4
Techniques that Attackers Use to Compromise Privacy
Newer technologies are introduced frequently, and our lifestyles constantly move us closer to cyberspace. Our relationship with the internet is getting stronger while exposing us more to the unregulated internet. A little over two decades ago, the only way we connected to the internet was through emails. We had dial-up connections, which prevented us from creating a stronger relationship with the internet due to the slow speed and time-based connectivity. When faster broadband connections were introduced, we started forming stronger relationships with cyberspace due to speedy and stable connectivity, irrespective of the time we stayed connected.
In the dial-up days, we connected to the internet only when we really wanted to. Now, we are always connected, whether we want to or not. Previously, we had to put in efforts to connect to the internet; now, we have to put in efforts to disconnect from the internet. The most critical problem, above all, is that while you are connected to your bank account app on a smartphone, another hundred apps on the same phone are connected to the internet using the same connectivity. When this connection is created, a number of layers collect your information, including your device, the Internet Service Provider (ISP), your browser, and connected apps and websites.
There are multiple ways that attackers compromise your privacy. This chapter concentrates on a range of techniques that attackers use to compromise your privacy, including the following:
- Information gathering
- Enumeration
- Identity exposure
- Artifacts that can be collected from devices
- Social engineering
Information gathering
Hackers often use a range of information-gathering techniques to collect information about a target. This is an important step of hacking, as information gathering provides insight into the target. Typically, there are five phases of attack. These phases are as follows:
- Information gathering
- Scanning and enumeration
- Gaining access
- Maintaining access
- Covering tracks
Of the five phases, information gathering is the most important phase, where the attacker spends a considerable amount of time gathering information about the target. If the attacker collects more information, then it’s easier to understand the attack surface. Information gathering is usually classified into four categories:
- Footprinting
- Scanning
- Enumeration
- Reconnaissance
The information that the attacker could collect includes user information, IP addresses, DNS information, subdomains, and company information, which consists of company employees, usernames, open ports and services, operating system versions, and so on. Attackers use a range of technologies and tools during information gathering. During information gathering, attackers often use open source intelligence (OSINT). Open source information is usually collected using major search engines, web pages, and other sources but is not limited to the searchable internet. A considerable portion of the internet cannot be found or searched using major search engines. This is called the deep web. The deep web consists of a large number of websites, databases, files, and other resources that cannot be indexed by Google, Bing, Yahoo, or any other commonly used search engines. Attackers use a range of tools, including web spiders, WHOIS databases, Maltego, intercepting proxies, and web resources such as Netcraft.
Types of information that attackers try to discover include the following:
- Public IP addresses
- Subdomains and DNS-related information
- Unintentionally shared sensitive documents
- Directory listings
- Leaked usernames and passwords
Information gathering is the first step of hacking and ethical hacking. Information gathering is a kind of art that any attacker or penetration tester should learn and master. According to the method that the attacker uses, information gathering is divided into two types:
- Passive information gathering
- Active information gathering
Passive information gathering
Passive information gathering is a method of gathering information by using other available sources without connecting to the target. When performing passive information gathering, attackers use search engines such as Google. This method is commonly known as Google hacking or Google dorking. In other words, attackers use Google’s capabilities to find information.
Attackers need to know published and unpublished subdomains. They use a range of tools to discover subdomains. You can use online services to find out this information – for example, https://searchdns.netcraft.com/.
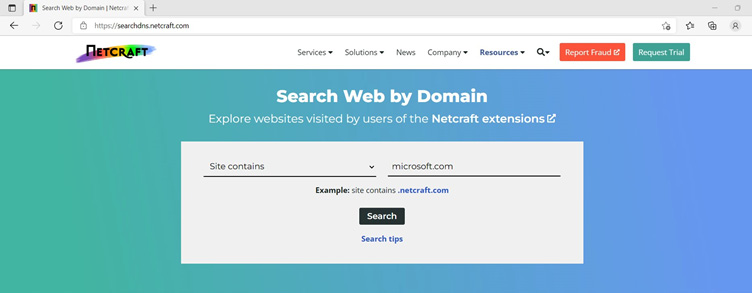
Figure 4.1 – A Netcraft search for subdomains
Attackers can use online tools to search subdomains of websites, using tools such as Netcraft. There are many tools that can be used for this purpose, including the following:
- Sublist3r: A subdomain scanner used by bounty hunters
- AMASS: A subdomain discovery tool
- SubBrute: A very fast subdomain brute-forcing tool
- Knock: A subdomain scanner written in Python
- DNSRecon: A collection of domain reconnaissance scripts written in Python
- Altdns: A permutation-based subdomain discovery tool
When you search the URL on Netcraft, it will generate a list of subdomains of the main domain. These subdomains can provide very interesting information, as some of them may not be exposed to the external world. These subdomains can be used for testing, internal use, and installing web apps. Netcraft can also generate DNS reports, which contain interesting information about the target, including the range of the IPs that were used by the URL, historical data, and operating systems used to host a web application.

Figure 4.2 – A Netcraft search for subdomains on Microsoft
When a company or an individual shares information on their own website or social sites, this information can be used by attackers. Hence, we need to know to what extent we should be sharing information on the web. Exposing more information than required is known as information overexposure.
Even the disclosure of a subdomain can create an entry point for an attacker. Sometimes, administrators may install content management systems in a subdomain for testing. It is possible that they might still be configured with default credentials or default installation. Once an attacker has identified the subdomain and scanned it, they can use the default configuration to reconfigure and gain access to the server or default credentials.
WHOIS lookup
WHOIS is a query-based protocol that is used to query information stored in a database related to users of internet resources. This is a publicly available database that contains information such as assigned domain names and IP addresses. Often, attackers use this to gather information and can use the nslookup tool to obtain DNS entries of the domain or online tools:
C:/nslookup
Set q=any
Microsoft.comThe Wayback Machine
The Wayback Machine is an internet archive that keeps over 650 billion web pages as a digital library, which allows users to go back in time and explore how websites looked in the past. This is a not-for-profit organization that keeps snapshots of websites around the globe, not just famous ones but also all possible websites. You can access the Wayback Machine at http://web.archive.org/ and search any URL you want. For example, if we search www.yahoo.com, it will show us the snapshot that the Wayback Machine has in its digital library.
