CHAPTER 4
Understanding Intrusion-Detection and Reporting Systems
While preventing unauthorized access is the first line of defense in physical security, layers of additional security measures are crucial to preventing intrusions from escalating into serious events. A closely related second tier of defense is intrusion detection, which enables potential intruders to be detected and removed before they can cause problems. This level of security involves detection devices that are monitored or that can create an alarm. In this chapter, you’ll learn to:
- Describe components of a typical, physical intrusion-detection and reporting system
- Explain the purpose for creating physical security zones and common techniques for defining them
- Identify common sensor types employed in a physical intrusion-detection system.
Intrusion-Detection and Reporting Systems
The components of a basic commercial security system, as depicted in Figure 4.1, come together to provide a functional intrusion-detection and reporting system. This system includes an intelligent control panel connected by wires (or radio signals) to sensors at various locations throughout the facility.

FIGURE 4.1 Basic Intrusion-Detection and Reporting System
The control panel includes the electronic components and central processor, which monitors and controls the entire system. The processor accepts input information from the various sensors attached to it. In a basic security system, these inputs can be divided into three distinct types: perimeter, interior, and fire.
Perimeter area inputs to the control panel typically include sensors at every perimeter opening including doors, windows, garage doors and windows, and doors to crawl spaces. Additional perimeter protection may include using sound, vibration, and motion-detector sensors to guard against entry through broken windows.
Some interior areas may also be protected with various types of sensors, such as motion detectors and interior door sensors. Most security systems also include inputs capable of handling adequate smoke and fire sensors.
When the controller receives an active input signal from one of its input sensors, it evaluates the conditions presented according to its programming (and the type of emergency response required), and if necessary, sends the appropriate output signals to annunciators (sirens or bells). It may also communicate with designated security contacts (security supervisors, monitoring services, or law enforcement/fire agencies) as directed by its programming.
Commercial security systems may use any of several notification methods to notify designated security personnel when an alarm condition is triggered. Some alarm systems use a telephone dialer to alert the remote security contacts that an alarm condition exists. These systems are designed to react when no one is present by placing the call over a standard telephone line or cell phone. Special digital codes are used to inform the security contacts as to what type of condition caused the alarm.
It is also possible to have a prepared text-messaging system, such as SMS, relayed by a cell phone to the designated security contacts. Another option is IP-based notification, which is used to notify the monitoring station via an IP network, such as the Internet, concerning an alarm condition.
Most security systems typically employ some type of keypad to provide the control interface for supervisors to arm and disarm the system using a programmed access code. The keypad may be designed to provide some level of visual and audible output signals to help monitor the status of the system.
Finally, most security systems include some type of emergency backup power (a backup battery or uninterruptable power supply) to provide emergency power to the security system when commercial power outages occur.
The choices for access-control and management system components and subsystems are extensive. The following sections of this chapter will explain the various subsystems typically found in the intrusion-detection and reporting portion of a typical infrastructure security system.
Security Controllers
The center of any intelligent security system is the controller. The security controller, shown in Figure 4.2, is typically installed in an enclosure that contains the security controller board, all of the electronic components, wire termination points, backup battery packs, and telephone termination wiring.

FIGURE 4.2 Control Box with Panel and Battery
A given security controller model will be designed to handle a specific number of programmable zones. A zone can be a single point of protection such as a motion detector, or multiple points can be combined into a single zone. For example, two hallway motion detectors could be connected to form a zone, or a stairway motion detector could be combined with the hallway sensors to form a single zone.
The security controller is the command center and distribution point of the intrusion-detection and reporting portion of the security system to which all input and output devices are connected. Each sensor receives power and is managed from the security controller.
The controller must have enough capacity and functionality to connect to and manage all the security devices that will be part of the security system, in addition to providing remote access capability for remote monitoring and control.
The controller’s enclosure should be mounted out of plain view and near a 120-volt AC outlet, where a plug-in transformer can supply low-voltage power to the total system.
Security Zones
As mentioned earlier, security controllers possess a fixed number of detection circuits that can be used to create physical security zones. For instance, a typical, commercial security controller may possess as few as eight zones and up to 250 zones or more. Typically, one of these inputs is dedicated to the fire detection system. Figure 4.3 shows a typical eight-zone security controller connection scheme.

