Apply Your Knowledge
Exercises
8.1. Enabling the Remote Access Service on a Computer Running Windows 2000 Server
Whether through a RAS, a VPN, or some other method, the ability to configure remote access methods has become an important consideration for network administrators. In this exercise, you'll configure a server to allow incoming remote access.
1. |
Select Start, Programs, Administrative Tools, Routing and Remote Access. The Routing and Remote Access window shown in
Figure 8.3 appears. Figure 8.3. The Routing and Remote Access window.
|
2. |
To make the system a RAS server, select the Add Server option from the Action menu. The Add Server dialog box appears. Select the This Computer radio button, as shown in Figure 8.4. Figure 8.4. The Add Server dialog box.
|
3. |
In the left pane of the Routing and Remote Access window, right-click on your server and choose Configure and Enable Routing and Remote Access. The Routing and Remote Access Server Setup Wizard opens. Click Next to start the wizard. |
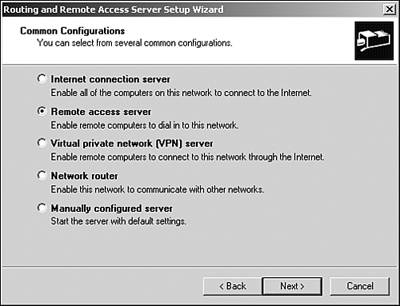
4. |
Select the appropriate Remote Access Server radio button, as shown in Figure 8.5, and then click Next. Figure 8.5. The Routing and Remote Access Server Setup Wizard.
|
5. | |
6. |
You need to decide how to handle client IP addressing. For now, accept the default setting of Automatically, as shown in Figure 8.6, and then click Next. Figure 8.6. Configuring automatic IP addressing for remote clients.
|
7. | |
8. |
The final wizard screen acknowledges the successful configuration of a Windows RAS server. Click Next, and the RAS service attempts to start automatically. Figure 8.7 shows the Routing and Remote Access window, with a successfully installed RAS server. |
8.2. Configuring a Client System to Access a Remote Server
After you have the server side of a remote access connection configured, you can configure the client side. To create a dial-up connection that allows a user to connect to a resource as a dial-up client, follow the steps in this exercise.
1. |
Select Start, Settings, Network and Dial Up Connections. The Network and Dial-up Connections window shown in Figure 8.8 appears. Figure 8.8. The Network and Dial-up Connections window.
|
2. | |
3. |
The first screen of the Network Connection Wizard allows you to choose the type of network connection you want to create. Select the Dial-up to Private Network option, as shown in Figure 8.9, and then click Next. The Phone Number to Dial dialog box appears. Figure 8.9. The Network Connection Type dialog box.
|
4. |
Enter the telephone number of the remote access server (a line that the remote access server will use to accept incoming calls). For this exercise, enter your personal telephone number. Click Next, and the Connection Availability screen appears. It allows you to limit the use of this dial-up connection to your personal logon or to anyone who logs on to this computer. |
5. |
Make sure For All Users is selected, as shown in Figure 8.10, and then click Next. Figure 8.10. The Connection Availability dialog box.
|
6. | |
7. |
The Completing the Network Connection Wizard dialog box appears. You need to enter a descriptive name for the connection you are creating, so for this connection, enter Real World Project Test. Select Add a Shortcut to My Desktop, and then click Finish. A shortcut icon appears on your desktop. |
8. |
Exam Questions
| 1: | Which of the following statements best describes a VPN?
|
| A1: | c. A VPN provides a secure communication path between devices over a public network such as the Internet. None of the other answers describes a VPN. For more information, see the section “Types of Remote Access,” in this chapter. |
| 2: | Which of the following is a disadvantage of SLIP?
|
| A2: | a. SLIP transmits passwords and usernames in clear text and is therefore insecure. SLIP is usable across all platforms that support it, including Linux and Windows. Answer d is not valid. For more information, see the section “Remote Access Protocols and Services,” in this chapter. |
| 3: | What is the function of SSL?
|
| A3: | a. SSL provides a mechanism for securing data across a network. Answer b describes SSH, and Answer d describes RAS. Answer c is not valid. For more information, see the section “Security Protocols,” in this chapter. |
| 4: | What is the function of RAS?
|
| A4: | d. RAS allows a remote system to dial in to a network and use the resources of the network. All the other answers are not valid. For more information, see the section “Remote Access Protocols and Services” in this chapter. |
| 5: | In a remote access scenario, what function does PPP serve?
|
| A5: | b. PPP is a protocol that allows for dial-up connections over serial links. Answer a describes SSL, Answer c describes a VPN, and Answer d describes PKI. For more information, see the section “Remote Access Protocols and Services,” in this chapter. |
| 6: | At what layer of the OSI model does IPSec operate?
|
| A6: | c. IPSec operates at the network layer of the OSI model. All the other answers are incorrect. For more information, see the section “Security Protocols,” in this chapter. |
| 7: | Which of the following are PPP authentication methods? (Choose the two best answers.)
|
| A7: | b, c. Both CHAP and MS-CHAP are PPP authentication methods. The other answers are not valid authentication protocols. For more information, see the section “Remote Access Protocols and Services,” in this chapter. |
| 8: | Which of the following protocols is used in thin-client computing?
