5
Security and Privacy Issues in Fog Computing
Ahmad Ali, Mansoor Ahmed, Muhammad Imran, and Hasan Ali Khattak*
Department of Computer Science, COMSATS University Islamabad, Islamabad, 44000, Pakistan
5.1 Introduction
Smart devices provide the building blocks for the Internet of Things (IoT). IoT is populating the research and development landscape exponentially in different dimensions like home automation, industrial automation, and manufacturing, as well as healthcare. Fog computing is the process that helps to extend the data storage, communication power and computing speed near to end users. In fog computing networks, the edge devices are connected and integrated closely, which helps to enhance the performance and system efficiency. To some extent, fog computing is also called edge computing, because both of them are used to increase the efficiency of the system; however, their processing systems are different.
We can move the data to the optimum place for processing; and decisions can be based on how quickly a result is needed. For example, time-sensitive decisions should be made closer to the things producing and acting on the data. In contrast, big data analytics on historical data needs the computing and storage resources of the cloud. While in fog computing, they work locally on the data that needs analysis instead of sending it to the server or cloud computing servers, as shown in Figure 5.1. In a fog computing system, there are nodes used for connection and working of this system, which are protected by the policy and procedure of the regular IT environment.

Figure 5.1 Fog computing enabled smart cities. (See color plate section for the color representation of this figure)
Security, privacy, and accountability of service providers are the core areas when it comes to the implementation and integration of smart devices that are connected to the fog-enabled infrastructures, as shown in Figure 5.2. It is obvious that “trust” would be included in a collective concept of security and privacy, as shown in Figure 5.3. Furthermore, IoT Security may be explored as “things identification,” “authentication,” and “authorization.” Unique identification and authentication provide the legitimacy of the thing. Access control is carried out by authorization methods, which define available roles and functions for a specific thing. However, with this state-of-the-art technology, several issues arise among which security and privacy are considered as the most significant challenges in fog computing. The security and privacy measures that were being applied in cloud computing cannot be applied in fog computing due to its different structure and functionalities like large-scale geo-distribution.
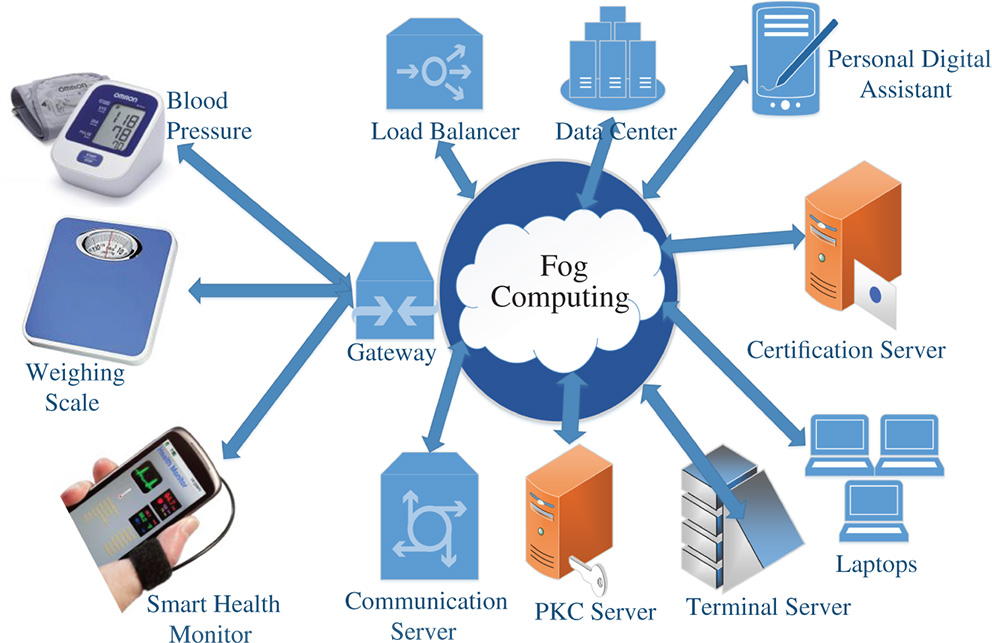
Figure 5.2 A generic fog enabled IoT environment. (See color plate section for the color representation of this figure)
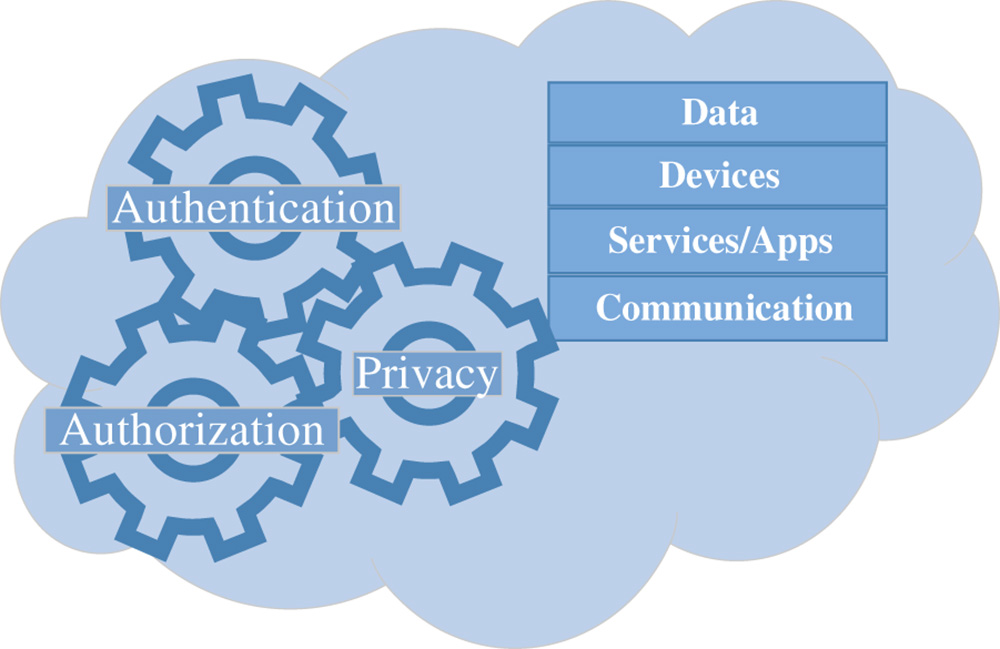
Figure 5.3 Internet of Things security phenomenon.
This chapter is organized as follows: initially, we start by describing the basics of trust and its important components. Then we move on to explore security, in which we present related work in sections of authentication and authorization. Privacy being one of the most important components discusses related work and basic requirements to ensure the trust of end users in the IoT and fog by proposing privacy-preserving techniques. The section on web semantics and trust management discusses the importance of web semantics and the possible problems that it can help us eliminate. Finally, the discussion section concludes our chapter by using a healthcare scenario and presenting the possible solutions that one may encounter while deploying an IoT-based solution.
5.2 Trust in IoT
Trust is a vital component in today's connected world. The users should believe that the resource providers could comprehensively fulfill the requested tasks as they committed, published, and provide security and privacy to confidential information [1]. The availability of claimed services and applications is the foremost thing in trust establishment. Security aspects in the IoT can be achieved by providing secure and stringent authentication and authorization procedures. There are multiple methods used in practice to provide user authentication. Multifactor authentication with mutual consent is required to be enforced. Privacy is “The right of the individual to decide what information about himself should be communicated to others and under what circumstances” [2]. Privacy should be applicable on both users' data as well as users' activities.
IoT provides a layered architecture for Trust management as shown in Figure 5.4. Information security is required at each layer. Security to information can be provided by providing basic information security measures [1, 3–5]. Provision of controlled and meticulous access to its users is the basic principle of Information Security in Electronic Data Processing (EDP). After qualifying physical access parameters, the next step for implementing Information Security is electronic authentication. Electronic access control covers the legitimacy of a user, i.e. user identification and then authorization of access on predefined resources to the legitimate users. A user authentication mechanism initially requires user identification by the principle of something you know (user ID) or something you have (physical access) or something you are (biometrics). The user may use any of the above discussed methods for his identification, but for assuring the legitimacy of a user, the system has to validate his identity by using different other parameters like primary PIN and secondary PIN. Smart cards and USB mass storage devices are in use as physical components, such as keys of locks for legitimate authentication.

Figure 5.4 Layered depiction of components of trust.
After a comprehensive arrangement of availability of services and data in an IoT, the purposes of information security encompass the key features, e.g. confidentiality (avoiding unauthorized disclosure of the resources), integrity (data health and accuracy), authentication (concurrence of sources and data) and non-repudiation (denial of any activity).
Trust can only be achieved by providing information security and privacy measures, i.e. authentication [6–10], authorization [11], and privacy [5, 12–16]. We can achieve trust by applying measures for AAP (authentication, authorization, and privacy) at each level and for each component in the environment. It will provide a trustworthy environment whether you are in a local area network (LAN), distributed computing, IoT, Web of Things (WoT), or even in cloud computing environment.
