Chapter 4. The Foundations of Digital Forensics
Best Practices
Information in this chapter:
• Who establishes best practices?
• Who should be following best practices?
• Summary of best practices
• What really happens in many cases
Digital forensics is a relatively new field compared to traditional forensic sciences. Digital forensics began as computer forensics in the early 1990s and has expanded with the introduction of new technology such as cellular phones, digital cameras, global positioning devices, and the explosive growth of Internet usage. With that comes the issue of whether or not there are established best practices and who is following them. What best practices should digital forensics examiners be following, why, and what are they really doing?
Keywords
Acquisition, Collection, Identification, Verification, Preservation, Evidence, Forensic Examiners, First Responders
Introduction
This chapter looks at who establishes best practices and what those best practices are. Specifically, this chapter provides a narrative of the processes for the collection and preservation of electronic evidence by forensic practitioners and first responders. This is not a step-by-step forensic collection manual, but an overview of the steps that should always be taken in the collection and preservation of electronic evidence, based on industry accepted best practices, when the evidence is being collected on scene or later on in the lab. It is important to know these best practices when assessing the validity and admissibility of evidence collected by anyone.
4.1. Who establishes best practices?
Guidelines published by the National Institute of Justice and the Association of Chiefs of Police set minimal standards for the collection and preservation of digital evidence. These guidelines are developed with the participation of law enforcement, government, academic, and industry practitioners. The best practices are then propagated to the industry through publications and digital forensic training programs. Certifications for persons in the field, such as the EnCase Certified Examiner (EnCE), the Computer Certified Examiner (CCE), the Access Certified Examiner (ACE), the Computer Forensics Certified Examiner (CFCE), and the GIAC Certified Forensic Analyst (GCFA), to name a few, reinforce these best practices by ensuring that the person being certified has a grasp of the proper procedures to correctly collect and preserve electronic evidence. These certification programs are covered in more detail in Chapter 9.
4.2. Who should be following best practices?
Anyone who proposes to work as a computer or digital forensics examiner should always follow the established best practices in the field. This is vitally important in a field where the results of the examiner’s actions are to be used to provide evidentiary findings based on the collection, preservation, and analysis of evidence. Failing to follow accepted best practices leaves the work of the forensic examiner open to challenge and the possibility of the evidence collected being suppressed. The very least of the results of failing to adhere to accepted minimal best practices in the collection and preservation of evidence can be to cast doubt on the skills and qualifications of the examiner and the entirety of the examiner’s work and potential testimony. It is also highly likely that an examiner will be questioned about these best practices when testifying in court.
4.3. Summary of best practices
Best practices apply to the collection and preservation of evidence. These are the two critical parts of ensuring that evidence will be accepted in a court of law as being authentic and an accurate representation of the original evidence. Modification of evidence, either intentionally or accidentally, can have a devastating effect on the entire case. Understanding best practices is critical for the legal professional so that attorneys and judges can properly assess the authenticity of the evidentiary findings. This is also critical for business and information technology professionals to understand that even if they are preserving evidence for the possibility of future litigation, these practices must be followed to protect the evidence.
If we look at preserving evidence as the overarching part of the collection and acquisition of digital evidence, we can see that the need to protect and preserve evidence begins before anything is collected, copied, or analyzed, and ends only at the final disposition of evidence. Whether that final disposition is to return the items collected to the owner, permanent seizure of the items by the government, or the destruction of that evidence via a destruction order, the preservation of the evidence must persist. In the digital forensic field, preservation is the overall protection of evidence, while acquisition is the actual act of making forensic copies of digital evidence either from hard drives, some other physical media, or live memory.
4.3.1. Volatile data and live forensics
Some evidence is only present while a computer or server is in operation and is lost if the computer is shut down. Evidence that is only present while the computer is running is called volatile evidence and must be collected using live forensic methods. This includes evidence that is in the system’s RAM (Random Access Memory), such as a program that only is present in the computer’s memory. These programs are considered TSRs or Terminate and Stay Resident programs. Many types of malware such as Trojan horse programs, viruses, and worms are designed to be only memory-resident programs, present in the computer’s memory when it is operating, and they disappear when the computer is turned off, in many cases leaving no traces. There are also many types of other volatile evidence that are only available while the computer is running, including certain temporary files, log files, cached files, and passwords. RAM is cleared when the computer is turned off and any data that is present is lost. This can be a critical step if there is suspicion that any kind of data encryption is enabled that prevents the hard drive or portions of the hard drive from being viewed. In many cases the only way to recover the password needed to remove the encryption on a hard drive is to collect the “live memory” before the computer is turned off. Also, if the computer is running, the encrypted portion of the data storage would be accessible, but only until the computer is turned off, making it essential that the hard drive is copied while the computer is still turned on. There are tools available to make copies of RAM and hard drives on running computers and line-of-business servers that cannot be shut down, and still ensure that those copies are forensically sound.
