Chapter 2. Active Directory Fundamentals
This chapter aims to bring you up to speed on the basic concepts and terminology used with Active Directory. It is important to understand each feature of Active Directory before embarking on a design, or your design may leave out a critical element.
2.1. How Objects Are Stored and Identified
Data stored within Active Directory is presented to the user in a hierarchical fashion similar to the way data is stored in a filesystem. Each entry is referred to as an object. At the structural level, there are two types of objects: containers and non-containers. Non-container objects are also known as leaf nodes. One or more containers branch off in a hierarchical fashion from a root container. Each container may contain leaf nodes or other containers. As the name implies, however, a leaf node may not contain any other objects.
Note
Although the data in Active Directory is presented hierarchically, it is actually stored in flat database rows and columns. The directory information tree (DIT) file is an Extensible Storage Engine (ESE) database file. This answers the question “Does Active Directory use JET or ESE database technology?” ESE is a JET technology.
Consider the parent-child relationships of the containers and leaves in Figure 2-1. The root of this tree has two children, Finance and Sales. Both of these are containers of other objects. Sales has two children of its own, Pre-Sales and Post-Sales. Only the Pre-Sales container is shown as containing additional child objects. The Pre-Sales container holds user, group, and computer objects as an example.
Note
User, group, and computer objects are actually containers, as they can contain other objects such as printers. However, they are not normally drawn as containers in domain diagrams such as this.
Each of these child nodes is said to have the Pre-Sales container as its parent. Figure 2-1 represents what is known in Active Directory as a domain.
The most common type of container you will create in Active Directory is an organizational unit (OU), but there are others as well, such as the type called “container.” Each of these has its place, as we’ll show later, but the one that we will be using most frequently is the organizational unit.
Uniquely Identifying Objects
When you are potentially storing millions of objects in Active Directory, each object has to be uniquely locatable and identifiable. To that end, objects have a globally unique identifier (GUID) assigned to them by the system at creation. This 128-bit number is the Microsoft implementation of the universally unique identifier (UUID) concept from Digital Equipment Corporation. UUIDs/GUIDs are commonly misunderstood to be guaranteed to be unique. This is not the case; the number is just statistically improbable to be duplicated before the year 3400 AD. In the documentation for the GUID creation API function, Microsoft says, “To a very high degree of certainty, this function returns a unique value.” The object’s GUID stays with the object until it is deleted, regardless of whether it is renamed or moved within the directory information tree (DIT). The object’s GUID will also be preserved if you move an object between domains within a multidomain forest.
Note
A cross-forest move of a security principal using a tool such as the Microsoft Active Directory Migration Tool (ADMT) will not preserve the object’s GUID.
Although an object’s GUID is resilient, it is not very easy to remember, nor is it based on the directory hierarchy. For that reason, another way to reference objects, called a distinguished name (DN), is more commonly used.
Distinguished names
Hierarchical paths in Active Directory are known as distinguished names and can be used to uniquely reference an object. Distinguished names are defined in the LDAP standard as a means of referring to any object in the directory.
Distinguished names for Active Directory objects are normally represented using the syntax and rules defined in the LDAP standards. Let’s take a look at how a path to the root of Figure 2-1 looks:
dc=mycorp,dc=com
In the previous distinguished name, you represent the domain root, mycorp.com, by separating each part with a comma and prefixing each part with the letters “dc”. If the domain had been called mydomain.mycorp.com, the distinguished name of the root would have looked like this:
dc=mydomain,dc=mycorp,dc=com
Note
dc stands for domain
component and is used to specify domain or application
partition objects. Application partitions are covered in Chapter 4.
A relative distinguished name (RDN) is the name used to uniquely reference an object within its parent container in the directory. For example, this is the DN for the default Administrator account in the Users container in the mycorp.com domain:
cn=Administrator,cn=Users,dc=mycorp,dc=com
This is the RDN of the user:
cn=Administrator
RDNs must always be unique within the container in which they
exist. It is permissible to have two objects with cn=Administrator in the directory; however,
they must be located inside different parent containers. There cannot
be two objects with an RDN of cn=Administrator in the Users
container.
DNs are made up of names and prefixes separated by the equals
sign (=). Another prefix that will become very familiar to you is
ou, which stands for organizational unit. Here is
an example:
cn=Keith Cooper,ou=Northlight IT Ltd,dc=mycorp,dc=com
All RDNs use a prefix to indicate the class of the object that
is being referred to. Any object class that does not have a specific
letter code uses the default of cn,
which stands for common name. Table 2-1 provides a complete list of
the most common attribute types amongst directory server
implementations. The list is from RFC 2253, “Lightweight Directory
Access Protocol (v3): UTF-8 String Representation of Distinguished
Names,” and the full text can be found at http://www.ietf.org/rfc/rfc2253.txt.
Key | Attribute |
| Common name |
| Locality name |
| State or province name |
| Organization name |
| Organizational unit name |
| Country name |
| Street address |
| Domain component |
| User ID |
Active Directory supports using CN, L,
O, OU, C,
and DC. CN or OU
is used in the majority of cases.
