Points of Disclosure
The points of privacy compromised increase as technology moves ahead. Traditionally, you gave your personal information only to sources such as banks, stores where you made credit card purchases, car dealers where you needed financing, and other such hardcopy/brick-and-mortar sources. Controlling and tracking how you gave away your information was easier because the backend technologies were not in place to share your information with the rest of the world. However, the advent of the Internet—and, more recently, personal technologies available to consumers—has greatly increased the potential point of information disclosure. These points of information access are discussed throughout the book.
Figure 1.5 is a basic outline of a simple Web shopping transaction, in which you make personal information available to the world at several points. If you are going to buy that digital camera you found on CNET, you would have to go through this basic process. Along the way are several points where your personal information can be subverted and captured for evil purposes. These are discussed in the following sections.
Figure 1.5. Potential points of information disclosure.
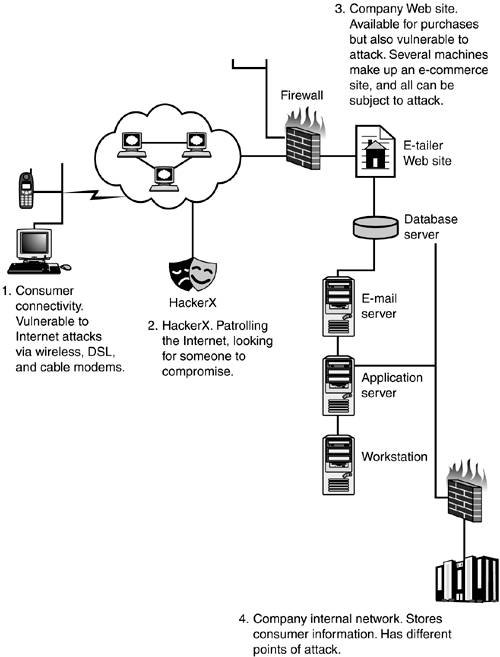
Potential Threat 1: Consumer Connectivity to the Internet
The consumer (you) is now present on the Internet through a variety of means, such as cable modems, dial-up connections, DSL, and wireless devices. You are now a node on the Internet and subject to attack, just as are large corporations. The goal of attackers, whether they are hackers or companies after your marketing information, are the same: find out as much about you as possible. How they use your information differs. In this step, you make a purchase from your favorite Web site. To do this, you connect to the Internet, browse through the Web site, make a purchase using your credit card, get an e-mail confirmation, and have the product sent to you. This basic transaction has many points of information dissemination.
With your computer always connected, using Windows 9.x, Windows Me, Windows NT, Windows 2000, Windows XP, Mac OS, or Linux variants, you leave yourself open to attack. If HackerX is after you, the first goal could possibly be hacking your computer and taking control of it. If you are not protected by security software, gaining control of your system is probably a simple five-minute exercise. This extreme example probably seems like it is prorogating fear, uncertainty, and doubt (the FUD factor), but we will strive to clarify all these steps throughout the book to give you a clear understanding of what is possible. On your computer are sensitive files, e-mail, and cookies (more to come on this later)—to name a few sources of information. HackerX now has a lot of information about you by taking advantage of you through client-side technologies, namely your own computer. If you are using wireless technologies to make a purchase, HackerX has a more difficult job of gaining your information and will probably target the server-side processes to invade your privacy.
If the attacker is a company looking for marketing material, it's a simple matter of buying your information from the product company. Each time you make a purchase, you have that option of subjecting yourself to mass marketing, in most cases. Of course, not all companies sell information. (We will discuss the merits of privacy polices to address this issue later.) There are ways of tracking your preferences other than purchasing your information from a product company. If you've used a search engine, the logs of what keywords you used and where you were surfing from can be compiled and sifted for relevant information, and geographic target segments of the population can be compiled based on such information.