Identification is highly coupled with security and privacy in IoT management. Different and dynamic methods of identification are key components in multiple layers of IoT, some of them are embedded in the end devices whereas some of those use message routing and discovery. Each type of identification (numbering, addressing, and naming) has a set of important influencing factors that create divergence and it is also important to appreciate that these differences are often necessary and sometimes advantageous. As IoT exploits established elements and applications there is a legacy environment that cannot be ignored, and which must be addressed in some part or in its totality. There are various ways to achieve this, but each technique ultimately has an effect upon IoT's scope.
Distributed environments are challenging, even those that are closed, bounded by similar functional and interoperable technologies, and supported by a clear governance structure.
5.3 Authentication
Authentication plays a key role in the security of any system. With the advancement in technology and an increased number of threats, systems need secure authentication. The authentication of assets/resources depends on their prominence and significance.
There are different authentication methods required at different layers of IoT. Device, application, and user authentications are the three major layers of authentication. Uniqueness of the devices in IoT can be achieved by enforcing architectures and policies to avoid cloning the devices [1]. Physical unclonable functions (PUF) is the concept of using intrinsic physical characteristics of the devices for identification. This concept provides hardware level physical characteristics to restrict and save the device from cloning problems. Dongle-based coupled devices is also another method for device authentication. Some devices are bounded with a detachable dongle for device authentication [17]. Both symmetric as well as asymmetric encryption techniques are widely used for secure authentication. The use of encryption for authentication credentials as well as public-key infrastructure (PKI) digital certificates are recommended for secure device authentication [18–22]. Application authentication is carried out using digital certificates, which are the key solutions to enforce application authentication [22].
The legitimacy of a user is carried out by his/her authentication using different authentication methods. Threats and vulnerabilities, an authentication procedure, and different authentication schemes are covered in the next section.
5.3.1 Related Work
Developments in electronic authentication are revolutionary and have reached their current state through a number of improvements to provide security to resources. With the advent of technology, initial text-based single-factor authentication was unable to meet the information security requirements. This resulted in the development of a two-factor authentication and further paved the way for multifactor authentication along with encryption and coupled devices (Table 5.1).
Recently, a comprehensive criticism on two-factor authentication is carried out by Wang et al. [7]. They highlighted weaknesses of two-factor authentications with the practical implementation of adversary's tools. After the implementation of two-factor authentication, usage of coupled devices is introduced. Van der Haar et al. surveyed the crucial implementation of recursive usage of IoT. IoT needs authentication for security, facilities, and benefits of using wearable sensors for authentication. There is the recursive implementation of IoT; e.g. IoT needs authentication, as well as these, are used for authentication in terms of wearable sensors also [39]. Munch-Ellingsen et al. presented their view point of two-factor authentication while using coupled/hardware-based authentication. CIPURSE contactless cards were originally designed to meet the requirements in the transportation sector and the first version of the specification mirrored and followed Open Standard for Public Transportation (OSPT) Alliance. Smartphones are very much equipped with Bluetooth. Bluetooth devices are proposed for controlling smartphones as coupled devices [17]. Host card emulation (HCE) and the near-field communication (NFC) are the two basic features of smartphones that are used for authentication. These provide single factor authentication in IoT. Authors highlighted vulnerabilities and misuse of these features. To counter these vulnerabilities, the authors proposed an additional approach of short message service (SMS) service as a second factor authentication [37].
Security and privacy risks of a user are highlighted in home automation systems by Jacobsson et al. explored the area of smart-homes [38]. A risk analysis of a smart home automation system resulted in the identification of human behavior is the main cause of these severe risks and related to the software components. The whole research concluded on the importance of integration of security and privacy in the design phase of any new development [38]. Impersonation, replay, and similar attacks are very common to OAuth. To overcome these types, work was done to introduce another concept of security manager [9]. This security manager improves the security and performance using a database having token expiration time along with other useful information to reduce multiple registrations and multiple logins for IoT network.
Arno et al. came up with the idea of using smart devices for securing assets and as an example introduced a smart lock for a bicycle using smartphones. The main logic of this lock is authentication using an accelerometer. The sample data is generated using an NFC, GPS, and Bluetooth modules and the concept is implemented using Android-based smartphones [48]. User authentication should be imparted and required when cloud and IoT service providers need periodic access to IoT/smart devices for firmware updates and other maintenance tasks [49]. Henze et al. collected research and response on privacy in which authors highlighted the issues in making users' decisions about privacy. Decisions about an individual's privacy settings should not be done by the developers or service providers. This paper presented a scheme for customizable user privacy. This scheme introduced multilevel privacy scheme and provides users with a transparent and adaptable interface for configuring privacy in IoT.
Table 5.1 State of the art research work timeline.
| 2004–2010 | 2011–2014 | 2015–2018 |
| Roaming agreements for handover procedures in mobiles [23] Proposed two-factor authentication [24] OS-based authentication [25] MFA with handheld device [26] Unique identification scheme [27] Algorithm for two-factor authentication [28] Biometrics and smart cards [8] Interoperability and standards issues Regulatory, legal, and rights issues [5] touch pattern threats (smudge attacks) [29] Threats to RFID-based authentication [16] Encrypted dynamic IDs and passwords [20] |
Visible security (two-factor authentication) [30] Need of OS for IoT as well as WSNs [31] Authentication in homogeneity as well as heterogeneity of IoT Redundant authentication [32] Electroencephalography in authentication [33] Two finger patterns [6] Three-factor authentication [34] (including USB mass storage) Authentication by secure identification [35] Mutual authentication by key management [36] Issues in two-factor authentication [7] Ciphering and physical authentication [18] Security and privacy concerns in IoT [1] |
SMS-based authentication for NFC-like communication [37] Security and privacy by design [38] A central security manager for OAuth [9] Multifactor authentication using biometrics [10] Continuous authentication [21] Verification of authentication [39] Delegation-based authentication [40] Another idea of dynamic IDs [41] IoT communication in 5G [42] Bluetooth as a coupled device [17] Identification using fuzzy [19] Asymmetric cryptography [22] Node-based mutual authentication [43] IPSec along with RFID [15] EAKA protocol [44] IoT literature [45] Multilevel privacy [12] Security issues in IoT [4] Private mutual authentication [14] Two-factor zero knowledge authentication [11] Markov chain devices authentication in trust management [46] Security and privacy issues in IoT and cloud [47] |
The idea of utilizing dynamic ID is very much active now and research is ongoing for securing IoT using dynamic IDs [41]. Node-based mutual authentication scheme for IoT considering the login ID, password hash and mandatory access control (MAC) address along with a DBMS (database management system) for the management and logging of authorized and unauthorized access controls is recommended [43]. Ruan et al. raised the issues of identity misuse. Impersonation attack is very common in the misuse of identity. A random oracle model is suggested to counter impersonation attack by extending the two-party setting to the “n” parties setting and developed an efficient two-party-based EAKA protocol as covered in the standard model [44].
Delegation-based authentication in IP-based IoT is carried out [40] to cope with the security and privacy matters in IoT. Private mutual authentication scheme to cope with privacy and discovery issues using new protocols are introduced using public-key infrastructures encryption schemes. Authors implemented this scheme using open source Vanadium framework [14]. Authors proposed identity-based cryptography (IBC) and elliptic curve cryptography (ECC) for end-to-end authentication. Asymmetric cryptography for end-to-end encryption [22]. Integration of Ciphering and other physical authentication approaches are suggested for further security and third factor authentication [18]. It is also highlighted that desirable security goals can be achieved by providing Dynamic IDs'-based authentication. An advanced framework for sharing multisite knowledge with Ciphered Dynamic credentials is also demonstrated in [20]. A protocol for Continuous Authentication in IoT where smart devices communicates limited data/messages frequently with short intervals is proposed by Bamasag et al. The protocol is based on Shamir's secret sharing scheme, with the advancement of mutual authentication. Claimer identity is verified using tokens issued for a function of time [21].
Development of new protocols and incorporate new features of IPV6 and 5G communication in IoT [42]. Mao et al. presented the idea of encryption in IoT using Fuzzy. This identity-based fuzzy encryption scheme is a lightweight, fully semantically secure and does not rely on random oracle models along with very short public parameters and quiet efficient because of its lightweight features [18]. A new term, threat index, is introduced to calculate vulnerabilities in IoT and suggested the development of new methods for security at each layer of IoT [4]. An introductory but comparative article on IoT in the area of IoT security, privacy, and trust [1]. Need for enforcement (i.e. governance in IoT) is the main crux of the paper. A comparative study was carried out where the latest European security projects in IoT analyzed and found “enforcement” to be missing [1].
