9.2. Dynamics of Information Dissemination
9.2.1. Introduction to Information Dissemination
Information dissemination (diffusion) has been a key social process, but especially in modern information-centric societies, it has become one of the most critical ones [46–48,59]. Furthermore, it can be observed that most of the commercial communication infrastructures have been initially developed in the last thirty years mainly to allow transferring diverse types of information. There are different types of information disseminating in human societies and especially through the computer and communications networks available. These different types range in scope (e.g. academic, educational, healthcare, gossip, financial, and military to name a few), criticality (e.g. confidential, noise-sensitive, and public information), value (e.g. low/medium/high cost and invaluable), and overall desire by human consumers (e.g. useful, harmful, and indifferent).
Recent advances in networking infrastructures and services developed have been partially stimulated in order to accommodate the emerging trends of increasing volumes and service demands of disseminated information, in conjunction with the diversity of information types, as explained above. In general, with respect to the manner that each piece of information is received by human users, information may be distinguished in three types, characterized of useful, malicious, or indifferent content and denoted accordingly. Each type is analyzed in more detail in the following.
Useful information consists of many diverse types of data, all of which are expected to be of some immediate or later use by the end-users. It may consist of news, multimedia content, financial, healthcare, educational data, etc. People are willing to accept such types of information, and usually store it for further use, e.g. e-books and health examinations. Consequently, with respect to useful information, a single state transition takes place for a user, namely, from the state of not having it to the state of having received and stored the information.
On the other hand, users may receive malicious information, most prominently malware. The users are, in principle, reluctant to accept and/or use this type of information. Frequently, the producers and distributors of malicious information devise ways to have their information accepted by some users, e.g. by hiding it in other types of useful or indifferent information, such as email viruses. Furthermore, the sources of malicious information also manage to devise new ways of spreading such data, by using hybrid diffusion means, alternating transmission channels they distribute their threats, and in general discovering new well-hidden methods for entrapping their victims. The net result of this trend is that malicious content is characterized by recurrent behavior, i.e. by a SIS diffusion model explained in the previous chapters. Users will eventually find a way to remove the currently diffusing malware. However, and depending on their level of acquaintance, they will become prone to become infected by the same or new malware that will disseminate in the network at a future time. This of course costs in time and money to the end-users that become victims.
Finally, indifferent information describes cumulatively multiple and diverse types of information that disseminates in societies, nowadays mostly through the Internet and social networks, that the user is not willing to follow, but at the same time the user does not consider harmful. Characteristic cases of indifferent information include spam email (typically unwanted advertisements, etc.), pop-up advertisements in various websites, leaflets in the general case, and other email targeted for general promotional purposes. The user typically discards such information, but relevant messages are of recurrent nature, namely, they are repeated at frequent rates in order to achieve their goal. Sometimes users can be bothered by very frequent recurring indifferent information; however, most of the times the user cannot do much to restrict or discard them. Characteristic examples include phishing email messages and promotional/discount pop-ups are various electronic shopping websites.
We should note that although malicious and indifferent types of information are essentially of different nature in terms of context, in many occasions, their diffusion nature is identical, or at least very similar. Thus, later in this chapter, we use the same SIS infection model to study their propagation. The reader should keep in mind their diverse contextual nature and use the corresponding models appropriately given the specific application framework they emerge.
Thus, it may be observed that the various types of information disseminated through networks and humans resemble different cases of malware and epidemic diffusion. Consequently, given specific assumptions, it may be possible to model the information dissemination via malware diffusion modeling techniques. In this section, we focus especially on these cases of application of the previously proposed malware diffusion modeling frameworks on information dissemination over wireless complex communication networks. As already explained in Part 1 of the book, modern networks typically consist of various complex subnetworks [164], which eventually merge as a heterogeneous large-scale network, possibly connecting to a wired infrastructure (Fig. 9.7). This is the trend in future 5G and heterogeneous networks, where contemporary users, equipped with devices having various radio interfaces, can communicate with each other in more complicated ways than in the past and utilizing multiple subnetworks. For example, a user may communicate with another user via mobile phone over cellular networks, while also communicating with a different user in his/her geographic vicinity via WiFi [107] or Bluetooth [230]. In order to evaluate the dynamics of information dissemination (information dissemination dynamics — IDD) in such heterogeneous complex communication networks, where communications are affected by both social relations (at overlay networks, e.g. social network) and physical proximity (contacts of network nodes by exchanging packets point-to-point), novel analytical models exhibiting parameters representing IDD for different types of underlying communication networks are required. In this section, as already explained, a radical approach of using a mapping between malware diffusion and information dissemination is presented and exploited for studying the dynamics of IDD, and moreover for obtaining means to control the IDD.

FIGURE 9.7 Contemporary wireless complex communication network architecture depicting all the considered and converged types of networks, including interconnections to wired backhauls. From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.
In the following, we present a generic modeling framework for IDD and discuss the analogy to epidemics models for describing such dynamic operation. Within this framework, specific IDD models for different types of complex networks and assessment metrics are developed. Different analytical approaches for describing useful-information dissemination malicious/indifferent-information spreading are presented and briefly analyzed, followed by indicative evaluation results.
