Chapter 13: Security and Performance Tests
In Chapter 11, Testing APIs with Postman, and Chapter 12, Static Code Analysis with SonarQube, we talked about test automation with API tests with Postman and static code analysis with SonarQube, respectively.
In this chapter, we will discuss how to carry out security and penetration tests on a web application using the ZAP tool based on the OWASP recommendations. Then, we will add to our Postman skills so that we can perform performance tests on APIs.
We will be covering the following topics:
- Applying web security and penetration testing with ZAP
- Running performance tests with Postman
Technical requirements
To use ZAP, we need to install the Java Runtime Environment (JRE), which is available at https://www.oracle.com/technetwork/java/javase/downloads/jre8-downloads-2133155.html (an Oracle account is required).
In this chapter, we'll talk about Postman, which we discussed in Chapter 11, Testing APIs with Postman.
Check out the following video to see the Code in Action: https://bit.ly/3HbOgD0.
Applying web security and penetration testing with ZAP
Today, application security must be at the heart of companies' concerns. As soon as a web application (or website) is publicly exposed on the internet, it is a candidate for an attack by malicious people. In addition, it is important to note that application security is even more important if it is used to store sensitive data such as bank accounts or your personal information.
To address this problem, there's Open Web Application Security Project (OWASP) (https://www.owasp.org/index.php/Main_Page), a worldwide organization that studies application security issues. The goal of this organization is to publicly highlight the security problems and vulnerabilities that can be encountered in an application system. In addition to this valuable security information, OWASP provides recommendations, solutions, and tools for testing and protecting applications.
One of the important and useful projects and documents that's provided by OWASP is the top 10 application security issues. This document is available at https://owasp.org/www-project-top-ten/. The document is very detailed and provides an explanation, examples, and a solution for each security issue. In this document, we can see that the top security vulnerability that applications are most vulnerable to is injection vulnerability, such as SQL injection, which consists of injecting code or requests into an application to collect, delete, or corrupt data from the application.
At the time of writing, the top 10 OWASP mitigation techniques are as follows:
- Ongoing risk assessment
- Use automated as well as manual means for assessments
- Choose a strong Web Application Firewall (WAF)
- Ensure that the web development framework and coding practices have inbuilt security
- Enforce multi-factor authentication (MFA)
- Encrypt all data
- Apply all software updates instantly
- Ensure that the web application is sanitized
- Have formal awareness initiatives
- Adhere to OWASP compliance standards
For more details about these mitigation techniques, read the following article: https://www.indusface.com/blog/owasp-top-10-mitigation-techniques/.
We also have another known security flaw in this document, which is cross-site scripting (XSS). This consists of executing HTML or malicious JavaScript code on a user's web browser.
The challenge for companies is to be able to automate the security tests of their applications to protect them and take steps as quickly as possible when a flaw is discovered.
There are many security and penetration testing tools available. A very complete list is available at https://www.owasp.org/index.php/Appendix_A:_Testing_Tools. Among them, we learned about SonarQube in the previous chapter, which allows you to analyze code to detect security vulnerabilities.
Another tool in this list that is very interesting is Zed Attack Proxy (ZAP) (https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project), which was developed by the OWASP community.
Let's learn how to use ZAP to perform security tests on our applications.
Using ZAP for security testing
ZAP is a free and open source graphical tool that allows you to scan websites and perform a multitude of security and penetration tests.
Unlike SonarQube, which also performs security analysis in the application's source code but does not execute it, ZAP runs the application and performs security tests.
When running, ZAP will act as a proxy between the user and the application by scanning all the URLs of the application, then performing a series of penetration tests on these different URLs. It is currently one of the most widely used tools in application testing because, in addition to being free, it provides many very interesting features, such as the ability to configure Ajax penetration tests, as well as also advanced test configurations. In addition, it integrates very well with many CI/CD pipeline platforms. Finally, it is possible to control it using REST APIs. The respective documentation is available at https://www.zaproxy.org/docs/api/.
What I propose to do is make a small lab using ZAP on a public demonstration website that has security holes. As we mentioned in the Technical requirements section, one prerequisite of using ZAP is to have Java installed on the machine that will perform the tests. It can be a local machine or a build agent.
We can download ZAP at https://www.zaproxy.org/download/; download the package that corresponds to your OS.
Then, install ZAP by following the software installation procedures of your OS. Once the installation is complete, we can open ZAP and access its interface.
The following screenshot shows the default ZAP interface:
Figure 13.1 – OWASP ZAP tool
We will perform our first piece of security analysis with ZAP by following these steps:
- In the right-hand panel, click on the Automated Scan button, which will open a form where we can enter the URL to be scanned.
