Network Forensics
Yong Guan, Iowa State University
Today’s cyber criminal investigator faces a formidable challenge: tracing network-based cyber criminals. The possibility of becoming a victim of cyber crime is the number-one fear of billions of people. This concern is well founded. The findings in the annual CSI/FBI Computer Crime and Security Surveys confirm that cyber crime is real and continues to be a significant threat. Traceback and attribution are performed during or after cyber violations and attacks, to identify where an attack originated, how it propagated, and what computer(s) and person(s) are responsible and should be held accountable. The goal of network forensics capabilities is to determine the path from a victimized network or system through any intermediate systems and communication pathways, back to the point of attack origination or the person who is accountable. In some cases, the computers launching an attack may themselves be compromised hosts or be controlled remotely. Attribution is the process of determining the identity of the source of a cyber attack. Types of attribution can include both digital identity (computer, user account, IP address, or enabling software) and physical identity (the actual person using the computer from which an attack originated).
Cyber crime has become a painful side effect of the innovations of computer and Internet technologies. With the growth of the Internet, cyber attacks and crimes are happening every day and everywhere. It is very important to build the capability to trace and attribute attacks to the real cyber criminals and terrorists, especially in this large-scale human-built networked environment.
In this chapter, we discuss the current network forensic techniques in cyber attack traceback. We focus on the current schemes in IP spoofing traceback and stepping-stone attack attribution. Furthermore, we introduce the traceback issues in Voice over IP, Botmaster, and online fraudsters.
1. Scientific Overview
With the phenomenal growth of the Internet, more and more people enjoy and depend on the convenience of its provided services. The Internet has spread rapidly almost all over the world. Up to December 2006, the Internet had been distributed to over 233 countries and world regions and had more than 1.09 billion users.1 Unfortunately, the wide use of computers and the Internet also opens doors to cyber attackers. There are different kinds of attacks that an end user of a computer or Internet can meet. For instance, there may be various viruses on a hard disk, several backdoors open in an operating system, or a lot of phishing emails in an emailbox. According to the annual Computer Crime Report of the Computer Security Institute (CSI) and the U.S. Federal Bureau of Investigation (FBI), released in 2006, cyber attacks cause massive money losses each year.
However, the FBI/CSI survey results also showed that a low percentage of cyber crime cases have been reported to law enforcement (in 1996, only 16%; in 2006, 25%), which means that in reality, the vast majority of cyber criminals are never caught or prosecuted. Readers may ask why this continues to happen. Several factors contribute to this fact:
• In many cases, businesses are often reluctant to report and publicly discuss cyber crimes related to them. The concern of negative publicity becomes the number-one reason because it may attract other cyber attackers, undermine the confidence of customers, suppliers, and investors, and invite the ridicule of competitors.
• Generally, it is much harder to detect cyber crimes than crimes in the physical world. There are various antiforensics techniques that can help cyber criminals evade detection, such as information-hiding techniques (steganography, covert channels), anonymity proxies, stepping stones, and botnets. Even more challenging, cyber criminals are often insiders or employees of the organizations themselves.
• Attackers may walk across the boundaries of multiple organizations and even countries. To date, the lack of effective solutions has significantly hindered efforts to investigate and stop the rapidly growing cyber criminal activities. It is therefore crucial to develop a forensically sound and efficient solution to track and capture these criminals.
Here we discuss the basic principles and some specific forensic techniques in attributing real cyber criminals.
2. The Principles of Network Forensics
Network forensics can be generally defined as a science of discovering and retrieving evidential information in a networked environment about a crime in such a way as to make it admissible in court. Different from intrusion detection, all the techniques used for the purpose of network forensics should satisfy both legal and technical requirements. For example, it is important to guarantee whether the developed network forensic solutions are practical and fast enough to be used in high-speed networks with heterogeneous network architecture and devices. More important, they need to satisfy general forensics principles such as the rules of evidence and the criteria for admissibility of novel scientific evidence (such as the Daubert criteria).2,3,4 The five rules are that evidence must be:
• Admissible. Must be able to be used in court or elsewhere.
• Authentic. Evidence relates to incident in relevant way.
• Complete. No tunnel vision, exculpatory evidence for alternative suspects.
• Reliable. No question about authenticity and veracity.
• Believable. Clear, easy to understand, and believable by a jury.
The evidence and the investigative network forensics techniques should satisfy the criteria for admissibility of novel scientific evidence (Daubert v. Merrell):
• Whether the theory or technique has been reliably tested
• Whether the theory or technique has been subject to peer review and publication
• What is the known or potential rate of error of the method used?
