2
Ways That Attackers Use Your Data
The constant data breaches reported around the globe have become common news in today’s world. Many hackers and hacker communities keep on compromising systems to steal data. These data breaches range from personal-level data breaches to enterprise-level, damaging companies’ economies and reputations. Often, attackers use stolen data to commit more crimes or as entry points to attack other companies.
When it comes to concentrating on data privacy in cyberspace, it is important to understand the ways that attackers use stolen data after data breaches.
In this chapter, we will be focusing on the following:
- Impersonation and identity theft
- Technical, procedural, and physical access
- Technical controls
- Procedural controls
- Physical controls
- Creating vulnerabilities to compromise systems
- Increasing the attack surface using sensitive data
Once privacy is compromised, attackers will have your data and information. When attackers have access to personal or sensitive information, they can utilize it for different purposes. Understanding the different ways that attackers use your information will help you to take precautions and even if there is a breach, this will help you to manage it effectively.
Primarily, attackers can use stolen data for impersonation and identity theft.
Impersonation and identity theft
Impersonation is when the attacker uses stolen data to pretend to be someone else. This information can be collected from social media or any type of privacy compromise. Then, the attacker can pretend to be you for different purposes.
Identity theft is when an attacker uses stolen data to access your bank accounts and create fake IDs and even passports. Also, attackers can use stolen personal information to get financial benefits such as car loans, credit cards, and checks without your knowledge or any type of consent. When they receive financial benefits, you will be naturally liable for them. The information stolen can be different from country to country and region to region. For example, in the United States, the most targeted piece of personal information is your social security number. Attackers use this to get financial benefits and even to release criminals on bail using stolen social security numbers, and eventually, the real owner will be liable if the criminals do not show up in the courts. Then, the real owner will be blacklisted financially and legally. They will not be able to get financial or any other benefits as they will have bad credit records.
Both impersonation and identity theft are illegal and can be prosecuted on different levels depending on the damage and the impact. Identity theft impacts millions of people annually around the world, and this can create a huge financial impact on the victims.
Impersonation and identity theft are not always a result of cyberattacks. They can be a result of reckless handling of your paper-based information. As an example, if you dump your bank account statements or credit card statements in the bin, they can be used by attackers to retrieve your information. This is often known as dumpster diving. Dumpster diving is an act of searching trash bins to obtain useful information. This information will later be used by attackers for impersonation and identity theft. Attackers can even use workstations and laptops that have been disposed of to obtain useful information by recovering data. Useful information that attackers would be interested in can include the following:
- Full name/address/email address
- Phone numbers: There are many tools available to extract phone numbers from an email, text, or the web.
- Credentials that are sent by postal mail or emails, particularly web hosting account information sent to your email address.
- Bank and financial statements.
- Important documents with personal and sensitive data.
- Health records.
- Confidential correspondence including trade secrets or business secrets.
- Employee records.
- Insurance and financial information.
The following screenshot shows stolen documents that are on the market on the dark web:
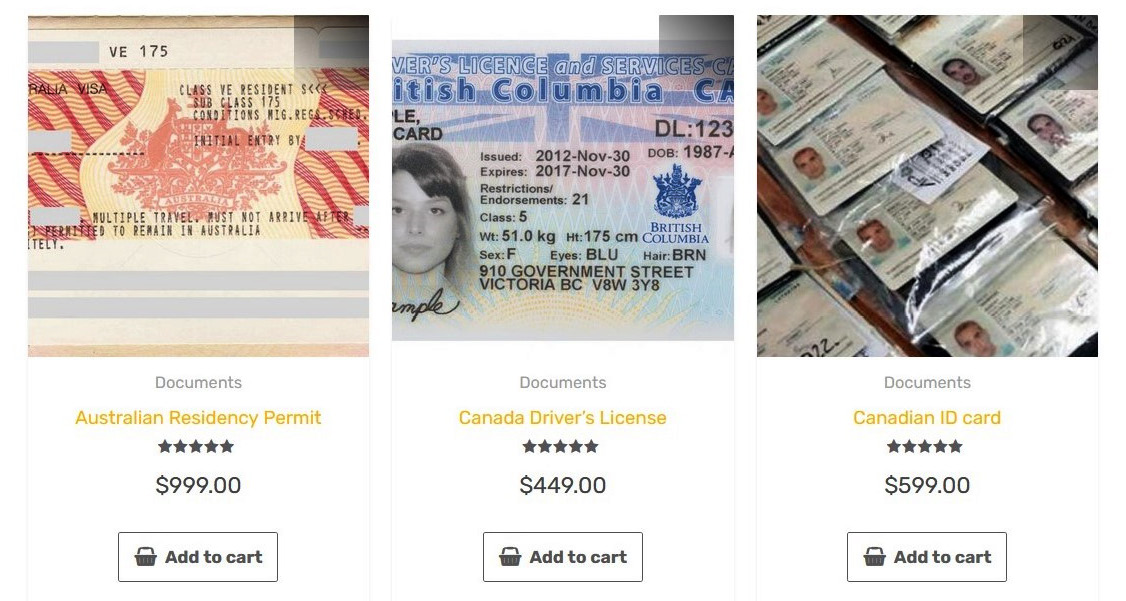
Figure 2.1 – Stolen documents available to buy on the dark web
Mostly, identity theft focuses on financial gains, but there can be other types of motivation by attackers. There are a few common scenarios in which attackers commit identity theft:
- Compromising mail accounts: When an attacker compromises mail accounts, they will hunt for useful information including unencrypted credit card information, tax-related communications, social media account-related emails, correspondence with banks, and communication with other financial services such as PayPal.
- Phishing and spear phishing: Attackers will trick users into submitting their sensitive information on fake websites that look and feel the same as authentic websites.
- Data breaches: This is when users or businesses expose sensitive information due to poor security and practices or because of hacking. Often, users or companies unknowingly share sensitive information in vacancy advertisements and professional communities such as LinkedIn.
Once attackers compromise your private or sensitive information, there are common ways attackers utilize this information:
- Using stolen information, they can apply for credit cards or loans.
- Attackers can get tax refunds transferred to their accounts.
- Attackers can redirect pre-ordered goods to their own addresses – if you order something on eBay, they can get the goods redirected to their addresses, or they can even order goods using your information.
- They can use it to cover their expenses (including medical, travel, and leisure) from your liabilities.
- Attackers can also use other benefits such as redeeming your airline miles to obtain duty-free benefits or cash.
- Attackers can get a mobile SIM card in your name to launch other attacks. When authorities trace the phone number, you will get caught instead of the real attacker.
- They can use your information to open utility accounts with electricity, gas, and communication companies, and then they will make you liable for debts for utilities that you have never used.

