5
Tools and Techniques That Attackers Use
In the previous chapter, we discussed various techniques that attackers use to compromise your privacy. This chapter will explain the different tools that attackers can use to compromise privacy by gathering information mainly from open intelligence and social media. There are many tools that attackers use to collect information about the target individuals and organizations. As we discussed in earlier chapters, publicly available sources contain a lot of information. Here, we will detail the tools and techniques employed by attackers to effectively collect information.
The following topics are discussed in this chapter:
- Maltego
- Google Advanced Search and dorks
- Uvrx Social Search
- Open Wi-Fi networks
- Phishing sites
Maltego
Maltego is a software developed by Paterva, a South African-based software company, to provide a framework to discover the data collected via open source intelligence (OSINT) and visualize it via easy-to-understand graphical representations. This is a very useful tool, as hackers or penetration testers usually try to collect as much information as possible before moving on to the next step. Maltego is treated as one of the best information gathering and data mining tools currently available. Users can query many types of data integrated with Shodan, VirusTotal, archive.org’s Wayback Machine, TinEye, and MITRE ATT&CK. Maltego uses over 50 open intelligent data sources to provide information. It supports public data sources that you can connect to, as well as commercial data sources.
Maltego is one of the most frequently used tools by security testers, forensic investigators, investigative journalists, and researchers and comes pre-installed in many tiger boxes, including Kali, Parrot Security, and Predator. Maltego is a Java application that is available for Windows, Linux, and Mac in three editions: Community, Professional, and Enterprise. The Community edition is free and has only 5% of the functionalities of the Professional or Enterprise editions according to Paterva.
Maltego can gather information from dispersed data sources. Some versions of Maltego can view up to one million entities on a graph. It can collect information from connected data sources, automatically interlink them based on RegEx algorithms, autodetect entity types to enrich the graphical interface, and use entity weights to detect patterns that can be used to annotate the graph and export it to various formats that can be used for later reference.
Maltego as an information-gathering tool provides real-world links between many entity types. That can be very useful during information gathering as it details relationships that include the following:
- People
- Social networks or groups
- Organizations
- Companies
- Websites
- Internet infrastructure information such as domain names, DNS names, and IP addresses
- Phases
- Documents and files
Maltego reveals links between entities using OSINT. Transform hubs are sources that Maltego uses to acquire information.

Figure 5.1 - Maltego (Community edition)
Maltego uses a range of transform hubs to integrate with many OSINT data providers in its free and commercial editions. Depending on your usage requirements and choices, you can connect free editions of data sources or paid premium editions. As an example, both VirusTotal Public and VirusTotal Premium Application Programming Interfaces (APIs) for integration can be connected with Maltego.
Maltego can create graphs when you perform OSINT for a domain name or DNS system. There is a long list of options available in Maltego to be used as entities including organization, company, DNS name, domain, MX records, URL, website, location, hash, port, people, services, and more.

Figure 5.2 – Entity types in Maltego
Then, you can select any entity type you want to investigate, as shown in Figure 5.2. Let’s say we are going to investigate a domain name. We can drag and drop the entity type to the graph window. If we need to investigate microsoft.com, we can type microsoft.com as the domain name and right-click to get transforms. Maltego has a built-in list of transforms, or we can add transforms using the Transform hub. When you execute the transform, Maltego connects through integrated APIs and collects OSINT information, which is then displayed in the graph window:

Figure 5.3 – Transform types in Maltego
When we click on the play button-style icon in front of the desired transform type, it will start transforming the information and display it in the graph window. Figure 5.4 displays a visual representation of the information collected by Maltigo:
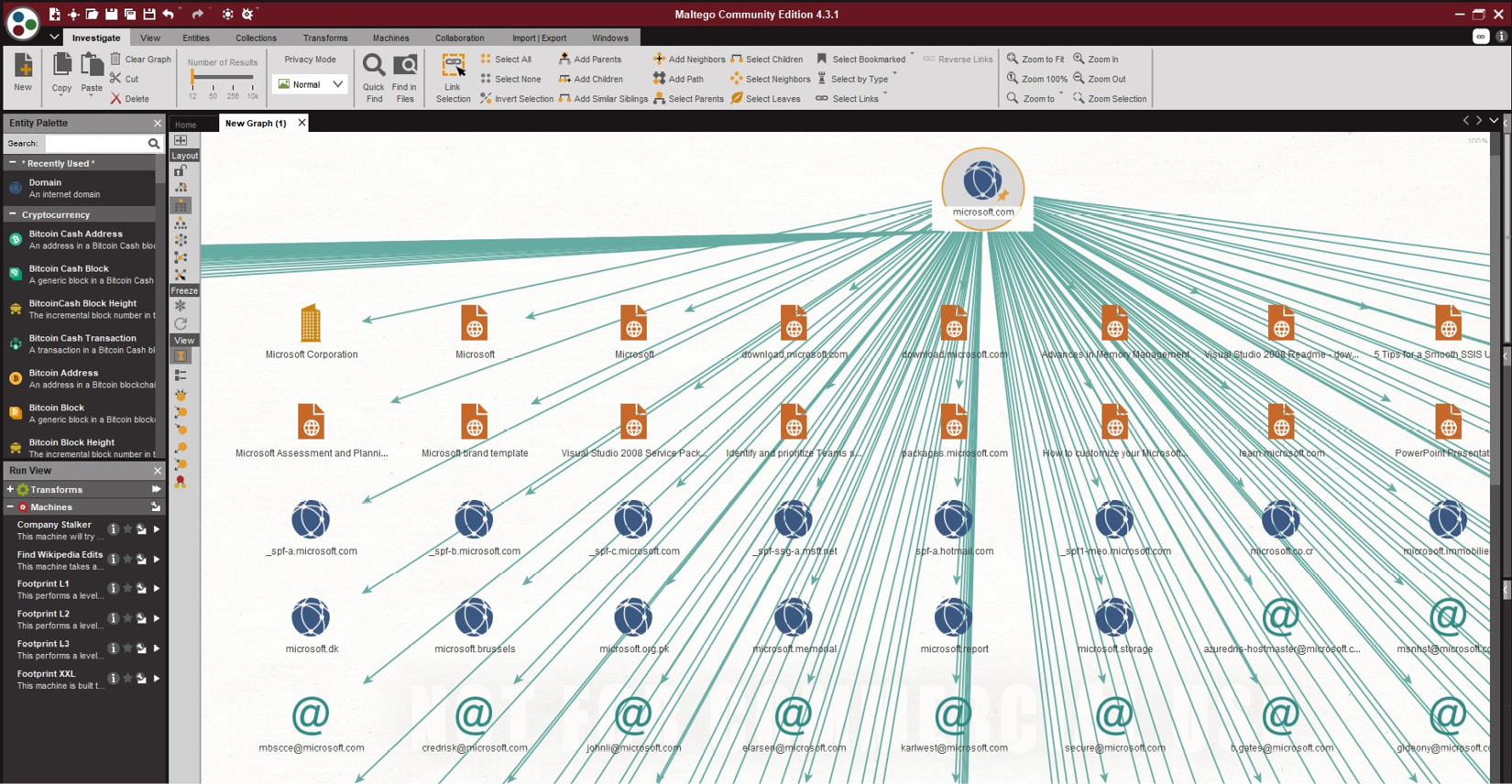
Figure 5.4 – A graphical representation of the information collected using OSINT in Maltego
In the same way, you can use a range of entity types, including email addresses, company names, URLs, and WHOIS data to transform the information of the target using Maltego. If you look at the available entity types and transformation hubs, you will understand how anything exposed to the internet matters. When it comes to information gathering, almost any kind of information exposed to the internet can be used by OSINT sources to collect information and understand the connection between different entity types. This has become very easy now, as Maltego provides visualizations and easy-to-understandable graphical forms, which allow security testers to easily interpret and co-relate entity types.
A Maltego-generated graph can be a gold mine for an attacker, as it provides interrelated information about entities. Especially when planning a social engineering attack or information gathering, this proves useful.
Google Advanced Search and dorks
Google is the most popular search engine, capable of searching through the searchable portion of the internet and providing accurate and most relevant results much faster than other search engines. Google frequently crawls through all the websites in the world and keeps cached copies of the web pages in Google Cache. Then, Google indexes all the web pages according to the keywords. The results we derive from a Google search are not something Google has searched on the go but have been searched and indexed even before you execute your own search. That’s the reason Google suggests you use keywords whenever you start typing a query on Google search.
Dorks
There are ways that we can use the hidden capabilities of Google by employing special syntaxes, which are known as Google dorks, or as Google hacking. Attackers use Google dorks to gather information from the internet using Google Search capabilities.
As an example, let us check what Google has in the cache for www.aljazeera.com. The reason to use www.aljazeera.com to demonstrate this is that we need a frequently changing site to understand that a live copy can be different from the copy that Google has in its cache. We are going to search cache: www.aljazeera.com in the Google Search box:

Figure 5.5 – A copy of www.aljazeera.com with the snapshot information from Google Cache
There is a range of Google dorks that can be used to gather more sensitive information using Google Search. Let’s try to understand some basic keywords that can be used in the Google dorks and then evaluate how to construct more advanced dorks to find out specific information. All Google dorks can be executed in the Google Search box in any popular browser. The following are some Google dorks:
- inurl – This command restricts the search to the URL of the web pages. For example, if you want to search for admin logins, you can use inurl:adminlogin.php. This will list out web pages with admin login in their URLs. All the web pages with admin.php will be listed.
- intitle – This command restricts the search to the titles of the web pages. If you need to view the list of items on a web page, you can use intitle:"index of". This will list web pages with indexed items.
- intext – This command only searches the body text by ignoring the URL, titles, or links. If you want to find the text cyber anonymity irrespective of URLs and titles, you can use intext: "Cyber anonymity".
- site – This command filters the search and restricts it to a single site. As an example, if an attacker wants to search for satya nadella only on www.microsoft.com, then the site: www.microsoft.com "Satya Nadella" command can be used. Google will not search anywhere other than the Microsoft website.
- link – This command returns a list of web pages linking to a specific website or web address. If you enter link: www.microsoft.com, Google will return a list of web pages that link to www.microsoft.com.
- related – This command finds pages related to other pages. If you search related:google.com, it will return a list of search engines.
- cache – If you use a frequently changing URL, you will see the page that Google returned can be different from the real page, as Google keeps a cached copy during crawling. cache:www.microsoft.com will show you a cached copy of the Microsoft home page that Google has on Google Cache servers.

Figure 5.6 – A Microsoft web page cached in a Google Cache server
- filetype – This command searches the filename or extension. You can search based on the filename and search for a specific file type. If you search filetype:htm, you can find a list of files with defined extensions.
You can also combine two search commands. Application filetype:pdf can search applications with the .pdf extension.
The following are some of the many examples of Google dorks that attackers use to find sensitive information:
- inurl:adminlogin.php – This will list out web pages with admin login in the URL.
- inurl:"*admin | login" | inurl:.php | .asp – This will list out php and asp pages with admin login in the URL.
- intitle:"index of" inurl:ftp – This will list out web pages with FTP file structures and indexes.
- intitle:"Login" intext:"IP Surveillance for Your Life" – This will search surveillance system logins.
- intitle:"Blue Iris Remote View" – This will list the “Blue Iris” cameras that are online, mostly without even having to provide credentials.
- intitle:"web admin login" "Huawei Technologies" – This shows admin login pages for Huawei routers and devices.
- inurl:/multi.html intitle:webcam – This shows the web applications with webcams.
- "Username" "Password" "ZTE Corporation. All rights reserved." – This shows ZTE appliance login screens.
- allintext:"*[email protected]" OR "password" OR "username" filetype:xlsx – This shows a list of web applications that has Gmail email usernames and passwords stored in root directories.
- inurl:/wp-content/uploads/ ext:txt "username" AND "password" | "pwd" | "pw" – This shows WordPress (wp) web applications with usernames and passwords stored in an uploads directory.
If you need to find more complex Google dorks, you can refer to the Google Hacking Database (GHDB). This also contains community-developed dorks. Currently, GHDB is hosted at https://www.exploit-db.com/google-hacking-database. This source provides a long list of Google dorks that can be used for retrieving sensitive information using Google Search.

Figure 5.7 – The GHDB with a range of Google dorks
Google dorks are one of the most common ways of retrieving information from a website; even attackers can personalize Google to only perform an advanced search for a specific website by limiting the Google search scope for a single website using site: www.sample.com.
Google search engines crawl through the web pages to collect more specific information to provide an accurate result. If you want to limit search engines from crawling through sensitive directories of your website, you can use “noindex" placed on the meta tag and as an HTTP response header. To prevent web crawlers from indexing a page on your site, you can place the following meta tag into the <head> section of the page:
<meta name="robots" content="noindex">Some developers think that they can keep sensitive directories out of Google Search by placing robots.txt with allow and disallow tags in the file for sensitive directories. However, this is used to avoid page overloading by search engine requests. If you type in any website and add robots.txt, you will find the directories that the crawler can still access. At the same time, the robots.txt file exposes the directory structure to attackers, which can then be used by the attackers for their benefit.
Let’s try to test this by typing www.microsoft.com/robots.txt as a URL into the browser. The browser will display the contents of the robots.txt file as follows:

Figure 5.8 – robots.txt shows the directory structure of the target website
Even though robots.txt provides information to crawlers this way to prevent overloading, attackers use a robots.txt file to understand the directory structure of the web application. That gives attackers the chance to construct specific attacks such as directory traversal attacks. In some cases, the attackers even get access to password files on the server.
Google Advanced Search
Another powerful search built into Google is Advanced Search. You can access Google Advanced Search from https://www.google.com/advanced_search or by clicking on the cog wheel that appears in the top right-hand corner of Google once you perform any search. Once you access Google Advanced Search, it has many advanced features that a basic Google search does not possess. Using the advanced options, you can refine the search the way you want. For example, if you search for something from the United Kingdom, the search result is different from the same search someone performs from Australia, as Google refines the search to the location as well. If an attacker wanted to find out information that is relevant to a specific country scenario, the attacker could use the location in the search criteria as well as other options, including the following:
- All these words
- This exact word or phrase
- Any of these words or none of these words
- Numbers ranging from x to y
- Language
- The last update
- Region

Figure 5.9 – Google Advanced Search helps perform advanced searching
Google Advanced Search is quite useful in case you want to perform advanced searches and refine the results. For example, if you want to search for something that was updated last month or year, you can refine the search accordingly.
Reverse Image Search
Another great feature Google provides is Reverse Image Search. Similar to how you search for a word or phrase, you can use an image to search the entire searchable internet to find a similar image or the same image on different websites. You can perform an image search just by uploading the image to the tool or by providing the image URL. To access Google Reverse Image Search, visit www.google.com/imghp:

Figure 5.10 – Google Image Search helps to find similar images on the internet
These types of techniques are used by attackers to retrieve information from publicly available sources. These tools are immensely powerful, comprising the information available also known as OSINT. As explained in earlier chapters, information gathering is the first step in hacking. Attackers use these tools to uncover as much information as possible, which will make their next steps easier.
Uvrx Social Search
There are huge amounts of data stored on the internet, which is searchable by general search engines such as Google and Bing. The term searchable internet was purposely used in many chapters, as the internet possesses huge space besides a searchable internet, which is known as the dark web. This is not searchable using common search engines. Chapter 9, Avoiding Behavior Tracking Applications and Browsers, will provide more information about the dark web.
Many online file storage systems host large amounts of data separate from the dark web or the searchable internet. Many users make use of free or commercial versions of online storage to store and share files with themselves or between communities. These storage systems may also contain important and useful data.
Uvrx is a very comprehensive search engine initially designed to search online file storage. Currently, Uvrx supports three types of comprehensive searches:
- File Search
- Social Search
- Health Search
Uvrx File Search
Uvrx File Search is a comprehensive online file storage search engine that can be used to search within many popular online file storage services. Uvrx provides individual search engine capabilities for the following online storage services:

Figure 5.11 – The Uvrx search engine can search a range of online storage
Currently, the Uvrx search engine supports multiple languages, including English, Chinese, Japanese, French, German, Spanish, Portuguese, and Russian.
Apart from the individual search engines for the aforementioned online storage services, Uvrx also provides a search all feature, which searches across a range of other online storage providers, such as FileFactory, DepositFiles, EasyShare, sharedzilla, GigaSize, DivShare, Sendspace, YouSendIt, Badongo, MediaFire, zShare, 4shared, Letitbit, drop, FileSurf, Hotshare, USAupload, SaveFile, Bigupload, upfiles, HyperFileShare, Zippyshare, uploaded.to, uploading, sharebee, Rapidspread, Taringa, and more with the search query. Uvrx provides a free service to search across many online storage providers conveniently, rather than having to search individually.
Uvrx Social Search
Uvrx Social Search is a free and comprehensive search engine enhanced by Google that supports searching on multiple social networks. This is a convenient way to search social networks such as the following:
- Myspace
- Plaxo
- Tumblr
- LiveJournal
- Flickr