Examples
Let’s take a look at Figure 2-1 again. If all the containers were organizational units, the distinguished names for Pre-Sales and Post-Sales would be as follows:
ou=Pre-Sales,ou=Sales,dc=mycorp,dc=com ou=Post-Sales,ou=Sales,dc=mycorp,dc=com
And if you wanted to specify a user named Richard Lang, a group called My Group, and a computer called PC1 in the Pre-Sales OU, you would use the following:
cn=Richard Lang,ou=Pre-Sales,ou=Sales,dc=mycorp,dc=com cn=My Group,ou=Pre-Sales,ou=Sales,dc=mycorp,dc=com cn=PC1,ou=Pre-Sales,ou=Sales,dc=mycorp,dc=com
2.2. Building Blocks
Now that we’ve shown how objects are structured and referenced, let’s look at the core concepts behind Active Directory.
Domains and Domain Trees
Active Directory’s logical structure is built around the concept of domains. Domains were introduced in Windows NT 3.x and 4.0. However, in Active Directory, domains have been updated significantly from the flat and inflexible structure imposed by Windows NT. An Active Directory domain is made up of the following components:
An X.500-based hierarchical structure of containers and objects
A DNS domain name as a unique identifier
A security service, which authenticates and authorizes any access to resources via accounts in the domain or trusts with other domains
Policies that dictate how functionality is restricted for users or machines within that domain
A domain controller (DC) can be authoritative for one and only one domain. It is not possible to host multiple domains on a single DC. For example, Mycorp has already been allocated a DNS domain name for its company called mycorp.com, so it decides that the first Active Directory domain that it is going to build is to be named mycorp.com. However, this is only the first domain in a series that may need to be created, and mycorp.com is in fact the root of a domain tree.
The mycorp.com domain itself, ignoring its contents, is automatically created as the root node of a hierarchical structure called a domain tree. This is literally a series of domains connected together in a hierarchical fashion, all using a contiguous naming scheme. If Mycorp were to add domains called Europe, Asia, and Americas, then the names would be europe.mycorp.com, asia.mycorp.com, and americas.mycorp.com. Each domain tree is called by the name given to the root of the tree; hence, this domain tree is known as the mycorp.com tree, as illustrated in Figure 2-2. You can see that in Mycorp’s setup we now have a contiguous set of domains that all fit into a neat tree. Even if we had only one domain, it would still be a domain tree, albeit with only one domain.
Trees ease management and access to resources, as all the domains in a domain tree trust one another implicitly with transitive trusts. In a transitive trust, if Domain A trusts Domain B and Domain B trusts Domain C, this implies that Domain A trusts Domain C as well. This is illustrated in Figure 2-3. Put much more simply, the administrator of asia.mycorp.com can allow any user in the tree access to any of the resources in the Asia domain that the administrator wishes. The user accessing the resource does not have to be in the same domain.
Note
Trust relationships do not compromise security; they are just setting up the potential to allow access to resources. Actual access permissions still have to be granted by administrators. This is why you should avoid granting access to Everyone or Authenticated Users on resources. Once a trust is established, everyone in the trusted domain will be able to access those resources as well.
Forests
Now that you understand what a domain tree is, we can move on to the next piece of the Active Directory structure, the forest. Where a domain tree was a collection of domains, a forest is a collection of one or more domain trees. These domain trees share a common Schema and Configuration container, and the trees as a whole are connected together through transitive trusts. As soon as you create a single domain, you have a forest. If you add any domains to the initial domain tree or add new domain trees, you still have one forest.
A forest is named after the first domain that is created, also known as the forest root domain. The forest root domain is important because it has special properties.
Warning
In Active Directory, you can never remove the forest root domain. If you try to do so, the forest is irretrievably destroyed. Under Windows Server 2003 and newer Active Directories, you can rename the forest root domain, but you cannot change its status as the forest root domain or make a different domain the root.
As we continue with Mycorp, we find that it has a subsidiary business called Othercorp. The DNS domain name allocated to and used by Othercorp is othercorp.com. In Othercorp’s case, all you would need to do is create the root of the othercorp.com tree as a member of the existing forest; othercorp.com and mycorp.com can then exist together and share resources, as shown in Figure 2-4. The forest containing the mycorp.com and othercorp.com domain trees is known as the mycorp.com forest, in which mycorp.com is the forest root domain.
Warning
While multiple domain trees in a forest can be configured, you
should seriously consider all the implications of such a configuration
before implementation. It can be confusing for troubleshooting efforts
when you are working on an issue in the domain
othercorp.com, but the configuration information
for the forest is maintained in the partition cn=configuration,dc=mycorp,dc=com. This is
especially true when bringing in outside resources not familiar with
the implementation.
While legitimate reasons exist to create multitree forests, we recommend that you endeavor to simplify your Active Directory design as much as possible and limit yourself to one domain tree and as few domains as possible.
Best practice for new forest designs is almost always a single-domain forest. We have outlined the various multidomain options when designing a forest here, but, we do not generally recommend them (including empty roots).
Individual companies often implement their own forests. If Othercorp elected to deploy its Active Directory as a separate forest, you would need to employ a forest trust between Mycorp and Othercorp to provide seamless resource access between the two companies.
A forest trust allows an administrator to create a single transitive one-way or two-way trust between two forest root domains. This trust allows all the domains in one forest to trust all the domains in another forest, and vice versa.