Figure 2.2 – Stolen documents available to buy on the dark web
As well as direct attacks, your information can be used by the attackers for indirect attacks that may create more complex and unpleasant situations. Some examples of indirect attacks include the following:
- Using stolen information, attackers can obtain mobile SIMs that can be used to call other people for different purposes including social engineering attacks and threatening people.
- They can create social media profiles impersonating you and be part of groups in which you have confidential communication to gather information.
- From the social media profiles impersonating you, they can send friend requests to your contacts and then damage your image or lure your contacts to access malicious websites, as your friends may trust them thinking they are you.
- They can launch spear phishing attacks impersonating you. Spear phishing attacks are a type of phishing attack targeting a specific individual or organization rather than everyone.
Some attacker groups may even sell your personal and sensitive information on the dark web. They sell stolen bank accounts, credit cards, and PayPal accounts on the dark web marketplaces.
The following screenshot shows how they sell stolen credit cards and other accounts for low prices on the dark web. There are many marketplaces on the dark web that sell stolen cards, bank accounts, and other financial service accounts for low prices:
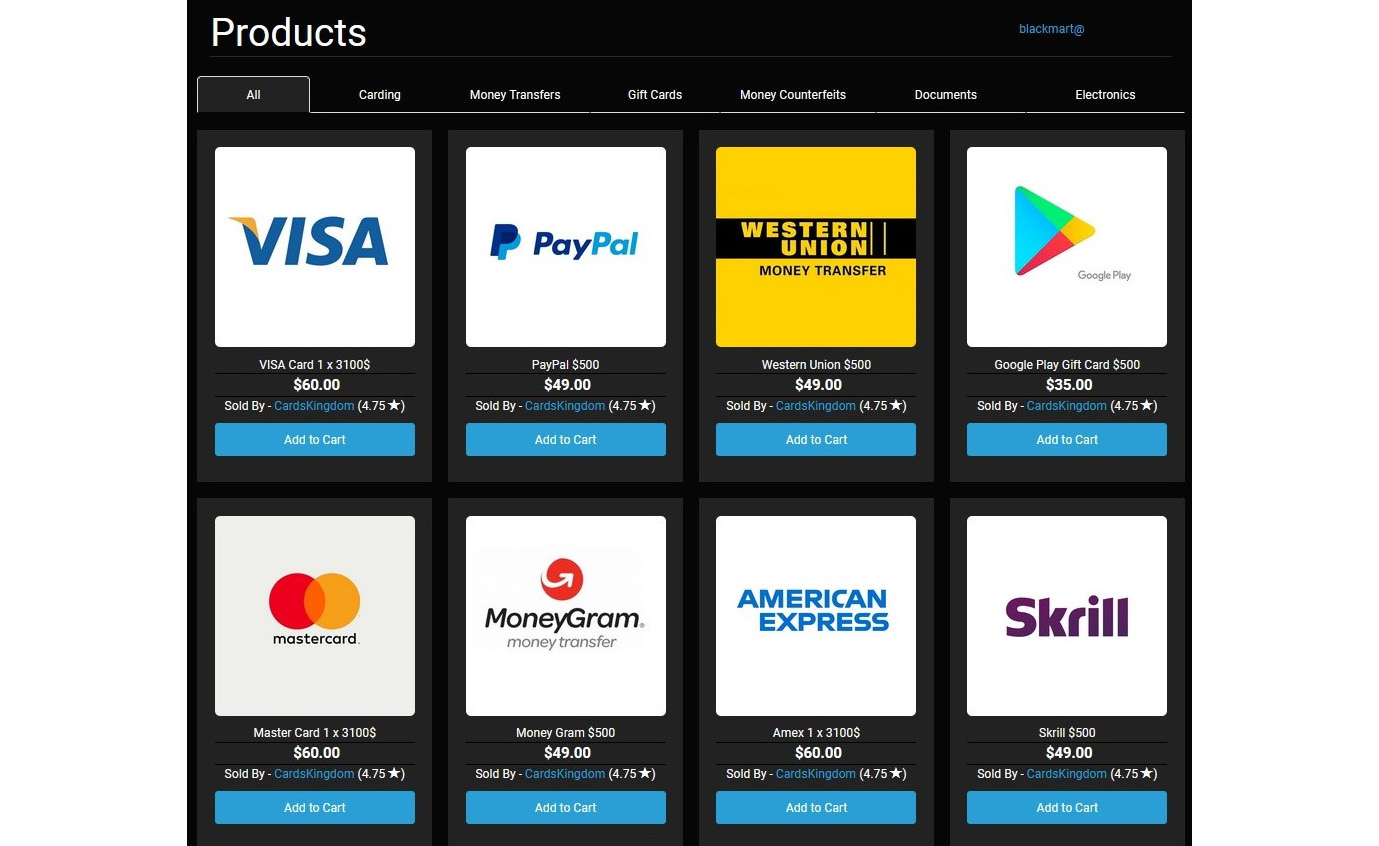
Figure 2.3 – Bank accounts with the balance available to buy on the dark web
Attackers price the stolen data in different price ranges. Social security numbers are treated as sensitive information in the US and are sold at different prices on the dark web.
In the past, there have been massive cyberattacks where attackers have stolen a massive amount of PII data. During a recent attack on Facebook, attackers stole over 500 million Facebook users’ data. The most preferred way to use stolen PII data by attackers is by selling it on the dark web. The data sold on the dark web can be used by other groups for fraudulent transactions or committing identity theft. Individual social security numbers, full names, and dates of birth are usually sold for between $60 – $80 on the dark web and among other hacker communities. The following figure shows a screenshot of things available on the dark web, including driver’s licenses and residency permits:
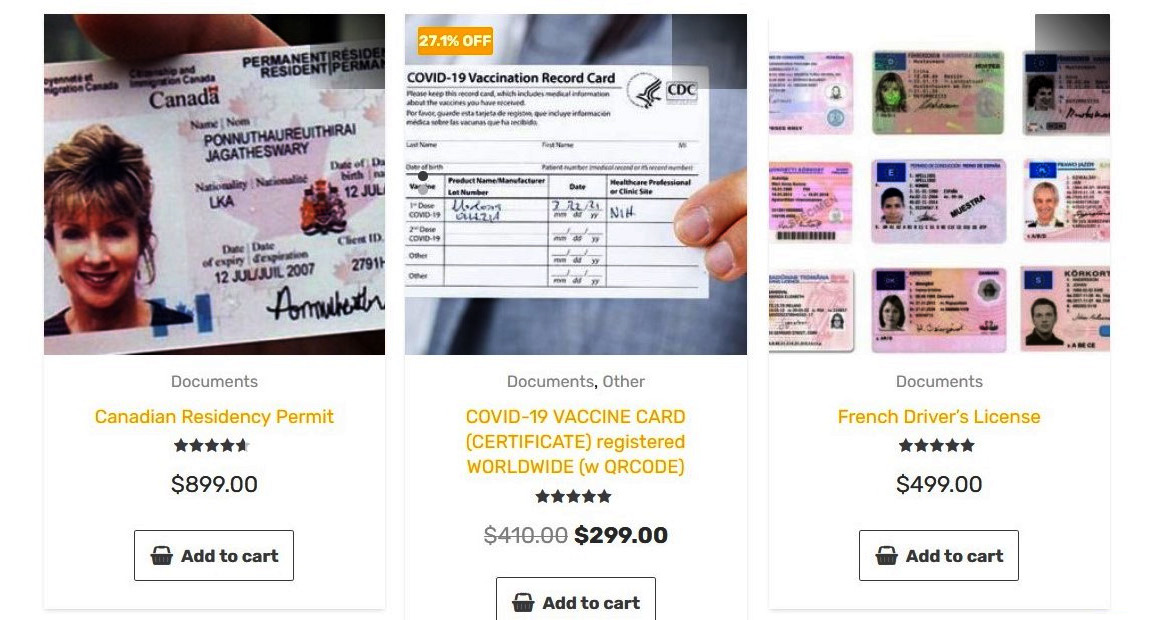
Figure 2.4 – Stolen documents available to buy on the dark web
The preceding figure shows a range of identity documents including residency permits, driver’s licenses, and other types of certificates, available to be bought on the dark web.
Technical, procedural, and physical access