|
| A8: | a. The ICA protocol is used in thin-client networking, where only screen, keyboard, and mouse inputs are sent across the line. PPP is a dial-up protocol used over serial links, PPTP is a technology used in VPNs, and RAS is a remote access service. For more information, see the section “Remote Access Protocols and Services,” in this chapter. |
| 9: | SSH is a secure alternative to which of the following?
|
| A9: | a. SSH is a secure alternative to Telnet. None of the other answers are valid. For more information, see the section “Security Protocols” in this chapter. |
| 10: | Kerberos is an authentication system that can be used on what operating systems?
|
| A10: | d. Kerberos is available for all the major operating systems. For more information, see the section “Security Protocols,” in this chapter. |
| 11: | What encryption method does CHAP use when replying to an authentication request?
|
| A11: | c. CHAP uses the MD5 encryption method. None of the other answers are correct. For more information, see the section “Remote Access Protocols and Services,” in this chapter. |
| 12: | How does the callback feature work in RAS?
|
| A12: | c. The callback feature in RAS allows it to call a preset or user-defined number when it receives a connection. None of the other answers are valid. For more information, see the section “Remote Access Protocols and Services,” in this chapter. |
| 13: | Which of the following URLs is using SSL?
|
| A13: | d. You can identify when SSL is used by the s in the URL (in this case https://www.comptia.org). Answer b is a valid HTTP URL, but it is not secure. None of the other answers are valid URLs. For more information, see the section “Security Protocols,” in this chapter. |
| 14: | Which of the following is not an authentication protocol?
|
| A14: | a. IPSec is not an authentication protocol. All the other protocols listed are classed as authentication protocols. For more information, see the section “Security Protocols,” in this chapter. |
| 15: | In a thin-client scenario, what information is propagated across the communications link between the client and the server?
|
| A15: | b. Only screen, keyboard, and mouse inputs are sent across the communications link in a thin-client scenario. This allows the processing to be handled by the server. None of the other answers are valid. For more information, see the section “Remote Access Protocols and Services,” in this chapter. |
| 16: | Which of the following is a reason to use L2TP rather than IPSec to create a VPN connection?
|
| A16: | b. You need to use L2TP instead of IPSec when you are using a protocol other than TCP/IP. IPSec can be used only with TCP/IP. None of the other answers are valid. For more information, see the section “Security Protocols,” in this chapter. |
| 17: | You are on-site as a consultant. The client's many remote access users are experiencing connection problems. Basically, when users try to connect, the system is unable to service their authentication requests. What kind of server might you recommend to alleviate this problem?
|
| A17: | a. By installing a RADIUS server, it is possible to move the workload associated with authentication to a dedicated server. A proxy server would not improve the dial-up connection's performance. There is no such thing as a Kerberos server or an IPSec server. For more information, see the section “Security Protocols,” in this chapter. |
| 18: | Your company wants to create a secure link between two networks over the Internet. Which of the following protocols would you use to do this?
|
| A18: | c. To establish the VPN connection between the two networks, you should use PPTP. PPP is a protocol used on dial-up links. A VPN is a type of network, not a protocol. SLIP is a nonsecure dial-up protocol. For more information, see the section “Types of Remote Access,” in this chapter. |
| 19: | Which of the following protocols does PPTP use to establish connections?
|
| A19: | d. PPTP uses TCP. None of the other answers are valid. For more information, see the section “Remote Access Protocols and Services,” in this chapter. |
| 20: | You are working for a client on a remote access connectivity solution. The client wants to use the RAS service for up to 10 clients at the lowest possible cost. Which of the following operating systems would you recommend to the client?
|
| A20: | d. Windows 2000 Server supports more than 10 remote clients. Windows Me is not capable of being a RAS server. Novell NetWare does not include RAS server capability because RAS is a Microsoft product. Windows 2000 Professional supports only a single dial-in RAS connection. For more information, see the section “Remote Access Protocols and Services,” in this chapter. |
Suggested Readings and Resources
1. Habraken, Joe . Absolute Beginner's Guide to Networking, third edition. Que Publishing, 2001.
2. Shinder, Debra Littlejohn . Computer Networking Essentials. Cisco Press, 2001.
3. Fortenberry, Thaddeus . Windows 2000 Virtual Private Networking. New Riders Publishing, 2000.
4. Yuan , Ruixi , W. Timothy Strayer . Virtual Private Networks: Technologies and Solutions. Addison-Wesley, 2001.
5. Computer networking tutorials and advice, compnetworking.about.com.
6. “TechEncyclopedia,” www.techencyclopedia.com.
7. Information on L2TP from Cisco, www.cisco.com/warp/public/cc/pd/iosw/tech/l2pro_tc.htm.
8. Microsoft RAS information, www.microsoft.com/technet/treeview/default.asp?url=/technet/itsolutions/network/default.asp.
9. Thin client (ICA) information from Citrix, www.citrix.com.
10. Independent thin client information, www.mcc.ac.uk/Thin/gothin.htm.
11. Information on VPNs, including security protocols, www.vpnc.org.