• Whether the theory or method has been generally accepted by the scientific community
The investigation of a cyber crime often involves cases related to homeland security, corporate espionage, child pornography, traditional crime assisted by computer and network technology, employee monitoring, or medical records, where privacy plays an important role.
There are at least three distinct communities within digital forensics: law enforcement, military, and business and industry, each of which has its own objectives and priorities. For example, prosecution is the primary objective of the law enforcement agencies and their practitioners and is often done after the fact. Military operations’ primary objective is to guarantee the continuity of services, which often have strict real-time requirements. Business and industry’s primary objectives vary significantly, many of which want to guarantee the availability of services and put prosecution as a secondary objective.
Usually there are three types of people who use digital evidence from network forensic investigations: police investigators, public investigators, and private investigators. The following are some examples:
• Criminal prosecutors. Incriminating documents related to homicide, financial fraud, drug-related records.
• Insurance companies. Records of bill, cost, services to prove fraud in medical bills and accidents.
• Law enforcement officials. Require assistance in search warrant preparation and in handling seized computer equipment.
• Individuals. To support a possible claim of wrongful termination, sexual harassment, or age discrimination.
The primary activities of network forensics are investigative in nature. The investigative process encompasses the following:
In the following discussion, we focus on several important network forensic areas.
3. Attack Traceback and Attribution
When we face the cyber attacks, we can detect them and take countermeasures. For instance, an intrusion detection system (IDS) can help detect attacks; we can update operating systems to close potential backdoors; we can install antivirus software to defend against many known viruses. Although in many cases we can detect attacks and mitigate their damage, it is hard to find the real attackers/criminals. However, if we don’t trace back to the attackers, they can always conceal themselves and launch new attacks. If we have the ability to find and punish the attackers, we believe this will help significantly reduce the attacks we face every day.
Why is traceback difficult in computer networks? One reason is that today’s Internet is stateless. There is too much data in the Internet to record it all. For example, a typical router only forwards the passed packets and does not care where they are from; a typical mail transfer agent (MTA) simply relays emails to the next agent and never minds who is the sender. Another reason is that today’s Internet is almost an unauthorized environment. Alice can make a VoIP call to Bob and pretend to be Carol; an attacker can send millions of emails using your email address and your mailbox will be bombed by millions of replies. Two kinds of attacks are widely used by attackers and also interestingto researchers all over the world. One is IP spoofing; the other is the stepping-stone attack. Each IP packet header contains the source IP address. Using IP spoofing, an attacker can change the source IP address in the header to that of a different machine and thus avoid traceback.
In a stepping-stone attack, the attack flow may travel through a chain of stepping stones (intermediate hosts) before it reaches the victim. Therefore, it is difficult for the victim to know where the attack came from except that she can see the attack traffic from the last hop of the stepping-stone chain. Figure 20.1 shows an example of IP stepping-stone attack.
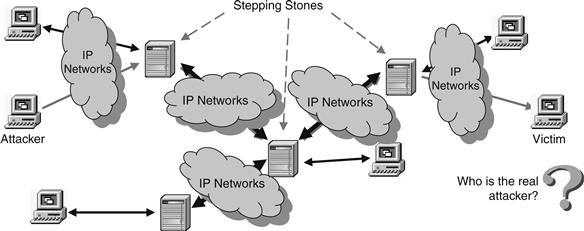
Figure 20.1 Stepping-stone attack attribution.
Next we introduce the existing schemes to trace back IP spoofing attacks, then we discuss current work on stepping-stone attack attribution.
IP Traceback
Here we review major existing IP traceback schemes that have been designed to trace back to the origin of IP packets through the Internet. We roughly categorize them into four primary classes:
Active Probing
Stone19 proposed a traceback scheme called CenterTrack, which selectively reroutes the packets in question directly from edge routers to some special tracking routers. The tracking routers determine the ingress edge router by observing from which tunnel the packet arrives. This approach requires the cooperation of network administrators, and the management overhead is considerably large.
Burch and Cheswick20 outlined a technique for tracing spoofed packets back to their actual source without relying on the cooperation of intervening ISPs. The victim actively changes the traffic in particular links and observes the influence on attack packets, and thus can determine where the attack comes from. This technique cannot work well on distributed attacks and requires that the attacks remain active during the time period of traceback.
