Chapter 27. Metadata
Information in this chapter:
• The purpose of metadata
• Common types of metadata
Metadata can be a veritable gold mine of useful information in a case. The prefix meta in English is used to express the idea that some information is about its own category. Hence the meaning of metadata is “data about data,” just as metacognition means “knowing about knowing.” While this might seem somewhat cryptic, when you get down to the nuts and bolts, metadata is not hard to understand. Metadata is found inside a file, kind of behind the scenes where an ordinary computer user will not see it. It stores useful information that the operating system uses to make a computer user’s experience easier and more enjoyable. The information stored within metadata can be used to build timelines, establish alibis, and so much more. In the hands of a skilled digital forensics expert, metadata can shed light on a particular issue in a case, or be the turning point altogether. In our experience as examiners, we have seen tiny snippets of metadata change how entire sequences of events were interpreted.
Keywords
Metadata, Picture Metadata, File System Metadata, Document Metadata, PDF Metadata
Introduction
Metadata can be a veritable gold mine of useful information in a case. The prefix meta in English is used to express the idea that some information is about its own category. Hence the meaning of metadata is “data about data,” just as metacognition means “knowing about knowing.” While this might seem somewhat cryptic, when you get down to the nuts and bolts, metadata is not hard to understand in principle, but can be confusing in detail. Metadata can be found inside a file, kind of behind the scenes where an ordinary computer user will not see it, or in an external data store such as Internet history files that record information about files.
The information stored within metadata can be used to build timelines, establish alibis, and so much more. In the hands of a skilled digital forensics expert, metadata can shed light on a particular issue in a case, or it can be the turning point altogether. In many cases, tiny snippets of metadata can change how entire sequences of events are interpreted. However, a word of caution about metadata: Metadata alone, like any snippet of digital evidence, is rarely enough to “prove” something. Nearly all digital evidence requires some type of corroboration through a combination of evidence, electronic or otherwise. Relying on a single piece of electronic evidence can lead to misunderstandings without properly establishing a foundation for that evidence.
27.1. The purpose of metadata
The purpose of metadata is to store information about other data. This can help with the organization and retrieval of data. For instance, web pages on the Internet have metadata in such forms as meta-tags. A meta-tag is coded into a website where you do not see it, but it contains information about a website, such as keywords so that it can be easily found when those keywords match your Google search. Metadata can also be found inside many pictures and videos, containing copyright information if there is any, as well as information such as when the picture was taken and the make and model of the camera the picture was taken with. Or, as in the case of office documents, when searching for a document in Microsoft Windows, you can choose to search for documents by the author, the creation date, the last modified date, and so forth. All of this information is contained in the document’s metadata.
27.2. Common types of metadata
In the following sections, the more common types of metadata are discussed as well as where the metadata can be found and how it is used as evidence.
27.2.1. File system metadata
File system metadata includes the times recorded by the operating system when a file is modified, accessed, or created. File system metadata is easily misinterpreted and can be very difficult to understand. For this reason, file system metadata is covered in detail in Chapter 30.
27.2.2. Internet metadata
There are two types of Internet metadata:
1. Web page
2. Browser metadata
27.2.2.1. Web page metadata
Metadata for web pages is contained within the “code” of the web page and is in the form of meta-tags, page titles, page headers. and meta-descriptions. While this type of metadata can be interesting, it is almost entirely controlled by the user who creates the web page and rarely offers very much in the way of forensic value. The original purpose of web page metadata was to assist search engines such as Yahoo or Google in finding and indexing web pages. However, widespread abuse of meta-tags, keywords, and meta-descriptions has resulted in modern search engines largely ignoring this metadata in favor of actual page content.
If you examine the web page metadata in Fig. 27.1, you will notice that what the metadata does not contain is any information about when, where, or by whom the web page was created. This web page could have been created on a computer and never published to the web. If this is the only evidence you have, you have no evidence at all. This is why web page metadata is of limited value in a forensic examination.
27.2.2.2. Browser metadata
While it is not commonly referred to as metadata, the history stored by Internet browsing programs certainly qualifies as data about websites and pages that have been visited, and websites or pages marked as favorites by the user. Browser metadata is used extensively as forensic evidence in all kinds of cases. The screenshot in Fig. 27.2 is from the program NetAnalysis by Digital Detective (www.digital-detective.co.uk) and shows the result of an Internet history analysis from a computer hard drive.