FIGURE 4.3 Security Panel Zone Inputs
Suppose that the facility in which you are installing the security system has fourteen windows, two personnel entrance doors, and a roll-up receiving door for the warehouse. In addition, it has two major hallways to monitor and an integrated fire-detection system.
How should you physically install and configure the controller so that it provides full protection for the facility? The answer is to logically group related sensors together to create a security zone. This is accomplished by connecting all of the related sensor switches (all sensors appear as switches to the security controller) together in a serial format as illustrated in Figure 4.4.

FIGURE 4.4 Creating a Physical Zone
The controller monitors the amount of electrical current flowing between the zone’s two connection points (referred to as a current loop). The loop requires that a resistor be placed within the loop to regulate the current flow to the correct level for the controller being used (different controller models typically require different resistance levels).
If one of the sensors is activated, its switch moves into an open condition and current flow through the loop stops. The controller detects the lack of current flow and processes the input according to its configuration programming.
The fact that a certain level of current must be flowing helps to make tampering with the loop more difficult. If the system used normally opens switches that close when activated, the system could be circumvented by simply cutting a wire in the loop; no signal would ever be presented to the controller.
For the sample installation presented earlier, it might be logical to wire all of the west-side window sensors into one input that could be reported as the West Side Windows. Likewise, the two personnel entry doors can be configured together because they will require special settings to allow exit and entry times for setting and disarming the system when leaving or entering the structure. Conversely, the other door may be connected into a different door zone or incorporated into one of the window zones since it has no timing requirement.
Zoning also enables the system to instantly sound an alarm for intrusion detection in a specific area, while other sensor alerts in a specific zone (such as the main front door) may require a short delay before sounding the alarm. This enables security personnel to arm the system by entering a secret code on a keypad when exiting the facility (exit delay).
It also allows them to enter a protected area when arriving at the facility and disarm the system through the entry area keypad within a specified entry-delay interval (usually 30 to 45 seconds). This feature allows keypads to be installed inside the facility near the exit door to avoid vandalism and tampering with keypads from the outside area.
Interior motion sensors that guard the hallways may be integrated into a window or a door zone. However, they are more likely to be configured separate from the exterior sensors so that they can be disabled at night when people may need to move around during the night but want the perimeter to be protected from outside intruders. Figure 4.5 describes a possible zoning solution for this example.

FIGURE 4.5 Zoning Concepts
The use of zoning also enables security personnel to arm only portions of the system, such as the perimeter doors and windows, while bypassing interior motion detectors in a specific zone. A bypass mode setting is normally accomplished by entering a predetermined numerical code through the keypad. When personnel leave the facility, all zones including the interior detectors can be armed as required.
A zoned security-system layout can also be used by an external monitoring service to know which sensor in a designated zone is causing an alarm. If a sensor is reported as just Sensor 3, Zone 5, this could mean that the event occurred just about anywhere. If the sensor was reported as Sensor 3, Zone 5 perimeter, this would inform the operator that the violated area is on the outside of the premises.
Zones also provide ease of troubleshooting. For example, if a sensor in the Zone 3 perimeter is reporting a problem, there is no need to troubleshoot sensors that are located in the interior of the system.
Sensors
Sensors are a class of input devices that convert physical activity into a signal that can be presented to the security controller. They are available in a variety of configurations including magnetic switches for doors and windows, acoustic detectors, vibration detectors, motion detectors, and glass-break detectors. Sensors protect the perimeter, selected outside areas, and the open spaces inside the facility.
As mentioned earlier, perimeter devices primarily protect doors and windows. The most common perimeter sensors are magnetic door switches, window vibration, and window acoustical detectors to detect breaking-glass sounds.
Open-space-protection sensors called motion detectors cover interior rooms and hallways. Outside motion detectors activate security lights when movement is detected. Indoor motion detectors can detect an intruder who has been able to defeat a perimeter device. Exterior motion detectors and motion-activated security lights are also used. The following paragraphs describe the sensors included in basic security and surveillance systems.
Magnetic Contact Switches
Magnetic contact switches basically consist of a two-part magnetic switch. One piece of the sensor is a magnet, while the other side is a switching mechanism, called a reed switch, that is sensitive to a magnetic field. The switch portion is mounted on the fixed structure (frame) of the barrier, as shown in Figure 4.6. Wires from the switch are routed to the security system’s control panel.