9.2.2. Previous Works on Information Dissemination
Information dissemination modeling has attracted significant attention the past years, with numerous works attempting to provide accurate and effective frameworks and techniques for modeling the spreading of information, many of which have focused mainly on wireless networks from as early as 1999 [97]. An indicative comparison of such protocols may be cumulatively found in [4]. However, the approaches in [97] are not based on traditional epidemic models, such as those presented in Chapter 3, e.g. [8] and [9]. Both [8] and [9] are involved in the development of adaptive bio-inspired information dissemination models for wireless sensor networks. However, such models consider only this specific type of networks and in addition they consider one type of information propagating in the network. Another type of approaches are probabilistic ones, such as those described in [131], and the family of gossip methods, such as those in [129], [91], [41], which are based on a combination of random walk protocol variations and epidemic routing techniques. These randomized techniques have additionally stirred novel research in information dissemination for delay-tolerant (intermittently connected) networks, such as those presented in [156] and [95], where combinations of probabilistic methods, gossip algorithms, or other epidemics based approaches can be used.
The main problem with all the above families of approaches and individual techniques is that typically, in most of these approaches only one type of information is considered over a specific network topology. The objective of each such approach is to spread the information to as many users as possible. However, this is not always the case in arbitrary networks, where different types of information may propagate.
Substantial works [46,60,68,231,236] have employed an analogy of IDD in a single network as infectious spreading diseases by using ODE in the field of epidemics [58,219], which could act as a quick reference to efficiently gather approximate knowledge of information dissemination speed and status with various settings of average node degrees and attain further control [47] in those networks. A more thorough summary of such protocols can be found in [4]. However, IDD are further complicated in wireless complex communication networks due to the presence of dynamic behaviors regarding the variability of topology and user behavior. Epidemic routing protocols are characterized as those randomized approaches that are based on both stochastic processes and epidemics models, such as the ones presented in [41,91,129] and references therein.
However, all such works mainly focus on specific types of information and network topology. The framework that will be presented in the following serves as one of the early attempts to systematically analyze IDD in a generic manner and allow assessing the dissemination and robustness performance in both current and future wireless complex networks and different types of information.
The main feature of this application, which is a joint application of the epidemics and queuing frameworks presented in Parts 1 and 2, is in realizing that different dynamics are governing the propagation of different types of information and provide appropriate models for each case. Specifically, with regard to useful data, the objective is to spread such information to as many users as possible, so that useful information reaches potentially all nodes of a network. On the contrary, in the event of malicious/indifferent-information spreading, the objective is to study the robustness of various network types against harmful or indifferent, but nevertheless network-stressing content. Consequently, there are two broad types of information, short-lived, i.e. useful information, with a short circulation lifetime and long-lived information, such as malicious information, with a longer circulation lifetime. We summarize the features of these types of information that we consider most important in Table 9.1.
Table 9.1
Types of Diffusing Information and their Features
| Features | Types of Information | ||
| Desired | Malicious | Indifferent | |
| Nature | Permanent | Recurrent | Recurrent |
| Infection model | SI | SIS | SIS |

To address the above, two different paradigms have been proposed that describe the behavior of systems, a SI for the first and SIS for the second type of information. Both paradigms were inspired by drawing analogies to the field of epidemics [48]. Two specific approaches have been analyzed, and the behavior of each case is demonstrated, showing how they can be used in order to identify the parameters and properties of the underlying wireless complex communication networks that govern IDD [48].
9.2.3. Epidemic-based Modeling Framework for IDD in Wireless Complex Communication Networks
As already explained, considerably different dynamics govern the propagation of useful and malicious/indifferent types of information. Regarding the spreading process, the dissemination of useful information resembles that of an epidemic disease, in which population members that get infected by a virus permanently transit to immunization (after recovery) or termination (if the infection is lethal). In epidemics, such models are readily referred to as Susceptible-Infected (SI) [58] or susceptible-removed (SR) [177]. Such behavior is effectively described by a two-state model, where nodes are initially prone to receive epidemics (susceptible) and then permanently transit to the infected state, once they receive the epidemic (SI model). The SR model essentially expresses the same behavior when nodes are removed from the network in cases of lethal epidemics. The SI (SR) model captures the characteristic behavior, where for each node, only a single and permanent transition takes place from the susceptible to the infected (removed) state.
Recognizing the similarities between IDD and the spread of infectious diseases, ODE models in the field of epidemic [58,219] have been widely adopted as tools to analyze IDD in communication networks [46,60,68,204,231,236]. Since ODE models provide closed-form formulas for the performance metrics of IDD, a wide range of effects can be encompassed by aggregating individuals in the network into two states (i.e. infected and susceptible), and thus reducing computation time and required resources. In contrast, both agent-based emulation model presented in [230] and simulation experiments presented in [221] try to precisely capture attributes of individuals in the network and the interactions among them via massive experiments; thus, the appeals of analytical tractability are neglected. Obviously, the complexity of modeling individual-level details significantly increases with the number of individuals, and thus the ODE model is suitable to act as a quick tool to identify IDD in large complex networks.
The dissemination of useful information resembles the SI process in epidemics, since a rational user waits to receive desired or useful information and then stores it for further use. If the information is indeed useful and valid, no further transaction for this information will be required/take place. Thus, the user experiences a single state transition when (s)he receives useful information from the noninformed state (node can potentially receive data, i.e. susceptible) to the informed state (i.e. infected). Under this regime, users obtain information either from information sources, or from legitimate users that have already stored the information (already in the “I” state). Several works have provided epidemic-based models for such type of information dissemination in the Internet [218], and in wireless networks [9,156].