Figure 5.12 – Uvrx Social Search for Packt
Even though Facebook blocks user information that is marked as private from being accessed, crawled, and indexed by search engines, not all the information on Facebook is marked as private. This can be due to a lack of understanding on the part of the users about privacy, whether mistaken or intentional. Therefore, all information on Facebook including pages, posts, and updates that are set as public can be crawled. For example, currently, Google has over 2 billion Facebook pages in the Google index.
This can be used by various interested individuals, including attackers, who can find out juicy information on Facebook, or users who do not understand how to minimize cyber exposure by using the privacy settings on Facebook.
Uvrx is a great resource for you to understand your status in terms of privacy on social media. If the privacy settings are not properly configured on your social media profile, you can see how much information that you think is personal is actually visible to the public.
You can find out by yourself about this level of exposure by using the Uvrx Social Search engine.
Uvrx Health Search
Many websites on the internet are created for advertising purposes. For example, if you need to find information about software, many sites provide reviews and suggestions. These suggestions or reviews may not always be realistic and trustworthy, as many sites are made-for-advertising. The objective of made-for-advertising sites is to attract users for advertising purposes. These sites are funded by vendors to provide reviews on their products and advertising, depending on the number of page views. We cannot expect neutral reviews from these sites, as they are always biased in favor of the companies that provide the funding. Moreover, made-for-advertising sites flood the internet, as they provide passive income generation for many individuals and companies.
When it comes to health-related concerns, this is more critical. For example, if you are searching for information about a specific illness or a drug, made-for-advertising sites provide biased information that is not trustworthy or reliable a lot of the time.
This makes it very difficult for individuals to find trustworthy, reliable, and unbiased information on the internet. Uvrx Health Search tries to solve this issue by maintaining a list of trustworthy and unbiased websites maintained by governments, trusted organizations, educational institutions, and research organizations.
As an example, let’s imagine an individual is experiencing numbness in their toe. If the person searches this on the internet to find information, websites will produce many different suggestions. Most of these websites are backed by pharmaceutical companies to promote their products. They can even suggest different medicines and ideas that are often confusing. Some websites may say it is a malnutrition issue, some a head injury, or even diabetes. But most of these websites are biased, as they are funded by companies or these companies advertise on them. In these situations, it’s difficult to understand which website will give you an honest opinion. Uvrx Health Search can be a lifesaver in this context.
Open Wi-Fi networks
With today’s complex lifestyles, connectivity has become an essential requirement. Before the 21st century, food, water, and shelter were treated as essentials. Later, electricity became an essential requirement. Now, in today’s world, besides food, water, shelter, and electricity, connectivity has become an essential requirement. This is the reason hotels and restaurants, for example, highlight their connectivity status. If you search for any hotel for your holiday on booking.com or tripadvisor.com, all the hotels show whether they provide internet access.
Most airports, restaurants, libraries, malls, and open areas provide Wi-Fi connectivity, as most individuals cannot stay disconnected. Even long-distance bus services and flights provide Wi-Fi access today as a complimentary service to attract customers.
In Chapter 1, Understanding Sensitive Information, we discussed the layers that are required for communication. If you need to maintain secure communication, we need to protect all the layers. If any of the layers are not secured to an adequate level, communication can be compromised.
What is open Wi-Fi?
