Chapter 36. Peer-to-Peer Networks and File Sharing
Information in this chapter:
• What is peer-to-peer file sharing?
• How it works
• Privacy and security issues with peer-to-peer file sharing
• Peer-to-peer network evidence
There is no “server” needed for peer-to-peer file sharing. Every computer connected to the network is both a server and a workstation. As of this writing, one of the largest of the file-sharing companies, LimeWire, has been ordered to cease operations. However, the file-sharing community is still alive and well thanks to the many other providers of this type of software and services, such as FrostWire, BearShare, BitTorrent, and dozens of others.
Keywords
LimeWire, BearShare, Phex, FrostWire, Peer to Peer, File Sharing
Introduction
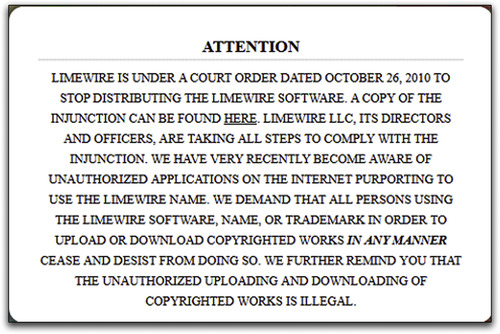
There is no “server” needed for peer-to-peer file sharing. Every computer connected to the network is both a server and a workstation. As of this writing, one of the largest of the file-sharing companies, LimeWire, has been ordered to cease operations as the result of a civil lawsuit. The official notice they have placed on their website can be seen in Fig. 36.1. However, the file-sharing community is still alive and well thanks to the many other providers of this type of software and services, such as FrostWire, BearShare, BitTorrent, and dozens of others.
36.1. What is peer-to-peer file sharing?
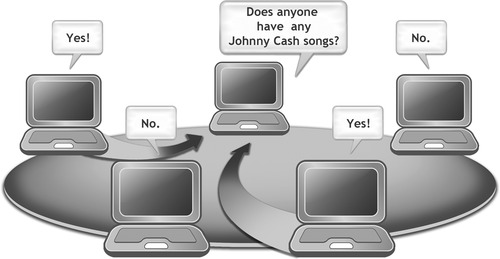
The basic premise of peer-to-peer file-sharing networks is to allow people who want to share files on their computer to freely connect with other persons of like mind without having to know anything about how the network operates or anything about other computers on the network.
Every computer in a file-sharing network can be both a client and a server, and the methods for connecting them together into one huge network are all handled by the file-sharing software. Figure 36.2 shows an example of what a file-sharing network looks like.
36.2. How it works
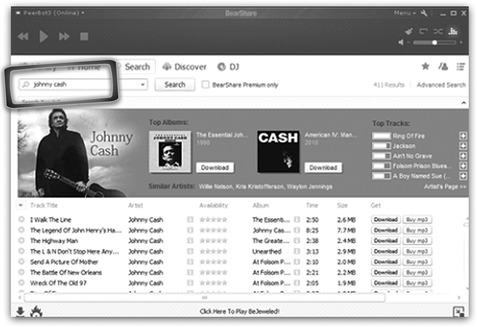
The first part of this chapter contains examples of file-sharing programs for the purpose of providing some background in this type of software. From a user’s standpoint, peer-to-peer file sharing is no more complicated than finding and installing a software application. In this section two popular file-sharing programs are examined, FrostWire and BearShare. One of the most simplistic of these programs is BearShare. The opening installation screen for BearShare is shown in Fig. 36.3.
During the installation process, the user is not asked much of anything. It does require that you create an account, but in testing, fake e-mail addresses (that do not exist) were found to work just fine. BearShare does not attempt to authenticate the e-mail address, or require that you respond to an e-mail to confirm that you are a real person using a valid e-mail address. Once the program installs, it will start automatically and the user can start downloading right away. The BearShare program is shown in Fig. 36.4.
36.2.1. It’s all about sharing!
Since the whole purpose of file sharing is to share, BearShare does not ask the user if they want to share their files. It just assumes that to be the case. Also, these programs can make it very hard for a user to turn off file sharing by hiding the settings for file sharing deep in their menu systems, if the program allows file sharing to be turned off at all.
