20
An Insight into 5G Networks with Fog Computing
Osman Khalid1, Imran Ali Khan1, Rao Naveed Bin Rais2, and Asad Waqar Malik3
1Department of Computer Science, COMSATS University Islamabad, Abbottabad, Campus, Pakistan
2College of Engineering and Information Technology, Ajman University, Ajman, UAE
3Department of Computing, School of Electrical Engineering and Computer Science, National University of Sciences and Technology, Islamabad, 44000, Pakistan
20.1 Introduction
4G has seen significant progress over the past few years, and with passage of time it has spread worldwide. A question remains about the future of wireless technologies. Current wireless technology generations have adopted a huge model shift, as shown in Figure 20.1. In the past few years, cellular communication experienced a tremendous increase in data traffic. Due to the popularity of smart devices, multimedia contents, video streaming, and voice services, higher data transmission rates are required [1]. Current 3G and 4G can handle continuously increasing mobile data traffic for next few years but will not be able to handle large data and rapidly growing devices [2]. Big data is getting bigger with the advancement of new and quick methods for gathering, storing, and processing data [3]. Higher capacity, low latency, improved transfer rate of data, and enhanced quality of service (QoS) are primary challenges that need to be handled. Continuously growing demand for 3D (“Device,” “Data creation,” and “Data transfer”) services has motivated manufacturers to develop a new wireless generation called 5G [4, 5]. Currently, 4G is not fulfilling all the above-mentioned requirements of cellular network, and, consequently, a new generation is being developed.
5G is the emerging standard beyond 4G and it will fulfill the current demands of wireless cellular communication [6–8]. Table 20.1 presents a comparison of 5G with existing technologies [9, 10]. What are the appropriate technologies that will define 5G? Will it just be the extension of 4G or it will be entirely a new technology? These are some of the questions that are the topic of hot debate among researchers. The following aspects are discussed encompassing 5G [8]:

Figure 20.1 Evolution of wireless technologies.
Table 20.1 Comparison of wireless technologies.
| Generations | 1G | 2G | 3G | 4G | 5G |
| Deployment | 1980s | 1990s | 1998–1990s | 2008–2009s | 2020 |
| Bandwidth | 2 kbps | 14.4 kbps | 2 Mbps | 200 Mbps–1 Gbps | 1 Gbps and higher |
| Web Standard | — | www | www (IPv4) | www (IPv4) | wwww (IPv6) |
| Switching | Circuit | Circuit | Packet | Packet | Packet |
| Limitations | Less security | Less security | Less support for Internet | Unable to support max. devices | — |
| Services | Mobile telephony | Digital voice/short SMS etc. | High quality audio/video | Dynamic access information, wearable devices | Dynamic access, wearable device with AI abilities |
- Device-centric architecture review, e.g. uplink/downlink and controlling all the channels to make routing information among nodes
- Massive multiple-input multiple-output (MIMO) requires some modifications such as design of macro-station
- IEEE 802.11 has set a standard for mmWave (millimeter wave) because of bandwidth limitations in backhaul in small cell
- Machine-to-machine (M2M) communication must have very low latency
- Heterogeneous Network (HetNet) design and support
- 5G must provide a seamless user experience [1]
In general, 5G copes with issues/challenges that include network deployments, capacity, data rate, minimization of end-to-end latency, devices' connectivity, capital reduction, operational cost, QoS, smart antenna system, wider area coverage, free movement from one technology to another, choice among various wireless systems, and data encryption [11, 12]. It is believed that 5G will fulfill all the growing demands of data-centric applications due to its physical layer security design and mmWave spectrum, and because of the use of multiple antennas. It will fulfill the demand of exceeding data rate, wide-area radio coverage, excessive amount of nodes, and less latency [2]. Another main challenge that 5G needs to address is data caching [13, 14].
The rest of the chapter is organized as follows. Section 20.2 discusses the vision of 5G. Section 20.3 discusses fog computing with 5G. Section 20.4 presents 5G network architecture. Section 20.5 illustrates the growing technologies based on 5G. Section 20.6 presents the 5G applications, and Section 20.7 discusses challenges of 5G. Finally, Section 20.8 concludes the chapter.
20.2 Vision of 5G
4G technology is practically implemented in few countries, but full-scale deployment is yet to be seen. 5G is conceptualized as a real network, and it must support all the existing applications supported by previous technologies. Now 5G technology is in its evolution and it will provide an affordable wireless connectivity on a very high speed [15]. According to Siddiqui et al. 5G has two aspects: revolutionary and evolutionary [9]. The revolutionary view states that 5G technology is able to connect the whole world by reducing the limits to wireless communication. Application can be robots with artificial intelligence. In addition, according to the evolutionary view, the 5G systems will be able to support WWWW, and will allow a flexible network, for instance, dynamic ad hoc wireless network (DAWN). Requirements change from app to app, which will have to fulfill certain configurations. For example, driverless cars or public security apps require solutions to the main issues of delay and reliability. Alternatively, high data rate apps, such as streaming high-quality videos, may exhibit delay and reliability.
20.3 Fog Computing with 5G Networks
20.3.1 Fog Computing
Fog computing is an emerging technology that extends the cloud capabilities, such as computation, storage, and networking services from the remote data center to closer to the end-user [16–18]. By locally processing the requests, data traffic is reduced on the core network, thereby reducing the processing time, latency, and network cost. The fog computing architecture is implemented on multiple layers of a network's technology [19, 20]. By adding layers of fog nodes, applications can be partitioned to run at the optimal network level [21, 22]. Fog computing specifically aims the time-critical applications, e.g. real-time gaming, virtual reality, emergency response system, vehicular networks, real-time health care, Internet of Things (IoT), and so on, to name a few [23, 24].
20.3.2 The Need of Fog Computing in 5G Networks
The future 5G networks aim for ultra-low latency and high bandwidth. 5G communication will be driven by high-frequency millimeter waves, and a 5G cellular network will connect mobile users to the base station (BS) connected to the core network. The low latency radio interfaces in the 5G network aim to reduce the delays between a user and a base station. However, the forwarding of user application requests from core network to the cloud would significantly increase latency. Consequently, 5G networks require moving processing power closer to the end-user, which can be accomplished with fog computing. Fog computing can be enabled in 5G by leveraging both the small and macro-based stations to achieve the ultra-low latency demanded in 5G networks. A fog computing–based radio access network (F-RAN) could provide 5G with reduced latency and high energy efficiency.
20.4 Architecture of 5G
20.4.1 Cellular Architecture
In 5G, each device (cell phone) has a constant “home IP address,” in additional to a “care-of” address. Care-of address represents actual current location whereas IP identifies network interface and location addressing. Before communicating with a mobile, a computer passes a message packet to its IP address. Then, it is moved to the care-of address by directory server through a tunnel. The directory tunnel replies back to the computer and informs it about the correct address, and then further communication starts. As compared to IPV4 addressing, a connectionless protocol is being used in the switched layer. A total of 128 bits are used, which are subdivided into four categories, dedicated for different functions. The first 32 bits are used for the “home” IP address, and the other 32 are specifically used for the “care-of” address. The second part is for communication among cell phones and other devices (e.g. computer). The third part is used for tunneling to establish interconnection among wired and wireless networks. In the third part, the directory server uses the IP address of the mobile phone to create a communication channel. The last 32 bits of IPv6 address may be used for local addressing, e.g. for VPN (virtual private networks) sharing [25]. Figure 20.2 shows a general 5G cellular network architecture [10].
