In today’s Information Technology (IT) landscape, administrators must concern themselves with the following key issues:
Achieving maximum availability and optimum performance from those systems they are responsible for monitoring
Ensuring the organization complies with internal procedures and external regulations that facilitate auditing network security
The successful administrator not only keeps systems running, but also proves to regulators and business stakeholders that there is an appropriate and effective audit capability for those systems.
Many organizations today rely extensively or completely on Windows networking functions to get their business done, and a credible security auditing solution must focus on monitoring the Windows security infrastructure. To investigate potential security breaches, the auditing solution (the audit trail) must be able to provide sufficient information to establish what events occurred, when they occurred, and who (or what) caused them.
Microsoft has included the Windows NT Security Event log mechanism with Windows since the first versions of the operating system. Depending on the security audit policies enabled on the computer, the Security Event log can record a full spectrum of security-related events. Information captured can range from no security auditing to full auditing of every file and object access event that happens on the computer. Deciding what to audit is among the most critical decisions to be made, because while capturing “everything” sounds great, it is rarely practical, desirable, or even possible to audit everything for everyone, all the time.
Audit events are stored on each computer in a local Security log, making analysis of each individual log extremely time-consuming. There are various Event log consolidation tools, but the huge volume of security events collected when auditing is enabled will overwhelm most operators and systems. In addition, simple Event log collection tools may not offer powerful search technologies to comb through the inevitable millions of security events for constructing that all-important audit trail. Given the clear business requirement to capture this information, many organizations have dedicated considerable effort to implementing their own tools for collecting, consolidating, and retaining audit-related data.
With Operations Manager (OpsMgr) 2007, Microsoft introduces Audit Collection Services (ACS) as an optional but integrated component of an OpsMgr management group. By deploying and using the ACS components of Operations Manager, the administrator fulfills a small but crucial part of an overall security compliance challenge for his organization. ACS overcomes the difficulties administrators have encountered in managing security and audit data by gathering, storing, and presenting security audit information. If you have invested in System Center Operations Manager 2007 for managing your network, additionally implementing ACS for security auditing is the logical choice.
Tip: Good Read: Regulatory Compliance Demystified
We found a very readable summary of Sarbanes-Oxley, HIPAA, and other security regulations at Microsoft—the link is http://msdn2.microsoft.com/en-us/library/aa480484. This document, written for the developer, takes a very practical approach to meeting the technical requirements of the various compliance requirements in a half-dozen industries.
This chapter walks though the primary activities that need to occur so you can take advantage of the new ACS features in OpsMgr 2007. To deploy ACS, we recommend following this sequence of procedures:
Plan an audit policy for your organization.
Plan your ACS component deployment. This includes making decisions about which management server(s) will be ACS collectors, provisioning each collector with a SQL Server database server, and identifying which managed computers will be ACS forwarders. Figure 15.1 illustrates the basic components of any ACS deployment.
An ACS collector is a management server that receives and processes data from ACS forwarders and then sends this data to the ACS database.
An ACS forwarder is a computer running the Audit Forwarder service and collecting security audit events. The service on ACS forwarders is included in the Operations Manager agent; it is installed but not enabled when the OpsMgr agent is installed.
After this service is enabled, all security events are sent to the ACS collector in addition to the local Windows NT Security log.
Install and configure your ACS database(s) and collector(s).
Install the ACS reports into the management group.
Run the Enable Audit Collection task to start the ACS Forwarder service on computers selected to be forwarders (OpsMgr agents that participate in ACS).
Implement your audit policy. There are ongoing organizational (people) and technical components to administer.
The bottom-line measure of success for an ACS deployment is that you satisfy regulatory requirements for security audit record keeping without degrading the organizational efficiency of the network. In the following sections, we’ll look at each of the primary activities involved in implementing ACS.
To get audit data into the ACS database, you must enable auditing at the Windows operating system level on each ACS forwarder. You enable auditing through security policies. Security policy in Windows is found in three locations:
Local Security Policy, accessed via Start-> Administrative Tools -> Local Security Policy.
Local Security Policy only exists on client computers and member servers; domain controllers do not have a Local Security Policy. Settings in the Local Security Policy are effective on the local computer unless they are overridden by Domain Security Policy.
Domain Security Policy, accessed via Start -> Administrative Tools -> Domain Security Policy on domain controllers, or using the Group Policy Management Console (GPMC).
Settings in the Domain Security Policy are effective on all non-domain controller computers in the domain and override the settings in the Local Security Policy of domain members. Domain Security Policy has no effect on domain controllers. You can override the Domain Security Policy on non-domain controllers using custom Group Policy Objects (GPOs); however, it is a best practice to use a standard security policy across your domain.
Domain Controller Security Policy, accessed via Start -> Administrative Tools -> Domain Controller Security Policy on domain controllers, or using the Group Policy Management Console (GPMC).
Settings in the Domain Controller Security Policy are effective on all domain controller computers in the domain. This is the only security policy that has any effect on domain controllers.
Whereas the settings available in the Domain and the Domain Controller Security Policies are identical to each other, the settings available in the Local Security Policy are a subset of those available in the domain policies. Table 15.1 summarizes these security-critical settings and indicates which are available as domain versus local policies. (The items in bold are at the same hierarchy level in the Security Settings for the local, domain, or domain controller policy.)
Table 15.1. Windows Server 2003 Security Policies
Setting | Description | Location |
|---|---|---|
Account Policies Password Policy | Password requirements (length, complexity, maximum age, history). | Local and domain |
Account Lockout Policy | Lockout parameters (number of permitted logon attempts, duration of lockout). | Local and domain |
Kerberos Policy | Kerberos key policies (how long the keys are valid). | Domain only |
Local Policies Audit Policy | Defines the events logged (for example, failed/successful logon attempts, access to specific resources, and so on). These are the key ACS settings; logged events are forwarded to the ACS collector. Table 15.2 provides the details. | Local and domain |
Event Log | Retention periods and parameters for event logging. This is not a security policy but is involved in ACS functionality; the Security Event log must not be too small. | Domain only |
Public Key Policies Encrypting File System (EFS) | Allows you to define whether to use the Encrypting File System (EFS) to encrypt files and folders on NTFS partitions. | Local and domain |
IP Security Policies | Configures the use of Internet Protocol Security (IPSec) to encrypt data in transit over the network. | Local and domain |
Any ACS forwarder not a member of a Windows domain must use Local Security Policy to enable auditing. Local Security Policy can be set manually at each computer using the Local Security Policy tool (Start -> Programs -> Administrative Tools -> Local Security Policy). Windows includes some built-in security templates (in particular SecureWS.inf) that you can import manually into the Local Security Policy on multiple computers.
You can import a built-in template using the Local Security Policy tool by right-clicking the Security Settings root and selecting Import Policy. The tool looks in the default location where security templates are stored, which is %windir%SecurityTemplates.
Generally, an ACS forwarder belongs to a Windows domain, making administration much simpler because we can concern ourselves only with the security settings in two locations in each domain—the Domain and the Domain Controller Security Policies (assuming you have not created GPOs to override the domain security settings on non-domain controllers). There is a double-edged sword effect however; the ease of configuring domain-based policies brings with it the ability to wreak havoc on the entire domain if there are incorrect policy settings.
Between the Domain and the Domain Controller Security Policy settings, every computer in the domain is equally and immediately impacted when it loads the security policy. If you inadvertently enable overly aggressive auditing, it can literally stop the network from functioning—due to the overhead of performing audit-related functions.
In a domain environment, you have the capability to enable auditing to a certain extent on some computers and in a different manner on others. Whereas all domain controllers will always implement the full Domain Controller Security Policy, non-domain controllers (workstations and member servers) can have one or more custom GPOs applied that override specific settings of the Domain Security Policy. In special circumstances, you can consider deploying custom security settings to subsets of non-domain controller computers; however, we recommend this be done very sparingly, if at all. The reasoning is the same as that behind the best practice of avoiding use of the Enforced and Block Inheritance settings on GPOs. The complexities of GPO inheritance can cause unintended results; in the security arena, standardization, consistency, and simplicity are of paramount importance.
You can choose which computers will be ACS forwarders, and the AdtAdmin.exe application on the ACS Collector Component has the ability to discard certain categories of security events without writing them to the ACS database (we cover how to do this later in the “Using AdtAdmin.exe” section of this chapter). However, every computer in the domain will begin auditing in accordance with the domain security policies regardless of whether that system participates in ACS or not.
Tip: Verifying with the Group Policy Management Console
The Group Policy Management Console (GPMC) is quite useful to include as a management tool for ACS. Using GMPC, you can quickly edit and verify all GPOs in the organization. Significantly, GMPC includes the Group Policy Modeling Wizard, which lets you sight-verify what GPOs a specific computer is going to apply. This step verifies that the GPOs are correctly configured to enforce your security policies.
Now we will closely examine the nine categories of auditing available in the Local Policy -> Audit Policy section of all three types of security polices (local, domain, and domain controller). Table 15.2 lists each category, a description of its effect, the audit settings (success or failure) in a default Windows installation, as well as the settings contained in the SecureDC.inf and SecureWS.inf security templates.
If your organization does not have more specific security needs (or if you just need a validated starting point to decide which auditing categories to enable and with what settings), we recommend importing the following templates:
The SecureDC.inf security template to the Default Domain Controller Policy. Modify the Default Domain Controller Policy to enable success auditing for system events after importing the SecureDC.inf template.
The SecureWS.inf security template to the Default Domain Security Policy.
The selection of category and audit settings shown in Table 15.2 is effective for collecting useful security audit data for most organizations.
Table 15.2. Window Server 2003 Audit Policies
Category | Description | Default Setting | “Secure” Templates |
|---|---|---|---|
Account Logon Events | Audits each instance of a user logging on to or logging off from another computer in which this computer validates the account. | DC: Success Non-DC: None | Success, Failure |
Account Management | Account management events including whether a user account or group is created, changed, or deleted; a user account is renamed, disabled, or enabled; and a password is set or changed. | DC: Success Non-DC: None | Success, Failure |
Directory Service Access | Audits the event of a user accessing an Active Directory object that has its own system access control list (SACL) specified. | DC: Success Non-DC: N/A | Failure |
Logon Events | Audits each instance of a user logging on to or logging off from a computer. | DC: Success Non-DC: None | Success, Failure |
Object Access | Audits the event of a user accessing an object—for example, a file, folder, Registry key, printer, and so forth—that has its own system access control list (SACL) specified. | None | None |
Policy Change | Audits every incident of a change to user rights assignment policies, audit policies, or trust policies. | DC: Success Non-DC: None | Success, Failure |
Privilege Use | Audits each instance of a user exercising a user right, with the exception of Bypass traverse checking, Debug programs, Create a token object, Replace process level token, Generate security audits, and Back up or restore files and directories. | None | Failure |
Process Tracking | Audits detailed tracking information for events such as program activation, process exit, handle duplication, and indirect object access | None | None |
System Events | Audits when a user restarts or shuts down the computer or when an event occurs that affects either the system security or the security log, such as clearing the security log. | DC: Success Non-DC: None | None (Should be enabled for DCs) |
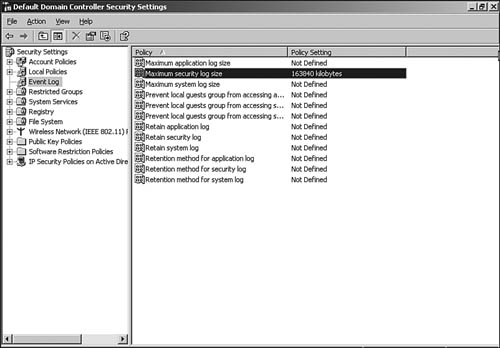
In addition to deploying the appropriate audit settings through Domain Group Policy or Local Security Policy, we suggest you enforce minimum security log sizes for domain controllers and non-domain controllers. In a domain environment, you can easily configure the Security Settings -> Event Log -> Maximum security log size setting in the Domain and Domain Controller Security Policies. We recommend domain controllers have a maximum security log size of at least 163,840KB (160MB) and non-domain controllers at least 16,384KB. In a workgroup environment, apply these settings manually at each computer (Event Viewer -> Security -> Properties -> Log Size). Figure 15.2 shows the maximum security log size policy setting for domain controllers.
You may notice that the security auditing mechanisms of Windows are cleanly divided into domain controller and non-domain controller modes of operation. This is because most of the relevant security events you want to audit take place on the domain controller. Domain user accounts receive their authentication token from a domain controller and then use that token to access resources across the domain. Capturing the issue of that token on the domain controller is how any audit trail involving domain security will begin.
Note: Determining the Number of Security Events Generated
Joseph Chan has written a script that counts the number of security events generated per second on the local computer. (To run it against a remote computer, supply the computer name as an argument). The script will continue to run until you kill it using Ctrl+C. We suggest you pipe the output to a file. Here’s an example:
SecurityEventPerSecond.vbs >> NumberOfEventsGeneratedPerSec.csv
This command sends the output to a CSV file that you can load with Excel. This utility can be useful when you want to measure the incoming event rate before or without installing an ACS collector.
For your convenience, we include this script, SecurityEventPerSecond.vbs, on the CD accompanying this book.
Planning an audit policy in itself does not involve considering the ACS components of OpsMgr, because enabling auditing affects all computers in the domain, regardless of their potential status as forwarders. After you make your audit policy decisions and deploy audit policies to your managed computers, you are ready to prepare the ACS components that will forward, collect, and store the auditing events generated at each computer in accordance with the settings in the audit polices. Your deployment planning includes the following decision points for the ACS components:
If you will host any of your ACS databases on clustered SQL Servers
If you will be implementing a security partition between your principal OpsMgr environment and the ACS Database Component
If you will integrate the ACS Reporting Component with the OpsMgr Reporting Component by sharing the same SQL Reporting Server, or if you will install ACS reports to a dedicated SQL Reporting Server
The number of ACS collectors/database pairs to include in your management group(s)
Whether to use SQL 2005 Standard or Enterprise Edition for your ACS database server(s)
The simplest of these decisions might be whether to cluster one or more of your ACS database servers. This is typically based on the following decision points:
Cost of downtime and possible emergency system restore costs
Loss of ability to collect or analyze security events while replacing a failed SQL Server hosting the ACS database
Liability for possible loss of safeguarded auditing data
Because OpsMgr 2007 does not require an Agent Component on the ACS database server, the procedures for ACS database installation and configuration on a single SQL Server or on a multinode SQL cluster are virtually identical.
Beyond the SQL cluster/no SQL cluster issue, the preferred configuration for larger environments is separating the Collector and Database Components on different servers. Separating the processing load of these dissimilar components increases the capacity of the Audit Collection Services in the management group and provides security separation between the Collector and Database Components. Because the collector is always a management server, it is subject to administrative control by the OpsMgr administrators.
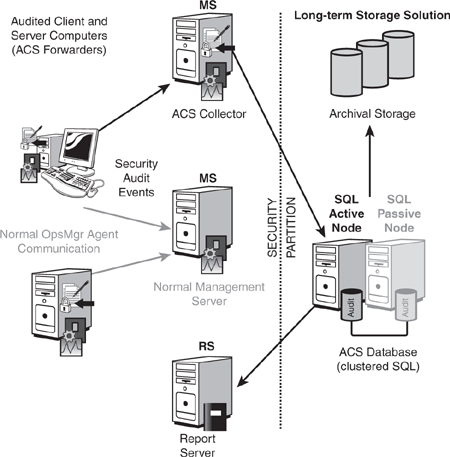
Figure 15.3 illustrates the OpsMgr components delivering Audit Collection Services in Operations Manager 2007. On the left side, you can see OpsMgr Agent Components on managed clients and servers, with the ACS forwarder enabled. While normal OpsMgr client-server communication occurs with the agents’ designated management server(s), ACS data is streamed directly from the forwarder to a collector, bypassing the regular OpsMgr management servers. On the right side of the diagram, you can see the ACS Audit Database Component and a representation of an external storage system (assuming long-term retention of audit data).
Notice in Figure 15.3 the vertical line labeled “Security Partition” separating the ACS database and archive storage system from the rest of the management group. This line represents a logical security boundary between the stored audit data and the audited management group.
It is not necessary, or in some environments even desirable, to install an OpsMgr Agent Component on the ACS database server in the same management group as the audited computers. For security considerations, you may decide to create a dedicated (even an “all in one server”) OpsMgr management group that monitors the ACS database computers in your organization. Using a separate management group prevents a careless or criminal user with elevated access to an OpsMgr configuration to run tasks on managed computers that completely compromise organizational security. Separating the ACS database server(s) (and any servers hosting long-term archive data from the organizational group they are data repositories for) can avoid this potential vulnerability.
If you require a security boundary between network administrators and network auditors, you can achieve the most complete separation when the ACS and OpsMgr Reporting Components are not integrated. This is Microsoft’s preferred deployment model and means that the SQL 2005 Reporting Services instance of the OpsMgr management group Reporting Server is not used for the audit reports. In this scenario, the audit reports are never visible in the Operations console.
You would enable this most secure scenario by installing the SQL Reporting Server Component of SQL 2005 on an additional SQL Server on the auditor’s (external) side of the security boundary. As part of installation, upload the audit reports to the external reporting server(s) where auditing personnel will have exclusive access to ACS reports. We discuss this further in the “Installing the ACS Reports” section of this chapter.
Another planning decision involves the number of ACS collector/database pairs to include in your OpsMgr deployment. Because each collector must have its own dedicated ACS database, there is always one ACS database (hosted on a standard or clustered SQL Server) for each collector. Whether you need more than one collector and database depends on the capacity of a single, given collector, as well as the bandwidth between the forwarder population(s) and their associated collector(s).
The maximum number of forwarders you can assign to the same collector will vary depending on the types of audit events selected in your audit policies. Assuming high-performance server hardware and sufficient database storage resources for the collectors and databases, here are estimated maximum loads of a single ACS collector/database pair:
150 domain controllers, or
3000 member servers, or
15,000 workstations
Most collectors have a mix of domain controller, member server, and workstation forwarders assigned to them. In that case, you can create weighted values for each type of ACS forwarder to estimate their aggregate load. We provide an example of creating weighted values later in this chapter, in the section “Managing ACS Database Size.”
A large number of forwarders cannot effectively share a low-bandwidth connection to a remote collector—for that scenario you might want to deploy several collectors, with each located in proximity to the largest forwarder populations. Figure 15.4 shows a possible ACS deployment with three collector/database pairs. Each collector is in a different physical location, with good network connectivity to its respective connected groups of ACS forwarders.
To estimate the bandwidth a particular forwarder requires to communicate with its collector, multiply the average size of a security audit event compressed for transmission (140 bytes) by the average number of security audit events in the Event log of the forwarder during a given period. For example, a moderately busy domain controller, with the desired security policy enabled, might generate 500,000 events in a 24-hour period. That equates to 70MB of network throughput per day, or about 1KB per second sustained bandwidth consumption.
Figure 15.4 illustrates each collector requiring its own dedicated ACS database and hosting SQL Server. You can implement a combination of clustered or non-clustered ACS SQL database servers, based on the requirements for each collector. This particular topology also features a shared long-term archive solution, although you can also architect dedicated archive solutions for each ACS database.
Tip: Sharing ACS Database Server Hardware
When you install ACS, you can select a named instance of SQL Server 2005 to connect to. To accommodate the one-to-one relationship between collectors and databases, you can use a single SQL Server 2005 box with named instances to create multiple ACS databases, provided it can support the additional load.
A final design decision to make is the version of SQL Server 2005 to use for the ACS database. ACS supports the use of SQL Server 2005 Standard Edition and SQL Server 2005 Enterprise Edition. The version used impacts how the system behaves during the daily 2:00 a.m. database maintenance window while the ACS database is reindexed. During the maintenance window, any database partitions with timestamps outside the data-retention schedule (14 days in the default configuration) are dropped from the database. Keep the following points in mind:
If SQL Server 2005 Standard Edition is used, security event insertion halts and events queue up on the collector until maintenance is completed. This is because SQL 2005 Standard Edition cannot perform online index operations, whereas the Enterprise Edition can.
If SQL Server 2005 Enterprise Edition is used, insertion of processed security events continues during the daily database maintenance, but at only 30%–40% of the regular rate.
SQL 2005 Enterprise Edition is probably mandatory in high-volume environments because it reduces the chance of lost security events from filling the collector queue during the maintenance window.
In Chapter 6, “Installing Operations Manager 2007,” we discuss the prerequisites and basic installation steps for deploying the ACS Database and Collector Components. This chapter picks up at that point. We have installed the ACS database on a separate server from the ACS collector, in the same manner as illustrated earlier in Figure 15.3.
If your organization does not include a separate auditing team—for example, if your OpsMgr deployment is in a smaller organization with a single IT group (or single individual!) and no one outside IT will use ACS—then no additional initial configuration of the ACS database is required. If, however, you are separating audit control from the IT group (typical in larger organizations), you must perform the following critical steps during the initial ACS database setup:
Creating a security group for the ACS auditors
Granting read-only permissions on the ACS database to the ACS auditors’ security group
Tip: About the ODBC Data Source
The ACS collector communicates with the SQL Server ACS database using an ODBC data source of the System DSN type, created on the collector during ACS installation. You can view this data source with the ODBC Data Source Administrator, launched from the Data Sources (ODBC) program in the Administrator Tools group on the Windows Start menu.
Select the System DSN tab to see the OpsMgrAC data source. Clicking the Configure button lets you change parameters of the ACS database connection, such as switching from Windows to SQL authentication, or moving the ACS database associated with the collector to another SQL Server.
Installing the ACS components does not create any security groups in the domain or on the ACS collector and database computers. If you need to create an ACS auditors security group, you can create a local or domain security group based on your particular conditions. This security group will contain the user accounts of those individuals who access and run reports on the data in the ACS database.
Base your choice of whether to use a domain or local security group on the following criteria:
“Ownership” of the security group
Ease of monitoring the membership of the group to ensure it continues to contain only the desired members
If your auditing team also owns the ACS database server, using a local group makes it easier for that team to control membership of the ACS auditors’ security group, whereas a domain security group is easier for a central IT department to administer. Most likely, if you are not integrating ACS and OpsMgr reports, you will create a local security group on the SQL Reporting Server(s) dedicated to ACS. If you install ACS reports to the same instance of SQL Reporting Server used by the OpsMgr Reporting Component, a domain security group for ACS auditors is appropriate.
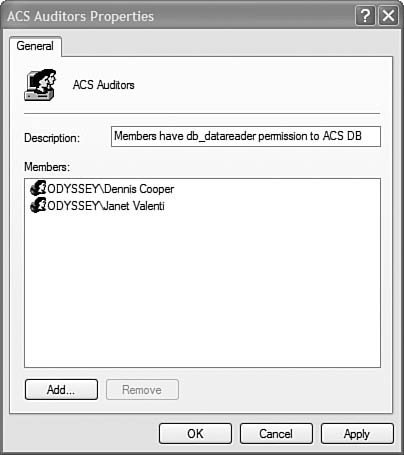
In our example, we will create a local security group on the ACS database computer (server name Fireball) and add domain user accounts as members to the group. If your ACS database is on a clustered SQL Server, create same-named local groups with the same memberships on each node of the cluster. We gave the local group on the ACS database server the name ACS Auditors. For our example, the ACS Auditors local group on Fireball has several user accounts from the Odyssey domain added as members. Figure 15.5 displays the local security group created on Fireball.
In Figure 15.5, the users who are members of the local ACS Auditors security group, Dennis Cooper and Janet Valenti, represent Odyssey Corp’s employees charged with auditing the network. If those individuals are administrators of the ACS database server and the SQL Server application is running on it, they can guarantee unauthorized employees cannot access the ACS database—by verifying their user accounts remain the only members of the security group.
Now we need to grant our ACS Auditors security group read-only rights to the ACS database. Read-only rights let those users access and run reports on the data in the ACS database without risk of modifying or deleting the collected security audit events. Perform this procedure using the SQL Server Management Studio application on the ACS database server. Open the SQL Server Management Studio and perform the following steps:
Navigate to Security -> Logins. Right-click Logins and select New Login to start the New Login Wizard.
Next to the Login name field, click the Search button.
On the Select Users or Group dialog box, click the Object Types button and add the Groups type of object. Click OK.
The From this location field should already contain the name of the ACS database server (the local machine and instance). If it does not, click the Locations button and select the local ACS database computer name. Click OK.
Enter the name of your local group (for example, ACS Auditors) and click OK. This returns you to the New Login Wizard. You should see the Login name field populated with your local ACS Auditors security group on the ACS database server.
In the Default database dropdown list, select the OperationsManagerAC database (assuming you used the default name during the installation) and click OK.
Navigate to Databases -> OperationsManagerAC -> Security -> Users. Right-click Users and select New User.
In the User name field, type a meaningful name, such as <Your Organization> ACS Auditors. (We use Odyssey ACS Auditors in our example.)
Click the selector button to the right of the Login name field. In the Select Login dialog box, click the Browse button.
In the Browse for Objects dialog box, locate the SQL login for the ACS database computer’s local ACS Auditors security group you just created. Check the box in the left column next to the local ACS Auditors security group and then click OK twice.
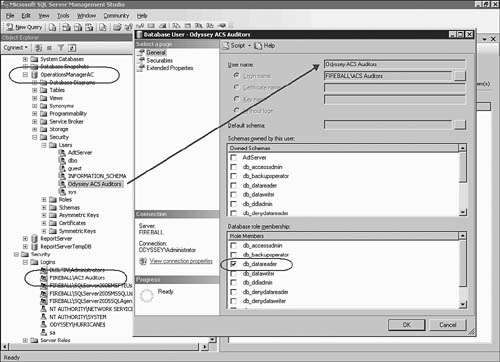
Back at the Database User – New dialog box, in the Database role membership area, check the box next to the db_datareader role and click OK.
Figure 15.6 shows the SQL Server Management Studio application after the described steps were used to create the ACS Auditors local group. We are viewing the properties of the Odyssey ACS Auditors database user. Notice the db_datareader role is the only selected role. Members of this role can run a SELECT statement against any table or view in the specified database.
Audit Collection Service Reporting uses SQL 2005 Reporting Services. In the highest security scenario, which is Microsoft’s designed environment for using ACS, audit reports run on dedicated SQL 2005 Reporting Server instances that are not part of the OpsMgr 2007 management group. Optionally and alternatively, you can integrate ACS reports with the Reporting Server Component of the OpsMgr 2007 management group. The OpsMgr installation media includes the report models and an installation utility. Follow these steps to upload the ACS reports to your management group:
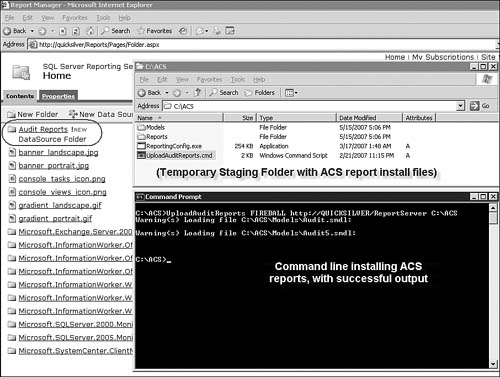
Create a temporary staging folder on a server in the management group (for example, C:ACS on the collector). Figure 15.7 is a composite screen capture showing the steps in this procedure. See the correct contents of this temporary staging folder on the upper-right side of Figure 15.7.
Copy the files and folders in the ReportModelsacs folder on the OpsMgr installation media to the staging folder. Copy the folder structure just as it is on the installation media to the staging folder.
Copy the ReportingConfig.exe file from the SupportTools folder on the OpsMgr installation media to the staging folder.
Open a command prompt (click Start -> Run and then type CMD) on the server where the staging folder is located and change directory to that folder (C:ACS).
Run the following from the command prompt:
<LINELENGTH>90</LINELENGTH>UploadAuditReports <ACSDBServerName> http://<ReportingServerName>/ReportServer <Drive:StagingFolder>
Here, <ReportingServerName> is the name of the OpsMgr management group’s Reporting Server only if you are integrating ACS reports with normal OpsMgr reports; otherwise, it is the name of the SQL 2005 Reporting Server instance used exclusively for audit reports.
If the report upload is successful, output from the UploadAuditReports command will have nothing listed after the Warning(s) message. See the command prompt output on the lower-right side of Figure 15.7 for a sample successful command-line output.
Confirm successful report loading by opening your browser and entering the web address of your management group’s reporting server, such as http://<ReportServerName>/Reports. Note the presence of the Audit Reports folder. On the left side and in the background of Figure 15.7, see Internet Explorer open to the Report Manager on the Quicksilver server, with the new report folder circled.
A fundamental decision is whether you will integrate ACS reports with your OpsMgr Reporting Server or will keep the ACS Reporting components completely separate from the OpsMgr management group. Microsoft designed ACS Reporting primarily to function in the “completely separate” model. Using this model, OpsMgr administrators have no access whatsoever to the collected audit data, report models, or templates uploaded to the SQL Reporting Server used by ACS. Auditing staff have complete ownership of, and exclusive access to, all the resources and data associated with collected security audit events.
This model is designed for larger and more security-conscious organizations. There are two other modes to deploy ACS reports; these other scenarios integrate ACS Reporting components with OpsMgr Reporting components to differing extents. The first alternative model installs the ACS reports to the OpsMgr Reporting Server but retains a separation between auditors and administrators. The second alternative model provides complete integration of ACS reports with OpsMgr reports but eliminates the security boundary. We will walk through these three different scenarios and discuss the procedures to implement them:
Complete Separation Scenario—. OpsMgr administrators and ACS auditors use different SQL Reporting Servers (ACS as designed).
To implement this scenario, install the audit reports to an instance of SQL Reporting Services separate from the instance used by the OpsMgr Reporting Component. ACS auditors are local administrators or power users of the SQL Server hosting the SQL Reporting Services instance used for collected audit data. Audit reports do not appear in the OpsMgr Operations console, and auditors use the web-based SQL Report Manager exclusively to configure and run audit reports.
Integration with Security Boundary Scenario—. Use the same SQL Reporting Server for both systems with separation between administrators and auditors, and no audit report access by OpsMgr administrators (supported by Microsoft).
This scenario retains a security boundary and simply leverages the same SQL Reporting Server instance the OpsMgr management group uses, thereby conserving SQL asset deployment. Audit reports appear in the Operations console, but you cannot run them from the console. Instead, you must use the web-based SQL Report Manager.
To implement this scenario, create a domain-based security group for the ACS auditors. Add that domain security group to the Power Users built-in local security group of the OpsMgr Reporting Server (necessary because the auditors require interactive logon rights to access the web-based SQL Reporting Manager). Also, add the domain ACS Auditors security group to the OpsMgr Report Operators user role (in the Operations console, navigate to Administration -> Security -> User Roles -> Operations Manager Report Operators -> Properties -> Add).