Many studies conducted around the world, including those by security research companies such as Kaspersky labs, have revealed that 25% of the world’s public Wi-Fi hotspots don’t use any type of encryption to protect their communication. These hotspots are generally referred to as open Wi-Fi connectivity. The public comprehends this term as open for anyone or a password not being required to connect to the internet. Due to this reason, they are very happy to find these open Wi-Fi networks and connect their devices to them. But the bitter reality is that open Wi-Fi networks do not have any wireless security protocol configured. This allows anyone to connect to the internet using the open Wi-Fi network and an attacker connected to the same network can sniff all the communication if the communication protocol used by the user is unencrypted. When you connect your device to the internet, there are many applications installed in the device to start communication using internet connectivity. These applications may or may not use security protocols. For example, if you configure an email client app installed on your device to use Simple Mail Transfer Protocol (SMTP), the communication is unencrypted unless Transport Layer Security (TLS) is enabled.
This can happen in coffee shops and other open restaurants such as McDonald’s. One of the most frequent questions customers ask is “what’s the password for the Wi-Fi?” It is quite common to see restaurants display Wi-Fi passwords publicly or print them on their invoices. Most restaurants have common passwords or open Wi-Fi hotspots.
Most importantly, every user must understand the importance of the sensitive data they carry within their devices. When connected to the internet, applications can continue communication as usual, even though users think otherwise. Users often think that only the applications that they use are currently connected to the internet, whereas the reality is that any of the applications installed on the device can communicate when connectivity is established.
Risks involved with open Wi-Fi
When connected to open Wi-Fi for communication, everyone should know the risks and threats, as there could be situations where we might need to connect to open Wi-Fi:
- Insecure connections – As open Wi-Fi does not configure with secure protocols, attackers can sniff and monitor your communication. If you connect to a website that provides secure connectivity using Hypertext Transfer Protocol Secure (HTTPS), the connectivity from your browser to the server is encrypted by a key. The browser-generated key is shared using the digital certificate installed on the server:
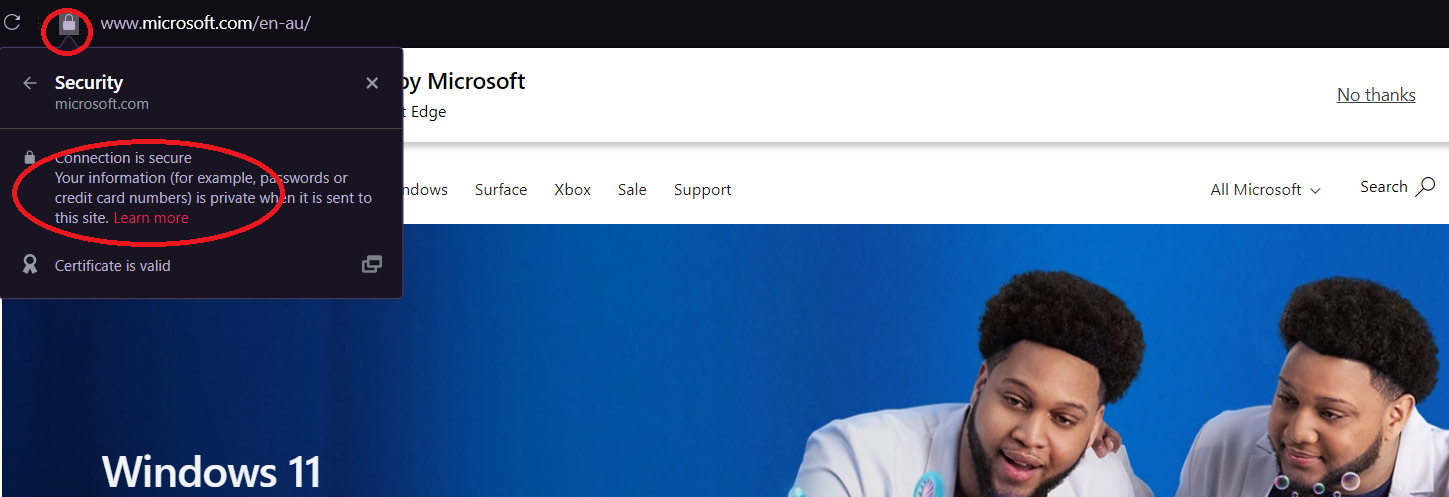
Figure 5.13 – A HTTPS secure connection from a browser to a web server
When the digital certificate is obtained and installed on the web server, it provides a secure connection from the browser to the server. This can be seen on the address bar with the padlock sign (Figure 5.13). When you click on the padlock sign, you can see the connectivity status. If you click on the certificate, the browser will show you the certificate information.
When the HTTPS connection is used on open Wi-Fi, the connection between the browser to the server is encrypted. This reduces the chances of the attacker monitoring your communication, including your credentials.
Not all the websites in the world are encrypted. Unencrypted websites can be detected by browsers and be shown as not secure. This means that when you send and receive information from this website, data sent back and forth is not encrypted. If an attacker is sniffing, they can see and intercept the data, which is in the form of plain text:
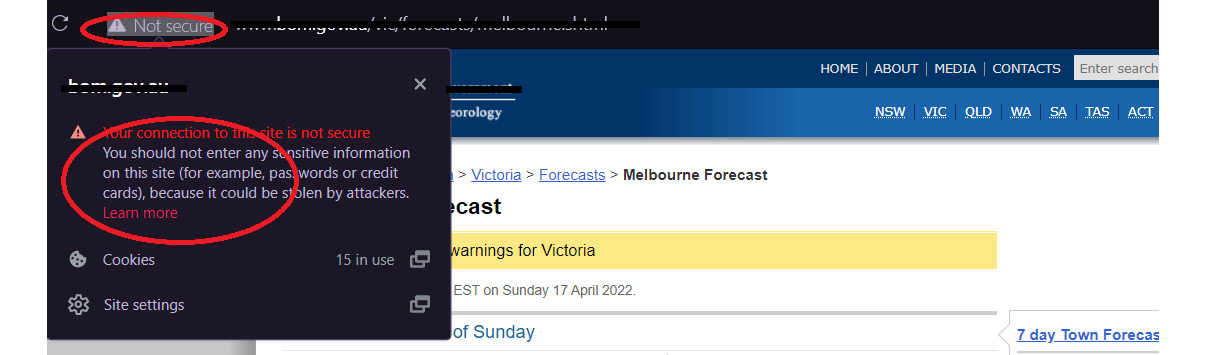
Figure 5.14 – A HTTP insecure connection from a browser to a web server
- Personal information can be theft – This is a very common threat in open Wi-Fi, where attackers collect personal and sensitive information during communication, including the following:
- Login credentials
- Personal data
- Private images
- Financial information
- Confidential information
This can be done simply by sniffing. If you use an unencrypted protocol for communication, attackers can simply sniff your information using a sniffer such as Wireshark. Wireshark is a free and open source protocol analyzer and sniffer that supports various operating systems. Once an attacker starts sniffing, all plaintext information sent through the communication can be sniffed.
For example, let’s use Wireshark to sniff unencrypted traffic. We will use previously learned techniques to find out a website with the following requirements:
- A website that only uses HTTP and not HTTPS
- We need to find the login page
This can be done using Google dorks. Let’s form a Google dork to find a website with these requirements. Here is the Google dork that we created; this may be different from your Google dork, as the same thing can be performed in different ways:
Inurl:http -inurl:https inurl:adminlogin.phpOnce the preceding Google dork is entered on Google Search, Google comes up with a list of web pages matching our requirements. Then, we can select one of the web pages and notice that it doesn’t have HTTPS, and it’s a login page:

Figure 5.15 – A HTTP insecure connection from a browser to a web server
Now, we will run Wireshark by selecting the network interface and start monitoring the traffic. Then we will enter a username and password (yes, we don’t know the credentials, so we will enter random credentials). Let’s check on Wireshark. You can see a lot of information on Wireshark; to search for the exact information, we will use search:
- Select Edit | Find Packet.
- Select String and type POST.
Then, Wireshark will highlight the answer. The reason to search for POST is that it is one of the two methods that web applications can use to communicate with the browser. Typically, the POST method is used by application developers to send credentials back to the web server.

Figure 5.16 – Wireshark collects the credentials from an insecure communication between a browser and a web server
This shows how easily a protocol sniffer can collect sensitive information from unencrypted communication. When you are connected to open Wi-Fi, attackers can easily collect your sensitive information, as shown here.
- Man-in-the-middle attacks (MITM attacks) – Attackers can create a rogue access point (using the same SSID, attackers can create an unauthorized hotspot that they can use to convert their own device into a hotspot) or an evil twin (a cloned access point with the same SSID). If the open Wi-Fi system is present, it’s easy for attackers to launch MITM attacks.
- Organization-targeted attacks – To access confidential organizational information, attackers can use open Wi-Fi. Some organizations use secure encrypted Wi-Fi networks within the corporate network and create open Wi-Fi for the guest users without distinguishing network segments. This configuration provides attackers with the possibility to access corporate networks over open Wi-Fi. Another possibility is that internal employees can often also use open Wi-Fi to bypass any filtering enabled for corporate users. If the attackers are monitoring the guest network, they can often collect confidential information from negligent users.
- DNS poisoning – Once attackers are connected to the open Wi-Fi, they can redirect user connections to the attacker’s desired web applications, including phishing sites, using DNS poisoning. For example, let’s say one of the users wanted to access www.facebook.com. When a user types www.facebook.com into the browser, the browser requests the DNS client of the operating system to resolve the IP of www.facebook.com. Then, the DNS resolver sends this request to the DNS servers if the required IP is not present on the local DNS cache. An attacker can listen to the DNS query sent to the DNS server and replace the result with the attacker’s desired IP. Then, the DNS resolver will receive a fake result, which is known as DNS poisoning. The browser will then try to connect to the fake phishing site using the attacker-replaced IP.
- Session hijacking and malware distribution – When a user connects to a website and a session is established after authentication, attackers can hijack the session and connect to the web application using a stolen session ID. Whenever a user enters valid credentials to a web application, the user will be authenticated by the web application. Typically, this creates a session for the user. Once the authentication is complete, the session ID will be used to control the user session. For example, some web applications such as banking applications are designed to terminate the session if the session is inactive. Using a packet sniffer or protocol analyzer such as Wireshark, attackers can collect the session information and rewrite session information to their browser to reestablish the connection without even using the credentials of the genuine user.
In the same way, attackers can redirect users to fake sites with malware and distribute malware among the users. Since users have entered the correct address in the browser, they think the website they have accessed is genuine, but in reality, it could be a phishing website created by the attacker to lure users and distribute malware.
How to minimize the risks with open Wi-Fi
Open Wi-Fi networks have various risks that we have discussed in this chapter. But there are unavoidable situations where we will still have to use open Wi-Fi systems, even though we know that there are multiple risks involved. Let’s look at the ways you can minimize the risks involved when using open Wi-Fi. For example, when you travel overseas and are in transit, you may need to send an urgent email. Maybe you need to transfer some funds from your bank account urgently and the only option that you have is through airport Wi-Fi. Some airports provide open Wi-Fi for their passengers while some airports, such as Changi airport in Singapore, provide authenticated one-time passwords (OTPs) to their passengers after scanning their passports:
- Use Virtual Private Networks (VPNs) – VPNs are one of the secure ways to access the internet and its services more securely, as it creates encrypted communication. There are open and commercial VPN solutions. Most VPN solutions support mobile devices and some even support multiple devices with a single license. When connected to open Wi-Fi, you then need to connect to a VPN. This will create an encrypted connection from your device using a VPN client to the server. Some VPN providers even let you use your desired server location:

Figure 5.17 – The Cyberghost VPN provides secure communication even if connected to open Wi-Fi
When you start your communication over VPN, communication is encrypted from the device to the server. Chances for attackers to sniff the communication will be drastically reduced. When you are connected to open Wi-Fi, a VPN such as the Cyberghost built-in module will automatically start protecting the communication:

Figure 5.18 – The Cyberghost VPN Wi-Fi module secures the communication
Using a trustworthy VPN service provider is important. There is a range of VPN tools that can be used to encrypt communication when connected through open Wi-Fi. You can select VPN services such as the following:
- NordVPN
- OpenVPN
- ProtonVPN
- NetMotion
- ExpressVPN
- Don’t send private or sensitive information over open Wi-Fi – As a rule of thumb, we should refrain from sharing sensitive and private information over open Wi-Fi. We can reduce the risk by connecting over VPN connections, but always try not to send personally identifiable information (PII) over open Wi-Fi.
- Multi-factor authentication (MFA) – Enabling MFA whenever possible is another way of reducing the risk. If you enable MFA, and even then, attackers collect your credentials, they will not be able to access your financial information or sensitive accounts, as they need another level of authentication. Most banks and social networking tools support MFA.
- Choose a cellular network over open Wi-Fi – In today’s world, most users are used to connecting to hotspots, including open Wi-Fi, whenever available, even if they have cellular networks. Mostly, this happens due to the speed and capacity limitations of cellular networks. But when it comes to security, your own cellular connection is more trustworthy than unknown open Wi-Fi or hotspots, as it’s easier to manipulate Wi-Fi than cellular networks. If you need secure connectivity, always use cellular networks or mobile hotspots instead of open Wi-Fi.
Phishing sites
Phishing is another technique that attackers commonly employ to compromise sensitive information. Phishing is a process of attempting to acquire sensitive information by masquerading as a trustworthy entity. Phishing can be used as an open attack or targeting attack. When a targeted attack is conducted on an organization or a user, then the attack is known as spear phishing. We have discussed various ways that attackers use phishing techniques and tools in the Social engineering section of Chapter 4, Techniques that Attackers Use to Compromise Privacy. The first-ever known phishing attack was reported in 1996, but a paper published in 1987 by the HP user group described a phishing technique 10 years before the real attack took place. Interestingly, in over 90% of successful data breaches, phishing is involved in some way according to the well-known security research company, KnowBe4. Phishing has over three and a half decades of history and has been constantly evolving in this time.
Newer phishing attacks are more sophisticated and innovative. Some developments that phishing attacks have seen include the following:
- Links sent by email addresses with fake Google search results, which redirect the user to attacker-controlled websites, mostly malware-laden
- Phishing company-controlled cloud logins, including Microsoft 365, that look real, so users will not think twice before entering their credentials
- Redirecting legitimate users to malware-laden, attacker-controlled sites using these aforementioned techniques and infecting the endpoint devices with malware
Summary
This chapter explained the different tools that attackers use to compromise privacy, including Maltego, Google Advanced Search, Google dorks, the Uvrx search tools, open Wi-Fi networks, and phishing attacks. This chapter also provided knowledge on how attackers use Google Search to collect sensitive data, how to search for anyone across social media, the risk of open Wi-Fi networks, and how to protect yourself from phishing.
In the next chapter, we will explain the types of data that competitors are interested in collecting from companies and individuals. We will be learning about various artifacts that attackers collect from you, the artifacts that competitors are interested in collecting from individuals and from companies, the ways that these attackers can access your networks, and how attackers can compromise browsers.
