Social engineering attacks are designed to trick a victim into providing information through misdirection or deceit. Attackers often pretend to be someone they are not, such as someone with authority or a family member, to gain a victim's trust. When they are successful, users might have given up passwords, access credentials, or other valuable secrets. There are stories about famous hackers who have been able to obtain intellectual property just by asking for it with a smile.
There are many tools that are available in Kali Linux to assist with a social engineering campaign; however, the most successful attacks are based on understanding your target audience and abusing their trust. For example, we have obtained sensitive information using fake accounts on social media sources such as LinkedIn and Facebook, which didn't require any advanced techniques to accomplish most of our goals. Other examples include calling somebody while pretending that you are an administrator or sending e-mails claiming to be a long-lost family member.
Note
You can learn more about the authors' research on executing a penetration test using social media by searching for "Emily Williams Social Engineering" on Google or at http://www.thesecurityblogger.com/?p=1903 and http://www.pcworld.com/article/2059940/fake-social-media-id-duped-securityaware-it-guys.html.
In this chapter, we focus on one of the most popular social engineering attack tools known as SET. SET can be launched from a Raspberry Pi, but it will probably function better from a more powerful system. The best practice is leveraging a Raspberry Pi for on-site reconnaissance that can be used to build a successful social engineering attack that is executed from a remote web server.
We will follow the discussion of SET with another popular social engineering tool that is used to exploit browsers. This is known as BeEF.
The Social-Engineer Toolkit (SET) was developed by David Kennedy at TrustSec and it comes preinstalled with Kali Linux. It is often used to duplicate trusted websites such as Google, Facebook, and Twitter with the purpose of attracting victims to launch attacks against them. As victims unknowingly browse these duplicate websites, attackers can gather the victims' passwords or possibly inject a command shell that gives them full access to the victims' systems. It is a great tool for security professionals to demonstrate the chain of trust as a vulnerability, meaning demoing how the average person will not pay attention to the location where they enter sensitive information as long as the source looks legit.
You can run SET from a Raspberry Pi; however, the victim's experience of the Internet speed will be limited to the throughput provided by the Raspberry Pi. We found in our testing that victims sometimes experienced long delays before being redirected to the real website, which alerted them to a possible attack. For this reason, we recommend that you target your SET attacks to a specific user rather than a blank audience when using a Raspberry Pi to keep the performance good.
In the following example, we will set up a Raspberry Pi to clone Gmail. As shown in the following image, the goal is to make a victim believe that they are accessing their Gmail account and redirect them to the real Gmail website after they log in but store their login credentials. The trick will be to get the victim to access the SET server; however, that's where your social engineering abilities come into play. For example, you could e-mail a link, post the link on a social media source, or poison the DNS to direct traffic to your attack server. The attacker can remotely access the Raspberry Pi to pull down stolen credentials for a final penetration testing report.
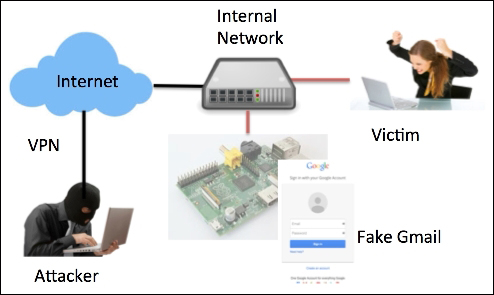
Let's take a look at how to use SET on a Raspberry Pi.
To launch SET, type
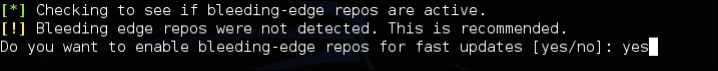
setoolkit in a command prompt window. You will be prompted to enable bleeding-edge repos. Bleeding-edge repos are a new feature in Kali that includes daily builds on popular tools such as SET. The best practice is to enable the bleeding-edge repos and test your exercise prior to using it in a live penetration test as things can slightly change. The following screenshot shows how to enable bleeding-edge repos:
Tip
Bleeding-edge repos are a great way to get the latest software packages on popular tools. However, seasoned security professionals will find that these tools often change and the features can no longer be used. The best practice is to disable updates prior to going live with a tool unless you have time to test updates from new releases.
Once SET is launched, you will need to agree to the license and terms of the software program by typing yes. At this point, you will see the main menu of SET, as shown in the following screenshot:
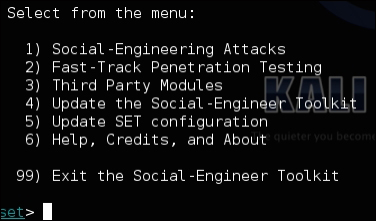
SET is a menu-based attack tool. Unlike other tools, it does not use the command line. This is based around the concept that social engineering attacks are polymorphic in nature and require multiple linear steps to set up. A command-line tool can cause confusion when developing these types of attacks.
For this example, we will select 1) Social - Engineering Attacks.
The following screenshot shows the menu under Social – Engineering Attacks:

Next, we will select 2) Website Attack Vectors. This will bring up a variety of different options. In this test scenario, we will perform a simple credential harvester attack, which is 3) Credential Harvester Attack Method, as shown in the following screenshot:

When you select the Credential Harvester Attack Method option, you have the option of using a pre-existing template or cloning a website. We found that most templates don't work that well against the average person, so it is best to clone a real website. In addition, websites often change, so cloning a website will give you the latest version that your victim will expect to see.
When you select the appropriate option, you will be prompted to enter the IP address of the interface that SET should listen on. If you have multiple interfaces, you should enter the IP address of your Internet-facing interface or the victims might have problems accessing your Raspberry Pi attack server.
If you selected 2) Site Cloner under Credential Harvester Attack Method, you will need to enter the full URL of the site that you want to clone such as https://www.facebook.com. If you select a website template, you will be choosing an existing template from a provided list. The following screenshot shows an example of some available templates. Note that these templates are very basic and dated, meaning they will probably not look like the real thing. This is why you should clone a site when performing a real penetration test.

The menu in the following screenshot offers several types of attacks. We recommend that you test each of these and make a selection based on your personal preference and success rate. Some of these attacks require a man-in-the-middle setup, which was discussed in the Man-in-the-middle attacks section of Chapter 3, Penetration Testing.

For our example, we will select 3) Credential Harvester Attack Method. This attack hosts a fake website and waits for victims to log in. When a victim sees the login and enters their login credentials, they will be redirected to the real website while unknowingly having their credentials captured for the attacker to use at a later time. The following example shows what the cloned Google login screen looks like:
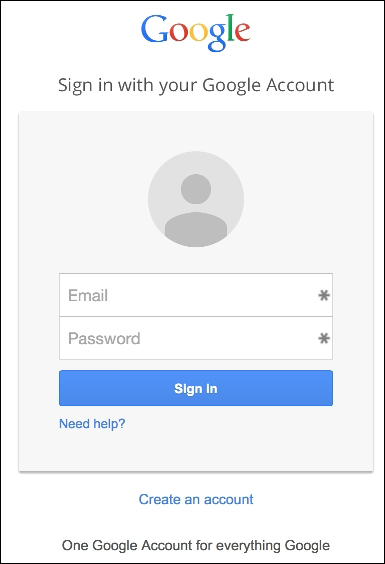
The difficult part of this attack is tricking the victim into believing that they are going to the real web page. This can be accomplished by sending them an e-mail with a fake link, posting a link on a social media website, performing DNS poisoning, and so on. SET has a number of tools and utilities to make this easier, but these are out of scope for a Raspberry Pi book. Check out SET's website found at https://www.trustedsec.com/social-engineer-toolkit/ for more information on these tools.
Tip
The best practice is to launch SET attacks from a remote server rather than the Raspberry Pi due to the process requirements to execute these types of attacks. From a user viewpoint, the attack will look the same if it is locally hosted on a Raspberry Pi or from an external system since our example is cloning a cloud service.