Additionally, you must modify the default settings of the SQL data source for the audit reports for this scenario to work. To make this modification, follow these steps:
Open the web-based SQL Report Manager in your browser. The address is http://<ReportServerName>/Reports.
Click the Audit Reports folder to open it.
In the Audit Reports folder, click the Show Details button on the upper-right side of the page.
Click the Db Audit data source object to open it.
Under Connect using, select Credentials supplied by the user running the report and Use as Windows credentials when connecting to the data source. Figure 15.8 shows the Db Audit source modified for this scenario.
Complete Integration Scenario—. Full integration of audit reports with the Operations console, with no security boundary between administrators and auditors (not supported by Microsoft).
This scenario is only appropriate where there is no concern over Operations console users having the ability to run audit reports. In a smaller OpsMgr deployment or an organization without dedicated auditing staff, implementing this scenario lets you run audit reports from the Operations console in almost the same manner as regular OpsMgr reports. Microsoft’s design for ACS is that report data will only be accessed using SQL Report Manager and only by members of the ACS Auditors security group. This scenario implements the opposite of that design, namely that report data is accessed in the Operations console by any OpsMgr administrator or user who is a member of the OpsMgr Report Operators User or Administrator role.
In an integrated ACS reporting installation, if you attempt to run an audit report in the same fashion as other reports in the Operations console’s Reporting space, you will see the following error message:
An error has occurred during report processing. Cannot create a connection to data source 'datasource1'
Reviewing the Application Event log of the Reporting Server, you will see that at that moment, the OpsMgr Data Reader account attempted to make a connection to the ACS database but permission was denied.
Because this scenario is not a supported configuration for ACS, if you choose to implement it, there may be various ways to circumvent default ACS security to make it work as desired. A simple way we discovered was to create the ACS Auditors local security group on the Reporting Server and then add the domain’s OpsMgr Data Reader Account to the ACS Auditors local security group. No changes to the default SQL data source are necessary when using this technique.
The stage is now set to begin collecting audit data from the managed computers. The final task in launching your organization’s audit collection components is to run the Enable Audit Collection task from the Operations console against the managed computers selected as ACS forwarders. By default, the service needed for an OpsMgr agent to be a forwarder (AdtAgent.exe) is installed but not enabled when the OpsMgr Agent Component is installed. Now that we have installed and configured the ACS collector and database, we must enable and configure the ACS Forwarder Component on those managed computers we identified in our audit policy to be ACS forwarders. Perform the following steps:
Open the Operations console and navigate to the Monitoring -> Operations Manager -> Agent -> Agent Health State view.
This view has two panes in the center area, and the actions in this procedure take place using the pane on the right, Agent State.
Select the computers the task will run against. You can make multiple selections by pressing Ctrl or Shift as you click.
After selecting the computers in the Agent State pane, click the Enable Audit Collection task in the Health Service Tasks area of the Actions pane in the lower-right section of the console. Figure 15.9 highlights the console features involved in this step.
Selecting the Enable Audit Collection task shown in Figure 15.9 opens a Run Task window. Specify the Fully Qualified Domain Name (FQDN) of the collector to assign to the selected forwarders, using the Override button in the Run Task window. Figure 15.10 shows the Enable Audit Collection task after specifying the FQDN of hurricane.odyssey.com as the collector.
If you have planned for only one collector in your OpsMgr management group, you will always enter the same FQDN in this task. However, if there is more than one ACS collector in your organization, take care to specify the correct FQDN for the appropriate collector. You would also need to run the Enable Audit Collection task again to target other forwarders to other collectors, because you can only specify the FQDN for one collector with each run of the task.
Click the Run button at the bottom of Figure 15.10 and optionally observe the progress of the task in the status window. When the task completes on a managed computer, the Operations Manager Audit Forwarding service on that forwarder changes from disabled startup type to automatic startup type, and then the service starts. Event 4368 from source AdtAgent will appear in the Application Event log of that system confirming that the forwarder connected to the collector. At the same time, event 4628 from source AdtServer will appear in the Application Event log of the collector. Figure 15.11 shows these two connection events from the perspectives of the Forwarder and Collector components.
During the beta-testing phase for Operations Manager 2007, Joseph Chan of Microsoft provided a PowerShell script that enables ACS on all agents to the provided ACS collector. Neal Browne from SystemCenterForum has modified the script to take the display name of the group as an added parameter, so you can control which agents are enabled.
Table 15.3 lists the parameters used by the scripts.
For your convenience, we include these two scripts—ACSBulkEnableAllAgents.ps1 and ACSBulkEnableGroupDisplayName.ps1—on the CD accompanying this book. You can also view http://goteamshake.com/?p=34 for information on these scripts.
Now that you have deployed, configured, and enabled ACS, your organization enters the long-term operating phase of the auditing solution. Your primary technical goal is to set in motion a perpetual process that keeps the ACS components secure and functioning as desired by the auditing stakeholders. You achieve your business goal when appropriate auditing reports are reviewed in a timely and recurring fashion by cognizant internal network security staff or external auditing personnel.
Here are some questions to answer regarding processes you must implement to sustain a production ACS deployment:
Who are the consumers of the security audit reports? | |
If the primary constituents of the ACS solution are external auditors not part of the normal IT team, those individuals must be positively identified by the senior leadership of the organization. If the members of IT staff are not to concern themselves with the collected audit data, make sure they are informed so they do not raise suspicion by running ACS reports! If no one is looking at the ACS reports on a scheduled basis (that is, if you deployed ACS only for use in possible future forensic investigations), someone must still periodically run some audit reports to verify the integrity and operation of the auditing solution. | |
How will authorized viewers of security audit reports physically access the reporting data? | |
If you extend access to ACS reports within the Operations console (by modifying the default security of an ACS installation), you can also provide console access to the ACS auditors. In that situation, you may want to create a user role for the auditors (under Administration -> Security -> User Roles) that has tailored and minimized access to console views and tasks. Microsoft designed ACS such that security audit reports are not viewable in the Operations console; in the default configuration of ACS, you must use the web-based SQL Report Manager to generate reports of audit data. It may be incumbent on the IT staff to support and train the auditors in use of SQL Report Manager, even though the IT staff is subject to audit scrutiny. Another excellent alternative, if acceptable to the auditing team, is to export audit reports on an automatic scheduled basis to files posted or otherwise delivered to the auditors for their review and offline retention. | |
Must auditing data be preserved in archives beyond the ACS database retention period? | |
Security audit data is automatically and permanently purged from the database after the specified retention period. To preserve data, you must create a mechanism or procedure to export data from the ACS database for longer-term retention. Because the security audit data exists in a regular SQL Server 2005 database, you can employ any standard method for SQL backup, export, log shipping, or external subscription of database data to create archival copies of records in the database. For some organizations, it is acceptable to permit grooming the ACS database records without archiving because exported audit report files provided to auditors remain available until deleted by the auditors themselves. Chapter 12, “Backup and Recovery,” discusses a methodology for archiving data from the OpsMgr data warehouse so the report data is available after the retention period. You can apply a similar technique to the ACS database. See Chapter 12 for additional information. | |
Is the ACS deployment in your organization secured to prevent circumvention? | |
Put yourself in the shoes of the malicious user who wants to do something wrong without being caught. That user might have intimate knowledge of the ACS topology in your organization. A rogue administrator would likely focus on disabling the ACS forwarder process on the computer where the illegal activity is contemplated and then wipe the local security log of the computer after the deed was done. Knowing a determined individual with broad administrative access, time, and opportunity can probably defeat almost any security initiative, it is at least prudent to perform some due-diligence “what ifs.” Implement as many reasonable countermeasures as you can envision. A simple but critical proactive measure is to eliminate common or shared use of the BUILTINAdministrator account. To audit individual administrator activity, each administrator must be required to use his own unique, named logins exclusively. | |
Have you provided for system-level management of the ACS database components? | |
Because the ACS database server(s) in your organization may not participate in your primary OpsMgr management group, you need to make sure that “care and feeding” of the SQL Server(s) is taking place. This includes antivirus, backup, updates, and server hardware health monitoring. An individual with SQL Server experience should also be responsible for periodically inspecting the ACS database server(s) to confirm there are no emerging issues with performance or database size. | |
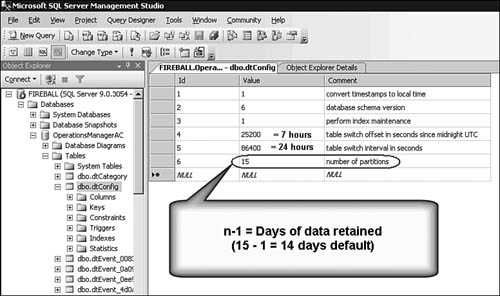
Is the default 14-day ACS data retention period sufficient for your organization? | |
Once a day (by default 7 hours after midnight Greenwich Mean Time [GMT]), grooming removes ACS database records of security audit events if they are older than the retention period. If the 14-day window is satisfactory for your organization, and if your ACS database hardware has sufficient storage resources, you need not modify the default retention period. However, you may not have enough storage for 14 days of data and you need to lower the number of days data is retained; alternatively, you may have plenty of storage and need to increase the number of days to satisfy your auditing goals. In these cases, you can modify the retention period by changing the number of partitions variable (ID 6) in the dtConfig table of the ACS database. Figure 15.12 is a view of the SQL Server Management Studio, open to the OperationsManagerAC database and showing the contents of the dtConfig table. Edit the value “n” such that “n×1” is equal to the number of days you desire to retain audit data in the ACS database. |
How you perform ongoing administration of ACS depends a great deal on whether you have implemented a security boundary between the primary management group and the ACS Database Component. It is not possible to operate an ACS deployment that is both convenient for OpsMgr administrators to access auditing data and strictly accountable to external auditing entities for integrity of the auditing solution.
ACS was designed primarily with the latter of these deployment models in mind, which makes the assumption that network administrative staff is not to be fully trusted. In this paradigm, administrators of systems are always assumed to be able to thwart security if that is their intention. The best auditing solution, therefore, is one that captures security events of interest in real time and speeds that information away from the sphere of influence of the administrator. Once the security audit events are safely stored in a location or manner that is inaccessible to your system administrators, that database of events retains its integrity as a record of the administrators’ activities.