We looked at different methods that attackers employ to access personal and sensitive data. We also discussed how attackers can use stolen data for their advantage. It’s important to focus on how individuals, governments, and organizations can take countermeasures to protect sensitive and personal data leakage. As a fundamental fact, any security system should protect information, assets, and people physically; physical protection is the foundation of any security system. If physical security is compromised, all other layers we discussed can be compromised quite easily.
When physical security is established, technical security mechanisms can be employed to enforce access control, information classification, surveillance, and monitoring. Procedural protection includes security control, certifications, and badges. Let’s look at this in more detail to understand how technical, procedural, and physical access support prevents attackers from assessing sensitive data:
|
Access Controls |
Physical |
Fences, gates, and locks |
|
Technical |
Access control systems, VPN, encryption, firewall, IPS, MFA, and antivirus software | |
|
Procedural |
Recruitment and termination policies, separation of duties, and data classification |
Table 2.1 – Physical, technical, and procedural access controls
Technical controls
When it comes to security, there are diverse types of controls that will be used to control access and usage of data. Technical controls use technological mechanisms to control access to resources and data. You will need to use different technical controls to control access depending on the operating system, resources you want to control access, type of the resource, and the protocol that needs to be used. Many distinct types of technical controls can be used.
Access controls
Access controls are used to authorize identity to access the recourse or object based on the required task. When designing access controls, we need to ensure that the principle of least privilege is ensured all the time, not most privilege access. The principle of least privilege states that a person should be given the minimum privileges required to complete the given task. If the person needs read-only access, they should only be given read-only access to the object. There are mainly three types of access controls in computer-based technology. These three main types of access control systems are discretionary access control (DAC), mandatory access control (MAC), and role-based access control (RBAC).
Discretionary access control
In DAC, subjects were assigned access rights to access objects by the rules. This is usually implemented using access control lists. New Technology File System (NTFS) files, a system in Microsoft and Linux, and file and folder security implementation are examples of DAC.