5G phone is designed to be an open source and includes every layer from physical layer to the end-user layer (application layer). Open wireless architecture, which was proposed for 4G mobiles phone, is adapted in this conceptual phone, and some changes in network layer and other layers up to application layer are made. The proposed concept divides the network layer into further two sublayers: upper and lower network layers. The lower layer is for each interface and the upper layer is for mobile terminal. The middleware between the upper and lower layer translates the IP addresses [26]. The protocol stack for the proposed 5G mobile phone concept is illustrated in Table 20.2. To allow the maximum optimized usage of specific wireless implementations of transport protocols, the open transport layer is proposed in this concept. The proposed concept will open a way to select many wireless technologies on different QoS and price constraints for different services, e.g. voice over Internet protocol (VoIP), streaming Internet protocol television (IPTV), web, messaging, and gaming. To fulfill this, 5G mobiles will create a database that will gather and provide information for all the services and technologies in the cellular device. Development modes will provide the best QoS and cost-to-use available wireless technologies within a 5G phone. Figure 20.3 explains the model, proposing a 5G architecture that is all-IP based and mobile network interoperability composed of nodes and independent radio access technologies (RATs). It is anticipated that 5G will change the concept of station-based-centric architecture of mobile networks, and methods of uplink/downlink control and data channels, to make routing and the flow of information in a better way. Currently, mobile systems are not letting devices communicate with each other directly. Every communication works through a base station. Tehrani et al. proposed a two-tier cellular network that allows a base-to-device communication, and device-to-device communication, as well [27]. In a two-tier mobile system, as users' data is passed by other users' cell phones, safety and security are the biggest concerns. To ensure breaches do not occur, the systems must be designed with smart interface strategies and managed allocation of resources. The traditional macro-cell tier includes a base station for device communication. In 5G-based device-to-device (D2D) communication, the device is directly connected to another device without a base station and transmission is directly among the two nodes with the assistance of other nodes. Base stations are still there, but devices will be allowed to create an ad-hoc mesh network. Another important thing is pricing and charge of D2D services. Pricing models are needed to be designed to let devices to participate in D2D communication [11].

Figure 20.2 5G cellular architecture.
Table 20.2 5G protocol stack.
| Application layer | Application (services) | |
| Session layer | Open transport protocol (OTP) | |
| Network layer | Upper network layer | Lower network layer |
| Data link layer | Open wireless architecture (OWB) |
20.4.2 Energy Efficiency
The main goal of 5G is to reduce energy. Therefore, energy efficient infrastructures play a vital role in 5G networks. Rowell et al. consider a usage of combined spectral efficiency and optimization of energy [28]. In a user-centric approach, a user's equipment is able to select uplink and downlink channels from various BS, depending upon amount of load, condition of channel, applications, and services requirements. Direct association cannot be performed entirely with user's equipment (UEs); it must consider both the channels at the time when they make an association with base stations (BSs). In this way, demodulation of signals and data is beneficial to save energy. An example of this scenario is a mobile base station (MBS), which may initiate signaling of a BS, and a server base station (SBS) to serve all data requests. If there is no data request for that time duration, we can hibernate the SBS. Zhang et al. proposed the same technique for decoupling of data in those UEs that are connected to SBS, according to the functionality provided by MBS, and output the result, which ensures less energy consumption and a lower chances of interference [29]. Hu et al. proposed C-RAN architecture for energy efficiency in a manner that UEs and Remote Radio Head (RHHs) serve almost the same number of times [30]. They also proposed an approach to interface management to decrease power consumption of SBSs and MBSs.
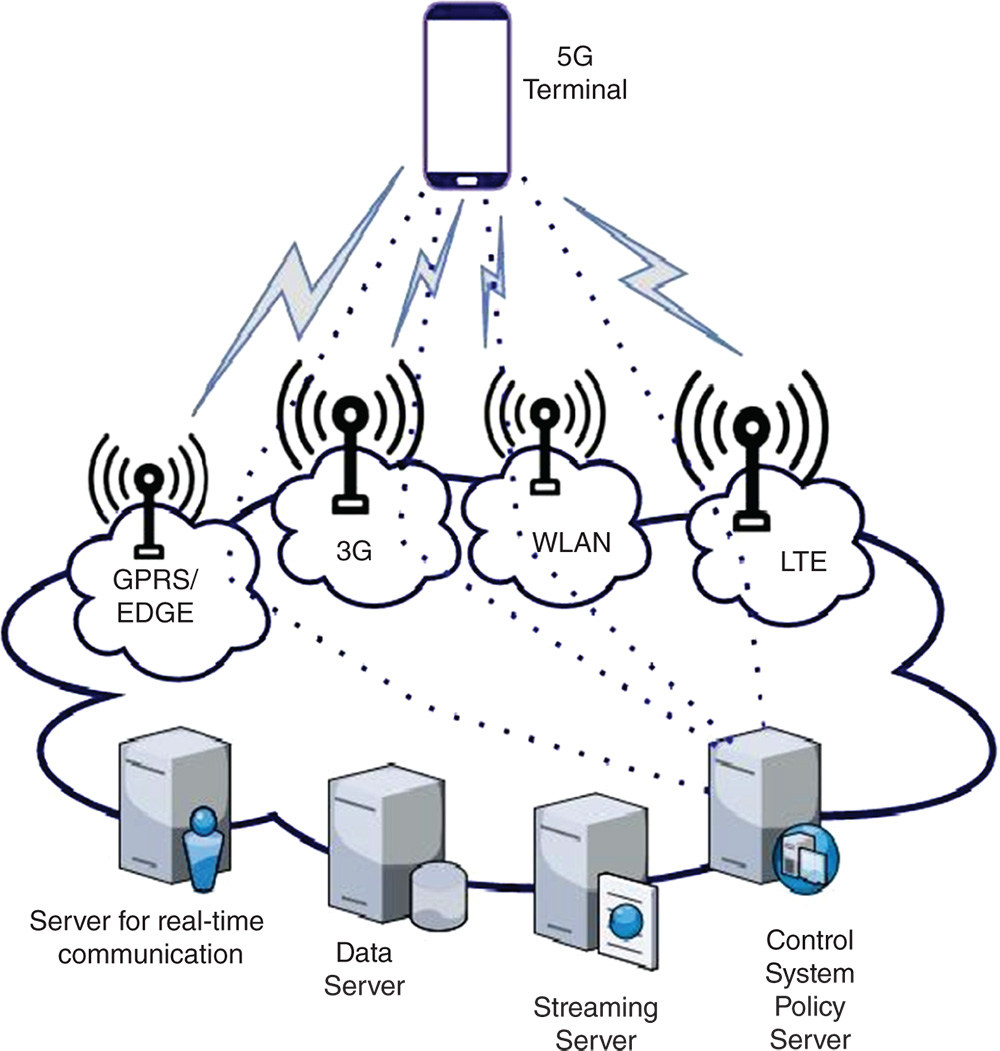
Figure 20.3 5G IP-based architecture.