27.2.3. Document metadata
Document metadata is metadata stored inside a document that provides information about the authorship, editing time, and even the computer on which the document was created. All of the major office suites such as Microsoft Office, WordPerfect Office, OpenOffice, and Star Office record metadata in some form inside the word processing documents, spreadsheets, and presentations created with the programs in these suites. Figure 27.3 is a screenshot of a Microsoft Word document as viewed in a metadata viewing program.
As you can see in the example shown in Fig. 27.3, office document metadata contains a wealth of information about the life of the document. In this example we see the name of the original author, who last saved the document, the original creation date, the date it was last printed, and the date it was last saved. Toward the bottom of the figure you can see the file system metadata also recorded inside the document including the file path, and the file system created, modified, and last accessed dates and times. You can also see the different hash values for the document. Hash values are covered in Chapter 4 and Chapter 26.
In addition to office documents, Adobe Portable Document Format (PDF) files also contain metadata. Figure 27.4 is an example of a Microsoft Word document after it has been saved as a PDF document and viewed in a PDF metadata viewer.
27.2.4. Picture metadata
Picture metadata can contain information about the make and model of the camera used to take the picture or about the software used to modify a picture. In the example in Fig. 27.5 you will see that the image was modified using Adobe Photoshop CS. When a photo has been modified using a program like Adobe Photoshop, the original camera information can be lost. However, the metadata will contain the name of the editing program that was used to modify the picture.
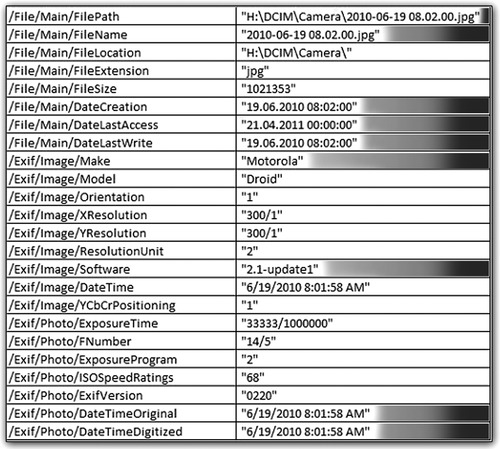
Figure 27.6 shows the metadata contained inside a picture taken with an Android phone. Instead of the camera make and model, in this instance you can see the make of the cell phone, a Motorola Droid, and the currently installed version of the phone’s imaging application, 2.1-update 1.
Metadata and Timelines
There was a case where a man was accused of molesting a girl while taking pictures of her using a camera. The pictures were innocent in content. While this girl and her family were visiting his home, she asked the accused to take pictures of her for her MySpace page. In the girl’s recount of the events, the molestation was said to have happened over a 30-minute period, where the accused was supposedly taking pictures of her, and in between taking the pictures was molesting her. A review of the metadata in the pictures showed that the entire picture-taking session lasted a total of four minutes and forty-six seconds. By examining the metadata of the first and last picture, the entire time period of the picture-taking session could be shown, and by looking at all metadata for all the pictures, it was revealed that no two pictures were taken more than 30 seconds apart. This information was critical in refuting the charges, as the picture metadata painted an entirely different picture than the girl’s story. What she claimed to have happened would have been physically impossible to have occurred in a timeframe of four minutes and forty-six seconds.
A good example of document metadata as evidence is not from the biggest or most complicated case. In fact, it is from a rather simple case, but it does highlight the usefulness of document metadata in an exemplary way. The case involved a student who submitted a paper from one of his classes at a university. The professor, upon reading the paper, did not believe that the student was smart enough to have written it. The student was accused of cheating, and subsequently kicked out of school. The professor claimed that the student must have plagiarized the paper from sources on the Internet.
The document metadata revealed that the paper was written over a period of several days, included 33 separate editing sessions and a total writing time of over 800 minutes. This indicates that the student did actually compose the paper on the computer on which it was found. However, that alone is not enough. Using key phrases and terms from inside the paper to perform a search of the student’s hard drive, it could be shown that no other references were on the computer hard drive that could have been copied and pasted into the paper.
The results of this investigation showed that the paper did not indicate any plagiarism from Internet sources or other documents on the computer.
Summary
In this chapter we looked at what metadata is, what it looks like, and how it can be used in cases. We also learned that the use of metadata should be tempered with caution as to corroborating the evidence with other evidence. Many cases will contain a combination of metadata from different sources; for example, picture metadata may be used in conjunction with document metadata to show that pictures contained inside a document or e-mail were taken using a camera model that is also in evidence.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.