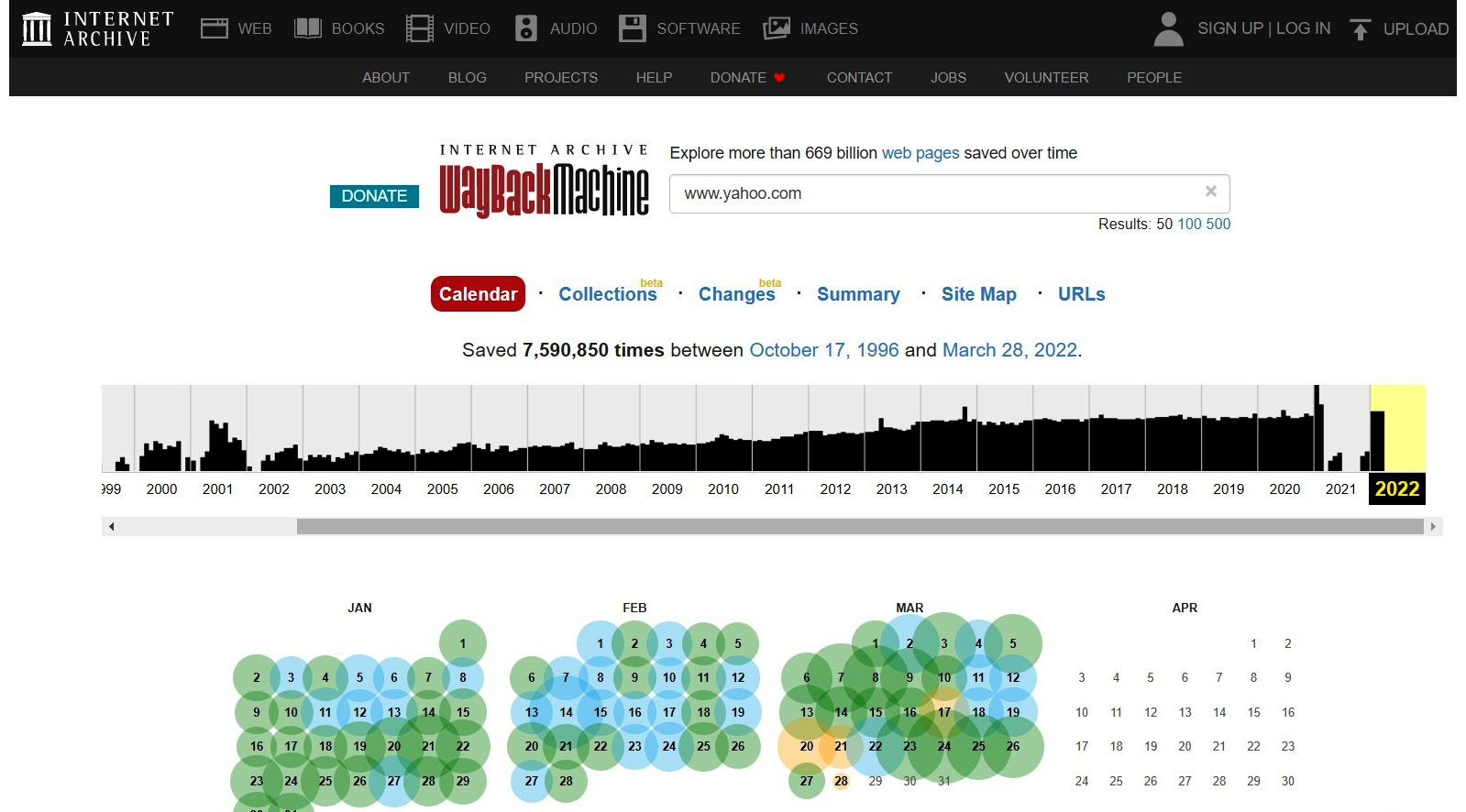
Figure 4.3 – Wayback Machine snapshots of www.yahoo.com
When you click any of the snapshots, it will take you to the web page that is stored in the digital library. You can even search for your own websites to see how many snapshots are saved in the digital library. If we select the www.yahoo.com snapshot that the Wayback Machine took in February 1997, it takes us to the relevant web page.
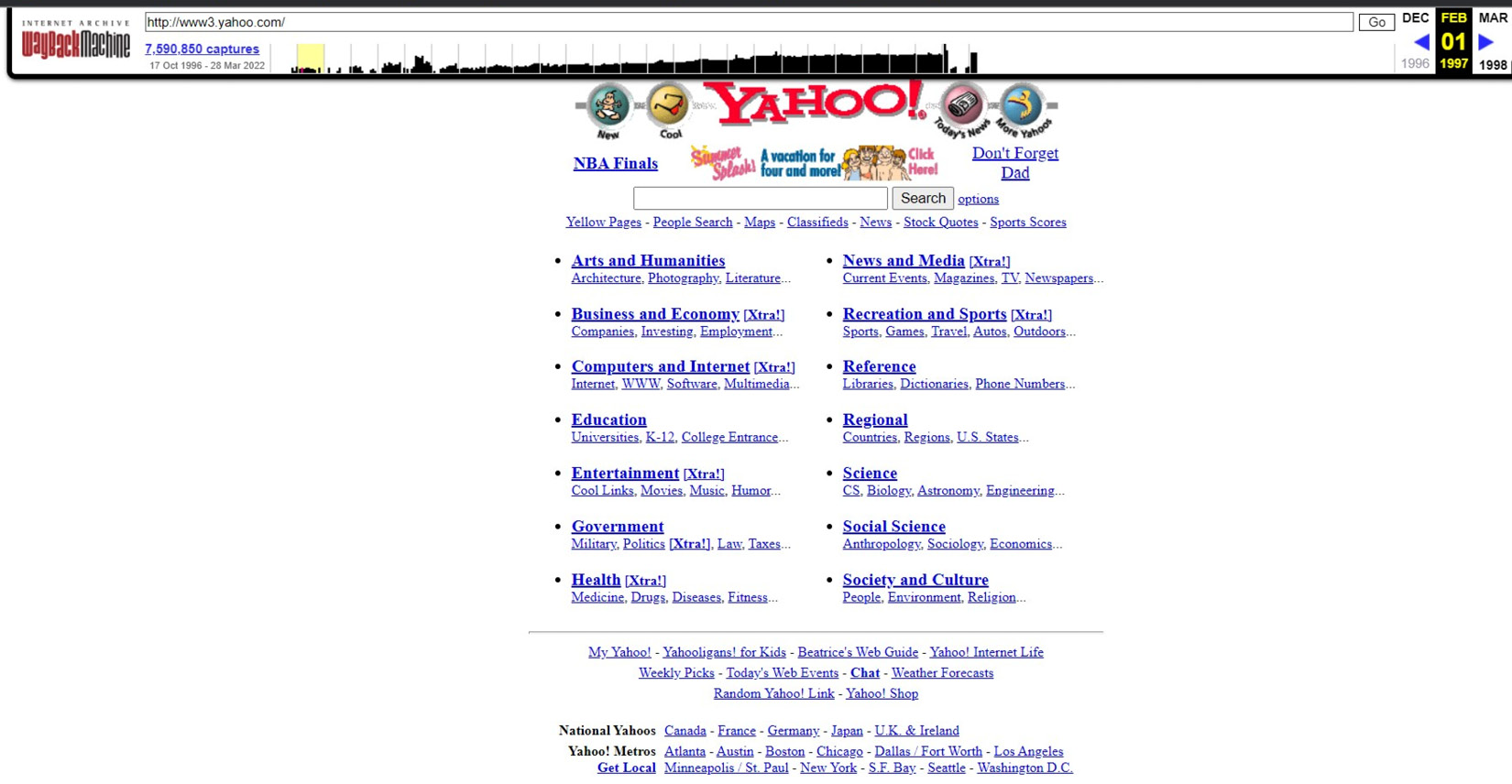
Figure 4.4 – A snapshot taken by the Wayback Machine of www.yahoo.com in 1997
These repositories may still have data that you deleted long ago.