Figure 2.5 – DAC permissions table
This is a DAC control table, which will be referred to by the operating system kernel before providing access to any subject to any object. When it comes to implementing this, we will be using permission systems given by the operating system. If you take a Windows 10 system as an example, if you go to the properties of any file or folder, you can configure DAC-based access control. Under the Security tab, you can see the list of users including built-in and inherited users that have access to the given object, and the permission given to the users:

Figure 2.6 – NTFS access model
If you click on the Edit button, you can provide more specific, least privilege-based access to this object, as follows:
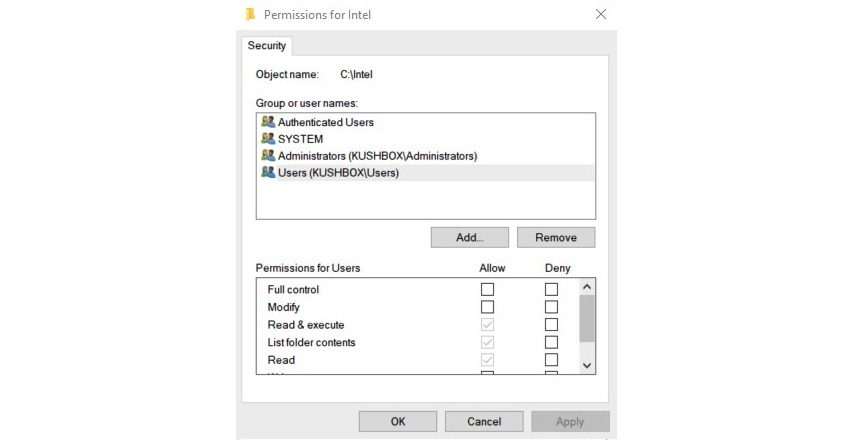
Figure 2.7 – NTFS access model
As per the given screenshot, we can provide more specific, least privilege-based access to the subjects using the DAC model. This can be useful to prevent information leakage if properly configured. Even Linux systems use the same type of DAC technical controls to provide access to the objects:
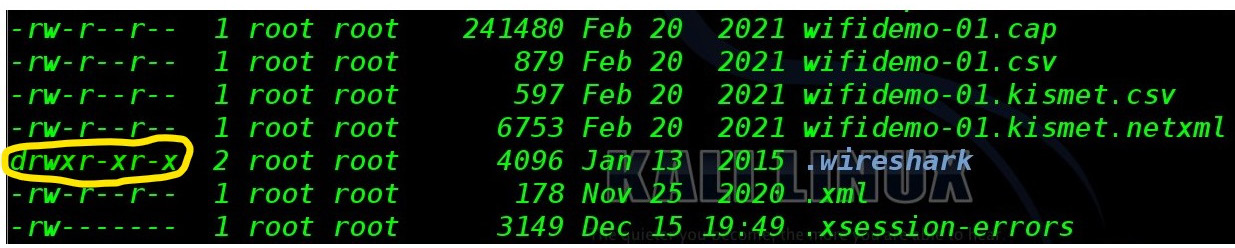
Figure 2.8 – Linux file access model
Linux systems use 10 bits to denote permissions for the users and groups to access the object. The first bit denotes the object as a directory (denoted by d) of a file (denoted by -), then the next nine bits are allocated to denote user access, group access, and rest of the world access.
Mandatory access control
From all the technical access controls, MAC is treated as strict access control and is typically used for critical systems and government access control systems. MAC uses the hierarchical method of controlling access to files, folders, or resources. Access to the resources is defined by the system administrators’ defined settings. When the access controls are configured using MAC, users will not be able to make any changes, as everything is preconfigured by the system administrators and hierarchically enforced to the below layers.
Role-based access control
Under the implementation of RBAC, other than focusing on the individual subject object-based access discussed in DAC, system administrators assign privileges to the roles. These roles can be predefined or can be created by the system administrators. RBAC is also referred to as non-discretionary access control. This gives users access to resources that are required to perform their tasks. One user can be part of one or more roles defined by the system administrator and can be used as and when required to access resources to perform their tasks.
Cloud systems such as Microsoft 365 and Azure mostly use RBAC. Each resource has a predefined set of roles and administrators can assign users based on the required task that the user needs to perform. Administrative roles and resource-based roles can be configured when implementing RBAC:

Figure 2.9 – Pre-created roles in Azure RBAC
Simply by assigning users to required roles, users will obtain the required set of permissions to perform the task.
The preceding figure shows the administrative roles, and the following figure shows resource-specific roles that can be used to define the level of access based on predefined roles:

Figure 2.10 – Pre-created roles in Azure resources
When implementing technical controls, there are many security solutions, including the following:
- When connecting to branch officers using unregulated connections such as the internet, we can use virtual private networks (VPNs). These encrypt end-to-end traffic and prevent attackers from eavesdropping on the communication.
- Implementing multi-factor authentication (MFA). MFA is a mechanism that provides an additional security layer during the authentication based on different factors including something you know, something you have, and something you are.
- Enabling a security policy with a login attempt threshold that blocks the account when a user attempts to log in more times than the threshold.
- Using conditional access policies to restrict access by different conditions including locations, devices, applications, and so on.
- Encrypting data at rest using built-in encryption tools such as BitLocker, and third-party encryption tools such as VeraCrypt to encrypt stored data.
- Ensuring devices are patched and updated with the latest security updates.
- Antivirus and antimalware solutions are properly updated and functioning.
- Device access and usage are properly logged – central logging is preferred.
- If the company allows users to use their own devices – bring your own device (BYOD) – the company must implement mobile device management/mobile application management (MDM/MAM) solutions.
- Implementing application-level control. Attackers can use application vulnerabilities and malicious applications to compromise systems, so it’s recommended to use application control mechanisms such as AppLocker.
VeraCrypt is an open source data encryption tool that uses strong AES256 encryption that can create encrypted volumes and assign drive letters directly to mounted encrypted volumes. Once you encrypt the data, attackers will not be able to access the encrypted data without the key. VeraCrypt can be used to create encrypted volumes or encrypt existing volumes including system volume. Also, VeraCrypt supports a range of operating systems including Windows, macOS, Ubuntu, Debian, CentOS, FreeBSD, and Raspberry Pi.

