Viruses, Trojans, and Worms
It is interesting to consider how fast time passes on the Internet. Just a few years ago, a difference was readily apparent between a virus, a Trojan, and a worm. Each had its place and caused its own mischief on a personal computer. Today, however, the lines have become blurred to the point of confusion, although it is quite common for a single program to represent characteristics of each. Today, viruses, Trojans, and worms have the potential to wreak havoc on the entire Internet infrastructure, bringing major Internet backbones and servers to their knees by overloading them with traffic.
What Is a Virus?
A virus is a piece of software that installs itself on your computer against your wishes. It typically has some sort of payload. Viruses are manmade and typically are created to bring destruction. Their payload might consist of such things as randomly deleting files on your hard drive, or making infinite copies of themselves until a computer's resources are overloaded and the system halts.
Viruses might piggyback on file attachments you get in e-mail. They rarely come as their own software, but more often come by another infected piece of software. The infected file attachment could be anything from a Microsoft Word document to an entertaining game program. The analogy can be likened to the flu bug. Most people get the flu bug by contact with infected people. The infected people might not even know that they are sick with the flu bug, although they are passing it around. The flu bug started somewhere, and then kept replicating, much as a computer virus does.
The common characteristic that represents a virus is that it replicates itself. The replication is usually local to the computer that is infected. The virus might infect memory on the computer, or might infect individual files on the computer. The virus might also infect the Master Boot Record (MBR), which is responsible for booting up the computer. Mass infection makes an infected computer difficult to clean.
What Is a Trojan?
A Trojan is also a piece of software that installs itself on your computer against your wishes. Trojans get their name from the ancient myth that the Greeks used a Trojan horse to gain access to the city of Troy. By fooling the people of Troy into believing that this huge wooden horse was a gift that would only bring good, the Greeks tricked the people into opening their gates and letting their guard down. The Trojan horse was filled with Greek soldiers. At night, when the people of Troy slept, the Greek soldiers who were hiding inside the Trojan horse quietly exited and either killed or captured everyone in Troy.
Software programs that install Trojans do not appear obvious. They come as e-mail attachments, like those funny executables that get passed around during the Christmas holidays, running a program that shows Santa riding his sleigh. The Trojan can be a secret piece of code that tags along and is launched with the executable. After the Trojan is launched, it installs on your machine. A Trojan also delivers a payload. In fact, it might look very much like the payload of a virus. Sometimes, the Trojans open backdoors in your computer. Backdoors are openings that allow control of your computer.
A hacker across the Internet, for example, might create a Trojan that e-mails him after it is installed on your machine. The e-mail contains the IP address of your computer, and the Trojan opens a backdoor for the hacker to connect to your computer. The hacker might connect using some special software, or just the built-in networking functions of the operating system. Typically, the connection will carry whatever privileges you were logged in with at the time the Trojan was installed. If you were logged in as an administrator with full control of your computer, the Trojan and the hacker gain the same level of control. Trojans do not replicate themselves like viruses do. A Trojan's main characteristic is that it comes disguised as a benevolent program.
What Is a Worm?
A worm is basically like a virus, in that it replicates itself many times over. However, worms replicate themselves over networks, whereas viruses remain local to the machine. A worm can spread over a network in many ways. It can spread by distributing itself through e-mail when someone launches it from an attachment. It can spread through JavaScript on a Web site, or it can spread itself by scanning for vulnerable computers and infecting them. The worm might be designed to exploit a specific application that is running on a computer.
This was recently the case with the Code Red and Nimda worms. Appearing in the wild in September 2001, the Nimda (Admin spelled backwards) worm displayed characteristics of a virus, Trojan, and worm. Nimda would arrive in a person's e-mail box as an e-mail message with an attachment named README.EXE. If the e-mail user tried to open this attachment, the Nimda worm would start infecting his computer and start looking for ways to spread itself. Nimda had virus characteristics because it would modify and create files on the computer and change the computer's configuration. It also had Trojan characteristics in that it would arrive as some benign e-mail attachment and would pollute trusted files on the computer, such as RICHED32.DLL, a file used to open Microsoft Word documents. Its worm characteristics were also advanced, because it could spread itself in multiple ways. Nimda would attempt to find and infect vulnerable Microsoft Web servers and spread between them. It would also modify (Trojan) the Web server's home page so that other users who trusted and visited the site with Internet Explorer would download and install the worm on their own computer. Then, of course, it would spread itself through e-mail messages, using its own e-mail engine instead of the e-mail client (Eudora or Outlook) that delivered it.
