CHAPTER 21
Protecting the Perimeter
The second level you need to secure is the inner perimeter, where the private network meets the Internet. What defines a perimeter is the boundary where you have control, versus where you don’t have control. The perimeter is where your private network touches those individuals and companies with which you want to interact. In this chapter, you’ll learn to:
- Implement firewalls and other intrusion-prevention devices and structures
- Describe common enterprise-network structures, including intranets, extranets, DMZs, and honeypots
- Describe the purpose and limitations of firewalls
- Describe the use of honeypots as an intrusion-prevention technique
- Understand the role of DMZs (demilitarized zones) in cybersecurity topologies
- Explain the configuration and operation of a demilitarized zone (DMZ) host, including the key services contained within the zone
Understanding the Perimeter
The inner perimeter is the point where we want to stop the bad people on the Internet from accessing the private network, as depicted in Figure 21.1.

FIGURE 21.1 The Perimeter
Network hardware is the integral component in Internet access and can usually serve a dual purpose in providing a certain amount of network security. Whether access is controlled via something as simple as a modem or as complex as a router or firewall, there is always at least one and generally two or more critical pieces of hardware between the user’s computer or device and their ISP, as shown in Figure 21.2.

FIGURE 21.2 Internet Connectivity
It is critical to understand that these devices can be the single point of failure or the portal to network tragedy when it comes to design, troubleshooting, and maintenance. These are the devices that technical support personnel will typically target initially while troubleshooting because they really are the most common trouble spots. They are also important in any security initiative.
Gateway devices often provide good security capabilities and even out-of-the-box and unconfigured, they will usually provide “good enough” security for the average residential or small office user. These days, the typical ISP-provided modem also functions as a router and packet-level firewall. However, if your modem does not function as a router, you will need to run security software to create a software firewall on your computer. Both Mac and Windows systems include basic firewall capabilities built-in and many dedicated software firewall products or firewall features bundled with antivirus software exist to help these users.
Every standalone computer or local area network that connects to the Internet will connect through some type of gateway device, as shown in Figure 21.3. This gateway device is often a router but may also be a switch that features some protocol conversion or translator to allow your Ethernet or wireless clients access to the technology your ISP provides at your location. This gateway device could also be a modem, an access point, or even a Voice over Internet Protocol (VoIP) adapter.

FIGURE 21.3 Gateway Connection Options
If the gateway is not also a router (or at least a switch), generally, you will need a router operating behind that gateway. If the gateway does not feature a router, it likely connects to a network that provides routing services, so going forward we will assume that all networks connect to the Internet through a router or routing device.
It is important that you understand exactly what features any network hardware between your router and your ISP performs. Security is not just about a single device; you might have to deal with many devices to further secure the environment. For example, many networks have key network components connected to their routers. These devices might act as a firewall or be a network appliance that provides some specific features for users.
In many networking environments, it is common to create some outwardly facing network services that provide available access to external users. These services might include web servers or mail servers that users can access easily while the organization maintains control of the content. Such networks that are insulated from the private network but that can be seen from the Internet, as illustrated in Figure 21.4, are referred to as public networks. Most organizations do this by creating a managed, externally accessible network called a demilitarized zone (DMZ) between their private network and the Internet. DMZs are discussed in greater detail later in this chapter.