This is not the case however in malicious/indifferent-information dissemination. Regarding malicious-information spreading, users are reluctant to retain the malicious information they receive. However, malicious information might return (if the user is not properly protected) or adversaries are capable of devising a new malware type or package for the malicious information. With respect to indifferent information, even tough it is usually of no interest to users, it might further load an already stressed infrastructure, and especially in the case of spam, its repetitive nature might eventually become disturbing, similarly to malware. Consequently, one may consider indifferent information as a special case of malware with respect to the users’ macroscopic behavior. In our treatment, we will employ this observation, due to the fact that we will focus on modeling the macroscopic behavior of IDD. For the rest of this chapter, we will focus on “malicious” information, while keeping in mind that similar models and behaviors can be obtained for “indifferent information” as well.
In principle, a user is able to recover (i.e. dispose malicious information) and return to the previous state, where it is possible to become infected again. As will be seen later from the obtained results, the model and employed methodology is similar to that of Chapters 3 and 4. The main difference is that now the topology corresponds to a potentially mesh-like network, and thus the network graph can be now any of small-world (SW), scale-free (SF), regular, or other type, compared to the random geometric graph (RGG) of the previously studied distributed wireless networks case (Chapter 4).
This behavior resembles epidemics, where individuals become infected, then recover from a disease, and become susceptible again to a different or the same disease (if they do not properly “vaccinate”) — SIS model. Contrary to useful information, we notice that the SIS model defines two potential transitions between the two possible states of a user, namely, switch from susceptible to infected and then switch back to the susceptible state. This model has been also adopted in [190] for information dissemination, but again it is targeted toward only a specific type of information and network topology, as the SI epidemic models mentioned above.
9.2.4. Wireless Complex Networks Analyzed and Assessment Metrics
As already explained in Part 1 of the book, in Network Science (complex network theory) [22,125,155], a network represents a system of interactions. We consider a graph  consisting of a set
consisting of a set  of nodes (i.e. wireless terminals or Internet users) and a set
of nodes (i.e. wireless terminals or Internet users) and a set  of undirected edges (i.e. physical channels). The number of nodes is denoted by
of undirected edges (i.e. physical channels). The number of nodes is denoted by 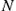 . In this consideration of complex networks and without loss of generality, in order to focus on the IDD rather than on the wireless propagation details, two nodes connected by a link are called neighbors and the number of neighbors for a node is defined as the degree
. In this consideration of complex networks and without loss of generality, in order to focus on the IDD rather than on the wireless propagation details, two nodes connected by a link are called neighbors and the number of neighbors for a node is defined as the degree  . We consider the degree distribution
. We consider the degree distribution  , as the probability of having
, as the probability of having  channels for a node and
channels for a node and  as the mean value of
as the mean value of  . Also, it is assumed that there is at most one edge between any node pair and no self loops in
. Also, it is assumed that there is at most one edge between any node pair and no self loops in  .
.
By employing the aforementioned analogy to epidemics and malware diffusion, IDD can be effectively described and mathematically analyzed for different types of complex communication networks and their topologies. Each network type is characterized by different topological features and the proposed approach allows in both cases of useful and malicious information to identify the impact of each topology on the IDD performance and robustness. The classification of these models will be based on the following critical parameters involved:
• Degree distribution: It provides a suitable representation of the structure of a network, especially for social ones (networks that their topology is of relational nature, rather than spatial). Based on the degree distribution, a network is of homogeneous mixing if the degree distribution of each node is centered around  and the degree variance
and the degree variance 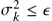 , i.e. that the degree variance is smaller than some threshold level. Otherwise, it is of heterogeneous mixing.
, i.e. that the degree variance is smaller than some threshold level. Otherwise, it is of heterogeneous mixing.
• Link connectivity: The finite transmission range of a wireless node determines its neighborhood. Moreover, wireless channel quality affects the success of transmissions. The transmission range and channel quality jointly affect link connectivity.
Connectible networks: For a network with variable connectivity, the network is (partially) connectible, if each node has a positive probability to establish an undirected connection to any other node in the network. A network with (different) same connection probability in each node is defined as (un)equally connectible. Regarding connectible networks, the probability to establish an undirected connection to any other node in the network involves a partial set of nodes in the network, not all of them.
Additional properties may be identified, capturing topological properties of the underlying complex networking infrastructures, and could be exploited for analyzing IDD in these types of networks. The clustering coefficient (indicative of the clusters building up due to social or other types of interaction) and the average path length between randomly selected node pairs are appropriate quantities [164]. Based on the specific metrics, the complex networks of interest for the analysis of the IDD via malware diffusion techniques can be classified in five main categories, cumulatively depicted in Table 9.2.
Table 9.2
Complex Network Classification
| Connectivity Mixing Type | Partially Connectible | Equally Connectible | Unequally Connectible |
| Homogeneous mixing | Lattice network wireless sensor network | ER network | Small-world network |
| Heterogeneous mixing | Machine-to-machine network wireless mesh, smart grid | Scale-free network |

Homogeneous Mixing and Partially Connectible (HoMPC): In a (regular) lattice with degree  every node connects to its
every node connects to its  nearest neighbors [23]. A lattice is a HoMPC network since the degree distribution is a delta function with magnitude equal to
nearest neighbors [23]. A lattice is a HoMPC network since the degree distribution is a delta function with magnitude equal to  located at
located at  [23]. Another example of HoMPC networks is wireless sensor networks, where sensors are uniformly and randomly distributed on a plane [202]. In the case of grid-based sensor networks, the number of neighbors in the communication radius of a sensor is fixed, which behaves exactly as a HoMPC network.
