Apply Your Knowledge
Exercises
6.1. Installing the DHCP Server Service and Configuring a DHCP Scope
In most networks, clients are able to obtain TCP/IP information from a DHCP server. Therefore, most network administrators are required to both install and manage a DHCP server.
In this exercise, you walk through the steps involved in installing a DHCP server on Windows 2000 Server, and you configure DHCP scopes.
NOTE
Authorizing DHCP Servers in Active Directory In an Active Directory environment, DHCP servers must be authorized in the directory before they can be used. This is beyond the scope of this exercise, but it must be understood in production environments.
1. |
Select Start, Settings, Control Panel. The Windows 2000 Control Panel appears. |
2. |
Locate and double-click the Add/Remove Programs icon in Control Panel. The Add/Remove Programs dialog box appears. Choose the Add/Remove Windows Components button on the left side of the screen. |
3. |
The Windows Components Wizard dialog box, shown in Figure 6.13, appears. Figure 6.13. The Windows Components Wizard dialog box.
|
4. |
Select Network Services, and then click the Details button. The Networking Services dialog box, shown in Figure 6.14, appears. Figure 6.14. The Networking Services dialog box.
|
5. |
From the Networking Services dialog box, it is possible to install a number of Windows 2000 network services. Select the DHCP option and click OK. The installation of the DHCP service begins. |
6. |
If your system is already configured to use DHCP—for instance, if you use a DHCP address from your ISP—you need to enter a static IP address. For this exercise, you can use one of the private IP addresses discussed in this chapter. An example is 192.168.2.1. |
7. |
After DHCP has been installed, you can access it by selecting Start, Administrative Tools, DHCP. The DHCP management console, shown in Figure 6.15, appears. Figure 6.15. The DHCP management console.
|
8. |
Before you can install DHCP scopes, you have to add the DHCP server. To do this, select Action, Add Server. You are then prompted to add a server to the console. Enter the IP address of your server. In this case, you can use the private IP address 192.168.3.1. After you enter this address, click OK. The DHCP server becomes visible in the DHCP configuration screen. |
9. |
Ensure that the IP address you entered as the DHCP server is the same as the IP address of your internal network interface card. If it is not the same, the system will not recognize the DHCP server. Figure 6.16 shows the error message you get when the IP addresses of the internal NIC and the DHCP server do not match. Figure 6.16. The Cannot Find the DHCP Server error message.
|
10. | |
11. |
The New Scope Wizard guides you through the process of establishing a scope for the network. Click Next to continue with the New Scope Wizard. |
12. |
The second screen in the New Scope Wizard requires you to identify the name and description of the scope. This information is used for identification and to describe the purpose of the scope. Enter a name and a description, and then click Next. |
13. |
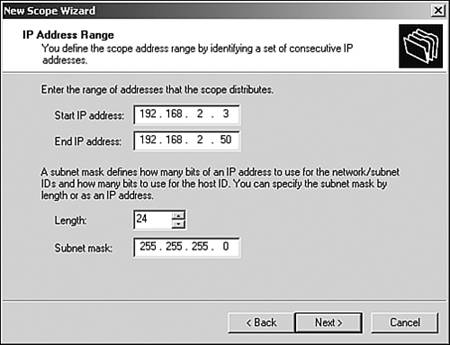
The next screen in the wizard (see Figure 6.17) requires you to specify the range of addresses that the scope will use. These are the addresses that will be assigned to the client computers on the network. For this exercise, enter a range from the private address range; for instance, start at 192.168.2.3 and end at 192.168.2.50. This range allows 47 computer systems to automatically receive IP addresses from the DHCP server. Notice that when the start and end ranges are typed in, both the length and subnet mask are automatically filled in. Leave these settings as they are and click Next. Figure 6.17. Inputting IP address ranges.
|
14. |
On this screen, identify any exclusions in the range of addresses. For this exercise, exclude the addresses from 192.168.2.14 to 192.168.2.21. Enter these addresses and click Add. The addresses are then excluded and will not be automatically assigned to client systems, but they can be manually assigned to other devices. Click Next to continue. Figure 6.18 shows the excluded IP address. Figure 6.18. Excluded IP addresses in a DHCP scope.