FIGURE 21.4 Private and Public Networks
Maintaining security for a network connected to the Internet can be a tremendous challenge. Most of the concepts presented here will be relevant to any network environment, but each network may have different challenges related to the services and applications featured on that network.
Going forward, we will focus on security for devices that must live on a public network and not so much about protecting the private network from threats originating from the Internet, even though many of those concepts are the same. Much like any other kind of security, the amount of emphasis placed on Internet security should be related to what stands to be lost. Important questions that must be answered to arrive at a satisfactory solution include:
- How important is what you are protecting?
- What is the worst-case scenario?
- How much will it hurt you or your company if the network is compromised?
- Do you have private data that must be protected or are there any liability concerns if data is obtained by outside users?
- Are there regulations or laws requiring you to protect your data?
Everyone should participate in a certain level of Internet security, but after you answer these questions you should realize how much additional security is needed.
Firewalls
The most common first line of defense in a network connected to the Internet is a firewall. These devices usually consist of some combination of hardware and software used to protect a private network from unauthorized access by way of the Internet. This is accomplished by limiting security exposures, enforcing the organization’s security policy, and sometimes logging or monitoring Internet activity.
Firewalls can be implemented in various ways in different network arrangements. A firewall might be a mission-specific hardware device, or it may be a function that is built into a router or switch, or it may be implemented in a computer that has multiple Ethernet interfaces. It can even be a pure software firewall installed on a host computer like any other application. Many network appliances are available that offer firewall and security capabilities along with other network features.
In a corporate or industrial network environment, the administrator controls firewall installations and configurations. The advantage of the network firewall is that it enables the administrator to control the flow of information to all the devices attached to their network, as illustrated in Figure 21.5.

FIGURE 21.5 Network Firewall
Firewalls must act as gateway devices, authorizing and granting access to both network applications and protocols. They might also act as proxy servers, provide Network Address Translation, and act as DHCP servers. Firewalls typically also filter both incoming and outgoing traffic.
A good firewall will provide packet filtering using defined rules to reject or accept both incoming and outgoing packets. This can be more challenging to configure, but effective firewall rules are really critical to security.
A packet-filtering firewall can be established through routers by configuring them with packet-filtering rules to allow or deny client access based on factors such as their source address, destination address, or port number. There are generally two types of packet-filtering firewalls to consider: static packet filtering and stateful packet filtering.
Static (or stateless) packet-filtering firewalls do not keep track of the state of a connection between two computers. They actually operate in much the same manner as any ACL does. This makes this variety of firewalls relatively faster than other firewall options. They also tend to be relatively inexpensive and easy to maintain. Conversely, static packet-filtering firewalls offer fewer security features than other firewall options.
Stateful packet-filtering firewalls do keep track of the connection state between entities. These firewalls collect network connection information and maintain dynamic state tables that are used for subsequent connections. As illustrated in Figure 21.6, this enables ports to be opened and closed as needed. Once a client has completed a communication session, the stateful packet-filtering firewall closes the specific port used until it is requested again.