ICMP Traceback (iTrace)
Bellovin21 proposed a scheme named iTrace to trace back using ICMP messages for authenticated IP marking. In this scheme, each router samples (with low probability) the forwarding packets, copies the contents into a special ICMP traceback message, adds its own IP address as well as the IP of the previous and next-hop routers, and forwards the packet to either the source or destination address. By combining the information obtained from several of these ICMP messages from different routers, the victim can then reconstruct the path back to the origin of the attacker.
A drawback of this scheme is that it is much more likely that the victim will get ICMP messages from routers nearby than from routers farther away. This implies that most of the network resources spent on generating and utilizing iTrace messages will be wasted. An enhancement of iTrace, called Intention-Driven iTrace, has been proposed.22,23 By introducing an extra “intention-bit,” it is possible for the victim to increase the probability of receiving iTrace messages from remote routers.
Packet Marking
Savage et al.24 proposed a Probabilistic Packet Marking (PPM) scheme. Since then several other PPM-based schemes have been developed.25,26,27 The baseline idea of PPM is that routers probabilistically write partial path information into the packets during forwarding. If the attacks are made up of a sufficiently large number of packets, eventually the victim may get enough information by combining a modest number of marked packets to reconstruct the entire attack path. This allows victims to locate the approximate source of attack traffic without requiring outside assistance.
The Deterministic Packet Marking (DPM) scheme proposed by Belenky and Ansari28 involves marking each individual packet when it enters the network. The packet is marked by the interface closest to the source of the packet on the edge ingress router. The mark remains unchanged as long as the packet traverses the network. However, there is no way to get the whole paths of the attacks.
Dean et al.29 proposed an Algebraic Packet Marking (APM) scheme that reframes the traceback problem as a polynomial reconstruction problem and uses techniques from algebraic coding theory to provide robust methods of transmission and reconstruction. The advantage of this scheme is that it offers more flexibility in design and more powerful techniques that can be used to filter out attacker-generated noise and separate multiple paths. But it shares similarity with PPM in that it requires a sufficiently large number of attack packets.
Log-Based Traceback
The basic idea of log-based traceback is that each router stores the information (digests, signature, or even the packet itself) of network traffic through it. Once an attack is detected, the victim queries the upstream routers by checking whether they have logged the attack packet in question. If the attack packet’s information is found in a given router’s memory, that router is deemed to be part of the attack path. Obviously, the major challenge in log-based traceback schemes is the storage space requirement at the intermediate routers.
Matsuda et al.30 proposed a hop-by-hop log-based IP traceback method. Its main features are a logging packet feature that is composed of a portion of the packet for identification purposes and an algorithm using a data-link identifier to identify the routing of a packet. However, for each received packet, about 60 bytes of data should be recorded. The resulting large memory space requirement prevents this method from being applied to high-speed networks with heavy traffic.
Although today’s high-speed IP networks suggest that classical log-based traceback schemes would be too prohibitive because of the huge memory requirement, log-based traceback became attractive after Bloom filter-based (i.e., hash-based) traceback schemes were proposed. Bloom filters were presented by Burton H. Bloom31 in 1970 and have been widely used in many areas such as database and networking.32 A Bloom filter is a space-efficient data structure for representing a set of elements to respond to membership queries. It is a vector of bits that are all initialized to the value 0. Then each element is inserted into the Bloom filter by hashing it using several independent uniform hash functions and setting the corresponding bits in the vector to value 1. Given a query as to whether an element is present in the Bloom filter, we hash this element using the same hash functions and check whether all the corresponding bits are set to 1. If any one of them is 0, then undoubtedly this element is not stored in the filter. Otherwise, we would say that it is present in the filter, although there is a certain probability that the element is determined to be in the filter though it is actually not. Such false cases are called false positives.
The space-efficiency of Bloom filters is achieved at the cost of a small, acceptable false-positive rate. Bloom filters were introduced into the IP traceback area by Snoeren et al.33 They built a system named the Source Path Isolation Engine (SPIE), which can trace the origin of a single IP packet delivered by the network in the recent past. They demonstrated that the system is effective, space-efficient, and implementable in current or next-generation routing hardware. Bloom filters are used in each SPIE-equipped router to record the digests of all packets received in the recent past. The digest of a packet is exactly several hash values of its nonmutable IP header fields and the prefix of the payload. Strayer et al.34 extended this traceback architecture to IP-v6. However, the inherent false positives of Bloom filters caused by unavoidable collisions restrain the effectiveness of these systems. To reduce the impact of unavoidable collisions in Bloom filters, Zhang and Guan35 propose a topology-aware single-packet IP traceback system, namely TOPO. The router’s local topology information, that is, its immediate predecessor information, is utilized. The performance analysis shows that TOPO can reduce the number and scope of unnecessary queries and significantly decrease false attributions. When Bloom filters are used, it is difficult to decide their optimal control parameters a priori. They designed a k-adaptive mechanism that can dynamically adjust the parameters of Bloom filters to reduce the false-positive rate.