If you have business units that are independent and, in fact, wish to be isolated from each other, then you must not combine them in a single forest. If you simply give each business unit its own domain, these business units are given the impression that they are autonomous and isolated from each other. However, in Active Directory, this level of autonomy and isolation can be achieved only through separate forests. This is also the case if you need to comply with regulatory or legal isolation requirements. Finally, some organizations choose to deploy Microsoft Exchange in a separate resource forest in order to handle separate administrative structures and requirements.
Organizational Units
Having covered the large-scale (domains, trees, and forests) view of Active Directory, we’ll now talk about the small scale. When you look inside an Active Directory domain, you will see a hierarchical structure of objects. This hierarchy is made up of objects that can act as containers and objects that cannot. The primary type of container that you will create to house objects is called an organizational unit (OU). Another type of container, which is actually called a container, can also be used to store a hierarchy of objects and containers.
Although both can contain huge hierarchies of containers and objects, an organizational unit can have group policies applied to it. (For more information on Group Policy, see Chapter 11.) For this reason, OUs are often used almost exclusively for building object hierarchies within a domain.
Let’s illustrate this with an example. Imagine that you are the administrator of the asia.mycorp.com domain from Figure 2-2. You have 500 users and 500 computer accounts in the domain. Most of the day-to-day account and machine management is very simple, but the manufacturing section is currently undergoing restructuring and an extensive recruitment program; people keep being transferred in or hired from the outside. You would like to be able to give this group limited autonomy over user objects by allowing one of the senior administrators to manage its own section of the tree. Complete segregation of security is not needed, and the manufacturing tree isn’t large enough to justify creating another domain to manage along with the associated domain controllers. You can instead create an organizational unit in your hierarchy called Manufacturing. You then give the senior engineer authority over that organizational unit to create and delete accounts, change passwords, and create other organizational units within the Manufacturing OU. Obviously, the permissions that the senior engineer would be given would be properly tailored so that he had control over only that organizational unit and not the asia.mycorp.com domain tree as a whole. You could do this manually or delegate control using the Delegation of Control Wizard, discussed in more depth in Chapter 16.
When you install an Active Directory domain, a number of default containers and organizational units are created automatically, including the Users and Computers containers and the Domain Controllers OU. If you try to create a new container, you will find that there is no option to do so from within the Active Directory Users and Computers (ADUC) MMC snap-in. This also applies to Organization, Locality, and Country container objects. This is intentional; in almost all cases, you would want to create an organizational unit instead of a container. It is possible to create the other types of containers from within scripts and other LDAP tools, but generally it is not necessary. So, throughout this book, whenever we advocate creating hierarchies within domains, we always recommend that you use organizational units. After all, an organizational unit is just a superset of a container. There is nothing a container can do that an organizational unit cannot.
The Global Catalog
The Global Catalog (GC) is a very important part of Active Directory because it is used to perform forest-wide searches. As its name implies, the Global Catalog is a catalog of all objects in a forest that contains a subset of attributes for each object. The GC can be accessed via LDAP over port 3268 or LDAP/SSL over port 3269. The Global Catalog is read-only and cannot be updated directly.
In multidomain forests, typically you first need to perform a query against the GC to locate the objects of interest. Then you can perform a more directed query against a domain controller for the domain the object is in if you want to access all the attributes available on the object.
The attributes that are available in the Global Catalog are
members of the partial attribute set (PAS). You can
add and remove attributes to and from the PAS by using tools such as the
Active Directory Schema snap-in or by modifying the attributeSchema object for the attribute
directly in the schema.
Note
Under Windows 2000, adding an attribute to the PAS caused all global catalogs in a forest to resynchronize the entire contents of the GC. This could have major replication and network traffic implications. Fortunately, this issue was resolved with Windows Server 2003; a GC resynchronization no longer happens after a PAS addition.
Flexible Single Master Operator (FSMO) Roles
Even though Active Directory is a multimaster directory, there are some situations in which there should only be a single domain controller that can perform certain functions. In these cases, Active Directory nominates one server to act as the master for those functions. There are five such functions that need to take place on one server only. The server that is the master for a particular function or role is known as the Flexible Single Master Operator (FSMO, pronounced “fizmo”) role owner.
Of the five roles, three exist for every domain, and two apply to the entire forest. If there are four domains in your forest, there will be 14 FSMO roles:
2 single forest-wide FSMOs
4 sets of 3 domain-wide FSMOs
The number of different role owners can vary greatly depending on whether you have domain controllers serving multiple roles, as is often the case.
The different FSMO roles are the following:
- Schema master (forest-wide)
The schema master role owner is the domain controller that is allowed to make updates to the schema. No other server can process changes to the schema. If you attempt to update the schema on a DC that doesn’t hold the schema master FSMO, the DC will return a referral to the schema master role holder. The default schema master role owner is the first server to be promoted to a domain controller in the forest.
- Domain naming master (forest-wide)
The domain naming master role owner is the server that controls changes to the forest-wide namespace. This server adds and removes domains and is required to rename or move domains within a forest, as well as to authorize the creation of application partitions and the addition/removal of their replicas. Like the schema master, this role owner defaults to the first DC you promote in a forest.