We can approach methods of accessing ACS information from two perspectives:
An OpsMgr management group that opened up the ACS database permissions to allow access by users of the Operations console
An external auditor who has no access to the Operations console and interacts with security audit data exclusively through the web-based SQL Report Manager
Common to both approaches is that using ACS requires running reports against the ACS database. Reporting is the only mechanism to examine the collected ACS security audit data; there is no other user interface.
Importing the ACS reports into the management group using one of the integrated reporting scenarios creates a new folder in the Reporting space named Audit Reports. Inside the Audit Reports folder are 18 predefined reports and two report templates, included on the Operations Manager installation media. The audit report names are prefixed to sort alphabetically into six categories. The categories suggest scenarios in which specific predefined reports might be useful or applicable:
Access Violation (unsuccessful login attempts)
Account Management (password, group membership changes, user account created and deleted)
Forensic (events for specific computers or users)
Planning (event counts, hourly event distribution)
System Integrity (audit failure and audit log cleared)
Usage (object access, user logon, sensitive security group changes)
The two security audit report templates are cryptically named Audit and Audit5. The Audit template contains fields for up to 22 security audit event strings, basically 22 lines or elements of text that might appear in the Description area of a security audit event examined with the Windows Event Viewer. The Audit5 template provides for only the first five text elements (strings or lines of text) from the security audit event Description area. Use these criteria when selecting a template for the basis of a new custom report:
Generally select the Audit5_Report_Template, because the great majority (over 90%) of possible security audit events has five or fewer description strings anyway, and reports based on the Audit5 template will index a little faster than those based in the Audit template.
Select the Audit_Report_Template when you know that the type of security event you are creating the custom report for will contain more than five description strings.
There are several differences in the behavior of the audit reports compared to the other predefined reports available in the OpsMgr Reporting space (remember that the data for security audit reports is coming from the ACS database rather than the Data Warehouse database like the other historical data viewed in the Reporting space):
An immediate visual difference is that audit reports open in a running state, with fully predefined report parameters.
The date range and object selection are preset, the report parameters pane is not displayed, and the report window opens with the “Report is being generated” message appearing as soon as you click the Open button in the Action pane of the Reporting space. Other OpsMgr reports begin with a static window waiting for the operator to input the desired data range and add groups or objects in the parameters pane of the report window.
After generating the report, you can optionally view the report’s parameters pane (View -> Parameters in the report window).
This is a mini-parameters pane compared to the parameters pane in the regular OpsMgr reports, with only the date range available to modify. There is no object or group selection area, although some audit reports (such as Event Counts by Computer) also include a parameter for a computer name. The default date range is from midnight the calendar day before the current time to midnight the day after. Depending on the time of day you run the report, the default view will include from 24 to 48 hours of data backward from the current time.
Figure 15.13 is a screenshot of the Reporting pane in the OpsMgr Operations console, listing the audit reports and templates imported from the OpsMgr 2007 installation media.
Like all OpsMgr reports, one can schedule audit reports for publication to file shares for offline viewing, rather than viewing them live in the Operations console or with the web-based SQL Report Manager. Audit reports lend themselves in particular to scheduled and published report generation in these scenarios:
Providing an offline record of selected audit events before grooming them from the ACS database, mitigating the purging of data due to the enforcement of the ACS retention interval
Furnishing to auditing staff for a permanent record of the state of select collected data, in lieu of auditors running the reports live themselves either from the Operations console or the SQL Report Manager
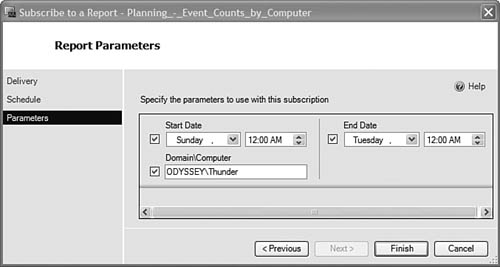
When scheduling publication of most security audit reports (also called creating a subscription in SQL Report Manager), you only need to specify the date range of the selected report. For those reports that also require the computer name parameter, there is a prompt for this when you schedule the report. Figure 15.14 shows the Report Parameters page while scheduling the Event Counts by Computer audit report. The scheduled report in this example will run against audit events from the computer Thunder (our Operational database server).
Microsoft intended that ACS reporting use the SQL Report Manager to view ACS security audit data. Unless you implement the completely integrated ACS reporting scenario, the SQL Report Manager is used exclusively for live interaction with security event data collected in the ACS database.
Even if you implement the completely integrated ACS reporting scenario and use the Operations console to run audit reports routinely, there are still several ACS-related functions that can only be performed using SQL Report Manager. For example, deleting either a predefined or a custom audit report from the Reporting Server is accomplished only through Report Manager (select Audit Reports -> Show Details and then select the report to delete and click Delete).
You can drill down into the properties of any predefined or custom audit report using SQL Report Manager. In the properties of each report, you can view and modify details such as the report’s default parameters or security. After you have scheduled an audit report for automatic publishing to a file share, you can modify the settings of that subscription by returning to SQL Report Manager. Figure 15.15 shows the Subscriptions tab of the Unsuccessful Logon Attempts audit report. Selecting Edit here would allow you to modify the schedule, published file share location, and security credentials for generation of the report.
All new and custom ACS reports are created using SQL Report Builder, a component of the SQL Reporting Service. The first time you open an audit report for editing or start a custom report authoring session, the system downloads a 6.5MB Report Builder runtime module from the SQL Reporting Server to your computer. We will be taking a closer look at the Report Builder when we create a custom report in the “Policy Changes Scenario” section later in this chapter.
The primary tool for administering ACS is a command-line tool, AdtAdmin.exe. This tool runs locally on the collector at the server console or in a Remote Desktop session. There are four categories of functions for using AdtAdmin.exe:
To change the authentication method or credentials the ACS collector uses to access the ACS database.
To use as a statistical and configuration tool for connected ACS forwarders.
To create ACS forwarder groups and assign ACS forwarders to ACS forwarder groups.
ACS forwarder groups are for convenience when updating or disconnecting large numbers of forwarders at one time.
To create Windows Management Instrumentation-based queries that limit the events stored in the ACS database.
We grouped the 12 AdtAdmin.exe commands into these categories in Table 15.4.
Table 15.4. AdtAdmin.exe Command Syntax
Category | AdtAdmin.exe Switches | Usage |
|---|---|---|
Authentication Method and Credentials |
| Displays and sets the authentication method used by the ACS collector to access the ACS database. The two available authentication methods are Windows Authentication and SQL authentication. |
ACS Forwarder Statistical and Configuration Tool |
| Lists statistical information about ACS forwarders connected to the ACS collector. See Table 15.5 for a list of statistics displayed. |
| Lists the forwarders that have ever connected to the collector, along with some statistics on each. The data that displays is a subset of the data that displays using the | |
| Changes the name and the priority value of an ACS forwarder. Also changes the group membership of a forwarder. | |
| Disconnects a specified forwarder or group of forwarders from the collector. | |
Create and Manage ACS Groups |
| Creates and deletes groups used to organize forwarders. |
| Renames an existing group. | |
| Outputs a comma-separated list of groups maintained by the collector. | |
WMI Queries to Limit Events Stored to ACS Database |
| Lists and sets the Windows Management Instrumentation (WMI) Query Language (WQL) queries used as filters on the ACS collector. |
Creating and using forwarder groups is an advanced task, only useful in very large and distributed environments where there are multiple collectors with weighted priority values or you wish to operate against large numbers of forwarders at once. Many environments use AdtAdmin.exe primarily to confirm lists of ACS forwarder populations, confirm forwarder-to-collector assignments, and manage WMI queries that filter out some events before writing to the ACS database. We exercise these common AdtAdmin.exe tasks at the command line, as shown in Figure 15.16.
Four command-line runs of the AdtAdmin.exe utility are shown in Figure 15.16. Here is an explanation of what is happening on each line:
AdtAdmin.exe /listforwardersWe see the names of the computers in the management group that are forwarders reporting to this collector. (The command AdtAdmin.exe /stats would list even more details about the state of each forwarder.) This is useful to confirm that the list of ACS forwarders we expect to be reporting to the ACS collector matches the forwarders actually reporting to the collector.
AdtAdmin.exe /getqueryThis query shows that the default WMI query is still effective. The default query state is
"select * from AdtsEvent"without any modifiers (filters). The default state writes all received security events to the database without filtering out any of them.AdtAdmin /setquery /query:"SELECT * FROM AdtsEvent WHERE NOT (HeaderUser='SYSTEM'ORHeaderUser='LOCAL SERVICE' OR HeaderUser='NETWORK SERVICE')"This particular query creates and enables a WMI query-based filter that will discard security events when the user account in the security event is the local computer account of the ACS forwarder. This is useful in a setting where you are interested in tracking only the activity of actual user accounts.
Applying one or more WMI queries as filters is a way to reduce the size of the ACS database, possibly allowing you to retain more days of meaningful audit data in the ACS database and certainly reducing the overhead of the system because there are fewer events to write to the database. WMI query-based filters apply globally to the ACS collector; any targeting of queries to specific forwarders takes place in the context of the query.
We run this command again (the same as command line 2) to confirm the WMI query that we created in command line 3 is now effective. Compared to the output of command line 2, command line 4 output includes the
WHERE NOTcondition after the default"select * from AdtsEvent". This indicates that if one of those conditions is true (in this case, if the user account is the local computer [machine] account), that condition is filtered from the event stream and not written to the ACS database.
We also wanted to include a list of the statistics returned with the command AdtAdmin.exe /stats. The output of this command can be redirected to a file (AdtAdmin.exe /stats > <filename>.csv) and the file opened in Excel as a Comma-Separated Value (CSV) text file. Viewed as a spreadsheet, there are 17 columns of data, with a row for each forwarder including a header row. Table 15.5 is a list of the contents of the header row, numbered from left to right as they appear in the spreadsheet.
