Description of DES
DES (Data Encryption Standard) is one of the most popular symmetric ciphers. DES is symmetric because it uses a single key both to encipher and decipher data. This is useful in situations in which parties that encipher data are allowed to decipher data as well. DES is a block cipher , which means that it processes data in fixed-size sections called blocks. The block size of DES is 64 bits. If the amount of data to be encrypted is not an even multiple of 64 bits, it is padded in some application-specific way.
DES is considered reasonably secure, and it runs fast, even in software. However, as with many ciphers, the security of DES has never been proven publicly. Nevertheless, the algorithm has stood up to years of cryptanalysis, which does suggest a certain level of confidence. Even so, as computing speeds continue to increase, DES becomes less and less secure. Today, its security is challenged regularly in contests that offer cash prizes to those who can crack messages encrypted with DES the fastest.
At its essence, the security of DES revolves around smoke and mirrors, or in cryptographic lingo, the principles of confusion and diffusion . The goal of confusion is to hide any relationship between the plaintext, the ciphertext, and the key. The goal of diffusion is to spread the effect of bits in the plaintext and the key over as much of the ciphertext as possible. Together, these make cryptanalysis very difficult.
With DES, we encipher a block of plaintext by performing a series of permutations and substitutions on it. Exactly how the permutations and substitutions affect the original plaintext is essentially a function of 16 subkeys, K 1, K 2, . . ., K 16, derived from a starting key, K 0, which is the key we provide. To encipher a block of plaintext, each subkey is applied to the data in order (K 1, K 2, . . ., K 16 ) using a series of operations repeated 16 times, once for each key. Each iteration is called a round. Deciphering a block of ciphertext uses the same process but with the keys applied in reverse order (K 16, K 15, . . ., K 1).
Computing Subkeys
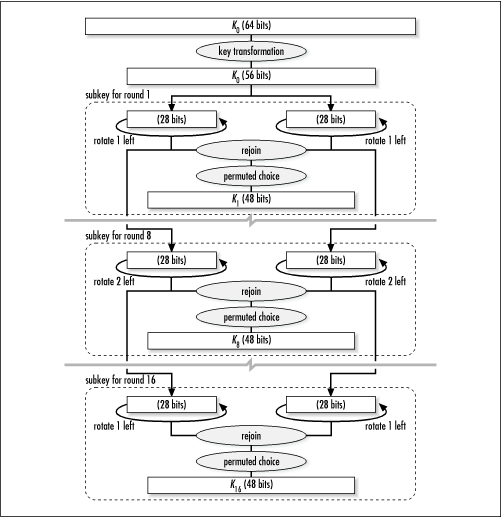
The first step in DES is to compute the 16 subkeys from the initial key. Figure 15.1 illustrates this process. DES uses a key that is 56 bits; however, the key we provide is a 64-bit value. This is so that in hardware implementations every eighth bit can be used for parity checking. In software, the extra bits are simply ignored. To obtain the 56-bit key, we perform a key transformation as shown in Table 15.1. To interpret this table, read from left to right, top to bottom. Each position p in the table contains the position of the bit from the initial key that occupies position p in the transformed key. For example, using Table 15.1, bit 57 of the initial key becomes bit 1 of the transformed key, bit 49 becomes bit 2, and so forth. The convention is to number bits from left to right starting at 1.
57, | 49, | 41, | 33, | 25, | 17, | 9, | 1, | 58, | 50, | 42, | 34, | 26, | 18, |
10, | 2, | 59, | 51, | 43, | 35, | 27, | 19, | 11, | 3, | 60, | 52, | 44, | 36, |
63, | 55, | 47, | 39, | 31, | 23, | 15, | 7, | 62, | 54, | 46, | 38, | 30, | 22, |
14, | 6, | 61, | 53, | 45, | 37, | 29, | 21, | 13, | 5, | 28, | 20, | 12, | 4 |
After transforming the key to 56 bits, we compute the subkeys. To do this, we first divide the 56-bit key into two 28-bit blocks. Next, for each subkey, we rotate both blocks an amount that depends on the round in which the subkey will be used (see Table 15.2), then rejoin the blocks. After this, we reduce the 56-bit subkey formed from the rejoined blocks to 48 bits by permuting it as shown in Table 15.3. (This table is read like Table 15.1.) Note that Table 15.3 contains two fewer columns because 8 bits are discarded. This permutation is called the permuted choice. This process is repeated once for each of the 16 subkeys. All together, the goal here is to ensure that we apply different bits from the initial key to the data in each round.