Figure 2.11 – VeraCrypt can be used to create encrypted volumes
BitLocker provides built-in encryption for Windows devices but is only supported for specific editions, including the Ultimate and Enterprise editions of Windows Vista and Windows 7, the Pro and Enterprise editions of Windows 8 and 8.1, and the Pro, Enterprise, and Education editions of Windows 10. However, it doesn’t support the Windows 10 Home edition:

Figure 2.12 – BitLocker can be used to create encrypted volumes
AppLocker is an application whitelisting technology available for Windows devices, introduced with Windows 7 operating systems. AppLocker can be used to restrict applications for the users based on the publisher of the application, application path, and integrity checksum (hash). AppLocker can be configured centrally and enforced using Group Policy:

Figure 2.13 – AppLocker can be used to restrict applications
Procedural controls
When you implement technical controls your security posture will be improved, but if users are bypassing technical controls or senior management is not adhering to them, their effectiveness is drastically reduced. This is where procedural controls are crucial.
Procedural controls define what the employees’ responsibilities are and how they should behave with the systems. This improves overall security posture and helps with incident prevention. Procedural controls make technical controls more effective in the following ways:
- Enforcing password policies for the organization, including the following:
- More than eight characters for the password.
- At least one capital letter.
- At least one simple letter.
- A special character.
- Banning common passwords even if they comply with the password policy (for example, Qwerty@123).
- Passwords must be changed after 35 days.
- The last 10 passwords cannot be used again.
- After three incorrect attempts, the account will get locked.
- Prohibiting password sharing.
- Every user must assign a separate account.
- User awareness training to train users on procedures and security
- Implementing disaster recovery and backup procedures
- Recruitment and employee termination procedures
- Communication procedures for sensitive information sharing
- Logging and auditing – this can help during incident handling and forensic investigatory processes
- BYOD and choose your own device (CYOD) procedures if the organization accepts these
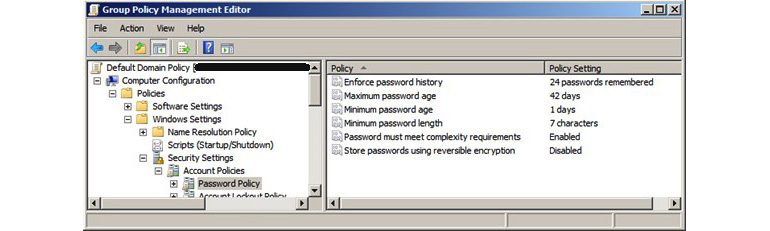
Figure 2.14 – Implementing password policies
Physical controls
Often, the importance of physical control is underestimated by individuals and organizations. But the reality is attackers can attempt to penetrate your infrastructure physically so then they will be able to bypass many other controllers. This must be prevented at any cost as, if attackers get to bypass physical controls, they will have a better chance to compromise other controllers as well. Physical controls include the following:
- Securing devices and physical access controls
- Closed-circuit surveillance cameras
- Motion or thermal alarm systems
- Security guards
- Picture IDs
- Locked and dead-bolted steel doors
- Biometrics (including fingerprint, voice, face, iris, handwriting, and other automated methods used to recognize individuals)
If someone compromises your physical security, you can install different kinds of hacker tools quite easily and get to access your infrastructure.
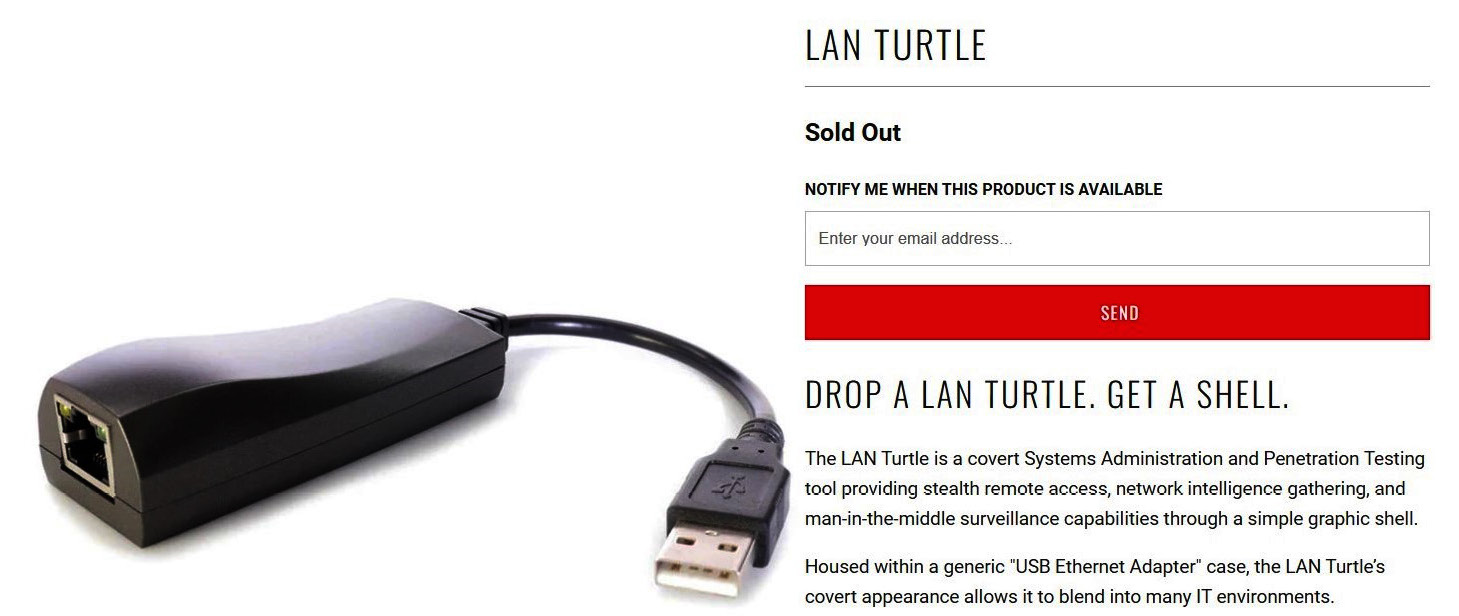
Figure 2.15 – LAN turtle to get a remote shell
A LAN Turtle is a tool that attackers can use to get access to the shell when they connect this to the network devices. If an attacker physically compromises the infrastructure, they can install this tool in a few seconds.

Figure 2.16 – AirDrive Keylogger
Once the attacker installs this device in a targeted device, they can retrieve anything you type on the keyboard from a close location over Wi-Fi.

