Chapter 1. Digital Evidence Is Everywhere
Information in this chapter:
• What is digital forensics?
• What is digital evidence?
• How digital evidence is created and stored
Digital evidence is everywhere and permeates every aspect of the average citizen’s life. No matter what you are doing these days, a digital footprint is probably being created that contains some type of digital evidence that can be recovered. Sending an e-mail, writing a document, taking a picture with your digital camera, surfing the web—all of these activities create digital evidence. This chapter will give an overview of what digital evidence is, how it is created, and where it is stored.
Keywords
Digital Evidence, Computers, Cell Phones, Digital Footprints, Electronic Storage, Electronic Data
Introduction
Digital evidence permeates every aspect of the average person’s life in today’s society. No matter what you are doing these days, a digital footprint is probably being created that contains some type of digital evidence that can be recovered. Sending an e-mail, writing a document, taking a picture with your digital camera, surfing the web, driving in your car with the GPS on—all of these activities create digital evidence.
1.1. What is digital forensics?
The term forensics can be defined as the application of science to a matter of law. The most accepted definition of digital forensics comes from the definition of computer forensics: computer forensics is the collection, preservation, analysis, and presentation of electronic evidence for use in a legal matter using forensically sound and generally accepted processes, tools, and practices.
Specifically, digital forensics is the application of computer technology to a matter of law where the evidence includes both items that are created by people and items that are created by technology as the result of interaction with a person. For instance, data created by a machine process requires that the machine be programmed to create data, and the machine must also be turned on by a person or even by an automatic process that is ultimately started by a person.
Data created as the result of an action performed by a person or user would result in data being recorded both manually and automatically.
The difference in those two types of data from an evidentiary standpoint is that when a computer or other device records data automatically through some process that is designed to be completed independent of user interaction, it is creating machine data; when data is stored or recorded in response to a user’s actions, it is creating personal data.
Personal data should ultimately be attributable to an individual; however, making that attribution can be difficult due to the presence or absence of individualized user accounts, security to protect those user accounts, and the actual placement of a person at the same location and time when the data is created.
1.2. What is digital evidence?
Digital evidence begins as electronic data, either in the form of a transaction, a document, or some type of media such as an audio or video recording. Transactions include financial transactions created during the process of making a purchase, paying a bill, withdrawing cash, and even writing a check. While writing a check might seem to be an old-fashioned method that is not digital or electronic in nature, the processing of that written check is electronic and is stored at your bank or credit card company. Nearly every kind of transaction today is eventually digitized at some point and becomes digital evidence: doctor visits, construction projects, getting prescriptions filled, registering a child at daycare, and even taking the pet in for a rabies shot.
In today’s connected world, it is nearly impossible to be completely “off the net” such that your activities do not create some form of electronic record.
The explosion of social media sites has created a whole new area of electronic evidence that is both pervasive and persistent. People today are sharing their everyday activities, their thoughts, their personal photos, and even their locations via social media such as Twitter, Facebook, and MySpace. Add to this the explosion of the blogosphere, where individuals act as citizen journalists and self-publish blog posts on the Internet ranging from their political views to their personal family blogs with pictures of their kids and pets.
In order for electronic data to become digital evidence, it must be stored somewhere that is ultimately accessible in some fashion; and it must also be recoverable by a forensic examiner. One of the great challenges today is not whether digital evidence may exist, but where the evidence is stored, getting access to that storage, and finally, recovering and processing that digital evidence for relevance in light of a civil or criminal action.
The potential storage options for electronic evidence are expanding every day, from data stored on cell phones and pad computers to storage in the “cloud” where a third-party service provides hard drive space on the Internet for people and businesses to store data.
More and more everyday computing processes are moving to the Internet where companies offer software as a service. Software as a service means that the customer no longer has to purchase and install software on their computer. Some examples of software as a service range from accounting programs like QuickBooks Online, Salesforce.com, or a sales management application to online games that are entirely played via the Internet with no required software installation on the local computer.
1.3. How digital evidence is created and stored
Whenever someone creates an e-mail, writes a document using Notepad or a word processing program, takes a ride in their car with the global positioning unit (GPS) turned on, or pays a bill online, they create digital evidence. Operating your computer, surfing the Internet, or making a phone call on your cell phone—all of these create digital evidence. Digital cameras, digital video cameras, web cams, and digital audio recorders all create digital evidence.