Note
It is a common misunderstanding that the schema and domain naming masters cannot be hosted outside of the root domain. Any domain controller in the forest (from any domain) can host the schema and domain naming master FSMO roles. In general, we recommend that these FSMOs be kept on a domain controller in the forest root unless you have a reason to place them elsewhere.
- PDC emulator (domain-wide)
For backward-compatibility purposes, one Active Directory DC has to act as the Windows NT primary domain controller (PDC). This server acts as the Windows NT master browser, and it also acts as the PDC for down-level clients. Even though the PDC has very important legacy functions, don’t be fooled into thinking that it is no longer important once you have removed all older clients.
The PDC emulator also has other important functions: for one, it attempts to maintain the latest password for any account. This is enforced by having the other DCs immediately forward any account password changes directly to the PDC. The significance of this feature is in helping to support PDC chaining functions. PDC chaining occurs when an account attempts to authenticate and the local DC doesn’t think the password provided is correct. The local DC will then “chain” the authentication attempt to the PDC to see if the PDC thinks the password is okay.
Note
PDC chaining and the matching forwarding of the passwords to the PDC across Active Directory site boundaries can be disabled by setting the
AvoidPdcOnWanregistry value to1. This is found in the registry keyHKLMSYSTEMCurrentControlSetServicesNetlogonParameters. If you suspect that PDC chaining isn’t working, make sure this registry value isn’t configured. You can find more information about this registry setting at this link.The PDC is also the target server of most Group Policy management tools. This is done to lessen the possibility of the same policy being modified in different ways by different administrators on different DCs at the same time. One other function of the PDC is that the PDC in each domain is the primary time source for the domain, and the PDC of the forest root domain is the primary time source for the entire forest. The AdminSDHolder process described in Chapter 16 also runs on the PDC emulator. Finally, the PDC emulator authorizes domain controller cloning operations. For more information about domain controller cloning, see Chapter 9.
- RID master (domain-wide)
A relative identifier (RID) master exists per domain. Every security principal in a domain has a security identifier (SID) that is comprised of several components, including a RID. The system uses the SID to uniquely identify that object for security permissions. In a way, this is similar to the GUID that every object has, but the SID is given only to security-enabled objects and is used only for security verification purposes. For more information about SIDs, see the sidebar What’s in a Security Identifier (SID)?. While you may log on or authenticate using the Security Accounts Manager (SAM) account name or universal principal name (UPN) to reference an object, the system always references you for authorization functions by the SID.
In a domain, the SIDs must be unique across the entire domain. As each DC can create security-enabled objects, some mechanism has to exist so that two identical SIDs are never created. To keep conflicts from occurring, the RID master maintains a large pool of unique RID values. When a DC is added to the network, it is allocated a subset of 500 values from the RID pool for its own use. Whenever a DC needs to create a SID, it takes the next available value from its own RID pool to create the SID with a unique value.
In this way, the RID master makes sure that all SIDs in a domain use unique RID values. When a DC’s RID pool drops to 50% of the available pool size, the DC contacts the RID master for another set of RID values. The threshold is not set to 0 to ensure that the RID master can be unavailable to other DCs for a brief time without immediately impacting object creations. The RID master itself is in charge of generating and maintaining a pool of unique values across the entire domain.
Note
RID pool size can be configured by setting the
RID Block Sizevalue in the registry keyHKLMSYSTEMCurrentControlSetServicesNTDSRIDvalues on the RID master FSMO role holder. A common scenario where you might use this registry setting is if you have a distributed environment where there can be prolonged connectivity issues between domain controllers and the RID master.If you decide to use this registry setting, it is a recommended practice to set this value on any domain controller that could become the RID master, so you do not have any inconsistencies in RID pool sizes after a RID master FSMO transfer.
- Infrastructure master (domain-wide)
The infrastructure master is used to maintain references to objects in other domains, known as phantoms. If three users from Domain B are members of a group in Domain A, the Infrastructure master on Domain A is used to maintain references to the phantom Domain B user members. These phantoms are not manageable or even visible through ordinary means; they are an implementation construct to maintain consistency.
The infrastructure master FSMO role owner is used to continually maintain the phantoms whenever the objects they refer to are changed or moved in the object’s domain. When an object in one domain references an object in another domain, it represents that reference by the GUID, the SID (for references to security principals), and the DN of the object being referenced. The Infrastructure master FSMO role holder is the DC responsible for updating an object’s SID and distinguished name in a cross-domain object reference.
The infrastructure master is also responsible for fixing up stale references from objects in its domain to objects in other domains (“stale” means references to objects that have been moved or renamed so that the local copy of the remote object’s name is out of date). It does this by comparing its (potentially stale) naming data with that of a Global Catalog, which automatically receives regular replication updates for objects in all domains and hence has no stale data. The Infrastructure master writes any updates it finds to its objects and then replicates the updated information around to other DCs in the domain. However, if a GC also holds the Infrastructure master role, by definition the server hosting the GC will always be up to date and will therefore have no stale references. If it never notices that anything needs changing, it will never update any non-GC servers with infrastructure updates.
Once the Active Directory Recycle Bin has been enabled, the infrastructure master’s functions are performed independently by every DC in the forest. That is, the tasks just described are no longer delegated to a single DC.
