Assets compliance requirements can be enforced in OER with the utilization of Policies. Policies can be applied to one or many Assets. An Asset can have more than one policy attached to it. A policy in OER consists of one-to-many Policy Assertions. When a policy is applied to an Asset, all of the assertions within the policy must be true in order for Asset to comply with the policy.
Each assertion has a name, a description, and includes a technical definition. Technical definitions support additional metadata that may be needed to validate the assertion (for example, a particular Asset must have less than 1 percent defects before the service can be deployed to the next environment).
According to the use case the following Policies are needed in to order to support the target governance model:
Note that for your organization, you may define as many Policies as you required. For the purposes of this chapter we simplified it.
- Requirement Compliance Enforcement Policy: This policy is applied to Asset Type Requirement Documents to assert:
- Document compliance to business and other enterprise templates
- All sections of the documents have been properly completed
- Traceability matrix exists for functional and nonfunctional requirements
- There are no open issues or gaps
- Design Document Compliance Enforcement Policy: This policy is applied to Asset Types Design Documents to assert:
- Adherence to enterprise architecture principles
- Bill of Materials has been created capturing all needed artifacts
- Data requirements have been captured
- Compliance to design standards and design patterns
- All relevant views (for example, static, dynamic, and sequential) are available and provide all levels of information required
- All design decisions have been reviewed and approved
- There are no open issues or gaps
- Code Compliance Enforcement Policy: This policy is applied to detail designs with the intention to assert:
- Compliance to programming standards
- Alignment to detail design
- Unit Test has been executed successfully and there are no open defects
- Deployment plans and other deployment pre-requisites have been successfully addressed.
- Operational Compliance Enforcement Policy: This policy is applied to detail designs with the intention to assert:
Tip
Policies are made compulsory by introducing compliance checks throughout lifecycle stages of the Asset. Different checks can be introduced during code promotion between environments. For example, code should not be promoted to SIT before quality testing policies have passed, or to UAT before SIT policies have passed. This could be done manually or automated by extending a deployment framework to integrate with OER using the REX APIs.
Policies are created in OER using the Asset Editor.
Before creating Policies you should ensure that:
- Policies have been enabled and that the Policy Management Solution Pack has been successfully imported as described in the section Installing Solution Packs in Chapter 5, Harvesting.
- Policy rights have been granted to the desired roles as follows:
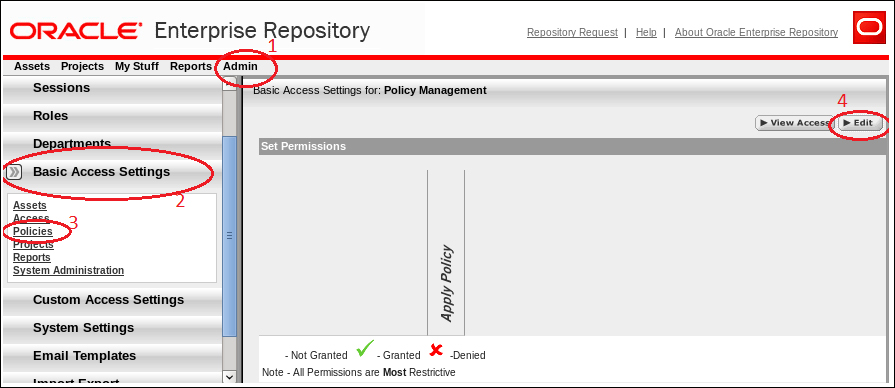
- Log on to OER as admin, and then navigate to the Admin page. From the Basic Access Settings menu, click on Policies and then click on the Edit button.
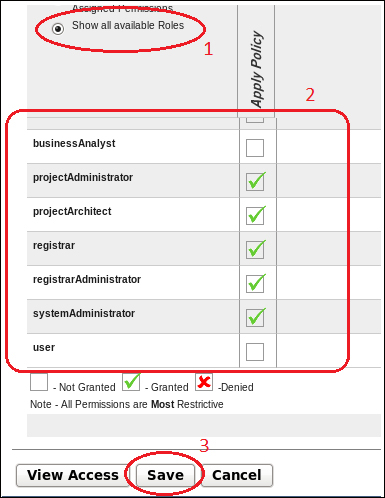
- In the Edit Access Settings window, select Show all available Roles to display existing roles. Then select the roles for which Apply Policy rights will be granted. Click on the Save button. Now a user with any of these roles will be able to apply policies to Assets.
The next step is to create all policies as it has been identified. In this chapter we will explain how to create the Requirement Compliance Enforcement Policy. As the process of creating policies is fairly similar regardless of the policy requirements, the following steps could be reproduced to create the remaining polices.
The fastest way to create a policy is by using an existing Policy Type rather than creating one from scratch (although, this is still perfectly possible by using the Type Manager). This can be done as follows:
- Log on to OER as admin and from the Assets page launch the Asset Editor.
- From the File menu select New.
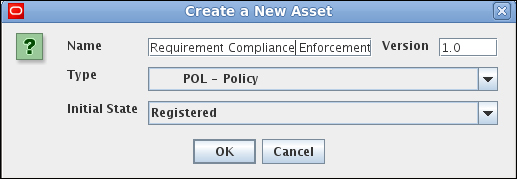
- Enter the name of the policy and its version. Select POL – Policy as the Type. Select the desired Initial State. If you are an administrator, you can set the status as Registered if no further approvals are needed.
- In the Asset details page enter as many details as possible as this will make it easier for someone to enforce the policy when needed. At the very minimum ensure that the Name, Version, Description, and Policy Assertions have all been populated accordingly.