4.3.2. Preservation best practices
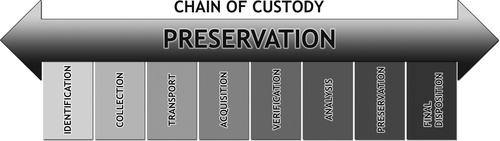
As evidence is collected, it must be preserved in a state that is defendable in court. Preservation is the process of creating a chain of custody that begins prior to collection and ends when evidence is released to the owner or destroyed. Figure 4.1 shows the preservation process in graphical form.
Preservation steps include:
• Identification: Identifying the type and location of digital evidence can be a challenge. In order to prepare a subpoena or search warrant, it is critical to include any location and item in which digital evidence may reside in that particular case, including but not limited to computer hard drives, cell phones, digital cameras, GPS devices, and personal storage devices such as portable USB hard drives and even media players like iPods. This is the first step that precedes collections. It is not acceptable to simply collect everything once you get to a scene; what you are going to collect must be previously identified in search warrant language and in civil subpoenas in order for the collection to be legal and allowable in a court of law. Collecting items not previously identified can cause that evidence to be suppressed in a legal action. Identification language must be specific and must have correct terminology; using language such as “CPU” instead of computer would mean that you can collect only the Central Processing Unit of a computer and not the computer itself. Collecting the CPU would be a waste of time since it does not contain any storage. Using language in which you specify collecting the “hard drive” would allow you to remove and collect the hard drive inside a computer, but not the computer itself. While the hard drive would contain evidence, you would not be able to verify the clock setting for the computer without access to the computer as a unit. This could lead to a challenge relating to the time stamps on files and activities on the computer hard drive since you would not have a method for verifying the time setting on the computer that created the time stamps. For more information, see Chapter 30.
• Collection: The collection step is critical since this is the first real contact with evidence. Not following proper collection procedures can lead to the destruction or modification of evidence, lost evidence, and subsequent challenges of the evidence collected. If someone attempts to collect a device and does not understand the proper methods to shut down the computer, operates the computer prior to shutdown, or shuts down a critical business server improperly, it can lead to data loss, civil liability for lost business, and the loss of critical evidence that could be collected prior to shutdown. Collection may include any or all of the following:
• Photographing the evidence in place prior to collection or duplication.
• Completing a complete inventory of each item including identifying information such as serial numbers, manufacturer, and descriptions.
• Tagging each item for tracking and identification.
• Securing each item to prevent inadvertent operation. This includes placing tamper-proof tape over power outlets, CD-ROM drives, USB ports, and floppy disk trays.
• Bagging each item in a forensically sound manner, into a secure container that is sealed with tamper-proof tape to ensure that the evidence is not modified or damaged during transport.
• Placing collected items in secure storage areas.
• Proper check-in and check-out procedures with a maintained chain of custody for any access to or movement of the evidence.
• Final disposition of the evidence, recorded in the chain of custody for any evidence that is released or destroyed.
4.3.3. Acquisition best practices
Acquisition is the part of the forensic process during which actual data is copied or duplicated. Following proper procedures is critical to ensure the integrity of evidence. The acquisition portion can be further broken down into two steps: duplication and verification.
• Duplication: This is one step that is easily performed incorrectly, especially if it is performed by someone who is not trained to properly duplicate electronic evidence. The only accepted method for duplicating electronic evidence requires that the original be protected from any possibility of alteration during the duplication process. This requires the use of accepted tools and techniques that allow the duplication of the evidence in a forensically sound manner. Using nonforensic methods will always lead to modification of the original evidence and/or incomplete copies of the original evidence that cannot be verified using forensic methods.
• Forensic method: The proper forensic method for duplicating evidence from a computer hard drive or other media storage device requires the use of write-blocking of the original storage device. Write-blocking can be accomplished either by using a physical hardware device that is connected between the original (source) and the copy (target) hard drive (see Figure 4.2) or by using a special boot media that can start a computer in a forensically sound manner.
 |
| Figure 4.2 |
The best option for making a forensic copy of a hard drive is to remove the hard drive from the computer, connect it to a physical write-blocker, and then use a forensic workstation and forensic software to make the copy. However, in some cases it is not practical to remove the hard drive. The computer may be of a type that makes the hard drive removal very difficult, such as some types of laptop. When this is the case, making a copy of the hard drive using a software write-blocking technique is the correct method.
To use a software-based write-blocking method, the computer must be started up in a forensically sound manner.
When a computer is first turned on, it goes through a set of steps, beginning with a Power On Self-Test (POST), followed by loading of the Basic Input Output System (BIOS). The BIOS is software that is stored on the main board of the computer that tells the computer what types of hard drives are present; initializes the keyboard and other input and output ports, such as the USB ports; initializes the computer video card; and basically prepares the computer hardware to operate before it can load the operating system software. Settings in the BIOS tell the computer where to look for the operating system to start up, such as on a hard drive, from a floppy disk, a CD-ROM, or a USB device.