The infrastructure master is additionally responsible for performing updates to the domain when upgrading to Windows Server 2003 or newer—the command adprep /domainprep must be run on the infrastructure master. We discuss adprep in Chapter 19.
The placement of the infrastructure master and whether or not it can be placed on a Global Catalog without causing issues is often a source of great confusion. Table 2-2 provides a matrix of permitted permutations for forests where the Active Directory Recycle Bin is not enabled.
Single-domain forest | Multiple-domain forest | ||
All domain controllers are GCs | All domain controllers are not GCs | ||
Infrastructure master relevant | No | No | Yes |
Infrastructure master permitted on GC | Yes | Yes | No |
Note
An infrastructure master technically exists for each application partition in the forest, in addition to domains. Prior to Windows Server 2008, the infrastructure master did not perform any functions for application partitions. However, Windows Server 2008 and newer setup versions now enforces a consistency check to make sure that the specified infrastructure master for each application partition is valid. For more information on this, reference microsoft.com. Application partitions are covered in detail in Chapter 4.
FSMO roles can be transferred between domain controllers. You can transfer the domain naming FSMO with the Active Directory Domains and Trusts snap-in, the schema FSMO with the Active Directory Schema snap-in, and the RID, infrastructure, and PDC emulator FSMOs using the Active Directory Users and Computers snap-in or with Windows PowerShell. Alternatively, you can use the ntdsutil utility to perform transfers from a command line. For more information on using NTDSUTIL to transfer FSMO roles, see Chapter 18.
Although the AD snap-ins and NTDSUTIL can trivially transfer a role from one server to another while both servers are available, there will be some cases in which a FSMO role owner becomes unavailable without the role previously being transferred. In this case, you have to use NTDSUTIL to force an ungraceful transfer of the role to a server, known as “seizing” the role. When you seize a FSMO role, you should not bring the original role owner back online. Instead, you should perform a metadata cleanup and then rebuild the domain controller. For more information on using NTDSUTIL to seize FSMO roles, see Chapter 18.
Note
If you are using the Windows Server 2008 or newer version of Active Directory Users and Computers, you can delete a domain controller from the Domain Controllers OU and metadata cleanup will be performed.
For earlier versions, in order to remove the metadata from the directory after a failed dcpromo, or if a domain controller cannot be brought back online for any reason, you will need to use NTDSUTIL. See microsoft.com for more details about the steps involved in using NTDSUTIL to perform a metadata cleanup.
If you lose one of the FSMO role holders for a domain, you should always make sure that you are in control of the situation and are promoting a new DC to be the relevant role holder, forcibly moving the role to an existing DC or swiftly bringing back the DC that is the relevant role holder.
Warning
If a server with a role becomes unavailable, another server is not automatically promoted to assume the role. The administrator must move the role to a new owner manually.
Many Active Directory administrators spend a great deal of time worrying about the well-being of their FSMO role owners and the “what-if” scenario of scrambling to bring them back into service if one of the role holders goes offline. It is worthwhile to consider just how important the immediate availability of each FSMO role owner is to your environment:
- Schema master
The schema master is only necessary when you are making changes to the schema. These are generally planned well in advance, so if your schema master goes offline you can afford to wait before bringing it back online.
- Domain naming master
The domain naming master is only necessary when adding domains and application partitions. This is another change that is planned well in advance, so again, if your domain naming master goes offline you can probably wait to bring it back online.
- Infrastructure master
If the infrastructure master is offline, you can’t run adprep /domainprep, and cross-domain phantom updates will stop. The first task is, of course, planned well in advance. The second seems important at first glance, but the infrastructure master updates phantoms over the period of a couple of days, so if you wait a bit to bring it back online, chances are you’ll be fine. If you have enabled the Active Directory Recycle Bin, an infrastructure master outage will only affect your ability to run adprep.
- RID master
If the RID master is offline, you can’t issue RID pools to DCs when they’re requested. Recall from the earlier description of the RID master that domain controllers request RID pools in blocks of 500, when they get down to 250 RIDs remaining. So, unless you expect to exhaust the RID pools on your domain controllers very rapidly (where “rapidly” is faster than you restore the RID master), you’re probably not going to have any issues if the RID master is offline for a period of time. One scenario where RID master availability could be more important is if you are provisioning large numbers of new security principals (users, groups, or computers) and the provisioning system targets a single domain controller or set of domain controllers for this task. For more information about RID pool exhaustion, reference this article.
- PDC emulator
The importance of the availability of the PDC emulator varies from environment to environment. The PDC emulator is the domain controller that applications that use legacy APIs will often contact; it is also how trust paths are resolved, how passwords are chained, where the time sync hierarchy is rooted, and so forth. Whether or not you should rush to bring the PDC emulator back online is really quite subjective to your environment, but generally speaking, out of the five FSMO roles, the PDC emulator is probably the most important role holder in your environment.
Note
FSMO role placement has been a subject of some debate over the years. Some administrators advocate placing each role on a different DC, while others advocate keeping all roles together. For the sake of simplicity, you can keep the roles together on a single DC in each domain unless the load on the FSMO role holder DC demands splitting them up onto different servers. If you decide to split them up, see the Microsoft support page for the latest guidance on how to best place these roles.
