Security Testing Procedures
Security testing should follow a logical progression. The first thing to remember is that you can only conduct testing against your own site. If you start trying to break into other sites to test their security measures, you become a hacker and break the law, even if you mean no harm. Before you proceed, be sure you know exactly what your IP address is and only conduct your tests against that IP address.
The basic steps you need to take to conduct a security test of your environment include discovery, enumeration, vulnerability mapping, password cracking, and exploitation. We will go through the first four steps and leave a detailed discussion of exploitation to another book. Exploitation of vulnerabilities usually requires in-depth knowledge. Tools are available to tell you if a site is potentially vulnerable, but it is up to you to actively break into the site by taking advantage of that vulnerability. Our goal is to help you secure your site, not create a whole group of script kiddies who can just use tools without understanding what they do.
Discovery
The first step is discovering your site as a hacker would. This step is called footprinting. An attacker can find out the ISP that owns your IP address. He can find out the routes to your system and find out what the upstream routers are that protect you. An ISP typically owns and operates these. We went through how an attacker can find out information about you personally; he can find information about your system in the same way. The discovery phase is more relevant to attackers who are trying to find out as much information as possible about a company. For your home network, it's pretty simple to just ping your IP address and find out if you system is alive, or port scan the system to find services. When an attacker goes after a company such as Foundstone, he has to track down numerous network blocks and addresses, find subsidiaries that might have connections into the company, and spend a great deal of time and effort. This is not necessary for your home network in most cases.
If a hacker were to perform a full discovery of your IP address, he would identify domain names and associated networks of the target. In the case of large organizations, this can take hours. If the hacker is targeting a home user, finding the ISP takes a matter of minutes. A whois query is performed to identify your ISP's network (and therefore, you). After finding the ISP information, querying their DNS servers can glean more information. This isn't important in hacking home users unless that attacker wants to hack the ISP and then use that connectivity to hack the home user.
To begin discovery, the owner of the network is first discovered. Pretending we are the attacker, we see that our own IP address from our cable modem provider is 24.7.48.68. Taking this IP address and plugging it into Arin (http://whois.arin.net/whois/index.html), we discover the whole range of addresses that our ISP owns, as shown in Figure 13.21.
Figure 13.21. ARIN whois information.
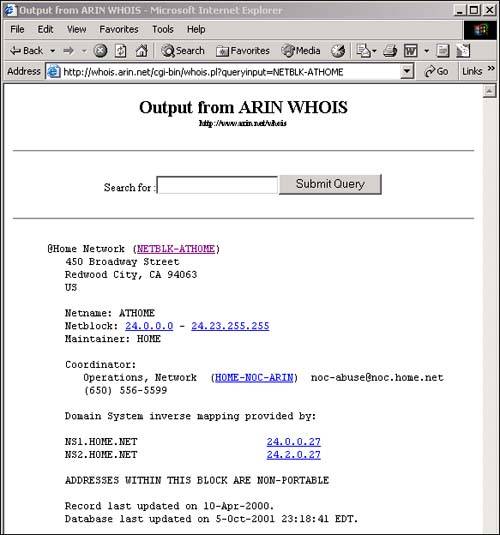
From this information, we see that @Home Network owns the network block to which our IP address belongs. The first step is accomplished; the attacker has a block of addresses to target and discover if anyone is alive. The attacker knows we are on an @Home network.
Enumeration
After specific domain names, networks, and systems have been identified through discovery, an attacker then gains as much information as possible about each one. Your IP address is within the range that the ISP owns. When doing your own testing, you don't have to worry about other IP addresses.
The key difference between discovery and enumeration is the level of intrusiveness. Enumeration involves actively trying to obtain usernames, network share information, and application version information of running services (such as IIS 4.0, Apache 1.3.X, BIND 8.2.1). This information is obtainable by connecting to the various open ports and extracting data through mechanisms such as anonymous connections and banner grabbing. For example, you can glean an inordinate amount of information from an unsecured Windows NT/2000 system just by using a null session (also called an anonymous connection). You can perform this manually or with tools. In addition, usernames can be gleaned from many systems and used during the exploitation phase to circumvent security barriers if login prompts are available.
When you are ready to enumerate the service running, you have to identify each service running to map it back to vulnerability in the next section. When each live system is identified, the attacker then identifies each service running on the target system. A machine cannot be hacked unless it has a vulnerable service running. This scanning gathers operating system, service, and banner information. When each service is identified, the attacker can begin the exploitation.
To determine what ports you have open, we can use SuperScan as we have done before. A possible 65,535 TCP ports can be open. A port allows connection to the system. Different software runs on different ports. Software can also run on UDP ports, but these are not as dangerous as TCP open ports. We need to check all open ports. To test your system for open TCP ports, scan it with SuperScan, as shown in Figure 13.22 (use your IP address, not ours).
Figure 13.22. Open ports on IP address 24.7.48.68.