[23]. Another example of HoMPC networks is wireless sensor networks, where sensors are uniformly and randomly distributed on a plane [202]. In the case of grid-based sensor networks, the number of neighbors in the communication radius of a sensor is fixed, which behaves exactly as a HoMPC network.
Homogeneous Mixing and Equally Connectible (HoMEC): ER random graphs [67] assume that an edge is present with probability  for
for  possible edges. The degree distribution of an ER network in relatively large networks is
possible edges. The degree distribution of an ER network in relatively large networks is
 (9.14)
(9.14)
where  . The above is a Poisson distribution that is homogeneously mixing because the variance is
. The above is a Poisson distribution that is homogeneously mixing because the variance is  , which is orders of magnitude less than
, which is orders of magnitude less than  , for large
, for large 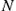 . It is observed that the degree distribution is centered around
. It is observed that the degree distribution is centered around  and a node has equal probability
and a node has equal probability  connecting to any other node in the network. Thus, an ER network is a HoMEC network. Some complex wireless networks can be effectively modeled by ER graphs, especially when considering the joint cyber-physical system forming from a social network overlaying a wireless one [198].
connecting to any other node in the network. Thus, an ER network is a HoMEC network. Some complex wireless networks can be effectively modeled by ER graphs, especially when considering the joint cyber-physical system forming from a social network overlaying a wireless one [198].
Homogeneous Mixing and Unequally Connectible (HoMUC): SW networks generated by the WS model [225] are constructed from a regular ring lattice1 with  edges for each node (where
edges for each node (where  is an integer number), and randomly rewiring each edge of the lattice with probability
is an integer number), and randomly rewiring each edge of the lattice with probability  such that self-connections and duplicate edges are excluded. The degree distribution of a SW network is
such that self-connections and duplicate edges are excluded. The degree distribution of a SW network is
 (9.15)
(9.15)
Since the degree distribution has a pronounced peak at  , it decays exponentially for large
, it decays exponentially for large  [164], and the connection probability is unequal except
[164], and the connection probability is unequal except  (extreme randomness), we regard SW as HoMUC network. This implies that as
(extreme randomness), we regard SW as HoMUC network. This implies that as  , a SW network becomes HoMEC. Many social network models are extensions of the WS model, since the HoMUC property explains well their clustering features [164]. SW topologies emerge very often in wireless complex networks, especially in cyber-physical systems with social networks overlaying the physical ones [198].
, a SW network becomes HoMEC. Many social network models are extensions of the WS model, since the HoMUC property explains well their clustering features [164]. SW topologies emerge very often in wireless complex networks, especially in cyber-physical systems with social networks overlaying the physical ones [198].
Heterogeneous Mixing and Partially Connectible (HeMPC): M2M networks [103], wireless mesh networks [5], or smart grids have potentially nonstructured degree distributions due to finite transmission range, heterogeneity in location, mobility, channel quality variations, and time-varying user behavior, eventually classifying the underlying topology as HeMPC.
Heterogeneous Mixing and Unequally Connectible (HeMUC): A HeMUC network is a power-law distributed network, i.e. having degree distribution  , with
, with  in the range
in the range  , which is also called a SF network. Barabasi and Albert observe two essential factors of SF network: growth and preferential attachment [1]. In this model, denoted by BA, every new node connects its
, which is also called a SF network. Barabasi and Albert observe two essential factors of SF network: growth and preferential attachment [1]. In this model, denoted by BA, every new node connects its  edges to existing nodes according to the preferential attachment rule, and
edges to existing nodes according to the preferential attachment rule, and  . The power-law degree distribution suggests that most nodes have few neighbors, while some “supernodes” (hubs) tend to have a great amount of neighbors. Thus, the power-law distributed network can be treated as a HeMUC network.
. The power-law degree distribution suggests that most nodes have few neighbors, while some “supernodes” (hubs) tend to have a great amount of neighbors. Thus, the power-law distributed network can be treated as a HeMUC network.
Table 9.2 summarizes the aforementioned complex network categories. Note that the size of the largest connected component (“giant component”) is also an important measure of the effectiveness of the network at information epidemics or cooperations. Regarding this, a network is saturated if the giant component size approaches the total number of nodes in the network. Otherwise, nodes may be isolated from the giant component (nonsaturated network). For instance, a giant component emerges almost surely in random graphs, if  [161].
[161].
9.2.5. Useful-information Dissemination Epidemic Modeling
As it was explained in the previous subsections, the macroscopic behavior of useful-information dissemination can be described by the SI epidemic model, in which, nodes receive the designated data once in their lifetime. In this section, we present an analytical approach for quantifying the process of useful-information dissemination in the types of complex communication networks considered above.