If you are concerned about being able to restore FSMO role holders from a backup, you should split the roles accordingly. It is specifically a bad idea to restore the RID master from a backup, so you should keep the RID master on a separate domain controller if you want to be able to restore the other FSMO role holders from a backup.
Time Synchronization in Active Directory
Active Directory is highly dependent on all of the domain controllers and domain members having synchronized clocks. Kerberos (which is the underlying authentication protocol for Active Directory clients) uses system clocks to verify the authenticity of Kerberos packets. By default, Active Directory supports a tolerance of plus or minus five minutes for clocks. If the time variance exceeds this setting, clients may be unable to authenticate and, in the case of domain controllers, replication will not occur. Newer versions of Windows can handle time skew without impacting Kerberos, as discussed in this article.
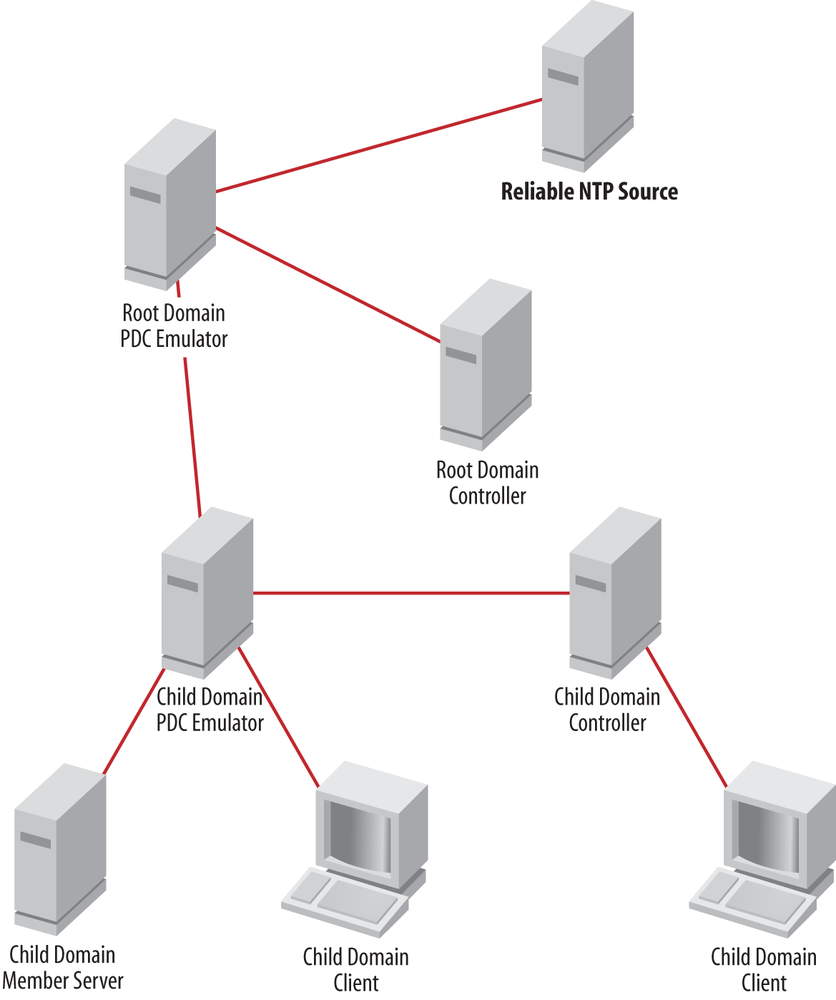
Fortunately, Active Directory and Windows collectively implement a time synchronization system based on the Network Time Protocol (NTP) that ensures that every machine in the forest has a synchronized clock. The w32time service implements time synchronization on every Windows 2000 or newer machine in the forest. The time synchronization hierarchy is outlined in the following list, and one possible effective hierarchy is shown in Figure 2-5:
The forest root domain’s PDC emulator synchronizes its clock with a reliable outside time source (such as a hardware clock, a government source, or another reliable NTP server).
Each child domain’s PDC emulator synchronizes its clock with a reliable time source in its domain or the parent domain.
Each domain controller synchronizes its clock with the PDC emulator of its domain or the parent domain.
Each domain member synchronizes its clock with the domain controller to which it authenticates.
Note
The Network Time Protocol was defined in RFC 1305, which is available at this link.
You should not need to configure the w32time service on any domain joined machine other than your root domain’s PDC emulator. While it is permissible to do so, our experience has been that many organizations that elect to use a different time sync hierarchy (such as using local routers or dedicated NTP servers) end up suffering from Kerberos issues later. For information on how to configure the w32time service on the PDC emulator, see the upcoming sidebar Configuring W32Time on the PDC Emulator.
Warning
It is crucial that you remember to reconfigure the w32time service on any domain controller that you transfer the PDC emulator FSMO role to or from in your root domain.
We recommend that you consider proactively configuring all of the possible candidates for holding the PDC emulator FSMO role to synchronize with an external reliable time source ahead of time. This will remove the need to remember to perform the manual configuration steps when the role is transferred.