FIGURE 4.6 Sensor Mounting
The magnet portion of the sensor is mounted on the movable barrier so that it is in close proximity to the switch when the barrier is closed. This also keeps the switch closed. Opening the barrier moves the magnet away from the switch and opens the switch, which is sensed by the central control panel, and activates an alarm.
This simple magnetic-switch sensor can be used to protect doors and windows or any other moving barrier. It alerts security managers when someone attempts to gain entry through a passageway through illegal or unauthorized means. Its magnet and reed-switch mechanism detects any intrusion and signals an alarm.
This type of sensor can be used to indicate the open/closed condition of a movable barrier, but it cannot determine whether the barrier’s locking mechanism is locked or unlocked. As mentioned earlier, some types of electrically operated door locks are equipped with sensors for determining whether the locking mechanism is locked or unlocked.
Even though up to 70 varieties of barrier sensors are available, a sensor alone cannot offer true control other than detection and warning. Its signal, however, can be used by other access-control system components to provide automated responses.
Glass-Breakage Sensors
As mentioned earlier, a perimeter security system may include a glass-breakage detection system. Magnetic switches do not protect against an intruder entering through a broken window. Two types of glass-breakage detection systems are available. The vibration type is mounted on the glass or on a nearby wall. Acoustical or sound discriminators sense the sound of breaking glass.
The unit may be tuned to react only to the specific frequency of glass breaking, typically 4 to 6 kHz, or to any loud noise. Some sensor manufacturers have combined vibration and sound detectors into one unit that will not activate unless both are detected. These units may be used where the normal conditions would cause a single technology detector to generate false alarms.
Vibration detectors are mounted on the glass, and the acoustical window sensors are normally mounted on an adjacent wall, as illustrated in Figure 4.7.

FIGURE 4.7 Glass-Breakage Sensors
Motion Detectors
Motion detectors work by detecting the changes in the infrared energy in an area. Because these devices do not emit any energy, they are called passive infrared (PIR) detectors.
PIR detectors use a lens mechanism in the sensor housing to detect any change in infrared energy across the horizontal sectors covered by the sensor. This type of detector is insensitive to stationary objects but reacts to rapid changes that occur laterally across the field of view. PIR detectors are the most common and economical type of motion detectors.
Motion detectors should be installed in open areas that cannot be protected by window or door sensors. An example of a PIR motion detector for interior use is shown in Figure 4.8.

FIGURE 4.8 A PIR Motion Detector
Motion Detector Locations
Motion detectors are normally mounted in the corner of a room. This allows the detector to cover a 90-degree field, as illustrated in Figure 4.9. Motion detectors are sensitive to movement across the sensor’s field of view.

FIGURE 4.9 PIR Field of View
Exterior lighting is often used to illuminate dark areas or areas to be protected using motion-detection sensors that activate security lighting to deter an intruder. Outside lighting is used solely as a deterrent and safety feature, so it is not normally connected to the security controller.
Dark areas surrounding the facility with trees or shrubs need to be illuminated with security lighting systems. Security lighting systems used during dark hours prevent intruders from entering the area surrounding a facility and attempting entry under the cover of darkness. Motion-detector-activated lights are also popular for exterior lighting.
Vehicle-Detection Sensors
Several methods are used to detect the presence of an automobile entering an area near a facility. The most common type of sensor used for this purpose is a motion detector placed above the entrance to the garage. Pressure sensors can also be employed to detect a vehicle on a driveway or garage area.
Photoelectric Beam Devices A photoelectric sensor is an optical control that detects a visible or invisible beam of light and responds to a change in the received light intensity. Photoelectric beam devices use this feature by having a narrow beam of light aimed through an area of interest such as a parking lot gate, as shown in Figure 4.10. When the light beam is interrupted, the photoelectric device is used to sound an alarm, or in the case of garage door safety system, to stop or reverse an automatic garage door’s lifter motor.