- If there are any specific tests that must be executed in this policy, the same can be added from the Tests tab.
- Save all changes made by clicking on the Save option within the File menu.
- Repeat these types for all policies that need to be created.
- Log on to OER as admin, and then navigate to the Admin page. From the Basic Access Settings menu, click on Policies and then click on the Edit button.
Policies can only be applied to Assets for which the element Applied Asset Policies has been added to its corresponding Asset Type. This can be done as follows:
- Log on to OER as admin and from the Assets Page launch the Asset Editor.
- From the menu Actions select Type Manager.
- Select the desired type that you wish to modify (in our example, Requirement Document).
- Select the Editor Tab.
- In the Tabs section, select Overview.
- In the Elements section, click on the Add button.
- In the new window, select Applied Asset Policies as the Element Type and click on the OK button.
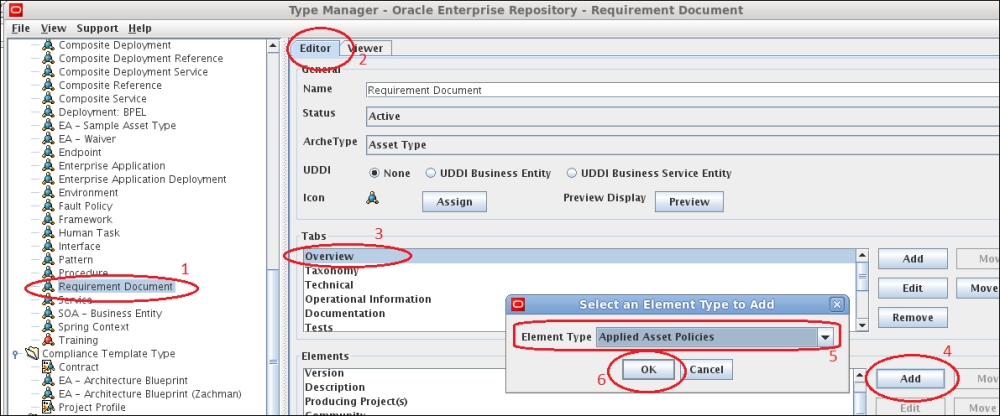
- The Edit Applied Asset Policies window opens. Enter Applied Asset Policies and click on the OK button.
- Click on the Viewer tab.

- In the Hidden Elements section select the Applied Asset Policies element and click on the Display In Group button.
- In the Move Element window, select Overview and click on the OK button.
- Save the changes by clicking on the Save button from the File menu.
- Repeat these steps as required for any Policies that have been created.
Note that it is possible to apply Policies from the
Policies are applied from the Assets page. It is also possible to do this from Asset Editor by editing; however, it is simpler to do it from the Assets Page. Policies can be applied as follows:
- Log on to OER as admin and go to the Assets page.
- Search the Asset to which the policy is to be applied (in our example, we searched for use case document which is of type Requirement Document).
- In the Asset details page click on the Apply Policies button.
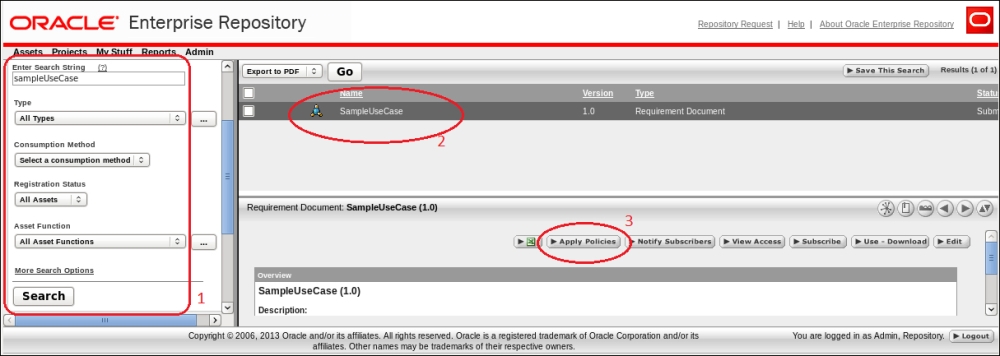
- To display all available Policies click on List All Policies. All available Policies will appear in the Available Asset Policies box.
- Select the policy you wish to apply (in our example, we want to apply the Requirement Compliance Enforcement Policy to the use case document Asset) and then click on >> to apply the policy and then click on the Save button.