36.2.2. Using a file-sharing program
These programs are centered on searching for keywords for the content the user wants. For instance, a search for the keyword Johnny Cash is used in all of the programs selected for examples in this chapter.
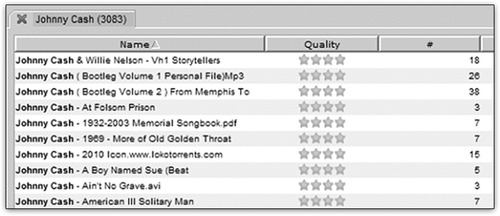
In this example all the user has to do is enter the keywords Johnny Cash and click on the search button to get a screen full of files that can be downloaded. Figure 36.4 and Figure 36.5 show the results of the keyword search in BearShare and in FrostWire.
What is interesting about both of these programs is the ability of the user to select multiple files at once and start downloading them all. This can lead to a user carelessly selecting files he doesn’t really want to download, resulting in the possibility of unintentionally receiving contraband files, copyrighted music, and software on their computer. Since a user does not have to actively click on each download, the likelihood of that user carefully reading the file description information is decreased. When downloading from peer-to-peer networks like FrostWire, it is common for many of the downloads to be fake or low quality, or for the download process not to work at all.
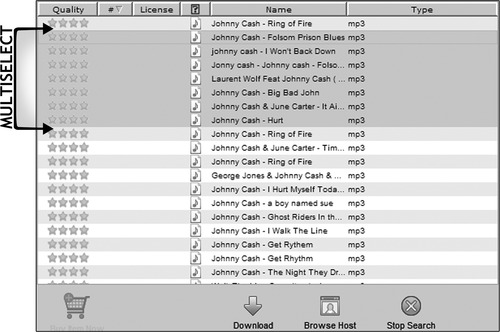
This can encourage a user to select multiple files at once, as in the example shown in Fig. 36.6, where they could select dozens of Johnny Cash songs at once to increase their chances of getting the music they want.
36.3. Privacy and security issues with peer-to-peer file sharing
When a user is connected to a file-sharing network with this type of software, the program can share information without the user’s knowledge, such as the files they are sharing and the Internet protocol address of the computer’s Internet connection.
Many users do not understand that careless installation of file-sharing software can put their personal information at risk. While doing the research for this chapter, personal tax returns, personal and business financial statements, tax ID numbers, contracts, legal settlement offers, and other personal documents that people are sharing on the peer-to-peer network were downloaded. This illustrates that using this kind of software can expose a user’s personal information to the world even when they do not intend to share anything at all.
36.4. Peer-to-peer network evidence
A great many cases involving child pornography stem from law enforcement personnel gathering evidence via the peer-to-peer networks. The Internet Crimes Against Children (ICAC) task force is aggressively funding federal, state, and local law enforcement agencies to enable them to perform investigations of child abuse including peer-to-peer network investigations of the distribution and receipt of child pornography.
In the fiscal year of 2008 and the first three quarters of fiscal year 2009, the ICAC trained 58,000 law enforcement personnel and 4,032 prosecutors. During that same time period ICAC investigations led to over 6,400 arrests. The ICAC program today is a national network of more than 3,000 federal, state, and local law enforcement agencies. 1
In addition to contraband material investigations, the Recording Industry Association of America (RIAA) has been aggressively pursuing persons sharing copyrighted music via the peer-to-peer networks for several years now and has filed thousands of lawsuits against file sharers.
Investigators and law enforcement agencies collect evidence during peer-to-peer investigations using various tools and techniques, some designed specifically for the purpose of locating files and gathering evidence about sharing computers.
36.4.1. Investigating file-sharing networks
Suppose you were interested in locating people who are sharing particular files. How would you go about finding out if those files were present on the peer-to-peer network and then how would you go about locating the source of those files?
If you wanted to find a particular file on the peer-to-peer network, you would develop a special software application that could search for files, not just by keyword, but also by the SHA1 hash. Hash values are covered in Chapter 4 and Chapter 26.