SI epidemic spreading model
We adopt the SI model in order to describe the IDD of useful information. In the analogy we draw between IDD and epidemics, an uninfected node in epidemics corresponds to a noninformed node in IDD, i.e. a node not having received yet useful information. On the other hand, an infected node corresponds to a node that has received and stored useful information. Such model is appropriate for describing a specific type of useful-information spreading, e.g. handbook disseminated to a population, similarly to the SI model describing the dissemination of a single viral threat. In the sequel, we will use the terms noninfected and noninformed, as well as the infected and informed terms interchangeably. Assume that 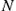 nodes are initially all susceptible noninformed except for a small number that are infected and contagious (denoted as infectious). These “contagious” nodes represent the nodes that generate the useful content to be disseminated, as will be explained in more detail in the following paragraph. Thus, by the previous analogy, in this scenario, all nodes would like to eventually become infected (i.e. informed).
nodes are initially all susceptible noninformed except for a small number that are infected and contagious (denoted as infectious). These “contagious” nodes represent the nodes that generate the useful content to be disseminated, as will be explained in more detail in the following paragraph. Thus, by the previous analogy, in this scenario, all nodes would like to eventually become infected (i.e. informed).
The infection parameter  is adopted to characterize the rate of spreading between S-I pairs. Considering the volatile nature of wireless channels and MAC, protocol operation information transmission over a communication link may not be successful. The availability (or the successful transmission rate) of a link in wireless communication channels is typically modeled as a two-state Markov chain with on and off states [84], which is sufficient for the consideration of IDD (channel propagation effects can be considered in future extensions). For a dynamic topology, the set
is adopted to characterize the rate of spreading between S-I pairs. Considering the volatile nature of wireless channels and MAC, protocol operation information transmission over a communication link may not be successful. The availability (or the successful transmission rate) of a link in wireless communication channels is typically modeled as a two-state Markov chain with on and off states [84], which is sufficient for the consideration of IDD (channel propagation effects can be considered in future extensions). For a dynamic topology, the set  of nodes is time-invariant, the set
of nodes is time-invariant, the set  of edges varies with time, while however, the network maintains its time-invariant statistical properties. The informed nodes adopt a “consistent broadcast” behavior, so that they tend to transmit the useful information to susceptible nodes in contact consistently, just as in the spread of biological viruses. Hence, the spreading rate (similar to infection rate)
of edges varies with time, while however, the network maintains its time-invariant statistical properties. The informed nodes adopt a “consistent broadcast” behavior, so that they tend to transmit the useful information to susceptible nodes in contact consistently, just as in the spread of biological viruses. Hence, the spreading rate (similar to infection rate)  is equivalent to the probability of an available channel (“on” channel state), which is independently determined for all channels such that the long time behavior of channel availability is equal to
is equivalent to the probability of an available channel (“on” channel state), which is independently determined for all channels such that the long time behavior of channel availability is equal to  .
.
Expressed quantitatively, if  and
and  are, respectively, the fraction of infected (informed) and susceptible (noninformed) nodes at time
are, respectively, the fraction of infected (informed) and susceptible (noninformed) nodes at time  , we have
, we have
 (9.16)
(9.16)
which has the same form as (3.1). Then, the simple analytic solution obtained identically as in Chapter 3 is
 (9.17)
(9.17)
From (9.17), it is clear that the informed density  approaches
approaches  as time evolves, as expected. In this study, we assume initially there is only one informed node, i.e.
as time evolves, as expected. In this study, we assume initially there is only one informed node, i.e.  . Note that the saturation2 of any complex network should serve as one of the important sufficient conditions when adopting the SI model for IDD, since the first-order differential equation in expression (9.17) fails to distinguish the saturation of a network. In the sequel, the proposed SI framework for static and dynamic saturated complex networks is presented.
. Note that the saturation2 of any complex network should serve as one of the important sufficient conditions when adopting the SI model for IDD, since the first-order differential equation in expression (9.17) fails to distinguish the saturation of a network. In the sequel, the proposed SI framework for static and dynamic saturated complex networks is presented.
Static complex networks
The static network is regarded as a time-invariant graph  where the topology is unchanged in time. Given that, in Fig. 9.8, numerical results for a regular lattice (HoMPC), an ER (HoMEC), a SW/WS (HoMUC), and a SF under the BA model (HeMUC) networks are presented, based on ensemble averages, obtained by 100 simulations in saturated complex networks. Since an ER network can be totally characterized by parameters
where the topology is unchanged in time. Given that, in Fig. 9.8, numerical results for a regular lattice (HoMPC), an ER (HoMEC), a SW/WS (HoMUC), and a SF under the BA model (HeMUC) networks are presented, based on ensemble averages, obtained by 100 simulations in saturated complex networks. Since an ER network can be totally characterized by parameters 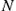 and
and  , IDD in ER is described through the SI model by adopting
, IDD in ER is described through the SI model by adopting  . However, compared to IDD in ER networks, the SI model amplifies the cumulative informed node fraction with time as it implicitly assumes the HoMEC property, resulting in inaccurate estimation. In Section 9.2.5, this discrepancy is addressed in order to obtain a more accurate IDD SI-based model.
. However, compared to IDD in ER networks, the SI model amplifies the cumulative informed node fraction with time as it implicitly assumes the HoMEC property, resulting in inaccurate estimation. In Section 9.2.5, this discrepancy is addressed in order to obtain a more accurate IDD SI-based model.

FIGURE 9.8 IDD in regular lattice (HoMPC;  ), ER (HoMEC;
), ER (HoMEC;  ), SF (HeMUC), and SW (HoMUC) networks for different
), SF (HeMUC), and SW (HoMUC) networks for different  with mean degree equal to
with mean degree equal to  ,
,  , and
, and  . From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.
. From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.