20.4.3 Two-Tier Architecture
Another proposed architecture for 5G is two-tier architecture. In two-tier architecture, MBS works at a higher tier and SBSs work under MBS, known as the lower tier. Higher and lower tiers share the same frequency band. There exists a macro cell, which covers all the small cells. These small cells include micro, pico, and femto cells. Small cells enhance the services and coverage area of macro cells. Two-tier architecture is enhanced to multitier architecture by using D2D and cognitive radio network (CRN)–based communication.
To separate the indoor and outdoor users is a big challenge. Wang et al. proposed a solution to this challenge by enhancing the MBS's responsibilities [14]. They deployed a huge array of antennas, having some of its elements distributed across macro cells, and they are connected by fiber optics to MBS. For communicating with MBS, a large array of antennas and SBS are deployed in buildings. SBS or Wi-Fi connects UEs with all other UEs in a building.
Wang et al. also proposed that a mobile (small-cell) placed inside a bus wants to communicate with internal UEs and an antenna that is located outside of the bus with MBS [14]. Thus, inside the bus, all UEs appear as a signal group or a single unit with corresponding MBS. SBS appear there as an MBS for all UEs inside the bus.
There are two basic issues while deploying two-tier architecture in small cells. Interference management and Backhaul data transfer. The interference may include inter-tier and intra-tier interference. The inter-tier interference will be as a result from MBS to SBS and from MBS to SBS's UEs. In intra-tier interference, resultant interference will be from SBS's to other SBS's UEs. In backhaul data transfer, an opaque placement of small cells in a network requires large data transfer rate and cost-efficient architecture. There are different models proposed by Nisha et al. for backhaul data transfer. They are wireless point-to-mMultipoint (PTMP), wired optical fiber (WPF), and wireless point-to-point (PTP). WPF backhaul data transfer is modeled through establishing the web objects framework (WOF) link from every BSS to MBS. It is an expensive and time-consuming process. PTMP deploys a wireless PTMP-base station on MBS. MBS then communicates with SBS and transfers backhauled data to the core network. In PTP, antennas are deployed in line-of-sight and have been proved to supply data at a high rate and capacity at low cost.
20.4.4 Cognitive Radio
A CRN is based on a two-tier architecture. It considers either MBS or SBS to implement cognitive radio properties at different mediums. Xuemin et al. [31] mention types of CRN-based architecture as (1) cooperative CRNs and (2) noncooperative CRNs. Cooperative CRNs use only cognitive and licensed bands/channels due to QoS. A licensed channel is used to serve UEs by a SBS, and the opportunistic access to the licensed channel is used to transfer backhauled data to the MBS. A noncooperative approach establishes a multi-RAT system, including radio interface and operates at temporary and licensed channels by programmable unit (PU), known as cognitive channel (CC). The source unit (SU) runs only on CC to form a CRN. It overlaps on an existing cellular wireless network. As there is connection between two networks, they can be integrated in the upper layer and must separate in the physical layer. The end-users use a cognitive and licensed channel to connect with a nearer MBS, and the communication between SBS and MBS occurs through a licensed channel.
In 5G, SBS works as an SU to monitor all activities and work on temporarily used frequency bands of small cells [31]. This band is called spectrum hole [32]. The PU provides services by micro cell to their UEs while having a minimum disturbance to macro cell functions. For the small cells, a dynamic pricing model based on theoretical framework is suggested in [28]. Due to this model, high data rates are achieved by UEs as compared to macro-cell and UEs pricing model is different as compared to macro-cell. Multitier architecture consists of different type of small cells, broadcasting, and serving D2D communication to serve users with QoS that are required for spectrum efficiency and energy efficient manners [33].
20.4.5 Cloud-Based Architecture
McKeown et al. defines cloud computing as an infrastructure providing simple, on demand, scalable, and less costly access to configurable resources that are at shared pool without worrying about resource management [34]. Mobile cellular communication and cloud's integration can provide tremendous beneficial growth to communication system. Here we briefly discuss cloud-based radio odes (C-RANs) for 5G as mentioned by [35]. Beyond C-RAN, the aim is to execute MBS functions in cloud hence; MBS's functionality is divided into two layers: control layer and data layer. Data layer contains heterogeneous physical resource and perform signal-processing task. Control layer performs resource management and baseband processing. C-RAN provides dynamic service without costly charges to network devices. Two basic components of MBS are baseband unit (BBU) and RRH. BBU implements baseband processing by utilizing baseband processor. Whereas, RRH is used for performing radio functionalities. C-RAN provides scalable and flexible architecture due to most of the BBUs placed in clouds, and RRHs are in MBSs.
Checko et al. proposed two-layered C-RAN architecture, in which two C-RAN are used based on MBSs [35]. The MBSs functionalities are divided into two groups: full centralized C-RAN and partially centralized C-RAN. In full-centralized C-RAN, BBU, and all high-level core functionalities of MBS are placed at the cloud level. While RHH and some other core functionalities are located in MBS, the high-level functionalities are still in the cloud, as mentioned in Figure 20.4.
