdown of how I interpret each transaction in the header:
∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗
Received: from p01c11m096.mxlogic.net (208.65.144.247) by mail.us.rgl.com
(192.168.0.12) with Microsoft SMTP Server id 8.0.751.0; Fri, 30 Nov 2007
21:03:15 -0700
Received: from unknown [65.54.246.112] (EHLO bay0-omc1-s40.bay0.hotmail.com)
by p01c11m096.mxlogic.net (mxl_mta-5.2.0-1) with ESMTP id
23cd0574.3307895728.120458.00-105.p01c11m096.mxlogic.net (envelope-from
<[email protected]>); Fri, 30 Nov 2007 20:59:46 -0700 (MST)
Received: from BAY108-W37 ([65.54.162.137]) by bay0-omc1-s40.bay0.hotmail.com
with Microsoft SMTPSVC(6.0.3790.3959); Fri, 30 Nov 2007 19:59:46 -0800
Message-ID: <[email protected]>
Return-Path: [email protected]
Content-Type: multipart/alternative; boundary=“=_reb-r538638D0-t4750DC32”
X-Originating-IP: [71.212.198.249]
From: Test Account <[email protected]>
To: Bill Nelson <[email protected]>, Scott Ellis <[email protected]>
Subject: FW: Norton Anti Virus
Date: Fri, 30 Nov 2007 21:59:46 -0600
Importance: Normal
In-Reply-To: <[email protected]>
References: <[email protected]>
MIME-Version: 1.0
X-OriginalArrivalTime: 01 Dec 2007 03:59:46.0488 (UTC) FILETIME=[9CAC5B80:01C833CE]
X-Processed-By: Rebuild v2.0-0
X-Spam: [F=0.0038471784; B=0.500(0); spf=0.500; CM=0.500; S=0.010(2007110801); MH=0.500(2007113048); R=0.276(1071030201529); SC=none; SS=0.500]
X-MAIL-FROM: <[email protected]>
X-SOURCE-IP: [65.54.246.112]
X-AnalysisOut: [v=1.0 c=0 a=Db0T9Pbbji75CibVOCAA:9 a=rYVTvsE0vOPdh0IEP8MA:]
X-AnalysisOut: [7 a=TaS_S6-EMopkTzdPlCr4MVJL5DQA:4 a=NCG-xuS670wA:10 a=T-0]
X-AnalysisOut: [QtiWyBeMA:10 a=r9zUxlSq4yJzxRie7pAA:7 a=EWQMng83CrhB0XWP0h]
X-AnalysisOut: [vbCEdheDsA:4 a=EfJqPEOeqlMA:10 a=37WNUvjkh6kA:10]
∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗∗
Looks like a bunch of garbage, right? Here it is, step by step, transaction by transaction, in reverse chronological order:
Received: from p01c11m096.mxlogic.net (208.65.144.247) by mail.us.rgl.com
(192.168.0.12) with Microsoft SMTP Server id 8.0.751.0; Fri, 30 Nov 2007 21:03:15 -0700
Received: from unknown [65.54.246.112] (EHLO bay0-omc1-s40.bay0.hotmail.com)
by p01c11m096.mxlogic.net (mxl_mta-5.2.0-1) with ESMTP id
23cd0574.3307895728.120458.00-105.p01c11m096.mxlogic.net (envelope-from
<[email protected]>); Fri, 30 Nov 2007 20:59:46 -0700 (MST)
– The email server receives the sender’s email in this next section. On most networks, the mail server is rarely the same machine on which a user created the email. This next item in the header of the email shows that the email server is located in the Pacific Time zone. 65.54.246.112, the x-origin stamp, is the actual IP address of the computer that sent the email:
Received: from BAY108-W37 ([65.54.162.137]) by bay0-omc1-s40.bay0.hotmail.com
with Microsoft SMTPSVC(6.0.3790.3959); Fri, 30 Nov 2007 19:59:46 -0800
Message-ID: <[email protected]>
Return-Path: [email protected]
– This content was produced on the server where the Webmail application resides. Technically, the email was created on the Web client application with only one degree of separation between the originating IP and the sender IP. By examining the order and type of IP addresses logged in the header, a trail can be created that shows the path of mail servers that the email traversed before arriving at its destination. This machine is the one that is likely in the Central Time zone, since it can be verified by the -0600 in the following. The X-originating IP address is the IP address of the sender’s external Internet connection IP address in her house and the X-Source IP address is the IP address of the Webmail server she logged into on this day. This IP address is also subject to change because they have many Webmail servers as well. In fact, comparisons to older emails sent on different dates show that it is different. Originating IP address is also subject to change since a DSL or cable Internet is very likely a dynamic account, but it (likely) won’t change as frequently as the X-source:
Content-Type: multipart/alternative; boundary=“=_reb-r538638D0-t4750DC32”
X-Originating-IP: [71.212.198.249]
From: Test Account <@hotmail.com>
To: Bill Nelson <[email protected]>, Scott Ellis <[email protected]>
Subject: FW: Norton Anti Virus
Date: Fri, 30 Nov 2007 21:59:46 -0600
Importance: Normal
In-Reply-To: <[email protected]>
References: <[email protected]>
MIME-Version: 1.0
X-OriginalArrivalTime: 01 Dec 2007 03:59:46.0488 (UTC) FILETIME=[9CAC5B80:01C833CE]
X-Processed-By: Rebuild v2.0-0
X-Spam: [F=0.0038471784; B=0.500(0); spf=0.500; CM=0.500; S=0.010(2007110801); MH=0.500(2007113048); R=0.276(1071030201529); SC=none; SS=0.500]
X-MAIL-FROM: <[email protected]>
X-SOURCE-IP: [65.54.246.112]
X-AnalysisOut: [v=1.0 c=0 a=Db0T9Pbbji75CibVOCAA:9 a=rYVTvsE0vOPdh0IEP8MA:]
X-AnalysisOut: [7 a=TaS_S6-EMopkTzdPlCr4MVJL5DQA:4 a=NCG-xuS670wA:10 a=T-0]
X-AnalysisOut: [QtiWyBeMA:10 a=r9zUxlSq4yJzxRie7pAA:7 a=EWQMng83CrhB0XWP0h]
X-AnalysisOut: [vbCEdheDsA:4 a=EfJqPEOeqlMA:10 a=37WNUvjkh6kA:10]
From: Test Account [mailto:[email protected]]
Sent: Friday, November 30, 2007 10:00 PM
To: Bill Nelson; Scott Ellis
Subject: FW: Norton Anti Virus
Bill and Scott,
By the way, it was 8:57 my time when I sent the last email, however, my hotmail shows that it was 9:57 pm. Not sure if their server is on Central time or not. Scott, can you help with that question? Thanks.