Table 15.5. AdtAdmin.exe /stats Output Column Headers
Number | Header |
|---|---|
1. | Value (Priority) |
2. | SID |
3. | Name (DomainComputer) |
4. | GroupID (ACS Group) |
5. | Version |
6. | Connected (State) |
7. | Total Transmitted Events |
8. | Total Size of Transmitted Events |
9. | Recv Packet Count |
10. | Recv Packet Size |
11. | Seconds Since Connection |
12. | Average Event Rate |
13. | Current Event Rate |
14. | Average time to collector (in ms) |
15. | Connect Time |
16. | Last Action (Time) |
17. | Disconnect Time |
From time to time, performance issues regarding the ACS collector may arise. These issues will manifest themselves in a lack of timeliness in writing security audit events to the ACS database or ceasing to collect events from forwarders. In an ideal ACS world, an unlimited number of forwarders could connect to a single ACS collector, and that collector would have limitless memory and network resources. In actuality, the capacity of a given collector is finite, and it is incumbent on the administrator of the ACS collector (the OpsMgr Administrator) to keep an eye on collector performance. Three Registry keys can be tuned to help performance. These keys work in conjunction with each other:
BackOffThresholdMaximumQueueLengthDisconnectThreshold
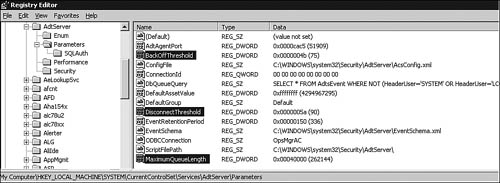
The first indication that a particular collector is nearing or exceeding its capacity limit is typically noticed when the ACS collector queue reaches the BackOffThreshold value. This is one of three parameters that control the behavior of the collector when it cannot write events to the database quickly enough. Memory on the collector is used for caching ACS events that need to be written to the ACS database. The BackOffThreshold value is a percent specifying how full the memory-based collector queue can become before the collector denies new connections from its forwarders. The default size of the collector queue is 262,144 events. With each event consuming an average 512 bytes, this means the collector queue occupies about 134MB of memory. Figure 15.17 shows the Registry Editor on the ACS collector open to the key where the threshold and queue levels are set (HKLMSystemCurrentControlSetServicesAdtServerParameters).
As exposed in the Registry of the collector in Figure 15.17, we see the BackOffThreshold is set to 75% of the MaximumQueueLength value. An additional performance-sensitive Registry key is highlighted in the figure, which is the DisconnectThreshold, also stated as a percent and by default set to 90% of the MaximumQueueLength. The settings of these three parameters work together to manage event insertion to the ACS database during capacity overload periods. When ACS is operating normally, the queue length should rarely reach the BackOffThreshold value, and it should never exceed the DisconnectThreshold (except during periods when the ACS database server is known to be unavailable, such as when the server is restarted after operating system updates have been loaded).
When the capacity of a given collector is completely exhausted, the sequence of events illustrated in Figure 15.18 will occur. Following the events clockwise in the figure, we describe what is happening at each step:
(Upper-left corner of Figure 15.18, AdtServer Event ID 4615.) The ACS Collector queue status is reported at 100%, which is above the 90%
DisconnectThreshold. All new ACS forwarder connections will be denied and some current connections will be disconnected.(Upper-right corner, Event ID 4630.) A particular forwarder (the computer Pantheon, in this case) is disconnected due to the
DisconnectThresholdbeing exceeded. The ACS collector will methodically disconnect ACS forwarders one by one until the queue is lower than theDisconnectThreshold. A separate Event ID 4630 will occur for each disconnected forwarder.(Lower-right corner, Event ID 4614.) The ACS Collector queue (now at 83%) has drawn down to below the
DisconnectThreshold(90%), but is still above theBackOffThreshold(75%). In this mode, new ACS forwarder connections continue to be denied, but the ACS collector stops actively disconnecting forwarders.(Lower-left corner, Event ID 4613.) The ACS Collector queue, at 73%, has now dropped below the
BackOffThresholdand resumed normal operation. ACS forwarders that were disconnected or denied connections will automatically and rapidly reconnect.
If you observe this sequence of events occurring frequently on a collector, that collector’s capacity has been exceeded and you need to modify the ACS environment to provide a credible and reliable audit collection service. To resolve collector performance issues, you can either reduce the volume of events written to the ACS database or add hardware to the ACS infrastructure.
To reduce the quantity of events, you can take one of the following approaches:
Modifying your security policies to collect fewer events
Applying WMI-based queries using AdtAdmin.exe on the collector to filter out unnecessary events
Reducing the population of forwarders
Hardware solutions to capacity issues include the following:
Adding one or more collectors to the management group to split the forwarder loads
Adding memory or otherwise upgrading the collector
Upgrading the SQL Server hosting the ACS database to provide faster disk writes
Tip: Detailed Logging on ACS Forwarders
If you are experiencing a performance issue with a particular forwarder, you might find it useful to temporarily enable detailed logging on the forwarder. To do so, create a new DWORD value named TraceFlags with a decimal value of 524420 in the Registry of the ACS forwarder at this location:
HKLMSYSTEMCurrentControlSetServicesAdtAgentParameters
After you create the Registry key, restart the Operations Manager Audit Forwarding service (AdtAgent.exe) on the forwarder. A detailed log will be created at %systemroot%TempAdtAgent.log.
A precursor condition, and one that may indicate collector performance issues, is increasing event latency—that is, an increase in the average time between event generation and collection. This is a measure of how quickly security audit events are captured to the ACS database after the events actually occur on the forwarder. A latency of between 1 and 2 seconds indicates a healthy forwarder-collector-database relationship. Although this latency may grow slightly as large numbers of forwarders are connected to a collector, if you keep an eye on this indicator, you will know when performance is beginning to degrade (hopefully in time to take corrective action before queue threshold events start to occur).
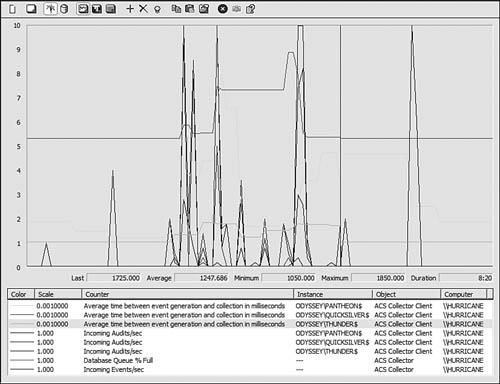
The Windows Performance Monitor is a great tool for observing ACS system health in real time. When you install the ACS Collector Component on an OpsMgr management server, two Performance Monitor objects are added: ACS Collector and ACS Collector Client. The ACS Collector object exposes 16 counters related to the functions of the ACS Collector server itself. The ACS Collector Client object adds just three counters—one of these is the average time between event generation and collection, a latency counter useful for assessing the health of a collector. Figure 15.19 shows the Performance Monitor running against the ACS collector.
In the Windows Performance Monitor chart view shown in Figure 15.19, we have loaded several ACS Collector counters related to the collector itself (the bottom two rows in the chart legend). Notice the Database Queue % Full counter, which can help you keep tabs on that important measure of the ACS Collector queue before it exceeds any thresholds.
We also loaded a pair of ACS Collector Client counters: the Average time between event generation and collection in milliseconds counter and the Incoming Audits/sec counter. An instance of each counter is running against three individual forwarders (computers Pantheon, Quicksilver, and Thunder). This information is also available in a snapshot format by running AdtAdmin.exe /stats, but it can be more convenient and useful to watch a live representation of the data in the Performance Monitor.
You must closely manage the ACS database size on the storage system of the SQL Server hosting it. Actively tracking database growth can avoid a possible database shutdown or system crash, which will occur if the database consumes all disk space. Once forwarders begin to send security events to the collector, the ACS database will grow in size.
Assuming a constant number of forwarders connect to the collector and you are collecting a uniform daily quantity of security events, the database will grow at a constant rate until it reaches the ACS database retention period, which is 14 days by default. If nothing changes after that, beginning at the 15th day, the ACS database would remain at about the same size indefinitely.
In the real world, of course, conditions are often constantly changing. It is difficult to precisely manage the size of the ACS database, due to the large number of variables that can rapidly affect the quantity and type of events collected by ACS. You can, however, make some informed estimates of how much disk space your ACS database is going to need—based on the number and composition of forwarders that are planned to connect to a particular collector.
From reviewing the ACS database, we determined that immediately after a fresh installation of OpsMgr 2007 ACS components, the database size on disk was 132MB, with the used portion of the total database size being 8MB. Microsoft has also published the capacity of a single collector based on weighted values that correspond to the volume of security audit events expected by different types of ACS forwarders. These maximum capacities are:
150 domain controllers, or
3000 member servers, or
15,000 workstations
This means we can assign a cost to each of these types of forwarders and interpolate mixes of the types of forwarders. We can assign workstations a value of 1 (15,000/15,000), member servers a value of 5 (15,000/3000), and domain controllers a value of 100 (15,000/150). We will use these weighted values in calculations that include all three types of forwarders.
Another key piece of data needed to create an ACS database size approximation is the average size (in MB) that a single forwarder contributes each day to database growth. We selected a base estimate of 8MB per day per workstation for this value, based on the data Microsoft published about its own experiences using ACS. We also have validated that member servers generate at least triple the quantity of events as workstations, and that domain controllers generate at least 100 times as many security events as workstations, so these weighted values appear reasonably accurate.
Note: ACS Database Daily Growth
Although Microsoft’s daily growth rate is approximately 8MB per day per workstation, you may consider this to be “heavy” usage (for example, growth in an environment with heavy logging). Your experience may vary based on daily activity.
We have determined that an environment with light usage will likely see 2MB per day, and with an average load, 4MB. The formula and graphic in this chapter show the upper-bound sizing of 8MB per day, because it is best to scale for worst-case unless you know how large the volume of data will be. If you know you will have significantly less activity, you can adjust the formula accordingly.
From this exercise, we developed the following formula to estimate the size of the ACS database:
(8 MB/day × (Number of Workstations) × Retention Days) + (8 MB/day × (Number of Servers * 5) × Retention Days) + (8 MB/day × (Number of Domain Controllers * 100) × Retention Days) + 8 MB (original base DB size) = ACS Database Size
Figure 15.20 displays a chart representing possible ACS database growth for given mixes of ACS forwarder types. At the top of the scale in our estimate, for a large environment with 3000 workstations, 600 servers, and 14 domain controllers, we can project an ACS database of about 840GB with a 14-day retention period. A large-scale real-world statistic comes from Microsoft’s own early use of ACS. Microsoft monitored the security of 5000 servers and 10,000 workstations, with a 30-day retention period, and it had about an 8TB (8000GB) ACS database. (We understand that Microsoft has since trimmed its retention period to 12 days.)
If you experience ACS database growth that is beyond what the SQL Server hosting your database can support, you can take one of several approaches:
Increase the storage available for the database
Reduce the amount of data going into the database
Modify the number of days of data you are retaining
You can reduce the amount of data written to the database in the same manner as if you were experiencing overloading of a collector, namely collecting fewer events by changing audit policies or discarding unneeded events with WMI query filters. Reducing the number of days in the retention period is the primary way to quickly cut the size of the ACS database.