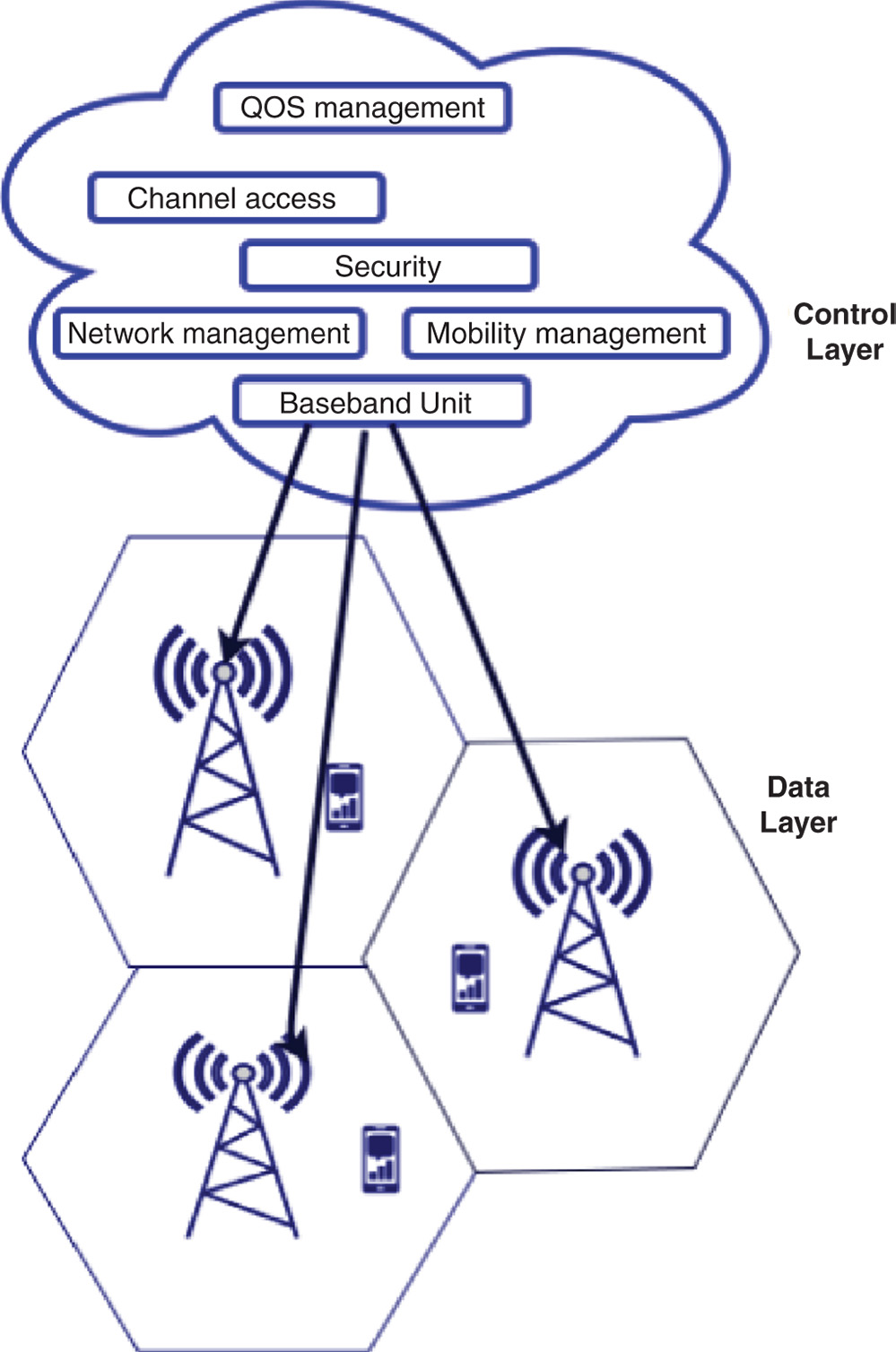
Figure 20.4 Cloud-based architecture.
20.5 Technology and Methodology for 5G
Integration of current and previous Wi-Fi and other cellular standards allows 5G to provide an extraordinarily high data rate with decreased delays for end-users. 5G enhances technologies like MIMO, mmWave reference, and ultra-densification. Despite all these benefits, an official standard of 5G is still needed, and the absence of such a standard means that 5G has endless possibilities. 5G is expected to fulfill and fix all the flaws of 4G, and will be divided into several sublayers for an all-in-one IP connectivity. 5G technology will enable us to create such systems, to address safety and security problems, and to improve the capacity of the systems. 5G literature framework is providing researchers with directions to address: security, technology, network implementation, and application problems for innovative development [36].
20.5.1 HetNet
Humans use services such as social networking, VoIP, video conferencing, video streaming, and multiplayer gaming. Such forms of data communication are called human-type communication (HTC). When machines communicate with each other without human interference, then this form of data communication is called machine-type communication (MTC). When humans and machines communicate with each other, then this form of communication is termed as combined-type communication (CTC). CTC and MTC are important for IoT and cyber physical systems (CPS). 5G networks are presented in different use cases to establish the aforementioned communication mechanisms. The use cases are categorized in three ways: HTC, MTC, and CTC.
HTC Use Case
- Inelastic. This use case is to satisfy user's demand for high-definition multimedia content at anytime, anywhere with a range of mobility and communication standards.
- Elastic. This handles the large number of users and availability of Internet anytime, anywhere with the mobility communication standard.
MTC Use Case
- Inelastic:
- Intelligent roads: A set of sensor and video cameras are arranged along a network of roads.
- Inter-vehicular communication. Autonomous driving, intelligent intersections, and traffic management need inter-vehicular communications.
- Industrial process automation. Sensors monitor automated industrial processes, and report their readings to a controller.
- Theft control. Sensor-based systems can be used to detect product theft in supply chain and/or in stores.
- Elastic:
- Home automation. Different devices inside a home collaborate to accomplish a task.
- Intelligent parking. Sensors attached to parking spaces can communicate with online servers to provide information about available parking spaces in a particular area.
CTC Use Case
- Inelastic. Critical control of remote devices and remote network management.
- Elastic. Controlling and monitoring different home appliances from within a house or over the Internet.
5G research community still face issues, such as a scalable network architecture, QoS framework, intelligent network selection, and inter-network handover algorithms to satisfy diverse HTC, MTC, and CTC requirements. 5G supports a large amount of data initiated by HTC, MTC, and CTC [37].
20.5.2 Beam Division Multiple Access (BDMA)
5G technology uses CDMA and beam division multiple access (BDMA). BDMA allows data rate up to 100 Mbps with high mobility and at low mobility it is up to 1 Gbps. It uses an orthogonal beam, which is allocated to each mobile station. To increase the capacity of the system, an antenna beam is used that divides the band allocated to the base station. Mobile stations and the base stations are in the line of sight; both transmit the beam for the proper communication and reducing interference [38]. BDMA is shown in Figure 20.5.
20.5.3 Mixed Bandwidth Data Path
The architecture of 5G combines pico cell, micro cell, and macro cell, and can utilize bandwidth based on WLAN and CDMA2000. The WLAN network covers a small area, whereas CDMA2000 covers a large area. Moreover, in 5G, data requests can be sent from one network (MN, BS, PDSN, CN) and replies can arrive from the other network (CN, PDSN, AP, MN). The bandwidth selection is made with the exchange of messages between the networks, as depicted in Figure 20.6 [39].
20.5.4 Wireless Virtualization
5G supports network virtualization. Virtualizing mobile networks and sharing of their resources will provide more efficient utilization of wireless networks. Network virtualization can reduce the amount of base station equipment, as well as reduce energy consumption [40].
