
Figure 1.1 Land-vehicular fog computing examples.
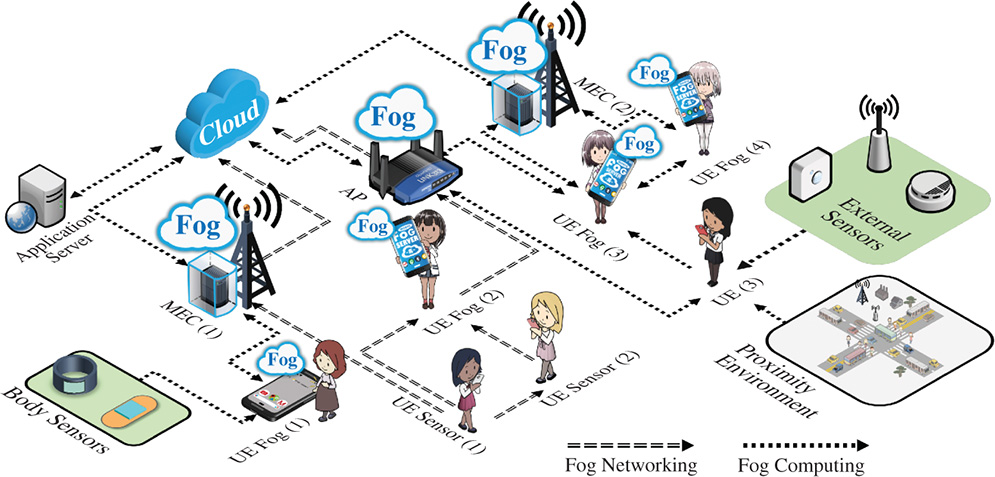
Figure 1.4 UE fog computing examples.

Figure 2.2 An overview of edge computing architecture [16].

Figure 2.4 Fog computing architecture [10].

Figure 5.1 Fog computing enabled smart cities.
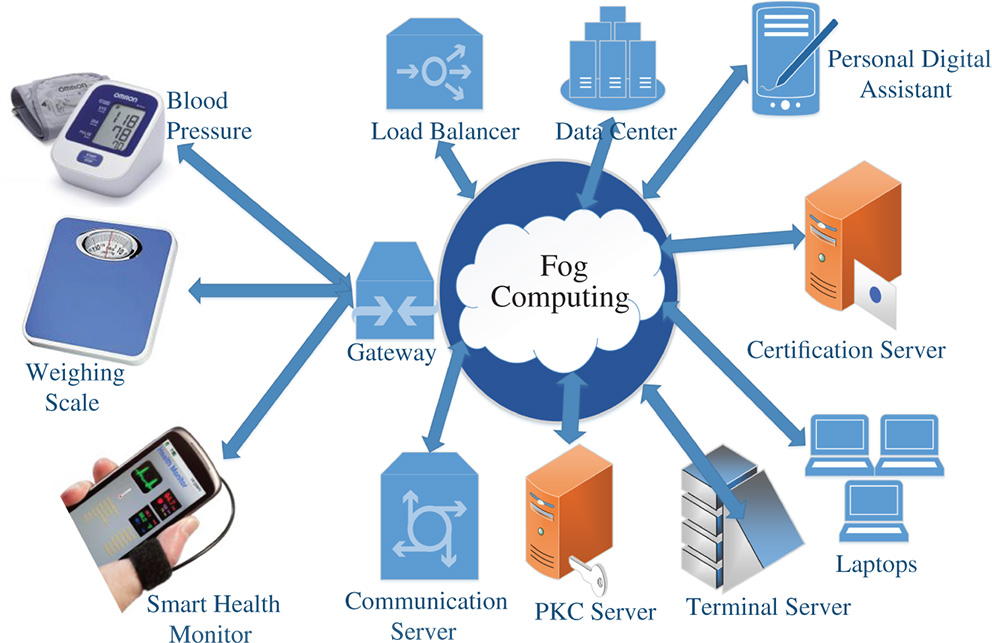
Figure 5.2 A generic fog enabled IoT environment.
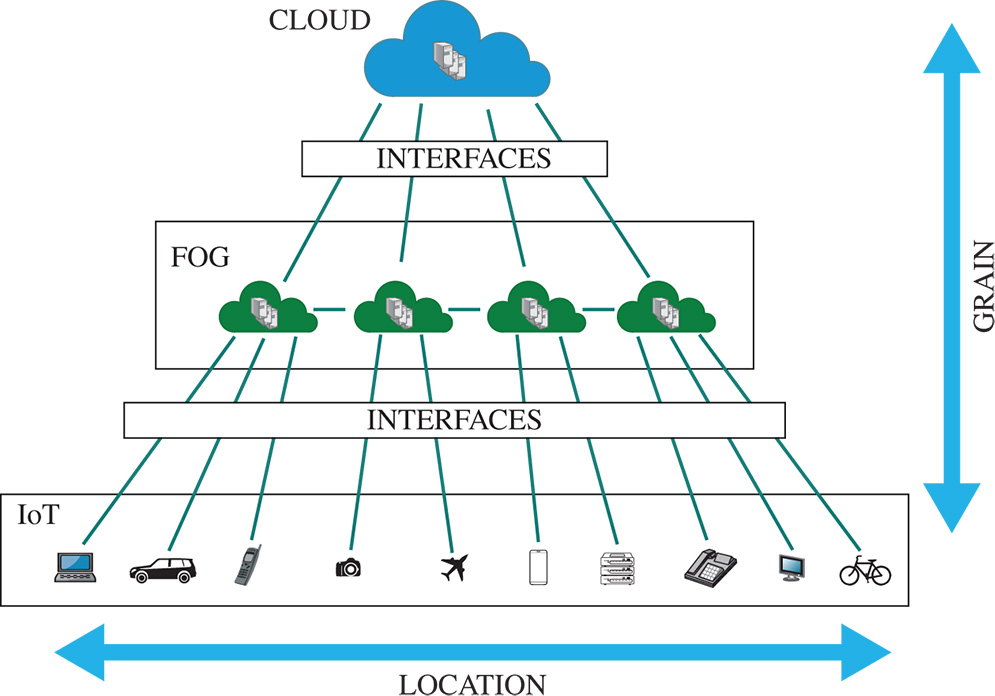
Figure 6.1 Cloud-fog-IoT architecture.