Table 5.2 Authentication grid.
| Parameters | |||
| Constraints | Something you know | Something you have | Something you are |
| Only me | ID/Password | RFID | Biometric |
| Only now | Session key | ||
| Only here | Geo location bounded | ||
In the use of IoT, the privacy of an individual always remains at stake. With the advent of smart devices, it is very crucial to take care of user privacy. Mostly radio-frequency identification (RFIDs) are used for identification purposes in IoT. Authors suggested the use of IPSec along with RFID to maintain user privacy. In this approach, “Need to Know”-based rule is introduced [15]. Similarly, Díaz et al. introduced the implementation of Zero-Knowledge Authentication Protocol along with some other authentication factors in IoT authentication. One-time password (OTP) and SMS are some other factors that can be used for authentication [11, 47].
Different types of authentications are implemented to strengthen the procedure. This can be explored using the grid given in Table 5.2, which discusses parameters for each constraint.
5.4 Authorization
The authorization of the system information in IoT is a fundamental management responsibility. Practically all applications that deal with security, confidentiality, or defense include some form of access controls. An important objective of access control is to protect available system resources against unwanted and inappropriate access. Sometimes access is granted after successful user authentication; however, most of the systems require more complex and sophisticated access control. Access control can be viewed as how authorization is structured. Most of the time authorization is designed according to the organization structure, while in some cases it is based on sensitivity and clearance of documents. Some commonly used access control mechanisms are access control list (ACL), role-based access control (RBAC), capability-based access control (CBAC) and extensible access control markup language (XACML). These mechanisms are well executed in a centralized information system. Though, in such distributed environments authorization becomes a formidable challenge [4, 50].
Table 5.3 Authorization requirements in the Internet of Things.
| Constraints | Parameters | |||
| Authorization management | User managed access | Usage access management | Authorization policy management | Fine-grained access privileges |
| Third-party authorization | Authentication, authorization, and accountability | Data confidentiality | Multiaccess | End-to-end communication Least privileges |
| Semantic authorization | Contextualization | Interoperability | Heterogeneous | Integrity |
An access control system should deliberate three notions: access control mechanisms, models, and policies. Access control policies are the high-level abstraction that specifies what type of access privileges are allowed, to whom, under what circumstances, such as location or time [51]? Access control polices enforce the access control mechanism (ACL) that can be used to protect an automated system resources by identifying and preventing unauthorized access. However, an access control model (i.e. discretionary access control model) represents a formal demonstration of security policies and thus acts as a bridge between policy and mechanism. Table 5.3 demonstrates secure authorization in IoT. Authorization management [52] is required for multiaccess. Accordingly, semantic authorization requires contextualization, heterogeneous, integrated, and interoperable environment [53]. Thus, it is easy to control the access for a single ontology store. Similarly, third-party authorization is needed whenever the third party wants to access a person's specific data.
5.4.1 Related Work
Discretionary access control (DAC), one of the most frequently used access control models, is a user centric approach that is based on user directions. However, ACL is a relatively simple example of DAC, on the contrary in MAC individual owner has no right to change the access policies. IoT deals with real-time data streaming and processing of smart objects [54] over the Internet. Thus, to support the IoT ecosystem it requires a deep revision and adaptation of existing access control mechanisms. A lot of existing work will deal with these aspects.
Attribute-based access control (ABAC) is a policy-based mechanism, in which certain pre-agreed policies are used to grant users access. Su et al. [55] present attribute-based signature scheme with standard Diffie–Hellman assumption to reduce computational cost. Ye et al. [56] define ABAC policies by using a light-weighted encryption mechanism called elliptic curve cryptography in a distributed ecosystem. However, this extended proposed mechanism lacks confidentiality, which is mandatory for the distributed environment. In [57], Ning et al. suggested aggregated-proof-based hierarchical authentication (APHA) to provide hierarchal attribute-based access control. This proposed scheme uses homomorphism function for Chebyshev chaotic maps and directed path descriptors to achieve data integrity and data confidentiality. However, in APHA the following assumptions are made, such as that path descriptor is fresh and a trusted third party has authority on the entitled values, so any malicious activity can cause the loss of user's personal data. Misra et al. [58] proposed a theoretical next-generation IoT architecture using distributive policy-based access control. Although ABAC used to assign permissions dynamically but nested groups are the major limitations of ABAC.
Role-based access control (RBAC) is more powerful and generalized than MAC and DAC because it grants access rights by assigning roles. The main advantage of using RBAC and ABAC in term of IoT is that it can be easy to modify the access rights dynamically by simply modifying the role and attribute assignments. However, there is a need to introduce a new form of RBAC [59–62] and ABAC [56, 58, 63, 64] styles in IoT because users are allowed to access particular data in real-time environment. Gusmeroli et al. [65] affirm that several authorization frameworks like ABAC [66] and RBAC do not provide an effective and manageable mechanisms to support IoT, because such frameworks cannot provide least privileges. For this, Adda et al. [59] proposed a CollABAC and CollRBAC models to evaluate IoT Collaborative requirements. Lee et al. [66] proposed a dynamic model called location-temporal access control (LTAC). This model combines time and location with security level for access control for stable communication. Access is granted only if a given node is located within an appropriated time interval and location with respect to another node.
The author in [67] introduces the concept of capabilities (called capability-based access control CapBAC) to achieve least privileges for access control and suggested the identity authentication and capability-based access control (IACAC) scheme to grant access on the local network. In CapBAC, user's authorization capabilities have to be presented to the service provider. Whereas in traditional ACL it is the responsibility of service provider to check if the user is indirectly or directly authorized for the requested resource. Mahalleet et al. [68] represent capability-based context aware access control for federated IoT networks. This scheme is flexible, integrated, and scalable but still lacks granularity, reliability, and trust. A distributed capabilities-based access control model (DCapBAC) [69] uses a distributed approach where smart objects are enabled with access control logic with IoT devices. Hernández-Ramos et al. [70] presented an efficient, scalable, integrated, usable, and fully DCapBAC for certification and authorization. However, this proposed model does not provide trust mechanism, so access control decisions are taken according to trustworthiness values. Bernabe et al. [71] proposed a trust-aware access control mechanism based on DCapBAC, which provides a flexible, efficient, and end-to-end security access control mechanism. However, it does not provide any privacy-aware feature that allows smart objects to create capability tokens anonymously. Hernandez-Ramos et al. [72] proposed enhanced privacy-aware DCapBAC mechanism for the IoT, by using anonymous authorization tokens in order to deal with privacy concerns with the integration of idemix. But there is a need that these capabilities be usable and easy to understand by the user. It is also important that least privileges are granted by default.
From the previously discussed work, the major challenges that are emerging in IoT scenario are the following.
- Which access control mechanism is required that not only grants access to the users but also smart objects that could be authorized to interact with the information systems?
- To deal with flexible and scalable IoT ecosystem, is it useful to exploit the distributed, centralized, or semi-distributed approach?
- How can the identification of smart objects (Things) be supported?
To deal with the identity issue, Li et al. [73] designed a practical identity-based framework for wireless sensor networks (WSN) in the context of IoT by using heterogeneous signcryption (HSC) scheme. Integrity, nonrepudiation, authentication, and confidentiality are simultaneously attained. However, two types of adversaries have an effect on the security of certificate-less systems. The first type of adversarial model refers to a trusted third party (TTP) who can easily fake the user's public key to the user's random secret value. In the second type of adversarial model, a key generating center (KGC) can be compromised and act maliciously to access the users' private and partial public keys. Furthermore:
- How is access control managed? How do we deal with the issuance of certificates and registration of smart objects and users?
- How do we define specific types of roles and functions in IoT systems?
To answer these issues, new solutions have been recently proposed that use the OAuth protocol to secure the network protocol. They leverage the idea of RBAC and reduce the numbers of rules by using the key-value attribute system. Customized fine-grained access policies can be used so that things can interact in an IoT environment. This demonstrates a further step in the direction of the management of registering things, users, and their certificates, but still, an extra effort is required to establish standards that will be globally accepted.
The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) includes practical, physical, and management standards of information systems for security and privacy. Almost all applications that deal with security, confidentiality, or defense include some form of access controls. Some commonly used access control mechanisms and services are role-based access control [74], capability-based access control, ACL, and XACML. These well-known access control models and mechanisms are implemented in a centralized information system. However, in a distributed environment, authorization becomes a formidable challenge when it is distributed to multiple systems [50].
5.5 Privacy
Privacy and security are undoubtedly the most important issues as they are at the core of trust, relationship building, and exchange [75]. In IoT and fog, the trust is developed based on security and privacy, and they lie under the umbrella of trust as shown in Figure 5.4. So, with reference to security, three essential components – confidentiality, integration, and availability (CIA) – are needed in addition to the authentication and authorization. Therefore, in privacy data protection and personal information of user have to be certified, whereas devices carry a lot of sensitive data.
In IoT, privacy is a major concern to keep the information of individuals from the coverage of the other devices in IoT environment. Privacy concerns in the IoT are improved by the way they expand the feasibility and spread the observation and tracking of devices. The motive behind this research is to explore the importance of privacy and how personal data is collected, analyzed, used, and protected in the IoT environment.