Active information gathering
Information gathering by connecting to a target is known as active information gathering. Active information gathering can be used to discover useful information about the target, including the following:
- Open ports and services
- SMB shares
- IP addresses and address shares
- Operating system versions and applications
- Information related to infrastructure
There is a range of tools that an attacker can use for active information gathering. Nmap is the most used information-gathering tool by attackers. It is a free command-line tool, but a GUI-based version can also be downloaded. Once it has scanned a target, nmap returns information related to the range of IPs or the specific IP address that the attacker needs to gather information on.
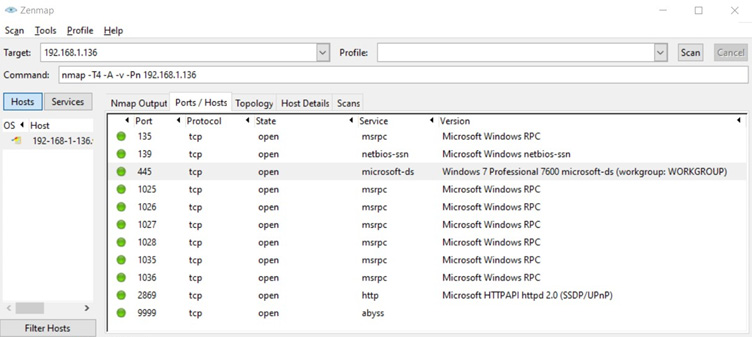
Figure 4.5 – An nmap scan shows open ports of a target system
This result generated after an nmap scan shows the list of open ports, services running, and service versions of the target system, which provide useful information to an attacker to uncover vulnerabilities. Depending on the scope, attackers use different tools. nmap is mostly used to carry out internal or external network-related scanning. If the attacker wants to scan a target website, there is a range of tools they can use.
Any type of information that we may expose can be used by an attacker. By reducing the amount of information that we share, we can reduce the attack surface. This information can be exposed by a company website, vacancy advertisements, and company portfolios, among others. For example, if a company wants to recruit an IT manager or systems administrator, they often advertise what they expect from candidates, including technical capabilities and work experience on specific products. This requirement can expose company infrastructure, including the products that the company uses within its IT infrastructure. Then, attackers can understand from the information on the vacancy advertisement the email server version of the company, the firewall model, the size of the infrastructure, and other security mechanisms in place. Some employers even share this information on their social media sites, such as LinkedIn, when they describe their job roles, thus often overexposing the company’s IT infrastructure and sensitive data.
If the scope is a web application, the risk is even higher, as web applications are published online and accessible over the internet. Attackers use a range of tools to scan and understand web applications. There are online scanners and offline scanners. There are some browser-based extensions used by attackers to collect information about web applications. The Wappalyzer technology profiler is such an extension, which can be installed in the Chrome browser, and attackers can analyze the web application on the go. You can install Wappalyzer by searching for it in the Chrome extensions. Once you have accessed a website or application and clicked on the Wappalyzer extension, it will show you the technologies behind the web application.

Figure 4.6 – Wappalyzer shows technologies used by the web application
There is a range of other tools used by attackers to collect information about targets.
Enumeration
Enumeration is a process during information gathering where attackers gather very specific information. Unlike passive information gathering, during enumeration, an attacker actively connects to a target and collects specific information. Since the attacker is connected to the target, the attacker can send direct queries to the target to collect specific information, which is useful to exploit a system to gain system access. During the enumeration phase, attackers will try to gather information such as the following:
- Users and group names
- Network and file shares
- Computer names
- Application-related information or banners
- Routing and Address Resolution Protocol (ARP) tables
- DNS information
- User lists from web applications and Active Directory (AD)
Enumeration is an important phase and attackers use a range of techniques to enumerate targets. Depending on the target, attackers change the technique as well. The most common enumeration techniques are as follows:
- Extracting information using default passwords and word lists
- Brute-forcing an AD
- NetBIOS enumeration
- User and group extraction in Windows
- Extracting DNS information
- Printer shares
Attackers specifically target a range of ports and services for enumeration. These ports and protocols are prone to enumeration attacks. The following are the most common services and ports targeted by attackers:
- TCP 445 SMB
- TCP 139 NetBIOS
- TCP 389 LDAP
- TCP 53 DNS
- TCP 25 SMTP
- TCP 135 Microsoft RPC
Utilities and tools are specifically targeted on these services and ports to extract information during enumeration.
Depending on the target, attackers use different tools to collect enumeration information. For example, attackers use https://dnsdumpster.com/ to collect web-based application targets.
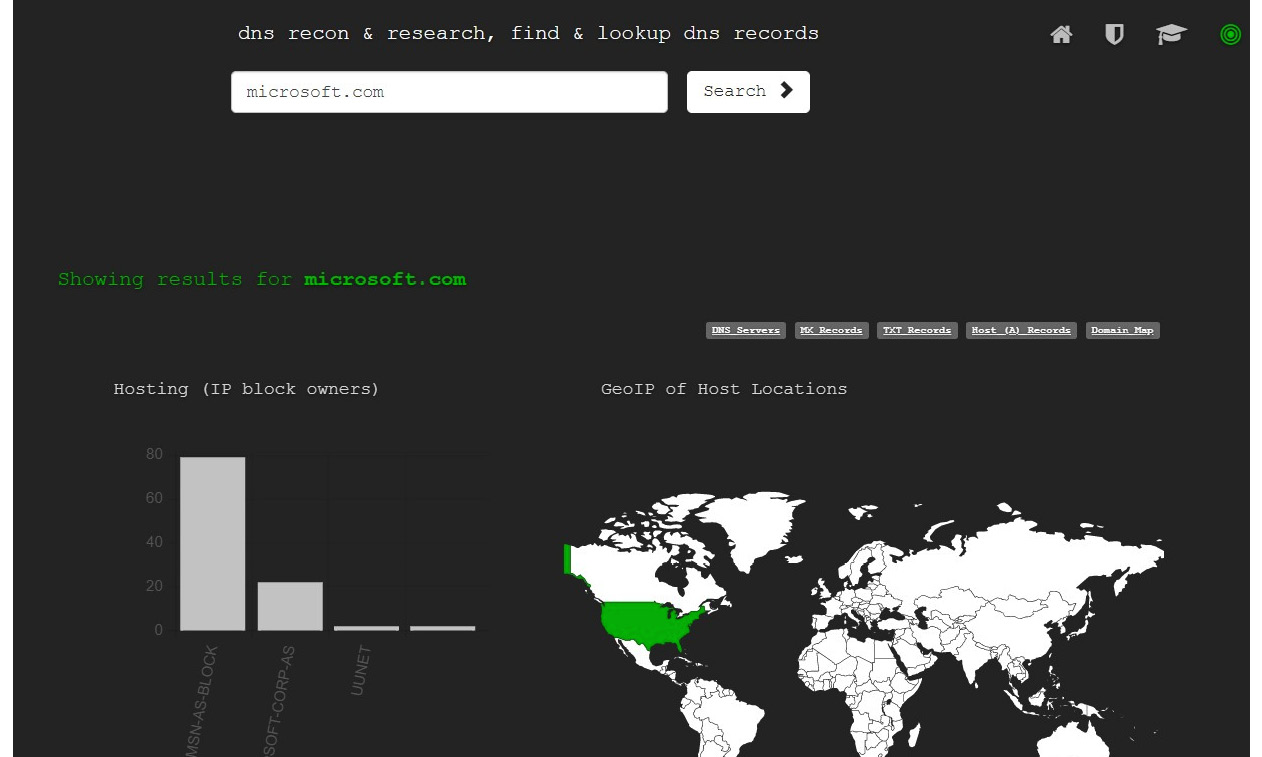
Figure 4.7 – DNSdumpster shows information on the URL that is given
When attackers scan the targeted web URL on this portal, it generates very important information about DNS servers, MX records, TXT records, host records, and domain maps. They can collect valuable information such as the following:
- DNS servers: Collecting information from the DNS servers and banner information.