Those are the more well-known forms of digital evidence. However, it is easy to overlook the many ways in which we create digital evidence, many times without realizing we are doing so. If you play games online with other players, view videos from the Internet, shop at one of the thousands of online stores, create a shipping label through UPS, or even send a greeting card through Hallmark’s online site, you are creating digital evidence. And don’t forget about the copy machine at work. Chances are if it is a fairly new copier, scanner, and fax unit, it has a hard drive in it as well that stores data. That security camera you see yourself on at the local convenience store is making a digital record of your visit, as is the financial institution that processes the credit or debit card you just used to buy that pack of gum.
These days it is just about impossible to get through a day without creating some form of digital footprint. Even if you are completely “off the grid” and don’t use a computer or cell phone, running a red light where there is a traffic enforcement camera can capture your license plate, noting your location, and of course, sending you a ticket in the mail and creating a digital record with all of that information. Figure 1.1 shows some of the many ways digital footprints are created.
In the beginning the only storage device available for personal computers was the floppy disk or audio cassette tape. When you wanted to share a file or document with someone, you had to save it to a floppy disk or cassette tape. Then you would mail the diskette or use the old “sneaker net” and jog yourself and the diskette over to the person who needed the file.
Today the storage technology available for the average computer user has evolved into multiple storage options including the floppy disk and hard drives. The floppy disk is beginning to disappear as a primary form of storage in favor of USB (Universal Serial Bus) thumb drives, portable hard disks, and online storage.
As a result of this incredible growth in storage options, today digital evidence can be found on everything from floppy disks to media cards, solid-state memory sticks, solid-state hard drives, cell phones, network attached storage devices, game consoles, media players, hard drives, and the “Internet cloud.” The Internet cloud is a collection of companies that provide data storage and applications entirely based on having huge banks of servers and data stores, allowing businesses to access a large network and computer infrastructure without having to make large investments in hardware and software. This allows businesses and individuals to have these resources available on a monthly or usage fee basis. The attraction of cloud-based storage and services is that the hardware and software needed are maintained and updated by the service provider and not by the individual or business. This is very attractive when a business does not want to make huge capital investments in buying hardware and software that must be maintained, secured, and updated on a regular basis.
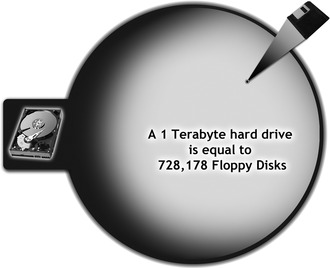
The high-density 3.5-inch floppy disk could store 1.44 megabytes of data. Today, a user can attach a multiterabyte hard drive to a computer simply by plugging the device into an available USB port. Figure 1.2 illustrates the growth in storage capacity sizes over time.
 |
| Figure 1.2 |
As more and more people take advantage of remote storage for backups using online backup services such as Carbonite, Mozy Pro, and other solutions offered to store data on the Internet via cloud storage, it is becoming more of a challenge to track down where all the data might reside in a forensic case.
And speaking of the “cloud,” there are now many applications and storage options available through such services as Google Apps, Google Docs, Microsoft’s Windows Live Skydrive, Apple’s Mobile Me, Dropbox, and many other Internet-based hard drive storage and data-sharing sites.
The most commonly used application for users who want to connect with one another is e-mail. E-mail is also one of the most commonly sought forms of digital evidence in all types of cases, civil, criminal, or domestic. In the early days of networked computing, e-mail was primarily a function of corporate networks that had some form of e-mail server such as Novell’s GroupWise, Lotus Notes, or Microsoft Exchange as well as various other types of server-based e-mail systems. There were e-mail programs that predated these applications; however, they are not of interest in this book because they are either not publicly accessible or they are no longer in service anywhere. While we could spend a lot of time covering all of the e-mail applications that have come and gone, detailing a complete history is not the purpose of the book. Our concern here is identifying digital evidence that you might encounter in legal actions today. E-mail can be stored on mail servers in large databases, on personal computers in the form of personal folder files, offline folder files, or e-mail databases created by the e-mail client being used.