Enciphering and Deciphering Data Blocks
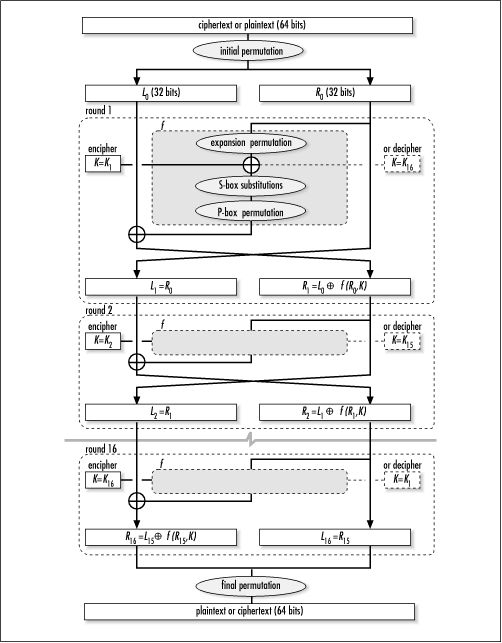
Once we have prepared the subkeys, we are ready to encipher or decipher data blocks. Figure 15.2 illustrates this process. We begin by permuting the 64-bit data block as shown in Table 15.4. (This table is read like Table 15.1.) This permutation is aptly named the initial permutation . It does not enhance the security of DES, but is believed to have been added to make data easier to load into DES chips before the advent of 16-bit and 32-bit buses. Although anachronistic, the permutation should still be performed in order to comply with the DES standard. After the initial permutation, the 64-bit data block is divided into two 32-bit blocks, L 0 and R 0.
58, | 50, | 42, | 34, | 26, | 18, | 10, | 2, | 60, | 52, | 44, | 36, | 28, | 20, | 12, | 4, |
62, | 54, | 46, | 38, | 30, | 22, | 14, | 6, | 64, | 56, | 48, | 40, | 32, | 24, | 16, | 8, |
57, | 49, | 41, | 33, | 25, | 17, | 9, | 1, | 59, | 51, | 43, | 35, | 27, | 19, | 11, | 3, |
61, | 53, | 45, | 37, | 29, | 21, | 13, | 5, | 63, | 55, | 47, | 39, | 31, | 23, | 15, | 7 |
After completing the initial permutation, the data block moves through a series of operations that are repeated for 16 rounds. The goal of each round i is to compute Li and Ri , which are used by the next round, until we finally end up with the data block R 16 L 16. We begin each round with Li - 1 and Ri - 1, and expand Ri - 1 from 32 to 48 bits using the expansion permutation , as shown in Table 15.5. (This table is read like Table 15.1.) The primary purpose of this permutation is to create an avalanche effect when enciphering data. This makes one bit in the data block affect more bits in the step to follow, and thus produces diffusion. Once the expansion permutation is complete, we compute the XOR (denoted ⊕) of the 48-bit result and Ki , the subkey for the round. This produces an intermediate 48-bit result, which is called R int. If we let E be the expansion permutation, the operations thus far in the round can be expressed as:
32, | 1, | 2, | 3, | 4, | 5, | 4, | 5, | 6, | 7, | 8, | 9, |
8, | 9, | 10, | 11, | 12, | 13, | 12, | 13, | 14, | 15, | 16, | 17, |
16, | 17, | 18, | 19, | 20, | 21, | 20, | 21, | 22, | 23, | 24, | 25, |
24, | 25, | 26, | 27, | 28, | 29, | 28, | 29, | 30, | 31, | 32, | 1 |
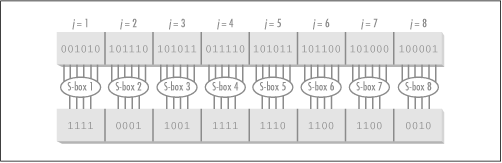
Next, Rint undergoes eight substitutions performed using eight separate S-boxes. Each S-box j takes a six-bit block from position 6j to 6j + 6 in Rint and looks up a four-bit value for it in a table (see Table 15.6). This value is written to a buffer at position 4j (see Figure 15.3).