Potential Threat 2: Hackers Searching the Internet
Hackers are patrolling the Internet looking for any opportunity to compromise a network or an individual user system. The reasons can vary from fun and profit to cyber terrorism. Hacker skills range from the “script kiddies” who just download and use tools in the hopes of compromising a computer to really knowledgeable hackers who write exploits, actually understand the underlying technologies, and know how to take advantage of weaknesses. HackerX can launch attacks at both the server-side information stores and client-side technologies. Both avenues of attack look for any weaknesses that can be exploited to gain access to your personal information. Hackers targeting individual user systems are mostly looking for resources to control, whereas individual information on the client side is usually secondary when attacking consumer systems. The reasons for attacking consumer systems can be
To use the client-side launching points for further attacks
To trade illegal software
Excitement in testing skills
To be used for distributed denial-of-service attacks
To gather personal user information
To destroy a user's systems
Revenge
HackerX targets corporate networks for somewhat different reasons. Financial gain and cyber terrorism are becoming increasingly more prevalent in hacker attacks. In the past, it was usually to show off their skills, have bragging rights in the underground community, trade illegal software, and make a statement. Now attackers have more specific goals in mind. The end result of HackerX targeting server-side resources is your private information being compromised. It is easier to hack a corporate e-commerce site and retrieve a whole database of customer credit card information than it is to hack individual user systems and hope credit card information is stored there.
In the case of the consumer using a wireless device to make a purchase, HackerX must compromise a system on the corporate network to gain the consumer's private information. One other possibility is to be in range of the cell phone with a scanner and eavesdrop on conversations, and perhaps “sniff” wireless traffic. Wireless hacking can be very difficult, and the technology is generally more secure that older wire-based technologies. But exploitable weaknesses do exist in wireless technology that HackerX can take advantage of to gain information. For example, the Wireless Equivalent Privacy (WEP) algorithm, which is designed to protect wireless networks from eavesdropping has emerged with flaws. The weakness stems from the ability of an attacker to decrypt traffic based on statistical analysis, inject new traffic from unauthorized mobile stations, decrypt traffic, and launch dictionary attacks. As the technology becomes more complex, exploitation of the technology will move forward at a matching pace.
Potential Threat 3: Vendor Sites Are Vulnerable to Attack
The company's e-commerce site has multiple points of attack as well as multiple ways of disseminating consumer information. All the information it collects about the consumer is stored in databases that are easily mined, with information sold to the highest bidder. Server-side security of your personal information is wholly dependent on the security measures put in place by the company. The user has no rights or influence on how the company protects her information, but public image and revenue loss are usually the driving factors behind the security measures put in place by the company. If news of a compromise of user information were made public, the company would lose the trust of the public, and that translates directly into revenue dollars. There are numerous steps companies take in securing data, from in-house internal audit departments to outsourced third-party security companies that look for weaknesses in the security measures that are in place.
In our example, the consumer enters data through the Web interface, the purchase is made, the credit card information is accepted, and the credit card processing is handled by banks and processing companies. The result is a charge to your credit card and revenues posted to the company's bank account. In many cases, the credit card number might not even be stored on the company's servers, which just means that another company has your financial information and might be the target of a hacker. Several servers on the company's network have to be secured from unauthorized access. This increases the risk of exposure of your data. If HackerX were to compromise one system on the corporate network, he could launch further attacks or just watch the traffic on the network and capture the sensitive information. The attacker can install a backdoor that will allow him access at a later time or Trojan programs that can perform malicious activity after some trigger has been activated by hiding what he actually is from the consumer.
Potential Threat 4: Credit Card Companies Are Also Subject to Attack
Credit card processing done by third-party companies has the same risk exposure to your personal data as does the company from which you are buying the product. The credit card processor has its own networks that are at risk from attackers. There might be secure connections between the company and the credit card processor, but after the transaction is complete and your financial information is stored on the credit card processor's server, the connections need to be secured. If the network is compromised, the hacker can install a backdoor and Trojans again and capture all further incoming credit card information.
If HackerX is looking for financial reward, he can blackmail the company into paying some money to not be made a public spectacle. This was done in the CD Universe hacking incident. In this case, an attacker hacked into the company, stole credit card information, and tried to extort money from CD Universe; however, the company did not pay the attacker any money. An attacker can cause destruction of the Web site or to the backend processing servers to cause financial ruin to the company. Code can also be modified to allow the attacker to reroute financial transactions or even change prices on the Web site to buy products cheaply. This type of attack can affect public companies, which can lead to stock price manipulation for profit by the attacker. The attacker can be very stealthy, steal information over a period of months, and use credit card information without the company even knowing it has been breached. There are numerous methods of gaining your personal information from server-side risks.