|
15. | |
16. |
You are prompted to configure the DHCP options. Select No, I Will Configure These Options Later, and click Next. |
17. |
The final screen in the wizard indicates that you have successfully completed the New Scope Wizard. |
18. |
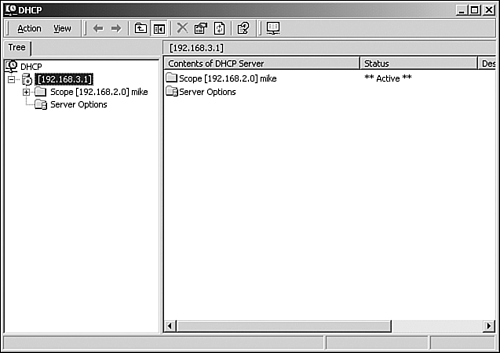
You are returned to the DHCP configuration screen, where the newly created scope appears. Notice in Figure 6.19 that beside the scope is a red arrow that points down. This lets you know that the scope is not yet active and cannot give IP addresses to clients. To activate the scope, right-click on the new scope and select Activate from the menu that appears. Figure 6.19. A deactivated DHCP scope.
|
19. |
When the scope has been activated, a green arrow appears by the scope. Figure 6.20 shows an activated DHCP scope. Figure 6.20. An activated DHCP scope.
|
Exam Questions
| 1: | What is the function of HTTP?
|
| A1: | a. Web browsers use HTTP to retrieve text and graphic files from Web servers. Answer b describes NTP, Answer c describes SSH or Telnet, and Answer d describes the function of WINS. For more information, see the section “TCP/IP Protocols,” in this chapter. |
| 2: | On a DHCP system, what term is given to the period of time for which a system is assigned an address?
|
| A2: | c. The term lease is used to describe the amount of time a DHCP client is assigned an address. All the other terms are invalid. For more information, see the section “TCP/IP-Based Network Services,” in this chapter. |
| 3: | When using FTP, which command would you use to upload multiple files at once?
|
| A3: | c. The mput command, which is an abbreviation for multiple put, allows more than one file to be uploaded at a time. mget is used to download multiple files in a single command, put is used to upload a single file, and get is used to download a single file. For more information, see the section “TCP/IP Protocols,” in this chapter. |
| 4: | During a discussion with your ISP's technical support representative, he mentions that you might have been using the wrong FQDN. Which TCP/IP-based network service is he referring to?
|
| A4: | d. DNS is a system that resolves hostnames to IP addresses. The term FQDN is used to describe the entire hostname. None of the other services use FQDNs. For more information, see the section “TCP/IP-Based Network Services,” in this chapter. |
| 5: | What is the function of ARP?
|
| A5: | c. ARP resolves IP addresses to MAC addresses. Answer a describes the function of RARP, Answer b describes the process of WINS, and Answer d describes the process of DNS resolution. For more information, see the section “TCP/IP Protocols,” in this chapter. |
| 6: | What is the function of NTP?
|
| A6: | d. NTP is used to communicate time synchronization information between devices. All the other answers are invalid. For more information, see the section “TCP/IP Protocols,” in this chapter. |
| 7: | Which port is assigned to the POP3 protocol?
|
| A7: | d. POP3 uses port 110 for network communication. Port 21 is used for FTP, port 123 is used by NTP, and port 443 is used by HTTPS. For more information, see the section “TCP/UDP Ports,” in this chapter. |
| 8: | You decide to move your network from NetBEUI to TCP/IP. For the external interfaces, you decide to obtain registered IP addresses from your ISP, but for the internal network, you choose to configure systems by using one of the private address ranges. Of the following address ranges, which one would you not consider?
|
| A8: | b. The 131.16 range is not one of the recognized private IP address ranges. All the other address ranges are valid IP address ranges. For more information, see the section “IP Addressing,” in this chapter. |
| 9: | Which of the following addresses is a Class B address?
|
| A9: | a. Class B addresses fall into the range 128 to 191. Therefore, Answer a is the only one of the addresses listed that falls into that range. Answer b is a Class A address, and Answers c and d are both Class C IP addresses. For more information, see the section “IP Addressing,” in this chapter. |
| 10: | Consider the IP address 195.16.17.8. Assuming that the default subnet mask is being used, which part of the address would be considered the network address?
|
| A10: | b. The address given is a Class C address and therefore, if you are using the default subnet mask, the first three octets represent the network address. None of the other answers are valid. For more information, see the section “IP Addressing,” in this chapter. |
| 11: | When you are configuring a new server application, the manual tells you to enable access through port 443. What kind of application are you configuring?
|
| A11: | d. Port 443 is used by HTTPS. Therefore, the application you are configuring is likely to be a secure Web site application. None of the other answers are valid. For more information, see the section “TCP/UDP Ports,” in this chapter. |
| 12: | Which of the following is the correct broadcast address for the Class A network 14?