 ), ER (HoMEC;
), ER (HoMEC;  ), SF (HeMUC), and SW (HoMUC) networks for different
), SF (HeMUC), and SW (HoMUC) networks for different  with mean degree equal to
with mean degree equal to  ,
,  , and
, and  . From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.
. From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.An interesting phenomenon for the IDD in SF networks generated by the BA model can be observed. The corresponding IDD curve exceeds that of the SI model in the beginning, but at some instance  , the curve of the SI model transcends. This is in accordance with the fact that the information has higher possibility to be transmitted to supernodes than the nodes with low degrees at early stages. Once the information spreading begins, the number of informed nodes highly increases as supernodes eventually become informed. Then, the spreading rate decreases as information dissemination is now mainly propagated to nodes with lower degrees. Thus, although the SI model is not suitable for describing the IDD in SF networks, it still provides useful insights for better understanding the IDD in networks with the HeMUC property. Note that since it was assumed that homogeneity holds for nodes of the same degree [177], an enhanced model can be derived to accurately match the IDD curves of HeMUC networks.
, the curve of the SI model transcends. This is in accordance with the fact that the information has higher possibility to be transmitted to supernodes than the nodes with low degrees at early stages. Once the information spreading begins, the number of informed nodes highly increases as supernodes eventually become informed. Then, the spreading rate decreases as information dissemination is now mainly propagated to nodes with lower degrees. Thus, although the SI model is not suitable for describing the IDD in SF networks, it still provides useful insights for better understanding the IDD in networks with the HeMUC property. Note that since it was assumed that homogeneity holds for nodes of the same degree [177], an enhanced model can be derived to accurately match the IDD curves of HeMUC networks.
Regarding SW networks, effects of different rewiring probabilities  are investigated (Fig. 9.8). Ranging from extreme regularity (
are investigated (Fig. 9.8). Ranging from extreme regularity ( ) to extreme randomness (
) to extreme randomness ( ), IDD accelerates due to the enhancement of connectivity and the SW network transforms from HoMPC network (
), IDD accelerates due to the enhancement of connectivity and the SW network transforms from HoMPC network ( ) to HoMUC network (
) to HoMUC network ( ) and finally HoMEC network (
) and finally HoMEC network ( ).
).
Corrected SI model
To overcome the above discussed discrepancies between the SI model and the proposed epidemic IDD model in complex networks, the emerging “degree correlation” problems should be addressed. The traditional SI model implicitly assumes that the degrees of different nodes are uncorrelated, i.e. that the interaction between a source of malware and a susceptible node, or between an infected and a susceptible node, does not exhibit correlations, even though they can be close to each other. This implies that the infection process will be independent and identically distributed in different links, even if those links are neighboring or interfering in reality. However, this is not always the case and caution should be taken to validate the assumption in detail. When a node is informed in a static network, this suggests that at least one of its neighbors has been informed, and hence the mean degree has to be corrected accordingly. Specifically, the average number of susceptible neighbors of an infected node is less than  and thus an effective mean degree
and thus an effective mean degree  metric has been proposed to accommodate this phenomenon. This phenomenon should be carefully modeled otherwise the overestimation problem [236] leads to significant deviation (see also Fig. 9.8). Considering HoMEC network as an example, due to its mean degree characterization, the rate of informed nodes will be given by
metric has been proposed to accommodate this phenomenon. This phenomenon should be carefully modeled otherwise the overestimation problem [236] leads to significant deviation (see also Fig. 9.8). Considering HoMEC network as an example, due to its mean degree characterization, the rate of informed nodes will be given by
![]() (9.18)
(9.18)
where  is a time-varying function accounting for the average number of informed neighbors of an informed node. By setting
is a time-varying function accounting for the average number of informed neighbors of an informed node. By setting  as a constant, a tight upper bound on IDD can be obtained when
as a constant, a tight upper bound on IDD can be obtained when  for HoMEC networks since intuitively, a node that is infected implies that at least one of its neighbors is infected. Thus, the following observation is applicable:
for HoMEC networks since intuitively, a node that is infected implies that at least one of its neighbors is infected. Thus, the following observation is applicable:
By setting appropriate values of  according to the features of different networks, the adjusted SI models successfully capture the corresponding IDD. This implies that upper bounds on IDD of HoMUC and HoMPC networks also exist. Considering IDD in sensor network (HoMPC) as an example, where sensors are uniformly and randomly distributed on a plane with node density
according to the features of different networks, the adjusted SI models successfully capture the corresponding IDD. This implies that upper bounds on IDD of HoMUC and HoMPC networks also exist. Considering IDD in sensor network (HoMPC) as an example, where sensors are uniformly and randomly distributed on a plane with node density  , the communication radius of a sensor
, the communication radius of a sensor  and the radius of the circle containing the informed sensors
and the radius of the circle containing the informed sensors  , obviously,
, obviously,  . This is approximated into the above model by having only the infected nodes that lie on the periphery of an informed circle in communication with the susceptible nodes located at a distance of at most
. This is approximated into the above model by having only the infected nodes that lie on the periphery of an informed circle in communication with the susceptible nodes located at a distance of at most  outside the infection circle, and thus have the potential to inform (infect) them. This is shown later in Fig. 9.10. In other words, the spatial broadcasting of the information is only contributed from the wavefronts of informed circles, while the infected nodes located in the interior of the informed circles are not engaged in further spatial dissemination. By using the general approximation of
outside the infection circle, and thus have the potential to inform (infect) them. This is shown later in Fig. 9.10. In other words, the spatial broadcasting of the information is only contributed from the wavefronts of informed circles, while the infected nodes located in the interior of the informed circles are not engaged in further spatial dissemination. By using the general approximation of  by
by  for small
for small  , since
, since  is negligible compared to
is negligible compared to  , function
, function  can be calculated as
can be calculated as
 (9.19)
(9.19)
where  and
and  is usually negligible compared with
is usually negligible compared with  . Applying
. Applying  to the corrected SI model, leads to obtaining the same result derived in [60]. From this example, the following observation is emerging.
to the corrected SI model, leads to obtaining the same result derived in [60]. From this example, the following observation is emerging.
