3
Ways That Attackers Reveal the Privacy of Individuals and Companies
In todays digitalized world, most of the information are exposed without individuals and companies’ knowledge. This has become a new landscape which presents new risks and threats to individuals and companies that must be remediate. Otherwise, exposed information can be increasing the attack surface and attackers can take the benefit. Let’s deep dive into the ways that attackers obtain this information by over exposure. As explained in earlier chapters information has become power and currency.
This chapter explains how attackers revealing privacy of individuals and companies. In this chapter you will be able to understand:
- Cyber exposure index
- Everything exposed in cyberspace matters
- We don’t need to enter our real information always
- Facts we shouldn’t be disclosing
- Social media matters
Cyber exposure index
Cyber exposure index provides indicative value of how much information a company has exposed based on sensitive disclosure, exposed credentials and hacker group targeting. Cyber exposure index is defined based on the data collected from publicly available data sources in the dark web, on the deep web, and in data breachers. Cyber exposure index shows how the company is ranked based on the following variables:
- Sensitive disclosure – Typically sensitive disclosure regulated by laws and policies and never be stored on the devices or shared without proper authorization as sensitive information consist of confidential data, trade secrets, business plans and other valuable information. When the sensitive data disclosed, disclosed information can be used for identity theft and other attacks.
- Exposed credentials – Usually exposed credentials can be usernames, passwords, tokens, or any other forms of identities that provide access to critical systems. This can be critical as exposed credentials are the mostly used way of compromising systems and provide hackers with access to critical systems. Attackers can collect credentials from compromised systems, information leaks and other attacks including social engineering.
- Hacker group targeting – Hacker groups are organized gangs or communities that can actively share stollen credentials and other information among them and launch collective attacks. Mostly these attacks can be launched from different geography’s that makes harder to traceback the real locations. Also, they can collectively launch distributed denial-of-service attacks to bringdown the cooperate and critical systems which prevents legitimate users access to the systems.
there are various ways that individuals and organizations expose their sensitive information to public sources unintentionally. This can be used by attackers for their benefits by launching direct attacks or use them for indirect attacks. Unintentional information exposure can happen through WHOIS records, Email addresses, Contact numbers and various other ways.
WHOIS records
Organizations and individuals often overexpose sensitive information intentionally or unintentionally. WHOIS records are publicly available information on internet entities. A company or individual can obtain a domain, and domain registration related information publicly available. By running a simple query or using an online tool, attackers can easily collect this information and use them for malicious activities. If you use online service www.who.is and search for preferred domain, it will return you the information including registrant contact information, administrative contact information and technical contact information. This information may be personnel contact information:
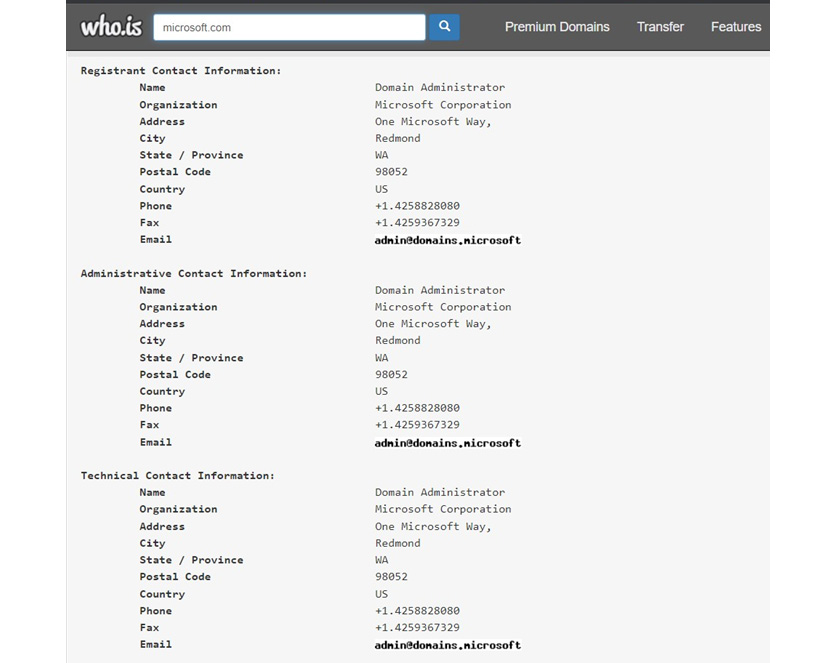
Figure 3.1: whois search for Microsoft.com domain
As you can see WHOIS database query shows the information related to the internet resource including contact information and organizational information.
You can prevent disclosing personnel information on WHOIS by enabling WHOIS privacy controls. If the domain service provider provides privacy controllers, we can prevent disclosing personally identifiable information. You should avoid entering false information on WHOIS data as it can revoke ownership for the domain. Best option is to enforce privacy controls to WHOIS information for the domain. Apart from that there are many other concerns that we should prevent disclosing our information:
- Increasing spam – if the email address is visible on the WHOIS record, it increases spams as spammers can easily collect authentic email addresses from WHOIS records.
- Entity mapping – when your information disclosed on the WHOIS database, attackers can map you with other information sources including social media and collect more information about you and map them to other attacks.
- Identity theft - when the authentic information is publicly available attackers can easily use them for Identity theft related attacks.
- Disclosure of the ownership – WHOIS records discloses the ownership of the site. Attackers can launch spier phishing attacks and more targeted attacks when the ownership is disclosed.
Considering these factors enabling privacy control and protecting from public disclose will prevent many attacks. Enabling privacy controllers is not expensive. Domain privacy controllers service fee is not very expensive. Most of the service providers provide these services for less than 20$ per year.
Email addresses
Email is one of the most used piece of personnel information for many requirements. Specially creating social media accounts, registering for government services, registering for banking services and many more. When using same email address to multiple services, it introduces a risk. One of the known risks is compromising email address can provides access to all the services. When registering to blogs, newsletters, and many other types of subscriptions email address increases the visibility to many services. As a result, user might start receiving spam mails, hoax mails, and emails with malicious attachments and targeted to phishing campaigns.
One of the countermeasures is creating email alias. Email alias is creating different email address for same mailbox. When a mail is sent to email alias, it will be received by the user’s primary mailbox. Many email service providers support mail aliases. Some providers only allow limited number of aliases to be created. It’s easy to create, maintain and work as a temporary email address. This reduces the risk of introducing same email address for all the services. Specially for newsletter subscriptions and related temporary services we can use email aliases and later we can remove when not required.
The following are some email alias service providers that we can use:
- AnonAddy – provides anonymous email forwarding.
- Firefox Relay – provides limited number of aliases.
- SimpleLogin – privacy focused opensource project provides email alias.
These services provide alias services where you can protect your inbox from spams, and you can be anonymous in the cyberspace. The following screenshot is a reference to SimpleLogin service:
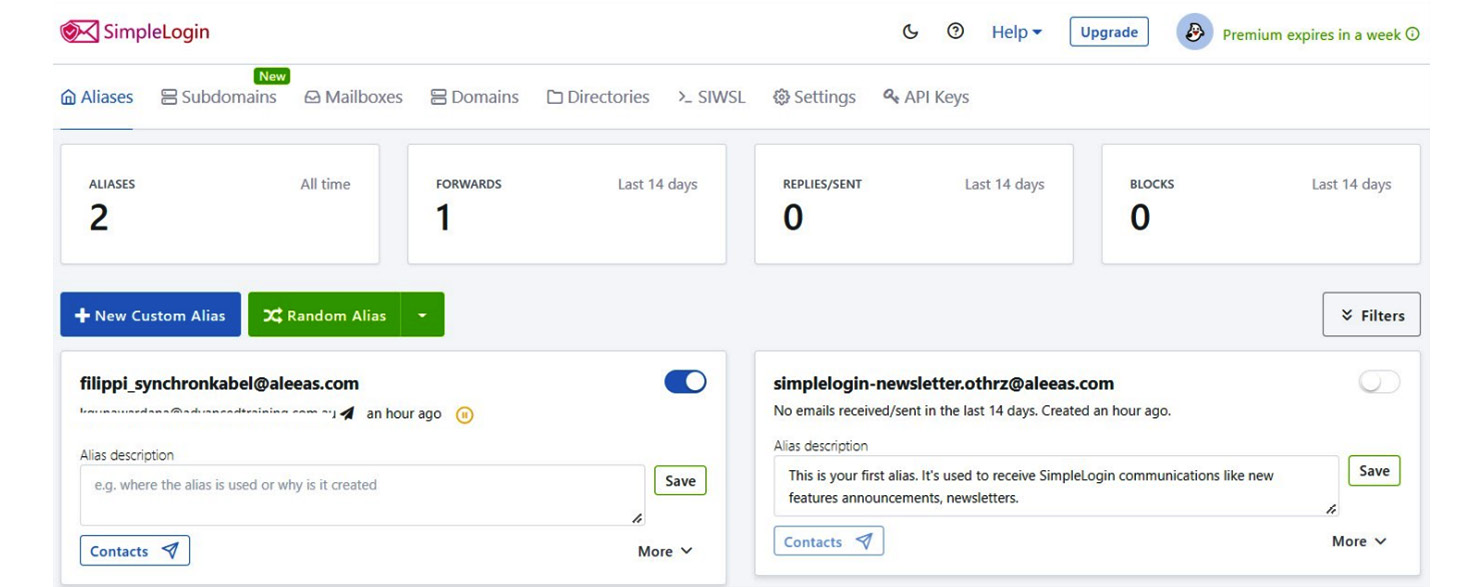
Figure 3.2 – Create custom and random alias using SimpleLogin
As the preceding example shows, SimpleLogin can create custom and random alias to your personnel or official email address to prevent disclosing your real address. These email aliases can be created, enabled, or disabled. This also shows the number of emails received or sent to monito email related activities.
SimpleLogin is opensource project which provides unlimited email aliases. It also offers iOS and Android apps for easy management. SimpleLogin support custom domains and Pretty Good Privacy (PGP) encryption. Additionally, SimpleLogin also provides browser extensions for Chrome, Firefox, and Safari.
If you are using corporate solutions like Microsoft 365 or Google workspace, you can manage this on admin portals and create any number of aliases you need and manage accordingly.
Mobile numbers