Anonymous
From: [email protected]
To: [email protected]; [email protected]
Subject: Norton Anti Virus
Date: Fri, 30 Nov 2007 21:57:16 -0600
Bill and Scott,
I am on the computer now and have a question for you. Can you please call me?
Anonymous
Steganography “Covered Writing”
Steganography tools provide a method that allows a user to hide a file in plain sight. For example, there are a number of stego software tools that allow the user to hide one image inside another. Some of these do it by simply appending the “hidden” file at the tail end of a JPEG file and then add a pointer to the beginning of the file. The most common way that steganography is discovered on a machine is through the detection of the steganography software on the machine. Then comes the arduous task of locating 11 of the files that may possibly contain hidden data. Other, more manual stego techniques may be as simple as hiding text behind other text. In Microsoft Word, text boxes can be placed right over the top of other text, formatted in such a way as to render the text undetectable to a casual observer. Forensic tools will allow the analyst to locate this text, but on opening the file the text won’t be readily visible. Another method is to hide images behind other images using the layers feature of some photo enhancement tools, such as Photoshop.
StegAlyzerAS is a tool created by Backbone Security to detect steganography on a system. It works by both searching for known stego artifacts as well as by searching for the program files associated with over 650 steganography toolsets. Steganography hash sets are also available within the NIST database of hash sets. Hash sets are databases of MD5 hashes of known unique files associated with a particular application.
5. First Principles
In science, first principles refer to going back to the most basic nature of a thing. For example, in physics, an experiment is ab initio (from first principles) if it only subsumes a parameterization of known irrefutable laws of physics. The experiment of calculation does not make assumptions through modeling or assumptive logic.
First principles, or ab initio, may or may not be something that a court will understand, depending on the court and the types of cases it tries. Ultimately the very best evidence is that which can be easily duplicated. In observation of a compromised system in its live state, even if the observation photographed or videoed may be admitted as evidence but the events viewed cannot be duplicated, the veracity of the events will easily be questioned by the opposition.
During an investigation of a defendant’s PC, an examiner found that a piece of software on the computer behaved erratically. This behavior had occurred after the computer had been booted from a restored image of the PC. The behavior was photographed and introduced in court as evidence. The behavior was mentioned during a cross-examination and had not, originally, been intended as use for evidence; it was simply something that the examiner recalled seeing during his investigation, that the list of files a piece of software would display would change. The prosecution was outraged because this statement harmed his case to a great deal. The instability and erratic behavior of the software was one of the underpinnings of the defense. The examiner, in response to the prosecutor’s accusations of ineptitude, replied that he had a series of photographs that demonstrated the behavior. The prosecutor requested the photos, but the examiner didn’t have them in court. He brought them the next day, at which time, when the jury was not in the room, the prosecutor requested the photos, reviewed them, and promptly let the matter drop.
It would have been a far more powerful thing to have produced the photographs at the time of the statement; but it may have also led the prosecution to an ab initio effort—one that may have shown that the defense expert’s findings were irreproducible. In an expert testimony, the more powerful and remarkable a piece of evidence, the more likely it is to be challenged by the opposition. It is an intricate game because such a challenge may ultimately destroy the opposition’s case, since a corroborative result would only serve to increase the veracity and reliability of the expert’s testimony. Whether you are defense, prosecution, or plaintiff, the strongest evidence is that which is irrefutable and relies on first principles. Aristotle defined it as those circumstances where “for the same (characteristic) simultaneously to belong and not belong to the same (object) in the same (way) is impossible.” In less obfuscating, 21st-century terms, the following interpretation is applicable: One thing can’t be two different things at the same time in the same circumstance; there is only one truth, and it is self-evidentiary and not open to interpretation. For example, when a computer hard drive is imaged, the opposition may also image the same hard drive. If proper procedures are followed, there is no possible way that different MD5 hashes could result. Black cannot be white.
The lesson learned? Never build your foundation on irreproducible evidence. To do so is tantamount to building the case on “circumstantial” evidence.
6. Hacking a Windows XP Password
There are many, many methods to decrypt or “hack” a Windows password. This section lists some of them. One of the more interesting methods of cracking passwords through the use of forensic methods is hacking the Active Directory. It is not covered here, but suffice it to say that there is an awesome amount of information stored in the Active Directory file of a domain server. With the correct tools and settings in place, Bitlocker locked PCs can be accessed and passwords can be viewed in plaintext with just a few simple, readily available scripts.
Net User Password Hack
If you have access to a machine, this is an easy thing, and the instructions to do it can easily be found on YouTube. Type net users at the Windows command line. Pick a user. Type net userusername∗. (You have to type the asterisk or it won’t work.) You will then, regardless of your privileges, be allowed to change any password, including the local machine administrator password.
Lanman Hashes and Rainbow Tables
• The following procedure can be used to “reverse-engineer” the password from where it is stored in Windows. Lan Manager (or Lanman, or LM) has been used by Windows, in versions prior to Windows Vista, to store passwords that are shorter than 15 characters. The vast majority of passwords are stored in this format. LM hashes are computed via a short series of actions. The following items contribute to the weakness of the hash:
• Password is converted to all uppercase.
• Passwords longer than seven characters are divided into two halves. By visual inspection of the hash, this allows us to determine whether the second half is padding. We can do this by viewing all the LM hashes on a system and observing whether the second halves of any of the hashes are the same. This will speed up the process of decrypting the hash.
• There is no salt. In cryptography, salt is random bits that are thrown in to prevent large lookup tables of values from being developed.