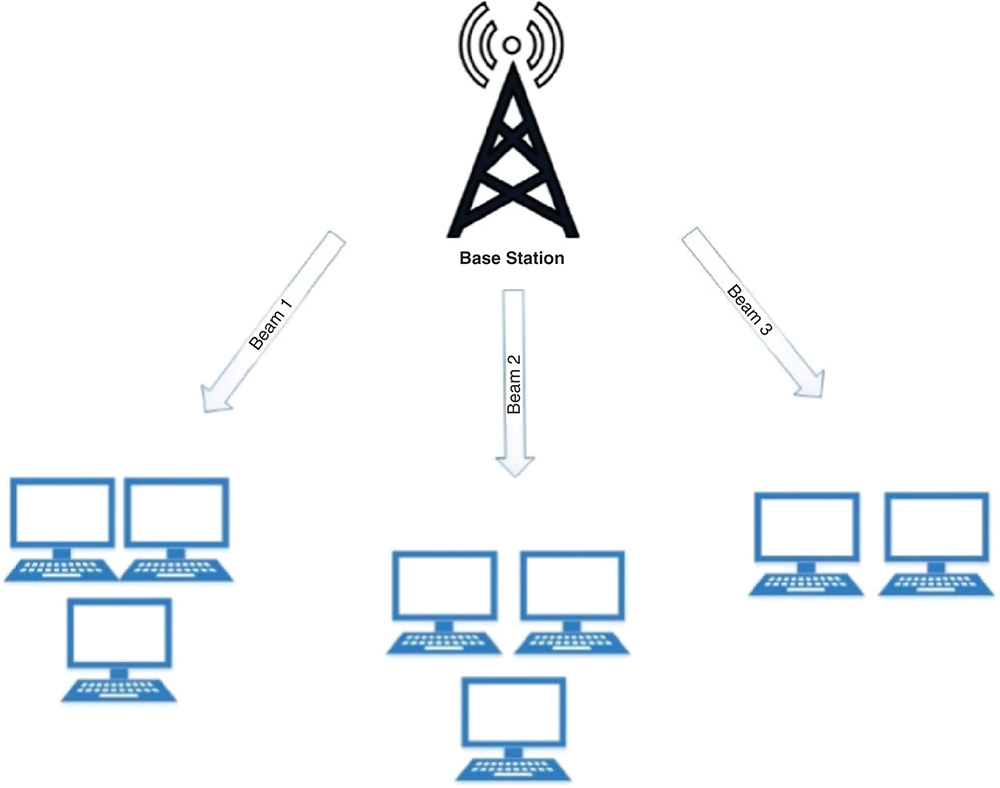
Figure 20.5 Beam division multiple access (BDMA).
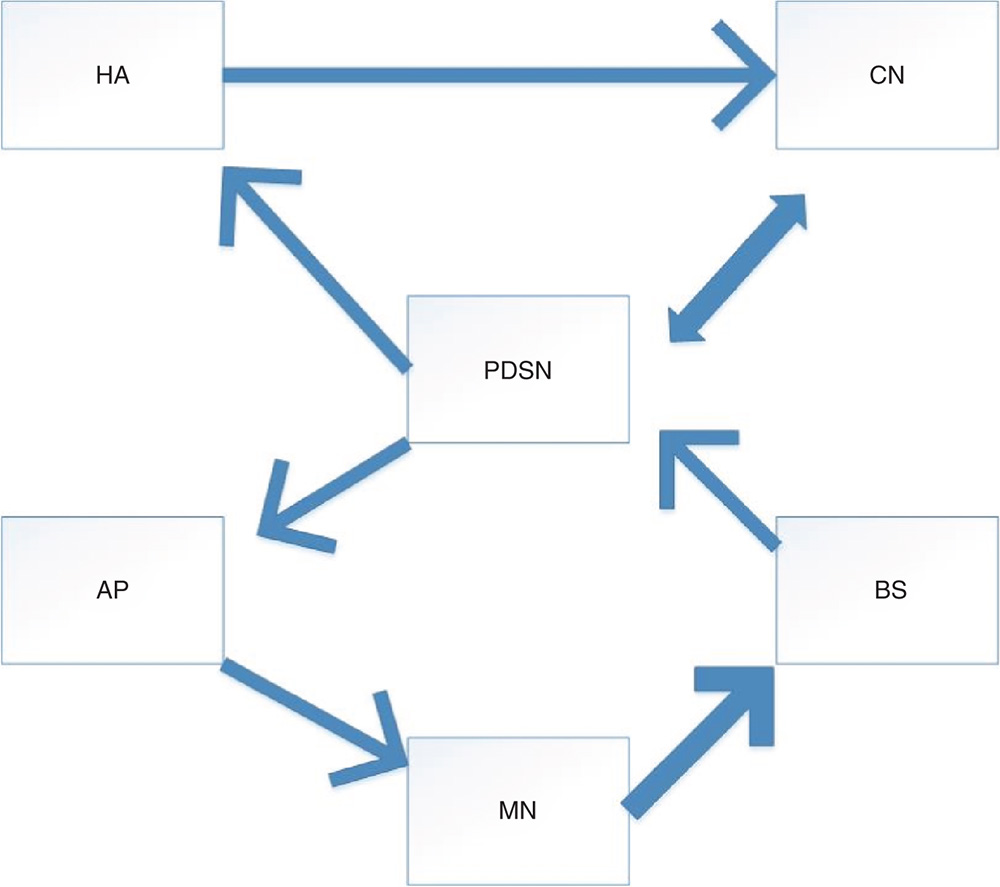
Figure 20.6 Mixed bandwidth data path.
20.5.5 Flexible Duplex
5G allows very flexible and dynamic test-driven design (TDD) transmission resource. Existing TDD-based mobile technologies include TDD-LTE for restriction on uplink/downlink configuration. The TDD requires interference like direct base-station-to-base-station and device-to-device that is similar to base-station-to-device and device-to-base-station [41].
20.5.6 Multiple-Input Multiple-Output (MIMO)
Multiple-input multiple-output (MIMO): Multiple antennas are used to multiplex messages for multiple nodes, keeping the energy radiations toward the specific directions, which decreases the mobile interference. 5G systems do not encourage the idea of keeping complete control at the infrastructure side and take advantage of intelligence at the device side among the different layers of the stack protocol. The 5G idea requires an enhancement at the device level (component change); it also has implications at the architectural level. As wireless technology is emerging and data traffic is rapidly growing, the demand for swift and reliable base stations has increased. A new term, massive MIMO, describes a system that is emerging to fulfill this need. There are many benefits of this technique that are being realized by using large antenna arrays at the transmitters of receivers [2]. Massive MIMO and advanced code technology is a new concept in wireless paradigm for multi-users with multi-antenna systems [42]. It is able to provide better improvement in radiated energy efficiency and bandwidth. Advanced code refers to polar code, which are the first-ever codes that achieved the capacity of symmetric binary-input discrete memory-less channels (B-DMCs). They are regarded as the most promising code candidates for 5G, due to having advantages in performance, complexity, and flexibility. A MIMO has a number of receivers and transmitters and channels by which they communicate. Massive MIMO with deployment of multiple antennas is represented in Figure 20.7.
20.5.7 M2M
In 5G, M2M includes three basic requirements: Support for a large number of devices with low rate of transfer, sustenance of low data rate in non-real-time situations, and lesser delay in data transfer rate. Different research directions are discussed, which can lead toward basic changes in mobile networks design. Technologies like mmWave, MIMO, device-centric architectures can lead to form the basic pillars of 5G.