Shanmugasundaram et al.36 proposed a payload attribution system (PAS) based on a hierarchical Bloom filter (HBF). HBF is a Bloom filter in which an element is inserted several times using different parts of the same element. Compared with SPIE, which is a packet-digesting scheme, PAS only uses the payload excerpt of a packet. It is useful when the packet header is unavailable.
Li et al.37 proposed a Bloom filter-based IP traceback scheme that requires an order of magnitude smaller processing and storage cost than SPIE, thereby being able to scale to much higher link speed. The baseline idea of their approach is to sample and log a small percentage of packets, and 1 bit packet marking is used in their sampling scheme. Therefore, their traceback scheme combines packet marking and packet logging together. Their simulation results showed that the traceback scheme can achieve high accuracy and scale well to a large number of attackers. However, as the authors also pointed out, because of the low sampling rate, their scheme is no longer capable of tracing one attacker with only one packet.
Stepping-Stone Attack Attribution
Ever since the problem of detecting stepping stones was first proposed by Staniford-Chen and Heberlein,38 several approaches have been proposed to detect encrypted stepping-stone attacks.
The ON/OFF based approach proposed by Zhang and Paxson39 is the first timing-based method that can trace stepping stones, even if the traffic were to be encrypted. In their approach, they calculated the correlation of different flows by using each flow’s OFF periods. A flow is considered to be in an OFF period when there is no data traffic on it for more than a time period threshold. Their approach comes from the observation that two flows are in the same connection chain if their OFF periods coincide.
Yoda and Etoh40 presented a deviation-based approach for detecting stepping-stone connections. The deviation is defined as the difference between the average propagation delay and the minimum propagation delay of two connections. This scheme comes from the observation that the deviation for two unrelated connections is large enough to be distinguished from the deviation of connections in the same connection chain.
Wang et al.41 proposed a correlation scheme using interpacket delay (IPD) characteristics to detect stepping stones. They defined their correlation metric over the IPDs in a sliding window of packets of the connections to be correlated. They showed that the IPD characteristics may be preserved across many stepping stones.
Wang and Reeves42 presented an active watermark scheme that is designed to be robust against certain delay perturbations. The watermark is introduced into a connection by slightly adjusting the interpacket delays of selected packets in the flow. If the delay perturbation is not quite large, the watermark information will remain along the connection chain. This is the only active stepping-stone attribution approach.
Strayer et al.43 presented a State-Space algorithm that is derived from their work on wireless topology discovery. When a new packet is received, each node is given a weight that decreases as the elapsed time from the last packet from that node increases. Then the connections on the same connection chain will have higher weights than other connections.
However, none of these previous approaches can effectively detect stepping stones when delay and chaff perturbations exist simultaneously. Although no experimental data is available, Donoho et al.44 indicated that there are theoretical limits on the ability of attackers to disguise their traffic using evasions for sufficiently long connections. They assumed that the intruder has a maximum delay tolerance, and they used wavelets and similar multiscale methods to separate the short-term behavior of the flows (delay or chaff) from the long-term behavior of the flows (the remaining correlation). However, this method requires the intrusion connections to remain for long periods, and the authors never experimented to show the effectiveness against chaff perturbation. These evasions consist of local jittering of packet arrival times and the addition of superfluous packets.
Blum et al.45 proposed and analyzed algorithms for stepping-stone detection using ideas from computational learning theory and the analysis of random walks. They achieved provable (polynomial) upper bounds on the number of packets needed to confidently detect and identify stepping-stone flows with proven guarantees on the false positives and provided lower bounds on the amount of chaff that an attacker would have to send to evade detection. However, their upper bounds on the number of packets required is large, while the lower bounds on the amount of chaff needed for attackers to evade detection is very small. They did not discuss how to detect stepping stones without enough packets or with large amounts of chaff and did not show experimental results.
Zhang et al.46 proposed and analyzed algorithms that represent that attackers cannot always evade detection only by adding limited delay and independent chaff perturbations. They provided the upper bounds on the number of packets needed to confidently detect stepping-stone connections from nonstepping stone connections with any given probability of false attribution.