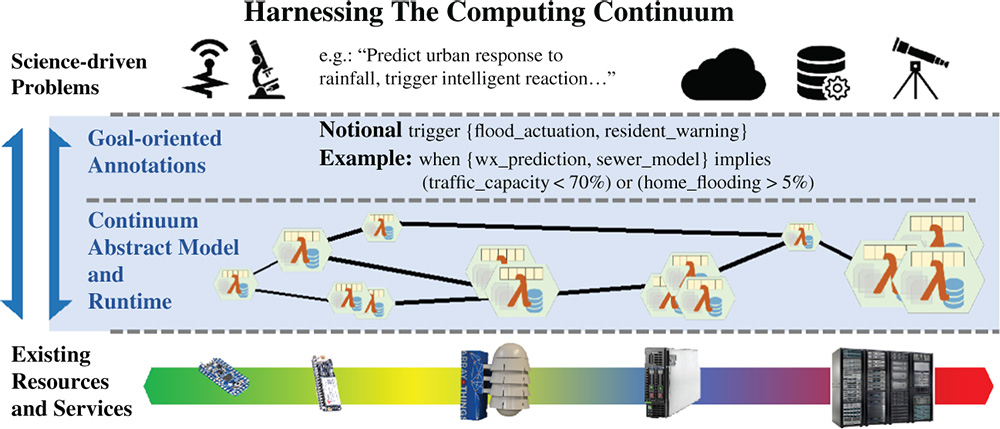
Figure 7.2 Continuum Computing Research Areas: A pictorial depiction of the computer science areas that require research to successfully program the computing continuum. To address problems, such as the sciences examples given in Table 1.4, using existing resources and services, we need an abstract programming model with goal-oriented annotations, along with a run-time system and an execution model.