The SHA1 hash is like a fingerprint for a file. If you find a file on the network with a SHA1 hash matching your file of interest, you could be confident that the file had been present on the network at some point.
Another file-sharing program, Phex, shows how easy it is to find information about someone’s file sharing. In Fig. 36.7, the search results window in Phex is shown for the keyword Johnny Cash. The sharing host gives the IP address of the Internet connection in use by the computer sharing the files. The SHA1 column gives the hash value of the file being shared.
 |
| Figure 36.7 |
The highlighted file matches (in this imaginary scenario) the SHA1 you are looking for.
Now that you have located a matching file, your next step is to see if the computer sharing the file is in an area of interest to you.
The Sharing Host IP address here is the key. You can find out who owns the IP address by using tools available for looking up this information, such as the lookup tools provided by websites like DNS Stuff (www.dnsstuff.com). This will typically lead to an Internet service provider like Time Warner, Verizon, or some other company that provides Internet access to consumers.
Meanwhile you might want to see if the computer sharing the one file has other files you are interested in. In Phex and many other file-sharing programs you can request that the program perform a Browse Host to see what other files that particular computer is sharing. However, bear in mind that even performing a Browse Host on a particular IP address is not a guarantee that the files listed are actually available to be downloaded. The results of a Browse Host command executed using the Phex file-sharing program are shown in Fig. 36.8.
 |
| Figure 36.8 |
In order to verify that the file of interest really is on the computer, a step that can be taken is to perform a direct download of a file from a particular sharing computer. Care must be taken to ensure that the file is downloaded only from the single host to verify that the file actually came from that host IP address. Figure 36.9 shows a file being downloaded only from the host computer of interest.
 |
| Figure 36.9 |
In Fig. 36.9, note that the # Candidates is shown as one / zero / one, meaning that the file is being downloaded from the single host and is not being assisted by other sharing computers.
However, it is important to remember that all of the evidence you have gathered in this scenario does not lead necessarily to an individual person, even if you can locate the physical address of the Internet subscriber assigned to the IP address at the time of the investigation. You would still need to locate the individual computer and perform a forensic examination to verify that the files are on the hard drive and that the files were in fact downloaded by the individual of interest.
A man was arrested for downloading child pornography on his girlfriend’s laptop computer using LimeWire. The computer was examined by law enforcement personnel and subsequently by the defense expert. The defense expert examined the hard drive and located the child pornography files along with the timeline of when the files were downloaded. He also examined the user profile information under which the downloads were made. It was discovered that the defendant did not have a password to access the profile that was logged in during the downloading and that the file-sharing program was installed under this password-protected user profile. The accused did have a user profile on the computer that was not password protected. However, the accused’s profile had not been logged on for some months prior to the downloading of the child pornography. Based on other evidence, it was learned that the accused did not have possession of the computer during the time in which the downloads occurred. This was a clear-cut case of a revenge setup, and all of the child pornography charges against the defendant were dropped.
Warning
We want to emphasize that the example scenario in this chapter is oversimplified and that the actual investigation of a peer-to-peer file-sharing case is complicated and must be analyzed on both sides with care to ensure that the evidence is authentic and verifiable.
Cases like the one shown in the case study tend to be the exception rather than the rule in file-sharing cases involving contraband files. And in many cases the evidence seems insurmountable when someone is arrested for downloading contraband files via the file-sharing networks. Even though evidence presented by a law enforcement examiner might seem cut and dried to someone not familiar with how peer-to-peer networking operates, depending on the claims made, the interpretation of peer-to-peer evidence in a case can have a significant impact on the outcome of the case. As with any form of digital evidence being presented, the evidence should be properly verified and not viewed in isolation without considering all of the facts that may come to light if the evidence is reviewed by another examiner. Based on experience as examiners in hundreds of cases, we have found that proper interpretation of evidence in light of the totality of the circumstances is a critical aspect of handling cases involving electronic evidence.
Summary
In this chapter we looked at peer-to-peer networking and how it works. We discussed some of the privacy issues related to peer-to-peer file sharing and how evidence is gathered using information revealed to the public by file-sharing software.
Reference
[1]
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.