As the cumulative informed fraction approaches  in a saturated network, Observation 9.2 serves as a more accurate benchmark to any broadcasting mechanisms in wireless complex networks for evaluating the performance of information dissemination. This can be justified by the fact that Observation 9.2 greatly mitigates the biased estimation due to degree correlations.
in a saturated network, Observation 9.2 serves as a more accurate benchmark to any broadcasting mechanisms in wireless complex networks for evaluating the performance of information dissemination. This can be justified by the fact that Observation 9.2 greatly mitigates the biased estimation due to degree correlations.
Dynamic complex networks
This section discusses the dynamic case where network topology changes with time, while maintaining the basic structure and properties. As it will be shown, a time-varying topology provides great chances for information dissemination to the entire network and therefore, it is suitable for describing complicated interactions within large-scale networks supporting mobility capabilities (e.g. routing protocols in MANET). Two nodes originally disconnected, might eventually establish a virtual link between them due to mobility, i.e. a link with short duration imposed by the mobility pattern that will last only while the nodes remain in proximity, thus yielding a virtual giant component. Given the condition that a network is originally nonsaturated (e.g. MANET in sparsely populated area), mobility may make the network virtually saturated, since all nodes can eventually receive the information due to change of connectivity in the dynamic sense.
The mobility of nodes facilitates connectivity in homogeneous mixing networks originally not saturated and thus dynamic HoMEC, HoMPC, and HoMUC networks are virtually saturated. In the following, the focus shifts on IDD in such networks where benefits from mobility can be obtained in a more obvious manner.
Due to the virtual saturation property in Observation 9.3, the SI model that fails to describe the IDD of nonsaturated networks is nevertheless to characterize the IDD of dynamic homogeneous mixing networks. As we define  according to the properties of the networks, the IDD curves can be accurately matched by using Eq. (9.18).
according to the properties of the networks, the IDD curves can be accurately matched by using Eq. (9.18).
To show the significance of these observations and the flexibility of the proposed model, Fig. 9.9 illustrates analytic and simulation plots depicting the epidemic routing via broadcasting in large-scale MANETs. Epidemic routing aiming at exploring the advantages of path diversity with concrete analysis [231] has been regarded as one practical way to achieve routing in dynamic HoMPC [172,215]. In the simulation experiments, we assume that each node has the same transmission range  with uniform random deployment in a
with uniform random deployment in a  plane with wrap-around condition. According to a stationary and ergodic mobility model, such as the truncated Lévy Walk model [185], the step length exponent
plane with wrap-around condition. According to a stationary and ergodic mobility model, such as the truncated Lévy Walk model [185], the step length exponent  and pause time exponent
and pause time exponent  have been set in order to fit the trace-based data of human mobility pattern collected in UCSD and Dartmouth [135]. The successful packet transmission rate to the spreading rate
have been set in order to fit the trace-based data of human mobility pattern collected in UCSD and Dartmouth [135]. The successful packet transmission rate to the spreading rate  has been incorporated. Fig. 9.9 shows that the MANET is nonsaturated (however, virtually saturated), and our model captures the complicated interactions among numerous mobile nodes precisely.
has been incorporated. Fig. 9.9 shows that the MANET is nonsaturated (however, virtually saturated), and our model captures the complicated interactions among numerous mobile nodes precisely.
Hybrid complex networks
When nodes are capable of communicating with each other using multiple heterogeneous connections, a hybrid complex network consisting of multiple complex subnetworks is built via heterogeneous links. As in the example we mentioned in Section 9.2.1, people could exploit mobile smart phones to communicate with individuals in their address books via traditional phone-call and short message, as well as the individuals in their geographic proximity via WiFi [107] or Bluetooth [230]. As shown in Fig. 9.10, the IDD in such complicated networks can be investigated by separately considering IDD in the social network constructed by contacts and IDD via broadcasting and then aggregating the results for the combined cyber-physical system.

FIGURE 9.10 The IDD in wireless complex networks (cyber-physical systems) consisting of both long-range and broadcast dissemination patterns. From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.