Windows will store passwords using the Lanman hash. Windows Vista has changed this. For all versions of Windows except Vista, about 70GB of what are called rainbow tables can be downloaded from the Internet. Using a tool such as the many that are found on Backtrack will capture the actual hashes that are stored for the password on the physical disk. Analysis of the hashes will show whether or not the hashes are in use as passwords. Rainbow tables, which can be downloaded from the Web in a single 70GB table, are simply lookup tables of every possible iteration of the hashes. By entering the hash value, the password can be easily and quickly reverse-engineered and access to files can be gained. A favorite method of hackers is to install command-line software on remote machines that will allow access to the Lanman hashes and will send them via FTP to the hacker. Once the hacker has admin rights, he owns the machine.
Password Reset Disk
Emergency Boot CD (EBCD) is a Linux-based tool that allows you to boot a computer that has an unknown password. Using this command-line tool, you can reset the administrator password very easily. It will not tell you the plaintext of the password, but it will clear it so that the machine can be accessed through something like VMware with a blank password.
Memory Analysis and the Trojan Defense
One method of retrieving passwords and encryption keys is through memory analysis—physical RAM. RAM can be acquired using a variety of relatively nonintrusive methods. HBGary.com offers a free tool that will capture RAM with very minimal impact. In addition to extracting encryption keys, RAM analysis can be used to either defeat or corroborate the Trojan defense. The Responder tool from HBGary (single-user license) provides in-depth analysis and reporting on the many malware activities that can be detected in a RAM environment. The Trojan defense is commonly used by innocent and guilty parties to explain unlawful actions that have occurred on their computers. The following items represent a brief overview of the types of things that can be accomplished through RAM analysis:
• A hidden driver is a 100% indicator of a bad guy. Hidden drivers can be located through analysis of the physical memory.
• Using tools such as FileMon, TCPView, and RegMon, you can usually readily identify malware infections. There is a small number of advanced malwares that are capable of doing things such as rolling up completely (poof, it’s gone!) when they detect the presence of investigative tools or that are capable of escaping a virtualized host. All the same, when conducting a malware forensic analysis, be sure to isolate the system from the network.
• RAM analysis using a tool such as HBGary’s Responder can allow reverse-engineering of the processes that are running and can uncover potential malware behavioral capabilities. As this science progresses, a much greater ability to easily and quickly detect malware can be expected.
User Artifact Analysis
There is nothing worse than facing off against an opposing expert who has not done his artifact analysis on a case. Due to an increasing workload in this field, experts are often taking shortcuts that, in the long run, really make more work for everyone. In life and on computers, the actions people take leave behind artifacts. The following is a short list of artifacts that are readily viewed using any method of analysis:
Users create all these artifacts, either knowingly or unknowingly, and aspects of them can be reviewed and understood to indicate that certain actions on the computer took place—for example, a folder in My Documents called “fast trains” that contains pictures of Europe’s TGV and surrounding countryside, TIF sites that show the user booking travel to Europe, installed software for a Casio Exilim digital camera, EXIF data that shows the photos were taken with a Casio Exilim, and email confirmations and discussions about the planned trip all work together to show that the user of that account on that PC did very likely take a trip to Europe and did take the photos. Not that there is anything wrong with taking pictures of trains, but if the subject of the investigation is a suspected terrorist and he has ties with a group that was discovered to be planning an attack on a train, this evidence would be very valuable.
It is the sum of the parts that matters the most. A single image of a train found in the user’s TIF would be virtually meaningless. Multiple pictures of trains in his TIF could also be meaningless; maybe he likes trains or maybe someone sent him a link that he clicked to take him to a Web site about trains. It’s likely he won’t even remember having visited the site. It is the forensic examiner’s first priority to ensure that all the user artifacts are considered when making a determination about any behavior.
Recovering Lost and Deleted Files
Unless some sort of drastic “wiping action” has taken place, as in the use of a third-party utility to delete data or if the disk is part of a RAIDed set, I have almost always found that deleted data is immediately available in EnCase (forensic software I use) within 20 to 25 minutes after a hard disk image is mounted. This is especially true when the drive has not been used at all since the time the data was deleted.
Software Installation
Nearly every software installation will offer to drop one on your desktop, in your Start menu, and on your quick launch tool bar at the time of program installation. Whenever a user double-clicks on a file, a link file is created in the Recent folder located at the root of Documents and Settings. This is a hidden file.
Recent Files
In Windows XP (and similar locations exist in other versions), link files are stored in the Recent folder under Documents and Settings. Whenever a user double-clicks on a file, a link file is created. Clicking the Start button in Windows and navigating to the My Recent Documents link will show a list of the last 15 documents that a user has clicked on. What most users don’t realize is that the C:Documents and Settings$user name$Recent folder will potentially reveal hundreds of documents that have been viewed by the user. This list is indisputably a list of documents that the user has viewed. Interestingly, in Windows 2000, if the Preserve History feature of the Windows Media Player is turned off, no link files will be created. The only way to make any legitimate determination about the use of a file is to view the Last Accessed time, which has been shown in several cases to be inconsistent and unreliable in certain circumstances. Be very careful when using this time stamp as part of your defense or prosecution. It is a loaded weapon, ready to go off.
Start Menu
The Start menu is built on shortcuts. Every item in the Start file has a corresponding .LNK file. Examining Last Accessed or Date Created time stamps may shed light on when software was installed and last used.
Extracting email is an invaluable tool for researching and finding out thoughts and motives of a suspect in any investigation. Email can be extracted from traditional client-based applications such as Outlook Express, Lotus Notes, Outlook, Eudora, and Netscape Mail as well as from common Webmail apps such as Gmail, Hotmail, Yahoo Mail, and Excite. Reviewing log files from server-based applications such as Outlook Webmail can show a user, for example, accessing and using his Webmail after employment termination. It is important that companies realize that they should terminate access to such accounts the day a user’s employment is terminated.
Internet History
Forensic analysis of a user’s Internet history can reveal much useful information. It can also show the exact code that may have downloaded on a client machine and resulted in an infection of the system with a virus. Forensic examiners should actively familiarize themselves with the most recent, known exploits.