Viruses, Trojans, and worms are often referred to as malicious software because they are essentially programs that have an ill intention. Most of the malicious software activity in 2000 and 2001 was by sophisticated programs. These programs represented characteristics from each of the categories of virus, Trojan, and worm, similar to the Nimda worm. The programs' propagation through e-mail was the worm-like activity, whereas the infection of computers was the virus-like activity. In most cases, the Trojan characteristic was simply that the software came disguised as a non-harmful file. Several people have even released so-called good worms, which find bad worms and fix the problems caused by those bad worms, but this is fighting fire with fire.
The media has not been shy about informing people of the dangers of e-mail. Many of the most popular viruses and worms of 2000 and 2001 got a fair bit of television coverage. These included the ILOVEYOU virus and the Code Red worm.
Malicious Software Solutions
In the end, it is up to each person to be aware of the dangers and to practice a few basic security measures to prevent being infected by a virus or spreading a worm. These malicious software programs are still growing in frequency and power. The following list represents some of the best practices that each person can follow to stay virus-free:
Do not open or forward e-mail attachments from untrusted sources— Also, you shouldn't open or forward ones that arrive unexpectedly.
Use antivirus software— AV software is discussed in Chapter 12, “Securing Your Standalone PC: Viruses, Chat, and Encryption.”
Learn your e-mail program's security features and exercise them— E-mail clients such as Outlook XP now prevent the execution of attachments by default.
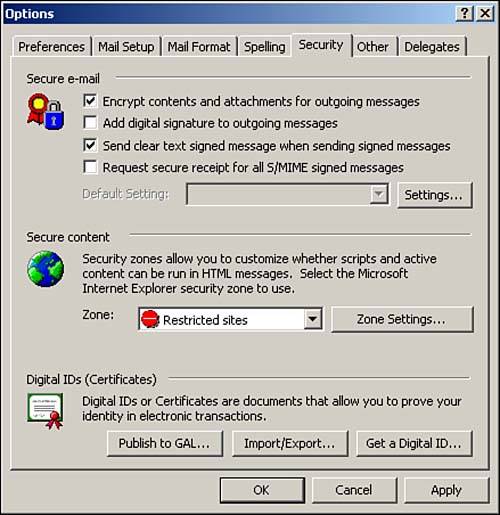
Disable processing of HTML in your e-mail client. Outlook XP processes HTML-enabled e-mail by default. However, it provides a means to minimize the risks. In Outlook XP, select Tools, Options and then select the Security tab. You see the dialog box shown in Figure 8.5. This dialog box presents you with the same zones that are used to configure security in Internet Explorer. Set the Zone to Restricted sites, and click Zone Settings to get more detailed with the configuration. Doing so applies strict security controls to e-mail that is composed in HTML. For instance, by default, Java and JavaScript content are disabled.
Figure 8.5. Outlook XP e-mail security options: Select Tools, Options, Security.
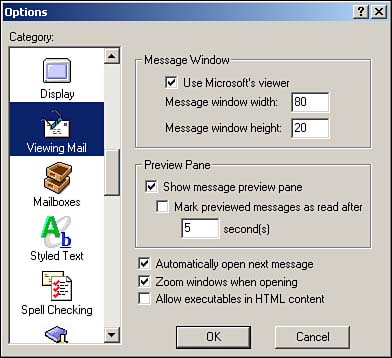
Eudora comes with HTML e-mail enabled by default. However, by default, it enhances security by disabling the processing of any active content such as Java, JavaScript, VBScript, and ActiveX controls. This is a configurable option displayed as Allow Executables in HTML Content, located under Tools, Options, Viewing Mail (see Figure 8.6). Be sure this check box is unchecked for tighter security.
Delete suspicious e-mail.
Keep your e-mail client software up to date and pay attention to security alerts— You can get the latest security news and updates for Eudora from http://www.eudora.com/security.html. The latest security alerts and patches for Outlook can be found at Microsoft's site (http://www.microsoft.com). Microsoft has a search engine for searching security vulnerabilities and patches for all Microsoft products. The search is done by product and version: http://www.microsoft.com/technet/treeview/default.asp?url=/technet/security/current.asp.
Figure 8.6. Eudora's options for securing HTML e-mail: Select Tools, Options, Viewing Mail.