Although there have been many stepping-stone attack attribution schemes, there is a lack of comprehensive experimental evaluation of these schemes. Therefore, there are no objective, comparable evaluation results on the effectiveness and limitations of these schemes. Xin et al.47 designed and built a scalable testbed environment that can evaluate all existing stepping-stone attack attribution schemes reproducibly, provide a stable platform for further research in this area, and be easily reconfigured, expanded, and operated with a user-friendly interface. This testbed environment has been established in a dedicated stepping-stone attack attribution research laboratory. An evaluation of proposed stepping-stone techniques is currently under way.
A group from Iowa State University proposed the first effective detection scheme to detect attack flows with both delay and chaff perturbations. A scheme named “datatick” is proposed that can handle significant packet merging/splitting and can attribute multiple application layer protocols (e.g., X-Windows over SSH, Windows Remote Desktop, VNC, and SSH). A scalable testbed environment is also established that can evaluate all existing stepping-stone attack attribution schemes reproducibly. A group of researchers from North Carolina State University and George Mason University utilizes timing-based watermarking to trace back stepping-stone attacks. They have proposed schemes to handle repacketization of the attack flow and a “centroid-based” watermarking scheme to detect attack flows with chaff. A group from Johns Hopkins University demonstrates the feasibility of a “post-mortem” technique for traceback through indirect attacks. A group from Telcordia Technologies proposed a scheme that reroutes the attack traffic from uncooperative networks to cooperative networks such that the attacks can be attributed. The BBN Technologies’ group integrates single-packet traceback and stepping-stone correlation. A distributed traceback system called FlyTrap is developed for uncooperative and hostile networks. A group from Sparta integrates multiple complementary traceback approaches and tests them in a TOR anonymous system.
A research project entitled Tracing VoIP Calls through the Internet, led by Xinyuan Wang from George Mason University, aims to investigate how VoIP calls can be effectively traced. Wang et al. proposed to use the watermarking technology in stepping-stone attack attribution into VoIP attribution and showed that VoIP calls can still be attributed.48
Strayer et al. has been supported by the U.S. Army Research Office to research how to attribute attackers using botnets. Their approach for detecting botnets is to examine flow characteristics such as bandwidth, duration, and packet timing, looking for evidence of botnet command and control activity.49
4. Critical Needs Analysis
Although large-scale cyber terrorism seldom happens, some cyber attacks have already shown their power in damaging homeland security. For instance, on October 21, 2002, all 13 Domain Name System (DNS) root name servers sustained a DoS attack.50 Some root name servers were unreachable from many parts of the global Internet due to congestion from the attack traffic. Even now, we do not know the real attacker and what his intention was.
Besides the Internet itself, many sensitive institutions, such as the U.S. power grid, nuclear power plants, and airports, may also be attacked by terrorists if they are connected to the Internet, although these sites have been carefully protected physically. If the terrorists want to launch large-scale attacks targeting these sensitive institutions through the Internet, they will probably have to try several times to be successful. If we only sit here and do not fight back, they will finally find our vulnerabilities and reach their evil purpose. However, if we can attribute them to the source of attacks, we can detect and arrest them before they succeed.
Although there have been a lot of traceback and attribution schemes on IP spoofing and stepping-stone attacks, we still have a lot of open issues in this area. The biggest issue is the deployment of these schemes. Many schemes (such as packet marking and log-based traceback) need the change of Internet protocol on each intermediate router. Many schemes need many network monitors placed all over the world. These are very difficult to implement in the current Internet without support from government, manufacturers, and academics. It is necessary to consider traceback demands when designing and deploying next-generation networks.
5. Research Directions
There are still some open problems in attack traceback and attribution.
VoIP Attribution
Like the Internet, the Voice over Internet Protocol (VoIP) also provides unauthorized services. Therefore, some security issues existing in the Internet may also appear in VoIP systems. For instance, a phone user may receive a call with a qualified caller ID from her credit-card company, so she answers the critical questions about Social Security number, data of birth, and so on. However, this call actually comes from an attacker who fakes the caller ID using a computer. Compared with a Public Switched Telephone Network (PSTN) phone or mobile phone, IP phones lack monitoring. Therefore, it is desirable to provide schemes that can attribute or trace back to the VoIP callers.
Tracking Botnets
A botnet is a network of compromised computers, or bots, commandeered by an adversarial botmaster. Botnets usually spread through viruses and communicate through the IRC channel. With an army of bots, bot controllers can launch many attacks, such as spam, phishing, key logging, and denial of service. Today more and more scientists are interested in how to detect, mitigate, and trace back botnet attacks.