- MX records: Mail exchanger records and hosts sharing the same IP.
- TXT records: All text records created on a domain.
- Host records: All host records and banners.
- Domain mapping: This has all the connected hosts and domain information of a main domain. This reveals information related to the domain and connected hosts and presents it in a graphical view. The domain map also shows the interconnection between domains, subdomains, and domain records.

Figure 4.8 – The domain map shows domain information
Depending on the target, attackers use multiple methods to collect information. As an example, if the target is a website, attackers try to find out legitimate usernames of the target website. WPScan is a tool that can be used to enumerate the username of a WordPress website. WPScan is a free and open source tool included in Kali Linux and many offensive security distros.
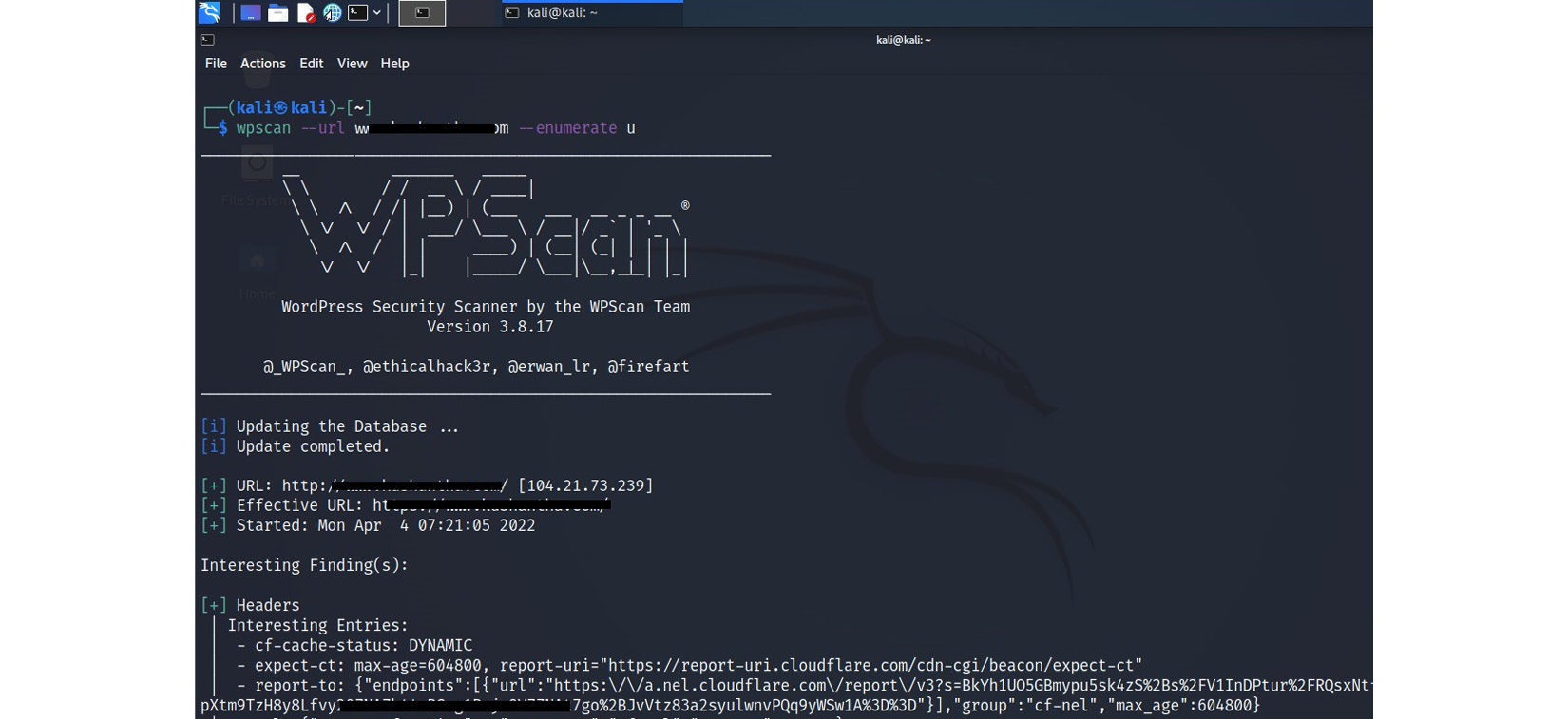
Figure 4.9 – WPScan enumerates usernames from a WordPress website
Once scanned, WPScan enumerates the list of users in the WordPress web application. Attackers can use collected usernames during the gaining access phase to compromise the systems.
Gathering information from complex networks with thousands of devices is not easy. Attackers use enumeration techniques to gather information about the connected devices from NetBIOS caches. A NetBIOS cache keeps information about recently resolved IP addresses. Rather than spending hours scanning complex and large networks, this is an ideal solution to collect accurate information readily available in a NetBIOS cache.
If an attacker is connected to a domain environment, enumerating usernames and groups is another common way of gathering specific information related to targets. In most enterprise networks, it is common to use AD as an identity system, if they use Microsoft technologies. When AD is used to maintain authentication and authorization, username and groups are created in an AD. AD enumeration tools are used to enumerate users and group names from the AD. Enum4linux is a commonly used AD enumeration tool. If the attacker has access to the network, they can run this tool to collect information.

Figure 4.10 – Enum4linux enumerates usernames from AD
When the attacker is connected to the network, they can use the enum4linux tool to enumerate the users and groups.