Domain and Forest Functional Levels
For the Windows Server 2003 release of Active Directory, Microsoft expanded on the domain mode concept by introducing functional levels. Whereas the domain modes applied only to domains, functional levels apply to both forests and domains. Like the domain mode, functional levels dictate what types of operating systems can assume the role of a domain controller in a domain or forest. Each functional level also has an associated list of features that become available when the domain or forest reaches that particular functional level. We cover many of the features that are available for each functional level in Appendix A.
Like domain modes, functional levels can be set via the Active Directory Domains and Trusts snap-in. For the Windows Server 2003 and Windows Server 2008 functional levels, once the functional level is “elevated” to a higher status, it cannot be rolled back. Windows Server 2008 R2 introduced the ability to roll back the functional level through the introduction of optional features that are enabled independently of functional levels.
Table 2-3 and Table 2-4 show the operating systems that are supported by the various domain and forest functional levels.
Functional level | Functional level number | Supported domain controller OS |
Windows 2000 Mixed | N/A | Windows NT 4.0 Windows 2000 Windows Server 2003 |
Windows 2000 Native | 0 | Windows 2000 Windows Server 2003 Windows Server 2008 Windows Server 2008 R2 |
Windows Server 2003 Interim | 1 | Windows NT 4.0 Windows Server 2003 |
Windows Server 2003 | 2 | Windows Server 2003 Windows Server 2008 Windows Server 2008 R2 Windows Server 2012 |
Windows Server 2008 | 3 | Windows Server 2008 Windows Server 2008 R2 Windows Server 2012 |
Windows Server 2008 R2 | 4 | Windows Server 2008 R2 Windows Server 2012 |
Windows Server 2012 | 5 | Windows Server 2012 |
Functional level | Functional level number | Supported domain controller OS |
Windows 2000 | 0 | Windows NT 4.0 Windows 2000 Windows Server 2003 Windows Server 2008 Windows Server 2008 R2 |
Windows Server 2003 Interim | 1 | Windows NT 4.0 Windows Server 2003 |
Windows Server 2003 | 2 | Windows Server 2003 Windows Server 2008 Windows Server 2008 R2 Windows Server 2012 |
Windows Server 2008 | 3 | Windows Server 2008 Windows Server 2008 R2 Windows Server 2012 |
Windows Server 2008 R2 | 4 | Windows Server 2008 R2 Windows Server 2012 |
Windows Server 2012 | 5 | Windows Server 2012 |
Note
For more information on upgrading Active Directory, check out Chapter 19.
Windows 2000 domain mode
Each Windows 2000 Active Directory domain runs in one of two modes: mixed mode (the default) or native mode. A mixed-mode domain allows servers running previous versions of Windows NT to exist as domain controllers in the domain. A native-mode domain supports only Windows 2000 or later domain controllers. Supporting a mixed-mode domain is necessary to allow administrators to update Windows NT domains to Active Directory. A mixed-mode Active Directory domain emulates some of the behaviors of a Windows NT domain. Remember that with previous versions of Windows NT, networks used to have a primary domain controller (PDC) for a domain that held a writable copy of the accounts database, and zero or more backup domain controllers (BDCs) that held a read-only accounts database copied from the PDC. For an Active Directory network to support older Windows NT domain controllers, one (and only one) of the Active Directory servers has to act as a PDC. The Windows NT PDC notifies the BDCs when a change occurs, and the BDCs then request a copy of the accounts database from the PDC to get the relevant user, group, and computer accounts from Active Directory. While all accounts are replicated out, the total attributes for each object are a much smaller subset of the total attributes that Active Directory now holds for these types of objects.
Going from mixed mode to native mode is a simple, but one-way, change. Since this is a one-way change, you should test it in your lab and plan accordingly. Once you have decided to move forward with the procedure, you simply connect to a DC with the Active Directory Domains and Trusts snap-in and change the mode under the General tab to native mode. After you have done this, the only way to go back is to reinstall all domain controllers of the domain and restore from a backup made prior to the upgrade.
Warning
Never upgrade to Windows 2000 native mode unless you are certain that you will not require any BDCs to exist anywhere in that domain.
The specific differences between mixed mode and native mode are shown in Table 2-5.
Action | Windows 2000 mixed mode | Windows 2000 native mode |
Replication | PDC FSMO master sends updates to Windows NT BDCs; same DC acts like ordinary Active Directory DC when communicating with other Active Directory DCs. All Active Directory DCs use multimaster replication between themselves. | Only Active Directory DCs allowed, so all DCs use multimaster replication. |
NetBIOS | Can’t disable. | Can disable. |
Group functions | Windows NT group nesting rules; same-scope group nesting disallowed for global and domain local groups. Domain local groups limited to DCs. Universal groups cannot be security enabled, but can be nested in other universal groups. No conversion between group types or scopes. | Windows AD group nesting rules; same-scope group nesting allowed. Domain local groups available on all domain members. Universal groups can be security enabled. Conversion between group types and scopes allowed. |
Account migration |
|
|
Note
Moving any domain from mixed mode to native mode has no bearing in any way on any other domain. It doesn’t matter if it is the root domain or a subdomain you are converting, because you are only removing the ability of that domain to replicate data to older Windows NT BDCs within the domain, not affecting its ability to replicate and interact with Windows 2000 domain controllers in other domains.