In Figure 13.22, we see several ports open: 21, 80, 135, 139, 443, 1025, and 1113. These ports are open with no firewall filters in place. Port 139 is dangerous in a Windows system. Much information can be retrieved from a Windows system using these ports, such as user accounts and system configuration information. An attacker will jump at the chance to pillage information from your system with these open ports. These ports allow a null session connection to be made to the system. All these open ports make the computer vulnerable from remote and local network attacks. If an attacker were to get to a machine within the local network, such as the Office PC in Figure 13.1, the attacker could compromise the system. As we discussed in Chapter 10, you can lock down the operating system better. An additional tool that is not built into the Windows operating system is the Microsoft Personal Security Advisor (http://www.microsoft.com/technet/mpsa). It can check your operating system settings for weaknesses, as shown in Figure 13.23.
Figure 13.23. Microsoft Personal Security Advisor.

With SuperScan, we checked open TCP ports. We can check for open UDP ports with another product, such as AW Security Port Scanner (www.atelierweb.com), as shown in Figure 13.24. We see a number of open UDP ports that also need to be restricted.
Figure 13.24. UDP port scan results.
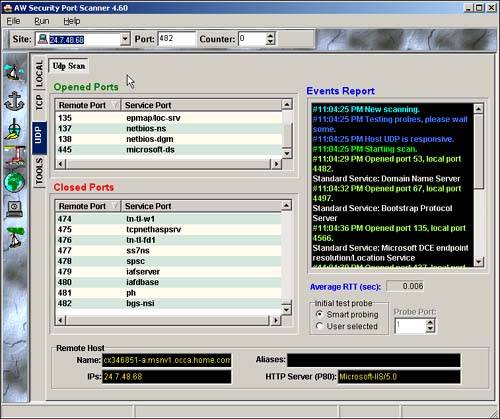
When you see open ports on your system such as these, you have to look at the rules set in your firewall. Having too many open ports or extremely dangerous ports open can indicate that your filter rules are not correctly set. When we turn on the rules shown in Table 13.1, we see the results of another port scan in Figure 13.25.
Figure 13.25. Port scan result with firewall rules enabled.

As we can see, the firewall rules we have implemented restrict access to the system and we see only one open port, 80 (Web). An attacker would see this port, and attacks would be restricted to the only open port available. Dropping ICMP packets will even hide your system from a typical port scan; if a system cannot be pinged (ping will tell you easily if the system is alive), the attacker would most likely not investigate an IP address, which has no response to ping. You would be invisible to most casual investigations by attackers.
If you do not want to run SuperScan or another port scanner against your Internet site, you can use a well-known site on the Internet to perform a port scan of your site. At Gibson Research Center's Shield Up site (http://www.grc.com), you can have Steve Gibsons' site port scan your site. Results of a port scan of our Internet connection, with firewall rules, are shown in Figure 13.26. By watching our firewall log output, we saw that only certain ports were tested. Be careful when using such sites; you want to check every port possible to see if anything is running, not just popular ports such as mail (25), Web (80) and FTP (21).
Figure 13.26. Gibson Research Center port probe.

Vulnerability Mapping
All the information in footprint analysis leads to specific targets with services running that might be vulnerable. If you were an attacker, you now have a detailed list of all devices that are alive and running services that are available. A smart attacker will look for specific vulnerabilities in the running services. The script kiddies will just launch vulnerability scanner programs against a range of IP addresses and hope for some results. With the sophistication of available tools, this shotgun approach will usually have some results. The attacker then launches attacks against the systems. You have to think the same way the attacker does. You must examine the open ports and vulnerabilities associated and lock down the ports that can be a problem.
The vulnerability mapping results in the following:
Host name and IP address
Services running on the system (that is, Microsoft IIS, MS SQL Server, FTP)
Version of each service running
Vulnerabilities associated with each service
In Figure 13.25, we saw that the Web port was open. Even with filter rules in place, as shown in Table 13.1, we can still test the security of the Web server because the Web port is open and traffic can be sent to the Web server. An attacker can use many Web security testing tools against your site when he sees a Web port open. One such program is Stealth HTTP Scanner (www.nstalker.com), shown in Figure 13.27. Running a security testing tool such as Stealth against your Web site alerts you to possible holes in your Web server.
Figure 13.27. Web site security scan results.