FIGURE 21.6 Stateful Firewall Operations
As described earlier, proxy servers, or proxy-filtering firewalls, are servers configured to filter out unwanted packets. Proxy filtering is a much more complex process than packet filtering. During this filtering process, each packet is disassembled, evaluated, and reassembled, making this type of connection significantly slower than other firewall types.
Proxy-filtering firewalls or application-level firewalls are configured to view entire packets for consistency, type of application, and appropriate ports. The data that is attempting to travel through these ports to a client must match what the proxy-filtering firewall expects, or the unknown packet will be dropped and the connection will be lost.
Newer firewalls will also provide Quality of Service (QoS) functionality, which allows for the prioritization and differential treatment of network traffic based on special rules or policies. A common use for QoS is to ensure that a Voice over IP (VoIP) phone system will always have enough bandwidth for phone service, regardless of how busy the network is.
Some applications are more sensitive to latency, and using Quality of Service (QoS) can make sure those applications always have enough priority to keep packets flowing to them, so that connections do not drop. QoS can also be a way to share or allocate bandwidth effectively on a busy network. Some firewalls will separate this sort of traffic management from QoS, but they are similar concepts.
Firewall Considerations
The firewall is generally the place to start when implementing or evaluating Internet security. Most administrators configure the firewall features they need and then try to make them secure. However, security really needs to be the first consideration. For instance, before configuring the firewall features, you should consider:
- What applications do outside users need to access?
- Will outside users be using a VPN or not?
You are almost always going to enable NAT and proxy server functionality on a firewall. But the design of the network and configuration of the firewall should be based on the applications to which outside users will need to connect.
If no one needs to access the network from the Internet, then the firewall configuration can be tightened up to disallow any packet that originates from the outside world. For example, if you disallow Internet Control Message Protocol (ICMP) and don’t respond on any port, then the firewall is better secured. However, at the tightest security levels, that firewall configuration might enrage network users as they typical want zero-configuration protocols, such as Universal Plug and Play (UPnP) enabled. As with other aspects of business, use of security controls is governed by the needs of the users and the business.
Before you can configure a network or a network appliance, you have to evaluate your needs as well as consider acceptable use policies and balance all of this against the available network resources. The network administrator who fails to consider all of these things will become unpopular with both management and staff quickly. A sound and organized approach to network design and security is imperative for efficient and effective management of the network. Many questions must be answered before you can create and organize a network properly:
- Resources:
- What are the available network resources?
- How many users will be sharing those resources?
- If you are working with limited bandwidth, you will need to consider traffic management and QoS features.
- What are the most critical network services?
- Configure QoS to prioritize those services.
- What is considered acceptable use to management?
It can be difficult to filter all the kinds of content that users can access. Sure, you can block access to Facebook, but what about streaming video? Netflix? Sporting events? You can spend time determining where your bandwidth was used and adding new blocking rules to keep users from accessing bandwidth intensive applications. On the other hand, you could simply set up QoS policies that fairly share bandwidth so that in periods of high demand, everyone gets their fair share of the resources. If that fair share will still support streaming, then maybe that’s OK.
Often management wants to make sure users can’t do anything but their work. So, the acceptable use policy is simple: only work-related activities are to be tolerated on the network. The degree to which you can block all nonwork-related access will largely be determined by the network hardware available. Hardware procurement is done according to business needs (per policy).
- Which remote access needs to be supported?
- VPN support will depend on the network hardware.
- Do you need to run an email server behind the firewall that can also be accessed by Internet users who aren’t connecting through a VPN?
- How will you segment the network to minimize risks?
Network Appliances
Increasingly, routers and switches are being integrated into smart switches, or even coupled with a traditional operating system to create smart network appliances. The degree to which each of these devices functions as a router varies, but often they offer a great deal of router functionality coupled with software that can ease the management of the network.
Generally, network appliances offer significant firewall capability, but many are specialized and focus on a single task, such as email, spam, or antivirus and malware detection. These devices can offer a strong arsenal of tools against attacks and ease the chore of managing access and network security.
Security appliances are also known as unified threat management (UTM) devices featuring gateway, antivirus, firewall, intrusion prevention and detection, and possibly more in a single product, as shown in Figure 21.7. Not only are many security features presented in a unified platform, but the solutions are streamlined and simplified to minimize the need for extensive training or security knowledge. Enterprises are increasingly relying on these appliances and expect their IT staff to manage them effectively.

