Case Study: Online Identity Search
Debit and credit cards are currently the most convenient forms of purchase. Cybercash-type technologies have not yet made it into the mainstream of Internet technologies, although they eventually will. If all your bank account information is tied to a debit card, how easily can some malicious person gain that information? Let's break down what type of information the malicious attacker (for the rest of this book we will call him/her HackerX) needs to re-create your debit card information or gather every piece of information about you. The first piece of information used to track you down is your name. You might think this is the most important piece of information, but as we will see throughout the book, other information about you is even more important, and your name doesn't even factor into some methods of compromising your privacy.
So, HackerX uses your name to start finding out everything there is to know about you. Literally hundreds of online methods are available to find information about someone using her name. HackerX can be anyone trying to do this, from a credit card company checking your credit history to the system administrator who runs the computer network of your favorite online shopping site. It's pretty simple to gain all your pertinent information the old-fashioned way, by copying your credit card receipt at the checkout stand. However, the online world poses new forms of privacy risks that are far greater than a clerk simply copying your receipt.
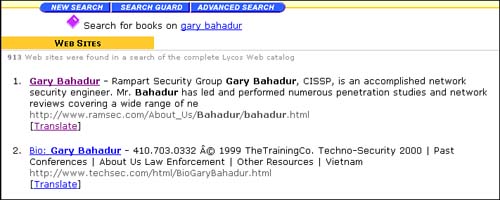
To find out more by using your name online, HackerX can use several person-oriented search engines as a start. These search engines are dedicated to finding all references about you in the online world. A quick search of www.whowhere.lycos.com for “Gary Bahadur” produces the results shown in Figure 1.4. It found 913 references, and the first 2 are a resume and a speaking engagement at a trade show. So, within a few seconds of starting a search, a short biography of Gary has been found, as well as information about where he will be at a certain date. The next piece of information that would be useful for HackerX to know is a phone number. Using the same Web site, HackerX can use the person's name to look up any phone numbers associated with him. HackerX has easily gotten a brief background and phone number of his victim. Using other sites such as Whitepages (http://www.whitepages.com) or US Search (http://www.ussearch.com), you can use a person's name or phone number to find out more information about him, such as his address.
Figure 1.4. Lycos result from searching for Gary Bahadur.
To make a purchase on the Internet using that person's identity, HackerX must have all relevant address and phone number information. Next, he must get the actual credit card information. If HackerX is a good hacker, he can easily break into the online shopping site where his victim is known to make purchases and steal that information from the online merchant's computer systems. As we have seen in repeated news stories, this is becoming a frequent occurrence. A perfect example of this type of hacking was done to CD Universe in January 2001. A hacker compromised credit card information and even posted that information on a Web site. A malicious hacker tried to extort money out of the company and captured thousands of credit card numbers. Using a combination of methods, a good hacker, or even just someone looking to garner information about you, can easily create a detailed profile of his intended victim.
The short case study is meant to underline the brief process of gathering your personal information. The rest of this book goes into detail of how this is actually done and what the consumer can do to prevent such information disclosure. Our everyday life in the online world submits personal data to various entities in numerous ways. Information such as where you are logging in from, phone calls made from your wireless phone, who you are sending e-mail to, what you are buying, and what your online habits are gets stored in databases throughout the Internet. Information does not go away in the online world; it just gets stored somewhere and waits to be found by the wrong person. Data mining, which is the search for information using different resources, uses numerous techniques to find all possible information about you that is floating around the online world.