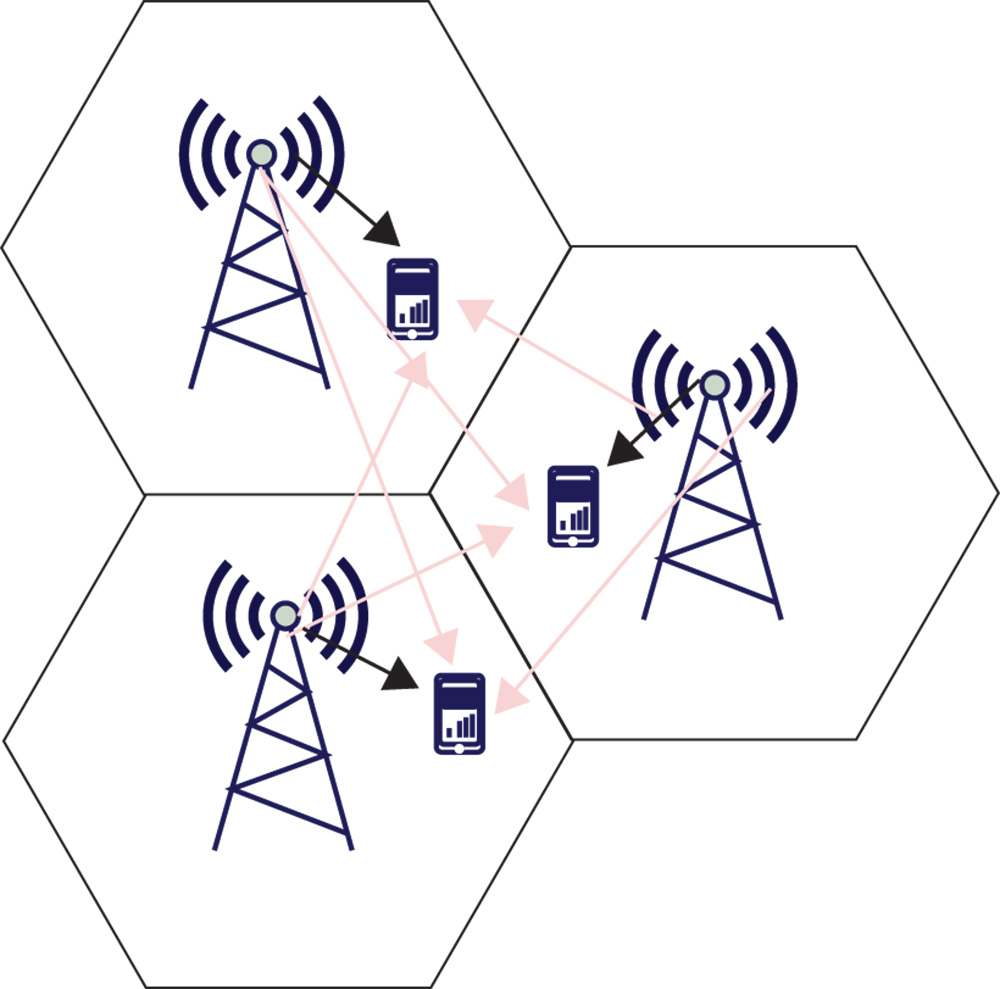
Figure 20.7 Cellular network with the deployment of massive MIMO.
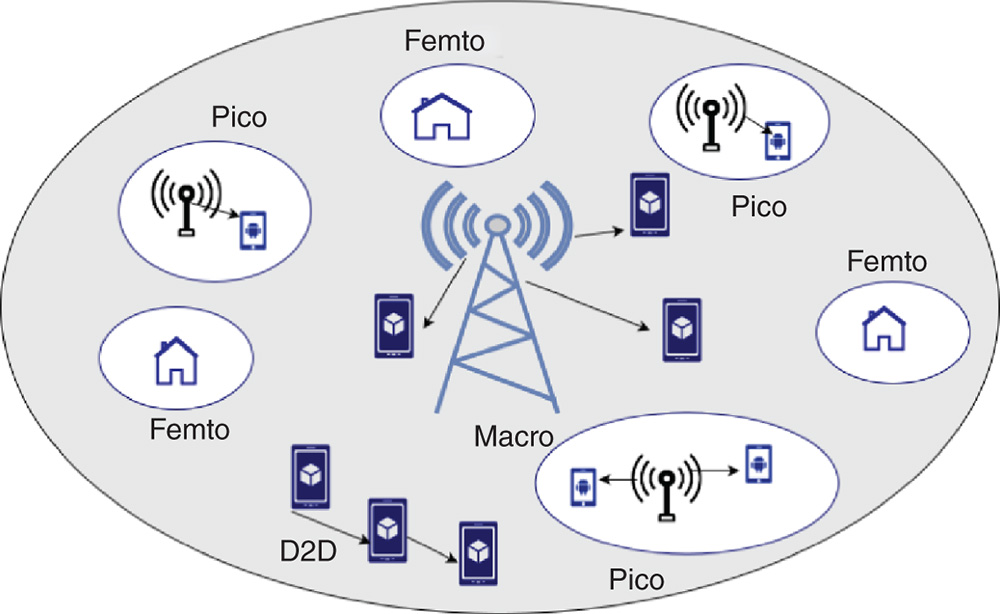
Figure 20.8 Heterogeneous network.
Yang et al. proposed the technique of heterogeneous network (HetNet), which creates a multinode topology in which many nodes of same attributes are deployed. In this perspective, the core components in HetNet are spatial modeling of nodes, associativity of cell users, and direct connection among devices. Figure 20.8 illustrates HetNet [2].
20.5.8 Multibeam-Based Communication System
MmWave has propagation limitations that are overcome by technologies like MIMO and beam-mmWave system. The basic structure for 5G is a multibeam-based communication system. Performance can be measured by the cell's capacity. Antenna array of massive MIMO and advanced beam technology is used to handle propagation limits of MMave band. 5G's basic structure for mobile network is known as a multibeam communication system. Advanced beam-forming technology has been introduced to evaluate cell capacity and disruption probability in mmWave systems with massive MIMO.
20.5.9 Software-Defined Networking (SDN)
Software defined networking (SDN) is one of the well-known techniques used by 5G. This technique partitions two functions of network: control and data-forwarding. Functions used by SDN are programmable and handle applications infrastructure, including services provided by a network. SDN is divided into three subgroups. The first is a software controller that is used to control network functions, such as a network's application programming interface (APIs), operating system, and global network view. The second group is southbound, and is dedicated to interface and protocols in the system's network. Third is the northbound group, which is responsible to provide an interface to applications of SDN and its controller.
20.6 Applications
With minimal latency and high data transfer rate, and all other salient features, 5G is supposed to serve a wide range of applications, including health care, personal usage, the tactile internet, automation, industrial usage, smart cities, virtualized homes, smart grids, etc. Some of the possible applications for 5G are discussed below.
20.6.1 Health Care
One of the most important and beneficial uses of 5G is in health care, by providing reliable and secure mobile communication for frequent data transmission from patient to cloud or to and from a remote health facility where the database for a specific patient has been maintained. A patient can get urgent and reliable medical service in the shortest possible span of time rather than by following the traditional procedures.
20.6.2 Smart Grid
5G can be pivotal in implementing smart grid technology, which focuses on better utilization of energy consumption by decentralizing energy distribution. Technologies used in 5G networks will help in smart distribution of power, providing efficient energy utilization.
20.6.3 Logistic and Tracking
5G is useful for location-based tracking. In future mobile communication systems, the tracking is easier. One of the practical examples of this application is radio frequency identification (RFID) tags.