Potential Threat 5: Internal Networks Are Vulnerable to Hackers and Disgruntled Employees
Assuming that the corporate internal network is secure and data stored on internal servers cannot be obtained from the Internet is a big mistake. Any company that has an Internet connection usually has some connection from its internal network to that Internet site; this is a necessity for easy administration. Protective measures such as firewalls usually are in place to control access, but attackers can still challenge that security to get to the internal environment. The internal network is usually less secure than Internet reachable networks. Stealing your personal information from the internal corporate database servers has the same effect as stealing it from the e-commerce database server.
Internal attacks from disgruntled employees or ex-employees make up the vast majority of internal hacking incidents. Employees can steal your information the same way a clerk in a store can copy your credit card information after you have made a purchase—only they can steal thousands of numbers by copying a whole database instead of just one or two handwritten copies a clerk can make.
These five potential threats to your privacy illustrate some of the points of access to your personal information that we will discuss in the rest of the book. Proactive techniques are needed to achieve personal privacy. In the preceding sections, we have identified points of weakness that we will illustrate in greater detail in coming chapters. Users and companies can manage the risk to consumer information by taking the necessary proactive steps. Server-side risks have been prevalent in the past, but with the advent of new technologies, the onus will be on the consumer to protect his privacy. The tools and procedures are available to fight the war on information dissemination; you just have to learn what they are and how to use them effectively.
Privacy Roadmap
After reading about all the risks to your privacy, you might be wondering how to combat all these attacks on your personal information. As technology advances, it's just a matter of time before someone comes up with an automated method of searching the Internet and compiling every bit of relevant piece of information about you. Privacy advocates such as the Electronic Frontier Foundation (EFF) (http://www.eff.org/) are leading the charge to keep us secure. But that is not enough. Consumers must take matters into their own hands about what type information is given out and how to protect themselves on the Internet and in the coming wireless environment. Data mining is becoming a science, and you do not want your information to be one of the nuggets mined from cyberspace.
Security measures need to be taken by the user to keep information private. Installing security systems on your computer is not synonymous with being private. Privacy refers to information about you, and it also includes your behavior and habits in using the online world, which can easily divulge information about you. Security is a process of keeping that information out of the hands of the wrong people, and security measures are tactical steps you can take to secure your data. Tangible assets and pieces of information can be made secure. On the client side of the privacy issue, the individual must implement measures such as personal firewalls and encryption to keep her data secure. On the server side, the corporation must take the same measures to secure information, only on a much larger scale. Consumer pressures and laws will have to be put forth to keep our information private on the server side. Companies understand such pressures and will do what is necessary to keep the revenues coming in and keep the customers happy.
Good security does not necessarily equal good privacy. As you will see through examples later in the book, a computer system can be made secure from hackers, but the user can still divulge information through several channels. All the information can be made secure on your home system, but after you send it to a company, you have no control of how it uses your data or who has access to that data. If you implement strong security measures to stop a hacker from breaking into your computer but download a file with a virus that wipes out your hard drive, you have still been compromised and your private information destroyed. Security can be compromised in a number of ways that we will cover later in detail. As an educated consumer, you will understand that you must play a large role in keeping your information from falling into the wrong hands.
The following chapters define steps that can be taken to secure yourself and your PC. The progression of the book lays out practical and legal aspects of privacy first. Next, the problems associated with information dissemination in the online environment are discussed in detail. Then, threats posed by other devices (such as game stations, Palm Pilots, and cell phones) that can share your personal information are discussed, as well as what threats they pose in the near future. Finally, security measures are explained that will show you how to secure your environments and be secure in the future.
The practical steps that can be taken by the consumer to secure their information include the following.
Understanding the Legal Environment
The laws are changing to address the issues of personal privacy, but they aren't changing fast enough to keep up with technology. You need to understand what these changes are and how they affect your daily life. Cybercrime prosecution has taken great leaps forward in recent years. More hackers are being prosecuted, and tangible measures for loss are being developed to help in prosecution. Cybercrime is a global problem that cannot be addressed by one country's laws alone. However, laws are also being passed that can be a liability to the consumer. Industries are lobbying for minimum controls in some areas to enable them to operate more freely and make large profits. For every new privacy law, there will be opponents that see a loss of revenue and therefore seek to bar such laws from being passed. The various privacy laws between countries are covered in Chapter 2, “Defining Privacy: Social and Legal Aspects.”