Typed URLs is a registry key. It will store the last 10 addresses that a user has typed into a Web browser address field. I once had a fed try to say that everything that appeared in the drop-down window was a “typed” URL. This is not the case. The only definitive source of showing the actual typed URLs is the registry key. Just one look at the screen shown in Figure 19.4 should clearly demonstrate that the user never would have “typed” all these entries. Yet that is exactly what a Department of Homeland Security Agent sat on the witness stand and swore, under oath, was true. In Figure 19.4, simply typing in fil spawns a list of URLs that were never typed but rather are the result of either the user having opened a file or a program having opened one. The highlighted file entered the history shown as a result of installing the software, not as a result of the user “typing” the filename. Many items in the history wind their way into it through regular software use, with files being accessed as an indirect result of user activity.

Figure 19.4 Spawning a list of URLs that were never typed (the Google one is deleted).
7. Network Analysis
Many investigations require a very hands-off approach in which the only forensics that can be collected is network traffic. Every machine is assigned an IP address and a MAC address. It is like an IP address on layer 3, but the MAC address sits on Layer 2. It is quite like a phone number in that it is unique. Software that is used to examine network traffic is categorized as a sniffer. Tools such as Wireshark and Colasoft are two examples of sniffers. They can be used to view, analyze, and capture all the IP traffic that comes across a port.
Switches are not promiscuous, however. To view the traffic coming across a switch you can either put a hub in line with the traffic (between the target and the switch) and plug the sniffer into the hub with it, or ports can be spanned. Spanning, or mirroring, allows one port on a switch to copy and distribute network traffic in a way such that the sniffer can see everything. The argument could be made in court that the wrong port was accidentally spanned, but this argument quickly falls apart because all network packets contain both the machine and IP address of a machine. ARP poisoning is the practice of spoofing another user’s IP address, however. This would be the smartest defense, but if a hub is used on a switched port, with the hub wired directly to the port, a greater degree of forensic certainty can be achieved. The only two computers that should be connected to the hub are the examiner and target machines.
Protocols
In the world of IP, the various languages of network traffic that are used to perform various tasks and operations are called protocols. Each protocol has its own special way of organizing and forming its packets. Unauthorized protocols viewed on a port are a good example of a type of action that might be expected from a rogue machine or employee. Network sniffing for email (SMTP and POP) traffic and capturing it can, depending on the sniffer used, allow the examiner to view live email traffic coming off the target machine. Viewing the Web (HTTP) protocol allows the examiner to capture images and text from Web sites that the target is navigating, in real time.
Analysis
Once the capture of traffic has been completed, analysis must take place. Colasoft offers a packet analyzer that can carve out and filter out the various types of traffic. A good deal of traffic can be eliminated as just “noise” on the line. Filters can be created that will capture the specific protocols, such as VoIP. Examination of the protocols for protocol obfuscation can (if it is not found) eliminate the possibility that a user has a malware infection, and it can identify a user that is using open ports on the firewall to transmit illicit traffic. They sneak legitimate traffic over open ports, masking their nefarious activities over legitimate ports, knowing that the ports are open. This can be done with whitespace inside of an existing protocol, with HTTP, VoIP, and many others. The thing to look for, which will usually be clearly shown, is something like:
VOIP>SMTP
This basically means that VOIP is talking to a mail server. This is not normal.3
Another thing to look for is protocols coming off a box that isn’t purposed for that task. It’s all context: who should be doing what with whom. Why is the workstation suddenly popping a DNS server? A real-world example is when a van comes screaming into your neighborhood. Two guys jump out and break down the door of your house and grab your wife and kids and drag them out of the house. Then they come and get you. Seems a little fishy, right? But it is a perfectly normal thing to have happen if the two guys are firemen, the van was a fire truck, and your house is on fire.
8. Computer Forensics Applied
This section details the various ways in which computer forensics is applied professionally. By no means does this cover the extent to which computer forensics is becoming one of the hottest computer careers. It focuses on the consulting side of things, with less attention to corporate or law enforcement applications. Generally speaking, the average forensic consultant handles a broader variety of cases than corporate or law enforcement disciplines, with a broader applicability.
Tracking, Inventory, Location of Files, Paperwork, Backups, and So On
These items are all useful areas of knowledge in providing consultative advisement to corporate, legal, and law-enforcement clients. During the process of discovery and warrant creation, knowledge of how users store and access data at a very deep level is critical to success.
Testimonial
Even if the work does not involve the court system directly—for example, a technician that provides forensic backups of computers and is certified—you may someday be called to provide discovery in a litigation matter. Subsequently, you may be required to testify.
Experience Needed
In computer forensics, the key to a successful technologist is experience. Nothing can substitute for experience, but a good system of learned knowledge that represents at least the last 10 years is welcome.
Job Description, Technologist
Practitioners must possess extreme abilities in adapting to new situations. The environment is always changing.
Job description:
Senior Forensic Examiner and eDiscovery Specialist
Prepared by Scott R. Ellis, 11/01/2007
• Forensics investigative work which includes imaging hard drives, extracting data and files for ediscovery production, development of custom scripts as required to extract or locate data. On occasion this includes performing detailed analyses of user activity, images, and language that may be of an undesirable, distasteful, and potentially criminal format. For this reason, a manager must be notified immediately upon the discovery of any such materials.
• Creation of detailed reports that lay out findings in a meaningful and understandable format. All reports will be reviewed and OK’d by manager before delivery to clients.
• Use of software tools such as FTK, EnCase, VMware, Recovery for Exchange, IDEA, LAW, and Relativity.
• Processing ediscovery and some paper discovery.
• Be responsive to opportunities for publication such as papers, articles, blog, or book chapter requests. All publications should be reviewed by manager and marketing before being submitted to requestor.
• Use technology such as servers, email, time reporting, and scheduling systems to perform job duties and archive work in client folders.
• Managing lab assets (installation of software, Windows updates, antivirus, maintaining backup strategy, hardware installation, tracking hardware and software inventory).
• Work week will be 40 hours per week, with occasional weekends as needed to meet customer deadlines.
• Deposition or testimony as needed.
• Occasional evenings and out of town to accommodate client schedules for forensic investigative work.
• Occasional evenings and out of town to attend seminars, CPE or technology classes as suggested by self or by manager, and marketing events.
• Other technology related duties as may be assigned by manager in the support of the company mission as it relates to technology or forensic technology matters
Job Description Management
A manager in computer forensics is usually a working manager. He is responsible for guiding and developing staff as well as communicating requirements to the executive level. His work duties will typically encompass everything mentioned in the previous description.
