TCP/IP Addresses
The Transmission Control Protocol (TCP) and Internet Protocol (IP) were developed to enable computers to talk to each other over long-distance networks. IP is responsible for moving packets of data between nodes and systems, and TCP is responsible for verifying delivery from clients to servers. TCP/IP forms the basis of the Internet and is built into every common modern operating system (including all flavors of Unix, the Mac OS, and the latest versions of Windows). Every device connected to the Internet has an IP address associated with it. Think of an IP address as an unique identifier for every system connected to the Internet. IP addresses typically take the form of ###.###.###.###. An example is 192.168.1.100. Each one the of the four groups of numbers is a value between 0 and 255. This provides for numerous address that can be used by millions of computer systems.
Note
To determine the IP address of your machine, use the following commands:
| Operating System | Command |
|---|---|
| Windows 95 or 98 | winipcfg |
| Windows NT or 2000 | ipconfig |
| Unix-based systems | ifconfig |
For example, in Windows 95 or 98, from the Start menu, select the Run option. Within the Run dialog box, type the command winipcfg.
If you are running a Windows NT or 2000 machine, open a DOS window by selecting Start, Programs, Accessories, Command Prompt. Within the DOS window, type the command ipconfig. The results are shown in Figure 6.1. Our IP address in this case is 10.1.1.101.
Figure 6.1. Finding the IP address on a Windows NT/2000 machine with ipconfig.

In this example, our IP address is 10.1.1.101, which is on our internal network. When you run these same commands, whether in Windows 98/NT/2000 or Unix, you will most likely see a different address. The second set of numbers, 255.255.255.0, is called a subnet mask. The subnet mask gives the machine further information on how the network is configured. The third set of numbers, 10.1.1.1, is the default gateway, which is the device on which traffic goes in and out of your network. In a mini-network environment, this usually is your home firewall machine. If you are using just one system to connect via a dial-up connection, this gateway typically is your machine's IP address. If you are using a DSL or cable modem, it is your ISP's gateway machine. Without a gateway IP address, you can't send traffic into and out of your system to the Internet.
Static and Dynamic Addresses
When the home user employs a modem to connect to the Internet via his ISP, a dynamic address is typically assigned to the machine for the duration of the connection. “Always-on” and broadband (cable modem or DSL) also have an IP address assigned to them, which is either dynamic or static. As the names imply, static addresses do not change, whereas dynamic addresses typically change each time the machine connects.
ISPs are assigned blocks of IP addresses that can be used by their customers. Typically, large ISPs, companies, and institutions have many addresses assigned or available to them. On the other hand, smaller ISPs and organizations have a fewer number of addresses available to them. Because IP addresses are finite in number (meaning you can't just create new addresses), they must be conserved.
A way to conserve addresses to the assign them on an as-needed basis. This applies directly to modem dial-up access. When a user connects to his ISP via modem, the ISP assigns an IP address from an available pool. The IP address is then associated with the user while the connection remains active (the lease time). After the user disconnects, the IP address is “released” and returned to the pool of available addresses. The next dial-up user can then be assigned that same address. This scheme of assigning IP addresses is referred to as the Dynamic Host Configuration Protocol (DHCP). This enables the ISP to have more customers than IP addresses because the likelihood of all its customers dialing in at the same time is slim. DHCP is also used in many DSL and cable modem connections, as well as in corporate local area networks (LANs).
Static addresses, on the other hand, are directly configured on the machine itself. Statically addressed machines have the same IP address until they are specifically reconfigured to have a different address. Many cable modem companies assign you an IP address via DHCP, but after you get that address, it's in effect static. It does not change for months or even years. A home user with a cable modem connection typically can set up a Web server on a home machine with his theoretically static address and register that address when he registers a domain name. Then, he can have complete control over his home Web servers rather than hosting his personal Web page on his ISP's servers.
Even though DHCP can be used, that is not to say there is no record of who had a specific IP address at a specific point in time. ISPs normally keep logs of this type of information. In the early days, ISPs gave out this type of information without much hesitance; as long as the request seemed reasonable, the information was given out. That is no longer the case. This type of data is no longer available for the asking; however, it is available with the proper legal authorization (court orders, subpoenas, and so on) to entities such as the government or law enforcement. An example of this is law enforcement requesting this type of data to aid in an investigation. One thing to keep in mind, though, is that the disclosure of your data is governed by the service agreement you agreed to when registering with your ISP. This information is usually in a term of services document or privacy policy document. The release, or non-release, of your data should be clearly described by the ISP.
To determine additional DHCP information, open a DOS window by selecting Start, Programs, Accessories, Command Prompt and then typing ipconfig /all. You see something similar to Figure 6.2.
Figure 6.2. ipconfig /all output.
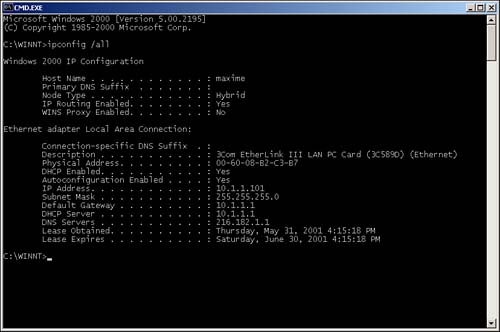
In this example, the command also gives you the address of the DHCP server and lease times associated with this address. Whenever an address is given out via DHCP, it is actually assigned with varying lease times. The lease times of DHCP addresses are configured by the network or system administrator.
So how do static and dynamic addresses affect your privacy on the Internet? Well, if you have the same address all the time (static), a definitive correlation or link can be made between you and your IP address. A static IP can be beneficial if you want to set up a Web server and domain name for home use. An address provided by your ISP is usually associated with a name, such as cco2-absha-home.com, so after you have a permanent address, you can register a domain name to that static IP address. When you set up your Web server, instead of using the given name of cco2-absha-home.com, in the browser, you could use www.privacydefended.com, for example, which is much easier for people to remember. The downside to having static addresses is that your system is always associated with that one IP address.
On the other hand, with dynamic addresses, you can't be sure of the linking between an IP address and a particular user. Each time you log on, your IP address can potentially be different. This makes setting up an easily accessible home Web server or network more difficult, but it also makes it harder for an attacker to track you down.
After a link can be made between IP address and user, there is an erosion of privacy. Web surfing and usage of data can then be correlated and linked to a specific person. (Chapter 7, “Understanding the Online Environment: Web Surfing and Online Payment Systems,” discusses cookies as a means of storing this type of data and this linkage of user and IP address.)
One of the easiest methods for a single Web site to monitor a particular user's surfing habits on that site is to search its Web server logs for traffic from a specific IP address. In the case of static addresses, the Web site will know that all traffic from that address comes from “User A.” Assuming the Web site operator has logging turned on, she can know exactly what User A clicked, at what time, and in what order. In the IIS Web server log shown in Figure 6.3, IP address 10.1.1.101 is surfing to Web server 10.1.1.103. Note the first two fields of each log entry: the date and time fields. Each Web page access can be tracked, and the time the user spent on that page can be determined. If it is an e-commerce site where the user has to enter sensitive information (name, address, credit card number, delivery instructions, and so on), a definitive link can be created. Now, imagine if that information is then passed along or even sold to another party.
Figure 6.3. Web server log file.
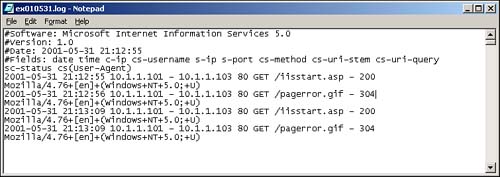
Often, a user's IP address is sent to a third party when a Web site is visited. This usually happens when banner ad networks are involved. The exact amount of information related to a specific IP address varies greatly depending on the specific IP address (static versus dynamic) and the specific pieces of data being logged.
Your ISP's Security
The ISP is a wellspring of valuable information. After all, it arguably contains your most private data: 1) the link between your screen name/username and your real identity; 2) your payment information (typically, credit card data); and 3) access to your e-mail if you are using the ISP's e-mail service. Such information is usually held in computers in an ISP's office. Many users also have their personal Web sites hosted by the ISP.
For the reasons listed previously, ISPs have become a frequent target of hackers. Therefore, the security over the ISP's systems is just as important as, if not more important than, that of the individual's machine. An ISP should provide a secure location for its devices and machines, establish policies about confidentiality of customers' e-mails, and not use customer information for any other purposes. Internal threats are usually the most frequent sources of information compromise. ISPs should be privacy-aware and strive to offer privacy-enhancing capabilities to their customers. Some ISPs provide the store-and-forward function of data traffic and connectivity to the Internet, such as AT&T's Worldnet Service, whereas others such as AOL provide content and applications for consumers to use. The confidentiality of data or content contained in Web pages hosted by the ISP for its customers or e-mails in-transit is usually not the responsibility of the ISP. If you as the end user have taken all the appropriate steps to secure your systems, there might still be an element of exposure from the ISP if its systems are vulnerable.
When you evaluate the services of an ISP, consider its capability to secure itself. Frequently, that's easier said than done. ISPs are naturally reluctant to discuss their security breaches, so you'll have to rely on reputation and recommendations. Generically speaking, larger, more established ISPs have better security. That is not to say, though, that they will not experience security breaches, but they typically have more resources available to aid in the prevention and detection of such occurrences. They also might have more resources to devote to putting security policies and systems into effect. Smaller, mom-and-pop ISPs might not always have these resources available to them (for example, dedicated security staffs). On the other hand, the larger ISPs make for more attractive targets. However, regardless of the ISP chosen, it is important to at least note that a potential exposure point exists at the ISP level.