Many home users run Web servers for various reasons. The problem that most people and companies face is that Web server security is not ingrained into the network design. The operating system has been the focus of security for so many years, and now we are seeing more application-level attacks. If the only port open on a network is 80, the attacker is forced to attack the Web application. A number of recent worms have specifically targeted Microsoft IIS Web server because, in many sites, that is the only source of attack.
Many programs in addition to Stealth can be used to test security. Microsoft has provided many of them on their Web site to assist with operating system and Web server security. Two such tools include the IIS Lockdown Tool (http://www.microsoft.com/technet/security/tools/locktool.asp) that allows you to configure an IIS 4.0 or 5.0 Web server securely, and URLScan (http://www.microsoft.com/technet/security/urlscan.asp) that only allows traffic that complies to a specified rule set. Further information such as IIS 4 and IIS 5 security checklists can be found on the Microsoft site at www.microsoft.com/technet/security.
It's easier than ever to learn how to hack and find programs that assist in compromising a system. There are those who write good programs that are used for hacking, and there are programs made for hacking. Some of the most popular sites for security resources include the following:
Packetstorm— http://packetstormsecurity.org
Securityfocus— http://www.securityfocus.com
Technotronic— http://www.technotronic.com
Another program we can use that is free is LANguard (www.gfisoftware.com). This freeware program does a good job of performing simple checking against running services and open ports on the target system. Figure 13.28 shows the output of a LANguard scan against our system.
Figure 13.28. LANguard output of system security scan.

Because we are not hackers and don't need to be stealthy, we can use these types of programs even though they generate a log of file information, as shown in Figure 13.29. All the attacks against the firewall can be logged and reviewed.
Figure 13.29. Log file output of LANguard security testing.

You can use numerous freeware and for-profit software programs to test your site security. Just perform a basic search for “network security,” and any search engine will show you hundreds of sites.
Password Cracking
A key step you should take to test the security of your network is to see how strong your password is on all your servers. Password cracking is really aimed at Unix and Windows NT/2000/XP. We mentioned using the programs Glide and Cain in Chapter 6, “Understanding the Online Environment: Addresses, Domains, and Anonymity,” to crack Windows 9x passwords. To test the security of your Windows NT/2000/XP password, one well-known tool you can use is called L0phtcrack (LC3) (www.atstake.com), shown in Figure 13.30.
Figure 13.30. Password cracking.

In this password cracking output, we see that several passwords have been cracked (kraa = SECURITY, littlebilly = CHILDREN, www = INTERNET). We can see that two of the passwords are less than eight characters, and several passwords were not cracked. L0phtcrack can use a dictionary, the characters on the keyboard, or both to attempt to guess passwords.
In Windows NT/2000, the password is broken up into two sets of passwords, each seven characters long. Therefore, if you have a 10-character password, you in essence have two passwords—one of seven characters and the other of three characters. It is easy to crack a three character password. For example, if your password ended in the characters 123, L0phtcrack would easily guess this password. In Windows, a 7-character password is stronger than a 10-character password.
Weak passwords are the bane of just about every company and most user home systems. Brute force attacks (where the attacker just tries to guess usernames and passwords) are the most typical method of gaining entry to a system. If you can ensure that you have no weak passwords, you will eliminate half your system security weakness. A strong password uses special characters, numbers, and letters.
Exploitation
The exploitation phase begins after the target system's vulnerabilities are mapped. If you were an attacker, you would attempt to gain privileged access to a target system by exploiting the identified vulnerabilities. This might take the form of launching a password guessing attack using usernames collected during the enumeration phase or using exploit code targeted against the specific service running. Regardless of the method used, the goals of the test are user-level and privileged access. Because this is your own system, you just have to identify the vulnerabilities and patch them or enable rules to protect open ports rather than exploit the vulnerabilities. You are not a hacker, so don't start using this penetration methodology to attack your neighbors.