Earlier in the “Planning ACS Component Deployment” section of this chapter, we discussed the ability to cluster the SQL database server that hosts the ACS database. Doing so can provide uninterrupted audit collection services while one of the SQL cluster nodes is unavailable. However, the secondary management server that has the ACS Collector Component cannot be clustered, leaving a single point of failure in the audit collection architecture. If the collector is down temporarily, such as during a restart following the routine installation of updates, the forwarders remain in a disconnected state and audit collection is paused. If the ACS Collector component fails completely, such as a drive array crash, the organization stops collecting audit data while a new ACS Collector Component is installed and the ACS architecture realigned.
To avoid these situations involving downtime of the ACS Collector Component, install multiple ACS collector/database pairs in your organization and configure your ACS forwarders for failover operation. Figure 15.21 illustrates an organization that has deployed two ACS collector/database pairs and has enabled failover operation of its ACS forwarders.
The procedure to activate an ACS forwarder and assign that forwarder to a particular collector, covered previously in this chapter in the “Running the Enable Audit Collection Task” section, is not used when enabling failover operation. The forwarder locates collectors by checking the Registry on the local agent computer. A list of ACS collectors is maintained at this Registry key on each forwarder:
HKLMSOFTWAREPoliciesMicrosoftAdtAgentParametersAdtServers
When the forwarder starts up, and when it is attempting to reconnect to a collector after being disconnected, it looks up the list of collector names at that Registry key and connects to the first one it can establish a connection with. The value at that key is of the REG_MULTI_SZ type, meaning that multiple string elements can exist, each on a different line of the value. When you invoke the Enable Audit Collection task in the Operations console, you can only enter a single collector name (a single string value), and the task running on the forwarder will overwrite whatever was at that Registry key with the single string value.
To implement ACS agent failover support in your organization, you must deploy one or more additional ACS collector/database pairs. You still run the Enable Audit Collection Task in the Operations console to enable an ACS forwarder initially—specify the name of that forwarder’s assigned primary collector when you run the task. Then you return to each ACS forwarder and edit the Registry key, adding the alternate forwarder names on the second and subsequent lines of the REG_MULTI_SZ value.
The VBScript command shell.regwrite, often used to automate Registry changes, does not handle multistring values, so you will have to make the change manually on computers that are to participate in the ACS agent failover scheme. The AdtServer Registry key, configured on a given forwarder as desired for a particular set of primary and alternate collectors, could be exported to a .REG file using the Regedit utility, and that .REG file merged into forwarder registries.
Once the AdtServer Registry key is configured with multiple collector names for agent failover support, be careful not to run the Enable Audit Collection Task in the Operations console again, because doing so overwrites the multiple collector names with the one name specified when running the task!
To force failover of forwarders to their alternate ACS collector(s), you can stop the Operations Manager Audit Collection service (AdtServer.exe) on the primary collector. Once a forwarder connects to an alternate collector, it will remain connected until disconnected for any reason (such as running AdtAdmin.exe /disconnect on the alternate collector). After each disconnection event, the forwarder again processes the list of collectors found at the Registry key. If the primary collector is available, the forwarder will connect to it and resume normal communication.
There may be situations where you want to audit computers that are not in the domain of the management group, or are not in domain(s) that trust the management group domain. Specifically, you may have computers in workgroups and in untrusted domains that need to participate in ACS.
To provide security auditing services to a computer that does not trust the collector, first enable certificate-based mutual authentication of the OpsMgr Agent Component as discussed in Chapter 11, “Securing Operations Manager 2007.” Then follow these steps to enable ACS:
One time only, on the ACS collector, stop the AdtServer service and run
AdtServer.exe -cat the command prompt. Select to import the certificate already issued and in use for the OpsMgr Gateway Component communication. Restart the AdtServer service.For each certificate-based ACS forwarder, use the Certificates MMC (Microsoft Management Console) to export the agent communication certificate in .CER file format (also known as an X.509 certificate).
Using the Active Domain (AD) Users and Computers MMC in the OpsMgr AD domain, create computer accounts with names that match the certificate-based forwarder computer names.
From the Name Mapping tab on the computer account object in AD Users and Computers, import the X.509 certificate exported in step 2 to the computer account created in step 3.
Run the Enable Audit Collection task against the agent in the Operations console.
On the forwarder, stop the AdtAgent service and run
AdtAgent.exe -cat the command prompt. Select to import the certificate already issued and in use for the OpsMgr Agent Component communication. Restart the AdtAgent service.
We close this chapter with four real-world situations where you can use ACS. Each scenario demonstrates the underlying audit plan and corresponding audit report that together meet a particular auditing objective. Essentially, ACS exists to enable enforcement of audit plans by reporting on compliance with those plans. In these scenarios, we describe a business-oriented situation that ACS can help with, and we clearly state the objective of the auditors, who are the customers of the ACS reports.
A couple of categories of audit reports are not covered in the four scenarios, those being the Planning and the Forensic audit reports. There are four predefined reports in the Planning audit report category:
Event Counts—. What are most common events across all computers?
Event Counts by Computer—. What are the most common events on a particular computer?
Hourly Event Distribution—. Show me the ACS utilization pattern.
Logon Counts of Privileged Users—. Are privileged logon accounts being overused or abused?
The predefined Planning reports are very useful to the ACS administrator for assessing the ongoing health of ACS. The two event count reports are excellent baselines the administrator should be familiar with to be able to compare against future similar reports and establish trends. If you are experiencing a capacity or performance issue with your ACS database or collector components, the event count reports can help you make informed decisions about which events to stop collecting. The Hourly Event Distribution report provides another baseline and helps you in detecting spikes and troughs. Marked departures from average hourly event volume should be accounted for by expected user activity levels or investigated further to determine the origin of the anomalies. Figure 15.22 shows off the Hourly Event Distribution report, in this case a copy of the report exported as a PDF file.
There are three predefined reports in the Forensic audit report category:
All Events for Specified User—. What computers did this person log on to?
All Events for Specified Computer—. Show me everyone that logged on to this computer.
All Events with Specified Event ID—. Show me every event of this type on any computer where it occurred.
Reports in the Forensic category are useful when investigating recent security-sensitive activity. These reports are broad nets cast across the entire ACS database, combing for and collecting specific events of interest. Although the reports in the scenarios that follow have specific focused objectives based on audit plans, the forensic reports can help auditors answer fundamental investigative questions. The following scenarios cover situations that lend themselves to routine and recurring generation of reports for enforcing ongoing audit objectives. The reports in the Forensic category are used “on demand” for live interactive queries to the database on an as-needed basis.
The controlling authority of a network wants to keep a close eye on the membership of the powerful Domain Admin and Builtin (Local) Administrators groups. The membership of these groups is set by organizational policy and should never change without advance knowledge and permission of the controlling authority.
Without ACS, the authority must manually and periodically examine the membership of the groups using the Active Directory Users and Computers MMC snap-in for the domain, the local Computer Management MMC snap-in for member servers, or command-line utilities that retrieve group membership. Group membership must be compared to lists of authorized members to detect unauthorized changes.
Verify that the membership of the administrator groups remains the same. Auditors need to be aware that changes have taken place and validate discovered changes with the controlling authority. When there are authorized changes, auditors will expect positive confirmation that the expected changes occur.
Audit success events in the account management category. Figure 15.23 shows the Default Domain Controller Security Settings, with the Audit account management policy and Success event auditing enabled.
Deploy this policy to the Default Domain Controllers Security Settings to monitor the membership of the Domain Admin and BuiltinAdministrator groups.
Deploy this policy to the Default Domain Security Settings as well if you will be monitoring the membership of the administrators groups on member servers.
The Domain and Built-in Administrators Changes report, shown in Figure 15.24, lists membership changes in the Domain Admin and BUILTINAdministrators groups. It looks for events 632, 633, 636, and 637 (membership change event for local and global groups) when the target is an administrator group. Figure 15.24 shows the results of this report, revealing changes did occur to both the Domain Admins group and the BUILTINAdministrators group of both the domain controller (Pantheon) and a domain member server (Thunder).
Auditors can review a report similar to that shown in Figure 15.24 on a scheduled basis, such as weekly, and confirm that membership additions and removals are expected and authorized. This report is a good candidate for scheduling publication to a file share for auditors to review offline. A blank or empty report indicates no changes occurring during the report period. Make sure the period of the report is equal to or greater than the interval between published reports (that is, if auditors receive a weekly scheduled report, the report period should cover at least 7 days).
Other reports in the Account Management Category include the following:
User Accounts Created and User Accounts Deleted—. These reports look for event 624, which tracks user account creation, and event 630, which tracks user account deletion. These reports serve as excellent offline records of user entry and exit from the organization’s directory services.
Password Change Attempts by Non-Owner—. This report details any password change or reset attempts by someone other than the account owner. Event 627 indicates password change attempt, and event 628 indicates password reset. Only routine and expected events should appear in the report, such as administrators and account operators provisioning and maintaining user accounts for the organization. You want to investigate password change attempts by unauthorized users or against privileged accounts.
Highly sensitive files in the Human Resources (HR) department file share require close watch. Network administrators must comply with an organizational policy forbidding any access attempts or access to certain folders in the file system of the HR networked file server.
Examples of these types of highly sensitive files include employee compensation information and legal correspondence. When high dollar values and very personal information is involved, senior management has requested the most stringent object access logging is enabled.
Protect sensitive files by alerting on possible unauthorized access attempts, and show access by authorized users. Senior management and auditors need to verify that only authorized users have accessed the sensitive files, and they need to follow up on any instance of a network administrator violating the access policy.
The official warning to IT staff, combined with auditing enabled to detect violations, should create a self-enforcing and auditable file integrity solution. The goal is to prove to senior management that highly sensitive files do not have inappropriate access by anyone, including IT staff.
Audit success and failure events in the system event and logon event categories, and audit success events in the object access category. Figure 15.25 shows the Default Domain Security Settings, with the Audit logon events and Audit system events policies set for Success and Failure event auditing. Also, the Audit object access policy is set for Success event auditing.
Deploy this policy to the Default Domain Controllers Security Settings only if the sensitive files reside on a domain controller.
Deploy this policy to the Default Domain Security Settings in order to monitor the sensitive files on member servers such as file servers.
