Other Tips for Your Home PC
Both Windows- and Linux-based operating systems come with a whole host of functions that we will not try to cover in detail in this book. Numerous books are available on every detail of the operating system. You can take a few steps in addition to those already mentioned to will help in your operating system security.
Server Software
Never run unnecessary servers on your machines. A server is a program that will allow others to access data on your machine. Examples are Web servers or FTP servers. If you run a Web site on your home computer through the functionality provided by your ISP, you allow people to interact directly with your computer. Most of these servers allow you to restrict access to certain directories. However, some servers are easily configured incorrectly. Others have bugs that can be exploited to bypass the access restrictions. If you have to run a server, make sure you read the manual and configure it properly. As an example, if you install Windows 2000 Server, it also automatically installs the IIS Web server, an FTP server, and an SMTP server (mail function). You must go into Internet Information Services Manager to turn these services off manually if you do not really want them running (see Figure 10.38). You can get to the Internet Information Services Manager by selecting the Administrative Tools option from the Control Panel.
Figure 10.38. Using the Internet Information Services Manager utility to administer Web, FTP, and Mail servers.

Remote-Control Programs
Use remote-control programs on home computers with caution. Programs such as PC Anywhere, Microsoft's Terminal Server, Carbon Copy, and Virtual Network Computing (VNC) should be paid special attention because they provide console-equivalent access to machines. By using this type of software, a user can connect to your machine remotely and have full control over it. It's easy to misconfigure such software to allow unauthorized individuals who find the open connection to take control of your computer remotely. Therefore, password authentication to access the computer via this class of software is absolutely required. Many of these programs also have built-in encryption functions that can add another layer of security. If the software allows it, set options that allow encryption of traffic as it travels from the host machine to the remote machine. You might also set options that allow access only from specific IP addresses.
Virus Scanning
Antivirus software is a must on every personal computer. We'll address this subject in more detail in Chapter 12, but suffice it to say, every personal computer should be running an up-to-date antivirus software package. Many of these programs have automated capabilities that can go to the vendor Web site and update the software with new virus signatures without your intervention.
E-mail Attachments
Most e-mail readers allow you to send and receive binary files as attachments. Be careful if you receive an attachment. Make sure you know where the e-mail came from. If you receive an attachment and do not recognize the sender's address, exercise caution. Lately, e-mail attachments contain malicious code that spreads across the Internet. The “I Love You”, Melissa, and Anna Kournikova viruses are all dangerous viruses. Viruses can range from the annoying to the destructive. The viruses just listed did not destroy data, but they did create a tremendous annoyance to mail and systems administrators, overloading servers and some network connections. If an e-mail recipient of the virus opened (double-clicked) the infected attachment, the virus automatically sent the message to contacts in the user's address book. When those recipients opened their e-mail, the same actions occurred, causing an avalanche of e-mail.
Never double-click an attachment to open it unless you trust the sender or already know that it has been scanned by an up-to-date virus checker. (Picture attachments are usually harmless.) Save the attachment, start the image viewer, and load the attachment. This prevents you from opening an executable that disguises itself as an image. Even if you receive an executable from a familiar source, it is still worthwhile to run it through a virus checker first. Many virus programs have the capability to scan e-mail attachments for infection and quarantine the e-mail if it is infected. The sender might not know that his system is infected by a virus and is sending out e-mail on the virus' behalf.
Deleting Files
Most of us know that when we delete a file by pressing the Delete key or dragging it to the Recycle Bin, the file isn't really deleted yet. What about when the Recycle Bin is emptied? Is the file really gone then? What about when a hard drive is reformatted? The answer is no in all cases. Measures can be taken to retrieve the supposedly deleted data. Delete commands usually only remove the pointers that tell the computer where on the physical hard drive the data is stored. When the pointer for a particular file no longer exists, the file is thought to be deleted, even though the data still resides on the disk. All of that data can still be recovered from the disk. Software programs such as Norton Utilities UnErase and various computer forensics products such as Encase allow for the recovery of these “deleted” files. If the deleted data was not overwritten by new data, the chances of recovering those lost files are excellent.
To completely wipe deleted files from your hard drive, make use of utilities such as PGPtools, Norton Utilities Wipeinfo, Shredder, and BC Wipe. Because a deleted file is not really deleted and can be recovered, you need some additional help to completely delete a file and make it unrecoverable. These utilities tackle this problem by over writing the hard drive's data portion. This cleaning process overwrites all parts of the hard drive multiple times so that it is next to impossible that data can be recovered.
One example of a program used to really delete a file is PGPtools. Using PGPtools (www.pgp.com), we can securely delete or “wipe” a file. You open the Wipe utility and specify the appropriate filename in the dialog box (see Figure 10.39). PGPtools deletes the file by not only removing its pointer, but also by overwriting the data on the hard drive. This easy-to-use utility should be employed when you need to really delete a sensitive file.