Table 5.4 Privacy requirements in the light of Internet of Things.
| Constraints | Parameters | |||
| Device privacy | Authorization | Reliability | Accessibility | Identification and tracking |
| Communication privacy | Accuracy | Transferability | Encryption | Timeouts |
| Storage privacy | Data minimization and portability | Data management, access control | Life cycle transition privacy and inventory attacks | Anonymity, linkage |
| Processing privacy | Transparent disclosure | Right to be forgotten, inevitability | Profiling, event detection, | Freedom of choice |
As individuals have their daily activities and performances measured, recorded, and analyzed, there is an insistent need for inventors to keep in mind who collects which kind of personal information, how it is then stored and used, and to whom and for what purposes it is disclosed. Our main concern in IoT and fog is about the privacy concerns that are covered under trust and how they should be treated.
5.5.1 Requirements of Privacy in IoT
In IoT the privacy is defined as “the right of an entity, acting in its own behalf, to determine the degree to which it will interact with its environment, including the degree to which the entity is willing to share information about itself with others” [76]. The privacy of a person using a device [77] may be revealed by the smartphone and it contains information about the user. Table 5.4 shows our findings that are related to protecting privacy in the IoT. There are four stages of privacy that we discuss in our grid, and every stage has some constraints.
5.5.1.1 Device Privacy
Device privacy is quite important in the context of IoT. It helps to preserve the secrecy of sensitive device data. It includes authorization, reliability, accessibility, identification, and tracking of malicious activity performed on data that should be recovered.
5.5.1.2 Communication Privacy
In communication privacy, encryption is the most important factor to guarantee data confidentiality during transmission, timeouts/session, accuracy, and transferability.
5.5.1.3 Storage Privacy
When it comes to trust management in IoT, storage privacy is the core of privacy. The least of personal information needs, to some extent, to be stored. Personal information would be reserved for a certain time period. “Need-to-know” should always be the basis of revealing information. Storage privacy includes data management, access control, data minimization and portability, life-cycle transition privacy, inventory attacks, and anonymity linkage.
5.5.1.4 Processing Privacy
Parameters that are part of communication privacy are transparent disclosure, right to be forgotten, and freedom of choice. Both privacy preservation and primary principles would include freedom of choice parameters. Profiling accumulates information records around entities in order to conclude securities by incorporating profiles and data. Inevitability is the ability for users to intervene: the right to access, change, correct, block, revoke consent, and delete their personal data.
Users can manage the process themselves and control their environment and communicate data with other humans entities. To achieve privacy in IoT, various privacy models from the literature are studied and summarized to determine whether they can be extended in the context of IoT. Protecting device privacy becomes increasingly difficult as the IoT becomes more prevalent. In [63] the attribute-based encryption is used to analyze the results of time, data overhead, energy consumption, and CPU/memory usage in PC-class and Android-based smartphones. In [78] the cooperative distributed systems (CDS) model of IoT is proposed for the prevention of the unauthorized acts of execution. In [79], the conditional privacy-preserving authentication with access linkability (CPAL) model proposed for roaming service provides multilevel privacy preservation for networking.
Communication privacy is one of the important factors that cannot be neglected in IoT. In [80], authors proposed a scheme called privacy preserved data mining (PPDM) in sensor data to evaluate the privacy risk in IoT. Similarly, [81] purposed an ecosystem within broad smartphone ecosystem that will be the platform responsible for the distribution of apps for smart home and IoT devices. In [82], authors purposed a key-policy attribute-based encryption (KP-ABE) scheme supporting any monotonic access structure with constant size ciphertext and verified that the proposed scheme is semantically secure.
IoT devices can collect data about people in one zone and transmit that data to another zone for data storage. A decentralized anonymous credential system is introduced and implemented by [83] within the privacy-preserving self-adaptive model of IoT community targets. In [72], certificate basic foundations under public key cryptography and anonymous credential system is proposed for privacy. The authors in [84] proposed a delay-free method of anonymization for privacy preservation in electronic health data stream, which can also be used in IoT.
Privacy during information processing in the IoT is also a very important factor. Authors in [85] presented a novel token-based approach to attain distributed privacy-preserving access control in single-owner multiuser sensor networks. Another approach proposes a communication protocol for the measurement of the overall security and privacy architecture of smart meters by counting friendly distribution [86]. Authors of the data streams usually contain confidential data are help to reveal other useful information for K-anonymity [87]. Figure 5.2 shows the taxonomy of privacy, where privacy preserving and privacy management schemes are further divided into categories.
5.6 Web Semantics and Trust Management for Fog Computing
Current Internet technologies facilitate the integration of information from a syntactical point of view, but future proposals are working toward a semantic approach. The initial goal of the semantic web was to achieve an intelligent and sophisticated web that will alleviate the human factor [88]. They presented the semantic Web services that leverage ontologies to generate and parse machine readable web pages. Along with the demand in a fully integrated web, the critical need for information management and its security becomes paramount. Various models and systems have been proposed as future proposals [89] to protect the data and information from unauthorized use as well as corruption since the early days of the web as shown through the detailed taxonomy in Figure 5.5
In this era where the emergence of web and information technology systems are excessively growing day by day, data will be an important information resource in many business areas. Essentially the semantic web is a collection of layers that take advantage of underlying technologies, the most basic layer is the protocol layer that is not included in the literature while discussing semantic web technologies as described in Figure 5.6. The next is eXtensible Markup Language (XML) layer, a document representation language, which lays the ground for a resource description framework (RDF) layer. This RDF provides a framework for specifying ontology languages, such as web ontology language (OWL), it not only addresses the inadequacy of RDF but also provides the power of reasoning about various policies using Semantic Web Rules Language (SWRL) [90] and Rule Markup Language (RuleML) [91]. On top of these, the literature proposes the Trust layer [92], which not only is important but a much-needed part of the whole Semantic web stack.
5.6.1 Trust Through Web Semantics
Trust is achieved through different access control models, such as MAC [93], DAC, RBAC [94], location-based access control (LBAC), temporal access control, and ABAC. MAC usually enforces access control by attaching security labels or tags to users and objects while DAC enforces permissions on objects based on the object owner's configuration. These two models can be simulated by RBAC, which is a loosely coupled form of a mixture of components. A role is a collection of permissions for performing a certain task, a permission is an access mode that can be exercised on an object, and, finally, a session that relates the user to the object for a certain role. Most of the modern access control methods not only rely on but also support web semantics for decision making when it comes to ensuring trust management.
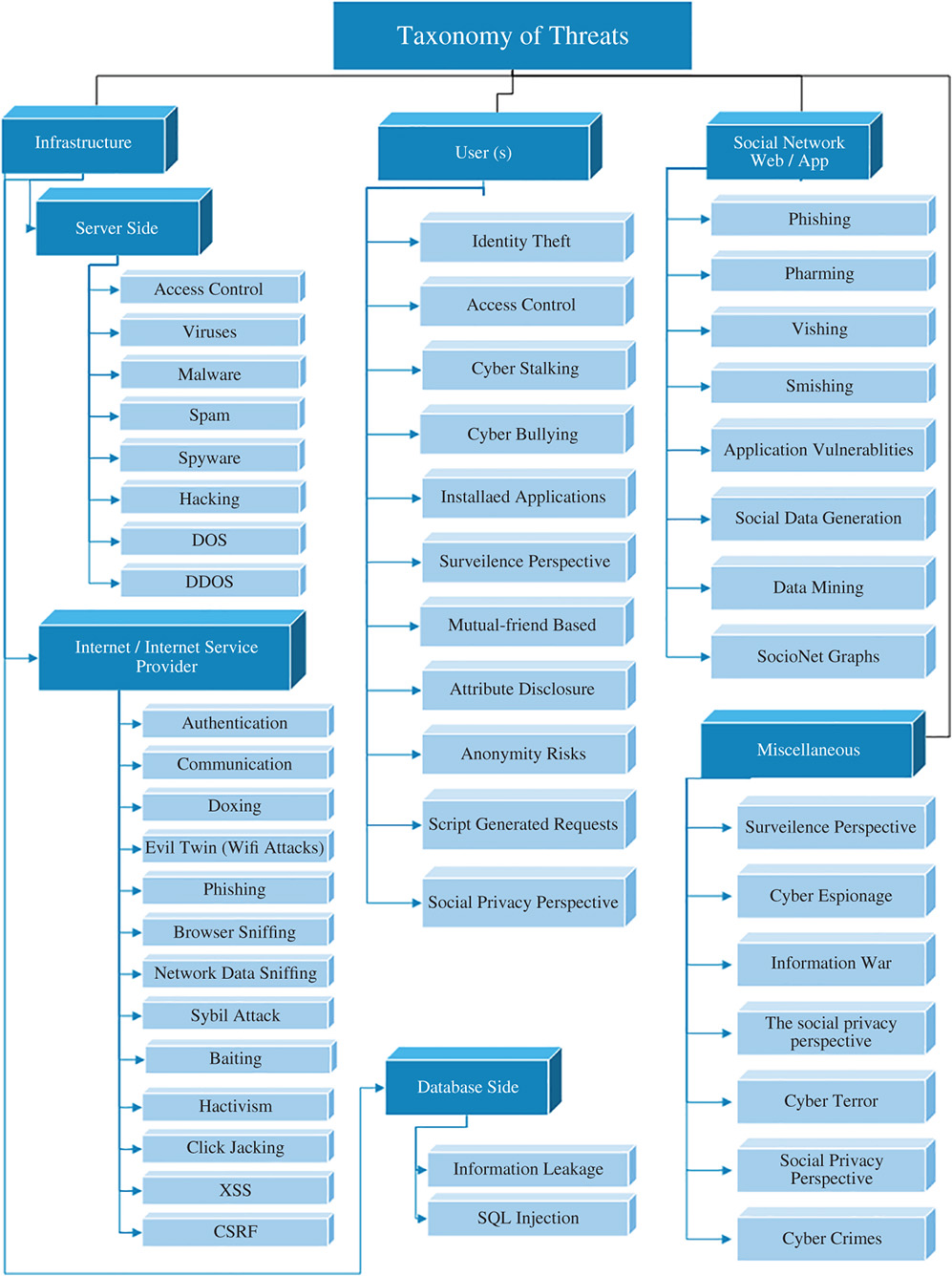
Figure 5.5 Detailed taxonomy of threats.