Traceback in Anonymous Systems
Another issue is that there exist a lot of anonymous systems available all over the world, such as Tor.51 Tor is a toolset for anonymizing Web browsing and publishing, instant messaging, IRC, SSH, and other applications that use TCP. It provides anonymity and privacy for legal users, and at the same time, it is a good platform via which to launch stepping-stone attacks. Communications over Tor are relayed through several distributed servers called onion routers. So far there are more than 800 onion routers all over the world. Since Tor may be seen as a special stepping-stone attack platform, it is interesting to consider how to trace back attacks over Tor.
Online Fraudster Detection and Attribution
One example is the auction frauds on eBay-like auction systems. In the past few years, Internet auctions have become a thriving and very important online business. Compared with traditional auctions, Internet auctions virtually allow everyone to sell and buy anything at anytime from anywhere, at low transaction fees. However, the increasing number of cases of fraud in Internet auctions has harmed this billion-dollar worldwide market. Due to the inherent limitation of information asymmetry in Internet auction systems, it is very hard, if not impossible, to discover all potential (i.e., committed and soon to be committed) frauds. Auction frauds are reported as ascending in recent years and have become serious problems. The Internet Crime Complaint Center (IC3) and Internet FraudWatch have both reported Internet auction frauds as the most prevalent type of Internet fraud.52,53 Internet FraudWatch reported that auction fraud represented 34% (the highest percentage) of total Internet frauds in 2006, resulting in an average loss of $1331. Internet auction houses had tried to prevent frauds by using certain types of reputation systems, but it has been shown that fraudulent users are able to manipulate these reputation systems. It is important that we develop the capability to detect and attribute auction fraudsters.
Tracing Phishers
Another serious problem is the fraud and identity theft that result from phishing, pharming, and email spoofing of all types. Online users are lured to a faked web site and tricked to disclose sensitive credentials such as passwords, Social Security numbers, and credit-card numbers. The phishers collect these credentials in order to illegitimately gain access to the user’s account and cause financial loss or other damages to the user. In the past, phishing attacks often involve various actors as a part of a secret criminal network and take approaches similar to those of money laundering and drug trafficking. Tracing phishers is a challenging forensic problem and the solutions thereof would greatly help law enforcement practitioners and financial fraud auditors in their investigation and deterrence efforts.
Tracing Illegal Content Distributor in P2P Systems
Peer-to-peer (P2P) file sharing has gained popularity and achieved a great success in the past 10 years. Though the well-known and popular P2P file sharing applications such as BitTorrent (BT), eDonkey, and Foxy may vary from region to region, the trend of using P2P networks can be seen almost everywhere. In North America, a recent report stated that around 41%–44% of all bandwidth was used up by P2P file transfer traffic. With the increasing amount of sensitive documents and files accidentally shared through P2P systems, it is important to develop forensic solutions for locating initial illegal content uploaders in P2P systems. However, one technique would not be applicable to all P2P systems due to their architectural and algorithmic differences among different P2P systems. There are many legal and technical challenges for tracing illegal content distributors in P2P systems.
1Internet World Stats, www.internetworldstats.com.
2G. Palmer, “A road map for digital forensic research,” Digital Forensic Research Workshop (DFRWS), Final Report, Aug. 2001.
3C. M. Whitcomb, “An historical perspective of digital evidence: A forensic scientist’s view,” IJDE, 2002.
4S. Mocas, “Building theoretical underpinnings for digital forensics research,” Digital Investigation, Vol. 1, pp. 61–68, 2004.
5H. Burch and B. Cheswick, “Tracing anonymous packets to their approximate source,” in Proceedings of USENIX LISA 2000, Dec. 2000, pp. 319–327.
6R. Stone, “Centertrack: An IP overlay network for tracking DoS floods,” in Proceedings of the 9th USENIX Security Symposium, Aug. 2000, pp. 199–212.
7S. M. Bellovin, “ICMP traceback messages,” Internet draft, 2000.
8A. Mankin, D. Massey, C.-L. Wu, S. F. Wu, and L. Zhang, “On design and evaluation of ‘Intention-Driven’ ICMP traceback,” in Proceedings of 10th IEEE International Conference on Computer Communications and Networks, Oct. 2001.
9S. F. Wu, L. Zhang, D. Massey, and A. Mankin, “Intention-driven ICMP trace-back,” Internet draft, 2001.
10A. Belenky and N. Ansari, “IP traceback with deterministic packet marking,” IEEE Communications Letters, Vol. 7, No. 4, pp. 162–164, April 2003.