FIGURE 21.7 A UTM Device
Probably one of the more complex aspects of a network appliance is choosing one. There are a number of big names in the industry—names such as Cisco, Barracuda, and Juniper—that are popular with midsize companies. However, many other companies—such as WatchGuard, Cyberroam, and Check Point—offer solutions for smaller organizations.
Beyond purchase price, it is important to evaluate a prospective device by carefully looking at the amount of training required, support for all of the features required by the network, as well as remote access and ongoing support and subscription costs.
Although UTM devices may seem like the best solution to Internet security issues, they also represent a single point of failure on the network and can potentially have vulnerabilities themselves. The device must also be able to handle all the network traffic or it will become a network bottleneck.
Selecting an appliance that is appropriate for your network needs is crucial, and you must consider many factors to ensure the product will be able to handle the demands of your networks rather than just focusing on security features.
Proxy Servers
A proxy server is a barrier that prevents outsiders from entering a local area network and prevents insiders from directly connecting to outside resources, as illustrated in Figure 21.8. Instead, it allows clients to make indirect network connections that are routed through it. The client connects to the proxy server, with or without any conscious authentication, and makes a request for a resource from a different server. The proxy server will handle the request by either returning the requested resource from its own cached copy or by forwarding the request to the other server (after potentially modifying the request).
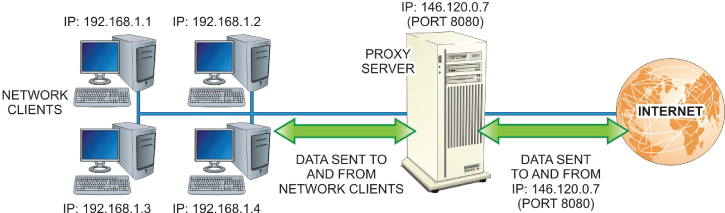
FIGURE 21.8 Operation of a Proxy Server
All addressing information sent to the Internet will use the IP address of the proxy server. Because the IP address of the client that’s requesting the resource isn’t used, an outside intruder has no way of accessing the local host.
When fully configured, the proxy server will supply the client with the addresses and port numbers for Internet services (HTTP, FTP, and so on) that are available to it. Client access is configured from the local web browser. Most operating systems and web browsers provide for proxy configuration.
Probably the most common use of this concept is with caching web proxies where a local server will cache web resources and then expire them intelligently. Web proxies help conserve Internet bandwidth and speed up connections, but they can also be used to filter content or even reformat that content.
A proxy server might be an anonymous proxy that provides client anonymity by concealing their original IP address.
A transparent proxy makes the original IP address available but only in the HTTP headers. Typically, the user is not even aware they are using a transparent proxy. Many ISPs will transparently proxy connections so they can provide a customized “404 page” or search result filter.
A distorting proxy acts in a manner very similar to a transparent proxy, but it includes incorrect IP information in the HTTP headers.
Data communication through proxies is typically unencrypted and can be hacked. So, you need to be careful using nonlocal proxy services.
Malicious proxy servers have been used for various purposes including malware delivery, ad injection, and for simple information gathering. While these proxy servers may not pass on your IP address, they will know your IP address and could use this information for other purposes.
There are a great many open proxies on the Internet offering to conceal your IP address while you browse the Web in the name of privacy, etc. Before considering such a service, research them well and only use proxy servers that are known and trusted.
It is common to put a cluster of web servers behind a reverse proxy server that handles public requests for web resources and then forwards them to one or more of the servers, as illustrated in Figure 21.9. To the requestor, this process appears as if those web servers are being accessed directly. This arrangement can be beneficial for load balancing, effectively distributing requests for a single site among a number of servers.

FIGURE 21.9 Reverse Proxy Operations
A reverse proxy can also be used to provide an SSL connection to allow the web server cluster to share a single secure certificate. They can also be used to cache static content, for data compression, filtering, and more. They also offer some additional security for the servers and can help with some types of attacks.
Demilitarized Zones (DMZs)
In addition to creating secure links to other trusted businesses, other organizations want to extend their business directly to their customers for Business-to-Customer (B2C) operations. This normally involves hosting web pages that advertise products and services to the general public over the Internet. While the organization wants these customers to access their site, they do not want them to be able to access their secured intranet zones. Therefore, the outward-facing web servers or computers that host the service cannot be linked directly with those zones.
Some organizations dedicate a portion of their network to a security structure called a demilitarized zone (DMZ). The DMZ is a separate perimeter network that isolates the secure intranet from the outside world, yet enables public access to outward-facing dedicated resources. Figure 21.10 shows a typical DMZ implementation.