Figure 5.6 Semantic web technology stack by Tim Berners-Lee 2000 (http://w3c.org).
Traditionally, security (authentication and authorization) and semantics are discussed in different contexts, mainly because security is considered as a separate layer in federated IoT ecosystem. To deploy IoT-based cost-effective solutions, a tremendous amount of work has been done to develop standards and protocols. The most challenging aspect of IoT standards is the availability of too many standards, which generates an interoperability issue. Interoperability becomes a worse problem in IoT because different architectures are used for communication in different ecosystems. For example, in web-based applications for healthcare, a REStful protocol stack, such as CoAP [95] is used. However, in the device-to-device communication in IoT and fog, several other stacks and protocols can be used, such as data distribution service (DDS) and message queuing telemetry transport (MQTT). Because of using multiple and a variety of protocols, there is another issue called integrity that arises. To overcome this issue there exist several access control models and policies to control unauthorized access [96]. If various security access models break the interoperable communication, it is still a problem because it creates compatibility issues between multiple secure access models. In these situations, a secure trusted environment is needed that allows entities to share and interact their information easily. A semantic-based approach allows controlling the access using a single ontology store [97].
Accordingly, semantic authorization requires to support contextualized, heterogeneous, integrated, and interoperable environment [53]. In a secure semantic web environment, the privacy-preserving methods are deliberated in access control model and trust modeling techniques. The access control models focus on subject-oriented requirements of information about resource access. Moreover, it also finds strong semantic relations for data models in knowledge. Proof of valid semantic web information is also considered under trust management. The privacy in semantic web regards keeping user-sensitive information secret throughout semantic web interaction. Privacy should be preserved, and confidential data should not be disclosed. Moreover, in information systems, both security and privacy must be provided protection of individual and nonmalicious users. In the semantic web, environment user should be protected against misuse and exposition of sensitive data where data is accessed, shared, exchanged, and mined. The semantic web would be facing a challenge regarding “how to collect and use personal information.”
Privacy is considered to be a nonfunctional requirement in the semantic web; thus, it should be present in all the layers of the sematic web. The main focus of the semantic web regarding privacy is to prevent information resources from unauthorized access, modification of data, and unwanted use of resources [98]. Consequently, implementation of the access control model and trust models' mechanisms should assure the execution of the privacy requirements. Moreover, privacy apprehensions relating to these mechanisms have an obligatory role for considering privacy-preserving methods in the semantic web.
5.7 Discussion
We demonstrate the findings of our work in trust for the IoT using a use-case scenario depicting the interactions as well as the components of an IoT-based patient monitoring system. The system is connected to different parts of the patient and continuously monitoring her. Trusting a new system is a difficult task on its own, and when the system involves a total machine-to-machine communication ideology, then it becomes even more difficult. Though this can be made possible with the enforcement of Identification, Authentication, Authorization, and Privacy mechanisms.
Alice is an elderly patient with cardiovascular complications and hearing impairment and has received a pacemaker, which can be connected to a prepaired Bluetooth control device while the hearing aid is installed to her ear, as shown in Figure 5.7. She also has healthcare insurance subscription, which entitles her to emergency as well as specialized healthcare treatment. The said subscription can be verified through a smart card that stores her information, not only related to her health record, but also her social and economic situation, to ensure the best possible healthcare policy from the insurance company. This RFID card is microchip-enabled, which provides necessary services to ensure her privacy.
On a certain day, Alice feels she needs to have a doctor's visit for some pain due to the hearing aid and thus wants to visit the hospital that covers her medical visits according to her insurance policy. On her arrival she passes through the information desk and upon swiping the smart card the hospital's automatic machine prints her a visitor's slip containing the booking with the ENT specialist. This scenario will tackle the situation in which Alice's smart card is used to authenticate her for accessing different services on the hospital premises. The sensors present in the hospital would be authorized to access her medical record upon providing legitimate signatures while the communication is done through public key cryptography to ensure her privacy.
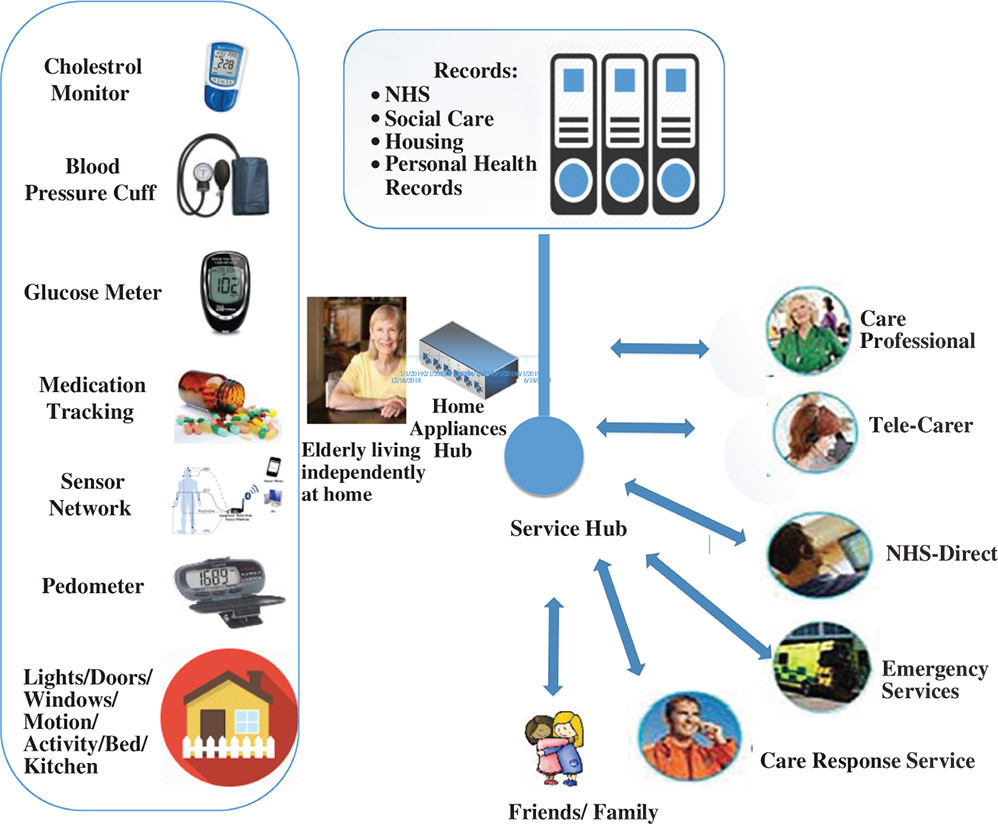
Figure 5.7 With the appropriate sensors and wireless technology, several wireless sensors enabled services can be provided to patients, such as the elderly.
Source: Freescale Semiconductor.
5.7.1 Authentication
General parameters for electronic authentication are unique identification and temporal variables. Identification variables may be used singularly as well as in a set of two or three to identify a legitimate user. Temporal variables are additional parameters to secure the authentication. Some known identification variables are (1) something you know, (2) something you have, and (3) something you are. Similarly, temporal variables are intended (1) only for an identified user, (2) only for a specified time, and (3) only at specified geo location to restrict individual, duration, and location.