Figure 11.3 FogNetSim++: Graphical user interface, showing static, mobile, and fog computing nodes.

Figure 11.4 FogNetSim++: showingthe handover features managed through single broker node.
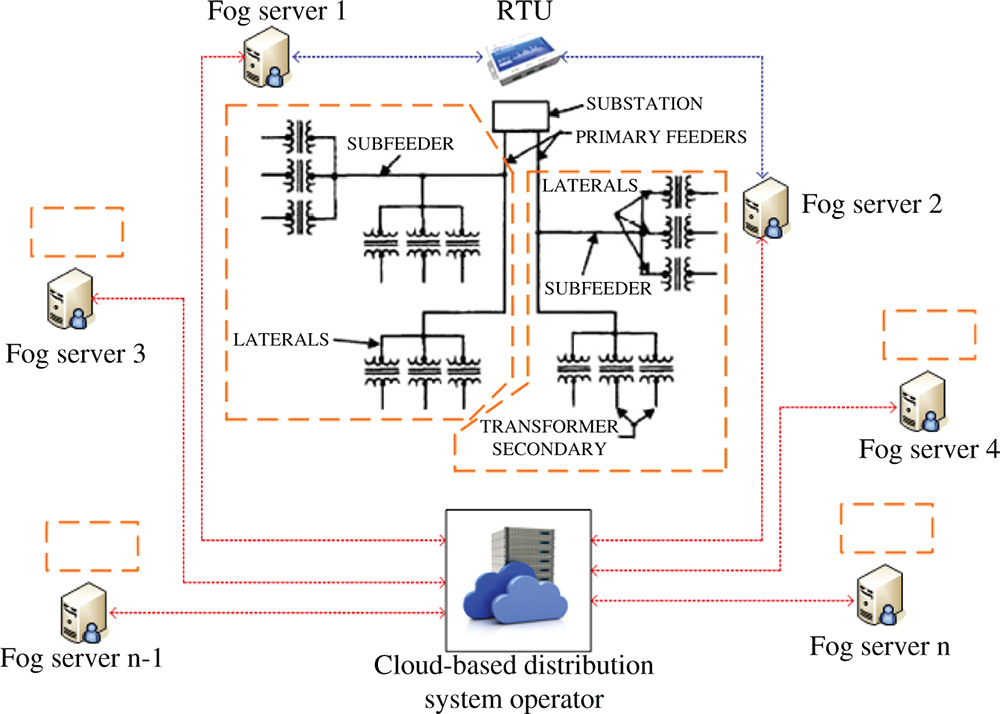
Figure 13.3 Feeder-based communication scheme for DMS using fog/cloud computing.
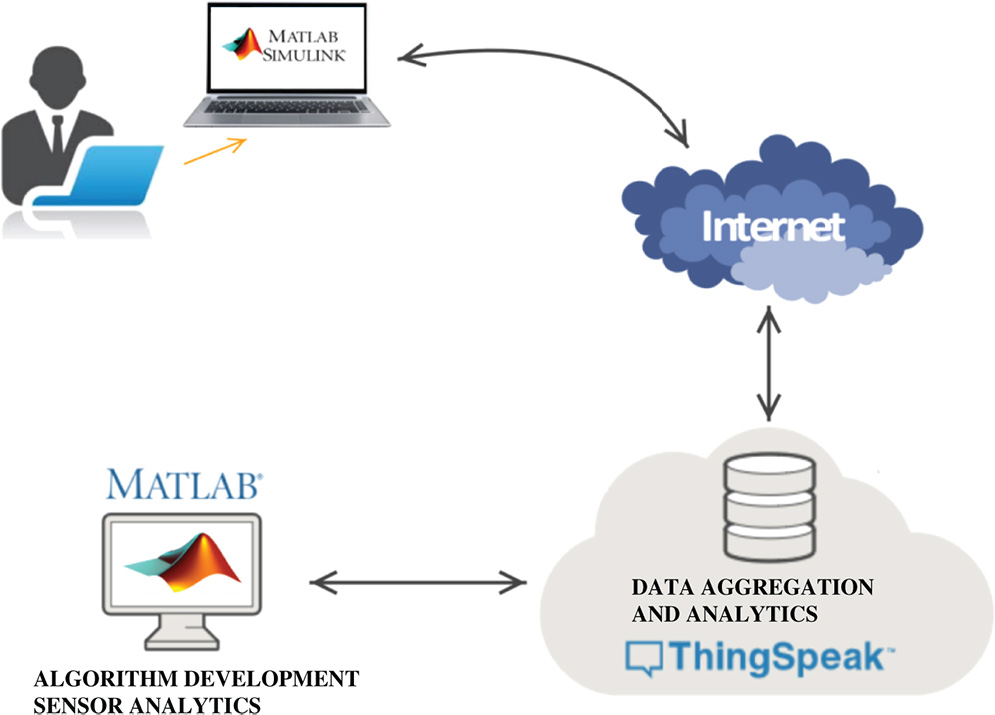
Figure 13.4 Simplified communication scheme connecting MATLAB/Simulink and ThingSpeak IoT platform used for DMS simulation.

Figure 15.3 Three smart phones are placed on three different locations of each participant's body (chest, right hand, and left jacket pocket) to collect accelerometer signals while walking on the treadmill.

Figure 16.1 Architecture of software-defined network (SDN).

Figure 17.1 Fog computing for vehicular applications.
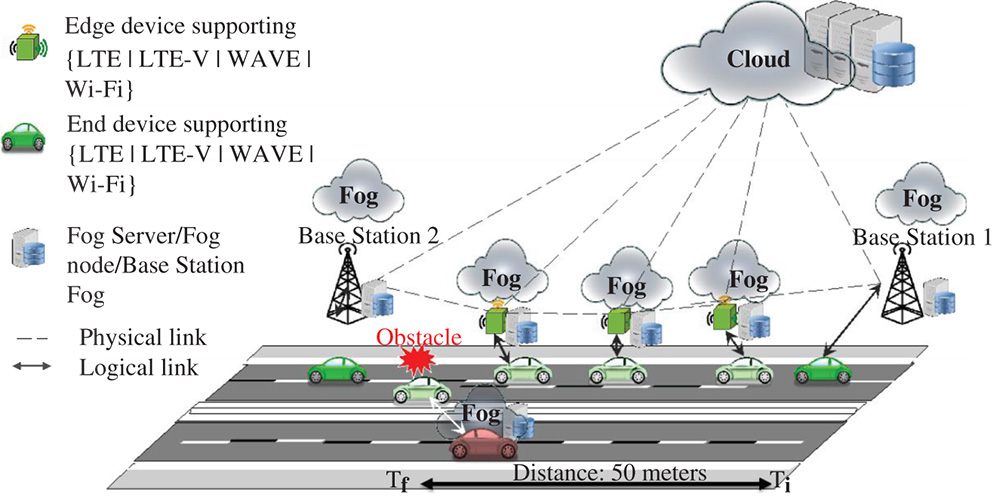
Figure 17.2 Obstacle detection as an example of delay-critical application scenarios.
