
Policing 305
designed or intended to be application-friendly. Policing either transmits a conforming
frame, or polices based on the configured contract. The (2 * burst) or (2 * RTT * rate)
recommendation is meant to be only a starting point. To obtain the desired results, you may
have to further modify the burst parameter after observing the behavior of the traffic,
Configuring the Single-Rate Policer
To configure and verify single-rate policing in Hybrid and Native modes, use the following
commands:
(Hybrid)
set qos policer {microflow | aggregate} {
name
} rate {
rate
} burst {
burst
} {policed-
dscp | drop}
show qos policer {config | runtime} {all | aggregate | microflow} [
name
]
show qos statistics { l3stats | {aggregate-policer [
name
]}}
(Native)
mls qos aggregate-policer {
name
} {
rate
} [{
burst
}] violate-action {drop | policed-
dscp-transmit | transmit}
police aggregate {
name
}
show mls qos aggregate-policer [
name
]
show mls qos ip {
type
num
}
When the aggregate policer is configured in Native mode, the command is applied under
the policy map class. The aggregate policer is referenced by configuring police aggregate
{name}. The {name} parameter can be up to 31 characters long and is case sensitive. The
policer name may include a–z, A–Z, 0–9, the dash character (-), the underscore character
(_), and the period character (.). Policer names must start with an alphabetic character. They
must also be unique across all microflow and aggregate policers. Keywords cannot be
utilized from any command as a policer name.
The valid range for the rate and erate parameters is 32 kbps through 32 Gbps, for Hybrid.
For Native mode, the maximum rate is 4 Gbps. To classify all traffic as out of profile, set
the rate parameter to zero (0). Although the range is consistent, the values are inputted
slightly different between operating systems. In Hybrid mode, rate is entered in kbps. As a
result, if the desired rate were 1 Mbps, the configured value would be 1000. For Native
mode the rate is configured in bps. Therefore, 1 Mbps is configured as 1000000. Table 8-15
lists some of the rate values and levels of granularity for the various ranges.
Table 8-15 Rate Configuration Table
Rate Range Granularity Rate Range Granularity
1 to 1024
(1 Mbps)
32768
(32 kbps)
65537 to 131072
(128 Mbps)
4194304
(4 Mbps)
1025 to 2048
(2 Mbps)
65536
(64 kbps)
131073 to 262144
(256 Mbps)
8388608
(8 Mbps)
2049 to 4096
(4 Mbps)
131072
(128 kbps)
262145 to 524288
(512 Mbps)
16777216
(16 Mbps)

306 Chapter 8: QoS Support on the Catalyst 6500
Within each range, the hardware is configured with rate values that are multiples of the
granularity values. The valid range for the burst parameters is 1 kb through 32 Mb. Again,
the burst values are configured slightly different depending on the operating system. With
Hybrid, burst is entered in kilobits (kb), whereas Native mode configures the burst in bytes
(B). To maintain consistent QoS results, when applying a single policer to multiple ports,
standardize the trust state across all affected ports.
Notice the previous commands do not include configuration for the microflow policer in
Native mode. Unlike the aggregate policer, which is configured in global configuration
mode, the microflow policer is entered using the MQC. To enable microflow policing in
Native mode, mls qos flow-policing must be enabled in global configuration mode. By
default, microflow policing is globally enabled in Native mode. You can verify this by
issuing the command show mls qos. In addition to the microflow policer, it is also possible
to configure a per-interface aggregate policer. Native mode offers the option of configuring
two different aggregate policers. The previously defined aggregate policer behaves the
same as the policer defined in Hybrid mode. The per-interface aggregate policer, on the
other hand, applies to ingress traffic only on the port to which it is applied. Both the
microflow and per-interface aggregate policers are configured under the policy map class
using the following commands:
(Native IOS)
(Microflow Policer)
police flow {
rate
} [{
burst
}] [conform-action {drop | set-dscp-transmit {
DSCP
} | set-
prec-transmit{
prec
} | transmit}] [exceed-action {drop | policed-dscp-transmit |
transmit}]
(Aggregate Policer)
police {
rate
} [{
burst
}] [conform-action {drop | set-dscp-transmit {
DSCP
} | set-
prec-transmit{
prec
} | transmit}] [exceed-action {drop | policed-dscp-transmit |
transmit}]
As mentioned in the “Classification And Marking” section, prior to 12.1(12c)E1 set ip
precedence and set ip dscp were not available options. As a result, to mark incoming
traffic, a policer was required. Marking is accomplished using the conform-action option.
Under this configuration option, it is possible to modify a frame’s existing DSCP or IP
precedence value. The frame is then forwarded to the appropriate egress port and scheduled
Rate Range Granularity Rate Range Granularity
4097 to 8192
(8 Mbps)
262144
(256 kbps)
524289 to 1048576
(1 Gbps)
33554432
(32 Mbps)
8193 to 16384
(16 Mbps)
524288
(512 kbps)
1048577 to 2097152
(2 Gbps)
67108864
(64 Mbps)
16385 to 32768
(32 Mbps)
1048576
(1 Mbps)
2097153 to 4194304
(4 Gbps)
134217728
(128 Mbps)
32769 to 65536
(64 Mbps)
2097152
(2 Mbps)
4194305 to 8000000
(8 Gbps)
268435456
(256 Mbps)
Table 8-15 Rate Configuration Table (Continued)
Policing 307
according to the CoS derived from the new DSCP setting. The following examples demon-
strate how to configure single-rate policing in both Hybrid and Native mode. The intent of
these examples is to demonstrate policing lower-priority applications, ensuring sufficient
bandwidth exists for mission-critical applications, particularly voice and video.