Figure 2.17 – AirDrive Forensic Keylogger
AirDrive Forensic Keylogger provides keylogger functionality without exposing the connection; this is a USB extension cable shape and is impossible to locate. This is an ultra-compact keylogger hidden in a USB extension cable. This has an ultra-small USB keylogger module that can perform the work of a hardware keylogger.
Creating vulnerabilities to compromise systems
We discussed how attackers compromise systems and steal personal data. This can be done in multiple ways; launching an attack and compromising the system is one of the ways that attackers steal your data. To launch an attack, there must be three components to be fulfilled.
Vulnerable system
The definition of a vulnerable system is a system with existing weaknesses. This is not only an operating system. There can be different layers of the system that can be vulnerable. It can be an operating system or installed applications, in which the procedures may allow for creating vulnerability, and the protocols used can be vulnerable. This can be recovered by vulnerability assessment. During vulnerability assessment, testers will try to understand whether the targeted system has any known vulnerability. Testers can use automated tools such as Nesses Pro, Core Impact, Open VAS, and SecPoint to scan the targeted system to recover vulnerabilities. There are plenty of known vulnerability databases. The National Vulnerability Database (NVD) (http://nvd.nist.gov) is a known vulnerability database:
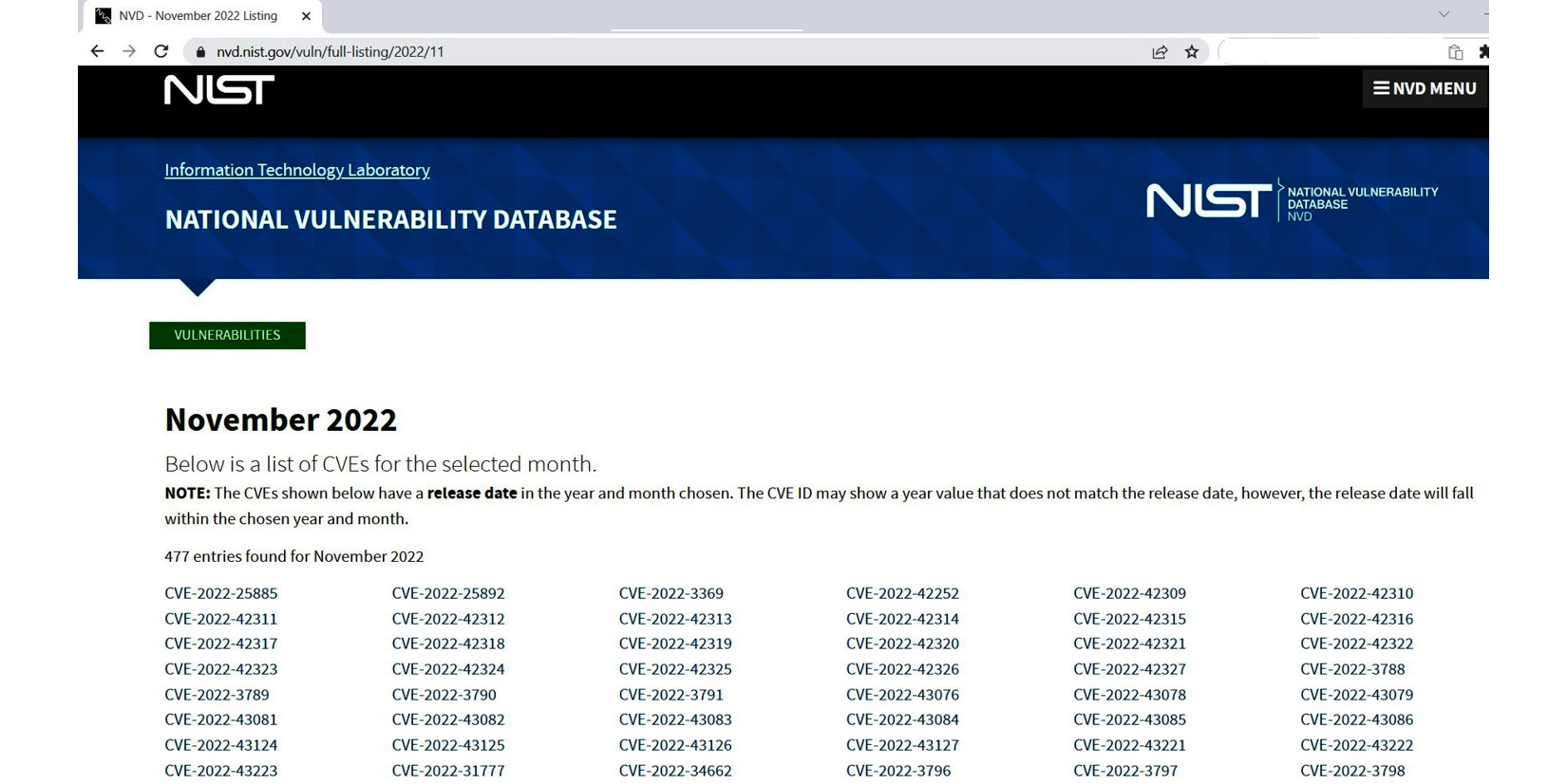
Figure 2.18 – National Vulnerability Database
From the security point of view, we need to maintain all our systems free of vulnerabilities. If vulnerabilities cannot be found, it’s much harder for an attacker to compromise systems. Then, the attacker must find a way to create vulnerabilities.
Exploit for the recovered vulnerability
Once the vulnerability is recovered, then the attacker must find an exploit to compromise the vulnerable system. An exploit is a defined way of compromising the system. There are databases and frameworks that attackers can use to find readily available exploits, or attackers must develop their own exploits.
If you access the Exploit Database (https://www.exploit-db.com), you can find many exploits developed for known vulnerabilities:

Figure 2.19 – Exploit Database
Exploit Database is a known exploit database that’s contributed to by many communities. They are constantly updating the exploit database with developed exploits. Attackers often use these exploits to launch attacks over known vulnerabilities. They can use also some frameworks, such as the Metasploit framework:
Figure 2.20 – Metasploit framework
The motivation of the attacker
To launch an attack, the motivation of the attacker is important. The reason is that even if the system is vulnerable and exploits are present, if the attacker is not motivated, an attack will not take place. Sometimes when we propose security assessments for companies, they say there is no requirement for testing as they are fully secure. No one can say they are fully secure as there can still be ways attackers can exploit your systems.
Previously, we discussed vulnerabilities of the target systems and a few databases that we can research for vulnerabilities. Still, there can be undiscovered and unpublished vulnerabilities that can lead to compromise of the system. When systems engineers and security teams suggest security solutions or improving existing security systems, sometimes management may deprioritize the requirement stating that they have been using older systems for a long time and have never been attacked. The reason can be that attackers may not be motivated to launch an attack on the infrastructure.
As we discussed, even if the systems are vulnerable, attackers will not try to exploit them if they are not motivated. Simply, attackers would wonder whether the attack was worth it. The main motivation for an attacker is money but sometimes, taking revenge or destroying the company’s image can be other types of motivation. Once, there was a guy who compromised an enterprise infrastructure just to see what his girlfriend was doing. These are various kinds of attacker motivations.
Out of the three components of attack, exploits, and motivation of attackers, we have no control. The only component that we have some level of control over is the vulnerabilities of the system. This is the reason we must conduct vulnerability assessments to recover existing vulnerabilities of the system.
Creating vulnerabilities
If the attackers have higher motivation to compromise a system and if they cannot recover any vulnerability, they will not be able to exploit it. Then, the only option available for attackers is to create a vulnerability in the system. Attackers use different ways to create vulnerabilities in your system and compromise it. These are some of the ways attackers create vulnerabilities:
- Trojans – Trojans, or Trojan horses, are types of malware that pretend to be legitimate software and are often infected through email attachments or malicious websites. Once infected, a Trojan provides attackers with access as a backdoor to the system.
- Phishing – Phishing is a type of social engineering technique where the target user or organization is misled via email or chat services. Once the user clicks a link in the email or chat, they will be redirected to a specially crafted website that looks legitimate, and the attacker will be able to steal sensitive data, typically credentials.
- Malicious insiders – If the infrastructure or system is not vulnerable, attackers might use malicious insiders or disgruntled employees to create vulnerabilities in the system.
There are many tools used by attackers to create vulnerabilities. Attackers use Trojans in many operating systems including Windows, Linux, iOS, and Android. Once the system is infected, attackers have access to the system. As an example, AndroRAT is a Trojan that can be bundled into APK files or used to create binder APK and installed on the Android device, which gives total access to the attacker. AndroRAT Binder will be used to create the apk installer, and then the APK file must be installed on the Android device:

Figure 2.21 – AndroRAT binder
When the APK is installed on the Android device, it will create a reverse connection to the attacker’s system that has AndroRat running. Once the connection is established through the configured port, it will be shown like the following screenshot to the attacker:

Figure 2.22 – AndroRAT control center window
When the connection is established, the attacker can take complete control of the device by double-clicking on the selected device if there are multiple connections to the AndroRAT control center:

Figure 2.23 – AndroRAT connection window
Once the attacker is connected to the device, there are many functions available for the attacker, including getting access to the Android device data, generating calls, sending SMS, vibrating the phone, and toasting the phone.
As well as Trojans, commercial apps are available to provide silent access to mobile devices. If you receive a mobile device as a gift, especially if the device is not a bubble wrap (bubble wrap is a term used to denote the device is unopened or sealed), there is a chance that the device has spyware or antitheft apps installed that gives access to your phone to a third person. At the very least, we need to factory-reset such devices before starting to use the device.