According to the proposed categories, ER random network (HoMEC) and sensor network (HoMPC) are used to, respectively, model the delocalized and broadcasting dissemination patterns. Thus, the subpopulation function  , where
, where  and
and  are those that have been disseminated via ER and sensor networks at time
are those that have been disseminated via ER and sensor networks at time  , respectively. The average degree
, respectively. The average degree  describing the social relationships between handsets provides the average number of contacts in the address book. According to Eq. (9.18), the basic differential equation that describes the dynamics of informed subpopulation is
describing the social relationships between handsets provides the average number of contacts in the address book. According to Eq. (9.18), the basic differential equation that describes the dynamics of informed subpopulation is
![]() (9.20)
(9.20)
When an informed node intends to disseminate via broadcasting, it first scans to search the nearby nodes within its transmission range  and connects to a neighbor so as to determine the susceptible neighbors for propagation. In this case, the average number of neighbors
and connects to a neighbor so as to determine the susceptible neighbors for propagation. In this case, the average number of neighbors  equals
equals 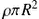 . The behavior of such spontaneous spreading can be regarded as a ripple centered at the infected source node which grows with time. As shown in Fig. 9.10, the spatial spreading of the information here is only contributed from the wavefronts of informed circles, while the infected nodes located in the interior of the informed circles are not engaged in further spatial infections, where similar arguments, as the ones employed before for obtaining (9.19), apply.
. The behavior of such spontaneous spreading can be regarded as a ripple centered at the infected source node which grows with time. As shown in Fig. 9.10, the spatial spreading of the information here is only contributed from the wavefronts of informed circles, while the infected nodes located in the interior of the informed circles are not engaged in further spatial infections, where similar arguments, as the ones employed before for obtaining (9.19), apply.
Without loss of generality, it is assumed that a single informed circle is generated at time  by a point source infected through and kept stretching for
by a point source infected through and kept stretching for 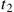 time units. Then, its incremental modified spatial infection at time
time units. Then, its incremental modified spatial infection at time  is
is
 (9.21)
(9.21)
where  accounts for the fact that for an infected node on a periphery, roughly half of neighbors outside the infection circle are susceptible, and
accounts for the fact that for an infected node on a periphery, roughly half of neighbors outside the infection circle are susceptible, and  is the spatial infection within the same time interval prior to the rectification. The incremental spatial infection at time
is the spatial infection within the same time interval prior to the rectification. The incremental spatial infection at time  of all infection circles is given by
of all infection circles is given by
 (9.22)
(9.22)
This means that there are  point sources originated at time
point sources originated at time  and each contributes
and each contributes  incremental spatial infection at time
incremental spatial infection at time  .
.
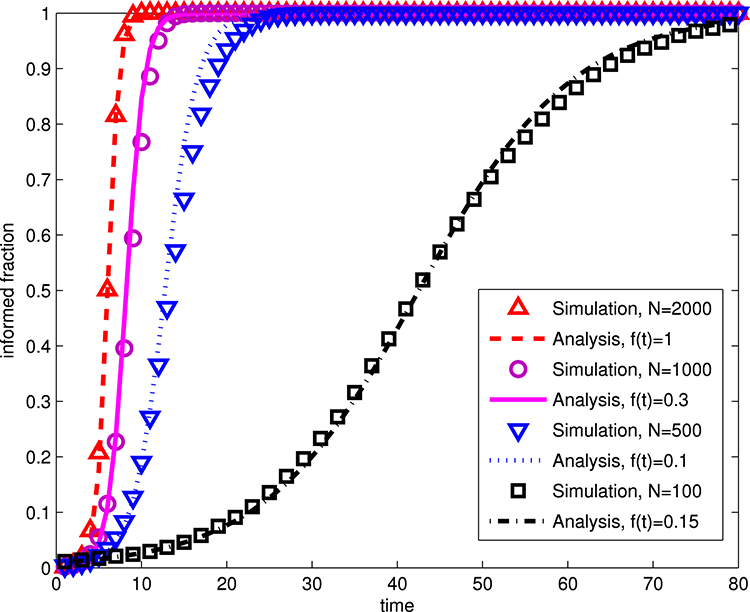
To validate the analytical model, experiments to simulate IDD in a hybrid network among  individuals uniformly deployed in a
individuals uniformly deployed in a  plane were developed. The constructions of social contact networks and setup of parameters (e.g.
plane were developed. The constructions of social contact networks and setup of parameters (e.g.  ) follow the data set in [221]. Fig. 9.11 illustrates analytic and simulation plots depicting the IDD via both delocalized communication and broadcasting in hybrid (HoMEC and HoMPC) complex networks. It can be observed that the curves of propagation dynamics closely match the analytical model, where limited discrepancy exists, mainly due to the fact that information may propagate to individuals who have already been informed and uncertain boundary conditions could not be considered in the analysis. Comparing with the traditional SI in Fig. 9.8, the corrected SI could capture the IDD of ER network (HoMEC) more precisely.
) follow the data set in [221]. Fig. 9.11 illustrates analytic and simulation plots depicting the IDD via both delocalized communication and broadcasting in hybrid (HoMEC and HoMPC) complex networks. It can be observed that the curves of propagation dynamics closely match the analytical model, where limited discrepancy exists, mainly due to the fact that information may propagate to individuals who have already been informed and uncertain boundary conditions could not be considered in the analysis. Comparing with the traditional SI in Fig. 9.8, the corrected SI could capture the IDD of ER network (HoMEC) more precisely.

FIGURE 9.11 IDD in hybrid (HoMEC and HoMPC) complex networks of propagating information in both delocalized and broadcast fashions, where  ,
,  , and
, and  . From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.
. From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.
 ,
,  , and
, and  . From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352.
. From Cheng S-M, Karyotis V, Chen P-Y, Chen K-C, Papavassiliou S. Diffusion models for information dissemination dynamics in wireless complex communication networks. J Complex Syst 2013;2013: 972352...................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.