FIGURE 4.10 Photoelectric Beam System
Microwave Beam Devices This device emits microwaves from a transmitter and detects microwaves at a receiver, either through reflection or reduction in beam intensity. The transmitter and receiver are usually combined inside a single housing for indoor applications and separate housings for outdoor applications. By generating energy in the microwave region of the electromagnetic spectrum, the detector operates as an active device that responds to:
- A Doppler shift frequency change. These devices are based on the Doppler Effect phenomenon, which observes frequency changes in energy waves (in this case, microwaves) in motion relative to a listener or receiver. These detectors emit microwaves of a specific frequency into a given environment and then analyze the frequencies of any waves reflected to it. Changes from its normal frequency reception cause the sensor to signal an alarm condition.
- A frequency phase shift. These devices also rely on changes in reflected energy waves caused by motion. Like the Doppler sensors, these sensors emit specific microwave frequencies into an area and measure phase shift of reflected waves, which are directly proportional to the velocity of the moving object.
- A motion causing reduction in received energy. These devices respond to changes in the level of energy between a transmitter and a receiver caused by some or all of the transmitted energy wave being blocked by an obstacle moving into its path.
Pressure Sensors Pressure mats are a type of sensor that can be placed under rugs in hallways or on stair treads. They react and alarm due to pressure from footsteps activating the alarm. Pressure sensors typically use normally open switch contacts. When pressure is applied to the pressure mat, the switch closes, which alerts the control panel that the pressure switch has been activated.
Keypads
Most intrusion-detection and reporting systems employ a keypad device for programming, controlling, and operating various access-control and management devices.
Keypads are input devices that are typically equipped with a set of numerical pushbuttons that are similar to a telephone touchtone keypad, as illustrated in Figure 4.11. Security personnel typically use keypads to initiate commands for control options such as arming and disarming the system or bypassing a zone.

FIGURE 4.11 Controller Keypad
Keypads can be located in any area of a facility that is convenient for security personnel to operate external gates and doors. However, many new security systems typically include software that runs on a tablet computer or a smart phone app to perform these functions from anywhere.
Key Fobs and Panic Buttons
A key fob is a wireless keychain device similar to the type used to lock, unlock, and alarm a vehicle. Convenient and easy-to-use remote-entry key fobs enable security personnel to arm and disarm a security system with a push of a button when outside the facility. The key fob often features a panic button function that allows the user to contact help in case of emergency. An example of a key fob is shown in Figure 4.12.
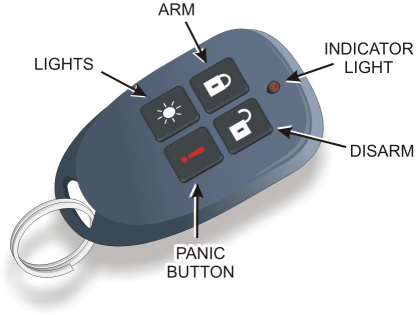
FIGURE 4.12 Security Key Fob
Panic buttons are devices that allow immediate triggering of an alarm system when facing an emergency situation such as the discovery of an intruder. As indicated in the previous paragraph, panic buttons are often integrated with a key fob but may also be mounted permanently at key locations inside the facility.
Fire-Detection Sensors
Many intrusion-detection and reporting systems include a fire-detection and alarm function as an integral part of the system. However, for larger or more complex security systems, standalone fire-detection and reporting systems may be used.
Two common types of fire-detection sensors are available: heat sensors and smoke detectors. They operate by detecting heat rise or the presence of smoke particles in the facility.
Heat sensors operate using a different technology than smoke detectors. The basic design features of each type are summarized in the following paragraphs. Heat sensors detect a rapid rise in temperature. They also set off an alarm when a fixed temperature is reached. On the other hand, smoke detectors, such as the one shown in Figure 4.13, do not react to heat but use one of two common sensor designs to detect smoke.

