9.3. Malicious-information Propagation Modeling
In this section, we present an analytical model which is able to capture the behavior of malicious IDD (modeled as SIS epidemics) in wireless multihop networks. Contrary to the case of useful information, regarding malicious/indifferent information, one is interested in the robustness capabilities of the network to sustain such traffic, which in both cases, it is of no use (or it can even be harmful in case of malware). The presented analytical model is based on the approach exploiting queuing theory, but contrary to Chapter 4, here it was applied on the wireless complex topologies shown in Table 9.2.
Contrary to the SI model, in the SIS paradigm employed for the malicious-information spreading, average quantities are of interest, while in the SI model instantaneous quantities were considered, as in the long-run the SI network converges to a pandemic (all nodes are informed) state.
9.3.1. SIS Closed Queuing Network Model
In this subsection, some of the material presented in the previous subsections is repeated, but also modified appropriately. For clarity and completeness purposes, we present such material in its proper sequence, stressing on the emerging reusability of the involved methodologies.
In the SIS paradigm, susceptible (noninformed) nodes essentially wait until the arrival of malicious information, in which case they alter to the infected (informed) state. A propagative network is considered, where nodes spread further the malicious information they receive. Consequently, a node might become infected from malicious software either from an attacker or an already infected legitimate node. This holds for several types of viruses and worms that have appeared [133,197]. Infections are assumed to arrive in a nondeterministic fashion. The recovery process (disposing malicious software) is of similar nature, but not necessarily of the same waiting behavior. Throughout the rest of this subsection, following current literature [80], it is assumed that the infection arrival process is Poisson, while the recovery process of each network node is exponentially distributed. The infection arrival rate in link  is denoted by
is denoted by  and the recovery rate of node
and the recovery rate of node  by
by  , as in Chapter 4.
, as in Chapter 4.
Legitimate nodes are again separated in infected and susceptible. Their transition from state to state can be mapped to a closed two-queue packet network, as shown in Fig. 4.3[48], where 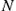 customers, i.e. network nodes, circulate. At any instance, if
customers, i.e. network nodes, circulate. At any instance, if  nodes are infected, then
nodes are infected, then  are susceptible. Both service rates are state-dependent according to the number of packets (user nodes) that exist in the corresponding queue at each time instance. Explicit definition of each queue’s equivalent service rate, which is state-dependent, i.e.
are susceptible. Both service rates are state-dependent according to the number of packets (user nodes) that exist in the corresponding queue at each time instance. Explicit definition of each queue’s equivalent service rate, which is state-dependent, i.e.  and
and  (for the corresponding system states with
(for the corresponding system states with  infected and
infected and  susceptible nodes), depends on the underlying complex network and employed infection paradigm. Without loss of generality, we assume that the lower queue represents the group of infected legitimate nodes and denote it as “infected,” while the upper queue represents the susceptible nodes and we denote the queue as “susceptible.” The state-dependent service rate of the susceptible queue can be extended to the case of multiple malicious-information sources (i.e. attackers), in which case the service rate will have the form
susceptible nodes), depends on the underlying complex network and employed infection paradigm. Without loss of generality, we assume that the lower queue represents the group of infected legitimate nodes and denote it as “infected,” while the upper queue represents the susceptible nodes and we denote the queue as “susceptible.” The state-dependent service rate of the susceptible queue can be extended to the case of multiple malicious-information sources (i.e. attackers), in which case the service rate will have the form  ,
,  being the number of attackers. Our analysis here is focused on the case of a single attacker (i.e.
being the number of attackers. Our analysis here is focused on the case of a single attacker (i.e.  ).
).