In addition to corporate e-mail systems, there are now dozens of free public e-mail providers available to anyone with access to the Internet. Services such as Yahoo Mail, Microsoft’s Hotmail and Live Mail, America Online’s AOL Mail, Gmail, and dozens of others have made e-mail available to the masses. These accounts are typically free to use, require no real authentication of the user’s identity, and are widely used for both benign and nefarious purposes.
E-mail services like those previously mentioned are entirely browser-based, where the user reads and sends their e-mail via Internet Explorer, Firefox, Google Chrome, or Safari, to name a few. E-mails from these browser-based services can many times be found in the Internet cache on the computer. (See the section “How Internet Browser (Web) Caching Works” in Chapter 31). Online-only e-mail can also be recovered from the company that provides the free e-mail service such as Yahoo, Microsoft, Google, and America Online (AOL).
More recently, as the social media phenomenon has exploded with applications such as MySpace, Facebook, Twitter, and LinkedIn, a new area of digital evidence has emerged dealing with these online applications. Not only can users create and post their own personal user profiles via these applications, but nearly all of them support both their own e-mail and chat functionalities.
Internet chat rooms are popular not only with people discussing hobbies, but also with people who are into the swinging lifestyle, child predators, cyber bullies, and people who are conducting illicit affairs. These same chat rooms are frequented by law enforcement personnel conducting online investigations into child predator activities, where they pose as underage children and make arrangements to “meet” the child predator in a sting operation. You can see how this works by watching the popular “To Catch a Predator” series on MSNBC. These chat room types of applications have been around since the early 1990s in the form of Internet Relay Chat servers. America Online, CompuServe, and Prodigy also provided their users with chat services early on in their incarnation. Today, services like Yahoo Chat, MSN Chat, AOL Chat, mIRC, Facebook Chat, and dozens of others offer millions of users the ability to chat with one another, both one-on-one via a friends list or in public and private rooms created by the users themselves.
Internet chats can be hard to recover since many of the programs people use to chat with others do not store a log of the chats on their local computer by default. In some instances, chat logs are stored by the chat service provider and can be recovered via subpoena. Even though the chat program may not automatically be storing logs of the chats, many times fragments of the chats can still be recovered from the user’s hard drive.
Peer-to-peer file sharing has grown immensely in the last decade through the introduction of Napster, followed by Kazaa and LimeWire and finally BitTorrent. These applications create a way for personal computer users to form networks to share files, without any knowledge of how the networks operate or any special setup to get connected and start consuming and contributing to the shared content.
Since there is no central server or provider for peer-to-peer file sharing, there is no custodian of records to contact to obtain information. Any information that can be recovered from these applications must come from the computer that is using the peer-to-peer software.
Cellular phones began as radio telephones that could do no more than connect two phones over a short distance for the purpose of voice communications between two parties on the same radio network. Today, cellular phones are full-blown computers that can do everything a computer can do in a tiny package. Cell phones have become a gold mine of digital evidence. Whenever a cell phone is used to make a call, send an e-mail or text message, or used as a push-to-talk radio, a record is created by the cell phone company that can later be retrieved and used as evidence. The phones themselves record contact lists, call logs, pictures, video, e-mail, text messages, and in some cases, even GPS location information. Everything a cell phone does that uses the cellular network is recorded by the phone company. However, there are limits as to how long some of the data is stored by the phone company.
Digital cameras record not just pictures, but data about the pictures themselves. Inside the file created when the user snaps a picture, the camera records data such as the make and model of the camera, the date and time the picture was taken, the focal length and shutter stops. Depending on the model of the camera, there are many options for how the pictures are stored prior to being deleted or transferred to a computer or other storage device. Digital cameras can store their pictures on floppy disks, DVDs, CD-ROMs, and media cards.
Summary
In this chapter we learned what digital evidence is, how it is created, some of the places it is stored, and the many ways that people are now connected electronically. We also learned about digital footprints and how they are created not only by you, but by others on your behalf. Digital evidence is everywhere, and knowing where it is and how to get access to it is half the battle.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.