In the Hybrid mode example provided, an aggregate policer controls bandwidth
consumption for web traffic. Web traffic is limited to 1 Mbps. All HTTP traffic exceeding
the normal rate is dropped. Figure 8-9 shows the example configured in Hybrid mode. In
the Native example, the same match criteria and limitations apply. In this instance, however,
a microflow policer is used. Figure 8-10 shows the example configured for Native mode. To
demonstrate the behavior of the different policers, a traffic generator is configured. The
generator is attached via Fast Ethernet to the port to which the policer is applied. Three
separate flows are created on the traffic generator, each destined for TCP port 80. In
addition, each flow is set to generate packets at a rate of 2 Mbps, for a total of 6 Mbps.
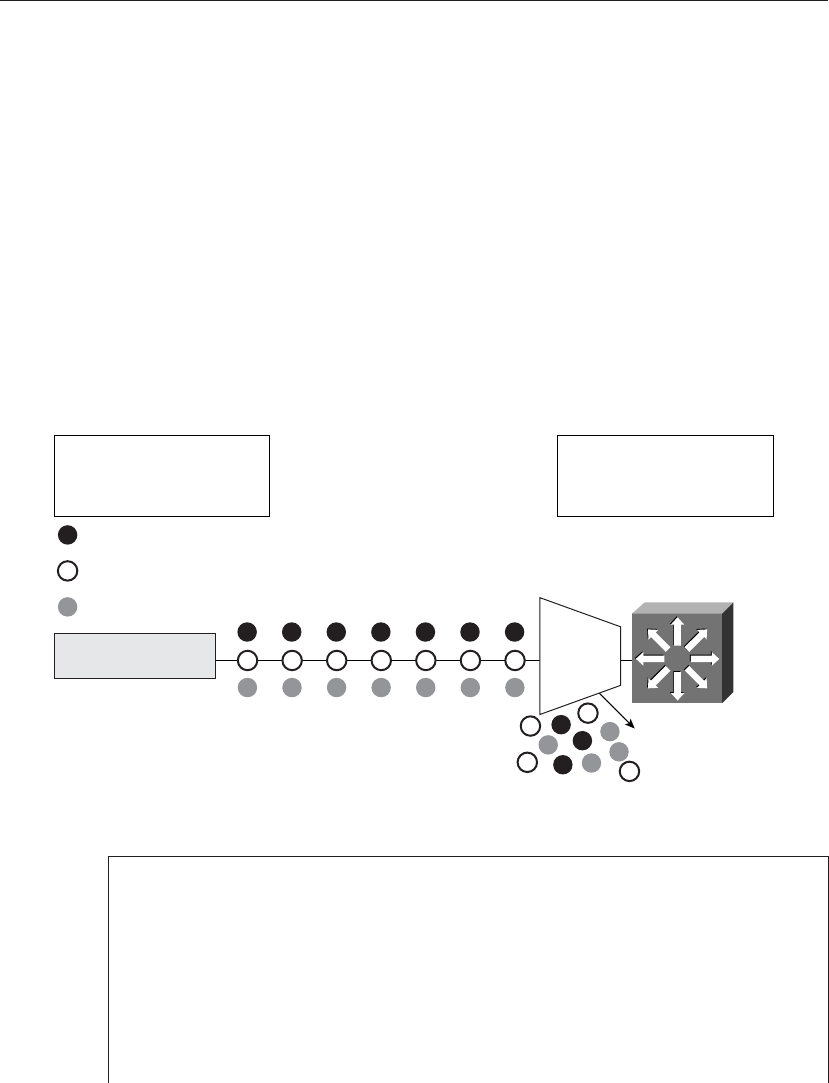
Figure 8-9 Single-Rate Aggregate Policer
Example 8-31 Configuring a Single-Rate Aggregate Policer in Hybrid Mode with a PFC2
hybrid (enable) set qos policer aggregate HTTP-police rate 1000 burst 13 drop
QoS policer for aggregate HTTP-police updated successfully.
Rate is set to 992, erate is set to 992 burst is set to 13 and eburst is set to 13
in hard
ware due to hardware granularity.
hybrid (enable) set qos acl ip HTTP-traffic dscp 0 aggregate HTTP-police tcp any any
eq www
HTTP-traffic editbuffer modified. Use ’commit’ command to apply changes.
hybrid (enable) commit qos acl HTTP-traffic
QoS ACL ’HTTP-traffic’ successfully committed.
hybrid (enable) set qos acl map HTTP-traffic 5/10
ACL HTTP-traffic is successfully mapped to port 5/10.
