Chapter 38. Video and Photo Evidence
Information in this chapter:
• The most critical steps in the forensic examination of video and photo evidence
• Using video and photo evidence in cases
Video and image evidence must be handled with great care, and any examinations or enhancements performed must be thoroughly documented. If the evidence is not received in the most viable format and preserved correctly, or if the examiner does not perform the forensic examination properly, it is possible to jeopardize the evidence by creating new evidence through the addition of image artifacts. In this chapter, we look at some of the ways that video and photo evidence is used in cases, and also at how evidence should be properly handled and enhanced. This chapter also shows some of the documentary methods that should be included with any enhancement to show exactly what was done in the enhancement process.
Keywords
Video, Photos, Enhancement, Workflow, Documentation, Artifacts, Photoshop
Introduction
The forensic examination of videos and images first requires that the evidence be collected properly, and requested properly. For information on how to get the evidence in the best possible way, and other supplemental information that can be critical in the examination of video and image evidence, refer to Chapter 18. Video and image evidence must be handled with great care, and any examinations or enhancements performed must be thoroughly documented. If the evidence is not received in the most viable format and preserved correctly, or if the examiner does not perform the forensic examination properly, it is possible to jeopardize the evidence.
38.1. The most critical steps in the forensic examination of video and photo evidence
It is critical that an examiner thoroughly document her work when performing video and photo examinations. One of the cornerstones of forensic methodology is that a process or examination method must be repeatable. If thorough documentation is not kept, it will hinder another examiner from being able to duplicate his work. An examiner should also understand how her video and photo enhancement tools work. If an examiner does not, then it is a plausible that the examiner could damage the evidence by adding visual information that is not in the original image when enhancing it.
38.1.1. Documentation
Documentation is paramount when examining video and photo evidence. The Law Enforcement/Emergency Services Video Association explains the necessity of proper and thorough documentation as follows:
The best way to ensure the reliability of the video evidence is to have standard operating procedures (SOPs) in place. SOPs assist the forensic video analyst inmaintaining proper records of the processes used to examine the evidence and that the processes are performed in a scientifically appropriate and uniformed manner. Records should be complete enough that a similarly experienced and trained individual, working with the same technology, could reproduce similar results.1
Just as with computer evidence, examiners dealing with video and photo enhancement needs to document everything they do in the process of their examination so that another expert can duplicate the results. Without this documentation, it would be extremely difficult and inefficient for another examiner to duplicate the results, if it could be done at all. Improper documentation also calls into question the viability of what the examiner produces in forensic analysis or enhancement, as the improper handling of video and image evidence can create visual information that did not exist in the original video or image, known as artifacts.
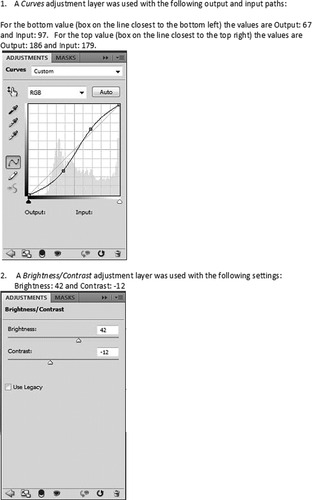
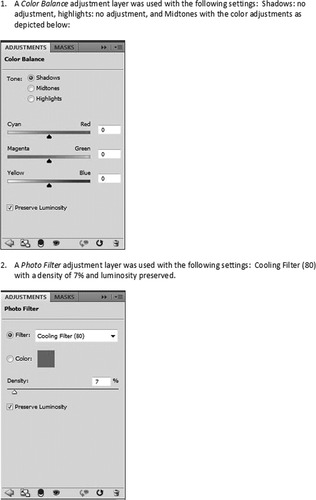
An example of how the workflow of the enhancement of video or photo evidence should be documented is shown in sequential steps in Figure 38.1, Figure 38.2, Figure 38.3, Figure 38.4, Figure 38.5, Figure 38.6 and Figure 38.7. With this information it would be possible for another examiner to duplicate the work exactly as the original examiner performed it.
38.1.2. Knowing how your tools work
An examiner who performs video or photo forensics should be able to explain what functions the tools they are using actually perform. If an examiner cannot do this, it calls into question whether or not he manipulated the image to show something that is not actually present in the original image. For example, many tools used in the enhancement of videos and photos allow for functions that increase the sharpness of the image, contrast, color correction, and so forth. If these enhancements are performed using a digital “brush” and painted on areas of the image, it can create detail that does not exist if applied incorrectly or too heavily. Figure 38.8 shows how an improperly enhanced image can distort the original and add additional information that was not present in the original.
 |
| Figure 38.8 |
Photoshop CS4 brush tools were used to enhance the picture of his face to try and pull out more detail. The brush tools were used in a manner that is not forensically sound, and as a result visual information has been created in the image that is not in the original. Notice that in the brushed image it looks as if Lars could have facial hair in this image, when in the original image he is actually clean shaven.
Similarly, if a filter performs functions such as sharpening to enhance an entire image or video at once, it can create artifacts and other detail in the image that does not exist in the original. This effect is shown in Fig. 38.9, which shows the same picture as seen in the previous figure. The image on the right was enhanced using filters in a method that is not forensically sound. If you look at his wrist, you can see that false visual information was created on the enhanced image. It now looks as if he could be wearing a watch or other item on his wrist. If this image was from a criminal incident, and a watch was of interest as an identifying item, this improper enhancement of the image could cause someone to believe that Lars was wearing that watch.