Commercial Uses
Archival, ghosting images, dd, recover lost partitions, etc. are all applications of computer forensics at a commercial level. Data recovery embraces a great many of the practices typically attributed to computer forensics. Archival and retrieval of information for any number of purposes, not just litigation, is required as is a forensic level of system knowledge.
Solid Background
To become a professional practitioner of computer forensics, there are three requirements to a successful career. Certainly there are people, such as many who attain certification through law-enforcement agencies, that have skipped or bypassed completely the professional experience or scientific training necessary to be a true computer forensic scientist. That is not to degrade the law-enforcement forensic examiner. His mission is traditionally quite different from that of a civilian, and these pros are frighteningly adept and proficient at accomplishing their objective, which is to locate evidence of criminal conduct and prosecute in court. Their lack of education in the traditional sense should never lead one to a desultory conclusion. No amount of parchment will ever broaden a mind; the forensic examiner must have a broad mind that eschews constraints and boxed-in thinking.
The background needed for a successful career in computer forensics is much like that of any other except that, as a testifying expert, publication will give greater credence to a testimony than even the most advanced pedigree. The exception would be the computer forensic scientist who holds a Ph. D. and happened to write her doctoral thesis on just the thing that is being called into question on the case. Interestingly, at this time, this author has yet to meet anyone with a Ph. D. (or any university degree for that matter), in computer forensics. We can then narrow down the requirements to these three items. Coincidentally, these are also the items required to qualify as an expert witness in most courts:
The weight of each of these items can vary. To what degree depends on who is asking, but suffice it to say that a deficiency in any area may be overcome by strengths in the other two. The following sections provide a more in-depth view of each requirement.
Education/Certification
A strong foundation at the university level in mathematics and science provides the best mental training that can be obtained in computer forensics. Of course, anyone with an extremely strong understanding of computers can surpass and exceed any expectations in this area. Of special consideration are the following topics. The best forensic examiner has a strong foundation in these areas and can qualify not just as a forensic expert with limited ability to testify as to the functions and specific mechanical abilities of software, but as a computer expert who can testify to the many aspects of both hardware and software.
Understand how database technologies, including MS SQL, Oracle, Access, My SQL, and others, interact with applications and how thin and fat clients interact and transfer data. Where do they store temporary files? What happens during a maintenance procedure? How are indexes built, and is the database software disk aware?
Programming and Experience
Background in computer programming is an essential piece. The following software languages must be understood by any well-rounded forensic examiner:
Develop a familiarity with the purpose and operation of technologies that have not become mainstream but have a devoted cult following. At one time such things as virtualization, Linux, and even Windows lived on the bleeding edge, but from being very much on the “fringe” have steadily become more mainstream.
• If it runs on a computer and has an installed base of greater than 10,000 users, it is worth reviewing.
• Internet technologies should be well understood. JavaScript, Java, HTML, ASP, ASPRX, cold fusion, databases, etc. are all Internet technologies that may end up at the heart of a forensic examiner’s investigation.
• Experience. Critical to either establishing oneself in a career as a corporate computer forensic examiner or as a consultant, experience working in the field provides the confidence and knowledge-base needed to successfully complete a forensic examination. From cradle to grave, from the initial interviews with the client to forensic collection, examination, reporting, and testifying, experience will guide every step. No suitable substitute exists. Most forensic examiners come into the career later in life after serving as a network or software consultant. Some arrive in this field after years in law enforcement where almost anyone who can turn on a computer winds up taking some computer forensic training.
Communications
• Computer forensics is entirely about the ability to look at a computer system and subsequently explain, in plain English, the analysis. A typical report may consist of the following sections:
– Healthcare information data on system
– User access to credit-card numbers
– Date range of possible breach and order handlers
– All other users logged in during Crist/Russel Logins
• Login failures activity coinciding with account activity
Each section either represents actual tables, images, and calculated findings, or it represents judgments, impressions, and interpretations of those findings. Finally, the report should contain references to contacts involved in the investigation. A good report conveys the big picture, and translates findings into substantial knowledge without leaving any trailing questions asked and unanswered. Sometimes findings are arrived at through a complex procedure such as a series of SQL queries. Conclusions that depend on such findings should be as detailed as necessary so that opposing experts can reconstruct the findings without difficulty.
Almost any large company requires some measure of forensic certified staff. Furthermore, the forensic collection and ediscovery field continues to grow. Virtually every branch of law enforcement—FBI, CIA, Homeland Security, and state and local agencies—all use computer forensics to some degree. Accounting firms and law firms of almost any size greater than 20 need certified forensic and ediscovery specialists that can both support their forensic practice areas as well as grow business.
Publications
Publishing articles in well-known trade journals goes a long way toward establishing credibility. The following things are nearly always true:
• A long list of publications not only creates in a jury the perception that the expert possess special knowledge that warrants publication; it also shows the expert’s ability to communicate. Articles published on the Internet typically do not count unless they are for well-known publications that have a printed publication as well as an online magazine.
• Publishing in and of itself creates a certain amount of risk. Anything that an expert writes or says or posts online may come back to haunt him in court. Be sure to remember to check, double check, and triple check anything that could be of questionable interpretation.
• When you write, you get smarter. Writing forces an author to conduct research and refreshes the memory on long unused skills.
Getting published in the first place is perhaps the most difficult task. Make contact with publishers and editors at trade shows. Ask around, and seek to make contact and establish relationships with published authors and bloggers. Most important, always seek to gain knowledge and deeper understanding of the work.
9. Testifying as an Expert
Testifying in court is difficult work. As with any type of performance, the expert testifying must know her material, inside and out. She must be calm and collected and have confidence in her assertions. Often, degrees of uncertainty may exist within a testimony. It is the expert’s duty to convey those “gray” areas with clarity and alacrity. She must be able to confidently speak of things in terms of degrees of certainty and clear probabilities, using language that is accessible and readily understood by the jury.
In terms of degrees of certainty, often we find ourselves discussing the “degree of difficulty” of performing an operation. This is usually when judges ask whether or not an operation has occurred through direct user interaction or through an automated, programmatic, or normal maintenance procedure. For example, it is well within the normal operation of complex database software to reindex or compact its tables and reorganize the way the data is arranged on the surface of the disk. It is not, however, within the normal operation of the database program to completely obliterate itself and all its program, help, and system files 13 times over a period of three weeks, all in the time leading up to requests for discovery from the opposition. Such information, when forensically available, will then be followed by the question of “Can we know who did it?” And that question, if the files exist on a server where security is relaxed, can be nearly impossible to answer.
