You should not launch attacks from a source such as your home network that can be traced back to you unless you don't mind being linked to your actions. The most common method to hide your real source address is using a proxy or multiple proxies between you and the victim. In simple terms, a proxy acts as an intermediary for requests from clients seeking resources from another system. The target will see traffic from the intermediary system and will not know the real source. Layering proxies can cause an onion effect, making tracing the real source extremely difficult during a forensic investigation.
There are hundreds of free network proxies available online. You can search Free Anonymous Web Proxy Server on Google to find various flavors such as Proxify, Anonymouse, Anonymizer and Ninja Cloak. The following screenshot shows Anonymouse including the explanation of surfing through a proxy. For their service, you need to simply type in the address you want to access in the search field.

Note
Administrators of proxies can see all traffic as well as identify both the target and the victims that communicate through their proxy. It is highly recommended that you research any proxy prior to using it as some might use information captured without your permission. This includes providing forensic evidence to authorities or selling your sensitive information.
Another option to hide your source IP address is using proxychains. Proxychains allows you to tunnel Kali commands through a proxy server. You will need to install proxy chains using the sudo apt-get install proxychains command since it is not preinstalled in the Kali Linux ARM image.
Once installed, you will need to add a proxy IP address in the etc/proxychains.conf file:
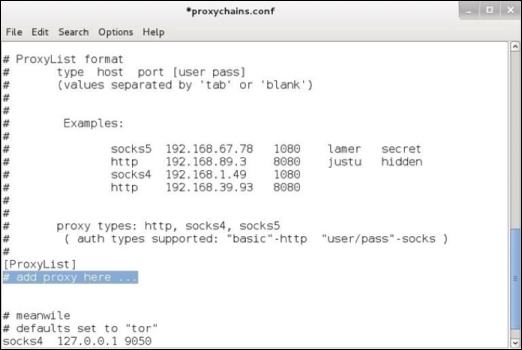
HideMyAss Internet security offers a list of free proxy servers that you can use for this purpose. You can find their website at http://proxylist.hidemyass.com. Remember, these are not very reliable and can possibly use your data without your permission since the proxy administrators see all the traffic.
The syntax for proxychains is proxychains < command you want tunneled and proxied> <optional arguments>. In the following example, we will use the nmap command to scan the 192.168.1.0/24 network through proxychains to hide from where the scan is being done. Note that we had to edit the .conf file with a proxy prior to executing this command.
proxychains nmap 192.168.1.0/24
Once you cover your tracks on the endpoints and network, the final step is to remove forensic evidence from the tools that you used. To clean a Raspberry Pi, you simply need to reimage the SD drive. You can find steps in Chapter 1, Raspberry Pi and Kali Linux Basics, to format your SD card using SD Card Formatter or Apple's Disk Utility. You can continue following Chapter 1, Raspberry Pi and Kali Linux Basics, to install a new image such as the original NOOBS software to hide that the Raspberry Pi once ran Kali Linux. You can also use a Kali Linux image that has been customized prior to launching your penetration test to save you the time of rebuilding an attack system, yet remove what was done during the previous penetration testing engagement.
Another option is to remove and break the microSD card. The following image shows an example of a cut up microSD card so that it can't be used for a future investigation:

You might be put in a situation where you can't physically access your Raspberry Pi and need to make sure that it can't be confiscated and later used for a future forensic investigation. This could happen if you planted a Raspberry Pi as a network tap, remotely accessed it to breach systems, and now need to conclude things by killing the Raspberry Pi. In this scenario, you can't wipe the microSD drive, so the next best thing is corrupting Kali Linux so that a forensic investigator can't access it to see how it was used during the network breach. Let's look at how you can remotely kill a Raspberry Pi running Kali Linux.
The first thing you might want to do is delete everything. You can do this by using the rm –rf / command which means rm = remove, -rf= remove recursively forcing all files and folders without prompting you and / tells this command to start in the root directory. Running the same command with a .* , that is rm –rf .*, would delete all the configuration files. This option isn't that good since deleting only tells the system that space is available, but it does not replace the data, meaning it can be uncovered with a forensic tool. A better approach is using dd if=/dev/zero of=/dev/sda1 so that you overwrite bytes making the data harder to recover.
Another option is to format the hard drive using the mkfs.ext4 /dev/sda1 command. The mkfs.ext4 command creates a new .ext4 file system and /dev/sda1 specifies the first partition on the first hard drive, which is what we are using to run Kali Linux.