Multiple methods are used in practice to provide user authentication; for example, one factor uses user ID and password. For more security, the second factor is used; for example, authentication verification via SMS, use of biometric devices, passcode through e-mail, or even using a phone call. Use of encryption techniques in transferring credentials provides the third factor for secure authentication. Another approach for secure authentication is three-dimensional (3D) authentication used in credit/debit card transaction validations. Smart cards also play an important role in the provision of secure authentication.
There are different authentication schemes covered in a comprehensive taxonomy presented in Figure 5.8:
- Text-based (using textual input like user id, password, SMS, email, etc.)
- Three-dimensional (third party guaranty required for the successful transaction on cards)
- Biometric (fingerprints, retina scans, voice signatures, and wearable sensors)
- Electronic gadgets (coupled devices like dongles, etc.)
We have to focus not only on identification but also for the authentication of the activity and transactions in terms of financial services. IoT operating system is another idea for central authentication for enabling control at the distributed level. With the development, availability and application of such operating systems will significantly increase users trust in IoT. The WoT operating system will also enhance user's trust in higher scale in WoT, i.e. scalability of IoT. Such operating systems will also be of great interest of success and confidence for local as well as universal control of IoT and WoT. Integration of Open Source Architecture with IoT and WoT in terms of hardware, as well as the software will enhance users trust in these technologies. Open Source Development of hardware and software for IoT and WoT by multiple vendors and further certification of things used in IoT and WoT will also enhance user's trust in IoT as well as WoT.
5.7.2 Authorization
Authorization management in the proposed grid provides fine-grained access policy management. Constrained devices in IoT may be attacked physically or through Denial of Service (DOS) attack. Protection from physical attacks is not in the scope of this document, but it should be kept in mind by developers of authorization solutions. There are different authorization frameworks and models, which are shown in a comprehensive taxonomy presented in Figure 5.9.
Sensors implanted in the elderly patient's body, whom we will refer to as Alice, are connected to the Internet using wireless technology. These devices send alerts and the current readings/values along with Alice's identity and geolocation to the duty doctor available in the hospital. Alice's medical data contains very sensitive information and therefore good protection is needed against unauthorized access. A frequent, contradictory requirement is needed as the capability for emergency access. In the meantime, typically users are not trained for security, thus secure default settings are used with an easy-to-use interface. Moreover, smart devices have short battery life, so changing a battery frequently is unacceptable.

Figure 5.8 Authentication methods taxonomy.
In the case of emergency, such as if Alice patient suffers a cardiac arrest, the gateway at her home will automatically send alerts and the current readings/values along with identity and geolocation information to the duty doctor available in the hospital. This device uses some intermediate nearby device, such as a smart card, to transmit such an alarm (P1). Alice configures a list of people (such as a close relative and doctor) to be notified in case of emergency (P2) (P3). Moreover, the smart card stored Alice's heartbeat data, which can be accessed later by a medical specialist.

Figure 5.9 Authorization frameworks and models.
Alice may have some privacy concerns, so she does not want John to monitor her location when there is not an emergency (P4). Sensors should generate alert only when the pulse rate is very high or very low. Finally, Alice is comfortable with this latest technology and easily uses the device because she is not trained in device security. If Alice cannot understand the meaning of device settings, then she can assume that manufacturers (third party) have initialized the devices to secure settings (P5) (in case the user does not have enough knowledge about their attached device. Their security may be breached, or malicious activity may occur and give unambiguous data).
In this scenario, a remote authorization grid is very useful. In the case of preconfigured access rights, there is a need for authorization management in which fine-grained access privileges and policies are granted, according to the user and resource usage. After configuring the authorization management, device user's security can be managed using third-party authorization that allows multiple accesses and ensures data confidentiality and integrity. Access rights must be dynamically changed and for this it is necessary that smart devices must have semantic authorization, which means the context of authorization. For example, in the above scenario, Alice requests that John monitor her location only in the context of an emergency. A taxonomy of the frameworks and models used for privacy is shown in Figure 5.10
The insurance companies may not get Alice's medical records; rather they receive only the information for a certain period when the device is embedded and it has access to the medical condition. Moreover, the National Health Service (NHS) does not allow Alice's data to be published, unless anonymity is granted to that data they can use or publish. In IoT the storage privacy is one of the most important factors, where devices are embedded, and they have to communicate with each other. Storage data privacy management is one of the major issues in communication between embedded devices. The mechanism to send alert system must be preserved by applying some encryption schemas like Shamir's Secret Sharing, fine-grained access control, or by applying attributes.
Alice's embedded device data must be stored at a remote location under an authorized person. The embedded device has not enough capacity to store data, if more issues arise, such as processing speed, storage capacity, battery time, etc. In case Alice's information may be revealed to an unauthorized party there must be transparent disclosure regarding who can reveal information. Conclusively, from the start to the end, in communication between the pacemaker to hospital alerts, system privacy applies at each step.

Figure 5.10 Taxonomy of the frameworks and models used for privacy.
5.8 Conclusion
IoT is a growing area of research. However, it still faces several challenges related to the application of access control frameworks due to the heterogenous nature of the connected devices. As access control is critical, so least privileges must be assigned to assure that during maintenance, the maintainer cannot use all authorized rights, as happens in RBAC and ABAC. In traditional access control frameworks, a thorough revision and adaptation is needed. For this, a capability-based access system is being available openly for access capabilities and revocation services. In recent years, because of the ubiquitous nature of IoT networks and devices, the protection of smart services and resources is addressed by centralized architecture. In such an environment, back-end servers are responsible for authentication and authorization tasks. The use of traditional access control mechanism prevents end-to-end security. Consequently, central architecture cannot provide scalability for smart objects in IoT.
In the scenario we discussed, a remote authorization grid is very useful. In the case of preconfigured access rights there is a need for authorization management in which fine-grained access privileges and policies are granted according to the user and resource usage. After configuring the authorization management, device user's security can be managed using third-party authorization that allows multiple accesses and ensures data confidentiality and integrity. A mechanism to dynamically change access rights can be ensured by embedding smart devices to have a policy for semantic authorization. The device-to-device privacy must be ensured if cardiologist needs hearing device access to monitor the patient's overall health. Only the desired data should be provided to the cardiologist, with the agreement of the patient, Alice. Appropriately, to deliver privacy in IoT, we have discussed the privacy properties that affect privacy connections, categorized them into four classifications, and shown that complete privacy preserving would need attention for parts of these categories in diverse frameworks and designed for diverse use cases. A general IoT privacy scheme model needs to satisfy some of the suggested parameters that are based on privacy requirement objectives for complete IoT privacy. As part of the future work, we will implement the proposed privacy grid to achieve privacy in IoT and present a comparative study with the help of simulations and practical implementations.
References
- 1 Sicari, S., Rizzardi, A., Grieco, L.A., and Coen-Porisini, A. (2015). Security, privacy and trust in internet of things: the road ahead. Computer Networks 76: 146–164.
- 2 Westin, A.F. (1970). Privacy and freedom. Science and Society 34: 360–363.
- 3 Farooq, M.U., Waseem, M., Khairi, A., and Mazhar, S. (2015). A critical analysis on the security concerns of internet of things (IoT). International Journal of Computers and Applications 111 (7): 1–6.
- 4 Kumar, S.A., Vealey, T., and Srivastava, H. (2016). Security in Internet of Things: challenges, solutions and future directions. In: 2016 49th Hawaii International Conference on System Sciences (HICSS), 5772–5781. IEEE Computer Society.
- 5 Medaglia, C.C.M. and Serbanati, A. (2010). An Overview of Privacy and Security Issues in the Internet of Things. Springer.
- 6 Sun, J., Zhang, R., Zhang, J., and Zhang, Y. (2014). Touching: sightless two-factor authentication on multi-touch mobile devices. IEEE Conference on Communications and Network Security (CNS) 2014: 436–444.
- 7 Wang, D., He, D., Wang, P., and Chu, C.-H. (2015). Anonymous two-factor authentication in distributed systems: certain goals are beyond attainment. IEEE Transactions on Dependable and Secure Computing 12 (4): 428–442.
- 8 Li, C.-T. and Hwang, M.-S. (2010). An efficient biometrics-based remote user authentication scheme using smart cards. Journal of Network and Computer Applications 33 (1): 1–5.
- 9 Emerson, S., Choi, Y.-K., Hwang, D.-Y. et al. An OAuth-based authentication mechanism for IoT networks. In: 2015 International Conference on Information and Communication Technology Convergence (ICTC), vol. 2015, 1072–1074. IEEE.
- 10 U. Gupta, Application of multifactor authentication in Internet of Things domain, arXiv Prepr. arXiv1506.03753, 2015.
- 11 Rafidha Rehiman, K.A., Veni, S., Rehiman, K.A.R., and Veni, S. (2016). A secure authentication infrastructure for IoT enabled smart mobile devices – an initial prototype. Indian Journal of Science and Technology 9 (9): 520–523.