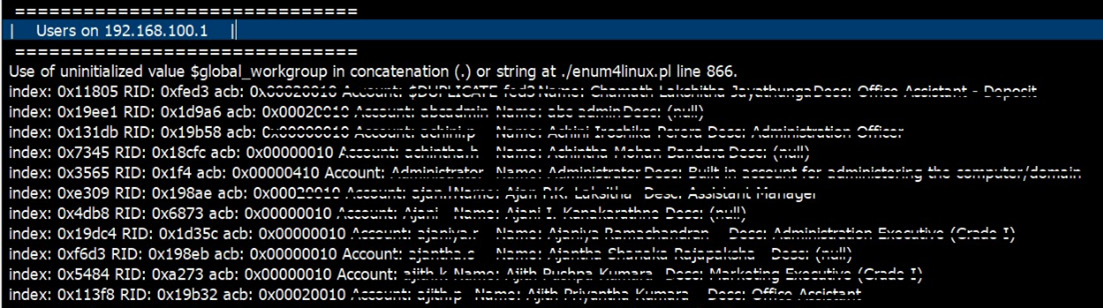
Figure 4.11 – Enum4linux enumerated usernames from AD
The preceding screenshot shows that enum4linux was used to acquire a list of users and their information from AD.
Identity exposure
An individual using multiple devices has become the norm in today’s world. Most of the devices we use today store our identities in various forms. This allows our identity information to be easily exposed. This can happen at an operating system level, an application level, a storage level, or a network level. Using various devices makes our life easy, but we are sacrificing identities and other sensitive information by ignoring privacy. If a device is stolen, stored data can be accessed easily unless the device storage is encrypted. Most identities are exposed due to unawareness of various types of attacks.
Individual identities can be exposed in multiple ways, including the following:
- Publicly available sources
- Blogposts and registrations to newsletters by email addresses
- Social media
- Registrations to various services using identity information
- Selfies and other images published on different platforms
- Online and offline forms
- Using shared devices and sold and stolen devices
Attackers can use the preceding methods to discover your identity without your knowledge.
It’s not only individuals but also enterprises that suffer from identity exposure. Organizations use enterprise identity systems such as AD to authenticate and authorize user entities to services and resources. Most organizations don’t have the required visibility of identities and their exposure at their endpoints. Most importantly, identities can increase an attack surface. When an organization doesn’t have the required visibility of its identities, it is difficult to identify the risks introduced by identity systems. Identities can introduce deadly exposures, misconfigurations, and incorrect permission allocations, which can increase the attack surface to a great extent.
Modern IT systems have many forms of identities, including the following:
- On-premises identities: For example, an AD
- Cloud identities: For example, Azure AD
- Hybrid identities and linked identities: For example, an AD and Azure AD linked by AD Connect
When enterprises deal with identities, they must always ensure identities are not exposed. This can be performed by adopting an attacker’s point of view. This can be done through vulnerability assessments and penetration testing.
Identity exposure has led to identity-based attacks, including account takeover attacks and a range of password attacks. Preventing these attacks is increasingly difficult as new ways of identity exposure are introduced on a daily basis. Attackers collect personal and sensitive information from various sources, including via credential leaks, social media, breachers, and publicly available information, to launch these attacks.
Identity attacks range from common password-related attacks, such as wordlist attacks and brute-forcing, to common user password profiling. Once an identity is exposed, attackers can easily build wordlists with usernames. Large password wordlists are usually available to download from multiple sources, including password generators. There are two main types of password cracking:
- Online password cracking
- Offline password cracking
Online password cracking
Online password cracking is a method that attackers use to compromise the password of online services, including those beginning with http, https, ftp, and smtp, by using attacking tools and probing online services with the help of a password list. You can download very large password lists directly from the internet by just googling. Once, a user in a hacker forum leaked 8.4 billion entries of passwords in text format in a massive 100 GB .txt file. This file contained passwords between 6–20 characters long without duplicates or spaces. Typically, attackers use two methods in online password hacking: dictionary attack and brute-forcing. A dictionary attack makes use of a password file known as a dictionary and tries all the passwords one by one until the password matches or you’ve reached the end of the file. The brute-force attack, meanwhile, tries all possible passwords generated from a given character set. The dictionary attack is a better choice over the brute-force one for online password cracking, considering the time that is required for the brute-force method. Brute-forcing is always successful if the required time and character set are available.
If the identities are exposed, attackers can always try online password attacks, especially for online services, including web applications. A credential breach is one of the most common and most used ways to breach systems. Attackers are interested in credential breaching, as it gives them complete control over a target. Most web applications are designed to provide full access or functionalities for legitimate users. If the attacker manages to get the correct credential from the online password cracking, that allows them to make use of any kind of capability offered to legitimate users.
Another important aspect of online password cracking is the vast range of protocols that accept online usernames and passwords to authenticate, and that can, therefore, be attacked by online password cracking from anywhere in the world over the internet. Attackers can strike from anywhere in the world if a service or protocol is open to the internet and accepts a username and password.
One of the disadvantages of online password cracking is it is very slow and has many dependencies, including network speed and service responses. There is a range of password cracking tools that support online password cracking, including the following:
- Hydra: One of the most used free online password cracking tools that supports a range of protocols
- Medusa: A faster tool when compared to Hydra but fewer services and protocols supported than Hydra
- Patator: A Python-based password cracker-supported range of protocols
Offline password cracking
Offline password cracking involves attempting to recover passwords from a password file. Typically, passwords are stored in an encrypted form. When you save a password or create one, it will be saved as a hash. As an example, if you enter a password as P@$$w0rd@123, it will be stored as 931e25cb35290d1eaff3a42f03f8d1f8 if the hashing algorithm is MD5. Depending on the hashing algorithm used in the application, the output will be different. Every hashing algorithm generates a fixed-size output, irrespective of the type or size of the input. Hashing is also irreversible.

Figure 4.12 – HashCalc generates the respective hash value for the given input
Since hashing is irreversible, offline password cracking is a two-step process. If attackers use wordlists for offline password cracking, the steps to recover the password will be the following:
- Take the first word from the wordlist and generate the hash using the respective algorithm.
- Compare the hashed output with the value in the password file.
If the two values match, the password is the word, and if not, the same process should be continued with the next available words in the word file, also known as the dictionary.
However, some tools and applications claim that they can crack a hash. As an example, we can use https://crackstation.net/. CrackStation supports a range of algorithms, including LM, NTLM, md2, md4, md5, md5-half, sha1, sha224, and sha256. CrackStation does not crack a hash but compares the entered hash with a long list of precomputed cracked password hashes. If CrackStation can locate a hash, hash that is like the entered hash value, it returns the respective plain text password. If the same hash value that we generated using HashCalc is entered into CrackStation, it will return the respective plain text value, as seen in Figure 4.13:

Figure 4.13 – CrackStation recovered the plaintext password from the entered hash input
Windows systems store passwords in a Sequential Alignment Map (SAM) file, which is in the C:WINDOWSSystem32config folder. Linux systems stores the passwords on /etc/shadow. If an attacker can obtain the password file, they can utilize the offline password cracking method. There are a couple of ways that the attacker can obtain the password hash:
- Sniffing: Sniffing is a technique that attackers can use if they get physical network connectivity. Then, the attacker can listen to communications, especially when users use unencrypted protocols. As an example, when a user is trying to access a network share, to validate permission, the network share will challenge the user for the password. If the attacker listens to the network and collects the challenge and the response, the attacker can obtain the password hash. Attackers use tools such as Wireshark, Ettercap, Cain and Abel, and tcpdump for sniffing.