To read Table 15.6, find S-box j, look up the row number having the two-bit value formed by the first and last bit of the six-bit block, and find the column having the four-bit value formed by the middle bits of the six-bit block (both zero-indexed). For example, in Figure 15.2, the third six-bit block in Rint is 101011. Therefore, we consult the third S-box in Table 15.6 to find 9, the four-bit value found in row 112 = 3 and column 01012 = 5 (both zero-indexed). S-boxes add confusion to the data, and more than anything else give DES its security. Consequently, they have also long been the source of great scrutiny. Some groups even suspect that they may include a back door by their designers. No one knows, or at least admits to knowing.
S-Box 1 | |||||||||||||||
14, | 4, | 13, | 1, | 2, | 15, | 11, | 8, | 3, | 10, | 6, | 12, | 5, | 9, | 0, | 7, |
0, | 15, | 7, | 4, | 14, | 2, | 13, | 1, | 10, | 6, | 12, | 11, | 9, | 5, | 3, | 8, |
4, | 1, | 14, | 8, | 13, | 6, | 2, | 11, | 15, | 12, | 9, | 7, | 3, | 10, | 5, | 0, |
15, | 12, | 8, | 2, | 4, | 9, | 1, | 7, | 5, | 11, | 3, | 14, | 10, | 0, | 6, | 13 |
S-Box 2 | |||||||||||||||
15, | 1, | 8, | 14, | 6, | 11, | 3, | 4, | 9, | 7, | 2, | 13, | 12, | 0, | 5, | 10, |
3, | 13, | 4, | 7, | 15, | 2, | 8, | 14, | 12, | 0, | 1, | 10, | 6, | 9, | 11, | 5, |
0, | 14, | 7, | 11, | 10, | 4, | 13, | 1, | 5, | 8, | 12, | 6, | 9, | 3, | 2, | 15, |
13, | 8, | 10, | 1, | 3, | 15, | 4, | 2, | 11, | 6, | 7, | 12, | 0, | 5, | 14, | 9 |
S-Box 3 | |||||||||||||||
10, | 0, | 9, | 14, | 6, | 3, | 15, | 5, | 1, | 13, | 12, | 7, | 11, | 4, | 2, | 8, |
13, | 7, | 0, | 9, | 3, | 4, | 6, | 10, | 2, | 8, | 5, | 14, | 12, | 11, | 15, | 1, |
13, | 6, | 4, | 9, | 8, | 15, | 3, | 0, | 11, | 1, | 2, | 12, | 5, | 10, | 14, | 7, |
1, | 10, | 13, | 0, | 6, | 9, | 8, | 7, | 4, | 15, | 14, | 3, | 11, | 5, | 2, | 12 |
S-Box 4 | |||||||||||||||
7, | 13, | 14, | 3, | 0, | 6, | 9, | 10, | 1, | 2, | 8, | 5, | 11, | 12, | 4, | 15, |
13, | 8, | 11, | 5, | 6, | 15, | 0, | 3, | 4, | 7, | 2, | 12, | 1, | 10, | 14, | 9, |
10, | 6, | 9, | 0, | 12, | 11, | 7, | 13, | 15, | 1, | 3, | 14, | 5, | 2, | 8, | 4, |
3, | 15, | 0, | 6, | 10, | 1, | 13, | 8, | 9, | 4, | 5, | 11, | 12, | 7, | 2, | 14 |
S-Box 5 | |||||||||||||||
2, | 12, | 4, | 1, | 7, | 10, | 11, | 6, | 8, | 5, | 3, | 15, | 13, | 0, | 14, | 9, |
14, | 11, | 2, | 12, | 4, | 7, | 13, | 1, | 5, | 0, | 15, | 10, | 3, | 9, | 8, | 6, |
4, | 2, | 1, | 11, | 10, | 13, | 7, | 8, | 15, | 9, | 12, | 5, | 6, | 3, | 0, | 14, |
11, | 8, | 12, | 7, | 1, | 14, | 2, | 13, | 6, | 15, | 0, | 9, | 10, | 4, | 5, | 3 |
S-Box 6 | |||||||||||||||
12, | 1, | 10, | 15, | 9, | 2, | 6, | 8, | 0, | 13, | 3, | 4, | 14, | 7, | 5, | 11, |