After protecting email address from disclosure, another very important personnel record is your phone number. There are many ways that attackers can recover your phone number. The following are some of the common ways that attackers can discover your phone number:
- WHOIS records.
- Social media accounts attackers can disclose phone numbers (Example, LinkedIn).
- From your resumes submitted to job portals.
- Your phone bill thrown out to the bin.
- From your email signature.
- Sending you spam mails and when you reply with your email signature.
It is important to remember that most of your security capabilities relying on your phone number. Even if you have strong passwords and Two-Factor Authentication (2FA) enabled, you are relying on your phone number. Imagine someone who has access to your phone number can bypass anything. For example, anyone who steals your phone number can easily reset your google password just by sending google code. The same technique applies to social media accounts, bank accounts and many others. Basically, the attacker who steals your phone number can virtually become you. As most of the services including government services identify you by your phone number, anyone who has access to your number can impersonate you.
Interestingly we try to protect our bank account numbers, social security numbers and credit card numbers but are we protecting our phone number in the same way? There are ways that attackers can steal your phone number and receive all the calls and text messages sent to your phone number.
Once they get your phone number, they call the service provider impersonating the customer. Most of the telco providers will port out the phone number to different SIM card after they verify you with series of questions. Answers to most of the questions can be found using information gathering techniques. In some countries even attackers can port out the number to different service provider and a different SIM online. In many countries such SIM cards can be bought from supermarkets. When the port out is completed, the new SIM will receive all the calls and text messages sent to the target number.
To mitigate this risk, we need to deploy additional layer of security like 2FA for the phone numbers. The options available are different from country to country and service providers. Some service providers provide different methods like secondary password attached to the number, which is required if you want to port out the number to another service provider.
Another way of protecting your number is using built in feature like blocking the caller ID from your phone. Many operating systems including iOS support blocking caller IDs. Once you make a call, recipient will not see your number. But if the recipient number is not available, some of the service providers send call alert with the caller number even when the caller ID is disabled.
Disposable phone numbers can be used to overcome this. Virtual numbers or secondary numbers are another option to make and receive calls securely. Virtual number can be changed whenever you want. Even you can use numbers from different countries if you use virtual numbers. There are many apps available to obtain virtual numbers. We will discuss disposable, virtual, and secondary numbers in detail on upcoming chapters.
Everything exposed in cyberspace matters
Once we are connected to the internet – which is the case at any given time, everything we share, search, download, access is collected, monitored, stored by multiple entities. These entities can be operating systems, applications, browsers, network connections and even the resources that we access. Even though the public go with I have nothing to hide attitude, hackers, spies and even governments may be interested in all your activities.
This is the reason, some of the countries have built massive filtering systems to monitor and prevent exposing sensitive information. As an example, China has built the Great Firewall of China which is a stronger censorship which prevents access to selected foreign websites and slowdown cross border internet traffic. Using this link, you can check which websites are blocked in China, https://www.greatfirewallofchina.org/. This will make accessing censored website more difficult from China using censorship circumvention technologies like VPNs for the blocked websites including Facebook, Twitter, Google and YouTube.
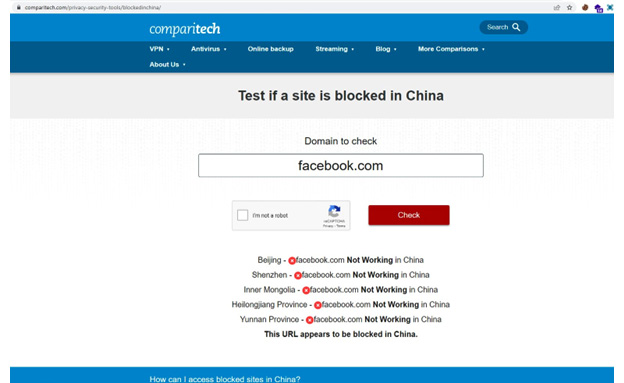
Figure 3.3 – greatwallofchina.org showing the blocked websites in China
Internet activities monitored in different levels including Internet Service Provider (ISP) level; all internet activities can be monitored by ISP. Even ISP level attacks can be conducted by the attackers and the services can be hijacked. This is not a common attack but the sites you visited can be tracked by the cookies. Cookies are small piece of text data created by the web server or web application within the web browser and stored in the device you access the website. Typically, cookies are used to provide better internet experience including items suggestions on a sales catalog like eBay. Once you search for a specific item, this information stored in cookie session data, and later the web application can refer to the previous data and suggest you a similar item. Also, cookies are used to target users for tailored advertising.
Exposing an email address
Generally, we think our email address is something that we can share freely with everyone. But we’ve forgotten our email address is the entry point for most of the services we use to access including social media and banking. Mostly our email address is an identity for many other services. It’s not a surprise that attackers try to compromise email addresses. If we compare this act with previously discussed hacker phases, finding the email address of a target can be treated as an information gathering. If an attacker knows your email address, that increases attack surface.
As a countermeasure we can use multiple email addresses and share relevant email address when required. Specially email address connected to your sensitive services must be kept confidential. And keep separate email address to social media, blog posts and other services which reveals your email address to public. This is the reason, attackers interested in finding email addresses posted in internet, there are ways that attackers can find email addresses posted in social media.
As an example, let’s say you want to find out people who are working as HR managers with Gmail address published in LinkedIn can be recovered by running simple Google dork that we discussed earlier. We will discuss Google dorks in detail in Chapter 5, Tools and Techniques That Attackers Use. But as of now you will see, when executing below google dork will output list of profiles in LinkedIn, working as HR Managers and has gmail.com email addresses on their LinkedIn Profiles. In the same way you can change the criteria and list out profiles with email addresses published based on the job title, country, language, and various other type of attributes published on LinkedIn.
The following statement shows a Google dork crafted for the criteria we discussed:
http://www.google.com/search?q=+"HR+Managers" -intitle:"profiles" -inurl:"dir/+"+site:www.linkedin.com/in/+OR+site:www.linkedin.com/pub/ "*gmail.com"
If the email address is Gmail, and if the email address is published on LinkedIn, attackers can simply list all LinkedIn users within the criteria defined, then attackers can copy all the google findings and use online email extractor services to extract only the email address from the copied text. As an example, attackers can use https://email-checker.net/extract-email. Attacker can select all the content or simply pressing (ctrl + A) to select all Google search result and paste it on this service and click extract email.
This tool extracts email addresses from the text data. Similarly, there are different types of tools that can extract specific data including contact numbers, locations, first name and last name.