- 12 Henze, M., Hermerschmidt, L., Kerpen, D. et al. (2016). A comprehensive approach to privacy in the cloud-based internet of things. Future Generation Computer Systems 56: 701–718.
- 13 Roman, R., Zhou, J., and Lopez, X. (2013). On the features and challenges of security and privacy in distributed internet of things. Computer Networks 57 (10): 2266–2279.
- 14 D. J. Wu, A. Taly, A. Shankar, and D. Boneh, Privacy, discovery, and authentication for the Internet of Things,” arXiv Prepr. arXiv1604.06959, 2016.
- 15 Gross, H., Hölbl, M., Slamanig, D. et al. (2015). Privacy-aware authentication in the internet of things. In: Cryptology and Network Security, 32–39.
- 16 Feng, H. and Fu, W. (2010). Study of recent development about privacy and security of the internet of things. International Journal of Computer Applications 2 (7): 91–95.
- 17 Jeong, H.-D.J., Lee, W., Lim, J., and Hyun, W. (2015). Utilizing a Bluetooth remote lock system for a smartphone. Pervasive and Mobile Computing 24: 150–165.
- 18 Crossman, M.A. and Liu, H. (2015). Study of authentication with IoT testbed. In: 2015 IEEE International Symposium on Technologies for Homeland Security (HST), 1–7. IEEE.
- 19 Mao, Y., Li, J., Chen, M.-R.R. et al. (2016). Fully secure fuzzy identity-based encryption for secure IoT communications. Computer Standards & Interfaces 44 (4): 117–121.
- 20 Ilyas, M., Ali, A., and Kueng, J. (2010). WebSeA: a secure framework for multi-site knowledge representation in software engineering. In: International Conference on Bio-Inspired Models of Network, Information, and Computing Systems, Springer, 682–686.
- 21 Bamasag, O.O. and Youcef-Toumi, K. (2015). Towards continuous authentication in internet of things based on secret sharing scheme. In: Proceedings of the WESS'15: Workshop on Embedded Systems Security, ACM, 1.
- 22 Markmann, T., Schmidt, T.C., and Wählisch, M. (2015). Federated end-to-end authentication for the constrained internet of things using IBC and ECC. ACM SIGCOMM Computer Communication Review 45 (4): 603–604.
- 23 Bargh, M.S., Hulsebosch, R.J., Eertink, E.H. et al. (2004). Fast authentication methods for handovers between IEEE 802.11 wireless LANs. In: Proceedings of the Second ACM International Workshop on Wireless Mobile Applications and Services on WLAN Hotspots, WMASH 2004, 51–60. ACM.
- 24 Schneier, B. (2005). Two-factor authentication: too little, too late. Communications of the ACM 48 (4): 136, ACM.
- 25 Farooq, M.O. and Kunz, T. (2011). Operating systems for wireless sensor networks: a survey. Sensors (Basel) 11 (6): 5900–5930.
- 26 Sabzevar, A.P. and Stavrou, A. (2008). Universal multi-factor authentication using graphical passwords. In: IEEE International Conference on Signal Image Technology and Internet-based Systems, 2008. SITIS'08, 625–632.
- 27 Sarma, A.C. and Girão, J. (2009). Identities in the future Internet of Things. Wireless Personal Communications 49 (3): 353–363.
- 28 Aloul, F.A., Zahidi, S., and El-Hajj, W. (2009). Two-factor authentication using mobile phones. IEEE/ACS International Conference on Computer Systems and Applications: 641–644.
- 29 Aviv, A.J., Gibson, K., Mossop, E. et al. (2010). Smudge attacks on smartphone touch screens. USENIX Conference on Offensive Technologies 10: 1–7.
- 30 Wimberly, H. and Liebrock, L.M. (2011). Using fingerprint authentication to reduce system security: an empirical study. In: 2011 IEEE Symposium on Security and Privacy, 32–46.
- 31 Baccelli, E., Hahm, O., Gunes, M. et al. (2013). RIOT OS: towards an OS for the Internet of Things. 2013 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS): 79–80.
- 32 Huang, X., Xiang, Y., Bertino, E. et al. (2014). Robust multi-factor authentication for fragile communications. IEEE Transactions on Dependable and Secure Computing 11 (6): 568–581.
- 33 Pham, T., Ma, W., Tran, D. et al. (2014). Multi-factor EEG-based user authentication. In: 2014 International Joint Conference on Neural Networks (IJCNN), 4029–4034. IEEE.
- 34 D. He, N. Kumar, J.-H. Lee, and R. S. Sherratt, Enhanced three-factor security protocol for consumer USB mass storage devices, IEEE Transactions on Consumer Electronics, Vol. 60, No. 1, pp. 30–37, IEEE, 2014.
- 35 Edwards, C. (2014). Ending identity theft and cyber crime. Biometric Technology Today 2014 (2): 9–11.
- 36 M. Turkanović, B. B. Brumen, and M. Hölbl, A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the internet of things notion, Ad Hoc Networks, Vol. 20, pp. 96–112, Elsevier, 2014.
- 37 Munch-Ellingsen, A., Karlsen, R., Andersen, A., and Akselsen, S. (2015). Two-factor authentication for android host card emulated contactless cards. In: 2015 First Conference on Mobile and Secure Services (MOBISECSERV), 1–6.
- 38 Jacobsson, A., Boldt, M., and Carlsson, B. (2015). A risk analysis of a smart home automation system. Future Generation Computer Systems 56: 719–733.
- 39 van der Haar, D. (2015). Canvis: a cardiac and neurological-based verification system that uses wearable sensors. In: 2015 Third International Conference on Digital Information, Networking, and Wireless Communications (DINWC), 99–104.
- 40 T. Borgohain, A. Borgohain, U. Kumar, and S. Sanyal, Authentication systems in Internet of Things,” arXiv Prepr. arXiv1502.00870, 2015.
- 41 Zhai, J., Cao, T., Chen, X., and Huang, S. (2015). Security on dynamic ID-based authentication schemes. International Journal of Security and Its Applications 9 (1): 387–396.
- 42 Mahmoud, R., Yousuf, T., Aloul, F., and Zualkernan, I. (2015). Internet of Things (IoT) security: current status, challenges and prospective measures. In: 2015 10th International Conference for Internet Technology and Secured Transactions (ICITST), 336–341. IEEE.
- 43 Devi, G.U., Balan, E.V., Priyan, M.K., and Gokulnath, C. (2015). Mutual authentication scheme for IoT application. Indian Journal of Science and Technology 8 (26): 15–19.
- 44 Ruan, O., Kumar, N., He, D., and Lee, J.-H.H. (2015). Efficient provably secure password-based explicit authenticated key agreement. Pervasive and Mobile Computing 24: 50–60.
- 45 Rose, K., Eldridge, S., and Chapin, L. (2015). The Internet of Things: an overview. Internet Society 80: 1–50.
- 46 Kang, D., Jung, J., Mun, J. et al. (2016). Efficient and robust user authentication scheme that achieve user anonymity with a Markov chain. Security Communication Networks 9: 1032–1035.
- 47 Díaz, M. et al. (2016). State-of-the-art, challenges, and open issues in the integration of internet of things and cloud computing. Journal of Network and Computer Applications 67 (1): 99–117.
- 48 Arno, A., Toyoda, K., and Sasase, I. (2015). Accelerometer assisted authentication scheme for smart bicycle lock. In: 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), 520–523. IEEE.
- 49 L. Barreto, A. Celesti, M. Villari et al., An authentication model for IoT clouds, in Proceedings of the 2015 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining 2015, IEEE, 2015, pp. 1032–1035.
- 50 Ferraiolo, D.F., Hu, V.C., and Kuhn, D.R. (2007). Assessment of access control systems, Interagency Report 7316. National Institute of Standards and Technology.
- 51 Keoh, S.L., Kumar, S.S., and Tschofenig, H. (2014). Securing the Internet of Things: a standardization perspective. IEEE Internet of Things Journal 1 (3): 265–275.
- 52 Seitz, L., Selander, G., and Gehrmann, C. (2013). Authorization framework for the Internet-of-Things. In: 2013 IEEE 14th International Symposium and Workshops on a World of Wireless, Mobile and Multimedia Networks (WoWMoM), 1–6. IEEE.
- 53 Alam, S., Chowdhury, M.M.R., and Noll, J. (2011). Interoperability of security-enabled Internet of Things. Wireless Personal Communications 61 (3): 567–586.
- 54 Ho, G., Leung, D., Mishra, P. et al. (2016). Smart locks: Lessons for securing commodity Internet of Things, Devices. In: Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security, Xi'an, China, 461–472.
- 55 Su, J., Cao, D., Zhao, B. et al. (2014). ePASS: an expressive attribute-based signature scheme with privacy and an unforgeability guarantee for the Internet of Things. Future Generation Computer Systems 33: 11–18.