Standard methodology from Chapter 4 may be employed to analyze the two-queue closed network. The focus is on the infected queue. Its steady-state distribution, denoted by  , represents the probability that there are
, represents the probability that there are  packets (nodes) in this queue. Using balance equations for the respective Markov chain, the explicit expression for the steady-state distribution can be obtained as
packets (nodes) in this queue. Using balance equations for the respective Markov chain, the explicit expression for the steady-state distribution can be obtained as
 (9.23)
(9.23)
where  is the probability of no infected nodes in the network. Applying the normalization condition
is the probability of no infected nodes in the network. Applying the normalization condition  , and appropriately specifying the total infection and recovery rates (where
, and appropriately specifying the total infection and recovery rates (where  and
and 
 ), and by setting
), and by setting  (following the reasoning presented in Section 9.2.4 and in Chapter 4) and considering a large number of legitimate nodes, the probability of no infected nodes can be approximated as
(following the reasoning presented in Section 9.2.4 and in Chapter 4) and considering a large number of legitimate nodes, the probability of no infected nodes can be approximated as
 (9.24)
(9.24)
and the steady-state distribution can be approximated as
 (9.25)
(9.25)
where  is the steady-state distribution for the noninfected queue. Using Eq. (9.25), the probability of a completely infected network equals
is the steady-state distribution for the noninfected queue. Using Eq. (9.25), the probability of a completely infected network equals  . It is noted that the error introduced by the above approximation is negligible for values of
. It is noted that the error introduced by the above approximation is negligible for values of  and
and 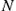 commonly used in practice (in the order of less than
commonly used in practice (in the order of less than  ).
).
Eq. (9.25) clearly indicates the critical parameters that affect the behavior of the system. Assuming a fixed area of the network deployment region, the number of legitimate nodes (i.e. the density of the network) along with the common transmission radius and the ratio of the link infection rate to the node recovery rate are decisive factors regarding the overall behavior and stability of the system.
Based on such model, the expected number of infected (informed) nodes (corresponding to the expected number of packets in the lower queue) for different types of networks may be obtained. The general expression yielded has a Poisson form, due to approximation (9.25),
 (9.26)
(9.26)
where  is the steady-state distribution of the underlying Markov chain, and
is the steady-state distribution of the underlying Markov chain, and  is the equivalent of the
is the equivalent of the  parameter mentioned above for a HeMPC network (wireless multihop) over a square deployment region of side
parameter mentioned above for a HeMPC network (wireless multihop) over a square deployment region of side  and each node having a transmission radius
and each node having a transmission radius  . For all other types of networks,
. For all other types of networks,  , where
, where 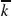 is the average node degree for each network under discussion (
is the average node degree for each network under discussion ( and
and 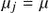 for all
for all  ,
,  without loss of generality).
without loss of generality).
Observing the analytic form of the average number of infected nodes for each network type, according to the specific expression of  , a major difference between HeMPC networks and the rest should be noted. More specifically, in a HeMPC, the spatial dependence among nodes (due to their multihop nature) is reflected by the fraction
, a major difference between HeMPC networks and the rest should be noted. More specifically, in a HeMPC, the spatial dependence among nodes (due to their multihop nature) is reflected by the fraction  representing the coverage percentage of each node with respect to the whole network area. On the contrary, in the expression of
representing the coverage percentage of each node with respect to the whole network area. On the contrary, in the expression of  for the rest of the networks for which the topology is mainly based on connectivity relations and not spatial dependence as in the multihop case, the corresponding quantity expressing the local neighbor impact is expressed by
for the rest of the networks for which the topology is mainly based on connectivity relations and not spatial dependence as in the multihop case, the corresponding quantity expressing the local neighbor impact is expressed by  . It is evident, that for the rest of network types, quantity
. It is evident, that for the rest of network types, quantity  expresses solely the special connectivity properties of the employed network through the value of
expresses solely the special connectivity properties of the employed network through the value of 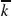 , since for these networks, no spatial dependence is expressed in their connectivity graph and thus, no such spatial feature has impact on IDD.
, since for these networks, no spatial dependence is expressed in their connectivity graph and thus, no such spatial feature has impact on IDD.
The average throughput of the susceptible queue  , corresponding to the average rate that nodes receive malicious information, can be computed as
, corresponding to the average rate that nodes receive malicious information, can be computed as
 (9.27)
(9.27)
Demonstration
As already mentioned, contrary to the SI model, in the SIS paradigm employed for the malicious-information spreading, average quantities are of interest, while in the SI model instantaneous quantities were considered, as in the long-run the SI network converges to a pandemic (all nodes are informed) state. Especially the average number of infected legitimate nodes is the most important quantity, since malicious information is of recurrent nature and if one observes the system macroscopically, nodes oscillate between the {S}, {I} states.
