Privacy and Instant Messaging
Instant messaging (IM) enables users to send messages to each other in near–real-time. IM is typically used while online on computers, but it is also sometimes used on other wireless devices, such as PDAs and cell phones. Even though each brand and version of IM software offers unique features, the basic premise—online chat—remains the same. These applications enable the user to set up lists of people with whom they chat, also known as buddy lists. When you log in to your IM software, your machine contacts the central server and checks to see which of your buddies are online. You can chat with multiple people at one time.
Instant messaging (IM) has grown significantly over the past several years. It has been spreading informally through networks of friends and colleagues. After one user is signed up with the service, he convinces and persuades other potential users to do the same. Not only have teenagers adopted this form of quick communication, but employees have also increased use of this technology in the businesses realm (although IM usually doesn't have an organization's IT group's approval or support). Employees have adopted this as an alternative form of communication with colleagues, vendors, and other parties. The immediacy and ease of use has helped the popularity and acceptance of this technology as a new form of communication.
The market leader for IM is America Online (AOL), which controls the top three IM clients: ICQ, AOL's native instant messaging, and its AOL Instant Messenger (AIM), which comes bundled with software such as Netscape's browser. Microsoft's MSN Messenger is second in terms of IM, and a number of others fill out the rest of the pie chart. In the next section, we'll take a look at these various IM clients and review the different configuration options that you can set when using this software.
As with the case of almost all types of technologies, the benefits of IM arrive with privacy and security risks. The problem with this technology is that it is inherently insecure. In the early days of IM, the software itself was vulnerable to several cracks and exploits. The latest versions of IM software have addressed many of the software programming problems, but plenty of security issues still exist. We'll now take a look at these various security issues and see how they can be addressed in AOL Instant Messaging, Microsoft MSN Messenger, ICQ, and Yahoo! Messenger. We will be looking at always-on broadcasting, leakage of personal information, IM logging, and clear text protocol.
Always-On Broadcasting
One thing that comes on by default on IM software settings is the “I am logged on!” broadcasting function. This is pretty ironic given the fact that users have taken steps to secure and “hide” their machine (not responding to pings is one example we discussed in an earlier chapter). IM software does the opposite—it is ready to answer with the “I am logged in!” type of message for anyone who asks. When this feature is turned on, people can learn more about you, such as your IP address and when you are logged in. It is as if people can check a bulletin board to see whether you are on your computer and see where you are (your IP address). Coupled with profile-type information supplied by many users, this can lead to a loss of personal information.
In AIM, this broadcasting feature can be configured by selecting My AIM, Edit Options, Edit Profiles. Then select the Privacy category option to get to the configuration window shown in Figure 12.1.
Figure 12.1. AIM privacy configuration.
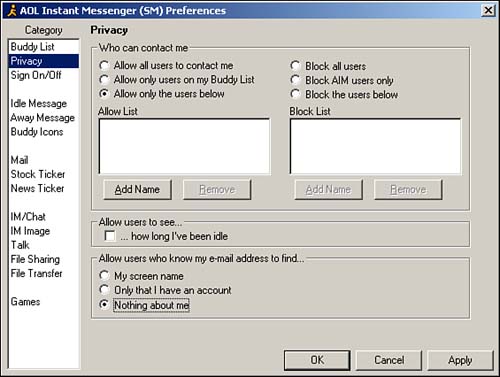
You can set options for who can contact you, prevent other users from seeing how long you've been logged on, and control how much another user can find out about you if he knows your e-mail ID.
In MSN Messenger, you can configure the privacy feature by selecting Tools, Options and selecting the Privacy tab, as shown in Figure 12.2.
Figure 12.2. MSN Messenger privacy settings.