The necessity for examiners to understand how their tools work might seem like common sense, but it is often the case that they do not. If an expert cannot explain how his tools work, then in all probability he is not qualified to testify when it comes to the video or photo evidence.
38.2. Using video and photo evidence in cases
The most common usage of video and photo evidence in cases is either to attempt to identify a person or to capture a piece of evidence such as a license plate number or an object like a vehicle. In cases where there is surveillance video of a vehicle that may be suspected of being used in a robbery or murder, or a vehicle involved in a police pursuit, or traffic accident, identifying the vehicle’s make, model, color, and other features can be a big help. Working with photographs as evidence when the photo has been edited poses many challenges, including how much of the photo may have been altered and in what manner. If the original is available, a comparison of the original unaltered photo to the allegedly altered photo is the best means of detecting changes. However, in many cases, the original is not available and the detection must rely on an expert who can spot artifacts created by altering a photo or other image. The following section shows some of the ways that photos or videos can be altered by a skilled graphics artist and how the changes can be detected.
38.2.1. Enhancing an image or video
The most obvious way to use video and photo evidence is in the enhancement of these forms of evidence to aid in the determination of whether or not the video or image evidence is of any interest. Enhancement can be performed to aid in the identification of a person of interest, and items of interest within the environment can be displayed in a video or photo. It is also possible to determine that the evidence cannot be enhanced enough to be relevant.
38.2.2. Determining the authenticity of a video or image
Many of the same tools that allow for videos and images to be enhanced or examined can also be used to create falsified images or videos. Programs such as Adobe Photoshop and Adobe Premier are available to the public and are powerful editing programs. A skilled operator of these types of image and video editing programs can create convincing fakes of images and videos. A faked image can come in the form of counterfeit money, documents, and pictures of persons who are not actually in the original picture. Usually, fakes are not created completely from scratch, but are instead composites and modifications of already existing videos or images. However, adding visual information to a video or image, or taking it away, makes it as much a fake as one intentionally made by a scam artist. Even the most convincing faked images and videos can display telltale signs of modification that a skilled examiner should be able to identify and explain in details the methods used to create the fake. Adnan Hajj, a photographer, made the news in 2006 for modifying images he took for Reuters of an Israeli air raid on Beirut:
Mr. Hajj, a Lebanese photographer based in the Middle East, may not be familiar to many newspaper readers. But thanks to the swift justice of the Internet, he has been charged, tried and convicted of improperly altering photographs he took for Reuters. The pictures ran on the Reuters news service on Saturday, and were discovered almost instantly by bloggers to have been manipulated. Reuters then announced on Sunday that it had fired the freelancer. Executives said yesterday that they were still investigating why they had not discovered the manipulation before the pictures were disseminated to newspapers.2
In Fig. 38.10 the photo on the left is the image Adnan Hajj modified to make the smoke plumes caused by the air raid look more dramatic. If you look closely, you can see that parts of the smoke plume look exactly the same, which is a clear sign of tampering with an image. This type of modification is called “rubber stamping.” Look for the small circular artifacts in the smoke plumes. 2
In Fig. 38.11 the photo of Lars toting a toilet is again used as an example, this time of creating a fake photo through image editing with Photoshop. In the photo, the toilet has magically become a cash register!
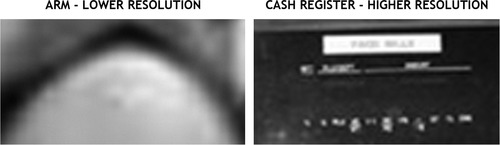
If we zoom in on the image and look at some of the details, we can see telltale signs that this is a fake image. Figure 38.12, Figure 38.13 and Figure 38.14 show some ways to detect that something was added to a photo after the fact, in this case, the cash register. In Fig. 38.12, compare the edges of the cash register to the edges of Lars’ arm. Notice that the register has much sharper edges, which indicate that the image of the register was added into this image from a higher quality image.
In Fig. 38.13, the shadow under Lars’ arm on the cash register is unnatural given the location of the light source.
In Fig. 38.14, if we zoom in very close to a portion of Lars’ arm, and compare that with a portion of the cash register, we can see that there are more pixels present in the image of the cash register. This is indicative of a merging of two images to make a fake, since one image is higher resolution than the other.
38.2.3. Contesting unqualified claims to video or image evidence
A common scenario is that a person will claim, from video or photo evidence alone, that they can identify a person portrayed in an image or video. While this is possible if the video or image is of high enough quality and resolution, often in these situations the quality of the evidence is poor at best. An appropriate response to such claims is to have the images enhanced as much as they can be without damaging them, showing that the person depicted in the video or image evidence cannot be identified based solely upon those forms of evidence. Having a video and image expert write an affidavit or testify to this effect can be beneficial when it is applicable to a case.
Summary
In this chapter we learned that video and photo evidence can be compromised if it is not handled properly in the process of being enhanced or analyzed by an examiner. We also learned that thorough documentation is critical when enhancing and examining video and image evidence so that another expert of similar training and experience can duplicate the work performed. We learned that a skilled examiner should know how his tools function so that he does not compromise evidence based upon inexperience or incompetence. We then learned how video and photo evidence can be used in cases.
References
[1]
[2]
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.