Fig. 9.12 shows the average number of infected nodes with respect to the infection/recovery ratio for various types of complex networks. It is evident that as the ratio  increases,
increases,  increases for all types of networks, denoting greater probability of users to get malicious information from a communication link. Parameters for each type of network are in accordance with the notation employed in the classification of Section 9.2.3.
increases for all types of networks, denoting greater probability of users to get malicious information from a communication link. Parameters for each type of network are in accordance with the notation employed in the classification of Section 9.2.3.

FIGURE 9.12 Average number of infected users of the legitimate network  as a function of
as a function of  . From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.
. From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.
 as a function of
as a function of  . From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.
. From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.With respect to ad hoc networks (HeMPC), the greatest the transmission radius of nodes, the denser the network, and thus the easier the malicious data to be spread. Especially for ad hoc networks, the dependence of the average number of infected nodes on the number of legitimate nodes is linear as shown in Fig. 9.13. The combination of larger values of  and
and  yields the higher number of
yields the higher number of  for all values of legitimate nodes, while the combination with smaller values of
for all values of legitimate nodes, while the combination with smaller values of  and
and  yields the lower values of
yields the lower values of  . It should be noted that the behavior of the spreading dynamics of the network is more sensitive to changes in the value of
. It should be noted that the behavior of the spreading dynamics of the network is more sensitive to changes in the value of  rather than variations in
rather than variations in  .
.

FIGURE 9.13 Average number of infected nodes  as a function of
as a function of 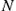 (numerical result). From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.
(numerical result). From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.
 as a function of
as a function of 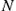 (numerical result). From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.
(numerical result). From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.Similarly to HeMPC networks, in ER networks, the greatest the probability two nodes are connected (thus the denser the network is), the easier for malicious information to propagate on average. Such property may be also identified with the rest of the network types, leading to the following.
For regular, random (ER type), SW (WS type), and SF (BA type) networks with the same 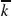 , the same result would be obtained, due to the expression of
, the same result would be obtained, due to the expression of  given before. In order to better demonstrate the different robustness properties of these network types, in Fig. 9.12, a different
given before. In order to better demonstrate the different robustness properties of these network types, in Fig. 9.12, a different 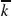 value was employed. The term robustness is meant here in the sense of resistance to malware diffusion so that a sufficient amount of susceptible nodes maintains the operation of the network. Regarding the different types of networks, HeMPC (ad hoc) is close to ER (HoMEC), exhibiting that in general, randomness aids the spreading of malicious information. This is a very useful outcome with significant practical value for designing efficient countermeasures for malign IDD. On the contrary, a regular lattice (HoMPC) makes the spread of malicious information more difficult, since each node is only connected to a typically small number of other nodes and it would take significant effort to quickly spread malicious information throughout the whole network. Similarly, WS (HoMUC) and BA (HeMUC) exhibit robustness closer to lattice networks, as their topologies are derived from such regular arrangements [164]. Among the latter three categories, a SF (BA) network may be more prone to spreading than a lattice (as shown in Fig. 9.12), because for the specific network instances, the given BA network is more dense than the lattice (the BA has mean degree
value was employed. The term robustness is meant here in the sense of resistance to malware diffusion so that a sufficient amount of susceptible nodes maintains the operation of the network. Regarding the different types of networks, HeMPC (ad hoc) is close to ER (HoMEC), exhibiting that in general, randomness aids the spreading of malicious information. This is a very useful outcome with significant practical value for designing efficient countermeasures for malign IDD. On the contrary, a regular lattice (HoMPC) makes the spread of malicious information more difficult, since each node is only connected to a typically small number of other nodes and it would take significant effort to quickly spread malicious information throughout the whole network. Similarly, WS (HoMUC) and BA (HeMUC) exhibit robustness closer to lattice networks, as their topologies are derived from such regular arrangements [164]. Among the latter three categories, a SF (BA) network may be more prone to spreading than a lattice (as shown in Fig. 9.12), because for the specific network instances, the given BA network is more dense than the lattice (the BA has mean degree  , while the lattice
, while the lattice  for the same number of network users). The following observations may be derived from the above analysis.
for the same number of network users). The following observations may be derived from the above analysis.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