- 56 Ye, N., Zhu, Y., Wang, R.-C. et al. (2014). An efficient authentication and access control scheme for perception layer of Internet of Things. Applied Mathematics & Information Sciences 8 (4): 1617.
- 57 Ning, H., Liu, H., and Yang, L.T. (2015). Aggregated-proof-based hierarchical authentication scheme for the internet of things. IEEE Transactions on Parallel and Distributed Systems 26 (3): 657–667.
- 58 P. Misra, Y. Simmhan, and J. Warrior, Towards a practical architecture for the next generation Internet of Things, arXiv Prepr. arXiv1502.00797, 2015.
- 59 Adda, M., Abdelaziz, J., Mcheick, H., and Saad, R. (2015). Toward an access control model for IOTCollab. Procedia Computer Science 52: 428–435.
- 60 Hummen, R., Shafagh, H., Raza, S. et al. (2014). Delegation-based authentication and authorization for the IP-based internet of things. In: 2014 Eleventh Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), 284–292. IEEE.
- 61 Chen, D., Chang, G., Sun, D. et al. (2012). Modeling access control for cyber-physical systems using reputation. Computers and Electrical Engineering 38 (5): 1088–1101.
- 62 Thomas, R.K. (1997). Team-based access control (TMAC): a primitive for applying role-based access controls in collaborative environments. In: Proceedings of the Second ACM Workshop on Role-Based Access Control, 13–19. ACM.
- 63 Wang, X., Zhang, J., Schooler, E.M., and Ion, M. (2014). Performance evaluation of attribute-based encryption: toward data privacy in the IoT. In: 2014 IEEE International Conference on Communications (ICC), 725–730. IEEE.
- 64 Bao, F. and Chen, I.-R. (2012). Dynamic trust management for Internet of Things applications. In: Proceedings of the 2012 International Workshop on Self-Aware Internet of Things, 1–6. IEEE.
- 65 Gusmeroli, S., Piccione, S., and Rotondi, D. (2013). A capability-based security approach to manage access control in the internet of things. Mathematical and Computer Modelling 58 (5): 1189–1205.
- 66 Lee, C., Guo, Y., and Yin, L. (2013). A location temporal-based access control model for IoTs. AASRI Procedia 5: 15–20.
- 67 Mahalle, P.N., Anggorojati, B., Prasad, N.R., and Prasad, R. (2013). Identity authentication and capability-based access control (iacac) for the internet of things. Journal of Cyber Security and Mobility 1 (4): 309–348.
- 68 Anggorojati, B., Mahalle, P.N., Prasad, N.R., and Prasad, R. (2012). Capability-based access control delegation model on the federated IoT network. In: 2012 15th International Symposium on Wireless Personal Multimedia Communications (WPMC), 604–608. IEEE.
- 69 Skarmeta, A.F., Hernandez-Ramos, J.L., and Moreno, M. (2014). A decentralized approach for security and privacy challenges in the Internet of Things. In: 2014 IEEE World Forum on Internet of Things (WF-IoT), 67–72. IEEE.
- 70 Hernández-Ramos, J.L., Jara, A.J., Marın, L., and Skarmeta, A.F. (2013). Distributed capability-based access control for the Internet of Things. Journal of Internet Services and Information Security 3 (3/4): 1–16.
- 71 Bernabe, J.B., Ramos, J.L.H., and Gomez, A.F.S. (2015). TACIoT: multidimensional trust-aware access control system for the Internet of Things. Soft Computing 20: 1–17.
- 72 Hernndez-Ramos, J.L. et al. (2015). Preserving smart objects privacy through anonymous and accountable access control for a M2M-enabled internet of things. Sensors (Basel, Switzerland) 15 (7): 15611–15639.
- 73 Li, F., Han, Y., and Jin, C. (2016). Practical access control for sensor networks in the context of the Internet of Things. Computer Communications 89–90: 154–164.
- 74 Ross, R. and Oren, J.C. (2014). Systems security engineering. NIST Special Publication 800: 160.
- 75 Weinberg, B.D., Milne, G.R., Andonova, Y.G., and Hajjat, F.M. (2015). Internet of Things: convenience vs privacy and secrecy. Business Horizons 58 (6): 615–624.
- 76 Schiller, J.I. (2002). Strong Security Requirements for Internet Engineering Task Force Standard Protocols, vol. 1, 1–8. ACM.
- 77 Cheng, Y., Naslund, M., Selander, G., and Fogelström, E. (2012). Privacy in machine-to-machine communications a state-of-the-art survey. In: 2012 IEEE Internationa. Conference on Communicaton Systems ICCS 2012, 75–79. IEEE.
- 78 Samani, A., Ghenniwa, H.H., and Wahaishi, A. (2015). Privacy in Internet of Things: a model and protection framework. Procedia Computer Science 52 (1): 606–613.
- 79 Lai, C., Li, H., Liang, X. et al. (2014). CPAL: a conditional privacy-preserving authentication with access linkability for roaming service. IEEE Internet of Things Journal 1 (1): 46–57.
- 80 Ukil, A., Bandyopadhyay, S., and Pal, A. (2014). IoT-privacy: to be private or not to be private. In: Proceedings-IEEE INFOCOM, 123–124. IEEE.
- 81 Ahmad, W., Sunshine, J., and Wynne, A. (2015). Enforcing fine-grained security and privacy policies in an ecosystem within an ecosystem. In: Proceedings of the 3rd International Workshop on Mobile Development Lifecycle, 28–34. ACM.
- 82 Wang, C. and Luo, J. (2013). An efficient key-policy attribute-based encryption scheme with constant ciphertext length. Mathematical Problems in Engineering 2013, 810969-810976. https://doi.org/10.1155/2013/810969.
- 83 Alcaide, A., Palomar, E., Montero-Castillo, J., and Ribagorda, A. (2013). Anonymous authentication for privacy-preserving IoT target-driven applications. Computers & Security 37: 111–123.
- 84 Kim, S., Sung, M.K., and Chung, Y.D. (2014). A framework to preserve the privacy of electronic health data streams. Journal of Biomedical Informatics 50: 95–106.
- 85 Zhang, R., Zhang, Y., and Ren, K. (2012). Distributed privacy-preserving access control in sensor networks. IEEE Transactions on Parallel and Distributed Systems 23 (8): 1427–1438.
- 86 Rottondi, C., Verticale, G., and Krauß, C. (2013). Distributed privacy-preserving aggregation of metering data in smart grids. IEEE Journal on Selected Areas in Communications 31 (7): 1342–1354.
- 87 Zakerzadeh, H. and Osborn, S.L. (2011). FANST: fast anonymizing algorithm for numerical streaming DaTaA. In: Data Privacy Management and Autonomous Spontaneous Security, 36–50. Springer.
- 88 Berners-Lee, T., Hendler, J., Lassila, O. et al. (2001). The semantic web. Scientific American 284 (5): 34–43.
- 89 H. A. Khattak, Internet of Things in the future Internet, 1st Workshop on the State of the Art and Challenges of Research Efforts, Politecnico di Bari, 2014.
- 90 Horrocks, I., Patel-Schneider, P.F., Boley, H. et al. (2004). SWRL: a semantic web rule language combining OWL and RuleML. W3C Member Submission: 1–20.
- 91 Boley, H., Tabet, S., and Wagner, G. (2001). Design rationale of RuleML: a markup language for semantic web rules. In: First International Conference on Semantic Web Working Symposium, vol. 1, 381–401. CEUR-WS.
- 92 Aghaei, S., Nematbakhsh, M.A., and Farsani, H.K. (2012). Evolution of the world wide web: from WEB 1.0 to WEB 4.0. International Journal of Web & Semantic Technology 3 (1): 1.
- 93 Nyanchama, M. and Osborn, S. (1995). Modeling mandatory access control in role-based security systems. Database Security 51: 129–144.
- 94 Ferraiolo, D., Cugini, J., and Kuhn, D.R. (1995). Role-based access control (RBAC): features and motivations. In: Proceedings of the 11th Annual Computer Security Application Conference, 241–248. NIST.
- 95 Khattak, H.A., Ruta, M., Eugenio, E., and Sciascio, D. (2014). CoAP-based healthcare sensor networks: a survey. In: Proceedings of 2014 11th International Bhurban Conference on Applied Sciences and Technology, IBCAST 2014, 499–503. IEEE.
- 96 Darshak Thakore, C. (2016). IoT Security in the context of Semantic Interoperability. In: Workshop on Internet of Things (IoT) Semantic Interoperability (IOTSI), Santa Claria, CA, March, 17–18.
- 97 Alamri, A., Bertok, P., Thom, J.A., and Fahad, A. (2016). The mediator authorization-security model for heterogeneous semantic knowledge bases. Future Generation Computer Systems 55: 227–237.
- 98 Nematzadeh, A. and Pournajaf, L. (2008). Privacy concerns of semantic web. In: Fifth International Conference on Information Technology: New Generations, 2008. ITNG 2008, 1272–1273. Elsevier.