FIGURE 4.13 A Typical Smoke Detector
Ionization detectors form an electrical path inside a small chamber with a very small amount of radioactive material. When smoke enters the chamber, the particles attach themselves to the ions and change the electrical current.
Photoelectric detectors work by using a photoelectric cell and a light source. Normally, the light does not reach the photoelectric cell; but when smoke is present, the light is dispersed, and the detector triggers an alarm signal.
The main difference between the two detector types is that photoelectric types are more sensitive to large particles and ionization types are more sensitive to small particles.
Carbon Dioxide and Carbon Monoxide Detectors
Carbon dioxide (CO2), a natural byproduct of normal respiration, is different from the toxic carbon monoxide (CO) gas—and much less dangerous. Outdoor air usually contains about 400 ppm (parts per million) of carbon dioxide, while carbon monoxide levels should normally be less than 0.2 ppm.
Although CO is a colorless and odorless compound produced by incomplete combustion, it is lethal at high levels. When dangerous levels of CO are detected, the detector sounds an alarm, giving people in the area an opportunity to safely leave the residence—or to apply immediate ventilation.
Carbon monoxide is generated through the incomplete burning of natural gas, kerosene, fuel oil, coal, or gasoline, and not by appliances that use only electricity. If the furnace, water heater, space heater, stove, or oven does not burn gas or fuel, it will not generate carbon monoxide. Accurate carbon monoxide data require that suspect appliances be operating before any readings are taken.
When a CO alarm activates, personnel need to call emergency services, the fire department, or 911. They must immediately move to a source of fresh air, either outdoors or by an open door or window. A head check should be taken to ensure that all personnel are accounted for. No one should return into the facility or move away from the fresh air source until the emergency services arrive and give the all clear.
Output Devices
Physical intrusion-detection systems typically include three basic types of output devices: visual notification, audible annunciators, and remote messaging. The visual and audible annunciators provide a local and general call for attention to a predefined alarm condition, while the remote messaging element is employed to notify specific personnel or organizations that an alarm condition exists. The following sections describe the various output signals and devices employed in a basic security system.
Sirens
The control panel provides the voltage for driving the external electronic siren or strobe light. The controller activates these devices when an alarm condition exists. Various types of audible annunciators (sirens, horns, buzzers, klaxons, and bells) are used to attract attention when an alarm condition is activated.
These different devices produce different levels of volume for use in various locations. Audible alarm sounders are used not only to attract the attention of others outside the facility or away from the area of the intrusion, but also to create a sufficiently high level of sound to discourage an intruder. Commercial security systems typically employ solid-state electronic sirens like the one shown in Figure 4.14. These sirens provide a higher level of sound output as well as a variety of tones and pitches.

FIGURE 4.14 Electronic Siren
Interior sounders installed in concealed areas within the facility are designed to operate at maximum sound levels to frighten an intruder into making a fast exit. This is because the sound masks any outside approaching police siren. Interior sirens are available from several vendors that operate at sound levels in the 110 to 120 dB range, which is near the threshold of pain.
Strobe Lights
Many security system installations include at least one strobe light to provide a visual indicator. These lights are typically mounted on the outside of the facility to attract attention of people in the vicinity of the intrusion and to discourage would-be intruders. Security strobe lights operate from various DC voltage levels provided by the security controller panel.
Security strobe lights, like the one depicted in Figure 4.15, produce light output levels specified in either foot-candles, or candelas, of light. A foot-candle is a measure of luminance (or light intensity) used by the lighting industry. Likewise, one candela is equal to foot-candles multiplied by distance squared:
FIGURE 4.15 Strobe Light
Security strobe lights are available in a number of different colors including red, blue, amber, and clear.
Remote Notification Systems
While strobe lights and sirens call general attention to alarm conditions in a localized environment, it is often necessary to notify specific people (such as a security specialist) or organizations (such as third-party security companies, fire departments, or police services) to respond to different types of alarm conditions.
The most common remote notification systems involve the use of a telephone line by the security-system control panel to automatically call a remote monitoring facility or key personnel when an alarm condition exists. When the security controller receives an active input signal from one of its zones, it activates the telephone dialer unit and causes a digital data message to be transmitted to a predetermined recipient. The message recipient can also use remote access to check on the status of the security system when away from the facility.
Some intrusion-detection and reporting systems employ a separate telephone dialer like the one depicted in Figure 4.16, or a built-in dialer. However, a growing number of systems utilize built-in cellular communications systems. Such systems provide additional dependability in that they can function even if the physical telephone lines are damaged.

FIGURE 4.16 Automatic Voice/Pager Dialer Console
Third-Party Alarm-Monitoring Services
Depending on the nature of the organization, the intrusion-detection and reporting system may be totally based on employees of the organization. However, in many organizations, the security systems are supported by professional third-party alarm-monitoring companies.
These companies provide 24-hour/7-days-per-week monitoring services for a monthly fee. When they receive an alarm notification, they perform a response action based on their contractual agreement with the subscriber (client) company.
The sequencing of the response typically corresponds to the nature of the alarm notice they receive and when they receive it. They may initially try to contact designated personnel or contact law enforcement or fire department agencies when an unanswered alarm condition occurs. They may also dispatch armed or unarmed security personnel from the monitoring company to investigate the alarm.
Hands-On Exercises
In this exercise, you will learn how to secure the interior. The objectives are as follows:
Discussion
Returning again to the ACME Warehouse project presented in the previous lab procedures, the last preparation step before creating your recommendations to be delivered to the ACME management staff is to research and design the intrusion-detection plan for the interior security zone of the facility.
In the previous procedures, you researched the options for monitoring and controlling access through the outer and inner perimeters, as well as monitoring the areas between those perimeters using video surveillance components.
In this procedure, you will be tasked to research components and strategies that can be used to monitor and control activity within the interior security zone. You will also be expected to make recommendations for implementing the most cost-effective solution that will provide the necessary levels of security.
Figure 4.17 depicts the ACME warehouse area. This portion of the facility is used to store ACME products for shipping to buyers and distributors. As the figure indicates, this area also contains the company’s local offices, including:
- The CEO’s office
- The shipping manager’s office
- The accounting office
- The marketing office
- A supply closet for office supplies
- A janitorial closet for cleaning supplies
FIGURE 4.17 The Warehouse Area and Offices
The remainder of the warehouse area is open floor space filled with rows of shelving racks that hold ACME products.
It should be apparent that there are two security matters to be considered for the warehouse interior area:
- What are the interior security needs when the warehouse is in operation?
- What are the interior security needs when the warehouse operation is shut down for evenings and weekends?
Procedure
- Review Figure 4.18 and identify/label the assets of the warehouse facility that should be monitored.