Understanding the Corporate Environment
Companies generally tend to address consumer needs, so you will find a Privacy Statement on just about every company's Web site. If you actually read these, you can better understand what the company's stance is regarding your private information. Half of the time it is very vague, but you can tell somewhat about how they regard your data. If you are using some piece of software, such as RealPlayer, that is connected to the Internet and the company's corporate networks, you should understand what these programs are actually doing. Are they sending information back to the company about you and your system? To understand the companies you are dealing with, it is important to know the following:
Do they resell information?
Have they had any prior incidents regarding privacy issues or hacker attacks?
Have they taken proactive steps to secure their own sites, such as with security testing or audits?
Do they support privacy initiatives such as those of the EFF?
What information are they capturing about you, and is it necessary?
Do they use third-party agents who will also have access to your information?
What security measures have been built into the software you have installed from a company?
Does the software you installed perform unknown functions?
How do they profile your preferences to see trends in your activities?
If a company goes out of business (such as the dot-gones), what happens to your information?
Knowing Your System
Your personal computers and home networks have become a focal point of attacks and compromise. Cable modem and DSL providers tout the always-on access to the Internet but don't mention the “always-vulnerable” aspect of being on the Internet. You have become another node that can be attacked. Without software to protect your system, you are basically an easy target for any hacker. When your system starts to perform outside the norm, you need to know why. When using browser technology, information is being stored on your hard drive for later retrieval. If you use free e-mail such as with Yahoo!, you have the option to have the site remember who you are. That involves using stored information on your computer to remember you. You must understand how these services and technologies affect you computer. In addition, if you have a home network or your own personal Web site, the potential risks just increase with the additional technology you are using. To know your systems you must
Understand the weaknesses in your computer systems.
Understand some of the tools that typically are used against your home systems.
Understand how to log and monitor your system.
Know what legal actions you can take and what actions would be deemed illegal if you were to start executing attacks against your attackers.
Know how to respond to a hacker compromise of your system.
Learn how to implement secure environments as you use the Internet.
The home user must become a system administrator. This does not mean you must go out and learn all about technology and programming languages. What it means is that you must take some time and effort in becoming knowledgeable about the devices in your home and the software needed to protect yourself. Accepting the default settings and configurations from your DSL and cable modem provider will only lead to attacks by malicious folks on the Internet. Assuming that the Web site you browse and the online shopping carts you use are secure, using proper encryption on your credit card information will lead to someone “sniffing” and pilfering your personal information. Assuming you can browse the Web from your cell phone and use your wireless network card on your laptop securely will only lead to dispensing your information to anyone within close range of you. The end user has more responsibility for his own security and privacy and cannot wholly depend on third parties.
Understanding the Threats You Face
Primary threats against you will be directly related to hacker activity. In knowing the technologies you are using, you will better understand what is possible when it comes to exploiting your privacy. Hacker threats are becoming more mainstream and prevalent, and chances are you will be touched by some hacker activity in the near future. To understand hacker threats, you need to know what technologies you are using and how they might be vulnerable. To do this, you must
Implement security features built into the technologies you are using.
Keep current with vulnerabilities associated with technologies you are using.
Know what information about you is available on your computer and what information is being sent out to companies and Internet service providers (ISPs) about your systems.
Monitor your environment for attacks.
Be aware that the threats facing the companies you do business with, are the same that you face on your home networks.
Know who your enemies are—there are more out there than you think.
The secondary threats you face are from corporate entities that seek to use your information in any way possible to make a profit. Companies attack you from an information gathering standpoint rather than a security standpoint. Your profile translates into dollars to the right marketing company.
Using Proactive Measures
Being secure today does not equal being secure tomorrow. The same goes for keeping your information private. Although security and privacy are not the same thing, they are inseparable. To keep data private on a system, you need good practical security measures in place. Each day poses a new threat to whatever measure you have taken, so proactive steps must be in place to keep up with technology changes. Numerous sources of information about system security are available. These need to be sifted through for the information pertinent to your privacy. As you install new technology or use a new product, investigate the potential weaknesses it has that could affect you personally. New technologies bring new weaknesses on a daily basis. By continuously updating and upgrading your security measures, you can keep current with the latest threats you will be facing in the wired world.
