There are other Python packages that are not specifically designed to obtain network interfaces in a computer, but they have some function for doing this task. For example, the psutil package (https://pypi.org/project/psutil) allows tasks related to process and system monitoring in Python.
This package provides the net_if_addrs() method for getting information related to network interfaces:
import psutil
psutil.net_if_addrs()
The information is returned in a dictionary structure, as follows:
{'Local Area Connection* 11': [snicaddr(family=<AddressFamily.AF_LINK: -1>, address='00-FF-C0-63-12-57', netmask=None, broadcast=None, ptp=None), snicaddr(family=<AddressFamily.AF_INET: 2>, address='169.254.219.137', netmask='255.255.0.0', broadcast=None, ptp=None), snicaddr(family=<AddressFamily.AF_INET6: 23>, address='fe80::f4ca:6a17:37a3:db89', netmask=None, broadcast=None, ptp=None)], 'Ethernet': [snicaddr(family=<AddressFamily.AF_LINK: -1>}
This method returns the addresses associated with each network interface card detected in the operating system. The information is returned in a dictionary data structure whose keys are the names of the NIC, and the value is a list of tuples for each address assigned to the NIC. Each named group includes five fields:
- family: Represents the family for Mac address.
- address: The primary IP address.
- netmask
- ptp: References the destination address on a point-to-point interface.
- broadcast
With this package, we also have the ability to get socket connections in our computer with commands such as netstat:
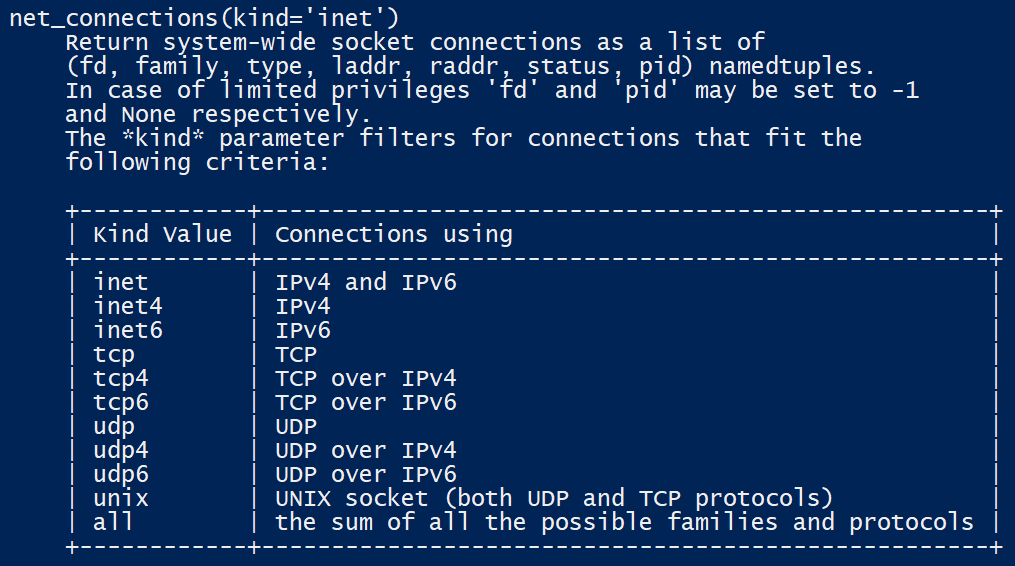
We can use the net_connections() method to get a list of socket connections available in your local machine in the same way that we can use the netstat command that is available in many operating systems:
psutil.net_connections()
Here is the output from executing the net_connections() method:
[sconn(fd=115, family=<AddressFamily.AF_INET: 2>, type=<SocketType.SOCK_STREAM: 1>, laddr=addr(ip='10.0.0.1', port=48776), raddr=addr(ip='93.186.135.91', port=80), status='ESTABLISHED', pid=1254),
sconn(fd=117, family=<AddressFamily.AF_INET: 2>, type=<SocketType.SOCK_STREAM: 1>, laddr=addr(ip='10.0.0.1', port=43761), raddr=addr(ip='72.14.234.100', port=80), status='CLOSING', pid=2987),
sconn(fd=-1, family=<AddressFamily.AF_INET: 2>, type=<SocketType.SOCK_STREAM: 1>, laddr=addr(ip='10.0.0.1', port=60759), raddr=addr(ip='72.14.234.104', port=80), status='ESTABLISHED', pid=None),
sconn(fd=-1, family=<AddressFamily.AF_INET: 2>, type=<SocketType.SOCK_STREAM: 1>, laddr=addr(ip='10.0.0.1', port=51314), raddr=addr(ip='72.14.234.83', port=443), status='SYN_SENT', pid=None)
...]
In the following script, we are going to obtain information about IPv4 and IPv6 interfaces with the psutil.net_if_addrs() method.
You can find the following code in the check_interfaces_psutil.py file:
#!/usr/bin/env python3
import socket
import psutil
def get_ip_addresses(family):
for interface, snics in psutil.net_if_addrs().items():
for snic in snics:
if snic.family == family:
yield (interface, snic.address)
if __name__ == '__main__':
ipv4_list = list(get_ip_addresses(socket.AF_INET))
ipv6_list = list(get_ip_addresses(socket.AF_INET6))
print("IPV4 Interfaces",ipv4_list)
print("IPV6 Interfaces",ipv6_list)
This could be the output of the previous script:
IPV4 Interfaces [('Local Area Connection* 11', '169.254.219.137'), ('Ethernet', '10.80.92.211'), ('VirtualBox Host-Only Network', '192.168.56.1'), ('Npcap Loopback Adapter', '169.254.204.194'), ('Wi-Fi', '169.254.52.200'), ('Local Area Connection* 2', '169.254.234.2'), ('Loopback Pseudo-Interface 1', '127.0.0.1')]
IPV6 Interfaces [('Local Area Connection* 11', 'fe80::f4ca:6a17:37a3:db89'), ('Ethernet', 'fe80::a568:f01f:d4ae:170'), ('VirtualBox Host-Only Network', 'fe80::e53f:e43b:ad07:9cab'), ('Npcap Loopback Adapter', 'fe80::8cd:714b:4e02:ccc2'), ('Wi-Fi', 'fe80::644d:7369:e8ca:34c8'), ('Local Area Connection* 2', 'fe80::856f:c54b:1d7e:ea02'), ('Teredo Tunneling Pseudo-Interface', 'fe80::ffff:ffff:fffe'), ('Loopback Pseudo-Interface 1', '::1')]