10, | 15, | 4, | 2, | 7, | 12, | 9, | 5, | 6, | 1, | 13, | 14, | 0, | 11, | 3, | 8, |
9, | 14, | 15, | 5, | 2, | 8, | 12, | 3, | 7, | 0, | 4, | 10, | 1, | 13, | 11, | 6, |
4, | 3, | 2, | 12, | 9, | 5, | 15, | 10, | 11, | 14, | 1, | 7, | 6, | 0, | 8, | 13 |
S-Box 7 | |||||||||||||||
4, | 11, | 2, | 14, | 15, | 0, | 8, | 13, | 3, | 12, | 9, | 7, | 5, | 10, | 6, | 1, |
13, | 0, | 11, | 7, | 4, | 9, | 1, | 10, | 14, | 3, | 5, | 12, | 2, | 15, | 8, | 6, |
1, | 4, | 11, | 13, | 12, | 3, | 7, | 14, | 10, | 15, | 6, | 8, | 0, | 5, | 9, | 2, |
6, | 11, | 13, | 8, | 1, | 4, | 10, | 7, | 9, | 5, | 0, | 15, | 14, | 2, | 3, | 12 |
S-Box 8 | |||||||||||||||
13, | 2, | 8, | 4, | 6, | 15, | 11, | 1, | 10, | 9, | 3, | 14, | 5, | 0, | 12, | 7, |
1, | 15, | 13, | 8, | 10, | 3, | 7, | 4, | 12, | 5, | 6, | 11, | 0, | 14, | 9, | 2, |
7, | 11, | 4, | 1, | 9, | 12, | 14, | 2, | 0, | 6, | 10, | 13, | 15, | 3, | 5, | 8, |
2, | 1, | 14, | 7, | 4, | 10, | 8, | 13, | 15, | 12, | 9, | 0, | 3, | 5, | 6, | 11 |
Once we have completed the S-box substitutions, the result is a 32-bit value that we permute using a P-box, as shown in Table 15.7. (This table is read like Table 15.1.)
16, | 7, | 20, | 21, | 29, | 12, | 28, | 17, | 1, | 15, | 23, | 26, | 5, | 18, | 31, | 10, |
2, | 8, | 24, | 14, | 32, | 27, | 3, | 9, | 19, | 13, | 30, | 6, | 22, | 11, | 4, | 25 |
At this point, it is convenient to think of the operations in the round as a function, typically denoted as f. If bj is the j th six-bit block of Rint , Sj is the j th S-box, and P is the P-box permutation, this function is defined as:
f = P(S1(b1), S2(b2),. . ., S8(b8))
The last operation in each round is to compute the XOR of the 32-bit result of f and the original left block passed into the round, L i - 1. Once this is complete, we swap the left and right blocks and begin the next round. In the last round, however, we do not swap the left and right blocks. All together, the computations for Li and Ri in each round can be concisely expressed as follows:
When all 16 rounds have been completed, we concatenate the final right block, R 16, with the final left block, L 16, to produce the 64-bit block R 16 L 16. (Recall that the left and right blocks are not swapped in the final round; thus, we have the last right block on the left and the last left block on the right.) The final step is to permute R 16 L 16 as shown in Table 15.8. This permutation is aptly named the final permutation . It simply undoes what the initial permutation did earlier. When enciphering data, the result is a 64-bit block of ciphertext; when deciphering data, it is the original 64-bit block of plaintext.