Figure 4.14 – Sniffing plaintext credentials of a user login using the HTTP protocol
- Physical access: If an attacker gets physical access to a device, they can obtain a SAM file. Typically, attackers use Linux live systems to boot a targeted system or some other tools, such as Hiren’s BootCD, freely downloadable from https://www.hirensbootcd.org/, which has a long list of tools that can be used to even reset an administrator password.
Artifacts that can be collected from devices
Most enterprise systems provide services through endpoints. Individuals access systems too through endpoints. When you access any system, including a cloud system, an on-premises system, or even an application, there are many artifacts collected by a device. If the device is lost or stolen, a third person can have direct access to these artifacts, unless the device is encrypted as per industry standards. During investigations, forensic investigators can use forensic tools to recover many artifacts and obtain information.
If an attacker has access to a device in the event of it being lost or stolen, they can collect the following information from it:
- Contact information and the phone book can be exported or downloaded.
- Messages, including SMS and application-based text messages.
- Multimedia content, including pictures, videos, and sensitive multimedia content.
- Call history, including incoming and outgoing calls.
- Stored passwords and codes.
- Wi-Fi network association data.
- System files, log files, and system-created temporary files.
- Geolocation information.
- Documents created and downloaded
- Plans and to-do lists.
- Internet browsing history, temporary files, and cookie information.
- Data collected by various applications that are installed.
- Deleted files and artifacts from the system, which can be recovered.
When an attacker has access to all this information, they can use it to do direct attacks and indirect attacks. Types of artifacts that can be collected can vary, depending on the form factor of the device and the operating system. Currently, many devices used in enterprises are Windows, Mac, Android, and iOS. Depending on the device’s operating system, attackers can use various techniques and tools to collect artifacts and information from it. If the attacker has full physical access to the device, the number of artifacts that can be collected is much higher. The attacker can even create a copy of the device using physical or logical acquisition methods. Once a copy is created, the attacker can then analyze the device’s contents further and acquire more information. This operation is similar to the methods that are used in forensic investigations.
To maintain cyber anonymity, the devices that we use to access the internet are very important. As we discussed earlier, attackers can access sensitive information on your devices, even if they aren’t stolen or lost, via applications, malware, and physical device access.

Figure 4.15 – USB Rubber Ducky injects keystrokes at superhuman speeds
USB Rubber Ducky is designed by Hak5 and looks like a USB stick. It can inject a series of keystrokes at superhuman speeds. Even if the USB storage port is disabled in the device, USB Rubber Ducky can still send a pre-created payload by posing as a keyboard. Other similar devices were introduced by Hak5. They introduced this device in 2010 with a simplified duckyScript language, which attackers can use to design their own payloads. Conversely, Hak5 itself provides a range of pre-crafted payloads that can be used directly with the device. USB Rubber Ducky was opened to the community when the tool got a lot of attention and many people were sharing creative payloads, with individuals submitting their own payloads in various categories, including credentials, execution, exfiltration, recon, and remote access.
This simple hacking tool can be used by attackers for different devices, ranging from Windows and iOS to Android and Linux operating systems, as almost any device that accepts inputs from keyboards can be emulated by USB Rubber Ducky.
If you keep your device unattended or let an attacker access it, intentionally or unintentionally, for a few seconds, that would be more than enough time for them to connect USB Rubber Ducky to your device and upload the payload to your device or steal all the saved credentials in the device, as all the keystrokes are pre-defined in the payload.
As we discussed in previous chapters, some applications such as Cerberus or backdoor tools such as AndroRAT can be used to collect information from your device, including contact information, images stored in it, call information, text messages, and social media interactions, including private messages.
There is a range of tools used by forensic investigators that can also be utilized by attackers to access a device or create a complete copy of it, which can be analyzed by the attackers later to acquire sensitive information. Forensic investigators extract data from mobile devices using three methods. These methods are physical acquisition, logical acquisition, and filesystem acquisition. Forensic investigators prefer the first method, as it gives them a complete replica of the device, and a successful physical acquisition provides stronger digital evidence for the investigators.
Attackers don’t really care about the forensic value of the acquired data if it provides them with the sensitive information they need. Forensic value entails admissibility in court, which is required in order to be accepted as evidence for any case. Attackers’ objectives are very different from that of investigators, even though they use similar tools to extract data.
The following list of tools is freely available on the internet for investigators and can be used by attackers to extract data:
- FTK Imager Lite: This tool can be used to create an image of a target device, which can later be used by attackers to analyze the image.
- Andriller: This tool allows attackers to acquire information from various social media app databases. This utility can crack lock-screen patterns or PINs and decode some databases used for various communications.
- Android Data Extractor Lite: This is a Python-based tool, used to acquire information from Android-created databases.
- Linux Memory Extractor: This tool allows an attacker to create a volatile memory dump (acquiring data in a memory) from a target device, and they can then execute this tool across the local area network.
- AFLogical OSE: This tool must be installed on a targeted device as an APK, and then an attacker can extract various information from the SD card, including the call log, the contact list, and text messages.
Social engineering
Social engineering is a type of attack in which attackers target users directly, rather than trying to compromise complex systems. It’s a psychological manipulation of human nature, which involves tricking them into disclosing sensitive information. An attacker first collects information and investigates a target to find out a potential point of entry and weak security procedures in order to launch attacks.
Types of social engineering
There are two types of social engineering: computer- and mobile-based social engineering and human-based social engineering.
Computer- and mobile-based social engineering
There is a range of social engineering attacks based on computers, including the following:
- Phishing and spear phishing: Phishing is a type of social engineering attack where an attacker sends a malicious link to a cloned website or an email that tricks the user or users to enter sensitive information. If the attack is aimed at a specific user or an organization, then it is referred to as spear phishing.
- Hoax letters: Typically, hoax letters are meant to scare or warn you about nonexistent malware, viruses, or ransomware, suggesting that you install fake antivirus from a given link. Another type of hoax letter trick to defraud a user is to an email asking you to send money for a particular reason. The reason can be religious, personal, or economical.
- Chain letters: This is a type of social engineering attack that involves tricking people into forwarding an email to multiple people in order to get a higher level of reach. The email can contain false information or be malicious.
- Spam messages: Spam messages are typically not harmful but irritating. This type of unsolicited message can try to gather information, such as by collecting authentic email addresses.
- Targeted chatting: Using instant chat services, including mobile apps and social media apps, attackers may try to chat via fake accounts to gather information. Scripts and bots are developed to automate this process. Some of the bots are smart, as they are backed by artificial intelligence and machine learning technologies.