11D. Dean, M. Franklin, and A. Stubblefield, “An algebraic approach to IP traceback,” Information and System Security, Vol. 5, No. 2, pp. 119–137, 2002.
12K. Park and H. Lee, “On the effectiveness of probabilistic packet marking for IP traceback under denial of service attack,” in Proceedings of IEEE INFOCOM 2001, Apr. 2001, pp. 338–347.
13S. Savage, D. Wetherall, A. Karlin, and T. Anderson, “Network support for IP traceback,” IEEE/ACM Transactions on Networking, Vol. 9, No. 3, pp. 226–237, June 2001.
14D. Song and A. Perrig, “Advanced and authenticated marking schemes for IP traceback,” in Proceedings of IEEE INFOCOM 2001, Apr. 2001.
15J. Li, M. Sung, J. Xu, and L. Li, “Large-scale IP traceback in high-speed Internet: Practical techniques and theoretical foundation,” in Proceedings of 2004 IEEE Symposium on Security and Privacy, May 2004.
16S. Matsuda, T. Baba, A. Hayakawa, and T. Nakamura, “Design and implementation of unauthorized access tracing system,” in Proceedings of the 2002 Symposium on Applications and the Internet (SAINT 2002), Jan. 2002.
17K. Shanmugasundaram, H. Brönnimann, and N. Memon, “Payload attribution via hierarchical Bloom filters,” in Proceedings of the 11th ACM Conference on Computer and Communications Security, Oct. 2004.
18A.C. Snoeren, C. Partridge, L. A. Sanchez, C. E. Jones, F. Tchakountio, B. Schwartz, S. T. Kent, and W. T. Strayer, “Single-packet IP traceback,” IEEE/ACM Transactions on Networking, Vol. 10, No. 6, pp. 721–734, Dec. 2002.
19R. Stone, “Centertrack: An IP overlay network for tracking DoS floods,” in Proceedings of the 9th USENIX Security Symposium, Aug. 2000, pp. 199–212.
20H. Burch and B. Cheswick, “Tracing anonymous packets to their approximate source,” in Proceedings of USENIX LISA 2000, Dec. 2000, pp. 319–327.
21S. M. Bellovin, “ICMP traceback messages,” Internet draft, 2000.
22A. Mankin, D. Massey, C.-L. Wu, S. F. Wu, and L. Zhang, “On design and evaluation of ‘Intention-Driven’ ICMP traceback,” in Proceedings of 10th IEEE International Conference on Computer Communications and Networks, Oct. 2001.
23S. F. Wu, L. Zhang, D. Massey, and A. Mankin, “Intention-driven ICMP trace back,” Internet draft, 2001.
24S. Savage, D. Wetherall, A. Karlin, and T. Anderson, “Network support for IP traceback,” IEEE/ACM Transactions on Networking, Vol. 9, No. 3, pp. 226–237, June 2001.
25D. Song and A. Perrig, “Advanced and authenticated marking schemes for IP traceback,” in Proceedings of IEEE INFOCOM 2001, Apr. 2001.
26K. Park and H. Lee, “On the effectiveness of probabilistic packet marking for IP traceback under denial of service attack,” in Proceedings of IEEE INFOCOM 2001, Apr. 2001, pp. 338–347.
27D. Dean, M. Franklin, and A. Stubblefield, “An algebraic approach to IP traceback,” Information and System Security, Vol. 5, No. 2, pp. 119–137, 2002.
28A. Belenky and N. Ansari, “IP traceback with deterministic packet marking,” IEEE Communications Letters, Vol. 7, No. 4, pp. 162–164, April 2003.
29D. Dean, M. Franklin, and A. Stubblefield, “An algebraic approach to IP traceback,” Information and System Security, Vol. 5, No. 2, pp. 119–137, 2002.
30S. Matsuda, T. Baba, A. Hayakawa, and T. Nakamura, “Design and implementation of unauthorized access tracing system,” in Proceedings of the 2002 Symposium on Applications and the Internet (SAINT 2002), Jan. 2002.
31B. H. Bloom, “Space/time trade-offs in hash coding with allowable errors,” Communications of the ACM, Vol. 13, No. 7, pp. 422–426, July 1970.
32A. Broder and M. Mitzenmacher, “Network applications of Bloom filters: A survey,” Proceedings of the 40th Annual Allerton Conference on Communication, Control, and Computing, Oct. 2002, pp. 636–646.