Degrees of Certainty
Most computer forensic practitioners ply their trade in civil court. A typical case may involve monetary damages or loss. From a computer forensics point of view, evidence that you have extracted from a computer may be used by the attorneys to establish liability, that the plaintiff was damaged by the actions of the defendant. Your work may be the lynchpin of the entire case. You cannot be wrong. The burden to prove the amount of damages is less stringent once you’ve established that damage was inflicted, and since a single email may be the foundation for that proof, its provenance should prevail under even the most expert scrutiny. Whether or not the damage was inflicted may become a point of contention that the defense uses to pry and crack open your testimony.
The following sections may prove useful in your answers. The burden of proof will fall on the defense to show that the alleged damages are not accurate. There are three general categories of “truth” that can be used to clarify for a judge, jury, or attorney the weight of evidence. See the section on “Rules of Evidence” for more on things such as relevance and materiality.
Generally True
Generally speaking, something is generally true if under normal and general use the same thing always occurs. For example, if a user deletes a file, generally speaking it will go into the recycle bin. This is not true if:
Reasonable Degree of Certainty
If it smells like a fish and looks like a fish, generally speaking, it is a fish. However, without dissection and DNA analysis, there is the possibility that it is a fake, especially if someone is jumping up and down and screaming that it is a fake. Short of expensive testing, one may consider other factors. Where was the fish found? Who was in possession of the fish when it was found? We begin to rely on more than just looking at the fish to see if it is a fish.
Computer forensic evidence is much the same. For example, in an employment dispute, an employee may be accused of sending sensitive and proprietary documents to her personal Webmail account. The employer introduces forensic evidence that the files were sent from her work email account during her period of employment on days when she was in the office.
Pretty straightforward, right? Not really. Let’s go back in time to two months before the employee was fired. Let’s go back to the day after she got a very bad performance review and left for the day because she was so upset. Everyone knew what was going on, and they knew that her time is limited. Two weeks later she filed an EEOC complaint. The IT manager in this organization, a seemingly mild-mannered, helpful savant, was getting ready to start his own company as a silent partner in competition with his employer. He wanted information. His partners want information in exchange for a 20% stake. As an IT manager, he had administrative rights and could access the troubled employee’s email account and began to send files to her Webmail account. As an IT administrator, he had system and network access that would easily allow him to crack her Webmail account and determine the password. All he had to do was spoof her login page and store it on a site where he could pick it up from somewhere else. If he was particularly interested in keeping his own home and work systems free of the files, he could wardrive her house, hack her home wireless (lucky him, it is unsecured), and then use terminal services to access her home computer, log into her Webmail account (while she is home), and view the files to ensure that they appear as “read.” This scenario may seem farfetched but it is not; this is not hard to do.
For anyone with the IT manager’s level of knowledge, lack of ethics, and opportunity, this is likely the only way that he would go about stealing information. There is no other way that leaves him so completely out of the possible running of suspects.
There is no magic wand in computer forensics. The data is either there or it isn’t, despite what Hollywood says about the subject. If an IT director makes the brash decision to reinstall the OS on a system that has been compromised and later realizes he might want to use a forensic investigator to find out what files were viewed, stolen, or modified, he can’t just dial up his local forensics tech and have him pop in over tea, wave his magic wand, and recover all the data that was overwritten. Here is the raw, unadulterated truth: If you have 30GB of unallocated clusters and you copy the DVD Finding Nemo onto the drive until the disk is full, nobody (and I really mean this), nobody will be able to extract a complete file from the unallocated clusters. Sure, they might find a couple of keyword hits in file slack and maybe, just maybe, if the stars align and Jupiter is in retrograde and Venus is rising, maybe they can pull a tiny little complete file out of the slack or out of the MFT. Small files, less than 128 bytes, are stored directly in the MFT and won’t ever make it out to allocated space. This can be observed by viewing the $MFT file.
When making the determination “reasonable degree of forensic certainty,” all things must be considered. Every possible scenario that could occur must flash before the forensic practitioner’s eyes until only the most reasonable answer exists, an answer that is supported by all the evidence, not just part of it. This is called interpretation, and it is a weigh of whether or not a preponderance of evidence actually exists. The forensic expert’s job is not to decide whether a preponderance of evidence exists. His job is to fairly, and truthfully, present the facts and his interpretation of the individual facts. Questions an attorney might ask a computer forensics practitioner on the stand:
• Did the user delete the file?
• Could someone else have done it?
• Could an outside process have downloaded the file to the computer?
• Do you know for certain how this happened?
• Did you see Mr. Smith delete the files?
• Isn’t it true, Mr. Expert, that you are being paid to be here today?
These are not “Yes or no” questions. Here might be the answers:
• I’m reasonably certain he did.
• Due to the security of this machine, it’s very unlikely that someone else did it.
• There is evidence to strongly indicate that the photos were loaded to the computer from a digital camera, not the Internet.
• I am certain, without doubt, that the camera in Exhibit 7a is the same camera that was used to take these photos and that these photos were loaded to the computer while username CSMITH was logged in.
• I have viewed forensic evidence that strongly suggests that someone with Mr. Smith’s level of access and permissions to this system did, in fact, delete these files on 12/12/2009.
• I’m not sure I didn’t just answer that.
• I am an employee of The Company. I am receiving my regular compensation and today is a normal workday for me.
Be careful, though. Reticence to answer in a yes-or-no fashion may be interpreted by the jury as uncertainty. If certainty exists, say so. But it is always better to be honest and admit uncertainty than to attempt to inflate one’s own ego by expressing certainty where none exists. Never worry about the outcome of the case. You can’t care about the outcome of the trial. Guilt or innocence cannot be a factor in your opinion. You must focus on simply answering the questions in front of you that demand to be answered.
Certainty without Doubt
Some things on a computer can happen only in one fashion. For example, if a deleted item is found in the recycle bin, there are steps that must be taken to ensure that “it is what it is”:
• Was the user logged in at the time of deletion?