Figure 3.4 – Email extractor extracts only the email addresses from pasted text
This online tool then extracts email addresses in the text, same technique can be used by the attackers to extract email addresses on websites, blogs, and other resources.
Other than commercial and online tools attackers commonly use grep tool in Linux to extract information using regular expressions. Command grep supports regular expressions.
The following command will extract email addresses from a text file call junk_text.txt:
grep -o '[[:alnum:]+.\_-]*@[[:alnum:]+.\_-]*' junk_text.txt[[:alnum:]+.\_-]*@[[:alnum:]+.\_-]* is a regular expression that matcher email addresses.

Figure 3.5 – Email addresses extracted
Not only email addresses, but attackers are also interested in your phone numbers or any kind of other contact details as well. Later attackers can use them to launch social media attacks. Some targeted attacks, attackers impersonate service providers and try to change phone numbers using social engineering techniques. Then they can even bypass multifactor authentication One Time Password (OTP) if successful.
African emperors’ treasure
The famous Nigerian Prince story is one of these techniques to collect authentic information that can be used for attacker benefits. Attackers contact random contacts and send emails claiming the sender is one of the great grandsons of African emperors and looking for someone to transfer his/her inherited treasure and asking information including full name, contact number, email address and bank account information. Sometimes they even attach a picture of them to make the story real. Some users share their information as they believe the story or sometimes, they think that no harm sharing information with the recipient. Users often think if the story is true, I will get the money, even if the story is not true there will be no harm.

