IPSec
You will also see the “IP Security Policies” section in your Local Security Policy. IPSec is an advanced topic that requires knowledge of some important networking and security concepts. In brief, the IPSec standards are newly built into the Windows 2000 and Windows XP operating systems. Although TCP/IP filtering on the network adapter is one method of restricting port access, it can be cumbersome and difficult to manage because you have to enable all ports that you want to use. TCP/IP filtering does not scale well to ranges of ports that are needed, and it can be difficult to understand.
IPSec is a combination of protocol standards that protect IP communications between two computers. You know that TCP/IP is the language that computers use to communicate with each other across the Internet. TCP/IP is an old set of protocols that was never prepared to deal with all of the evildoers on the Internet. It is inherently insecure and easily taken advantage of by attackers and criminals.
IPSec is a new set of standards that is just starting to be implemented in computers across the Internet. It has been widely tested and proven secure, gaining industry-wide respect. IPSec provides three important security protections to communications between computers:
Confidentiality— Communication is encrypted so that third parties cannot intercept and read the data being transferred.
Authentication— Communicating computers authenticate with each other to prove their identities. This way, you can be sure that you are talking to the right computer, and not some hijacked host.
Integrity— Communications are protected packet by packet. If one packet is tampered with while in transit, the system is alerted and the packet is dropped.
To set up IPSec policies, select Start, Settings, Control Panel, Administrative Tools, Local Security Settings, IPSec Policy on Local Machine. Select Action, Create IP Security Policy. Give the policy a descriptive name for what you want to do and walk through the wizard, selecting the default options. When you reach the Rules tab, shown in Figure 10.34, you can set up filtering rules.
Figure 10.34. IPSec Rules tab.

You can then add a rule. Select the defaults, including applying the rule to all network connections. Two existing policies exist: All ICMP Traffic and All IP Traffic. You will see these when you start to create an IPSec rule. These are too broad for our needs, so we need to add specific rules. Click Add to create a name for your filter. In this case, we will name it Net Filter, as shown in Figure 10.35.
Figure 10.35. New filter rule.

At this screen, we then click Add. In the Source Port field, we select Any IP Address, and in the Destination Port field, we select My IP Address. The Protocol Type is TCP, and the To This Port option is set to 139. When this is complete, edit the new filter by double-clicking it and then clearing the Mirrored check box. What we have just done is set up filters that will block anyone (Any IP Address) on the Internet from connecting to port 139 on our machine (My IP Address). We will then redo this process to filter out ports 445, 137, and 138 for TCP and 139 and 445 for UDP. These ports are default Windows ports that can be used to retrieve information about your system and attempt connections to your system over the Internet. When complete, our filter rule should look like Figure 10.36.
Figure 10.36. Filter rule.
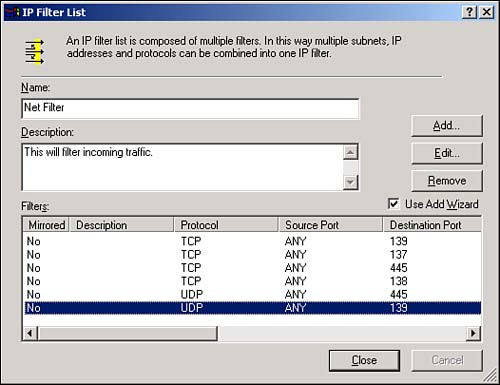
When you have finished the filter list, click Close. Then select the filter you created and click Next. This will get you to the filter action screen. By default, you cannot block traffic, so click Add, and then click Next on the first page. Type a name (Block), and click Next. The action you want to select on the next page is Block. Click Next and then Finish. When your action is defined, click Finish. After you associate the Block action with your Net Filter, you will have enabled your filter, as shown in Figure 10.37.
Figure 10.37. Enabled filtering rule.

IPSec can be granular and robust, but it is easy to set up filters incorrectly. Like corporate system administrators who implement expensive firewalls incorrectly, you can make the same mistakes inadvertently and allow an intruder to bypass your filtering rules. If you want to learn more about IPSec and the security services it can provide, start by reading the documentation that Microsoft has provided in the help files. Be prepared for a head spinning blast of information.
After you have installed your Windows operating system, you should put together a checklist of security measures you need to take to secure it and keep it secure. Table 10.6 is a good start to follow in creating your security checklist.
| Step | Windows 95/98 | Windows NT | Windows 2000 |
|---|---|---|---|
| Address physical security concerns. | X | X | X |
| Use a BIOS or bootup password. | X | X | X |
| Perform backups and secure media properly. | X | X | X |
| Apply Windows updates (windowsupdate.Microsoft.com). | X | X | X |
| Disable file and print sharing. | X | ||
| Use user and group accounts. | X | X | X |
| Use Policy Editor to enforce password security. | X | ||
| Password-protect the screensaver. | X | X | X |
| Set audit policy. | X | X | |
| Set password characteristics. | X | X | |
| Set security for sensitive files and shares (NTFS permissions). | X | X | |
| Set Registry keys. | X | X | |
| Use the Encrypting File System (EFS). | X | ||
| Disable unnecessary services, applications, utilities, and programs (IIS, FTP, SMTP, and so on). | X | X | X |
| Use virus scanning software and keep it up-to-date. | X | X | X |
| Run hfnetchk.exe on a regular basis to see if machine is up-to-date on patches. | X | X | |
| Use local security settings to enforce password restrictions. | X | X | |
| Use NTFS for disk volumes. | X | X |