20.6.4 Personal Usage
For heterogeneous networks, one of the key application of 5G is personal usage. It provides maximum use of UEs and meets high demand of not only text data but high-resolution video calls, voice calls, web surfing, and multimedia content, as well as providing QoS.
20.6.5 Virtualized Home
One of the most interesting applications of 5G is called virtualized home. They can be used by advances in wireless sensor networks. It will use C-RAN architecture with low-cost UEs with services of physical and data link layers.
20.7 Challenges
5G networks must address a few mentioned challenges that are not discussed for traditional LTE networks [11]. Table 20.3 briefly illustrates these challenges, and Table 20.4 shows the current research projects to address these challenges. Another big challenge that the 5G network faces is caching, which will need to meet high multimedia content demands, due to the rapid growth of smart devices' users. Moreover, currently used wireless networks cannot cope with this usage and fail to tackle the explosively growing traffic, due to its centralized architecture. Intermediate servers or routers use content caching so that the same content can be loaded easily and swiftly without the need of retransmission from remote servers, and redundant or duplicated traffic could be eliminated. The traditional caching used by both 3G and 4G LTE networks has been shown to reduce mobile data traffic by one to two thirds. However, there are still some issues including where to cache, e.g. at evolved packet core (EPC) or radio access network (RAN); and what to cache and how to cache, e.g. least recently used (LRU), LFU, or FIFO. EPC and RAN caching can minimize the redundant traffic to servers. Also, caching on the network edge balances the traffic for longer periods. By studying the traffic reduction and cost estimation, it is concluded that EPC and RAN caching techniques can enhance current 3G and 4G wireless networks and could be useful in 5G [14]. 5G systems will have different technologies and standards in one device and platform and will properly combine the CDMA-OFDMA together that will enhance the quality and performance. This new reuse division system of HMA will increase the capacity of the nodes [43, 44].
Table 20.3 Challenges of 5G.
| Challenges | Enable to address challenges | 5G design principles |
| Capacity ×1000 >70% indoor |
|
UHF and other spectrum options, e.g. pooling. |
| Data rate ×10–100 |
|
Optical transmission and switching wireless possible. |
| Massive number of connections ×10–100 |
|
Minimize number of network beam and pool resource as much as possible. |
Table 20.4 Research projects on 5G.
| Research project/institutions Research groups | Research area | URL |
| 5G NOW (5th Generation Non Orthogonal Waveforms for asynchronous signaling) | Nonorthogonal waveform | http://www.5gnow.eu |
| 5G PPP (5G Infrastructure Public Private Partnership) | Next generation of communication networks, ubiquitous super-fast connectivity | http://5g-ppp.eu/ |
| COMBO (Convergence of fixed and Mobile Broadband access/aggregation networks) | Fixed/mobile converged (FMC) broadband access/aggregation networks | http://www.ict-combo.eu |
| (Interworking and Joint Design of an Open Access and Backhaul Network) | RAN-as-a-Service, radio access based upon small cells, and a heterogeneous backhaul | http://www.ict-ijoin.eu |
| MAMMOET (Massive MIMO for Efficient Transmission) | Massive MIMO | http://www.mammoet-project.eu |
| METIS (Mobile and wireless Communications Enablers for Twenty-twenty) | Provide a holistic framework 5G system concept | https://www.metis2020.com |
| MCN (Mobile Cloud Networking) | Mobile network, decentralized computing, smart storage | http://www.mobile-cloud-networking.eu/site |
| MOTO (Mobile Opportunistic Traffic Offloading) | Traffic off-loading architecture | http://www.ict-ras.eu/index.php/ras-projects/moto |
| PHYLAWS (Physical Layer Wireless Security) | Security approaches for handsets and communications nodes | http://www.phylaws-ict.org |
| TROPIC (Traffic Optimization by the Integration of Information and Control) 5GrEEn | Femto cell networking and cloud computing environmentally friendly 5G mobile network | http://www.ict-tropic.eu |
| University of Edinburgh | Indoor wireless communications capacity | www.ed.ac.uk |
| University of Surrey 5G Innovation Centre (5GIC) | Lowering network costs, anticipating user data needs to preallocate resources, dense small cells, device-to-device communication | www.surrey.ac.uk/5gic |
20.8 Conclusion
This article has discussed and observed a complete and detailed survey of 5G's future. The discussion involved basics of existing technologies, their comparison and evolution. 5G wireless requirements are defined as capacity, data flooding, and energy efficiency, low latency, high frequency, delay tolerant, and QoS in future cellular networks. Further, we discussed different works on wireless network architecture with amendments required for 5G that are energy efficient, cloud-based, and data-centric, and cognitive RAN-based architecture. A complete survey of 5G architectures is defined, along with all growing technologies and their architectures such as BDMA, mmWAVE, HetNet, flexible duplex, and more. The article concludes with the main issues faced by 5G and research areas.
References
- 1 Zheng, M., Quan, Z.Z., Guo, D.Z. et al. (2015). Key Techniques for 5G Wireless Communications: Network Architecture, Physical Layer, and MAC Layer Perspectives. Berlin, Heidelberg: Science China Press/Springer-Verlag.
- 2 Yang, N., Wang, L., Geraci, G. et al. (2015). Safeguarding 5G wireless communication networks using physical layer security. IEEE Communications Magazine 53 (4): 20–27.
- 3 Kiran, P., Jibukumar, G.M., and Permkumar, V.C. (2016). Resource allocation optimization in LTE-A/5G networks using big data analytics. In: Proceedings of the 2016 International Conference on Information Networking (ICOIN), 254–259. Washington, DC: IEEE.
- 4 Lin, Z., Du, X., Chen, H. et al. (2019). Millimeter-wave propagation modeling and measurements for 5G mobile networks. IEEE Wireless Communications 26 (1): 72–77.
- 5 Yaacoub, E., Husseini, M., and Ghaziri, H. (2016). An overview of research topics and challenges for 5G massive MIMO antennas. In: 2016 IEEE Middle East Conference on Antennas and Propagation (MECAP), Beirut, Lebanon.
- 6 Addad, R., Bagaa, M., Taleb, T. et al. (2019). Optimization model for cross-domain network slices in 5G networks. IEEE Transactions on Mobile Computing https://doi.org/10.1109/TMC.2019.2905599.
- 7 Elayoub, S.E., Brown, P., Deghel, M., and Galindo-Serrano, A. (2019). Radio resource allocation and retransmission schemes for URLLC over 5G networks. IEEE Journal on Selected Areas in Communications 37 (4): 896–904.
- 8 Yao, M., Sohul, M., Marojevic, V., and Reed, J.H. (2019). Artificial intelligence defined 5G radio access networks. IEEE Communications Magazine 57 (3): 14–20.
- 9 Siddiqui, M.M. (2011). Vision of 5G communication. In: Communications in Computer and Information Science, Springer Nature, 252–256. Springer.
- 10 Gupta, A. and Jha, R.K. (2015). A survey of 5G network: architecture and emerging technologies. IEEE Access 3: 1206–1232.
- 11 Agyapong, P.K., Iwamura, M., Staehle, D. et al. (2014). Design considerations for a 5G network architecture. IEEE Communications Magazine 52 (11): 65–75.