- A confirmation message is displayed. Click on the Close button.
- Refresh the Asset detail frame and notice that the Policy Status icon (a yellow icon with a warning symbol) appears in the results page next to the Asset and also in the Assets details page.

The policy status indicates if an Asset is compliant with the assertions available in a policy. For example, if a policy is applied to an Asset, the Asset achieves passed status only when it is compliant with the assertions defined in the policy.
The different statuses are as follows:
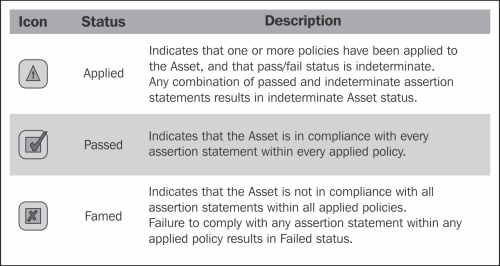
Policies can be validated manually through the Asset Editor or automatically using external tooling (that is, a customized workflow or BPM process) and the REX API's. The following is an example of how to manually validate a policy:
- Log on to OER with any user with a role that has the Apply Policy grants.
- Search for the Asset to validate the policy either from the Assets page or from the Asset Editor. If searched from the Assets page, find the Asset and then from the Asset details page click on the Edit button.
- From the Overview tab of Asset Editor, scroll down and from the Applied Asset Policies select the policy to validate and click on the Details button.

- Select the Assertions to validate and click on the Edit button.

- Enter the Evaluation Date, Evaluation Value (pass or fail), and some description on the evaluation in the Evaluation Information field.
- Click on the OK button.

- Click on the OK button again.
- Save the changes made to the Asset by clicking on the Save button from the File menu.
- The status of the icon will change in accordance with evaluation of the assertions for the Policies. For example, if all assertions are set to pass then the icon status will be Passed.
When policies are applied to several Assets, it becomes unpractical to manually check the status of the Policies applied to Assets. For this purpose it is possible to leverage the reporting capabilities of OER and thus generate reports using the built-in BI Publisher 11g reporting capabilities.
Reports can be accessed from the Reports page. From this page the following policy related reports can be run by clicking on the report link:
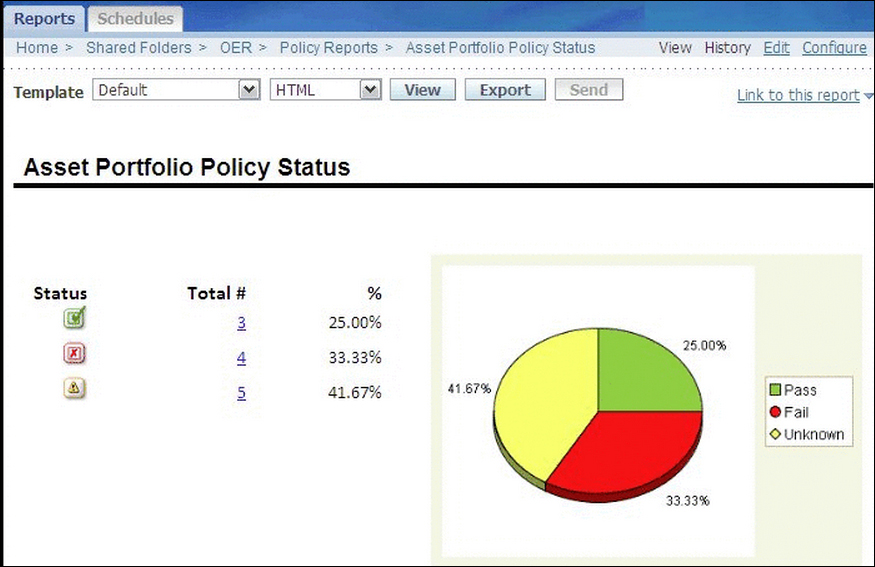
- Asset Portfolio Policy Status: This report provides a summary of the policy status (Pass, Fail, Unknown) for an organization's entire Asset portfolio. The report then allows you to view a list of Assets for each status, for example, all of the Assets that are failing. The detailed reports list all policies applied to each Asset and the status of all policy assertions.
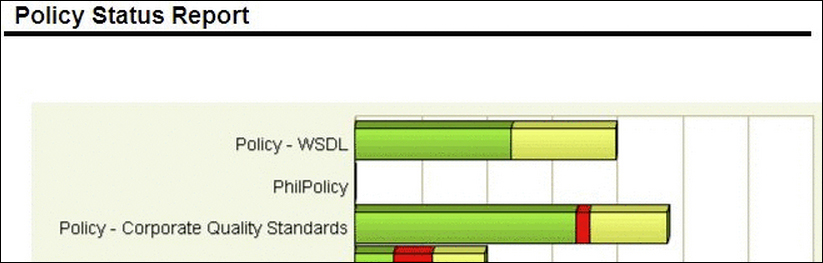
- Policy Status: This report provides a summary of all Policies in an organization's policy portfolio, and the number of Assets that are passing, failing, or have an unknown status. This report also shows a detailed list of the Assets that are governed by each policy, and the number of assertions that are passing, failing, or have an unknown status.