- In the URL to attack field, enter the URL of the website to analyze. In our example, we will enter the URL of a demo site: http://demo.guru99.com/Security/SEC_V1/.
- Then, to start the analysis, click on the Attack button.
The following screenshot shows the preceding steps visually:
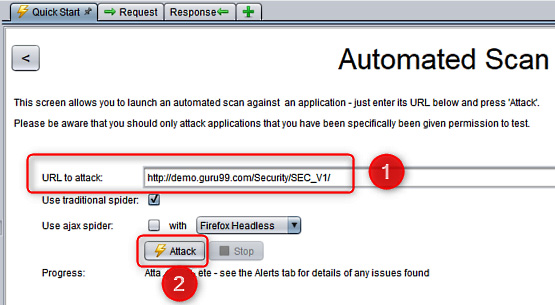
Figure 13.2 – OWASP ZAP – Automated Scan
We must wait for the security test analysis of this website to be completed.
- As soon as the analysis is completed, we can see what security problems were encountered in the panel at the bottom left.
- Finally, clicking on one of the alerts displays the details of the problem and helps us solve it.
The following screenshot shows the analysis results that we have just mentioned:

Figure 13.3 – OWASP ZAP scan result
With that, we've learned how to use ZAP, a graphical tool that's used to analyze the security vulnerabilities of a website very quickly.
Now, let's look at the different ways to automate the execution of ZAP.
Ways to automate the execution of ZAP
We can also automate this ZAP analysis by installing it on an agent server of our CI/CD pipeline and using the zap-cli tool, which is available at https://github.com/Grunny/zap-cli. This is used in the command line and calls the ZAP APIs.
The following screenshot shows using zap-cli on the command line to analyze our demo website:
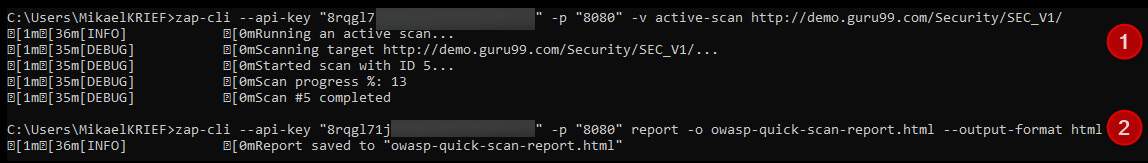
Figure 13.4 – zap-cli scan command line
In the preceding execution, two commands are used:
- The first, zap-cli active-scan, analyzes the website that was passed as a command parameter.
- The second, zap-cli report, generates a report of the scan result in HTML format.
Note
In the preceding commands, we used the --api-key parameter. To retrieve your API key value, go to the Tools | Options | API menu in your ZAP tool instance.
If we use Azure DevOps as a CI/CD pipeline platform, we can use the OWASP Zed Attack Proxy Scan task of Visual Studio Marketplace, which is available at https://marketplace.visualstudio.com/items?itemName=kasunkodagoda.owasp-zap-scan. If we have an Azure subscription, Azure Pipelines can also run ZAP in a Docker container, hosted in an Azure Container instance, as explained and detailed at https://devblogs.microsoft.com/premier-developer/azure-devops-pipelines-leveraging-owasp-zap-in-the-release-pipeline/.
If we're using Jenkins as a build factory, then look at the following article, which explains how to integrate and use the ZAP plugin when you're running a job: https://www.breachlock.com/integrating-owasp-zap-in-devsecops-pipeline/.
We've just learned how to perform security tests on our web applications with ZAP, which is developed by the OWASP community. We looked at its basic use via its graphical interface and performed security tests on a demonstration application. Then, we saw that it is also possible to automate its execution with zap-cli so that we can integrate it into a DevOps CI/CD pipeline.
Now, let's learn how to do performance tests with Postman.
Running performance tests with Postman
Among the tests that need to be done to guarantee the quality of our applications and ensure they are functional, including code analysis and security tests, there are also performance tests. The purpose of performance testing isn't to detect bugs in applications; it's to ensure that the application (or API) responds within an acceptable time frame to provide a good user experience.
The performance of an application is determined by metrics such as the following:
- Its response times
- What resources it uses (CPU, RAM, and network)
- The error rates
- The number of requests per second
Performance tests are divided into several types of tests, such as load tests, stress tests, and scalability tests.