- SMS: Attackers often use fake SMS messages, claiming you won the lottery, your shipment is on the way, your courier has delivered your parcel, or you’re selected for a raffle draw, and requesting you to register with confidential information.
- Malicious apps: Applications downloaded from untrusted sources or shared links can be malicious. These applications can collect confidential and personal information in the background and share it with attackers.
- Baiting: In this attack, attackers attract users with information that the users believe can be useful to have. It can be presented as an important software or feature update; sometimes, attackers can leave USB memory sticks with an interesting label unattended to attract a target.
- Quid pro quo: This attack is similar to baiting attacks, but instead of baiting you with a thing that is valuable, attackers perform an action. For example, the attacker might call a company and pretend to be technical support returning a call and providing instructions to the targeted user to download and execute pre-created malicious code or script, which provides attackers with access to the target systems.
- Scareware: This attack displays a warning notice to the target users, typically something like Your computer is under attack or Your device is infected. Sometimes, these tools display that they are scanning the target computer and convince users to install antimalware from an attacker’s link, which will end up installing the attacker’s tools on the target system.
Human-based social engineering
There is a range of social engineering attacks targeting humans, including the following:
- Impersonating users: This involves pretending to be a legitimate user and trying to get access to important information. This type of attack can be done over the phone, in person, or by using chat services. Often, attackers pose as a higher authority and ask for sensitive information.
- Dumpster diving: This involves collecting information from dustbins or discarded computer systems through data-recovery techniques. This is the reason we should be properly shredding confidential information before disposal. For example, if you need to dispose of a credit card statement or any letter sent to your name and address, you should remove personally identifiable data and sensitive information before disposal. Even if you want to dispose of computer systems, you need to permanently remove electronic data as per data destruction standards, such as NIST 800-88 or DoD 5220.22-M. If the data is recoverable, attackers can use simple tools to recover deleted data, including on mobile devices. Attackers can even recover deleted partitions using simple tools.
- Shoulder surfing: This can be performed by an attacker as part of direct observation, such as looking over a user’s shoulder when entering important information such as credentials. Attackers can also use surveillance systems such as closed-circuit television (CCTV) to obtain this information.
- Piggybacking: An attacker can pretend to be an employee and request a legitimate employee to allow them access to restricted areas by providing a convincing reason.
- Eavesdropping: This involves unauthorized listening to conversations in person, over the phone, or by using similar technology to collect information.
These methods clearly show that we shouldn’t be disclosing our information from publicly available sources. Also, we should be aware of social engineering attacks, as there is no other way of preventing social engineering attacks than building awareness. We will be discussing countermeasures for social engineering attacks in the latter part of this chapter.
Tools used by attackers to launch social engineering attacks
User awareness is the key to protecting any entity from social engineering attacks. There is a range of tools available, both open source and commercial, to test social engineering readiness. You can use these tools to test user readiness while attackers use the same set of tools to launch real attacks:
- Social-Engineer Toolkit (SET): SET is an open source tool written in Python to conduct social engineering penetration testing. Anyone can create and clone a phishing website using SET to launch a social engineering attack. Attackers use a range of tools, including free ones such as SET, to clone websites to lure users and collect confidential information.
SET comes with pre-created templates that help a user or attacker launch an attack in no time. The built-in web server in SET provides a ready-made web server to host a cloned website. This capability is useful to launch exploits that compromise most web browsers.
Attackers can use built-in templates in SET to clone a legitimate website, which creates a more realistic output. Also, SET has readily available pre-created web pages for popular web applications such as Google, Yahoo, Twitter, and Facebook.

Figure 4.16 – Using SET to create phishing websites
Most tiger boxes, including Kali Linux, have SET built in, and it is also downloadable from GitHub.
When you execute SET from Kali Linux and select Social-Engineering Attacks (Figure 4.16), it provides a range of options to launch different attacks (shown in Figure 4.17).

Figure 4.17 – An SET-supported attack list
The most used option by attackers is Website Attack Vectors (Figure 4.17), after which they can clone any website login page they desire. They can also use built-in templates. On selecting the second option, which is Google (Figure 4.18), SET uses a pre-created Google template and hosts it on a built-in web server. The attacker can use any IP associated with Kali Linux or use DNS servers to provide a more convincing URL to publish the web page.
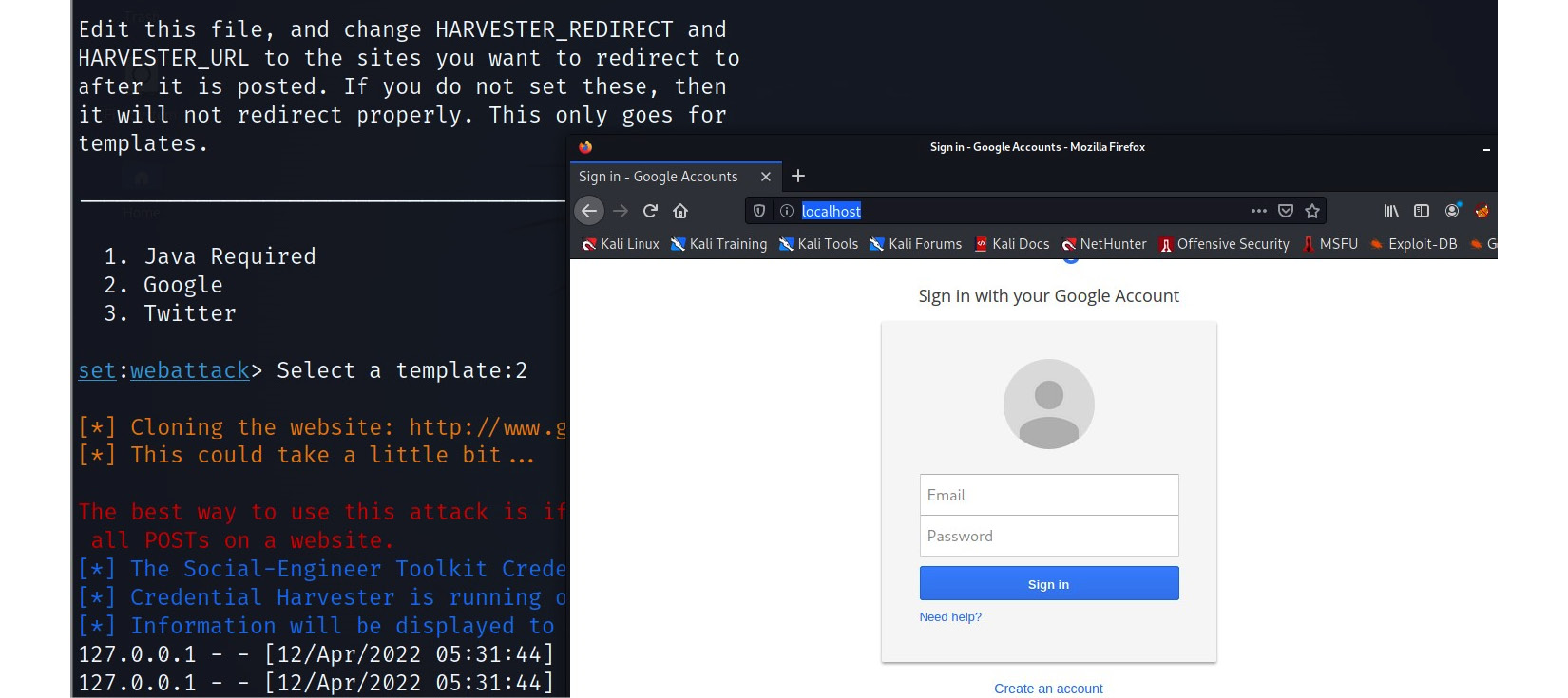
Figure 4.18 – An SET-created Google login
Once an attacker has created a cloned login page or used an existing template, it will be published automatically by a built-in web server. Then, the attacker can share the link with targeted users by email, social media, or messengers. Whenever any user submits their credentials, the real-time attacker will receive the credentials in the SET console or they can store the credentials on a text file created in SET.