Figure 3.6 – Sample for similar attack requesting information to transfer huge fund
But for attackers’ point of view information is the most important part. When they get authentic information about full name, contact numbers, email address, postal address, and banking information, they can easily impersonate you to the bank. By impersonating you, they can request bank to change the postal address and request for ATM cards. When the bank sends out ATM cards and PIN numbers to new address, attacker can withdraw cash from your ATM card, or they can purchase online services or buy crypto currency using your card. Usually, attackers change your postal addresses to commonly accessible postal addresses. For example there are apartments with insecure and unprotected post boxes located in the ground floor or share insecure common post boxes. When the attackers found these types of unattended and unprotected postboxes, they can use them to redirect important letters to unattended postboxes and collect them without noticing to anyone. Then attackers changes the postal address of the target to this type of unprotected postboxes, they can collect the postal mails sent to the target user without noticing anyone.
Nigerian prince story and similar attacks are types of information gathering where attackers collect legitimate and authentic sensitive information for their benefit. Attackers use this information to launch direct attacks or to be used for indirect attacks. Maltego is a commonly used tool among Penetration testers, Security researchers, forensic investigators, and hackers, for information gathering. We will discuss in detail about Maltego in the Chapter 5, Tools and Techniques That Attackers Use.
IP addresses
We use IP addresses to communicate with the devices connected to network. Devices can have different form factors and different operating systems. We use private IP address to communicate with internal devices and we must have public IP address to connect to internet. If you have multiple devices connected to your home network, typically all the devices go through single public IP address assigned to the router. Public IP address is assigned by ISP. Your IP is your path to internet. All the communication will go through the public IP address. Public IP address can be assigned dynamically or statically. Static IPs usually assigned for specific services like web server to publish web service. Generally, home connections use dynamic IP addresses. Dynamic IP addresses are changing frequently but static IP addresses will not be changed.
If you open command terminal window and type ipconfig or ipconfig /all will show your internal IP information.
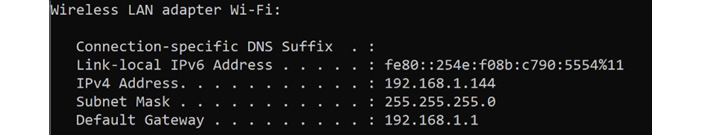
Figure 3.7 – Internal IP configuration
Attackers are more interested in your public IP than your internal IP as Internal IP address is only useful within the network. You can find your public IP address by just opening your web browser and typing whatsmyip on the google search or accessing https://ip4.me website.

