10
Proxy Chains and Anonymizers
In the previous chapter, we discussed how to maintain cyber anonymity and techniques that we can use to maintain cyber anonymity related to the following topics:
- Avoiding behavior-tracking applications and browsers
- Using secure messaging apps
- Using disposable emails and contact numbers
- Using virtual machines and virtual applications
- Maintaining cyber anonymity at all the layers
This chapter explains the tools and techniques that can be used to maintain cyber anonymity. During this chapter, you will come to understand what proxy chains and anonymizers are and gain knowledge on censorship circumvention. We will discuss live Operating Systems (OSes) for maintaining anonymity and how they work, how Virtual Private Networks (VPNs) work and maintain cyber anonymity, and finally, how we can use logless services to maintain cyber anonymity.
In this chapter, we will discuss the tools and techniques that can be used to maintain cyber anonymity related to the following topics:
- What proxy chains and anonymizers are (for example, Tor)
- Censorship circumvention (for example, Psiphon)
- Live OSes (for example, Tails)
- VPN solutions
- Logless services
What proxy chains and anonymizers are (for example, Tor)
The term proxy is used in information technology to define a tool or application that acts as an intermediary between a client and a server. Anonymizers are special kinds of proxy tools that can keep activities on the internet untraceable. In other words, anonymizers are special applications that can make activities that are usually traceable between client and server communication on the internet untraceable. Proxy chains are a series of proxy servers that forward traffic to each other. The objective is to provide higher anonymity than usual proxy servers or anonymizers. For example, even if the traffic is sent through a proxy server, from the internet side, it is always possible to detect the proxy IP. If the proxy servers are accessible and proxy server owners are cooperative, the real IP behind the proxy server can even be discovered by analyzing the proxy server logs. Most anonymizers say that they don’t provide information to third parties, but that depends on the requester. When using proxy chains, one proxy always forwards traffic to the other proxy on the chain, making it hard or impossible to trace the real IP of the user.
Anonymizers
The main objective of anonymizers is to provide a reasonable level of confidentiality. Anonymizers support a range of protocols including internet traffic – Hypertext Transfer Protocol (HTTP) and File Transfer Protocol (FTP) – and internet services – such as Gopher. Anonymizers typically act as an intermediate application between you and the service that you are accessing. The advantages of using anonymizers include the following:
- Provide an acceptable level of privacy – Protects your identity by ensuring your internet navigation activities are untraceable. Most anonymizers protect your privacy, with the exception of intentional disclosure by users – for example, providing personal data in an online survey.
- Provide an acceptable level of protection against online attacks – Typically, when users are using anonymizers, their traffic goes through the anonymizer. In other words, the anonymizer will be the front gate for the internet. Even if there is an attack, it will be directed through the anonymizer, as your presence is hidden behind it. Most anonymizers use their own protected DNS servers to manage the traffic.
- Access restricted content – In some countries, governments prevent their citizens from accessing certain web content including inappropriate content, websites that publish information that goes against the government, or sensitive information concerning national security. However, anonymizers can be used to access restricted content, as the anonymizers are located outside the country, and their internet connections come through different Internet Service Providers (ISPs).
- Evasion of security rules – Many organizations configure security appliances to block access to certain websites using rules and content filtering mechanisms. Since anonymizers encode and encrypt the traffic within the anonymizer traffic, these appliances will only see the traffic directed to the anonymizers from the client device. However, the reality is that the traffic directed to the anonymizer contains the traffic to restricted destinations. Since the traffic is encoded and encrypted, these appliances, including firewalls, intrusion detection, and prevention systems, cannot block traffic to restricted destinations.
Anonymizers typically access websites for you by protecting your privacy. There are many anonymizers you can use for this purpose including the following:
- Zendproxy – Zendproxy is an anonymous web proxy that allows you quick and easy access, protecting your privacy. It changes the IP address connected to your computer quickly and easily. When you surf the internet, your IP determines your location. You don’t need to install anything to use Zendproxy – it ports your access over Zendproxy with no hassle. You can control the script on the site and cookies through Zendproxy. There is a range of options that can be configured when surfing the net. You need to enter the URL you desire into the given space and configure whether you want to encrypt the traffic, allow cookies, remove scripts from the website, or remove objects such as ActiveX controls when surfing the internet:

Figure 10.1: Zendproxy provides anonymous access when surfing the internet without any installation
Typically, ActiveX controllers, scripts, and mobile codes are used by web applications to collect information about you. Let’s look at the difference between accessing a website directly and through an anonymizer. First, let’s access https://ip.me directly from the browser:
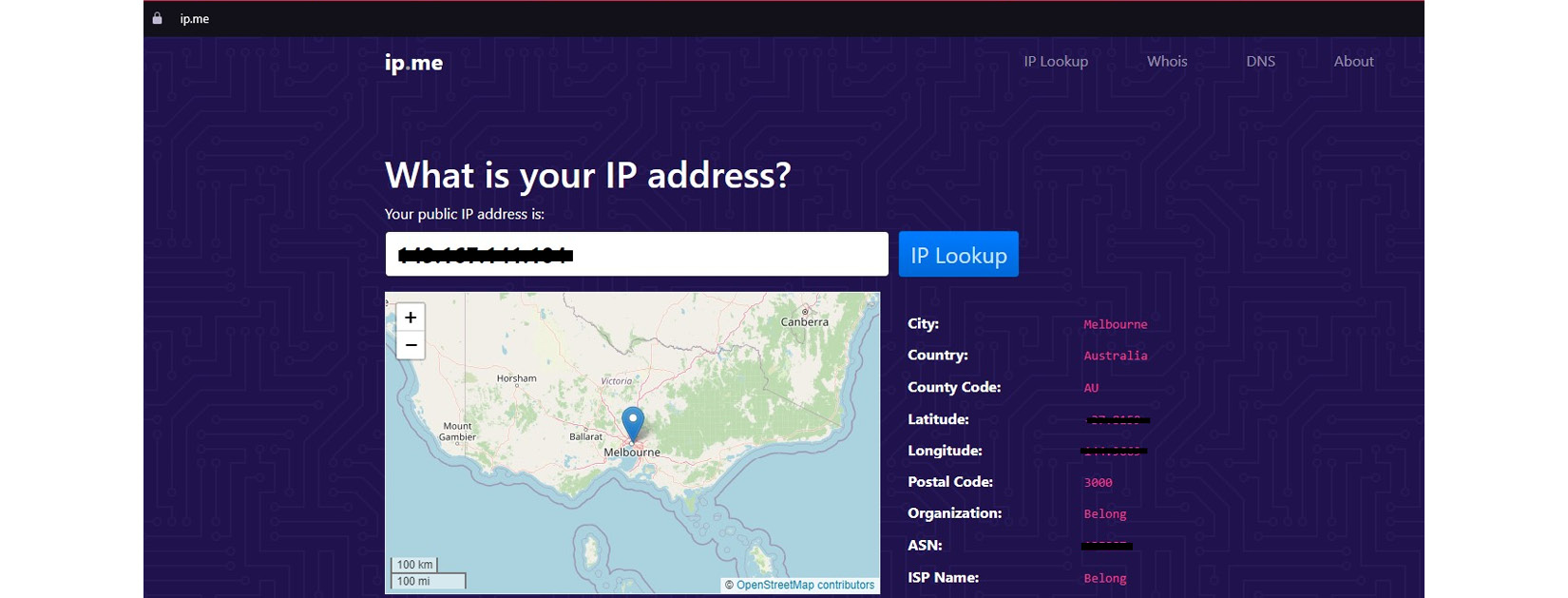
Figure 10.2: https://ip.me shows your location and other information
When you directly access https://ip.me, it shows your IP address, location, and GPS information on the site, as the website collects all your information using your IP address. This is how web applications collect your information when you are navigating the internet. When you directly access the internet, it detects your IP address and from that application, detects your location as Melbourne, Australia, your ISP as Belong, the postal code of your location, and GPS information, including latitude and longitude. Scripts running on the web application show your location on a map.
Now, we will try to access the same website using the Zendproxy anonymizer:
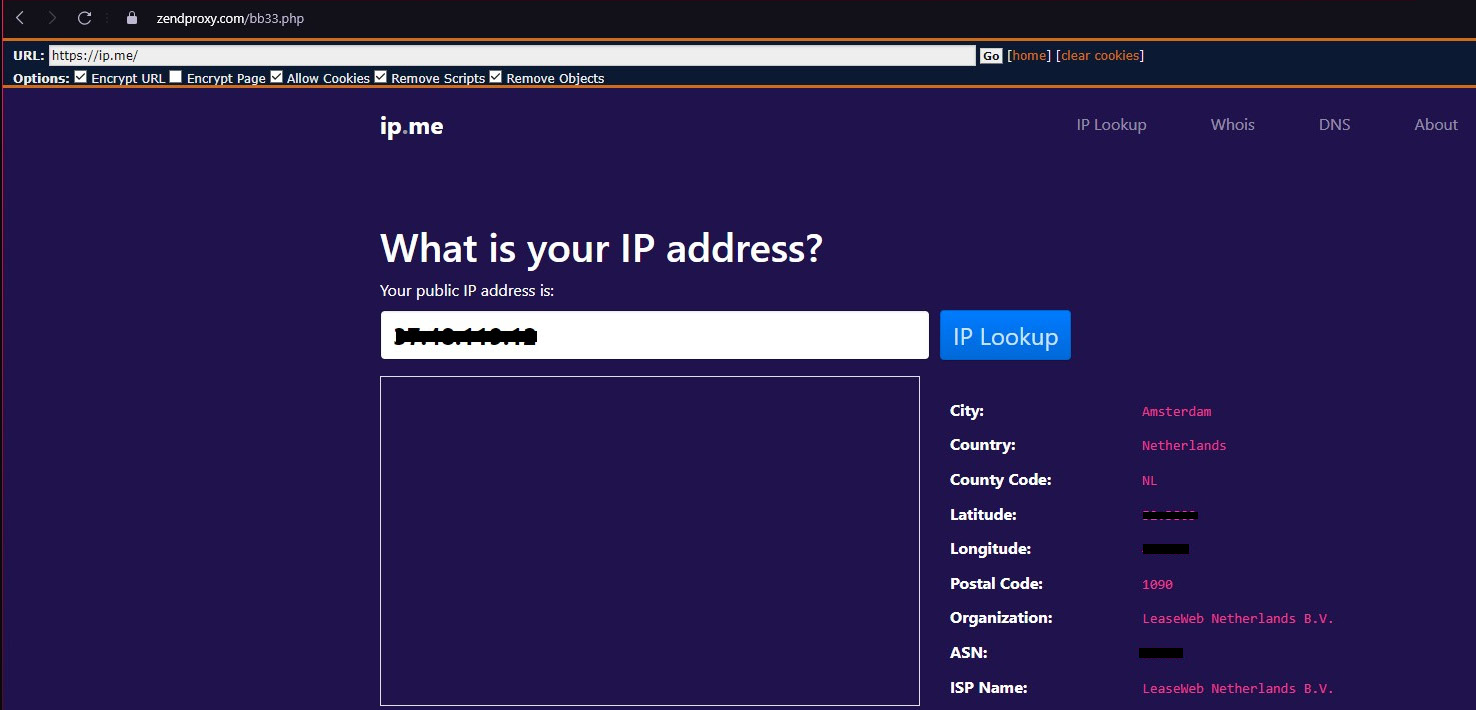
Figure 10.3: Accessing through Zendproxy hides your location and other information
As you can see from Figure 10:3, when accessing through the Zendproxy anonymizer, it shows a completely different location – the location of the anonymizer in Amsterdam, Netherlands, and the GPS information, postal code, and service provider information are given as LeaseWeb Netherlands. Now, you may notice that the map doesn’t appear, as Zendproxy has removed the scripts and objects on the website.
- Anonymouse – Anonymouse is another anonymizer that hides your whereabouts when surfing the internet. You can access Anonymouse by accessing http://anonymouse.org/anonwww.html. By entering the desired web URL on Anonymouse, you can surf the internet without exposing yourself:

Figure 10.4: Surfing the internet anonymously using Anonymouse
Anonymouse hides all your whereabouts when accessing the internet, providing a faster and easier way of accessing it safely. The best thing is that Anonymouse blocks all the scripts and mobile codes while providing faster access without any ads:

Figure 10.5: Surfing the internet without leaving any traces with Anonymouse
As you can see in Figure 10:5, you can access the internet without revealing your real information, the same as Zendproxy. Anonymouse removes the scripts and changes the real location to Frankfurt, Germany, and the other information accordingly.
- Hide My Ass (HMA) – HMA provides a range of features in both its free and pro editions. Even the free edition supports a range of security features that users can use even without registering to the site:

Figure 10.6: HMA anonymizer provides a range of features
As you can see from Figure 10.6, HMA provides the option to select a location for users. Even when you are using the free version, you can select one of the desired locations.
Besides this, it also supports typical features such as encryption, disabling cookies, and removing scripts. The HMA free version is good enough for simple browsing and maintaining an acceptable level of anonymity, while HMA pro provides better features for larger devices and even for gamers using gaming apps.
- Kproxy – Kproxy is another anonymous proxy available with free and pro versions and provides functionality using a browser extension as well. Kproxy can bypass online content filtering and government- or workplace-related censorship. Even the Kproxy browser extension provides an acceptable level of security, preventing attempts to steal your personal information, including passwords and financial information, even when you are on insecure public Wi-Fi. Kproxy also provides general proxy features such as hiding your IP address to prevent data snooping by ISPs:

Figure 10.7: Kproxy anonymizer for hiding your identity online
Data snooping by an ISP means that an ISP can sell your browsing activities, behaviors, and history to other parties that want to send you directed ads. Kproxy can prevent this and it also provides the option of selecting a range of Kproxy public servers to redirect your traffic.
- ProxySite – ProxySite is a proxy server that provides similar functionality but specializes in social media. If you want to access social media through a proxy, ProxySite is the best proxy server. When accessing any website through ProxySite, it always ensures traffic is encrypted with Secure Socket Layer security even if the site you are trying to access is not a secure site with HTTPS. Users can block ads when using ProxySite or switch between the functions of multiple proxies, allowing users to access sites using multiple countries. Most of the proxy servers for ProxySite are in the United States and the United Kingdom and allow users to remove cookies, scripts, and objects such as mobile code when accessing the web.
Free proxy servers
We learned how to use anonymizers to surf the web without our data being collected while browsing. Many anonymizers we discussed support removing third-party cookies, objects, and scripts while browsing. Many open proxy servers are there if you want to redirect your traffic through proxy servers, but these proxy servers will not remove objects, cookies, or scripts – what they do is redirect traffic through their proxy. There are many sources that provide free proxy lists. If you search for free proxy server list on Google, you can find many proxy server lists. If you access https://geonode.com/free-proxy-list/, the best thing about Geonode is that it provides users with a long list of proxy servers that can be filtered based on the country, port, anonymity level, such as highly anonymous, anonymous, and non-anonymous, proxy protocol, speed, owned organization, and uptime, among other things:

Figure 10.8: Geonode free proxy list
If you need, you can export the current proxy list as a text file, a Comma-Separated Value (CSV) file, or a Java Script Object Notation (JSON) file. Once you have the information, you can configure your device or the browser to go through the proxy server. Depending on the browser, the configuration is varied. Typically, under the settings, you can find proxy configuration, or if you are using a Windows 10 device, you can go to the device settings, and under Network and Internet configurations, you can find the proxy settings. Then, you can configure the proxy IP and the protocol in the proxy settings and save them. Once you have saved the proxy settings, when you browse the internet, your internet traffic will be redirected through the configured proxy server. Similarly, you can find a proxy option on various browsers and different OSes, but the configurations are very similar, as our objective is to set up the IP and the port to redirect traffic:

Figure 10.9: Proxy configuration on a Windows 10 device
You might feel this configuration is cumbersome, as changing the proxy configuration each time is time-consuming. There are tools that can help to switch over multiple proxy servers quickly. FoxyProxy is one of these kinds of tools, which is available as a browser extension that can help you to configure multiple proxy configurations and change quickly whenever you need. You can access https://getfoxyproxy.org/downloads to download the FoxyProxy extension, which is available for multiple browsers, including Chrome, Safari, Microsoft Edge, Firefox, and Opera. With the same method we discussed earlier, we can install the FoxyProxy browser extension in the same way and enable it on our browser.
Then, click on the FoxyProxy browser extension and go to the Options tab. You can configure the proxy server IP and the port number on FoxyProxy for the desired proxy server configurations. You can select the Add new proxy option to add the servers:

Figure 10.10: Adding proxy servers to FoxyProxy
You can add all your proxy server configurations one by one to FoxyProxy.
Another option on FoxyProxy is configuring an automatic proxy configuration URL. You can use the Geonode free proxy list using the Load proxies through URL option given at https://geonode.com/free-proxy-list/. You can copy the URL from Geonode and paste the Automatic proxy configuration URL configuration into the FoxyProxy Proxy Details options. Then, FoxyProxy will use the automatic configuration:

Figure 10.11: Adding a proxy server to the FoxyProxy configuration
Once you have completed adding proxy configurations to FoxyProxy, you can close the Options window, go to your browser, click on FoxyProxy, and select the desired proxy server from the list to redirect your traffic. When you are using FoxyProxy, you can configure a list of proxy servers in different countries and different port numbers to redirect your traffic. Whenever you want to redirect traffic, it’s just one click away. You can save all the proxy server configurations on FoxyProxy and select which proxy you want to activate:
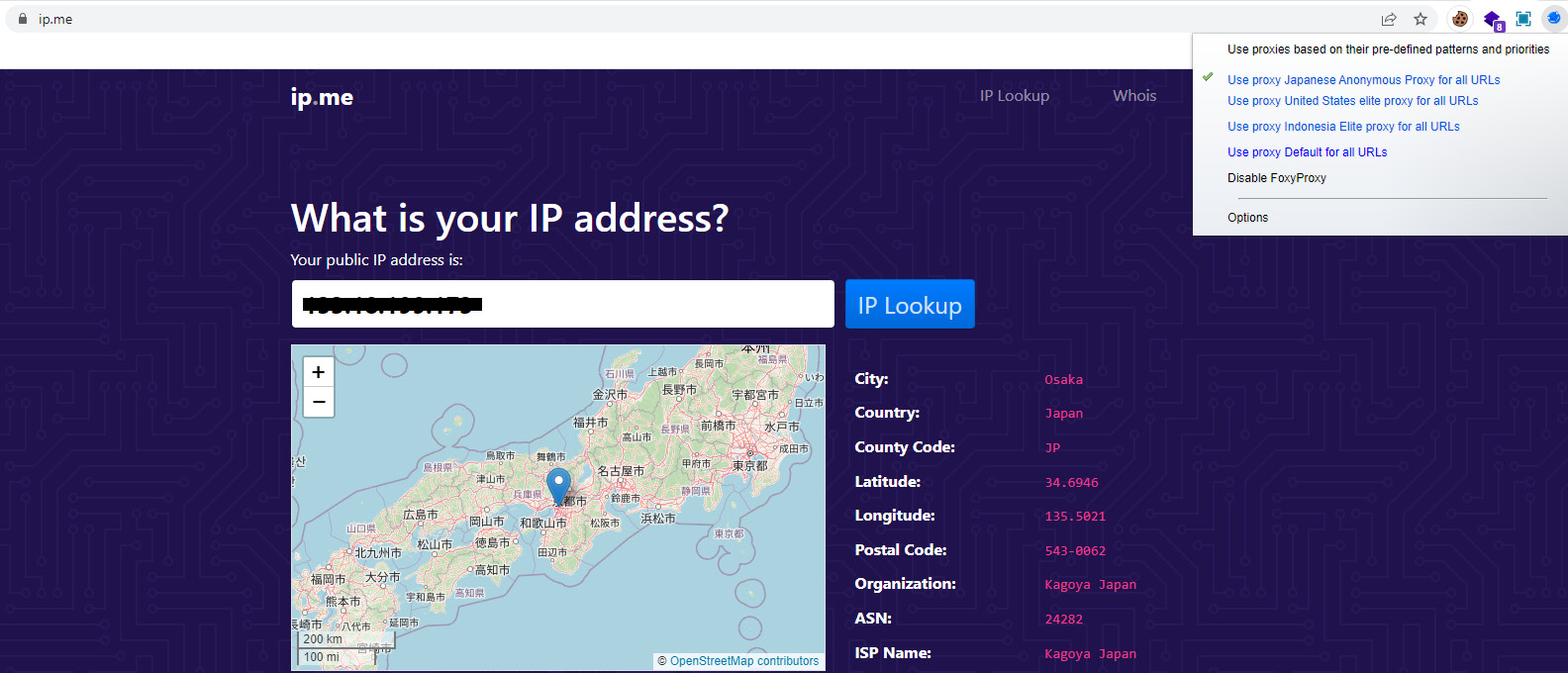
Figure 10.12: FoxyProxy helps to select the proxy server and redirect the traffic
When you select the proxy that you want to activate from the list of proxy servers you configured, FoxyProxy will start redirecting traffic straight away through the selected proxy server. This is a very efficient way of switching between multiple proxy servers on the go.
Proxy chains
Proxy chaining is a method of forwarding internet traffic through a sequence of proxy servers before traffic reaches its real destination. Once you configure proxy chaining properly and then you try to access the internet, your request first forwards to the first proxy server, and then the first proxy server forwards it to the second proxy server. The second proxy server forwards it to the third proxy server and the third proxy server connects to the destination server. When you send traffic over proxy chains, it will be more secure and increase the level of anonymity, as the destination will only detect the IP address of the first proxy server.
If they need to trace the real IP, an investigation must be conducted to gather information from the log files residing on the first, second, and third proxy servers. If the attacker uses proxy servers from multiple geographies and multiple countries, this process can become very hard or impossible considering the technical, operational, and legal challenges. Proxy chains provide a way of maintaining anonymity, but they don’t provide complete anonymity, as every proxy server keeps the information about the connections in its logs. Typically, these log files must be obtained and analyzed to understand the connections made by the proxy servers with each other. When it comes to investigations, this is not an easy task, especially when the proxies are in multiple countries. Owners or administrators of each proxy server should support the process and provide logs if someone wants to investigate the incident. It can be very hard or impossible, but there is a possibility. Many attackers use proxy chains to launch attacks and typically, they use at least five foreign proxy servers when launching attacks:
- Proxifier – Proxifier is a powerful tool when it comes to maintaining anonymity, which provides the proxy-chaining capability. Proxifier offers a fully functional copy of the software free for 31 days – then, if you want to continue, you need to purchase the license, which is under 40 USD. Proxifier offers a standard edition and a portable edition (the portable edition does not require installing the software). You can download Proxifier from https://www.proxifier.com/download/ and configure Proxifier to connect through various proxy servers around the world. You can configure each proxy server IP, port, and socket type in Proxifier. Once the list of proxy servers is configured, the proxy server will forward traffic from one proxy server to another, maintaining a higher level of anonymity. When you configure Proxifier, there are a few things you need to keep in mind:
- Proxifier supports a range of proxy types, including SOCKS V4, SOCKS V5, and HTTP (SOCKS is an internet protocol that supports exchanging packets within server-client communication through a proxy server. This information can be collected from a site such as Geonode, as we discussed in the previous section).
- Proxifier supports a mix of different proxy types in a single proxy chain. If there is an HTTP proxy server, it must always be placed as the last proxy server in the proxy chain.
- When you configure a list of proxy servers for the proxy chain and at least one proxy server is down or not functioning, the entire proxy chain will not function.
- If the proxy servers connected to the proxy chain have lags (as in, a delay in communication, also known as latency), the total lag will be the sum of all the lags on all proxy servers in the proxy chain.
- Once all proxy servers are configured to the proxy chain, if the connection to a single proxy server is broken, complete communication to the remote host will be lost.
Once you install Proxifier, you can easily create a proxy chain by clicking on Proxy Settings in the Profile menu. Then, you can use the Add button to add two or more proxy servers. Once the list of proxy servers is added to Proxifier, you can click on the Create button to create a proxy chain. Once you create the chain, you can drag and drop previously configured proxy servers into the proxy chain while maintaining the sequence in the way you want:

Figure 10.13: Proxifier can be used to create a proxy chain
Once you configure the proxy chain, Proxifier will redirect all your traffic through the proxy chain. The sequence of the proxy servers can always be changed by dragging and dropping them in the way you want. The last proxy server will always be the one connected to the target. You can enable and disable the proxy servers in the list using the checkbox. Proxifier provides all the information related to the connections, traffic, and statistics of the connection:
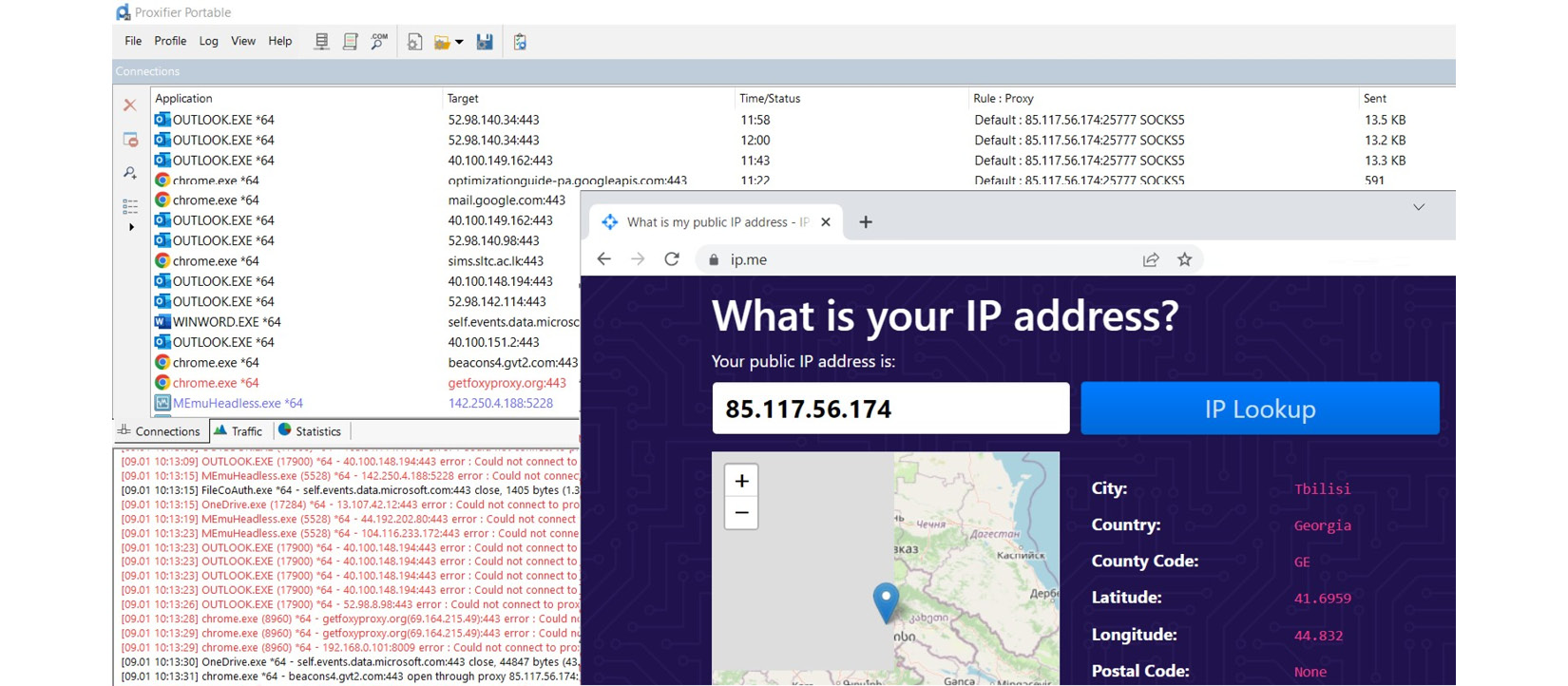
Figure 10.14: Proxifier redirects all the traffic generated by the device through the chain of proxy servers
Proxifier shows the connections made by each process within the device to the target. Interestingly, Proxifier has the option to configure rules to define which process needs to be using which proxy chain. You can create multiple proxy chains and define rules on Proxifier to redirect traffic according to your requirements – for example, if you want, you can send Google Chrome traffic through one proxy chain, while your email application uses another proxy chain:
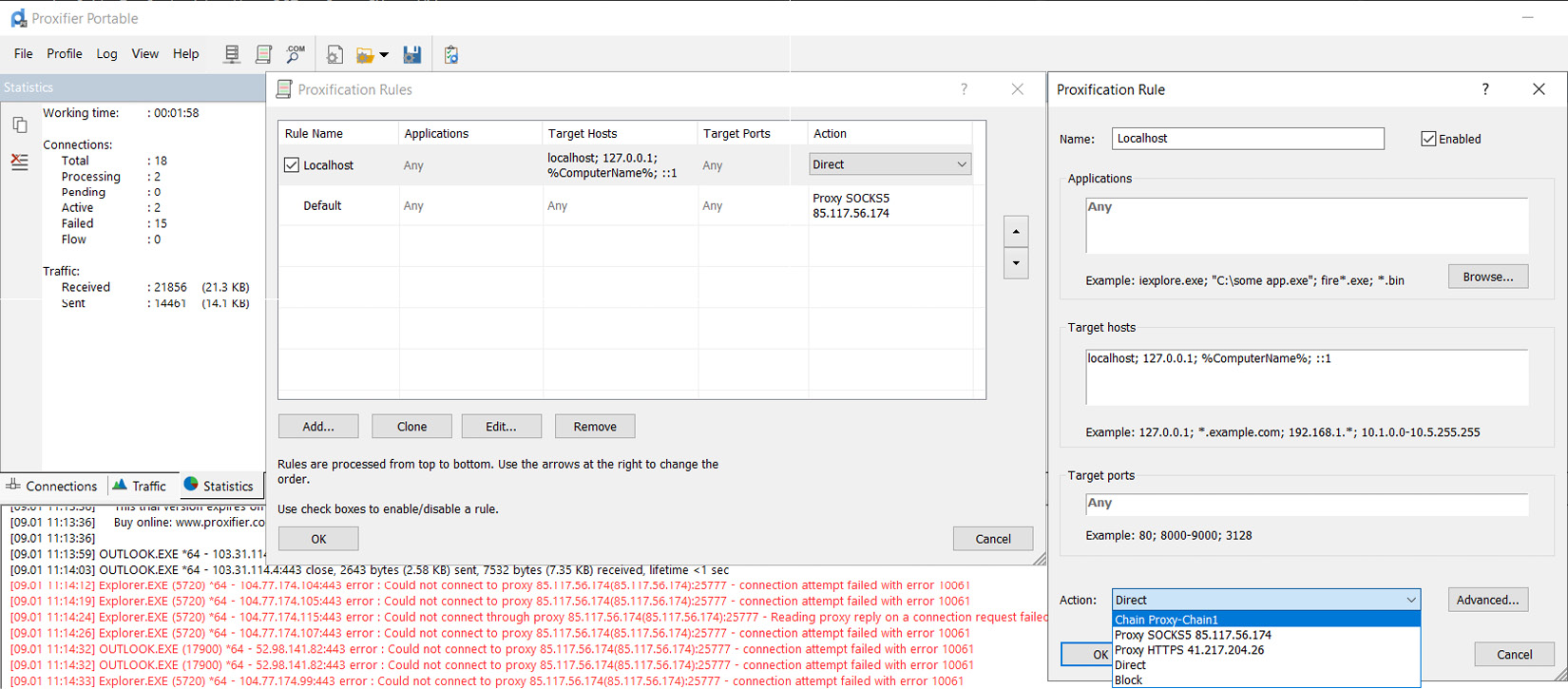
Figure 10.15: Proxifier rules can be configured to direct traffic to different proxy chains
As you can see in Figure 10.15, you can configure Proxifier rules to direct traffic through different proxy chains. It shows all the applications are configured to direct traffic through proxy chain 1; if you create multiple proxy chains, you can create different rules to direct traffic generated by individual applications through a single proxy or a proxy chain or block traffic. Advanced configuration options are there to redirect traffic through different network interface cards if you have multiple network interface cards connected to your device. It’s a great feature to design traffic through different interface cards, especially on a virtual machine with multiple network interface cards.
- ProxyChains – ProxyChains is a free and open source program that forces any type of TCP connection initiated or established by any program to go through a sequence of proxy servers. ProxyChains is capable of dynamically forcing any program to go through a chain of proxy servers. ProxyChains hides your IP, sending traffic through restrictive firewalls, and forces a range of programs and utilities, including Network Mapper (Nmap), Telnet, FTP, APT, VNC, and Wget, to go through proxy chains. For example, if you want, you can use Nmap (one of the free open source utilities most used by security professionals and hackers to scan target devices to collect information, including OS information, open ports, services on the target, and their versions) through ProxyChains. When you use Nmap to scan targets through ProxyChains, from the target side, they will only see the ProxyChains’ IP, not the attacker’s real IP. ProxyChains has a range of capabilities including the following:
- ProxyChains supports HTTP, SOCKS4, and SOCKS5 proxy servers.
- Supports different types of proxy servers to work on the same proxy chain.
- ProxyChains supports tunneling TCP and DNS traffic through proxy chains.
- ProxyChains hooks traffic generated by network-related functions into dynamically linked programs and forwards it through a chain of proxies.
Being a Unix program, ProxyChins works in the terminal. You can download ProxyChains from GitHub or use Linux security distributions such as Kali Linux or Parrot Security, which have ProxyChains preloaded. If you use a Debian-based Linux distribution, you can get ProxyChains by executing the following command on the terminal:
apt-get install proxychainsThe first thing to do when configuring ProxyChains is edit the configuration file stored in /etc/proxychains.conf. The main configuration is selecting the mode. There are three modes in proxy chains, which you can enable on ProxyChains by uncommenting the desired mode in the configuration file:
- Strict chain – All proxies configured in the list will be chained as per the given order.
- Random chain – Every connection made will be directed through a randomly selected set of proxies in the list.
- Dynamic chain – Dynamic chain will work as per the strict chain, excluding removing functioning proxies from the list.
Then, you can configure the list of proxy servers on the same file using the following format:
type host port [username password]Once you have configured /etc/proxychains.conf with the desired proxy servers, it will look as follows:
socks5 192.168.67.78 1080 lamer secret
http 192.168.89.3 8080 justu hidden
socks4 192.168.1.49 1080Once you have configured ProxyChains, you are ready to go. When you edit /etc/proxychains.conf with the proxy servers and the mode you desire (dynamic chain is the best mode to maintain anonymity), you can start using proxy chains with any program that you would like to use. It’s easy to redirect traffic using ProxyChains – you need to simply follow the following syntax:
proxychains [original command]For example, let’s say you wanted to surf a website. Then, you need to execute the following command to redirect traffic through ProxyChains:
proxychains firefox packtpub.comThe following are some of the commands that you can execute to tunnel traffic through ProxyChains:
- proxychains nmap -sT packtpub.com – This command will perform a nmap scan through ProxyChains.
- proxychains telnet packtpub.com – This command will telnet through listed proxy servers.
ProxyChains will tunnel the traffic through the chain of proxy servers that we configured by configuration file and mode.
- Tor proxy – Tor is known as the best proxy chaining tool, which has its own browser to simplify the proxy chaining process. When using Tor, we cannot configure the specific proxy servers as with the previously discussed proxy chaining tools, but the Tor browser itself uses its own set of proxies in the Tor network to redirect and tunnel the traffic. Tor supports users reaching blocked destinations and viewing censored content by going through a chain of proxies. Tor distributes your traffic through a network of relays maintained by volunteers around the world. Tor forwards traffic through a worldwide volunteer overlayed network of over 7,000 relays that can conceal the user’s usage and location from anyone trying to collect information and traffic analysis. Because of the nature of the Tor network, it makes it very difficult to trace someone’s internet activities when they are using Tor. Tor’s objective is to protect the privacy of its users and provide freedom and the ability to communicate while maintaining confidentiality and anonymity. You can get your very own copy of Tor at https://www.torproject.org/download/. The Tor browser is a completely open source project and is available on Windows, macOS, Linux, and Android.
The name Tor was derived from the privacy project managed by the naval research lab in the United States known as The Onion Router. The principle of The Onion Router is to maintain privacy through a number of encrypted layers and encapsulating data like in the layers of an onion. Inside the Tor network, there are a large number of sites known as <sitename>.onion that provide hidden services. The design of the Tor network facilitates anonymous web surfing by processing the traffic that goes into or goes through Tor network nodes, immediately relaying to the next destination without collecting or analyzing the destination or original sender. This design obfuscates the original source and the destination of the messages, providing a higher level of anonymity.
The Tor browser provides the easiest method for accessing the Tor distributed network. The installation of the Tor browser is straightforward. Once you download the browser from the original location provided earlier, you can easily install Tor on your device. Then, you can open Tor and access the internet just like any other browser, but Tor ensures anonymity by redirecting traffic through a chain of distributed proxies. The Tor browser has built-in security features to ensure security and privacy, such as disabling JavaScript and other mobile codes, automatic images, videos, and scripts. The Tor browser, including the additional software bundle, is developed and maintained by The Tor Project, which is a non-profit organization continuously carrying out research to improve anonymity in the face of newer developments.
The Tor browser provides access to the internet known as the searchable internet or surface internet – just like any other browser – but Tor also provides access to the unsearchable internet referred to as the dark web. According to research, the dark web has more sites and information than the searchable surface internet, which was primarily only accessible by the Tor browser. When compared to the dark web, the usual surface internet was referred to as the tip of the iceberg. Even though some legitimate sites are available on the dark web, including a lot of information related to scientific research, many of the sites on the dark web are said to be illegal sites that promote drugs, counterfeit money, child pornography, weapons, and other kinds of illicit material. Even hackers can be hired on the dark web for hacking assignments. Illegal activities take place because of the higher level of anonymity provided within the dark web.
Apart from the access to the dark side of the internet, Tor also provides many advantages to people who would need to maintain anonymity for ethical reasons. Sometimes, people need to maintain anonymity to prevent discrimination while accessing information as a part of their job. These special categories of users include the following:
- Research students
- Journalists
- Law enforcement bodies
- Military and special agents
- Political activists
- People from countries governed by the repressive regimes
- Users who don’t want third parties to monitor their activities online
- People who want to share their genuine thoughts on the internet without discrimination
Tor provides benefits for them by bypassing censorship and avoiding spying and information collection:

Figure 10.16: Tor tunnels traffic through relays
Tor provides privacy using a network of virtual tunnels on the internet by sending your traffic via three random relays (offered by servers maintained by volunteers around the globe known as relays). The last relay forwards traffic to the target via the public internet. As you can see in the figure, when using Tor, it sends the traffic through the computers in the middle and maintains encryption between the client and each relay. As you can see in the figure, it anonymizes the network connection and the IP address that you are connecting from.
However, while Tor was designed to provide security and anonymity, there have been some occasions where authorities revealed the real identities of the attackers even though they were using Tor. Even though the number of occasions where the authorities unmasked the identities is low, this shows that there is a possibility that attackers can be traced. This raises the question of how they can reveal people even if they use Tor when Tor has multiple layers to maintain anonymity. The answer is not hard; Tor provides network-level anonymity, as we discussed before, but there are many other layers still collecting your information, such as the OS and the applications that you use.
While Tor maintains a higher level of anonymity at the network layer, masking your IP, if you are using OSes that collect your information, or if you use your real information on the application, Tor cannot protect you. This is the reason we have discussed multiple layers of anonymity. When you need to maintain a higher level of anonymity, it’s essential to maintain anonymity at all the layers. For example, you need to use pseudonyms instead of your real name and shouldn’t be revealing your real location, as an IP address is not the only way of revealing your real location.
The reality is that a small clue is more than enough to reveal your entire identity. In particular, investigators can concentrate on behavior-based analysis from open source intelligence and collected information from the searchable internet, the dark web, and various sources that carry telematic information (information that is collected by OSes or applications). This can be used to build a sketch of the picture, adding little pieces of information and clues to it that reveal a real identity, even though this can be a cumbersome process. For this reason, we should maintain anonymity at all layers. Some systems can block Tor. You can use Tor bridges to access Tor in places where it’s blocked. In the Tor browser settings, you can configure a Tor bridge by requesting a bridge from The Tor Project, using a known bridge, or building a bridge through systems such as obfs4, Snowflake, or meek azure.
Censorship circumvention (Psiphon)
In the cyber world, censorship is the suppression of internet activities, including communicating and publishing information that can impact governments and repressive regimes. Then, governments or repressive regimes can force ISPs to enforce censorship. When the ISPs enforce censorship, these websites, services, or applications will not be accessible within these regions.
Internet censorship circumvention defeats censorship using various methods. These methods range from low-tech methods to complex methods depending on the technology that the ISP has to censor, using different services including the following:
- Using the IP address instead of a URL – Some censorship can be bypassed by simply using an IP address instead of a real URL (you can find the IP address just by searching the whois records or pinging). For example, let’s say www.google.com is censored. You can open a terminal and type ping google.com to find the IP address and then use an IP address instead of a URL on the browser to access Google:

Figure 10.17: Censorship circumvention using alternative IP
- URL encoding – You can bypass censorship using hexadecimal encoding. For example, if you need to bypass censorship enforced on Facebook, we can try hexadecimal encoding. There are many online services for HEX conversion, including https://www.rapidtables.com/convert/number/ascii-to-hex.html. Let’s go to this link and convert our URL to HEX with a % delimiter string, as otherwise, the browser will not accept encoded text. Once the online converter has converted the URL, make sure you enter the % delimiter string in front of the hexadecimal output before entering it into the browser:

Figure 10.18: Censorship circumvention using hexadecimal encoding
- Using caches and mirrors – Even though censorship circumvents the real sources of information, the information may still exist on cached servers or mirrors. There are some resources you can use, including the Google cache and the Wayback Machine. The Google cache is a web cache maintained by Google for all the websites in the world. The Wayback Machine keeps snapshots of all the websites in its repository. You can access these repositories for censored information when the real website is blocked. To access the Google cache, you can use cache:<website URL> in Google Search as we discussed before. The Google cache keeps the latest copy of the real website while the Wayback Machine keeps snapshots taken from the website from the day the website appeared on the internet. Let’s say we search cache:www.microsoft.com on Google:

Figure 10.19: Google cache copy of the Microsoft website
As you can see from the preceding figure, Google has cached a copy of the Microsoft website and kept it in Google cache servers. When the next snapshot is taken, Google will replace this copy with the latest snapshot.
If you use the Wayback Machine, it will keep multiple snapshots taken from time to time of the websites. You can access the Wayback Machine at https://archive.org/web/. Enter the site you wish to access and click on BROWSE HISTORY:

Figure 10.20: The WayBack Machine keeps over 7 billion web pages
Once you enter the website that you wish to access and press BROWSE HISTORY, it will show you the snapshots of the website taken over time. Then, you can select any snapshot you wish to view:

Figure 10.21: The Wayback Machine shows the saved snapshots
As you can see in the figure, the Wayback Machine shows all the snapshots taken over time. In this example, www.packtpub.com appeared on the internet for the first time in 2004. When you select 2006, it shows snapshots taken during the year in blue color circles. When you select the blue circle, it will even show you the time of the snapshot. When you select the required time, the Wayback Machine will load the snapshot. This method is useful to access content that is censored:
- Proxy servers – We discussed proxy servers in the previous topic and understood how proxy servers can circumvent censorship.
- VPN solutions – We will discuss VPN solutions in this chapter’s fourth section.
- Alternative platforms – The same content can be published in multiple locations by the content publishers. There are decentralized, peer-to-peer platforms supporting sustainable hosting by decentralization. Napster, Gnutella, and ZeroNet are examples of decentralized alternative hosting.
- Censorship-circumvention networks – The objective of censorship-circumvention networks is to circumvent internet censorship. As we discussed before, many governments and repressive regimes can enforce internet censorship to prevent people from accessing information. Psiphon, previously known as XP Psiphon, allows users who are using Windows, Mac, or Android devices to connect to censorship-circumvention networks for the purpose of circumventing internet censorship. You can download Psiphon by accessing https://psiphon.ca/en/download.html.
Once you have downloaded Psiphon, you can execute the program straight away without additional configuration and it will connect to a censorship-circumvention network. Additionally, you can select the region to which you want to connect, as Psiphon provides a list of servers from around the world:

Figure 10.22: Psiphon connects to a censorship circumvention network in Singapore
Psiphon is open source software where the source code is available in GitHub but it maintains all servers by itself. When it comes to privacy concerns in Psiphon, it uses cookies and shares access data with Psiphon partners who can see website visits and statistics. According to the privacy bulletin of Psiphon, it occasionally records usage-related data. When it comes to privacy and anonymity considerations, Psiphon may not be the best pick, as the objective of Psiphon is to provide censorship circumvention without drawing unwanted attention, as Psiphon uses common transport protocols. As we discussed, Tor is the best option when it comes to privacy and anonymity, but ISPs can detect if someone uses Tor.
Live OS (for example, Tails)
As we discussed in the previous topic, Tor provides privacy and anonymity at the network level. In other words, maintaining privacy and anonymity cannot be achieved just by using Tor. We need to concentrate on various other layers if privacy and anonymity are our concerns. The main reason is our privacy is compromised at various layers not just at the network layer. The OS in particular collects information, from the time of logging in to the system to an entire set of activities. As a part of the OS, it creates temporary files, a cache, logs, and events for every activity we perform on the device. Depending on the OS, the amount of data collected can vary but typically, any OS which is installed on the device collects information for various reasons, including auditing, troubleshooting, and improving systems performance.
If you need to maintain the highest level of anonymity, you need to get rid of installed OSes and installed applications before you connect to the Tor network. Even though Tor protects you at the network level, your OS and installed application can still unmask you in cyberspace. We already discussed live OSes before and booting your device with a live OS without really installing it on the device. This prevents the creation of logs, events, and temporary files on the device. Especially to overcome the concern that we have with Tor, which is maintaining OS-level anonymity, we can use OSes such as Tails or Qubes OS, which support booting the systems using a USB drive without installing it in the device.
Tails
Tails is a portable OS, fully compatible with running on a USB stick in external hardware, which protects you from censorship and surveillance. Tails is also capable of protecting you from trackers and advertising. Tails on a USB can be used to start your computer instead of the installed OS and doesn’t leave any trace once the device is shut down. Tails comes with a bunch of applications that support maintaining privacy and anonymity and are ready to use. Tails is designed with security, privacy, and anonymity in mind – it will be ready to use with even default settings. Tails is a Linux Debian-based, free, and open source OS, which security researchers can always verify and validate its code against privacy and anonymity. Tails provides benefits for a range of users including the following:
- Journalists – When using Tails, journalists can publish their sensitive content while maintaining complete anonymity if they use pseudonyms when publishing content on public forums and access the internet from unsafe locations without revealing their real whereabouts.
- Political activists.
- People from countries governed by the repressive regimes.
- Users who don’t want third parties to monitor their activities online.
- Domestic violence survivors – use Tails to escape home violence.
- You – anyone who needs extra privacy in cyberspace.
You can download Tails from https://tails.boum.org/install/index.en.html – there are many options when it comes to downloading Tails, including the following:
- USB image of Tails that supports Windows OSes from Windows 7 or later
- USB image of Tails that supports macOS after 10.10 Yosemite or later – supports an Apple M1 chipset
- USB image of Tails that supports any distribution of Linux
- USB image of Tails that supports the command-line terminal for Debian or Ubuntu
- Cloning from an existing copy of Tails on a PC or Mac
- USB image of Tails for USB
- USB image of Tails for DVD
- USB image of Tails that supports virtual machines
Tails doesn’t support smartphones or tablets. When downloading Tails, you need to transfer an image to the USB drive. There are many tools that you can use to transfer a downloaded image to a USB drive, but Tails recommends you use balenaEtcher, which is a free and open source tool that you can download from https://www.balena.io/etcher/ depending on your OS. balenaEtcher is a cross-platform tool that can flash USB drives and create live SD cards and live USB sticks from .iso, .img, and even .zip folders. If you want to create a Tails virtual machine, you can skip balenaEtcher.
If you are using a virtual machine, you can boot Tails directly from the .iso file. Once you boot from Tails from the ISO file, it will prompt you with the welcome screen that allows you to select the language and keyboard layout, as with any OS. Then, you need to connect Tails to the network using the network connectivity option –if you are using a virtual machine, Tails will automatically connect using the available network. The next major step is connecting to the Tor network, as Tails traffic is redirected through the Tor network to maintain network-level anonymity:
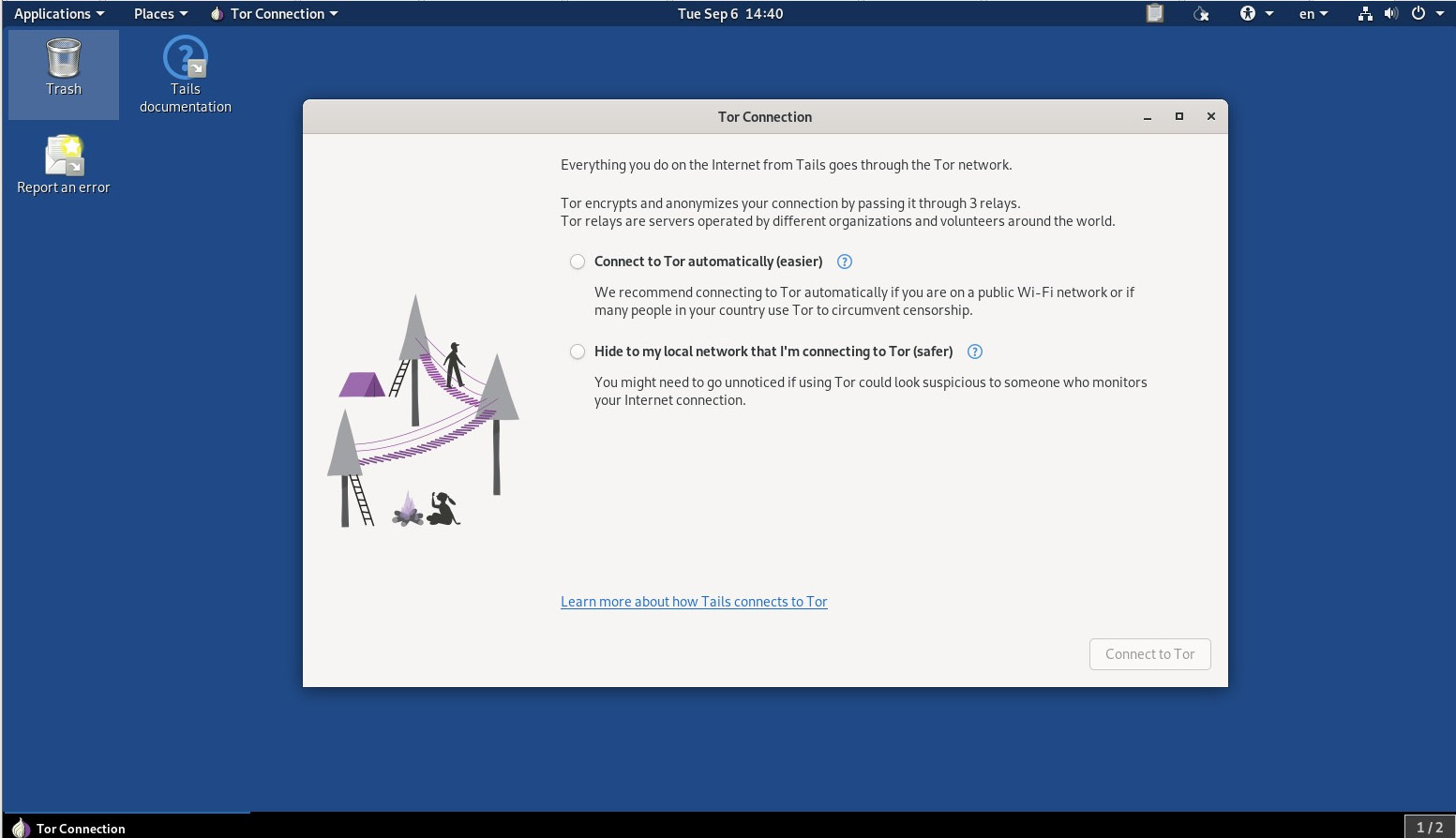
Figure 10.23: The Tails OS needs to connect through the Tor network
Everything you do with the internet from Tails goes through Tor, which maintains network-level anonymity. As we know, Tor encrypts your internet traffic through three relays that are operated by volunteers around the world. There are two options in Tails to connect to Tor:
- Connect to Tor automatically – This is the easiest way to connect, especially when you are connecting to the internet using a public internet connection or you need to circumvent censorship.
- Hide to the local network that I’m connecting to Tor – This is a safer method to connect to Tor. Especially when your connection is being monitored by an ISP or when you don’t want to draw unnecessary attention when using Tor, this is the best option.
If you select the first option, Connect to Tor automatically (easier), Tails will enable another checkbox option, Configure a Tor bridge; Tor bridges are secret relays that can evade Tor restrictions. For example, some countries, universities, enterprise networks, or parental controls can block the use of Tor. In these scenarios, you can configure a Tor bridge or Tails will auto-direct to a Tor bridge if your connection is blocked and you need one. Then you can click Connect Tor to connect Tails to the Tor network. This will connect Tails to the Tor network and direct internet traffic through Tor.
If you are using any other OS, it will store the following:
- All the websites you visited, including the sites you visited in private mode on the browser
- Every file you opened, even if you delete them
- All the passwords you use, even using a password manager
- All the storage media you connected to the device and all the Wi-Fi networks to which you connected
When you use Tails, it will never write anything on your hard drive. Everything you do will remain in memory. When you shut down or restart Tails, everything will be removed, and Tails will always start from the same clean state. If you really wanted to store some data, you could create encrypted persistent storage on the USB stick where Tails operates. This option is available only if you need it.
Tails comes with a ready-to-use set of applications, which can be used with safe default settings to work on sensitive documents if required and communicate safely. These preconfigured applications include the following:
- The Tor browser for browsing with the uBlock Origin browser extension ad blocker
- LibreOffice, an open source office suite
- Thunderbird, an email client for secure email communication
- KeePassXC, a password manager and generator
- OnionShare, a secure file share over the Tor network
The default settings and the configurations of the applications that are readily available on Tails are safe to use even without additional configuration. For additional security, if any of the applications try to connect to the internet without Tor, the application will be automatically blocked by Tails.
When using Tails, every bit of communication goes through the Tor network. As we discussed before, Tor encrypts the traffic using three secure relays in different locations around the world. Relays are maintained by different volunteers and organizations around the world.
A single relay out of three relays participating in any communication in Tor doesn’t know all the information about the communication. When traffic is generated, the first relay only knows about the source of the traffic but not the destination of the traffic. Out of the three relays, the third relay only knows about the destination but not the traffic source. Since the traffic is encrypted using different keys from one relay to another, relays don’t really know much information about the communication.
When using Tails connected to Tor, it prevents online censorship and surveillance at multiple layers. This prevents someone from monitoring you and your activities on the internet. Even if you are from a region or country with heavy censorship enforced and even Tor blocked, you can still use Tor bridges to hide that you are connected to Tor. This completely prevents advertisers, trackers, and anyone who is monitoring you from tracing you unless you reveal yourself or your real identity on blogs or any online services. If you are using pseudonyms instead of real identities, online trackers won’t be able to trace you again. The best part is using Tails and Tor is completely free!
Qubes OS
Previously, we discussed Tails, which provides privacy and anonymity at the OS and application levels. Since Tails connects to the internet through Tor, it also maintains anonymity at the network level. Qubes OS is a security-oriented OS that takes a different approach to providing security through isolation. Qubes OS is a free and open source distribution that provides desktop computing over virtualization powered by Xen. Qubes OS provides the ability to create and manage isolated compartments known as Qubes, leveraging Xen-based virtualization. Even Edward Snowden, an American former computer intelligence consultant who became popular in 2013 after leaking highly classified information from the American Security Agency, used Qubes OS for his work. You can download Qubes OS at https://www.qubes-os.org/downloads/.
As per the Qubes OS tagline itself on the Qubes home page, “a reasonably secure operating system,” it provides security through virtualization, using compartmentalization and integrated privacy features and allowing freedom. The approach taken by Qubes is virtualization, which provides security-over-virtualization. For example, in Qubes OS, you can run the same browser side by side on different security domains – while logged in to your account on one browser for a specific service, the other browser can work without logging in, as both browsers will run on different virtual instances where it creates two separate sessions on the same browser. The reason is both browsers are working on different domains with separate sessions, technically on separate virtual instances. In Qubes OS, separate virtual machines are used to separate and compartmentalize the environment. Technically speaking, it’s like running multiple virtual machines on the same environment, which is integrated by Qubes. For this reason, Qubes doesn’t support the live OS scenario that we discussed before and it would not be totally compatible to install Qubes on a virtual machine, as then it would be nested virtualization.
VPN solutions
When it comes to maintaining anonymity and privacy, we cannot ignore VPN solutions. VPNs have been around for a long time, even before the internet was introduced. Before the internet was introduced, there was no common way to connect multiple networks. The only available option was to use someone else’s network that was already implemented to connect two networks. For example, let’s say you had a Local Area Network (LAN) in one geographical location and you had another LAN in a different geographical location. If you needed to communicate from one LAN to another since there was no internet at that time, you could use an already established network maintained by a different company, but the question was that even if the physical network was there, when you connected your LAN to it, the company owning the network could see the communication that you sent through it. To overcome this problem, traffic between one LAN and another LAN was encrypted so that the company providing the infrastructure to connect two LANs could not monitor the traffic. The term “secure VPN” was used for this type of solution.
When the internet was introduced, it provided a great way of not only interconnecting two networks but the same technology also allowing a device in one geographical area to connect to a LAN in a different geographical area through the internet securely. Since the connection was encrypted, they could use even the inherently unsecured public internet for this secure communication. A VPN extends a private network through a public network, which allows users to communicate securely as the VPN provides security, functionality, and management. Initially, VPNs were created by establishing point-to-point connectivity through dedicated circuits managed by different companies, but now, the same implementation can be done over the public internet using tunneling protocols. When using VPN solutions, you can configure different types of VPN solutions including the following:
- Point-to-site VPN – When configuring point-to-site VPNs, you can connect one device to a LAN over the public internet securely. This is helpful for working from home and remote worker scenarios.
- Site-to-site VPN – This implementation supports connecting two LANs together over the internet or an intermediate connection provided by an ISP. When the connection between two LANs is established, the devices connected to the LANs can communicate with each other as if they are on the same local network.
Typically, in point-to-site VPN implementations, VPN servers are responsible for accepting requests coming from VPN clients. The VPN server has a public IP address to which VPN clients are initiating the connection. Clients usually need VPN client software to be installed on the client device unless the VPN configuration is native (for example, if you use a Microsoft server to configure as a VPN server, Windows clients have VPN client capability built-in and you don’t have to install any client software). A VPN client is configured with connectivity information such as the IP of the VPN server, tunneling protocol information, and authentication information.
Even though the classification of VPN solutions is into point-to-point and point-to-site, there are many other classifications of VPNs including the following:
- Based on the tunneling protocol used to establish the VPN
- Based on the topology of the VPN – as an example, a hub and spoke VPN or mesh VPN
- Based on the level of security on the VPN
- Based on the number of simultaneous connections configured on the VPN
When considering privacy and anonymity, this technology provides a range of benefits including the following:
- Confidentiality – Since the traffic is encrypted by the tunneling protocols, even if someone sniffs the network, they won’t be able to understand the communication without the key.
- Authenticity – Since every connection must be authenticated using a password, key, or certificate, this ensures authenticity, which prevents unauthorized access to the communication.
- The integrity of the communication – VPN uses hashing functions to ensure the communication is not tampered with.
There are many free and commercial solutions that can be used to maintain privacy and anonymity. We discussed the configuration of a free VPN solution known as OpenVPN in Chapter 7, Introduction to Cyber Anonymity.
VPN servers have a capability known as Authentication, Authorization, and Accounting (AAA), which means VPN servers are authenticating the requests, providing access only to the authenticated users, and keeping information about the connections. This means that even though VPN solutions have promising capabilities to improve privacy and anonymity, they also collect and keep information about the connections made. In a corporate environment, it is acceptable to keep a track of all the connections. When it comes to privacy and anonymity, this is a major concern. This capability varies depending on the solutions. Because of this, we need to look at solutions that do not collect or keep information about the connections if we are looking at maintaining anonymity.
As we discussed before, VPN servers or service providers perform authentication. This means they validate the users. Even though some of the VPN service providers claim that they provide complete anonymity, the reality is these service providers can see your IP addresses and your whereabouts, as you need to register on the service by providing your information and they can even keep this data in their logs. Some VPN service providers provide an acceptable level of privacy with strong encryption along with a no-logs policy. They won’t guarantee complete anonymity, but they ensure your online activities are kept secret. The best thing about VPN services is that they encrypt your traffic during communication, which enhances privacy even if you are connected to an untrusted public Wi-Fi network or even if your ISP is trying to monitor you. As we discussed before, privacy and anonymity are two different concepts and most VPN service providers use the term “anonymous” just to refer to providing a stronger VPN with zero logs, which actually means they provide privacy. However, the advantage is that even if surveillance agencies wanted to analyze the traffic, they wouldn’t be able to do that since the services aren’t maintaining any logs. If you want to be truly anonymous, it’s better to use a service such as Tor, as we discussed earlier in this chapter, rather than just a VPN solution.
Let’s look at some of the popular VPN solutions and evaluate how they improve privacy and anonymity. When comparing available solutions, you will understand which solutions are better in terms of maintaining privacy and anonymity. Since our main objective is to maintain privacy and anonymity, we need to consider whether these VPN solutions provide the following:
- Zero logs or a logless policy – the VPN solution shouldn’t be keeping logs about the connections
- Strong encryption with proper implementation – it should provide well-implemented, stronger encryption
- Registration and payment options that encourage anonymity – for example, using pseudonyms to register and cryptocurrency for the payments
- The capability to select connections in multiple geographical areas
- Additional security and privacy features
Considering these facts, let’s try to assess some of the popular VPN servers that claim to provide anonymity:
- VyprVPN – VyprVPN is a reputed VPN service provider that operates from Switzerland, which we discussed earlier as a highly reputed location when it comes to privacy. VyprVPN maintains a zero-log policy, which means that they don’t maintain any logs of the connections made through VyprVPN. VyprVPN also claims that they don’t keep any information related to your browsing data and don’t pass your information to any third party. This company owns all its servers and hardware, so they do not depend on any other service provider. The VyprVPN no-log policy is audited independently and publicly (they claim that they are the first company in the industry to audit a no-logs policy). You can get VyprVPN at https://www.vyprvpn.com/buy-vpn and it provides a 30-day money-back guarantee. VyprVPN confirms that they run their services totally without any third parties and even using their own DNS, known as VyprDNS.
From the easy-to-manage user interface, you can select any VPN location that you want, with server clusters located in North America, South America, Europe, Asia, Africa, and Oceania from over 700 VPN servers. Each location is powered with top-of-the-line hardware for faster connection and better speeds. They have over 300,000 available IP addresses and over 70 server locations and guarantee that “no third party will ever have access to your privacy.”
- ExpressVPN – ExpressVPN is another renowned VPN solution that is popular as one of the best VPNs to provide anonymity with its zero-log policy and stealth servers. ExpressVPN provides services from 94 countries at the time of writing and counting. Users can switch often over any country without limitation. ExpressVPN supports users to stream, watch, and listen to censored content and blocked websites around the globe even while traveling. ExpressVPN supports IP address masking, as you are connecting over their servers, which mask your IP address with an ExpressVPN server IP. You can subscribe to ExpressVPN at https://www.expressvpn.com/order.
ExpressVPN provides more promising features in terms of anonymity, as it allows users to pay for the subscription using cryptocurrency (for example, you can pay for an ExpressVPN subscription using Bitcoin). ExpressVPN supports cross-platform, as you can use ExpressVPN on Windows, mac, iOS, Android, Linux devices, and even routers and game controllers. ExpressVPN also supports a range of advanced features including the following:
- VPN split tunneling – Routing some traffic over a VPN while the rest of the traffic accesses the internet directly.
- Trusted servers – These servers do not write anything to hard drives to ensure anonymity.
- Network Lock kill switch - This lock keeps data safe by blocking all traffic if the VPN connection is down without directing through direct internet.
- Private DNS – ExpressVPN maintains an encrypted DNS service on every server to make sure connections are safe from DNS-level attacks.
- Best-class encryption – Data is protected by Advanced Encryption Standard (AES) 265, which is the default worldwide accepted encryption standard.
- Zero-log policy – ExpressVPN never logs traffic data and connection-related data, DNS queries, or anything that can identify you.
Typically, VPN solutions don’t provide complete anonymity, but ExpressVPN provides a faster and more reliable VPN solution that completely conceals your online activities from governments, ISPs, or any surveillance agency trying to track you. While providing a promising set of features, ExpressVPN has the capability of obfuscating your traffic to conceal it from ISPs by disguising it as regular HTTPS traffic.
- NordVPN – NordVPN offers secure servers in around 60 countries and over 5,000 secure servers to provide its VPN service. NordVPN accepts cryptocurrency for payment, which ensures anonymity when subscribing to the services. When you subscribe to NordVPN, malware-blocking tools come as part of the subscription. NordVPN maintains a strict no-log policy that does not track, collect, or share your private data. NordVPN’s client provides an easy-to-use interface where you can get all these benefits with just one click. You can subscribe to NordVPN at https://nordvpn.com/pricing/deal-nordvpn/.
Apart from the preceding services offered by NordVPN, it also provides a set of advanced features including the following:
- Multiple devices – You can use up to six devices with a single subscription, securing all your communication, even though you use multiple devices for your communication.
- Faster VPN – Typically, VPN services make connection a bit slower, as they do a lot of work in the background, such as encryption and encapsulation, but NordVPN both provides security and speed.
- Threat protection – NordVPN supports threat protection against a range of threat actors, including viruses, infected websites, and trackers.
- Private Internet Access (PIA) – PIA has gained a good reputation within online communities for its unique advanced privacy and security features. According to their tagline, “100% risk-free, no logs,” this provides a sense of security for its users. PIA maintains a strict no-logs policy that does not keep any logs for later investigation. PIA provides access for up to 10 devices with a single subscription, offering a dedicated PIA app for every platform. You can subscribe to PIA at https://www.privateinternetaccess.com/buy-vpn-online.
Thousands of servers around the world from undefined countries provide easy access to censored content regardless of where you live. PIA is completely open source, which makes it the most secure of all, as anyone can access and check the source code. PIA has built-in ad blocking that blocks ads, trackers, and malicious websites to provide users with a faster and safer internet browsing experience. PIA also supports a kill switch, split tunneling, which we discussed before, torrent support, and highly flexible settings, including support for various themes, OpenVPN encryption, obfuscation, and port forwarding. PIA has also proven its zero-log policy a couple of times even if the origin is the United States – in front of a United States court, it has been proven that PIA doesn’t collect any logs of the connections made by the users.
- PrivateVPN – PrivateVPN is a relatively new VPN service from Sweden. Especially for new users, it gives a higher level of benefits, as it’s just easy to use for anyone, even if you don’t have experience using VPN solutions before. You can subscribe to PrivateVPN at https://privatevpn.com/prices/pvpndealen. PrivateVPN has a range of additional features to offer, including the following:
- Zero data logging policy – No traffic logs or connectivity logs kept.
- Leak protection – Your identity will be safe even if you suddenly disconnect from the VPN.
- Encryption with AES 256 – Highest encryption in the industry.
- Servers in 63 countries – Get access from over 60 countries.
- Kill switch feature – Automatically suspends internet connection if you disconnect from PrivateVPN.
- Simultaneous connections – PrivateVPN is the only provider to connect to six devices simultaneously, all to unique IP addresses.
Logless services
When concentrating on cyber anonymity, it is very important to understand the layers at which your information is collected and how they can be accessed by ISPs, governments, and other snoopers. We have discussed the different layers that collect your information. In the previous section, we discussed how important VPN solutions can be for cyber anonymity, but it can be challenging if snoopers can get information from VPN solution providers, as they can see your activities from the logs that are maintained by them. The best solution for this is logless or zero-log VPN services. The reason is that if the VPN service is not collecting logs, no one, not even VPN solution providers, will not know your activities on the internet. Even in the worst case, if law enforcement wanted to analyze your activities while you were on the VPN connection, they would not be able to do so, as there are no logs whatsoever collected by the VPN solutions provider if they maintain a zero-log policy. Some of the VPN service providers even audit their services on zero-logs policy using independent and public audits. Some VPN service providers have proved during court cases that they never collect logs.
The tricky part is that even though some VPN service providers claim that they don’t collect logs, they still keep logs. Because of this reason, before selecting a VPN service provider, you should check whether they conduct independent audits against their zero-log policy, whether they have any mechanism for leak protection, where their services are offered from (as an example, we already discussed Switzerland has strong jurisdiction to protect privacy), and whether they have services such as a kill switch feature to automatically suspend the connection when the VPN is disconnected. Some service providers even keep the services in volatile memory, meaning they never write anything onto hard drives. Importantly, when subscribing to these services, if the users are given the option to make payments using cryptocurrency such as Bitcoin, this will be a definite advantage when maintaining anonymity. Otherwise, users must reveal their real identity to the VPN service provider along with credit card payment information, which will provide the option for them to validate the real whereabouts of the users and compromise anonymity.
We discussed how an OS runs on a USB connected to Tor and can provide anonymity at multiple layers, taking Tails as an example. The idea is to understand how to battle at multiple layers to maintain anonymity in the preying eyes of attackers. There are various options available to ensure anonymity at multiple layers. Apart from the Tor chain proxies, we discussed how VPN solutions can be effective and useful in this regard, especially VPN solutions with zero-log policies. When you look at the multiple layers that we have to consider when maintaining cyber anonymity, you must be thinking it’s cumbersome. If a layman or a basic user wanted to maintain anonymity on the internet without much of a technical background, how would they maintain and configure all this before connecting to the internet?
To provide an answer to this question, there are easy-to-use free OSes available for such scenarios that come with secure default configuration, easy-to-use graphical user interfaces, and no additional configuration required to maintain cyber anonymity at multiple layers. The best example is Whonix, which is a security-hardened OS designed to provide anonymity on the internet.
The Whonix OS
Whonix is a security distribution based on Kicksecure. Kicksecure is a security-hardened Debian-based Linux distribution that provides better protection from malware attacks. You can download Whonix, which is an easy-to-use and beginner-friendly open source distribution, from here: https://www.whonix.org/wiki/Download.
The main objective of Whonix is to provide stronger privacy and anonymity for users with any knowledge level. In particular, they are trying to keep Whonix an easy-to-use, beginner-friendly, and free OS to overcome all the obstacles we discussed before to being protected and anonymous when surfing the internet. The Whonix website home page provides an interesting comparison between Whonix and VPNs with regard to privacy and anonymity and shows how secure Whonix is when compared to the VPNs that we discussed. Other than hiding your IP address, which is a unique identifier when you access the internet commonly supported by both Whonix and VPNs, Whonix provides a range of safety features in a single OS that most of the VPNs don’t provide:

Figure 10.24: Comparison between the Whonix OS and VPN solutions
Whonix supports a range of additional privacy and anonymity features that VPNs don’t, including the following:
- Hidden Identity – Whonix doesn’t just hide your IP address and location; it also protects you from browser and website fingerprinting (protects you from others snooping on your browser activities and your information from being collected on websites).
- No Logging – Due to Whonix’s fundamental architecture, it cannot log your IP address or activities performed when using Whonix, which makes it the perfect OS for anonymity.
- Leak Shield – Whonix can completely protect you from unintentional leaks. Even if you use a VPN, some applications can connect directly to the internet, completely de-anonymizing the user. Whonix has a watertight leak shield, preventing any of the traffic from directly connecting to the internet.
- Server Relays avg. – Servers used to relay the traffic must not understand the user or identifiable information about the user; this can only be achieved by using multiple relays maintained by independent owners with onion-layered encryption. Most of the VPN services claim that they provide server relays and then these are typically maintained by the same company. Then, the anonymity is questionable.
- Virus / Malware Protection – Even if you are protected at all the layers, if the OS is infected, attackers can still steal your data, including personal information. Whonix is based on Kicksecure, which is a hardened and well-documented open source Linux distribution, so Whonix is inherently secure.
- Keyboard Typing Cloak – Nowadays, attackers are very advanced and use complex technologies, including keyboard typing patterns, to understand user behaviors and identities. Whonix protects you from these types of attacks.
- Timestamp Attack Protection – Since users connect from different time zones, exposing user time zone synchronization data can also reveal a user’s identity. Whonix can protect you from these types of attacks.
- App Stream Isolation – There are a set of pre-installed apps in Whonix by default. Whonix has the capability of routing distinct application traffic through a different path, which provides additional security.
- Open Source / Freedom – Whonix is a fully open source product, which means anyone can review the code for suspicious content. Independent security experts continuously review the code, which makes Whonix more secure in terms of privacy and anonymity.
- Pricing – This is the best part! Whonix is completely free and open source, only relying on donations. Whonix doesn’t support any kind of advertising that collects any kind of user data.
- Kernel Self-Protection – Whonix has preconfigured kernel hardening settings recommended by the Kernel Self-Protection Project, which makes the Whonix kernel more secure against complex attacks.
- Built-in advanced firewall – The Whonix firewall is pre-configured specifically for security and anonymity.
- Brute force defense – Whonix provides protection against different types of brute-force attacks using pam tally2, which is a module in Linux that can be configured to lock user accounts after a certain number of failed user login attempts.
Whonix is available on a range of platforms, including Windows, macOS, Linux, Debian, Kicksecure, VirtualBox, Qubes, USB, and KVM.
There are two options to select when downloading Whonix as beginner-friendly:
- Easy-to-use Xface with a graphical user interface
- Terminal only with a CLI for advanced users that only have low-power systems consumption requirements
You can select any of these Whonix versions depending on your requirements. Let’s say we’ve chosen the Windows user version with the GUI Xface beginner-friendly version. This will download the Whonix.ova (Open Virtual Appliance) file. Once you have downloaded the .ova file, you can import it to VirtualBox. VirtualBox is a free, general-purpose full virtualization platform powered by Oracle. Installing and configuring VirtualBox is like the VMWare workstation that we discussed before. VirtualBox can be downloaded from https://www.virtualbox.org/wiki/Downloads for free. Let’s say you have installed VirtualBox on your device. Then, you can import Whonix.ova directly to VirtualBox using VirtualBox Manager. Open the VirtualBox menu, click on Import, select Whonix-XFCE-16.0.5.3.ova, and click Open. Once open, you can change the hardware configurations if required, and this will import two virtual systems:
- Whonix-Gateway – This connects the traffic to Tor servers.
- Whonix-Workstation – This will be in a completely isolated network and connect to Gateway. You will not be able to connect without Gateway:

Figure 10.25: Importing Whonix to VirtualBox
First, you need to start Whonix-Gateway, as it will be routing all the traffic to the Tor network. You can start Whonix-Gateway by simply double-clicking on it. When starting Whonix-Gateway for the first time, it will prompt you to configure how you want to connect your Whonix box to the internet. You cannot use Whonix-Gateway to access the internet, as browsing is disabled on Whonix-Gateway by default:

Figure 10.26: Whonix-Gateway settings to connect the Whonix workstation to the Tor network
There are three configuration options as you can see. The first option is the best for most scenarios where it will connect Whonix-Gateway directly to the Tor network. The second option to configure will be useful if Tor is censored and blocked and you need to use Tor bridges, as we discussed in the previous section. The last option is to disable Tor, but it will prompt you next time on how you want to connect. This configuration can be changed later by just running Anon Connection Wizard under the System tab in the Whonix menu. Once you click Next, Whonix-Gateway will connect to the Tor network to provide a higher level of anonymity.
Then, you need to start Whonix-Workstation by double-clicking on it, as browsing is disabled in Whonix-Gateway:

Figure 10.27: Whonix-Workstation hides your whereabouts completely
Whonix-Workstation also comes with a range of apps that are preconfigured with the relevant security settings to ensure application-level anonymity, including the following:
- Tor browser – Protects you from browser fingerprinting to get rid of trackers.
- OnonShare – Open source program that allows users to send and receive files, maintaining anonymity by utilizing the Tor network.
- Thunderbird – Secure open source email client that supports protection and email encryption.
- KeePassXC – Open source strong password generator and password manager.
- HexChat – Open source hardened internet relay chat.
- VLC – VLC media player with JavaScript disabled, protecting from fingerprinting while accessing multimedia files.
- Electrum – Electrum is a popular Bitcoin wallet focused on speed and simplicity.
- Bitcoin – Decentralized digital currency that enables instant payments over the internet, maintaining anonymity.
- Monero – Privacy-centric cryptocurrency, allowing anonymous digital payments without central authority.
These tools are pre-installed in Whonix-Workstation, which is ready to use. When you are using Whonix, it protects you from a range of snooping and information gathering at multiple layers. Whonix is a great, free, open source, less complex solution that can be even used by a beginner without much technical knowledge, as Whonix looks after all the layers that we discussed, maintaining privacy and anonymity with the support of the Tor network.
Summary
In this chapter, we discussed the tools and techniques that can be used to maintain cyber anonymity, using proxy chains and anonymizers and taking Tor as an example, using censorship circumvention, taking Psiphon as an example, using a live OS, with Tails as an example, a range of VPN solutions and how VPN solutions can protect your privacy, and logless services, with Whonix as an example.
After this chapter, readers will understand what proxy chains and anonymizers are and improve their knowledge on censorship circumvention, understand how live OSes maintain anonymity and how they work, understand how VPN techniques work and maintain cyber anonymity, and finally, understand how to use logless services to maintain cyber anonymity.
Cyber anonymity is very essential, as most devices, applications, and browsers collect information on every single activity that you perform in cyberspace. Once you know how to maintain cyber anonymity, depending on what your objective is, it will be helpful to perform tasks without disclosing your information. The objective of this book is to give you enough of an understanding to work with the internet and internet-connected devices safely by maintaining cyber anonymity. This book not only provides conceptual knowledge and understanding but also tools that can be used to maintain cyber anonymity.
