Spoofing and Spamming
Spoofing and spamming are two completely separate e-mail phenomena. When someone spoofs an e-mail message, he is making it appear to be coming from an e-mail address that you trust. For example, I can send you an e-mail message that looks like it was sent by [email protected]. You would probably not even question the authenticity of this e-mail message; you would trust it just as if it were your mother who sent it. By masquerading as a trusted person, I can trick you into giving out sensitive information. This tactic is similar to when somebody calls you up under a disguised voice, trying to trick you into saying or doing something. People do not commonly question the authenticity of an e-mail message. Most people see the e-mail address that its from and assume that person really composed the message.
The problem is that it takes little skill for someone to forge an e-mail message. I can make any e-mail message look like it is coming from an e-mail address of my choice. The only real way to defend against spoofing is to use digital signatures. (These are discussed in more detail in Chapter 9, “Securing Digital Transactions or SSL and Digital Certification.”)
Authenticity of an e-mail message is only secured in one real way. By digitally signing an e-mail message using PGP or some other digital certificate, a person is sealing the message and providing a level of assurance that he is the one who sent it. Digital signatures prove almost beyond a doubt that the e-mail message is authentic and from the person it appears to be from. If someone tampers with a signed message and tries to forge its contents, the signature becomes invalid and the recipient is notified.
Authenticity is not a new problem to the Web or to e-mail. Knowing that information is truly coming from the expected source is a problem that has largely been solved. PGP has provided a means for proving authenticity in e-mail messages and allowing you to identify spoofed, or forged, messages.
Spam is the junk e-mail you get. Spam is also known as unsolicited e-mail because it comes unwanted and unexpected. However, most spam is commercial in nature, bringing a sales pitch or other advertising propaganda. For this reason, spam is most commonly used to refer to unsolicited commercial e-mail (UCE). However, many people consider unsolicited mail of any content, sent by itself or in bulk, to contribute to the overall spam problem. Spam can come as an e-mail advertisement for a low-cost Web site development company, a flame war between two people on your same mailing list, or a chain letter reminding you to spread peace on Earth.
People get spammed because their e-mail address has been “harvested” (collected). It happens if someone surfs the World Wide Web and accesses as many newsgroups as he can to collect every e-mail address he comes across. If he is smart, he might create an automated program that will do this for him. Indeed, such programs exist; some call them Web bots, and their job is to find and collect as many e-mail addresses as possible.
If you want to avoid spam, you have to be selective about when you use your e-mail address and where you give it out. You shouldn't put your e-mail address in every message board and newsgroup posting, or on every Web site you visit. Purists will tell you that you shouldn't even put your e-mail address on your own personal Web site, at least not in obvious form. To avoid acquiring more spam over the course of your online lifetime, be conscious about where you use your e-mail address, and consider the following guidelines:
Keep two separate e-mail accounts— Keep a public e-mail address and a private one. Use the private address for communications between people close to you, and never post it online. Use the public e-mail address for other communications, and be prepared to receive a lot of spam mail for the account.
Use your public e-mail address for public postings— When building your personal Web site or participating in newsgroups, message boards, or chat rooms, use your public e-mail address. You can expect that no matter where you display your e-mail address online, it is just a matter of time before the e-mail harvesters get it.
Never respond to spam, and never visit hyperlinks that a spam message might contain— Most spam today comes as HTML-enabled e-mail, and many e-mail clients will launch the HTML code unless you have this option disabled. When image hyperlinks are launched in HTML code, a message might be sent to the spammer indicating that you read the e-mail message and that your e-mail address is valid. When you respond to a spam message, you are also telling the spammer that your e-mail address is valid. Valid e-mail addresses are valuable to spammers, who collect many bogus e-mail addresses through their harvesting techniques. A collection of valid e-mail addresses is more valuable than bogus ones.
Use third-party spam filters or ones built into your e-mail client— Spam filters are designed to catch the junk or spam mail and automatically move or delete it. Although the filters are not 100% effective, they can manage to cut down on the majority of spam that you get.
By following the first three tips, you can minimize the amount of spam you receive. Spam filters, on the other hand, are designed to help you deal with the spam that you do get.
Spam Filtering
Most e-mail clients today, including Outlook and Eudora, have robust spam filtering capabilities. They provide the ability to filter e-mail messages based on e-mail address, subject, keywords in the body, and more. Some ISPs even provide filtering for their customers. By using the granular level of filtering provided in these e-mail clients, you can manage the majority of your spam mail by automatically deleting it or by moving it to a junk-mail folder.
In Outlook XP, you can get to the spam filter by selecting Tools, Organize. This brings up the window shown in Figure 8.1 from which you can set up a rule for the e-mail message you have selected. Similar features can be found in Outlook Express by selecting Tools, Message Rules, Mail.
Figure 8.1. By selecting Tools, Organize in Outlook, you can control your spam mail.
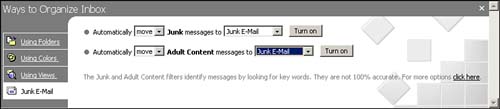
Outlook also gives you detailed control of your messages. If you cannot do what you want with the Organize Wizard, try selecting Tools, Rules. This is where you can find the most detailed control of e-mail, in an easy-to-follow display, similar to Figure 8.2. These filters are designed to help you fully control how your e-mail is handled. You can define filters to search for curse words in the subject or body of a message and automatically move the message to a specified folder. You can also define filters to search for messages that appear to be junk mail, and automatically move them to a folder for review or delete them. The purpose of these filters is to let you control spam and your e-mail in general.
Figure 8.2. The Outlook Rules Wizard gives you comprehensive control over your e-mail.

In Eudora, you also have detailed control over your e-mail filters. By selecting Special, Make Filter, you can see a quick and easy-to-use screen for setting up a filter, as shown in Figure 8.3.
Figure 8.3. Eudora provides an easy method of making filters to control e-mail.

The filter defined in Figure 8.3 says to find incoming mail from [email protected] and automatically delete the message.
When you are ready for maximum control over your filters, select Tools, Filters to make modifications. Eudora gives you a central place for managing the filters, with control over what is filtered (that is, e-mail address, keywords in subject or body, and so on), and what actions to take when an e-mail message matches a filter. For example, you can choose to automatically delete, play a sound, or move to another folder when a message matches a filter, as shown in Figure 8.4.
Figure 8.4. Eudora provides a more advanced method of controlling e-mail when you select Tools, Filters.

The slightly more advanced filter shown in Figure 8.4 tells Eudora to find incoming mail where either the sender's e-mail address is [email protected], or the subject contains the words “get rich.” When Eudora finds a matching e-mail, it transfers it to the trash.
With the options available under Tools, Filters, you can control your e-mail in more ways than you ever thought possible.
Spam filters can also be set up on e-mail servers and at network gateways. System administrators can set the same filters to block spam before it ever reaches their mail servers. They can also set filters directly on the mail server to reject spam that comes to it.
Many of the online, Web-based e-mail systems such as Yahoo! Mail and Hotmail also offer spam filters. Many of these online e-mail services, including HushMail and LokMail, block spam before it ever arrives at your mailbox, leaving you with little to worry about. Look through the documentation and help files for your e-mail client of choice to figure out just what its options are for e-mail filters and spam control.
For more information on spam, visit http://www.spamfree.org, http://www.cauce.org/, and the Network Abuse Clearinghouse at http://www.abuse.net/.