• Are there link files that support the use or viewing of the file?
• Was the user with access to the user account at work that day?
• What are the permissions on the folder?
• Is the deleted file in question a system file or a user-created file located in the user folders?
• Is the systems administrator beyond reproach or outside the family of suspects?
If all of these conditions are met, you may have arrived at certainty without doubt. Short of reliable witnesses paired with physical evidence, it is possible that there will always be other explanations, that uncertainty to some degree can exist. It is the burden of the defense and the plaintiff to understand and resolve these issues and determine if, for example, hacker activity is a plausible defense. I have added the stipulation of reliable witnesses because, in the hands of a morally corrupt forensic expert with access to the drive and a hex editor, a computer can be undetectably altered. Files can be copied onto a hard drive in a sterile manner that, to most trained forensic examiners, could appear to be original. Even advanced users are capable of framing the evidence in such a way as to render the appearance of best evidence, but a forensic examination may lift the veil of uncertainty and show that data has been altered, or that something isn’t quite right. For example, there are certain conditions that can be examined that can show with certainty that the time stamps on a file have been somehow manipulated or are simply incorrect, and it is likely that the average person seeking to plant evidence will not know these tricks (see Table 19.4). The dates on files that were overwritten may show that “old” files overwrote newer files. This is impossible.
Table 19.4
Example of a Forensic View of Files Showing Some Alteration or Masking of Dates

As shown here, the file kitty.jpg overwrites files that appear to have been created on the system after it. Such an event may occur when items are copied from a CD-ROM or unzipped from a zip file.
10. Beginning to End in Court
In most courts in the world, the accuser goes first and then the defense presents its case. This is for the very logical reason that if the defense goes first, nobody would know what they are talking about. The Boulder Bar has a Bar manual located at www.boulder-bar.org4 that provides a more in-depth review of the trial process than can be presented here. Most states and federal rules are quite similar, but nothing here should be taken as legal advice; review the rules for yourself for the courts where you will be testifying. The knowledge isn’t necessary, but the less that you seem to be a fish out of water, the better. This section does not replace true legal advice, it is strictly intended for the purpose of education. The manual located at the Boulder Bar Web site was created for a similar reason that is clearly explained on the site. The manual there was specifically developed without any “legalese,” which makes it very easy to understand.
Defendants, Plaintiffs, and Prosecutors
When someone, an individual or an organization, decides it has a claim of money or damages against another individual or entity, they file a claim in court. The group filing the claim is the plaintiff, the other parties are the defendants. Experts may find themselves working for strictly defendants, strictly plaintiffs, or a little bit of both. In criminal court, charges are “brought” by an indictment, complaint, information, or a summons and complaint.
Pretrial Motions
Prior to the actual trial, there may be many, many pretrial motions and hearings. When a motion is filed, such as when the defense in a criminal case is trying to prevent certain evidence from being seen or heard by the jury, a hearing is called and the judge decides whether the motion has any merit. In civil court, it may be a hearing to decide whether the defense has been deleting, withholding, or committing other acts of discovery abuse. Computer forensic practitioners will find that they may be called to testify at any number of hearings prior to the trial, and then they may not be needed at the trial at all, or the defense and plaintiff may reach a settlement and there will be no trial at all.
Trial: Direct and Cross-Examination
Assuming that there is no settlement or plea agreement, a case will go to trial. The judge will first ask the prosecutor or plaintiff whether they want to make an opening statement. Then the defense will be asked. Witnesses will be called, and if it is the first time appearing in the particular trial as an expert, the witness will be qualified, as discussed in a moment. The party putting on the witness will conduct a direct examination and the other side will very likely cross-examine the witness afterward. Frequently the two sides will have reviewed the expert report and will ask many questions relating directly to it. “Tricks” may be pulled by either attorney at this point. Certain prosecutors have styles and techniques that are used in an attempt to either rattle the expert’s cage or simply intimidate him into a state of nervousness so that he will appear uncertain and unprepared. These prosecutors are not interested in justice. They are interested in winning because their career rotates around their record of wins/losses.
Rebuttal
After a witness has testified and undergone direct examination and cross-examination, the other side may decide to bring in an expert to discuss or refute. The defendant may then respond to the prosecution’s witness in rebuttal. In criminal court, when the state or the government (sometimes affectionately referred to by defense attorneys as “The G”) brings a case against an individual or organization, the attorneys that prosecute the case are called the state’s attorney, district attorney, assistant U.S. attorney (AUSA), or simply prosecutor.
Surrebuttal
This is the plaintiff (or prosecutor’s!) response to rebuttal. Typically the topics of surrebuttal will be limited to those topics that are broached in rebuttal, but the rules for this are probably best left to attorneys to decipher; this author has occasionally been asked questions that should have been deemed outside the bounds of the rebuttal. This could most likely be attributed to a lack of technical knowledge on the part of the attorneys involved in the case.
Testifying: Rule 702. Testimony by Experts
Rule 702 is a federal rule of civil procedure that governs expert testimony. The judge is considered the “gatekeeper,” and she alone makes the decision as to whether or not the following rule is satisfied:
If scientific, technical, or other specialized knowledge will assist the trier of fact to understand the evidence or to determine a fact in issue, a witness qualified as an expert by knowledge, skill, experience, training, or education, may testify thereto in the form of an opinion or otherwise, if (1) the testimony is based upon sufficient facts or data, (2) the testimony is the product of reliable principles and methods, and (3) the witness has applied the principles and methods reliably to the facts of the case (U.S. Courts, Federal Rules of Evidence, Rule 702).
There are certain rules for qualifying as an expert. In court, when an expert is presented, both attorneys may question the expert on matters of background and expertise. This process is referred to as qualification and, if an “expert” does not meet the legal definition of expert, he may not be allowed to testify. This is a short bullet list of items that will be asked in qualifying as an expert witness:
• How long have you worked in the field?
• What certifications do you hold in this field?
• Where did you go to college?
You may also be asked if you have testified in other proceedings. It is important to always be honest when on the stand. Perjury is a very serious crime and can result in jail time. All forensics experts should familiarize themselves with Federal Rules 701–706 as well as understand the purpose, intent, and results of a successful Daubert challenge, wherein an expert’s opinion or the expert himself may be challenged and, if certain criteria are met, may have his testimony thrown out. It is accepted and understood that experts may have reasonably different conclusions given the same evidence.