FIGURE 4.18 The Interior Security Zone
- Use the Internet or other available research tools to research access-monitoring and control devices and systems that can be used to secure the access points you identified in the previous step.
- Use Table 4.1 through Table 4.3 to organize the specified details about the access-monitoring and control products you find there. For each item, try to locate at least two vendors.
TABLE 4.1 Door Locks
Product Description Vendor Number Required Cost Per Unit Total Price A Mag Door Lock Kit Entry Vision 1 $274.99 $274.99 B Electronic Keyless Door Lock Gino Development 4 $89.99 $359.96 C Schlage B581 Doorware.com 1 $52.00 $52.00 Product Description Vendor Number Required Cost Per Unit Total Price A Surface Mount Seco-Larm 4 $1.90 $7.60 B Wireless Surface Insteon 4 $25.00 $100.00 C Recessed Mount Interlogix 4 $6.86 $27.44 TABLE 4.3 Motion Detectors
Product Description Vendor Number Required Cost Per Unit Total Price A PIR Motion Sensor Vedard Alarm 2 $8.50 $17.00 B Pir 360 Motion Audio Sensor Lithonia 2 $117.00 $234.00 C PIR 360 Motion Sensor Optex 2 $54.00 $108.00 - List your recommendation for the access-control door locks you think should be utilized by ACME.
Answer: Mag Door Lock Kit, Electronic Keyless Door Locks, Schlage B581 deadbolt.
- Where you would utilize the door locks you are recommending?
Answer: The Mag Door Lock Kit should be applied to outside warehouse pedestrian door for entry authentication and control. Electronic Keyless Door Locks should be installed for the CEO’s office, the shipping manager’s office, the accounting office, and the marketing office. The locks can be actuated without authentication steps from inside the offices, but require keys or passcodes to operate doors from inside of warehouse. Schlage B581 should be used for the outside showroom and the outside warehouse pedestrian door to secure the perimeter during closed hours.
- List your selection for the door sensor types you would recommend to ACME for their interior assets.
Answer: The Interlogix Recessed Mount should be utilized to provide additional tracking of people’s movement into sensitive offices such as the CEO’s, both during operating hours and after hours of operation.
- List your recommendation for the motion detectors ACME should use for their interior security zone.
Answer: The Lithonia 360 PIR Motion and Audio Sensors will allow full coverage/cross coverage of the warehouse floor after hours to trigger the security system if any other sensor fails before an intruder actually enters the security zone.
Review Questions
- Which type of access-control devices might be good recommendations for securing the CEO’s office door?
Answer: A biometric ID device, a cipher lock, or a keyed lock. The information available in most executive offices typically requires some level of protection. The level of security depends on the organization’s tolerance for risk and should be based on a risk assessment. This typically holds true for other management offices (for example, accounting and sales/marketing offices).
- Which type of access-control devices might be good recommendations for securing the doors of the supply and janitor’s closets?
Answer: Either a simple keyed lock or no lock at all. These closets do not contain valuable assets and are often shared by various levels of employees requiring access so they may not require any security beyond a door.
- Where would infrared motion detectors be an appropriate choice for the ACME facility?
Answer: In the open floor area of the warehouse. There are no access points to monitor, so motion detectors can provide good wide-area monitoring for interior zones. Of course, these devices would only be effective during the evening and weekend time periods when the warehouse operation was closed down and unattended.