Traffic generator creates
three separate 2 Mbps
streams destined for port 80
Catalyst 6500 polices all
port 80 traffic received on
ingress interface to 1Mbps
Interface
Aggregate
Policer
Stream 2
Stream 3
Stream 1
Policer
Discard
Traffic generator
continues

308 Chapter 8: QoS Support on the Catalyst 6500
Example 8-31 Configuring a Single-Rate Aggregate Policer in Hybrid Mode with a PFC2 (Continued)
The first step is to define the policer with the appropriate parameters. Although 1 Mbps is
the configured rate, the value is rounded down to the closest 32-kbps increment to
conform to the hardware granularity for this particular range. Next, to account for the
largest potential frame size (1518 bytes), the value 13000 is chosen for the burst. The
policer is then applied to the appropriate ACL. When the ACL is applied to the desired
port, it is necessary to verify configuration and performance.
hybrid (enable) show qos info config 5/10
QoS setting in NVRAM:
QoS is enabled
Policy Source of port 5/10: COPS
Tx port type of port 5/10 : 2q2t
Rx port type of port 5/10 : 1q4t
Interface type: port-based
ACL attached: HTTP-traffic
The qos trust type is set to untrusted.
Default CoS = 1
(text omitted)
Based on the show qos info output for port 5/10, it is confirmed the interface is set for
port-based QoS. Also the ACL HTTP traffic has been applied. Further, note that the port
has been left at the default untrusted state. As discussed in the previous sections, frames
arriving on port 5/10 are marked with the port default CoS. Given this scenario, however,
this value is overwritten. Remember, the internal DSCP value is derived from the default
ACL, which equates to DSCP 0. Fortunately, because the port is untrusted, even if the default
ACL DSCP value was modified, all traffic matching the ACL configured in the example is set
to DSCP 0.
hybrid (enable) show qos policer config aggregate HTTP-police
QoS aggregate policers:
Aggregate name Avg. rate (kbps) Burst size (kb) Normal action
------------------------------- ---------------- --------------- -------------
HTTP-police 1000 13 policed-dscp
Excess rate (kbps) Excess burst size (kb) Excess action
------------------ ---------------------- -------------
1000 13 drop
ACL attached
------------------------------------
HTTP-traffic
show qos policer verifies the configuration for the defined policer HTTP-police. Notice
that because the single-rate policer is configured on a Catalyst 6500 equipped with a PFC2,
excess rate and burst are visible fields. Because the excess rate and burst are equal to the
normal rate and burst, however, the excess policing feature is not invoked.
hybrid (enable) show qos statistics aggregate-policer HTTP-police
QoS aggregate-policer statistics:
Aggregate policer Allowed packet Packets exceed Packets exceed
count normal rate excess rate
------------------------------- -------------- -------------- --------------
HTTP-police 42768 208811 208811
Finally, reviewing show qos statistics for the aggregate policer reveals the desired perfor-
mance. In total, 251,579 packets were forwarded to the port. This is confirmed by adding
the total number of packets exceeding the excess rate (208,811) to the total number of

Policing 309
packets conforming to the policing contract (42,768). When the percentage of conforming
packets is computed (42,768 / 25,1579), it is evident the aggregate policer is operating as
expected. Approximately, 1/6th of the total traffic conforms to the specified rate. The next
example demonstrates the configuration and behavior of a microflow policer in Native mode.
Figure 8-10 Single-Rate Microflow Policer
After the interesting traffic has been defined, in addition to the class maps and policy
maps, the results are applied to the appropriate interface with the command service-policy
input {name}. At this point, the policer is now operational.
native# show mls qos ip fastEthernet 6/10
[In] Policy map is HTTP-police [Out] Default.
QoS Summary [IP]: (* - shared aggregates, Mod - switch module)
Int Mod Dir Cl-map DSCP AgId Trust FlId AgForward-Pk AgPoliced-Pk
--------------------------------------------------------------------------------
Fa6/10 1 I HTTP-traf 0 3* dscp 2 682858 0
native# show mls ip detail
Displaying Netflow entries in Supervisor Earl
DstIP SrcIP Prot:SrcPort:DstPort Src i/f:AdjPtr
--------------------------------------------------------------------
20.20.20.2 192.168.10.1 tcp :www :www 0 : 0
20.20.20.1 192.168.20.1 tcp :www :www 0 : 0
20.20.20.3 192.168.30.1 tcp :www :www 0 : 0
Example 8-32 Configuring a Single-Rate Microflow Policer in Native Mode with a PFC2
native(config)# mls qos flow-policing
native(config)# access-list 101 permit tcp any any eq www
native(config)# class-map HTTP-traffic
native(config-cmap)# match access-group 101
native(config)# policy-map HTTP-police
native(config-pmap)# class HTTP-traffic
native(config-pmap-c)# police flow 1000000 2000
Traffic generator creates
three separate 2 Mbps
streams destined for port 80
Catalyst 6500
polices
individual port
80 traffic
flows received
on ingress
interface to 1 Mbps
Microflow
Policer
Stream 2
Stream 3
Stream 1
Discard
Discard
Discard
Traffic generator
continues
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