During normal operation, the computer will load the operating system installed on the hard drive, such as Microsoft Windows or the Mac OS. It is possible to prevent the computer from loading the operating system that is installed on the hard drive in favor of loading an operating system from a CD-ROM, floppy disk, or USB device.
When preparing to perform a forensic copy of a computer’s hard drive(s), a forensic examiner would force the computer to load a special forensic operating system from a specially prepared boot media. This can be done by changing the settings in the computer BIOS to tell the computer to look for an operating system on a CD-ROM, a USB device, or a floppy disk. This can also be done by pressing a function key when the computer is first turned on to bypass the default setting in the BIOS for the startup location for the operating system. For instance, pressing F9 on many computers will bring up a menu where the examiner can choose which device to use to load the operating system. This can also be done on a Mac by pressing and holding the C key while powering on the computer.
This boot media can be a floppy disk, CD-ROM, or USB device that is specially prepared to load a forensically sound operating system. This is critical because when a computer starts up (boots) normally from the installed operating system, whether Windows or Mac OS or Linux, these operating systems automatically “mount” the hard drive(s) in read/write mode. This allows the user to read and write files, such as documents, to and from the hard drive.
Special boot media is media that contains an operating system that can start a computer up, but does not allow writing to the original hard drive. These forensic operating systems are modified to effectively turn off the ability of the computer to make any changes to the hard drive(s).
Once the computer is started up, either with a hardware write-blocker in place or by using a forensic operating system, the forensic examiner would make a forensic copy of the hard drive(s) installed in the computer.
Making a forensic copy of a hard drive means getting a “bitstream” copy, which is is an exact duplicate of the entire hard drive recording surface.
• Nonforensic Method: Personnel not trained in the proper forensic methods for duplicating electronic evidence may start a computer up and then make copies of the data on the hard drive. When a computer is started up in this manner, the operating system can write to the hard drive and change file dates, change log files, and other types of files, effectively modifying and destroying critical evidence. Figure 4.3 shows two hard drives connected without any protection in place for the original evidence hard drive, putting the evidence at risk.
Nonforensic methods usually include just simply copying files from a hard drive to another storage device or using a backup program like Norton Ghost. While Norton Ghost has the ability to make a forensically complete (bitstream) copy, it is not generally accepted as forensically sound because Ghost copies are difficult to verify using hash values. (Hash values for verification are covered in detail in Chapter 26.) The reason for this is that Norton Ghost does not have a method for creating a hash value of the evidence being copied during the copy process. Additionally, a nonforensic copy of a hard drive will get only the data stored on the hard drive, such as documents, spreadsheets, and Internet history. A nonforensic copy will not get deleted files or areas of the hard drive where evidence can still reside that is not visible to the computer user.
• Verification: This is the final step in the forensic copy process. In order for evidence to be admissible, there must be a method to verify that the evidence presented is exactly the same as the original collected. Verification is accomplished by using a mathematical algorithm that calculates a number based on the contents of the evidence. Figure 4.4 illustrates the drive and file hashing process used to calculate the verification hash.
 |
| Figure 4.4 |
This is called creating a “hash value” and is performed by using either the Message Digest 5 (MD-5) algorithm or a Secure Hash Algorithm (SHA). The MD-5 is the most commonly used method for verification in computer forensics at this time. Forensic duplication tools automatically create a “verification” hash for the original and the copy during the duplication process. If these hash values do not match, there is an opening for a challenge to the authenticity of the evidence as compared to the original.
4.4. What really happens in many cases
The propagation of computers, cell phones, and other digital devices as potential evidence has far exceeded the resources of law enforcement to properly dissimilate and train crime scene first responders in the proper best practices for handling this evidence on scene and in custody. In many cases, law enforcement personnel will modify evidence accidentally, simply because they do not have the training, or their department has not had the opportunity to establish procedures for handling digital evidence.
On the civil side, due to the lack of qualified examiners for hire, private attorneys are using computer support personnel rather than forensic examiners to collect and process evidence. This is especially true in small civil cases and domestic cases. Computer personnel are not trained in these best practices and are not following any type of methodology to protect and preserve the original evidence; not only is the training a prerequisite for following best practices, but the proper tools for the collection and preservation of the evidence are required as well. Lacking knowledge of best practices goes hand in hand with not having and applying proper tools for safe collection of evidence.
Summary
In this chapter we covered who establishes best practices for the collection and preservation of evidence, by looking at some of the organizations who publish best practices and some of the certifications that include best practices in their programs. We also discussed what those best practices are, including the specific parts of the best practices for handling digital evidence. Finally, we looked at who should be following these best practices and why some examiners are not following them.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.