Figure 4.19 – SET displays the credentials entered by the target user
Figure 4.19 shows the credentials and other parameters that the browser intended to send to Google servers, which were captured by SET. Once the attacker receives the information, the attacker can log in to the web application using the real credentials that the user entered.
We have only displayed web attack vectors, but there is a long list of attacks possible with SET, including more sophisticated attacks. In some complex attacks, attackers can use SET to launch social engineering attacks using payloads created by the Metasploit framework.
- Wifiphisher: This tool is built into Kali Linux, or you can download it for free from GitHub. It is used by attackers to automate phishing attacks on Wi-Fi networks to obtain Wi-Fi passwords. Using this tool, attackers can jam nearby Wi-Fi Service Set Identifiers (SSIDs), commonly referred to as Wi-Fi networks or hotspots, and clone them. The newly cloned fake SSID does not require a password to log in. This act is also known as an evil twin, as there are two access points with the same SSID in the same range, but users will only see them as a single Wi-Fi hotspot.
When anyone connects to the fake SSID, there will be a legitimate-looking password prompt, requesting users to enter their Wi-Fi password for a firmware update. The notification further states that without the firmware update, the Wi-Fi will not work. Once the legitimate user enters the Wi-Fi password, it will present the user with a fake update process and reboot timer while notifying the attacker of the Wi-Fi credentials. It’s a useful tool for wireless penetration testing and is also used by attackers.
- Maltego: This tool is useful for gathering information before launching a social engineering attack. There are three phases involved in a social engineering attack: research, planning, and execution. Attackers must carefully plan the attack first. A successful attack requires proper research and planning. This requires a considerable amount of information gathering to understand the organizational structure, and information about individuals, behaviors, and interests.
Maltego is an OSINT investigation tool that generates a graphical representation of how pieces of information are linked with each other. We will discuss Maltego in more detail in Chapter 5, Tools and Techniques That Attackers Use. Maltego supports a range of inputs, including DNS information, domain names, organization names, and individual names, and then collects information automatically from the integrated publicly available sources, providing a graphical representation of the interlinked information.
There are many tools used by attackers to launch social engineering attacks. Many organizations now use various platforms to test the social engineering readiness of the organization. Building user awareness is the key to preventing many social engineering attacks. There is a list of platforms available for individuals and organizations to test their readiness:
- Gophish: This is an open source platform supported by many operating systems. This tool is very user-friendly. You just need to extract the compressed folders and can then start testing right away. Users can be added one by one or by importing CSV files. There, built-in templates can be used for testing by creating campaigns. Reporting is built in, where testers can test the statuses and detect the users who fall for social engineering attacks.
- Infosec IQ: Infosec IQ is used to test sophisticated simulations for an entire organization and contains a library of thousands of pre-created templates for testing. This tool also provides a free phishing risk test, which can be used by organizations to launch a phishing campaign and find out an organization’s phishing rate.
- Attack Simulator: This tool is a part of a Microsoft 365 Enterprise edition subscription or can be subscribed to as an individual feature with a Microsoft Enterprise Mobility and Security subscription. Organizations that have licenses for Attack Simulator can use hundreds of built-in templates to simulate phishing attacks for selected users or all of their users. This also has an interactive awareness education feature built in for users to gain more knowledge about phishing attacks.
- Simple Phishing Toolkit: This tool also combines a simulated phishing attack and awareness education for targeted users.
Apart from these tools, there are standalone utilities, such as SuperPhisher, which clones any login page in seconds, along with a .php file that is capable of writing submitted credentials on a text file, which attackers can access later.
Preventing social engineering attacks
Social engineering attacks have become very sophisticated, and prevention is not that easy. As we discussed in this chapter, social engineering attacks cannot be prevented by security appliances such as firewalls or intrusion prevention systems, as the targets of social engineering attacks are humans. There is a common quote among security professionals – There is no patch for human stupidity, which means social engineering attacks cannot be prevented by applying patches or hardening systems. When attackers cannot find vulnerabilities in a target system, attackers can create vulnerabilities using social engineering. It is, therefore, important to prevent social engineering attacks using the following measures:
- Security awareness and training: There is a myth stating that security training is only for IT professionals, which is incorrect. IT professionals represent a very low percentage of the total employees of an organization. Cybersecurity risks are present for every employee who is a part of the system and connected to the internet. We cannot expect IT professionals or IT security professionals to protect every security aspect of an organization. IT staff and security staff can be critical in this, but every employee should hold equal responsibility in cybersecurity. Due to this reason, cybersecurity training should be an ongoing activity at any company.
- Security products: Antivirus systems and endpoint protection tools cannot protect users directly from social engineering attacks but can be useful to detect the payloads that can be downloaded as a part of such attacks. Many phishing messages and links try to download or upload malicious payloads to a system; however, if antivirus protection is active, malicious payloads can be eliminated.
- IPS and SIEM: Some Intrusion Prevention Systems (IPSs) and Security Information and Event Management (SIEM) solutions have features such as User Event Behavior Analysis (UEBA), which creates a baseline for user behavior that is capable of detecting anomalies. Microsoft Sentinel, which is a cloud-based SIEM solution built into Azure, has this feature.
Summary
Throughout this chapter, we discussed different types of techniques that attackers will use to compromise your privacy, various phases of attacks, and how information gathering is useful to conduct a successful attack by attackers. We listed the different types of tools that attackers will use to gather information, the important information that attackers will collect during another important phase, enumeration, and the various tools that can be useful. We also learned how identity exposure can be very critical for any organization. If devices are stolen or kept unattended, that can be a goldmine for attackers. On the other hand, if vulnerabilities are not available, attackers can create vulnerabilities using social engineering attacks.
In the next chapter, we will improve our knowledge of the different kinds of tools that attackers can use to compromise privacy.