Figure 10.39. Securely delete (wipe) a file by using PGPtools' Wipe utility.

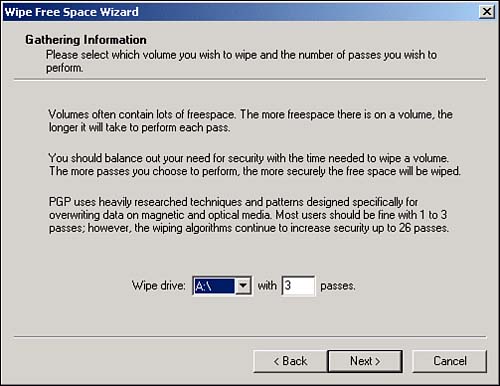
Another interesting utility available in PGPtools is FreeSpace Wipe. It does what its name implies—it overwrites freespace so that preexisting data is overwritten. When you open the FreeSpace Wipe utility in PGPtools, a wizard appears, guiding you through the process, as shown in Figure 10.40. The wizard prompts you for information such as the drive to be wiped and the number of passes that it should make. The more passes that the utility makes, the less likely that the file can be recovered. For most purposes, a setting of 5 is adequate. Department of Defense standards for secure deletion of files require multiple writes, implying that there is technology that can read data if only one pass is made.
Figure 10.40. Using PGPtools FreeSpace Wipe to overwrite freespace.
If you ever need to dispose of your computer equipment or computer disks, make sure you take the appropriate steps to clean the storage media. You might have heard the press lately about failing dot.coms that auctioned off their computer equipment without deleting, much less cleansing, the data that was present on their hard drives. These computers contained information such as social security numbers of employees, salary information, termination letters, and meeting minutes from executive and board meetings. Actually, it is not surprising that cleansing hard drives is not a priority when it comes to closing down a business. However, given the fact that employee and customer data was present and unsecured, greater care should have been taken.
Electronic Eavesdropping
An individual (or, more likely, an organization) can thwart most of the logical access controls described so far with access to sophisticated (expensive) electronic eavesdropping equipment. Eavesdropping is the interception of radio frequency interference (RFI) and electromagnetic interference (EMI) emitted by the various computer equipment in use (screens, keyboards, cables). All electronic equipment emits these faint signals, which, if interpreted correctly, reveal the information being processed. An example of EMI is the use of older household appliances while watching TV or listening to the radio. Whenever these appliances were turned on, they emitted interference, which, in turn, affected the image on the TV screen. These emanations can theoretically be captured and analyzed. Although there might be no interest in capturing emanations from a toaster, one could certainly find interesting information when capturing emanations from a computer monitor or printer.
This type of technology is also thought to be possible because of the existence of Transient Electromagnetic Pulse Emanation Standard (TEMPEST) standards and TEMPEST-related certifications. TEMPEST typically refers to a set of standards for limiting RFI and EMI “leakage” from computer equipment. It's also used to describe the process of preventing those emanations.
Realistically, you are only at risk for TEMPEST-based attacks if the data you are processing is of extremely high value. The resources required to purchase and develop this technology remain out of reach for most people and organizations. Only governments are thought to be able to carry out TEMPEST-based attacks. A mini-industry has developed around TEMPEST hardware and consulting.
Keystroke Logging
Another interesting item to be aware of is the use of keystroke loggers. Keystroke loggers take every key pressed on the keyboard and record it in a log. This is particularly useful when someone wants to discover a password. As a user types a password, the keystrokes are recorded in the log, which can later be retrieved and analyzed. Hackers commonly use software-based keyboard loggers after they have broken into a machine. Alternatively, if physical security is breached, a hardware-based keystroke logger can be installed. This kind of device is installed between the keyboard cable and the computer. Unless the keyboard cable is checked frequently for the existence of such a device, the detection of a hardware-based keystroke logger remains low. These devices are widely available, however. They can be purchased for less than $200, as opposed to TEMPEST equipment, which falls in the millions of dollars (if it's available at all).
The detection of software-based keystroke loggers can be fairly easy if a thorough search of a computer is performed, although some loggers conceal themselves quite well. Detection of hardware-based loggers is much easier, obviously, but can be difficult based on where and how the computer equipment is situated.
An example of a software-based keystroke logger is Invisible KeyLogger Stealth (IKS), manufactured by Amecisco (http://www.amecisco.com). IKS is shown in Figure 10.41. After it is installed, it captures every keystroke typed at the console, including the password you type after pressing Ctrl+Alt+Delete. Keystrokes are saved to a file on the hard drive. In the case of IKS, a special viewer is required to view the file.
Figure 10.41. Keystroke capturing.