Groups
Active Directory supports three group scopes: domain local, domain global, and universal. Groups in each of these scopes behave slightly differently based on the domain and forest functional levels. To complicate matters further, each group scope can have two types: distribution and security.
The type is the easiest piece to define. If the type is distribution, the group’s SID is not added to a user’s security token during logon, so it cannot be used for Windows security purposes. Distribution groups are generally used as a messaging list (a set of users that you can mail or send instant messages to all at once), though it is possible to use them for security groups for LDAP-based applications or for other applications that don’t use the standard Windows security model. Microsoft Exchange represents distribution lists with Active Directory distribution groups. Security groups, by contrast, are enumerated during logon, and the SIDs of any groups of which the user is a member are added to the user’s security token. Security groups can also be leveraged by Exchange as distribution lists.
All Windows editions that support Kerberos will encounter problems if security principals are members of too many groups. The issue is that the token of the security principal becomes too large for Windows to handle, and users may experience authentication or other Kerberos issues. This phenomenon is often referred to as token bloat. For more information on token size issues, reference this link. The three different scopes of mailing lists and security groups result from the legacy of Windows NT and the introduction of the GC. Global groups and domain local groups are the direct descendants of Windows NT groups; the membership of these groups is only available from domain controllers of the domains in which they are created. Universal group membership is available both from the domain controllers of the domains in which they are created in and from all Global Catalogs in the forest. Universal and global groups can be used in access control lists (ACLs) on any resource in the forest or in trusting domains. Domain local groups can only be used in ACLs in the domain in which they are created.
In order to help you fully understand how groups work in Active Directory, we will explain the following items in this section:
Which security principals each group type may contain
How you can nest groups across domain boundaries
What options are available to you for converting between different group scopes
To start with, let’s take a look at what rules govern nesting of groups within a domain. Table 2-6 shows which types of groups can be nested within other types of groups.
Can contain domain local | Can contain domain global | Can contain universal | |||||
Scope | Type | Distribution groups | Security groups | Distribution groups | Security groups | Distribution groups | Security groups |
Domain local | Distribution groups | Yes | Yes | Yes | Yes | Yes | Yes |
Security groups | Yes | Yes | Yes | Yes | Yes | Yes | |
Domain Global | Distribution groups | No | No | Yes | Yes | No | No |
Security groups | No | No | Yes | Yes | No | No | |
Universal | Distribution groups | No | No | Yes | Yes | Yes | Yes |
Security groups | No | No | Yes | Yes | Yes | Yes | |
Although this table is fine, there is one other complicating factor that needs to be taken into account: cross-domain group membership.
Group membership across domain boundaries
Restrictions for all groups are shown in Tables 2-7 and 2-8. Note that while universal groups can contain members from different domains, those domains cannot span forests. All universal group members must be from the same forest.
Group scope | Can contain users and computers from | Can contain domain local groups from | ||
Same domain | Different domain | Same domain | Different domain | |
Domain local groups | Yes | Yes | Yes | No |
Domain global groups | Yes | No | No | No |
Universal groups | Yes | Yes | No | No |
Group scope | Can contain domain global groups from | Can contain universal groups from | ||
Same domain | Different domain | Same domain | Different domain | |
Domain local groups | Yes | Yes | Yes | Yes |
Domain global groups | Yes | No | No | No |
Universal groups | Yes | Yes | Yes | Yes |
Tables 2-7 and 2-8 work in conjunction with Table 2-6. You would normally check which groups may be members from Table 2-6 (if any) and then cross-reference with Tables 2-7 and 2-8 to identify what options you have across domain boundaries.
Converting groups
There are limits on what groups can be converted, based on the existing members of the group and the current type and scope of the group. The former should be fairly obvious, based on the existing restrictions shown in Table 2-6. The conversion process cannot work if the existing group members would not be valid members of the new group type once the conversion has taken place. The ability to convert between groups is based on these restrictions:
Security groups can be converted to distribution groups.
Distribution groups can be converted to security groups.
A domain local group can be converted to a universal group provided that the domain local group is not already a member of another domain local group.
A domain global group can be converted to a universal group provided that the domain global group does not contain any other domain global groups.
A universal group can be converted to a domain global group provided all members in the group are users from the domain in which the group existed.
Note
The benefit of converting a distribution group to a security group is probably obvious: you get to use the group for Windows security purposes. The benefit of converting a security group to a distribution group is usually not so obvious. The most useful aspect of this conversion is that you can safely disable a security group to verify whether or not it is being used for Windows security.
Previously, if you didn’t know whether a group was being used for Windows security, you would have to delete it and hope that nothing broke. If anything did break, you found yourself figuring out how to restore the group or how to use a new group. Now you can simply convert the group to a distribution group; and if anything breaks, you simply change the group back into a security group, thereby restoring the old functionality.
2.3. Summary
In this chapter, we’ve gone over the groundwork for some of the main internals of Active Directory. We covered such concepts as domains, trees, forests, organizational units, the Global Catalog, FSMOs, and forest and domain functional levels. We then delved into how groups work in Active Directory and what features are available under the various domain modes and functional levels.
With this information under our belts, let’s now take a look at the management tools available to you for administering Active Directory.