FIGURE 21.10 A DMZ
As the figure illustrates, select servers and other resources dedicated to customer traffic are located in the DMZ. These resources are referred to as bastion hosts. A bastion host may be a firewall, a router, a server or a group of computers that are not protected behind another firewall, but that have direct access to the Internet.
The most common bastion hosts found in a DMZ are servers that provide public access services, such as:
- Web servers
- Mail servers
- FTP servers
- VoIP servers
Access to the DMZ is controlled by one or more firewalls. In a single-firewall DMZ, like the one depicted in Figure 21.11, the firewall must be a multihomed device that can provide three separate network interfaces: FIGURE 21.11 A Single-Firewall DMZ
In this configuration, the firewall examines all incoming traffic to determine whether it should be routed over to the DMZ or passed to the intranet. Likewise, the DMZ examines all outgoing traffic from the intranet to determine whether it should be:
Multihomed, single-firewall DMZs are typically selected over other security structures because they are relatively inexpensive to implement. However, in this configuration, the firewall becomes a single point of failure for the entire network. If the firewall is breached, the attacker has gained access to the entire network. All that’s required is a poorly configured firewall that leaves a port open to attack. In a dual-firewall DMZ, such as the one shown in Figure 21.12, firewalls are positioned on each side of the DMZ to filter traffic moving between the intranet and the DMZ, as well as between the DMZ and the Internet. These firewalls are used to route public traffic to the DMZ and internal network traffic to the intranet. FIGURE 21.12 A Dual-Firewall DMZ Dual-firewalled DMZ configurations offer a much higher level of security in that an attacker would have to hack multiple devices to compromise the intranet. If they are successful at compromising the first firewall, they only gain access to the public-facing resources in the DMZ.Single-Firewall DMZs

Dual-Firewall DMZs

Honeypots
Honeypots are another perimeter network-security structure used to lure attackers away from gaining access to legitimate intranet resources. A honeypot is a decoy server, network device, or network segment designed to attract attackers away from the real network. This is accomplished by providing attackers with relatively easy access to decoy systems on the network and hiding truly critical systems.
Typically, honeypot servers are designed as poorly configured production servers, making them appear to be easy high-value targets. These servers are normally placed in a DMZ to separate them from other sections of the intranet. Figure 21.13 depicts a generic honeypot implementation.

FIGURE 21.13 Honeypot Implementation
The honeypot typically includes monitoring software that is configured to initiate alerts to the network administrator when an attack occurs. They also include some type of passive IDS (intrusion-detection system) to collect forensic information. This information normally includes attacker signature data, attack methods, and legal support information that can be used to pursue legal prosecution for attempted cracking activities.
Honeypots can be valuable as training or research tools. However, given their vulnerable nature, it is critical to stay vigilant in monitoring a honeypot. Otherwise, a compromised honeypot can be turned into a hacking platform from which more attacks are made, perhaps even internally. The risk of a honeypot being used against yours and others’ networks demands constant monitoring.
A security structure referred to as a honeynet extends the concept of the honeypot to establish a small decoy, production network to attract would-be attackers. This structure is used in some larger networks that have extremely critical resources. However, the cost of implementing and managing such a security system becomes prohibitive in medium and smaller networks.
Extranets
While an intranet is designed to provide a secure network structure for authorized members within the organization, many businesses add one or more Business-to-Business (B2B) channels to their networks that are used to conduct secure transactions with other trusted organizations.
The term extranet is used to describe an intranet structure that grants limited access to authorized outside users, such as corporate business partners. In other words, a partially private, partially public network structure, like the one illustrated in Figure 21.14. B2B relationships are the main reason for establishing this type of network structure.

FIGURE 21.14 An Extranet
In the example presented in the figure, a web server for customers is placed between the organization’s intranet and the Internet to service trusted external users. The server must authenticate requests from these users before they can access the server’s contents. A firewall is typically positioned between the web server and the intranet to block outside users from accessing the organization’s internal network structures.
The extranet creates a special security zone that extends the network to the other trusted organization. This zone can also employ secure communication techniques such as VPNs or tunnels between the two organizations.
Hands-On Exercises
Objectives
The purpose of this lab is to set up a VPN and confirm that the VPN is working. You will download and install software, configure the software, and examine the difference before using a VPN and after using a VPN.
Resources
- PC with Windows 10
- An Internet connection
- At least 200 MB of drive space
Procedures
- Open Microsoft Edge, type www.opera.com in the address bar, and press Enter. The results are shown in Figure 21.15.

FIGURE 21.15 Viewing
www.opera.com - Click Download.
- Click Run in the dialog box.
- Click Accept And Install when the installer appears, as shown in Figure 21.16. Allow the software to make changes if necessary.

FIGURE 21.16 Using the Installer
- If there is a message to close Edge, as shown in Figure 21.17, click Skip Import.

FIGURE 21.17 Skipping the Import
- Open a new tab by pressing Ctrl+T.
- Close the other two tabs by clicking on the X on the tabs you want to close.
- Your Opera browser should look similar to Figure 21.18.

FIGURE 21.18 Opera Browser
- Click on the Settings icon in the top-right corner. This icon looks like a set of three sliders.
- Scroll to the bottom and select Go To Browser Settings. This should bring up a window similar to that shown in Figure 21.19.

FIGURE 21.19 The Browser Settings Gear
- Click Privacy & Security in the Settings window.
- Scroll down to VPN section, as depicted in Figure 21.20.

FIGURE 21.20 The VPN Settings
- Click on the Enable VPN check box. You may notice that a blue VPN icon has appeared in the address bar.
- In the address bar, type https://www.askapache.com/online-tools/whoami.
Your Internet connection may seem slower. This is normal when using a VPN. The VPN creates more routing and encapsulation requiring more time and bandwidth to facilitate communications. If this website doesn’t work, you can try using the keyword “whoami” in an Internet search engine.
- Examine the information displayed; see Figure 21.21 for an example. The
REVERSE_DNSlisting is the most important information.
FIGURE 21.21 The Results of Apache “Whoami
- Scroll down and click on Show My Information.
After clicking, you should see a map and a guess of your location.
- To verify the information provided by a second source, navigate to
www.google.comand type where am i in the query box. You should see results similar to those depicted in Figure 21.22. Note, if you allow Google to use geolocation services, this step might indeed show your true location.
FIGURE 21.22 The Results of “Where Am I”
- Perhaps this location is in fact near you. Click on the VPN icon at the left side of the address bar. Click on the words “Optimal Location” to change where Internet websites think you are. Choose a location far away from you. (We chose a location in Asia, as shown in Figure 21.23.)

FIGURE 21.23 Choosing Location in Asia
- Click on the search bar and press Enter to request “where am i.”
Where are you now? Your reported location should be different, although it could be nearby.
- Close your browser.
Lab Questions
- What is the purpose of a VPN?
- Is using Opera an effective VPN solution in an enterprise environment?
- Why is using a VPN slower than using the normal connection?
- If your computer is behind a VPN, will this interfere with normal IP diagnostic tools, such as
pingorTRACERT? Why?
Lab Answers
- What is the purpose of a VPN?
The purpose of a VPN is to provide secure communication with another server over a nonsecured network.
- Is using Opera an effective VPN solution in an enterprise environment?
Definitely not. The VPN service (and the browser) are free and allow unlimited data to pass through the VPN. This VPN is also very easy to set up. While cheap, scalable, and easy, there is no support. In addition, there is nothing to configure or set up, which means no customization for your use case.
- Why is using a VPN slower than using the normal connection?
Because there is more routing, more encapsulation, and an increase in bandwidth usage to accommodate the additional data. In addition, packets are traveling a much different path than normal. Because this affects all your packets, web pages take more time to load.
- If your computer is behind a VPN, will this interfere with normal IP diagnostic tools, such as
pingorTRACERT? Why?Yes. Because it will slow down communication and cause different routing than normal based on the identified different connectivity node location.