Many tools are available to perform performance tests. The following article lists the 15 best ones: https://www.softwaretestinghelp.com/performance-testing-tools-load-testing-tools/. Among the tools we've already seen in this book, Postman is not a dedicated tool for performance testing, especially since it focuses mainly on APIs and not on monolithic web applications. However, Postman can provide a good indication of the performance of our API.
We discussed its usage in detail for API testing in Chapter 11, Testing APIs with Postman. When you're executing a request that tests an API in a unitary way, Postman provides the execution time of that API, as shown in the following screenshot:
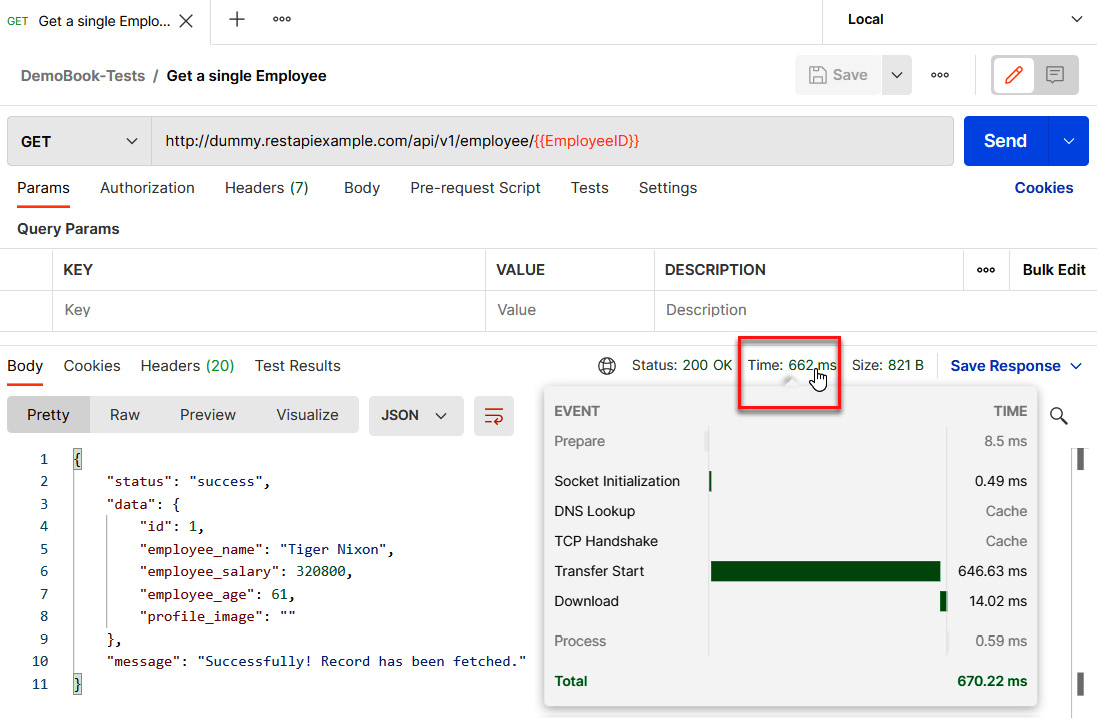
Figure 13.5 – Postman performance test
In addition, in Postman's Collection Runner, it is possible to execute all the requests of a collection and indicate the number of iterations; that is, the number of times the runner will execute the loop tests. This simulates several connections that call the API, and it is also where the execution time that's rendered by Postman becomes very interesting.
The following screenshot shows the configuration of Postman's Runner with several iterations in the input parameters:

Figure 13.6 – Postman Runner configuration test
The following screenshot shows the results of the runner:

Figure 13.7 – Postman Runner test results
Here, we can see that the runner displays the execution time of each request, which means we can identify overload problems on an API.
Now that we've learned how to perform performance tests with Postman, let's summarize this chapter.
Summary
In this chapter, we looked at how to use ZAP, a tool that's developed by the OWASP community to automate the execution of web application security tests. We also saw how Postman can provide information on API performance.
In the next chapter, we will continue to talk about security and DevSecOps by learning how to automate infrastructure testing with Inspec, how to protect secrets with Hashicorp's Vault, and using Secure DevOps Kit for Azure to check the security compliance of Azure infrastructures.
Questions
Answer the following questions to test your knowledge of this chapter:
- Is ZAP a tool that analyzes the source code of an application?
- In Postman, what is the metric that allows us to have performance information?
Further reading
To learn more about what was covered in this chapter, take a look at the following resources:
- Learn Penetration Testing: https://www.packtpub.com/networking-and-servers/learn-penetration-testing
- Pluralsight videos about OWASP and ZAP: https://www.pluralsight.com/search?q=owasp