MSN Messenger enables you to control who can see your online status and also allows you to view the list of users who have you on their contact (buddy) lists.
In ICQ, you can control the privacy feature by right-clicking the ICQ icon in the system tray and selecting the Status option. Your choices will be Available/Connect, Free for Chat, Away, N/A (Extended Away), Occupied (Urgent Msgs), DND (Do Not Disturb), Privacy (Invisible), and Offline/Disconnect. The recommend option for remaining stealthy is Privacy.
You can choose additional settings by opening the ICQ panel and clicking Security and Privacy. A security configuration window appears, as shown in Figure 12.3. It has various tabs available for indicating status to other users. By going to the Invisible and Visible tabs, you can control your ICQ visibility to other online users.
Figure 12.3. ICQ security and privacy.

You also can configure Yahoo! Messenger to show you as “invisible.” Select Login, Preferences and then choose the General category, as shown in Figure 12.4. At the bottom of the window, check the Login as Invisible (Others Cannot See Me Online) option. Selecting the Privacy category, shown in Figure 12.5, also allows you to set additional options. You can choose to ignore instant messages from people who do not appear on your list and not allow users to see you online and contact you when they see your ID on Yahoo! sites. You also can select Invisible mode by selecting Login, Change My Status. That setting allows you to appear invisible to other users and to set additional Privacy options.
Figure 12.4. Yahoo! Messenger General options.

Figure 12.5. Yahoo! Messenger Privacy options.
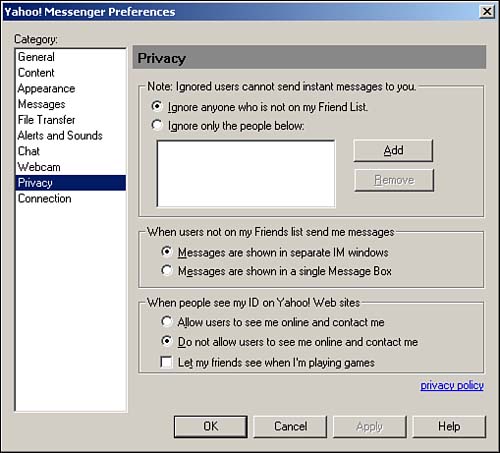
Releasing Personal Information
Every IM client enables you to complete a profile for your IM identity. It enables you to specify varying types of demographic information (age, sex, address, contact) and data on interests and hobbies. You can choose to release as little or as much information as you feel comfortable with. We recommend giving out as little information as possible.
AIM has pretty strong capabilities to prevent other users from seeing profile data. As you begin to edit your profile, it displays a warning reminding you that the data you input is not private and can be seen by all AIM members, as shown in Figure 12.6. You can also control whether users can search for you and if you are available for chatting, as shown in Figures 12.7 and 12.8.
Figure 12.6. IM warning message about member profiles.

Figure 12.7. Privacy profile in AIM.

Figure 12.8. Chatting preferences in AIM.

MSN Messenger enables you to configure your Profile information by making updates on its Member Directory Web page. By selecting Tools, Options and clicking the Edit Profile button, you are brought to a Web site where you can control what information is released to the public, as shown in Figure 12.9. Note that all information is optional. Once again, use your judgment, but realize that less information is better.
Figure 12.9. Editing your MSN optional profile.

The setting of ICQ profile information is also purely voluntary, and even warns you with a message shown in Figure 12.10. By selecting View, Change My Details, a window appears allowing you to contribute information—everything from your interests and hobbies all the way to submitting a picture of yourself, as shown in Figure 12.11. Once again, the information you submit is purely voluntary; like AIM, ICQ provides you with a gentle reminder that information is viewable by others. Enter information as you feel appropriate.
Figure 12.10. Information warning message.

Figure 12.11. ICQ user profile.

Much like MSN Messenger service, Yahoo! allows you to update your profile information by visiting a Web site. By selecting Login, Account Info, you are brought to a Web site where you can edit your information as well as select whether other Yahoo! users see your online status, as shown in Figure 12.12.
Figure 12.12. Yahoo! Messenger online profile.