- 12 Modi, H. and Patel, S.K. (2013). 5G technology of mobile communication. International Journal of Electronics and Computer Science Engineering 18 (3): 1265–1275.
- 13 Qazi, F., Khalid, O., Rais, R.N.B. et al. (2019). Optimal content caching in content-centric networks. Wireless Communications and Mobile Computing 2019, Art. No: 6373960: 15. doi: 10.1155/2019/6373960.
- 14 Wang, X., Chen, M., Taleb, T. et al. (2014). Cache in the air: exploiting content caching and delivery techniques for 5G systems. IEEE Communications Magazine 52 (2): 131–139.
- 15 Sapakal, R.S. and Kadam, S.S. (2013). 5G Mobile technology, International Journal of Advanced Research in Computer. Engineering & Technology 2 (2): 568–571.
- 16 Wang, Y., Wang, K., Huang, H. et al. (2019). Traffic and computation co-offloading with reinforcement learning in fog computing for industrial applications. IEEE Transactions on Industrial Informatics 15 (2): 976–986.
- 17 Ning, Z., Huang, J., and Wang, X. (2019). Vehicular fog computing: enabling real-time traffic management for smart cities. IEEE Wireless Communications 26 (1): 87–93.
- 18 Nobre, J.C., Souza, A.M., Rosárioc, D. et al. (2019). Vehicular software-defined networking and fog computing: integration and design principles. Ad Hoc Networks 82: 172–181.
- 19 Mutlag, A.A., Ghania, M.K.A., Arunkumar, N. et al. (2019). Enabling technologies for fog computing in healthcare IoT systems. Future Generation Computer Systems 90: 62–78.
- 20 Yao, X., Kong, H., Liu, H. et al. (2019). An attribute credential based public key scheme for fog computing in digital manufacturing. IEEE Transactions on Industrial Informatics 15 (4): 2297–2307.
- 21 Bilal, K., Khalid, O., Erbad, E., and Khan, S.U. (2018). Potentials, trends, and prospects in edge technologies: fog, cloudlets, mobile edge, and micro data centers. Computer Networks 130: 94–120.
- 22 Qayyum, T., Malik, A.W., Khattak, M.A.K. et al. (2018). FogNetSim++: a toolkit for modeling and simulation of distributed fog environment. IEEE Access 6: 63570–63583. https://doi.org/10.1109/ACCESS.2018.2877696.
- 23 Ghosh, A., Khalid, O., Rais, R.N.B. et al. (2019). Data offloading in IoT environments: modeling, analysis, and verification. EURASIP Journal on Wireless Communications and Networking 2019 Art. No: 53 https://doi.org/10.1186/s13638-019-1358-8.
- 24 Barzegaran, M., Cervin, A., and Pop, P. (2019). Toward quality-of-control-aware scheduling of industrial applications on fog computing platforms. Proceedings of the Workshop on Fog Computing and the IoT, Montreal, Quebec, Canada, April 15.
- 25 Andrews, J.G., Buzzi, S., Choi, W. et al. (2014). What will 5G be? IEEE Journal on Selected Areas in Communications 32 (6): 1065–1082.
- 26 J. Sheetal, Architecture of 5G technology in mobile communication, Proceedings of the 18th IRF International Conference, Pune, India, 2015.
- 27 Tehrani, M.N., Uysal, M., and Yanikomeroglu, H. (2014). Device-to-device communication in 5G cellular networks: challenges, solutions, and future directions. IEEE Communications Magazine 52 (5): 86–92.
- 28 Rowell, C.L.I.C., Han, S., Xu, Z. et al. (2014). Toward green and soft: a 5G perspective. IEEE Communications Magazine 52 (2): 66–73.
- 29 Zhang, X., Zhang, J., Wang, W. et al. (2015). Macro-assisted data-only carrier for 5G green cellular systems. IEEE Communications Magazine 53 (5): 223–231.
- 30 Hu, R.Q. and Qian, Y. (2014). An energy-efficient and spectrum efficient wireless heterogeneous network framework for 5G systems. IEEE Communications Magazine 52 (5): 94–101.
- 31 Hong, X., Wang, J., Wang, C., and Shi, J. (2014). Cognitive radio in 5G: a perspective on energy-spectral efficiency trade-off. IEEE Communications Magazine 52: 46–53.
- 32 Akyildiz, F.I., Lee, W.Y., and Chowdhury, K.R. (2009). CRAHNs: cognitive radio ad hoc networks. Ad Hoc Networks 7 (5): 810–836.
- 33 Hossain, E., Rasti, M., Tabassum, H., and Abdelnasser, A. (2014). Evolution toward 5G multitier cellular wireless networks: an interference management perspective. IEEE Wireless Communications 21 (3): 118–127.
- 34 McKeown, N., Anderson, T., Balakrishnan, H. et al. (2008). OpenFlow: 1197 enabling innovation in campus networks. IEEE Computer Communication Review 38 (2): 69–74.
- 35 Checko, A., Christiansen, H.L., Yan, Y. et al. (2015). Cloud RAN for mobile networks – A1099 technology overview. IEEE Communication Surveys and Tutorials 17 (1): 405–426.
- 36 Felita, C. and Suryanegara, M. (2013). 5G key technologies: identifying innovation. In: 2013 International Conference on Quality in Research, QiR 2013, 235–238. IEEE.
- 37 M. O. Farooq, C. J. Sreenan, K.N. Brown, Research challenges in 5G networks: a HetNets perspective, Proceedings of the 19th International Conference on Innovations in Clouds, Internet, and Networks (ICIN 2016), 2016.
- 38 Goyal, P. and Buttar, A.S. (2015). A study on 5G evolution and revolution. International Journal of Computer Networks and Applications 2: 2.
- 39 Aryaputra, A. and Bhuvaneshwari, N. (2011). 5G – The future of Mobile Network, Proceedings of the World Congress on Engineering and Computer Science 2011, 843–847. San Francisco, CA.
- 40 Le, L.B., Lau, V., Jorswieck, E., Dao, N., Haghighat, A., Kim, D.I., Le-Ngoc, T., “Enabling 5G mobile wireless technologies,” EURASIP Journal on Wireless Communications and Networking, no. 218, (2015). https://doi.org/10.1186/s13638-015-0452-9.
- 41 E. White, 5G radio access [online]: http://www.5gsummit.org/seattle/docs/slides/Kumar-5GSummit-Radio-Access-revA3.pdf, 2019 (accessed December 2019).
- 42 Liu, L. and Zhang, C. (2015). Circuits and systems for 5G network: massive MIMO and advanced coding. In: IEEE 11th International Conference on ASIC (ASICOON), 34–55.
- 43 Wang, L. and Rangapillai, S. (2012). A survey on green 5G cellular networks. In: International Conference on Signal Processing and Communications (SPCOM), 232–245. IEEE.
- 44 Ge, X., Cheng, H., Guizani, M., and Han, T. (2014). 5G wireless backhaul networks: challenges and research advances. IEEE Network 28 (6): 6–11.