When testifying, stay calm (easier said than done). If you’ve never done it, approaching the bench and taking the witness stand may seem like a lot of fun. In a case where a lot is on the line and it all depends on the expert’s testimony, nerves will shake and cages will be rattled. The best advice is to stay calm. Drink a lot of water. Drinking copious amounts of water will, according to ex-Navy Seal Mike Lukas, dilute the affect of adrenalin in the bloodstream.
Testifying in a stately and austere court of law may seem like it is the domain of professors and other ivory tower enthusiasts. However, it is something that pretty much anyone can do that has a valuable skill to offer, regardless of educational background. Hollywood often paints a picture of the expert witness as a consummate professorial archetype bent on delivering “just the facts.” It is true that expert witnesses demand top dollar in the consulting world. Much of this is for the reason that a great deal is at stake once the expert takes the stand. There is also a very high inconvenience factor. When on the stand for days at a time, one can’t simply take phone calls, respond to emails, or perform other work for other clients. There is a certain amount of business interruption that the fees must make up for somehow.
Testifying is interesting. Distilling weeks of intense, technical investigation into a few statements that can be understood by everyone in the courtroom is no small task. It is a bit nerve wracking, and one can expect to have high blood pressure and overactive adrenalin glands for the day. Drinking lots of water will ease the nerves better than anything (nonpharmaceutical). It can have other side effects, however, but it is better to be calm and ask the judge for a short recess as needed than to have shaky hands and a trembling voice from nerves. Caffeine is a bad idea.
Correcting Mistakes: Putting Your Head in the Sand
The interplay of examiner and expert in the case of computer forensics can be difficult. Often the forensic examiner can lapse into speech and explanations that are so commonplace to her that she doesn’t realize she is speaking fluent geek-speak. The ability to understand how she sounds to someone who doesn’t understand technology must be cultivated. Practice by explaining to any six-year-old what it is you do.
Direct Testimony
Under direct questioning, your attorney will ask questions to which you will know the answer. A good expert will, in fact, have prepared a list of questions and reviewed the answers with the attorney and explained the context and justification for each question thoroughly. If it is a defense job, you will likely go first and testify as to what your investigation has revealed. Avoid using big words and do make some eye contact with the jury if you feel you need to explain something to them, but generally speaking, you should follow the attorney’s lead. If she wants you to clarify something for the jury, you should do so, and at that time you should look at the jury. Generally, the rule of thumb is to look at the attorney who asked you the question. If the judge says, “Please explain to the jury . . .” then by all means, look at the jury.
Cross-Examination
The purpose of a cross-examination is to get the testifying expert to make a mistake or to discredit him. Sometimes (rarely) it is actually used to further understand and clarify things that were discussed in direct. In most cases, the attorney will do this by asking you questions about your experience or about the testimony the expert gave under direct. But there is another tactic that attorneys use. They ask a question that is completely unrelated to the topic you talked about. They know that the vast majority of time you spend is on the issues in your direct. For example, you may give a testimony about Last Accessed time stamps. Your entire testimony may be about Last Accessed time stamps. It may be the only issue in the case you are aware of. Then, on cross, the attorney asks a question about the behavior of the mail icon that appears on each line next to the subject line in an email. “Great,” the expert thinks. “They recognize my expertise and are asking questions.”
Stop. They are about to ask you an arcane question about a behavior in a piece of software in the hopes that you are overconfident and will answer from the hip and get the answer wrong. Because if you get this wrong, then everything else you said must be wrong, too. Whenever you are asked a question that does not relate to your previous testimony, pause. Pause for a long time. Give your attorney time to object. He might not know that he should object, but the fact is that you might get the answer wrong and even if there is no doubt in your mind that you know the answer, you should respond that you had not prepared to answer that question and would like to know more details. For example, what is the version of the software? What is the operating system? What service pack? If it is Office, what Office service pack? You need to make it clear that you need more information before you answer the question because, frankly, if the opposition goes down this road, they will try to turn whatever you say into the wrong answer.
As a forensic examiner, you may find yourself thinking that the reason they are asking these questions in such a friendly manner is because they forgot to ask their own expert and are trying to take advantage of your time because possibly this came up in a later conversation. This could very well be the case. Maybe the counselor is not trying to trip up the expert. Maybe the Brooklyn Bridge can be purchased for a dollar, too.
What is the best response to a question like this? If you give it a 10 count and your attorney hasn’t objected, and the asking attorney has not abandoned the question, you may have to answer. There are many schools of thought on this. It is best to understand that a number of responses can facilitate an answer to difficult questions. One such response might be, “That is not really a forensics question” (if it’s not), or “I’m not sure how that question relates back to the testimony I just gave.” Or, if it is a software question, you can say, “Different software behaves differently, and I don’t think I can answer that question without more details. I don’t typically memorize the behavior of every piece of software, and I’m afraid that if I answer from memory I may not be certain.” At the end of the day, the expert should only speak to what he knows with certainty. There is very little room for error. Attorneys can back-pedal a certain amount to “fix” a mistake, but a serious mistake can follow you for a very long time and can hamper future testimony. For example, if you make statements about time stamps in one trial, and then in the next trial you make statements that interpret them differently, there is a good chance that the opposition will use this against you.
Fortunately, when computer forensic experts testify in a defense trial, the testimony can last a number of hours. Great care is usually taken by the judge to ensure that understanding of all the evidence is achieved. This can create a very long transcript that is difficult to read, understand, and recall with accuracy. For this reason, rarely will bits and pieces of testimony be used against a testifying expert in a future trial. This is not, of course, to say that it can’t or won’t happen.
It is important, in terms of both setting expectations and understanding legal strategy, for an expert witness to possess passable knowledge of the trial process. Strong familiarity with the trial process can benefit both the expert and the attorneys as well as the judge and the court reporter.
1“Computer forensics and ethics,” Green Home Plate Gallery View, Chicago Bar Association Blog, September 2007.
3M. J. Staggs, FireEye, Network Analysis talk at CEIC 2008.
4Boulder Bar, www.boulder-bar.org/bar_media/index.html.