IM Logging
Log files save the contents of IM discussions, including sensitive, private ones. This content is only as secure as the PC on which it resides. In one case, thousands of confidential messages from IM logs were posted to the Internet. IM communications between the CEO of an Internet company and his top executives were all posted on the Web. In this case, the logging feature of ICQ worked as designed, storing all incoming and outgoing messages in a log on the machine. That machine was apparently compromised and the bandits made off with the log. This feature is not shared by the MSN Messenger service, Yahoo! Messenger, or AOL Instant Messenger (AIM) for Windows. AIM for Macs have this feature as well, but it is turned off by default.
You can access the ICQ log by clicking the ICQ button (the MyICQ button in ICQ 2000) and selecting Message Archive. From this window, shown in Figure 12.13, you can delete individual messages and URLs. If you want to disable this logging altogether, click the ICQ button and choose Preferences & Security, Preferences. Click the Accept tab. At the bottom of the window, check the box labeled Do Not Log Event History. Future messages will not be logged. (In ICQ 2000, select Preferences, Events, General to find the Do Not Log Event History check box, as shown in Figure 12.14.)
Figure 12.13. Deleting messages in the ICQ message archive.
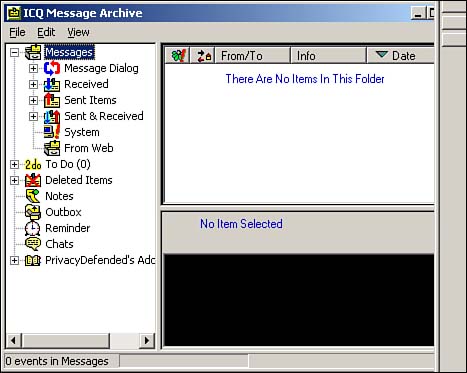
Figure 12.14. Disabling ICQ event logging.

Centralized Logging
Your PC is not the only place where message logs are kept. Most common IM applications send data through a central server where all communications are recorded and stored. The messages remain there until logs are purged or maybe even until an attacker steals them. These logs can also be subpoenaed by law enforcement. This was the case during the investigation of the World Trade Center attacks of September 11, 2001. The FBI approached AOL and Mindspring for their IM and e-mail logs during its investigation. Being cooperative, AOL handed the FBI AIM log files for the several days surrounding the events.
Yahoo! Messenger has logging off by default. You can check its current configuration by selecting Login, Preferences, Messages. Make sure that the Enable Archiving box is not checked. If you do decide to archive messages and chat, you can also configure the expiration period for messages.
Clear Text Protocol
Because the majority of instant messages are sent over a public network without encryption (cleartext), it is easy for someone using a sniffer to eavesdrop on the chat in real time. Some of these IM packages also allow for file sharing, and as such, viruses like Trojan horses and worms can be readily sent and spread. All information being exchanged via IM clients travels over public networks and is relatively easy to intercept. Because the IM protocol uses a specific port and is constructed in a specific way, sniffers can be programmed to eavesdrop on this type of communication.
Even the ICQ and AIM user agreements tell users not to use their applications for anything that is sensitive or mission-critical. MSN Messenger hasn't had the same security problems, but it is subject to its own liabilities. MSN Messenger relies on the Passport protocol for authentication, and it has had problems in the past. It is subject to compromise if a user's password is disclosed. In summary, all major IM software carries security risks, and they must be used with the appropriate security and privacy considerations. IM was never intended to be a form of secure communication.
Secure IM
Because the demand for IM has been large and because its security weaknesses are well established, a couple of startup organizations are developing secure instant messaging solutions. Startups like Bantu, Ikimbo, FaceTime Communications, Jabber, Mercury Prime, Odigo, QuickSilver Messenger, WiredRed, and 2way have raised millions of dollars in venture capital in the pursuit of a secure IM solution. Most of the companies listed are really developing IM applications for businesses rather than the home or casual user. At this time, this crowded field has no clear leader. One problem facing many of the new products is that the existing products are so popular that new products, even better ones, have trouble being accepted. After an installed base of users exists for a particular product, getting people to switch is difficult.
