Nmap has an option that simplifies and streamlines the process of performing TCP connect scans:
- To perform TCP connect scans with Nmap, the -sT option should be used with the IP address of the host to be scanned, as follows:
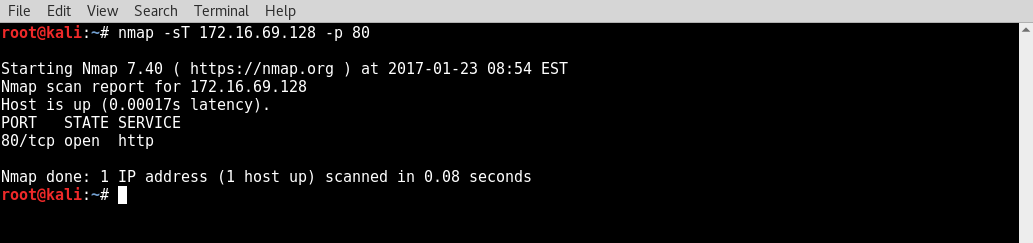
- In the example provided, a TCP connect scan was performed on the TCP port 80 of the specified IP address. Similar to the technique used with Scapy, Nmap listens for a response and identifies open ports by analyzing the TCP flags that are activated in any responses received. We can also use Nmap to perform scans on multiple specified ports by passing a comma-delimited list of port numbers, as follows:

- In the example provided, a TCP connect scan was performed on the ports 21, 80, and 443 of the specified target IP address. We can also use Nmap to scan a sequential series of hosts by indicating the first and last port numbers to be scanned, separated using dash notation:

- In the example provided, a TCP connect scan was performed on the TCP ports 20 through 25. In addition to providing the ability to specify the ports to be scanned, Nmap also has a preconfigured list of 1,000 commonly used ports. We can scan these ports by running Nmap without supplying any port specifications:

- In the example provided, the 1,000 common ports defined by Nmap were scanned to identify a large number of open ports on the Metasploitable2 system. Although this technique is effective in identifying most services, it might fail to identify obscure services or uncommon port associations.
- To scan all of the possible TCP ports, all possible port address values must be scanned. The portions of the TCP header that define the source and destination port addresses are both 16 bits in length. Furthermore, each bit can retain a value of 1 or 0. As such, there are 216, or 65,536, possible TCP port addresses. For the total possible address space to be scanned, a port range of 0-65535 needs to be supplied, as follows:

- In the example provided, all of the possible 65,536 TCP addresses were scanned on the Metasploitable2 system. Take note of the fact that more services were identified in this scan than in the standard Nmap 1,000 scan. This is evidence of the fact that a full scan is always best practice when attempting to identify all of the possible attack surfaces on a target. Nmap can also be used to scan TCP ports on a sequential series of hosts using dash notation:

- In the example provided, a TCP connect scan of the TCP port 80 was performed on all hosts within the range of hosts specified. Although this particular scan was only performed on a single port, Nmap can also scan multiple ports and ranges of ports on multiple systems simultaneously. Additionally, Nmap can also be configured to scan hosts based on an input list of IP addresses.
- This can be done using the -iL option and then by specifying either the filename, whether the file exists in the execution directory, or the path of the file. Nmap then cycles through each address in the input list and performs the specified scan against that address, as follows:

