CHAPTER 2
Understanding Access-Control and Monitoring Systems
If you skipped reading the “Introduction,” you might wonder why there’s an entire Part I devoted to infrastructure security. However, as the “Introduction” pointed out, without physical security there is no security. Infrastructure security operation and management is based on three basic types of subsystems: access-control and monitoring systems (covered in this chapter), video surveillance systems (covered in Chapter 3), and intrusion-detection and reporting systems (covered Chapter 4). In this chapter, you’ll learn to:
- Understand the application of the following concepts of physical security: access control, physical barriers, and biometrics
- Differentiate between authentication and authorization
- Identify commonly used physical access-control systems/devices including keypads, card readers, biometric readers, proximity readers, electronic deadbolts, and magnetic locks
A Quick Primer on Infrastructure Security
The overall aim of any security effort is to establish a peace-of-mind condition (a carefree state free from worries) for an individual, a group, or an organization. This condition is ideally achieved by securing exclusive rights to assets (objects and information), access to those assets, and use of those assets. This condition creates value and provides peace of mind to asset owners.
A more modern definition for security is the science, technique, and art of establishing a system of exclusion and inclusion of individuals, systems, media, content, and objects. It also provides increased safety and utilization with physical assets such as machinery or processing equipment.
Physical security is the science, technique, and art of establishing a system of exclusion and inclusion for tangible assets. In practice, this involves policies, practices, and steps aimed at combating theft, preventing physical damage, maintaining system integrity and services, and limiting unauthorized disclosure of information.
Similarly, the term cybersecurity involves securing physical access to property, systems, and equipment ports while securing intangible assets including electronic, optical, and informational access to the system’s data and controls.
In any modern system, security is a function of the synergies of both the physical and cybersecurity domains. Both entities are necessary to support a strong overall security posture and program.
When physical security initiatives are applied to providing security for the basic physical and organizational structures needed for the operation of an enterprise, an organization, or society, this is known as infrastructure security.
Although we may think of infrastructure security in simple physical terms such as a lockable door, a patrolling security guard, or as some other method used to protect our assets; there are several additional components that go into constructing an effective infrastructure security system. Such systems generally involve a combination of several critical security procedures that have been well planned and tested to meet or exceed operational and organizational security needs.
As shown in Figure 2.1, there are three general layers to designing and implementing a plan to physically secure an infrastructure asset (a property, building, physical space, system, or device):
The Outer Perimeter Securing this space involves controlling who can move (walk, drive, fly) across the legal or physical line that marks this perimeter. Examples of typical physical outer perimeters include property lines or the exterior walls of a building or complex.
The Inner Perimeter This perimeter typically involves physical barriers such as walls, doors, and windows—either exterior or interior, depending on the context of the outer perimeter.
The Interior This is the innermost level of security and consists of the interior of the building, office, cubicle, etc. that is surrounded by the inner and outer perimeters.
FIGURE 2.1 The Three Perimeters
In a comprehensive security plan, control of all three layers is addressed. Security at each layer typically consists of a formulation of specifically selected devices working together to provide an effective physical security system.
At each layer there are two concepts at work:
Natural Access-Control Methods Natural access control involves using natural design elements, such as structures and landscaping, to guide people as they enter and exit spaces.
Territorial Reinforcement Territorial reinforcement employs structures, systems, and devices to prevent unauthorized entry and create a clear difference between what is public and private.
Infrastructure security operation and management is based on three basic types of subsystems:
- Access-control and monitoring systems
- Video surveillance systems
- Intrusion-detection and reporting systems
In this chapter, you will learn about access-control and monitoring systems. However, before reading further, take a couple of minutes to update the security scenarios in Chapter 1 to reflect these introductory ideas.
Access Control
Most security experts agree that the first and most basic objective of any infrastructure security system is to deter potential intruders, as shown in Figure 2.2. This is the goal of access control. You can’t damage, destroy, or steal what you can’t physically access.

FIGURE 2.2 Access Control
The basis of designing efficient access-control systems involves three terms: ingress, egress, and regress. By definition, ingress is the right of an individual to enter a property, while egress is the legal right to leave a property. Similarly, regress is the term used to describe the legal right to reenter a property.
On a physical security basis, ingress can be defined as the physical path of an individual to properly enter a property, while egress is the physical path to properly leave a property.
In security terms, a right is a legal privilege or permission granted to someone, or some group, by some recognized source of authority. This source can be a government, a legally recognized governmental agent, or a legally recognized owner of an asset. By extension, a person who has the right to access an asset is said to be authorized (by the recognized authority), while anyone who has not been given this right is labeled as unauthorized. When unauthorized people attempt to gain access to an asset they do not have rights to access they become intruders.
Therefore, access control involves being able to control the ingress, egress, and regress to an asset based on authorization, as depicted in Figure 2.3. In particular, limiting the access of unauthorized personnel to important assets is the most fundamental security step that you can take.

FIGURE 2.3 Authorization
From the list in the previous section, you can see that access control begins at the outer perimeter. Depending on the specific example being studied, this may be the property line of the organization’s physical property or the front door of their facilities.
Recall that the goal at the outer perimeter is to control who can walk or drive across the perimeter. Control at this point can be as simple as planting hedges at the edge of the property or including appropriate visual signs to warn unauthorized people to stay out, or as complex as a barbed-wire fence with gates and armed guards.
Access-control efforts typically extend into the area between the outer and inner perimeters. These efforts can include natural access-control techniques such as strategic placement of employee and guest parking, as well as the use of landscaping features to channel people to selected entrances and exits and inhibit access to other possible entry/exit points. This also extends to clearly marking ingress and egress approaches to facilities and properties.
Inner perimeter control of a physical infrastructure involves the use of physical structures such as walls, windows, and doors that can act as barriers that impede the ability of an intruder to advance from the outer perimeter to the interior region. Once again, depending on the specific security scenario being discussed, these barriers may be part of the building’s external structure that encloses the entire interior environment, or they can be interior structures that control movement into and out of individual work areas.
Interior security is the innermost level of infrastructure security, and it involves monitoring the area inside the inner perimeter. Such monitoring may consist of both human and electronic security systems to observe, track, and detect intruders as well as record evidence of different activities. The mixture of empowered people and electronic devices makes for an effective security tool at the interior security level.
Security Policies
A key component that brings all three levels of security together is a well-designed security policy that states how security is implemented at each level. Businesses and organizations develop comprehensive security policies that define who is authorized to access different assets and what they are allowed to do with those assets when they do access them.
For example, allowing employees and visitors to have free access to all the departments inside the organization provides a variety of security risks. You will want to maintain access control to create an environment that reduces the human nature of temptation. If everyone can move freely within the interior of the organization, it is much more difficult to implement safeguards to prevent them from accessing or taking physical or cyber assets. You also need to maintain access control to prevent accidents.
For example, you do not want a sales representative accidentally spilling their coffee on one of the production servers in your engineering department.
Instead, develop a cohesive access-control policy at each level that provides authorized people with appropriate levels of access to selected assets, while inhibiting access to assets by people who are not authorized. Then enforce those policies with the correct types and numbers of access-control devices (sensors, barriers, logs, ID badges, or security guards) as deemed appropriate.
Frequently, badges or smartcards are used to control access. Employees may also be identified by a Radio Frequency Identification (RFID) transponder as they move within proximal range of an RFID sensor. Transponders store access codes and use radio receivers and transmitters.
These access-control techniques, systems, and devices are discussed in detail throughout the remainder of this chapter.
Physical Security Controls
Enforcing access-control measures may initially include placing locks on doors that access offices and separating departments or networking sections with similar physical barriers. Many companies have a front door or an entranceway that includes a receptionist to control access. During business hours, the receptionist acts as a physical barrier, inquiring about the nature of clients’ visits, as illustrated in Figure 2.4.

FIGURE 2.4 Physical Barriers
In some institutions, the visitor may be required to be accompanied by an escort to physically limit their movement through the company. For additional access control, a human guard could be employed to control access to specific, restricted interior locations, such as a laboratory, or to an elevator that services a restricted area, such as a basement.
At night, the physical barrier may simply be a locked door. However, the door may also be equipped with a sensor and an alarm. The alarm could be a local annunciator such as a siren, or it could be linked directly to an external monitoring system or to the police department.
Locks and Keys
The primary physical barrier in most security perimeters is the lockable door. The door provides the physical barrier but in itself will only keep honest people out. The lock, on the other hand, provides the authentication function of the barrier through its key. Having the key signifies that the person either possesses or knows the information required to gain access through the door.
Many different types of locks are used with security barriers. Likewise, many different types of keys are used to disengage the locking mechanism. Depending on the type of lock being used, the key can be either physical or logical.
In most organizations, only select personnel who work in a particular office may possess a key to access their working environment. Maintaining tight key control and using numbered keys that are clearly coded for nonreproduction helps to maintain the locked door as an effective physical barrier.
Standard Key-Locking Deadbolts
Standard key-locking deadbolts have a locking mechanism similar to that of the electronic solenoid-operated deadbolt but are engaged or withdrawn with a key. They provide an added level of security for doors that can be operated manually. A key-locking deadbolt is available with a single or double cylinder, as shown in Figure 2.5.

FIGURE 2.5 Key-Locking Deadbolt
Solenoid-Operated Deadbolt Locks
Electronically operated deadbolt locks offer an increased level of security for the perimeter. Adaptable to any security system, electric deadbolts perform well as auxiliary locks on doors where access control is desired.
The main actuation component of solenoid-operated deadbolt locks, like the one displayed in Figure 2.6, are electrically activated solenoids. When electric current is applied to the solenoid’s coil, an electromagnetic field is developed around it. The electromagnetic field applies magnetic pressure on the core in the center of the coil, causing it to move. This movement either engages (activates) the physical locking mechanism or it disengages (deactivates) the locking mechanism.

FIGURE 2.6 Electronic Deadbolt
The operation of the solenoid is typically controlled by a remotely located switch or through an electronic access-control system. In the latter case, the system is typically actuated by input from intelligent identification card-access devices.
Solenoid-operated deadbolts can be set to either lock or unlock when energized and are listed by Underwriters Laboratories (UL) as burglary-protection devices. In security applications, the solenoid lock is typically configured so that it automatically moves to the locked position when the door is closed. This helps prevent tailgating, where an unauthorized person slips past the locking door closely behind someone who is authorized to pass through it.
However, some doors that use automatic locks need to be configured to operate in a fail-safe manner (unlocks when power is removed). This type of configuration must be used to enable employees to exit through the door in case of emergency.
A dead-bolted door configured to operate in a fail-secure manner (locks when the power is removed) would not be suitable for use as an emergency exit, because it could not be used to exit the perimeter in an emergency. With a fail-secure lock, the door would default to the locked condition and would not open because of the lack of electricity to operate it.
Electronic deadbolts can be used with swinging, sliding, power-operated, and vertical-lift doors, as well as on fence gates.
Cipher Locks
Cipher locks requiring personal access codes known by the user are often used in access-control and management systems. These locks operate by unlocking magnetic door locks when the correct programmed code is entered by the user on the cipher-lock keypad. They provide an added level of security for perimeter entry areas. An example of a cipher lock is shown in Figure 2.7.

FIGURE 2.7 Cipher Lock
While electronic door pads may offer a more secure physical barrier, their entry codes need to be periodically changed for such pads to be effective over time.
Access-Control Gates
Like a door, a gate is a type of physical barrier that can be swung, drawn, or lowered to control ingress and egress through a wall or fence. Access-control gates can be classified into two main types:
- Sliding gates
- Swinging gates
Both types can be opened or closed through the use of a motorized operator. The size of the gate operator is determined by the width of the pathway and the weight of the selected gate.
Sliding Gates
Sliding gates, such as the one shown in Figure 2.8, are used where high levels of operational safety and security are needed.

FIGURE 2.8 Sliding Gate
Swinging Gates
Swinging gates, like the one depicted in Figure 2.9, are equipped with fully adjustable hinges that allow the gate to swing through 180 degrees. An articulated arm, which runs from the operator to the gate, pulls or pushes the gate open and closed. Manufacturers sometimes use a piston/cylinder configuration as the actuator for the arm.

FIGURE 2.9 Swinging Gate
Control Relays
Relays are electromechanical devices that employ safer, low-voltage/low-current control signals to be used to control higher-voltage/higher-current devices. In access-control settings, relays are commonly used to control the operation of electric gates and door locks, garage door openers, and other remote devices.
Figure 2.10 shows a schematic diagram of a simple single-pole, single-throw (SPST) relay. As the diagram illustrates, the relay consists of a coil with two external connections, a Common connection, and two output connections.
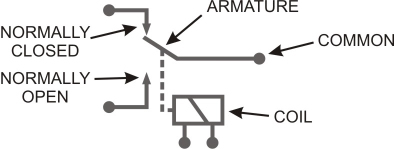
FIGURE 2.10 SPST Relay Schematic
The output connections are specified by their relationship to the Common connection when no energy is applied to the coil. One output is called the Normally Open (NO) contact and the other is the Normally Closed (NC) contact.
When no signal is applied to the coil, the relay is at rest, and there is a physical connection from the Common terminal to the NC terminal. Conversely, there is no physical connection between the Common and NO terminals. In this state, any signal (current) applied to the Common terminal will pass through to the NC terminal, but no signal (or current) can pass through to the NO terminal.
When an electrical current is passed between the two Coil terminals, the coil is energized, and everything changes. The magnetic field developed by the coil causes the electromagnetic core to move (in this illustration the core would move to the right).
The mechanical linkage from the core to the relay switch (shown as a dotted line) also moves. This opens the path between the Common and NC terminals and closes the path between the Common and NO terminals. Therefore, current can flow between the Common and NO terminals, but no current can flow between the Common and NC contacts.
Relay Operations
The decision to use the NO or NC output is typically based on the application the relay is being used to control. In many cases, control circuits are designed so that they provide either fail-safe or fail-secure performance. A fail-safe circuit is designed so that in the event of a power or component failure, the system being controlled will remain in its safe condition (either on or off).
The fail-secure circuit is one that fails in a most secure condition. For instance, if the power fails to an automated security gate, the system should fail in a manner that keeps the operation of the gate secure (it should remain closed unless it is opened manually from a secure location).
Activating relays are frequently built into the keypads, key fobs, door locks, or gate actuators. The relay kit shown in Figure 2.11 is designed for use as a gate controller and provides a view of the relay and associated components. The accompanying key fob is typically used to operate the controller.

FIGURE 2.11 Gate Controller Relay and Associated Components
Authentication Systems
Authentication is the process of determining that someone is who they say they are. Recall that effective access control involves being able to control the ingress, egress, and regress to an asset based on authorization. In particular, limiting the access of unauthorized personnel to important assets is the most fundamental security step that you can take. Therefore, authorization is based on authentication.
Multiple factors are involved in authentication:
- Knowledge: Something you know or something that only the designated person should know
- Possession: Something you have or something that only the designated person should have
- Inheritance: Something you are or something that only the designated person is
- Location: Somewhere you are or somewhere that only the designated person is
Many physical authentication systems are based on single authentication factors that depend on possession, such as possessing a key device that opens a lock. The key can be a physical or virtual key as needed to open physical or virtual locking mechanisms.
More intelligent and effective authentication methods involve two-factor authentication (a process that requires two of the factors to grant authorization) based on knowledge (something you know) and possession (something you have).
Advanced authorization and authentication methods include multifactor authorize and authenticate systems. In these systems, information must be presented to an authentication device that, in turn, passes it to the security controller’s authentication system. A number of different authentication devices are used routinely in access-control systems. The major device types are covered in the following sections of the chapter.
Magnetic Stripe Readers
A magnetic stripe card is a physical credit-card-like device that contains authentication information in the form of magnetically coded spots on a magnetic stripe, as illustrated in Figure 2.12. The cardholder uses the information on the card to access physical spaces or assets by passing the stripe on the card through a magnetic card reader.

FIGURE 2.12 Magnetic Stripe Card System
The card reader reads the magnetically encoded information as it passes through the reader’s magnetic sensor and translates it into digital data that it passes to a host system. The programming of the host system determines whether the information on the card is relevant to provide authorization and access for the cardholder.
Smart Cards
Smart cards are also credit-card-like devices that often resemble magnetic stripe cards, as shown in Figure 2.13. However, they offer improved data security due to the presence of intelligent circuitry that can be used to hide the user’s data until an authentication process has been performed. They typically contain information about their owners, such as their passwords, personal identification numbers (PINs), network keys, digital certificates, and other Personally Identifiable Information (PII) that can be used in the authentication process.

FIGURE 2.13 Smart Cards
Physically, smart cards are intelligent, credit-card-like devices, ID badges, and plug-in devices that communicate with a smart card reader.
Internally, all smart card designs contain a microprocessor and a memory device that are embedded in the card’s structure. The smart-card memory section holds user-specific identification information, as well as all the programming the card needs to communicate with the host security system.
Some organizations that use smart cards issue their employees single cards that they can use to get into their buildings, log on to their computers, and access appropriate applications.
Smart cards are designed to be resistant to tampering. Tampering with a smart card generally disables it. In addition, some care must be taken with smart cards as even bending one may render it unusable.
RFID Badges
Radio Frequency Identification (RFID) badges provide hands-free access-control tools that improve on the bar code, magnetic stripe, and proximity reader technologies. The RFID system employs radio signals to identify unique items using an RFID reader device and RFID tags, as illustrated in Figure 2.14.
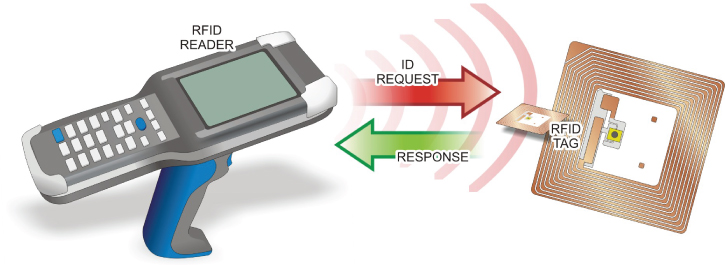
FIGURE 2.14 RFID System
The reader sends and receives radio frequency data to and from the RFID tags. Each tag stores the data sent to it on an embedded integrated circuit (IC) device. While the specific information stored on the RFID tag is determined by the RFID system programmer, it generally consists of a serial number that identifies it, along with information about the item with which the tag is associated.
When the system wants to know something associated with the tag, such as what (or who) it is associated with or where it is at, it simply sends out a request which causes the addressed RFID tag to radiate its information from its built-in antenna. The reader receives the data from the tag and relays it to its host computer for processing. The most interesting part of this technology is that the passive RFID tags are able to perform their task without the presence of an external power source.
Biometric Scanners
Biometrics is the term used to describe access-control mechanisms that use human physical characteristics to verify individual identities. Biometric authentication involves using uniquely personal physiological characteristics to verify people are who they say they are.
Every human possesses unique physical characteristics that differentiate them from other humans. Even identical twins have separate and distinctive voice patterns, fingerprints, eye features, and other characteristics. The qualities most often involved in biometric authentication include voice patterns, fingerprints, palm prints, signatures, facial features, and retinal and iris scans, as shown in Figure 2.15.

FIGURE 2.15 Typical Biometric Authentication Methods
In each case, a biometric scanning device is required to convert the physiological quantity into a digital representation. The results are stored in a database where they can be used in an authentication process. The underlying application will use the truly unique qualities of the data as a basis to compare with future access requests. If the data from a future authentication request matches the key points of the stored version, then access will be granted.
However, not all biometric scanning devices are equally accurate at authenticating users. In Table 2.1, U.S. government data shows how different biometric scanning devices rate in terms of their abilities to accurately authenticate people.
TABLE 2.1 Biometric Device Comparisons
| False Positive Rate | False Negative Rate | |
| Palm Print | 1.43% | 4% |
| Facial Structure | 0.1% | 0.8 – 1.6% |
| Voice Patterns | 2 – 5% | 5 – 10% |
| Eye (Retina or Iris) | 0.1% | 1.1 – 1.4% |
| Signature | 0.49% | 7.05% |
| Fingerprint | 2.2% | 2.2% |
In general, the characteristics of the human eye—iris and retinal scans—tend to make it the most reliable source of authentication. Of the remaining biometric variables in the list, fingerprint readings tend to be more accurate than voice scans. However, fingerprints can be stored on a clear surface and used later. On the other hand, illnesses and user stress levels can affect voiceprints.
As shown in Table 2.1, there are two basic types of authentication failure:
Type 1 – False Rejection or False Negative Failures This is a report that produces an incorrect rejection of the individual, thereby locking them out of a facility or security area that they should have been able to access.
Type 2 – False Acceptance or False Positive Failures This is a report that incorrectly authenticates the individual, which could lead to providing access to equipment or data that this person should not be able to access. Of the two types of authentication failures, this is the most significant in that it could grant access to malicious people.
Because of the potential for false reporting and inaccuracies, a second method of access control may need to be used in conjunction with biometric devices. In areas requiring higher security, a passport, additional fingerprints, or some other type of verification could be used to ensure that the individual was not mistakenly authenticated.
Remote-Access Monitoring
Remote monitoring refers to monitoring or measuring devices from a remote location or control room. In the security realm, this involves having external access to the security system through a communication system.
Remote-access monitoring systems are used to notify supervisory security personnel when an unauthorized access is attempted. In these systems, the controller monitors the open/close conditions of the infrastructure’s sensors. When a sensor such as a magnetic switch or a motion detector is activated, the system automatically identifies it as an intrusion and notifies specified security personnel of the occurrence.
The notification can come in the form of a visual notification on a security control panel, a call via telephone, an instant messenger notice, or a text message to a smart phone. The notification can also involve activating strobe lights and high intensity sirens to call attention to the intrusion attempt. Figure 2.16 shows different options for remotely accessing a typical security system.
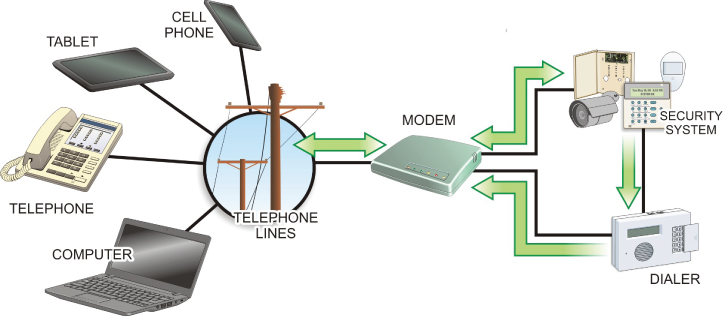
FIGURE 2.16 Remote-Access Communication Options
Opened- and Closed-Condition Monitoring
Various sensors can be used to detect the opened, closed, locked, or unlocked condition of an automated door or gate. They can also be configured to initiate an opened, closed, locked, or unlocked condition at a specified door or gate.
A simple magnetic sensor and a matching set of contacts for a movable barrier (door, gate, or window) are shown in Figure 2.17. The sensor’s transmitter sends a signal either to a control panel or to an emergency dialer when the magnetic switch contacts are broken as the door is opened.

FIGURE 2.17 Window Sensor with Magnetic Switch Contacts
Signaling and reporting between the sensor and the controller is continuous during the elapsed time between the opening and closing of the barrier. If the barrier is left open for a specified time, that information is also noted and recorded by the system. The condition-monitoring system includes an event log, detailing the times and dates of various events. For example:
Locked-Condition Monitoring Locked monitoring is a feature that allows the security supervisor to confirm that a door is locked. In addition to monitoring the locked status of a door or gate, the condition-monitoring system can also provide details as to how long and during what time periods the door or gate has remained locked.
Unlocked-Condition Monitoring The condition-monitoring system can record and signal each time a specific gate or door is unlocked (granting access) and what type of access was granted. Unlocked monitoring can also identify who was granted access.
Time-of-Day Settings Most automated access-control systems base decisions about valid or invalid entry requests, also called transactions, on preconfigured time-of-day settings. This is normal because any entry request that does not fit the predefined time profile or time schedule of an identified user is subject to suspicion.
Such a situation might occur for a daily delivery that arrives later than normally expected. The user, in this case a recognized delivery agent, has been identified but is seeking entry at an unauthorized time. An authorized human supervisor will need to intervene to accept the delivery.
Automated Access-Control Systems
Automated access-control capabilities add another dimension to standard security monitoring and reporting functions. Although automated access control is not an integral part of the typical intrusion-detection and monitoring system, it adds to the safety and convenience of perimeter-access control. Automated access-control systems come in two flavors: remote-access-control systems and remote-control access systems.
Remote-access control is a design feature that manages entry to protected areas by authenticating the identity of persons entering a secured area (security zone or computer system) using an authentication system located in a different location than the access point.
This can be accomplished by a number of methods including password readers, magnetic key cards, and secret-cipher lock codes.
Although the differences are minor, the design considerations for remote-control access systems are different from those for remote-access systems. Remote-control access is a design feature that works with remote monitoring systems to monitor, control, and supervise doors, gates, and conveyances from a distance. Figure 2.18 shows the typical components involved in a remote-access-control system.

FIGURE 2.18 Remote-Control Operations
The Remote Control function enables the security specialist to initiate communications with a remote site, enter an access code, obtain current conditions, and set system parameters. A closed-circuit television (CCTV) system may be added to the security system to provide visual recognition functions to the remote-control options. Some remote-monitoring and control systems, such as the one depicted in Figure 2.19, can also be used or obtain status messages concerning any sensor that has detected a value outside of programmed values such as heat, cold, water leakage, loud noises, alarm history, or other custom features.

FIGURE 2.19 Remote-Monitoring Systems
Wireless communications devices are often used to connect the components of an automated access-control system. This type of connectivity is an economical solution that eliminates the need for new wiring between control devices, intercoms, and electrically operated security gates and doors.
Hands-On Exercises
In this exercise, you will learn how to secure the outer perimeter. The objectives include:
- For a given facility, define its outer perimeter, inner perimeter, and interior areas, and determine key vulnerabilities associated with each layer.
- For the specified facility and its vulnerabilities, perform research to determine what components (devices and systems) are available to secure these points and what the cost options are for the components you find.
- Design an access-monitoring and control system for the outer perimeter of the facility that will enable the customer to implement the security system required to monitor and control access to their facility.
The resources necessary for this exercise are as follows:
- Internet access
- Pencil/pen and paper
Figure 2.20 depicts the ACME warehouse facility. This facility is used to store ACME products that are ready for shipment. Its loading docks handle tractor trailer trucks, as well as smaller delivery trucks, through three roll-up doors. The trucks pass in and out of the warehouse loading yard located at the rear of the building through a 30-foot-wide opening in the fence that surrounds the yard. The fence attaches to the building at each corner of its back wall, as shown in the figure. The truck opening in the fence provides access to the street that runs behind the warehouse. FIGURE 2.20 The Facility Customers enter the building from the front where there is an open parking area and an attractive customer entrance featuring double glass doors. This parking area is open to the street and has no fencing around it. The customer showroom and sale staff desk areas occupy the front of the building, while the warehouse and management offices are in the rear of the building. Employees can transition between the warehouse and the showroom through an interior pedestrian door between the two portions of the building. ACME personnel park in an employee parking area along the side of the building. They enter the facility through an employee pedestrian door that faces their parking area. The employee parking area is open and also has no fencing around it. Each ACME employee (warehouse, showroom, and management) will be issued a company ID device. The access-monitoring and control system should be capable of determining which employees have authorization to enter the warehouse portion of the facility. The warehouse also houses the management offices and a pair of supply closets. Each office has a single window that faces the showroom and a door that opens into the warehouse area. The supply closets are equipped with a solid door and no windows. The facility is nearing completion, and the ACME Company has asked you to research and recommend security and surveillance systems that will enable them to monitor and control the flow of people into and out of their warehouse. In this procedure, you will use whatever resources you have available to research physical security devices and systems that can be used to secure the outer perimeter of the ACME facility in preparation for developing a comprehensive physical-security proposal. FIGURE 2.21 Security Perimeters TABLE 2.2 Access-Control Gates TABLE 2.10 Door Locks ___________________ Answer: Viking meets the desired specifications for length and anticipated weight requirements to open a 30-foot sliding gate for the best price point. Vendors can be given access through RFID card or programmable access code. For the Warehouse Pedestrian Door:_______________________ Answer: The Entry Vision unit can use programmable keycards to allow all employees access to enter the building at the beginning of their work day. Manual deadbolt locks can secure the door at night. For the Showroom Entry Doors:___________________ Answer: Manual deadbolt with actuation to inside of showroom only. ___________________ Answer: The LiftMaster model can be configured to meet the needs of business, can be tied into security system to trigger if activated after an alarm is set or bypassed, and can be remotely operated by management or CEO if tied into network for after hours or weekend deliveries. ___________________ Answer: Leviton HAI OmniPro II. It offers the best price point for the features. The OmniPro II is Leviton’s flagship security and automation control system. Boasting the largest feature set, it can control the maximum number of devices and is designed to provide security and automation for large residences and small commercial installations such as restaurants, offices, and franchise locations. This allows all security considerations to be tied into one controller with multiple zone configurations for varying perimeter requirements. It can cover up to 176 zones so you can segregate or integrate as needed. ___________________ Answer: Omni 33A00-4 is the best selection because it can be expanded for increased control over loading-bay doors and a slide gate in the freight yard, and it is guaranteed to be compatible with the selected controller. ___________________ Answer: The Gogogate sensors with an integrated indoor and outdoor sensor system utilizing magnetic contact sensors should be used for eight units. There is a wide enough gap for commercial and residential applications, so they should work well with delivery bay and pedestrian doors as well as the freight gate to monitor access. ___________________ Answer: The CarSense unit can be used to automate the opening of the gate for delivery trucks leaving, and it can be tied into/bypassed from the security system to trigger an alarm if activated by a vehicle leaving after hours. ___________________ Answer: RFID passcards should be used to enter through the pedestrian door to the warehouse from outside. The Mag Door Lock Kit already has this feature integrated as part of its design. Also specify where you would employ the authentication devices/systems. ___________________ Answer: They should be used to enter through the pedestrian door to warehouse from employee parking outside. ___________________ Answer: The Mag Door Lock Kit should be applied to the outside warehouse pedestrian door for entry authentication and control. The Electronic Keyless Door Lock should be applied to the pedestrian door between the warehouse and showroom. It can be actuated without any authentication steps from inside the warehouse, but it requires a key or passcode to operate the door from inside the showroom. Schlage B581 should be used outside the showroom and outside the warehouse pedestrian door to secure the perimeter during closed hours.
Answer: Apply the Mag Door Lock Kit to the outside warehouse pedestrian door for entry authentication and control. Apply the Schlage B581 to the outside showroom and outside warehouse pedestrian door to secure the perimeter during closed hours. The CarSense unit can be used to automate the opening of the gate for delivery trucks leaving, and it can be tied into/bypassed from the security system to trigger an alarm if activated by a vehicle leaving after hours. Use seven Gogogate sensors as an integrated indoor and outdoor sensor system utilizing magnetic contact sensors. The gap is wide enough for commercial and residential applications, so they should work well with the delivery bay and pedestrian doors, as well as the freight gate to monitor access. The Leviton HAI OmniPro II has the best price point for its features. The OmniPro II is Leviton’s flagship security and automation control system. Boasting the largest feature set, it can control the maximum number of devices and is designed to provide security and automation for large residences and small commercial installations such as restaurants, offices, and franchise locations. This allows all security considerations to be tied into one controller with multiple zone configurations for varying perimeter requirements. It can cover up to 176 zones, so you can segregate or integrate as needed. The Liftmaster model can be configured to meet the needs of the business. It can be tied into a security system to trigger if activated after an alarm is set or bypassed. It can be remotely operated by management for after hours or weekend deliveries if tied into the network. Viking meets the desired specifications for length and anticipated weight requirements for opening a 30-foot sliding gate for the best price point. Vendors can be given access through an RFID card or a programmable access code. FIGURE 2.22 Device Locations
Answer: The street access opening in the fence for trucks to come and go, the warehouse employees’ entrance door, and the main entrance door to the showroom Answer: The inner perimeter Answer: The access door between the warehouse and the showroom, the loading dock doors, and the pedestrian door into the warehouse from employee parking Answer: The warehouse Answer: The outer perimeter
Discussion

Procedure

Product Description
Vendor
Number Required
Cost Per Unit
Total Price
A
Slide Gate Op.
DoorKing
1
$889.00
$889.00
B
Slide Gate Op.
Viking
1
$1,048.00
$1,048.00
C
Slide Gate Op.
LiftMaster
1
$1,499.00
$1,499.00
Product Description
Vendor
Number Required
Cost Per Unit
Total Price
A
Electronic Keyless Door Lock
Gino Development
1
$89.99
$89.99
B
Mag Door Lock Kit
Entry Vision
1
$274.99
$274.99
C
Cobra Controls Lock Kit
Maglocks.com
1
$1,699.99
$1,699.99
Product Description
Vendor
Number Required
Cost Per Unit
Total Price
A
Chain Drive
Genie
3
$185.88
$557.64
B
Jackshaft
LiftMaster
3
$273.39
$820.17
C
Screw Drive
Genie
3
$229.00
$687.00
Product Description
Vendor
Number Required
Cost Per Unit
Total Price
A
HAI OmniPro II
Leviton
1
$1,094.90
$1,094.90
B
Honeywell Intrusion
Ademco
1
$345.53
$345.53
C
Mercury Security EP4502
Mercury Security
1
$1,495.90
$1,495.90
Product Description
Vendor
Number Required
Cost Per Unit
Total Price
A
Omni 33A00-4
Leviton
1
$192.00
$192.00
B
Honeywell Lynx 7000
Alarm Liquidators
1
$204.95
$204.95
C
Interlogix CaddX Keypad
Home Security Store
1
$94.65
$94.65
Product Description
Vendor
Number Required
Cost Per Unit
Total Price
A
Door Sensor Wired
SensaPhone
8
$9.00
$72.00
B
Gate & Com. Door Sensor
Gogogate
8
$35.00
$280.00
C
SDC MC-4
Grainger Industrial
8
$53.95
$431.60
Product Description
Vendor
Number Required
Cost Per Unit
Total Price
A
Driveway Sensor
Mighty Mule
1
$180.78
$180.78
B
Direct Burial Sensor
CarSense
1
$208.46
$208.46
C
WPA 3000 Magnetic Probe
Absolute Automation
1
$249.00
$249.00
Product Description
Vendor
Number Required
Cost Per Unit
Total Price
A
Mag Door Lock Kit
Entry Vision
1
$274.99
$274.99
B
Electronic Keyless Door Lock
Gino Development
1
$89.99
$89.99
C
Cobra Controls Lock Kit
Maglocks.com
1
$1,699.99
$1,699.99
Product Description
Vendor
Number Required
Cost Per Unit
Total Price
A
Mag Door Lock Kit
Entry Vision
1
$274.99
$274.99
B
Electronic Keyless Door Lock
Gino Development
1
$89.99
$89.99
C
Schlage B581
Doorware.com
2
$52.00
$104.00

Review Questions