Enable auditing on the sensitive files or folders. Enabling auditing of object access is a two-step procedure. First, you apply the Audit Object Access policy to the domain or domain controller security policy, then you specify what kind of object accesses are to be audited in the advanced security properties of the files, folders, or other objects of interest.
After deploying security settings to computers that include any auditing of object access, you must then specify in the advanced security properties of the objects to be audited exactly what event(s) you want to audit. In our example, illustrated in Figure 15.26, we have enabled object access auditing of members of the IT Department Staff against the folder used by the Human Resources department for highly sensitive files. Only object accesses and attempted object access by members of the IT Department Staff security group generate audit events.
Notice that because we want to audit all the files and folders in this sensitive folder, we have selected the Replace auditing entries on all child objects setting before clicking the Apply button. We want to point out that this same method of auditing file and folder access can be used for other Active Directory objects such as GPOs and Organizational Units (OUs). Once object access auditing is enabled in the domain, any object in the Windows environment that includes advanced security properties can be enabled for audit.
Tip: Be Specific when Enabling Object Auditing
To reduce the volume of events generated and maximize the effectiveness of each event, only audit the actions that really interest you. For example, if you are interested in users reading a file, do not audit Full Control. Also, for best system performance, minimize the number of auditing entries on the Security properties, Auditing tab through the judicious use of Windows security groups. Avoid adding many individual auditing entries for particular users and groups—it is better to create a group that contains all the users and groups to be audited and specify just that group on the Auditing tab.
The Object Access report shows all object access-related audit events within the specified time range. It uses the events 560 (permission requested) and 567 (permission exercised) to track items with object access auditing enabled. Figure 15.27 shows the results of this report, which did discover an attempted access violation. User CPrice, who is a member of the IT Department Staff security group, attempted to access the Pending Legal Cases.xls file, which is in the Legal subfolder of the DepartmentsHuman ResourcesRestricted Access folder on server Thunder, which we are auditing.
An organization has deployed ACS as its primary vehicle to track compliance with auditing objectives. We have seen in this chapter that audit settings, deployed via Active Directory group policy, underpins all of Audit Collection Services. If an administrator were to surreptitiously or inadvertently modify the audit settings in the group policy, entire categories of audit reports may no longer contain the data ACS was deployed to collect. The organization needs a positive means to catch changes in audit policy as they occur; in other words, a way to audit the auditing system.
Verify that no changes to audit policy occur without direction from the controlling authority of the network. As with the Domain and Administrator Group Changes report we looked at previously in the “Account Management Scenario” section, auditors need to review a report on a regular and scheduled basis. The objective is to both detect unauthorized changes to audit policy and validate implementation of authorized changes.
Audit success events in the policy change event category. Figure 15.28 shows the Default Domain Controller Policy, Security Settings, with the Audit policy change policy set to audit Success events.
Deploy this policy to the Default Domain Controllers Security Settings to monitor changes to the domain controller audit policy.
Deploy this policy to the Default Domain Security Settings as well if you will be monitoring changes to the local audit policy of member servers. Note that if the setting for a particular policy in the domain security settings is undefined, local policy on a member server can be modified by any user with administrator rights on the member server.
A predefined report to detect audit policy changes is not included with Operations Manager 2007, so we will create a custom report to detect audit policy changes as part of this scenario. The basis of this report is security event ID 612; an example of this event type is shown in Figure 15.29.
Security event ID 612 has an atypical construction; the description field of the event is actually a little chart with plus and minus symbols in columns lined up with audit policy names. The pluses indicate auditing was enabled; minuses indicate it was disabled. For example, in the Event ID 612 shown in Figure 15.29, circled to the left of the System policy row, notice the plus in the Success column and the minus in the Failure column. This corresponds to setting the Audit system events policy to audit success events and to not audit failure events.
Each of the plusses and minuses in the description of Event ID 612 is stored in the event as a separate string value. ACS reporting is able to extract those string values individually, and you can create a custom report with columns that match those in the event description field. We will now step through the creation of a custom report using the SQL 2005 Report Builder. Because this report focuses on a particular event ID, we will save time by copying the All Events With Specified Event ID report and modifying it, rather than starting with a generic report template. Perform the following steps:
Open your browser and enter the address http://<ReportServerName >/Reports. The SQL Server Reporting Services page will open. Click the Audit Reports folder in the main window.
In the Audit Reports folder, click the Report Builder button in the menu bar of the window. The SQL Server 2005 Reporting Services Report Builder application will download and open.
In the lower-right corner of the Report Builder window, click the Open from Report Server link. Browse to the Audit Reports folder, select the Forensic_-_All_Events_With_Specified_Event_ID report, and click the Open button. The Report Builder will launch, with the All Events With Specified Event ID report open for editing.
First, we will change the report, from one that prompts you to input the event ID of interest at runtime, to one that is fixed on a particular event. Click the Filter button on the menu bar and change the setting of the event ID from prompt to specified, and select 612 as the value. Figure 15.30 shows the Filter Data window. Click the item Event ID next to the green question mark and unselect Prompt. Click OK to return to the main Report Builder window.
Because this report now only contains events with the same ID, you can delete the report column that displays the event ID. Right-click the Event ID column and select Delete.
The predefined report we are modifying only has columns for the first five string fields in the event. By counting the 18 plusses and misuses in the Event 612 description field, we know that our custom report will need 18 columns to display the 18 string fields. Beginning with String 06, select the 13 string fields from 06 to 18 in the Fields area in the lower left of the Report Builder, and drag them using the left mouse button to the right edge of String 05 in the main design window. Release the mouse button, and you should see your report now extend further to the right and contain String 01 to String 18 in 18 contiguous columns. Figure 15.31 illustrates this select, drag, and add action.
The foundation of our custom report is now built! The remaining steps are cosmetic and increase the readability and meaningfulness of the report. Begin by changing the report title and description to match the new custom purpose of the report. For example, change the All Events with Specified Event ID report title to All Audit Policy Changes. Optionally, add additional text boxes (Insert -> Text Box) with information that might be useful to readers of the report anywhere on the report that makes sense.
Because we added so many columns, the report now extends off the page to the right. Select File -> Page Setup from the Report Builder menu and set the report orientation to Landscape. We also selected a custom paper width of 15 inches (38 centimeters) to accommodate the wide format.
Now, we will modify the column headers from their generic text (String 01, String 02, and so on) to headers that match the meaning of the plus or minus signs that will appear in the columns. Double-click each string column header and type the new text, such as Logon-Logoff Success and Logon-Logoff Failure for the first two string columns.
Save the report with a new name to the Report Server (select File -> Save As). To maintain consistency with the predefined reports, we gave this custom report the name Policy_Changes_-_All_Audit_Policy_Changes.
Before you close the Report Builder, export a file-based copy of your custom report. Select File -> Save to File. The Report Builder saves your custom report to an RDPL (sometimes also called a RDL) file that can be backed up for archive purposes, as well as imported to other ACS report servers in your organization.
By default, RDPL files are saved to the My Documents folder. Because this folder is unique to each user, we suggest a centralized place to store your reports, such as c:exports. This not only makes it easy to see all customized ACS reports in one place (because each person has a unique My Documents folder), but it also gives you a single location from which to collect them for backup purposes.
To import your custom report to another instance of ACS, open Report Builder from another SQL Reporting Server (as we did in step 2 of this procedure), but select Open from File rather than Open from Report Server as we did in step 3. Select the RDPL file exported from the original instance, and once it’s loaded in Report Builder, save it to the additional Report Server (File -> Save).
Figure 15.32 displays the custom report after it has run against the ACS database. Each occurrence of Event ID 612 is listed with the plusses and minuses in columns that describe their significance. We circled the same System Success and System Failure policy status indicators on the custom report as we did in Figure 15.29, a sample Event ID 612 from an ACS forwarder.
An organization acknowledges that an administrator wishing to destroy evidence of inappropriate activities will seek to disable the ACS forwarder before the unauthorized activity and then clear the security event logs of the involved computers afterward (covering his tracks). The controlling authority of the network has instructed network administrators that they are never to clear the security log on audited computers. The organization needs a way to detect when the security log is cleared on computers—which is always a violation of policy—so that an investigation can be initiated.
Verify that no occurrences of security event logs being cleared exist. Auditors need to review a report of any instances of the prohibited action on a regular and scheduled basis.
It is not necessary to deploy any audit policy setting to enable the collection of Event ID 517, The audit log was cleared. This event is always written to a Windows computer’s security event log when the log is cleared. To detect security event logs being cleared, it is sufficient to enable the forwarder on a computer and run this report at least as frequently as the retention period of events in the ACS database.
The Audit Log Cleared report, shown in Figure 15.33, shows which computers’ audit logs were cleared and who cleared them. In this example, the domain Administrator account cleared the security event log on computer Thunder, then two minutes later it was cleared again by user IFong—definitely something suspicious that should be checked out.
If you run the Audit Log Cleared report and get a blank or empty report, it means there were no instances of the security audit log being cleared during the period of the report. This, of course, is the normal and desired result at most organizations! Be aware that if you implement the WMI query-based filter to discard events sourced from computers’ system accounts, as we demonstrated in the “Using AdtAdmin.exe” section of this chapter, you will not get any data in the Audit Log Cleared report. That is because the user for Event ID 517 is the NT AUTHORITYSYSTEM account.
There is one other report in the System Integrity category that is useful to run on a scheduled basis in tandem with the Audit Log Cleared report—the Audit Failures report. The Audit Failures report looks for Event ID 516 and indicates that the system failed to audit events due to a lack of resources. If any computers appear in the Audit Failures report, it indicates a serious problem that should be resolved as soon as possible to prevent further loss of audit data.
Before the introduction of the Audit Collection Services (ACS) in Operations Manager 2007, organizations desiring to achieve a central view of all critical security-related events in their enterprise faced some daunting challenges. Microsoft’s bundling of ACS with OpsMgr is a triumph that for some organizations will justify the deployment of OpsMgr just to get ACS!
In this chapter, we stepped through the process of deciding which audit polices we will deploy as well as how to deploy ACS components to enable enforcement of those policies. We covered how ACS is administered during routine operations and how to handle some special challenges related to the capacity and redundancy of the ACS infrastructure. We closed with four reporting scenarios that tied the selection of audit policies to deploy with the reports to be run, which together deliver the desired information to auditors. The next chapter discusses additional new capabilities in Operations Manager 2007, user workstation management, and client monitoring features.