33A.C. Snoeren, C. Partridge, L. A. Sanchez, C. E. Jones, F. Tchakountio, B. Schwartz, S. T. Kent, and W. T. Strayer, “Single-packet IP traceback,” IEEE/ACM Transactions on Networking, Vol. 10, No. 6, pp. 721–734, Dec. 2002.
34W.T. Strayer, C. E. Jones, F. Tchakountio, and R. R. Hain, “SPIE-IPv6: Single IPv6 packet traceback,” in Proceedings of the 29th IEEE Local Computer Networks Conference (LCN 2004), Nov. 2004.
35L. Zhang and Y. Guan, “TOPO: A topology-aware single packet attack traceback scheme,” in Proceedings of the 2nd IEEE Communications Society/CreateNet International Conference on Security and Privacy in Communication Networks (SecureComm 2006), Aug. 2006.
36S. Savage, D. Wetherall, A. Karlin, and T. Anderson, “Network support for IP traceback,” IEEE/ACM Transactions on Networking, Vol. 9, No. 3, pp. 226–237, June 2001.
37J. Li, M. Sung, J. Xu, and L. Li, “Large-scale IP traceback in high-speed Internet: Practical techniques and theoretical foundation,” in Proceedings of 2004 IEEE Symposium on Security and Privacy, May 2004.
38S. Staniford-Chen and L. T. Heberlein, “Holding intruders accountable on the Internet,” in Proceedings of the 1995 IEEE Symposium on Security and Privacy, May 1995.
39Y. Zhang and V. Paxson, “Detecting stepping stones,” in Proceedings of the 9th USENIX Security Symposium, Aug. 2000, pp. 171¨C184.
40K. Yoda and H. Etoh, “Finding a connection chain for tracing intruders,” in Proceedings of the 6th European Symposium on Research in Computer Security (ESORICS 2000), Oct. 2000.
41X. Wang, D. S. Reeves, and S. F. Wu, “Inter-packet delay based correlation for tracing encrypted connections through stepping stones,” in Proceedings of the 7th European Symposium on Research in Computer Security (ESORICS 2002), Oct. 2002.
42X. Wang and D. S. Reeves, “Robust correlation of encrypted attack traffic through stepping stones by manipulation of interpacket delays,” in Proceedings of the 10th ACM Conference on Computer and Communications Security (CCS 2003), Oct. 2003.
43W. T. Strayer, C. E. Jones, I. Castineyra, J. B. Levin, and R. R. Hain, “An integrated architecture for attack attribution,” BBN Technologies, Tech. Rep. BBN REPORT-8384, Dec. 2003.
44D. L. Donoho, A. G. Flesia, U. Shankar, V. Paxson, J. Coit, and S. Staniford, “Multiscale stepping-stone detection: Detecting pairs of jittered interactive streams by exploiting maximum tolerable delay,” in Proceedings of the 5th International Symposium on Recent Advances in Intrusion Detection (RAID 2002), Oct. 2002.
45A. Blum, D. Song, and S. Venkataraman, “Detection of interactive stepping stones: Algorithms and confidence bounds,” in Proceedings of the 7th International Symposium on Recent Advances in Intrusion Detection (RAID 2004), Sept. 2004.
46L. Zhang, A. G. Persaud, A. Johnson, and Y. Guan, “Detection of Stepping Stone Attack under Delay and Chaff Perturbations,” in 25th IEEE International Performance Computing and Communications Conference (IPCCC 2006), Apr. 2006.
47J. Xin, L. Zhang, B. Aswegan, J. Dickerson, J. Dickerson, T. Daniels, and Y. Guan, “A testbed for evaluation and analysis of stepping stone attack attribution techniques,” in Proceedings of TridentCom 2006, Mar. 2006.
48X. Wang, S. Chen, and S. Jajodia “Tracking anonymous peer-to-peer VoIP calls on the Internet,” In Proceedings of the 12th ACM Conference on Computer Communications Security (CCS 2005), November 2005.
49W.T. Strayer, R. Walsh, C. Livadas, and D. Lapsley, “Detecting botnets with tight command and control,” Proceedings of the 31st IEEE Conference on Local Computer Networks (LCN), November 15–16, 2006.
50P. Vixie, G. Sneeringer, and M. Schleifer, “Events of Oct. 21, 2002”, November 24, 2002, www.isc.org/ops/f-root/october21.txt.
51Tor system, http://tor.eff.org.
52Internet Crime Complaint Center, Internet crime report, 2006 ic3 annual report, 2006.
53Internet National Fraud Information Center, 2006 top 10 Internet scam trends from NCL’s fraud center, 2006.