|
| A12: | d. The broadcast address for a network uses the network ID, and all other octets in the address are set to all nodes, to indicate that every system should receive the message. Therefore, with a network address of 14, the broadcast address is 14.255.255.255. None of the other answers are valid. For more information, see the section “IP Addressing,” in this chapter. |
| 13: | What is the purpose of a reverse lookup in DNS?
|
| A13: | a. A reverse lookup resolves an IP address to a hostname rather than the hostname-to-IP address resolution normally performed by DNS. Answer b describes the functions of WINS, Answer c describes the process of a standard DNS resolution, and Answer d is not a valid answer. For more information, see the section “TCP/IP-Based Network Services,” in this chapter. |
| 14: | You ask your ISP to assign a public IP address for the external interface of your Windows 2000 server, which is running a proxy server application. In the email message you get that contains the information, the ISP tells you that you have been assigned the IP address 203.15.226.12/24. When you fill out the subnet mask field on the IP configuration dialog box on your system, what subnet mask should you use?
|
| A14: | b. In CIDR terminology, the number of bits to be included in the subnet mask is expressed as a slash value. If the slash value is 24, the first three entire octets form the subnet mask, so the value is 255.255.255.0. None of the other answers are correct. For more information, see the section “IP Addressing,” in this chapter. |
| 15: | You are the administrator for a small network of 25 PCs. All the workstations are Windows 2000 Professional systems, and the server is a Windows 2000 Server system. Presently, the only Internet access is from a single PC that uses a modem, but your manager has asked you to get cable Internet access and share the connection with all the other workstations on the network. Which of the following services might you use to accomplish this?
|
| A15: | b. As its name implies, ICS allows a single Internet connection to be shared among multiple computers. None of the other services mentioned are used in shared Internet access. For more information, see the section “TCP/IP-Based Network Services,” in this chapter. |
| 16: | You are troubleshooting a problem with a system: A single workstation is unable to communicate with a server on another network; however, it is able to communicate with the other systems on its own segment. All the other workstations on the subnet are able to contact the server on the remote network. Which of the following is most likely the cause of the problem?
|
| A16: | c. The symptoms described indicate that the default gateway configuration on the system in question is likely incorrect. If Answer a or Answer b were correct, you would not be able to connect to other systems on the same subnet. If Answer d were correct, other systems would not be able to access the remote server, which, according to the question, you are able to do. For more information, see the section “Default Gateways,” in this chapter. |
| 17: | Which of the following addresses is a valid IPv6 address?
|
| A17: | b. IPv6 addresses are expressed in hexadecimal format and can therefore use only the letters A through F and numbers. They are also expressed in eight parts. None of the other answers fit these criteria. For more information, see the section “IP Addressing,”in this chapter. |
| 18: | While examining the data statistics for your network, you notice that there is a large amount of NetBIOS name resolution traffic being generated. What might you do to remedy this problem?
|
| A18: | b. A WINS server allows client computers to perform NetBIOS name-to-IP address resolution without broadcasting. None of the services listed in the other answers can reduce the amount of NetBIOS resolution traffic. For more information, see the section “TCP/IP-Based Network Services,” in this chapter. |
| 19: | In SNMP, what message is sent by a system in the event of a threshold being triggered?
|
| A19: | b. The term used to refer to a message sent by an SNMP agent when a condition is met is trap message. None of the other terms are used to describe the message sent by SNMP. For more information, see the section “TCP/IP-Based Network Services,” in this chapter. |
| 20: | Which of the following port ranges is described as “well known”?
|
| A20: | a. Well-known ports are defined in the range 0 to 1023. Answer b describes the range known as registered ports 1024 to 49151. Answer c describes the dynamic, or private, ports, which range from 49152 to 65535. Answer d is not a valid answer. For more information, see the section “TCP/UDP Ports,” in this chapter. |
Suggested Readings and Resources
1. Habraken, Joe. Absolute Beginner's Guide to Networking, third edition. Que Publishing, 2001.
2. Shinder, Debra Littlejohn . Computer Networking Essentials. Cisco Press, 2001.
3. Comer, Douglas E. Complete TCP/IP Training Course, student edition. Prentice Hall PTR, 2001.
4. Hunt, Craig . TCP/IP Network Administration, third edition. O'Reilly & Associates, 2002.
5. Subnetting information, www.howtosubnet.com.
6. Computer networking tutorials and advice, compnetworking.about.com.
7. General TCP/IP and networking information, www.cisco.com.
8. “TechEncyclopedia,” www.techencyclopedia.com.
9. Links to various TCP/IP resources, www.private.org.il/tcpip_rl.html.