Figure 3.8 – Public IP configuration
Your public IP address is the path to locate you even if it does not expose your personnel data. Often public IP is not treated as PII hence companies does not take extra precautions to conceal public IP.
If you are connected to the internet via home router, your public IP address is associated to the WAN link. Often attackers use multiple ways to extract your public IP including:
- Email communication – some email providers does not mask your public IP, when you send email, attackers can obtain your public IP by analyzing email header.
- Online advertisements and accessing websites – when you access a website or click online advertisement it collects your public IP.
- Internet sharing and torrents- when you are part of file sharing or torrents, your peers will see your public IP address.
Your public IP address will not reveal your personnel information, but attackers can obtain location information by IP address as your ISP assigns your IP address. If attacker collects your Public IP address, attacker can:
- Attackers can use your public IP address to ban you from some services including online games and emails.
- Your IP address reveals your location.
- Attackers can use your public IP address to impersonate you.
- Your will be framed for crimes that you never performed.
- Can try to compromise your router and gain access to internal services and information gathering.
When an attacker knows your public IP address, they can scan your IP address and try to find the device that is connected you to internet and open ports and running services of the device. Most of the ISP’s configure devices with default passwords, attackers can try to access your route through WAN link. For an example if the attacker enters your public IP into a browser, typically attacker can see the login information of the router.

Figure 3.9 – Login screen of your home router over the public IP
Then attackers can try to obtain access to the router using default passwords assigned to this router model or using password cracking techniques. If the attacker successful, attacker can find information of the connected devices, users, MAC addresses of the devices and even your SSID passwords.
We don’t need to enter our real information always
As described earlier, any information shared in the cyberspace matters. We never know what types of Open-source intelligence (OSINT)sources have access to them. Anything shared on social web applications, blogs, or even simple email can increase attack surface. Often, we disclose personal information like full name, postal address, email address, hometown, mother’s maiden name unnecessarily. On the other hand, by using accurate information we are risking ourselves.
Let’s say there is a document that you want to download from a social site, but it demands to register to get you access to the download link. During the registration process it often required your full name, address, contact number and the email address. Your only intention is to download the document, but it is required to register by providing all these information to get the link. Do you think it is necessary to provide accurate information to get download link? Probably, this can be an attacker’s trap to collect your information. This can be social engineering attack. Download link can be either fake or real. But it required to provide your information to get the link.
Let’s see the ways to overcome this kind of an information leakage. We can typically provide false information on full name, home address and contact number but email address is the challenge as often the link will be sent to your email address. We will take this question in two parts; one is to provide your information. There are many sources that provide test data to be used in this type of situations without providing your real data. https://dlptest.com/sample-data is an example for a public data source to provide sample data:

Figure 3.10 – Publicly available test data
This site provides sample data including full name, Social Security Number (SSN) – unique identifier assigned for US citizens to track income and other government benefits), date of birth and credit card information.
Next challenge is providing your email address as without email address you will not receive download link or activation of your account. One method is to create temporary email address or email address with false information and can be used to this type of temporary registrations. We can use free email address provider to create a temporary email address like Gmail, Yahoo or Live. But these email providers often need another email address or your contact number to create temporary email address for you. Some of the email services like https://protonmail.com/ and https://www.mail.com/ can be used in some countries without additional information to create temporary email address. Other option is to use disposable email address.
On the other hand, providing accurate information when not required can increase attack surface. For an example when you provide answer for security question to reset the password for your personnel email address, you are risking your credentials. Some of your personally identifiable data are not confidential for your close circle. If you look at PII data including your full name, your postal address, email address, contact numbers is known by your friends and relatives. Sometimes your mother’s maiden name, date of birth and even your passport number and your identity document information may not be confidential to your closer complainants. Let’s assume, security question to reset your password is mother’s maiden name. If one of your close relatives wanted to reset your password, its super easy as they know about your mother’s maiden name. That’s the reason, we should not be using accurate information when not required. Specially for the security questions we shouldn’t be using our accurate information. This information only required when you need to reset your password if forgotten. The question will be, if you forgotten your password, we should know the answer to the security question to reset it, if you provide inaccurate information how you remember what you provide in your security question. If you think about this in smarter way, probably you can use your partners information as yours when answering security question, so if required you remember whose information you have used.
Best way to protect your credentials is to enable 2FA or MFA to protect your credentials. 2FA/MFA uses any of the two from something you know (Password, PIN), something you have (Mobile phone, hardware key) and something you are (biometric authentication).
In today’s world many users have multiple account information to remember. When security administrators enforced password complexity policies on the credentials, for the users it’s hard to remember. Most of the users use same password for multiple accounts which is not a good practice. As we discussed earlier, if the same password used, attackers can find out multiple account used by the same user and if the one account is compromised, attacker can compromise all the accounts connected to the same user.
Solution is using password manager to keep all the credentials and secure the password manager database using master password. There are many password managers including:
- KeePass
- LastPass
- Bitwarden
- 1Password
- Dashlane
- Keeper Password Manager
The following is an example of KeePass password manager:

Figure 3.11 – KeePass opensource password manager
KeePass is opensource password manager with secure and stronger encryption algorithms including AES-256 to protect your credentials. Whenever required you can decrypt and copy credentials and paste it on the applications. This can be used as a solution for keyloggers. If you are looking for online solution, you can use Bitwarden, which is opensource online password manager which supports most of the latest browsers. BitWarden uses encrypted vault to keep credentials. BitWarden can be used to create stronger passwords as an additional functionality. BitWarden is free for personnel user with single username, but for professional and enterprise they have separate licenses:

Figure 3.12 – BitWarden open-source online password manager
There are many tools and online services which can generate information that can be used without revealing your real Personally Identifiable Information (PII). When you use the information generated by these tools will prevent exposing PII to untrusted entities.

Figure 3.13 – Fake name generator to generate personnel information
Fake Name Generator is an online site that generates fake name and personnel information based on gender, name set and country. It generates interesting set of information that you can create a fake identity without revealing your real PII. Same tool provides option to create bulk identities if you want multiple identities:

Figure 3.14 – FakeINFO can generate vast range of information
FakeINFO is another online resource where you can generate broad list of personnel information including usernames, addresses, fake driver license, addresses and company names depending on your requirement. Then you can use the information whenever you need to enter in untrustworthy websites, blogs, or any service which will make your personnel information available in public internet.
Also, the same website can be used to generate fake social media outputs including WhatsApp chats, Facebook chat and YouTube channels.
From these sources we can understand that we shouldn’t be disclosing our real information always as most of the sources can make our personnel information available in public sources that attackers can obtain quite easily. We should be reducing our footprint on the public internet if you wish to reduce attack surface and the risk on our personnel and sensitive data.
Facts we shouldn’t be disclosing
Now it has come to a point where posting, or sharing anything online, sharing by email or social media can introduce new threats. As we discussed before, it can increase the attack surface. It’s always good to think before you post or share anything on the internet. Main reason is anything you post, or share can be seeing by anyone. As we discussed in the previous chapters, sharing sensitive and PII is risky and should be avoided. Along with that, consider removing your name and contact information published on websites and public records.
Remove personnel information from WHOIS
Often, we use personnel information in DNS registrations and other public databases. Without our knowledge this information can be collected by attackers using OSINT techniques. Typically, WHOIS records contains registrant contact, administrative contact and technical contact which contains personnel information. We can use privacy controls to mask personnel information from WHOIS.
Image meta data
When sharing photos, meta information attached to photos can go with them including GPS location and other information as we discussed previous chapters. There can be targeted and untargeted social engineering attacks which can collect sensitive information without your knowledge. We shouldn’t be sharing images anywhere including social media without removing the meta information embedded to the photos. On the first chapter we discussed how much information can be extracted from an image. We can remove meta information from any image using windows settings or there are many tools available to do that. If you want to remove personnel information from an image, if you are using Windows operating system, you can right click the image and go to properties. Then click on the Remove properties and Personnel Information link and you can remove selected attributes, or all meta information form the image:

Figure 3.15 – Remove properties and personnel information from an image
Using this option, we can remove properties and personnel information. You can remove selected information or all meta information on an image. This method can be used to remove information form a selected image. There are tools that you can use to remove meta information from bulk set of images at one go. You can download the Exif Purge tool from http://exifpurge.com:

Figure 3.16 – Remove properties and personnel information from set of images
Disposed devices
We often dispose devices or donate devices after years of usage. Sometimes we sell used devices including mobile devices. These devices contain heaps of personnel and sensitive information. We delete data before the disposal. But can we be certain that the data cannot be recovered? There are many tools available to recover data even from deleted partitions.
Commonly used media to store data are hard drives. Typically, digital media stores data as a sequence of 1s and 0s in magnetic media. Data removed by common techniques like data deletion can be easily recovered. Usually, the operating system deletes the reference to the file when file is deleted but the real data never get deleted. Deleted references can be easily created by data recovery tools. This can expose personnel and sensitive data. This has created risk every time we delete confidential data. We think that we deleted data, but in reality, data cannot be deleted, only can over written.
If you really want to remove data to the extent that attackers will never be able to recover, we need to overwrite data completely and multiple times as there can be techniques that attackers use to recover data. Following are some standards for sanitizing media:
- Russian Standard: GOST P50739-95
- German: VSITR
- American: NAVSO P-5239-26 (MFM)
- American: DoD 5220.22-M
- American: NAVSO P-5239-26 (RLL)
- NIST SP 800-88
Driver eraser is one of the tools that is available to securely remove data according to the standards.

Figure 3.17 – BitRaser securely wipe data beyond recovery
Even though data wiping software claims that they remove data securely to unrecoverable state, many organizations still prefer hard disk shredders to physically destroy data.

Figure 3.18 – Hard disk shredders to physically destroy data
Hardware shredders physically destroy data by spreading hard drives to small particles where any of the data recovery tool cannot recover. Many cloud service providers use this technology to shred hard drives when they wanted to replace damaged or older drives with new ones as they must comply with compliant standards.
Unsecured cameras
As we discussed in earlier chapters, attackers can use device search engines like SHODAN or Google to find internet connected camera systems. For an example if you search intitle:"Blue Iris Remote View" on Google, you can find plenty of cameras that you can view without any credentials. These cameras can be viewed without any credentials. Some cameras installed in common areas, and some are even in private stores. This type of devices can expose personally identifiable information to attackers:

Figure 3.19 – Simple Google dork connects to live camera feed without credentials
When you use google dorks to search, these devices can be accessible by anyone, and any piece of information exposed can be used by these devices can be used by the attackers against you.
Social media matters
Social media has introduced a paradigm shift in communication and interaction with family, friends, and colleagues. Social media has become a part of social life as most of us can interact with our closer circle of friends, relative and colleagues irrespective of the physical and geographical boundaries. Even though social media platforms including Facebook, LinkedIn, Twitter has introduced revolutionary change of communication and introduced many benefits, they also pose significant security and privacy risks to companies, organizations, and individuals. Most of the organizations and individuals are on one or more social media platforms due to their popularity and various benefits.
Concerns on social media
Social media can increase attack surface acting as vulnerable platform for the attackers to launch various types of attacks. Some of the serious concerns when using social media can be as follows:
- Data privacy and over exposure – Users often share their information without masking on social media can cause privacy breaches. Most of the social media platforms default privacy setting is Public, meaning is anyone on the same platform can view users’ information including shared images embedded with metadata.
- Malicious and third-party applications - most of the social media platforms allow users to integrate third-party applications. Third party applications can be gaming apps, communicating on apps, location related apps and many more. When the third-party app is integrated, there is a possibility that third-party app can access your data. Most of the apps request your permission to access your information including contacts and location information. But there can be malicious app running in the background can access your personnel information without your knowledge.
- Data mining – Most of the social media platforms perform data mining by the information collected during the registration or after the registration including your name, location, age, date of birth and your behavior. This information will be used by the platform for targeted advertising. Even your behavior patterns, can be used for targeted advertising.
- Malware attacks – malware attacks can be performed over the social media in multiple ways including shared links, shared files, link redirection, pop-up windows, or advertisements.
- Impersonation – Attackers can create fake profile of an internal employee and send friend requests to other employees and can be a part of many important groups to collect information. This can happen to individuals in a similar way, creating fake profile impersonating your friend, then start chatting or through messages collect information and share malicious links. Others trust the links shared as the profile impersonates a known and trustworthy person. Then people assume attacker is internal employee and share confidential information without suspecting. This attack can be performed in WhatsApp groups, Viber groups and Google groups.
Risks involved with social media
When using social media, there are range of risks involved. Social media is a gold mine for scammers. There have been many social media scams through which organization and individuals lost their privacy and collectively lost billions of dollars. There are many common scams, but attackers use different techniques to lure users for the scams:
- Banking and payment services scam – scammers will send you a fake banking link or payment service link to perform transaction tricking you to enter your information including bank credentials.
- Lottery and gift card scam – users receive congratulations message on their email or social media, stating you won a lottery and ask you to enter information including banking information to transfer your winning price. Often attackers might request you to transfer small amount as administration fee to get bigger lottery amount of gift card.
- Romance scams – This is a fraudulent act performed by scammer pretending romantic interest in the target. This includes stablishing relationship and maintaining it for some time. After the required level of trust is gained, scammer might attempt to get money for convincing reason or collect sensitive information. Sometimes scammer will send you some gifts or photos to gain high level of trust. Often, they will pretend that they are going to book tickets to come to see you. Also, scammer will pretend that they need some money for personnel emergency like surgery for their mother and try to get funds from the target.
- Forex scammers - Often scammers would try to create your interest in forex trading by convincing screenshots and trying to influence you indirectly. Some scammers introduce other fraudulent scammers as forex account managers and try to get your information and money. There are chat groups convincing new users to the group, most of the members are scammers and they try to influence others to invest on fake forex services.
- Escort scammers – scammers pretend that they provide escort services and share advertisements on social media like Facebook pages, WhatsApp groups. Often, they advertise on personnel classified pages in web portals like https://www.locanto.com, https://www.skokka.com with contact information. Mostly they encourage text and WhatsApp messages. When the interested people contacted, they share fake photos, services offered and their rates. Once both parties agreed, scammer will demand a half payment to confirm the booking on payID (payID is a unique identifier linked to attackers mobile or Internet banking) Depending on the country there are similar payment methods that can transfer funds almost instant as mobile cash. When the half payment is made, scammer disappears or block your number.
- Social media account disabled scam – scammers send an email to the target, stating that they received a request to disable your account or account is already disabled. To activate your account scammer will request your personnel information or they will provide link to enable your account providing sensitive information. Both ways attacker collects your sensitive information.
Solutions for the risks introduced by social media
Not only scams, but there are many other risks including Cyber stalking, Cyber bullying, and Cyber terrorism exist on the social media. There are solutions to minimize the risks that involved with social media:
- Protect your credentials – Create a strong and complex passphrase (Combination of upper case, lower case, special characters, digits and more than eight characters), enable 2FA/MFA if possible and never share passphrase with anyone. Consider using password manager or vault.
- Treat social media as showcase, everything that you share matters. Be sensitive on everything you share. Never share personnel information or sensitive information on social media. Think again before you share images. Often images carry more information than we think. We discussed metadata but images may directly carry information in the background. As an example, a couple posted selfie taken during the candlelight dinner may include the credit card they use to settle the bill still on the table or photo taken in the office wearing your office access card can provide enough information for an attacker to duplicate the card.
- Common sense – This is the best way to protect yourself from scammers. Most of the scams are too good to be true. Simply, you can’t win a lotter that you never entered, or you can’t receive a courier that you never ordered. No one will give away hundred iPads to celebrate their anniversary without any gain. You will never receive anything by doing nothing.
- Reduce the information you disclose over the social media - Consider using alias than using full name in social media. Consider using separate email address for social media. Try to prevent disclosing your home address, work address, phone numbers, contact information on social media.
- Never access your social media accounts using untrusted devices or untrusted networks – never access your accounts by public devices, Common devices in airports and internet cafes.
- Configure privacy settings – consider configuring privacy settings, which reduces exposing your information to public. Depending on the social media platform, these settings are very, typically every social media provide an option to configure privacy settings.
- Don’t blindly accept friend requests from strangers.
- Don’t submit social media surveys require your personnel information even if they claim that there will be a prize for the winners.
- Never download apps via links posted on social media.
- Never share personnel information even if you trust the person as profile can be impersonated.
- Never click suspicious link posted in social media.
Most of the social media platforms available as mobile apps. When downloading app, we need to make sure that the app is downloaded from the trusted app store. Device operating system must be up to date and the App should have the latest update.
Spot potential scams on social media
Most of the scams looks too good to be true. Still the users believe today can be my lucky day and falling to common traps. Most of the social media related scams starts with common friend request. Whenever you receive friend request, better to screen the request for:
- If it is newly created profile with row and limited content.
- Many grammatical and spelling errors.
- Content is very generic, not specific.
- Low number of friends or all of them in opposite gender.
- Try to understand their motive by sending you a friend request unless you have common friends.
- Profile pic looks like a celebrity or face is not properly visible.
- Be skeptical if suddenly they wanted to something that you are interested, and they request for some amount of money. Probably they wanted to book an air ticket to come to your city and they are short of some amount. Sometimes one of their very close family members need to undergo a surgery.
- If they ask you to add them on WhatsApp or Telegram after short chat.
- If they try to convince profitable business which is very much favorable to you.
- If you receive direct messages asking cash, or gift card or crypto currency for a service, or asking cash advances before the service.
Once you accepted the friend request, they are trying to be very friendly in a very short period. Trying to share personnel pics or video of them and encouraging you to do the same. Think before share anything personnel as often attackers may try to blackmail you.
Summary
This chapter explained overexposure and types of exposing personnel and sensitive data even without our knowledge. Everything that we share or post on the cyberspace can expose our information. Always we don’t have to share our real information and there are ways that we can protect privacy without disclosing authentic information. Sometimes we disclose our information that we shouldn’t have disclosed. There are ways to reduce the information that we share online. Social media can be a gold mine for attackers to collect sensitive information of targets without disclosing their real identity and how we can protect ourselves from such attacks.
In next chapter you will learn about the techniques that attackers compromise privacy.