Figure 2.24 – Cerberus Phone Security
Cerberus is capable of a rich set of features that any attacker would expect of a good remote access tool (RAT), including locating the device, backing up data, data exfiltration, locking the device, changing the PIN, wiping data, and taking photos. Interestingly, all these capabilities and many other features will be available from any web browser or by sending special SMS text commands.
Increase the attack surface using sensitive data
Previously, we discussed the main elements of attacks including vulnerabilities. If the vulnerabilities cannot be recovered, attackers could try to create vulnerabilities. From the users’ perspective, we need to reduce vulnerabilities as much as possible. The challenge is that there can be vulnerabilities in the system that have not yet been recovered or published. We can only remove vulnerabilities that are known. Unknown or undiscovered vulnerabilities are typically referred to as zero days.
Even though we conduct vulnerability assessments, we conduct an assessment based on known vulnerabilities. To battle against zero days, we need to reduce the attacker surface. An attacker surface is a set of entry points or boundaries in the environment that attackers can use to try to enter, create connections, and exfiltrate data from the systems, system components, or infrastructure. To increase security, we need to always try to decrease the attack surface.
An attack surface can comprise the following:
- System endpoints, such as workstations, laptops, and mobile devices used to access your environment or infrastructure
- Servers in the system including domain controllers, file servers, application servers, and database servers
- Routers, firewalls, and switches
- Printers and other network-connected devices including all-in-one printers
- Identity systems, including Active Directory Domain Services or lightweight directory access protocol (LDAP)
We need to reduce the attack surface as these endpoints can introduce potential attacks on the system. For example, if you have remote desktop protocol (RDP) (which is used to establish remote access to systems) access enabled in your server that has a public IP address assigned, attackers can easily locate these servers and try to compromise them.
If you access Censys (https://search.censys.io/) and search for Windows 2003 RDP, you will find a list of Windows 2003 servers with RDP enabled, which increase the attack surface:
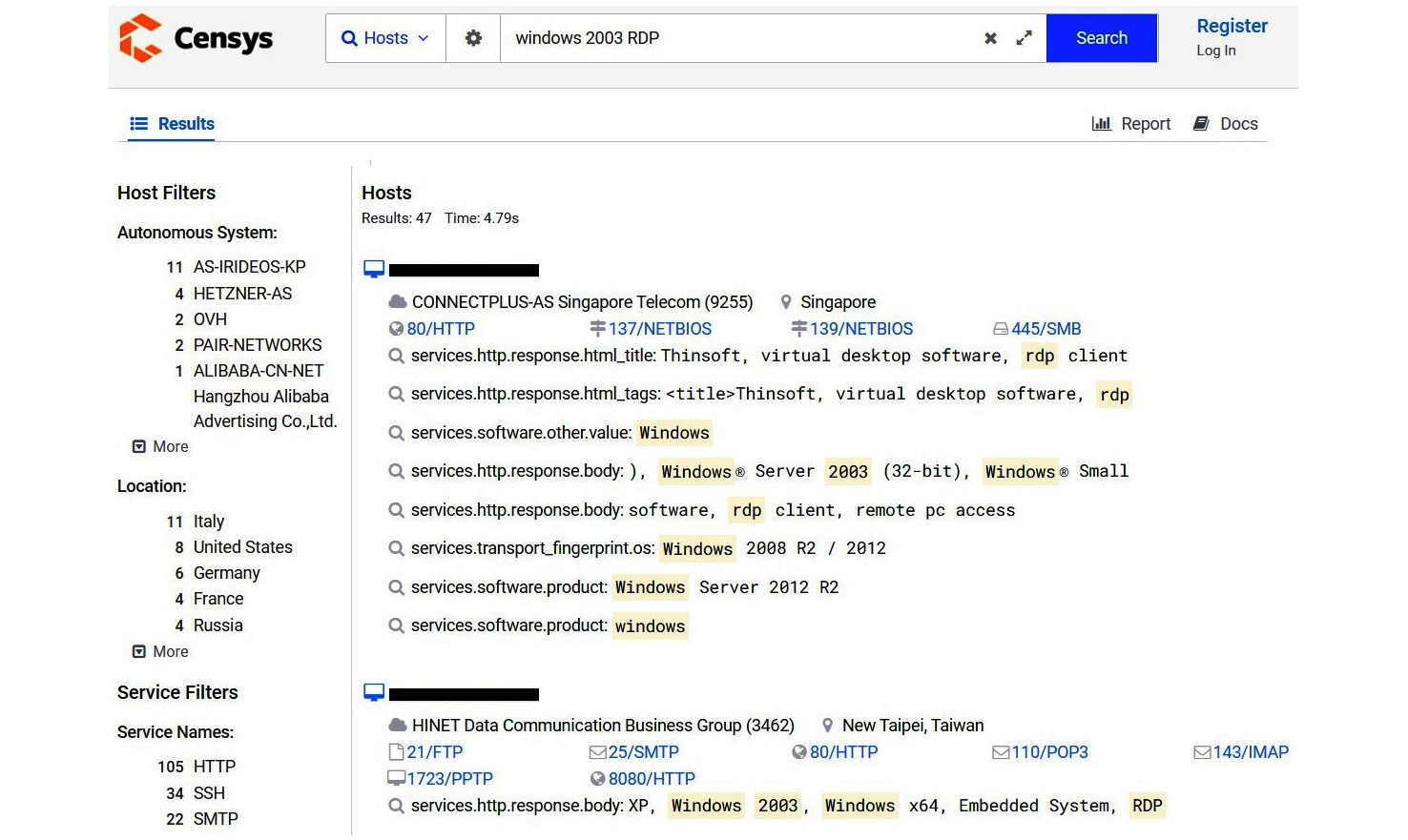
Figure 2.25 – Censys search
Once you try to connect, it will give you a connection prompt. This shows very clearly some configurations increase the attack surface.
Attackers go through five phases to launch an attack, as follows:
- Information gathering or reconnaissance – gathering information as much as possible will help an attacker launch an attack on the target more accurately
- Enumeration and scanning – this phase is to collect more specific information about the services and the ports on the target, which allows the attacker to recover vulnerabilities and map the target with exploitations
- Gaining access – this is the real exploitation phase
- Maintaining access – if the attacker needs to connect to the target another time, they do not have to go through the time-consuming information gathering and scanning phases if the attacker plants a backdoor on the compromised system
- Covering tracks – the attacker removes all traceable entries on the compromised system
From these phases, the first two phases are typically time-consuming, as the more information is collected, the more possibilities the attacker has to compromise the system.
Overexposure can reduce the time that the attacker needs to spend for the first two phases. If the attacker collects information in the ways that we discussed earlier, this reduces the time for attacks. For example, some users overexpose system information on social media such as LinkedIn, which can reduce the attacker’s time.
Sometimes, people publish selfies taken during a candlelit dinner, and exposing their official identities or credit cards on the table can be used by attackers to launch attacks, as this sensitive information increases the attack surface.
The same thing can happen with the information collected by applications, browsers, and social engineering techniques that we discussed earlier. Attackers can find a list of people working for specific organizations using a tool such as TheHarvester:

Figure 2.26 – TheHarvester search for employees working for Microsoft posted on LinkedIn
The preceding figure illustrates how easily attackers can find out the people working for specific organizations just by executing a simple command.
Creating entry points and bots
Attackers use different types of entry points to enter systems and infrastructures. As we discussed, the attack surface can be used by the attackers as entry points to the systems through different methods and attacks, including the following:
- Compromised credentials – Typically, your username and password are treated as the primary method of authentication. You can enable MFA to increase security. If the credentials are exposed to attackers, they can use the credentials to access the systems, even if these credentials do not provide administrative access. Compromised user accounts can be critical as they represent legitimate user behavior for most security systems. As well as users, there can be service accounts with the Password never expire option enabled, and local administrative accounts with the same password on all the systems that never change the password. These can be easy targets.
- Common and weak credentials – Even though we configure complex password policies, some users can use common passwords as they fulfill the basic requirement to become a complex password. Examples are Qwerty@123, Admin@123, Test@123, and Asd@123.
- Missing and poor encryption – Encryption converts plain text to cipher text, which makes it harder to understand by humans. Typically, all passwords are stored as a hash. Even if someone gets to access the hash, they will not be able to get the real password. We discussed how encryption can be used to store data, but also, encryption can be used to establish secure data in transit. If the encryption is not present, passwords sent as plain text can be easily compromised by attackers by launching man-in-the-middle attacks:
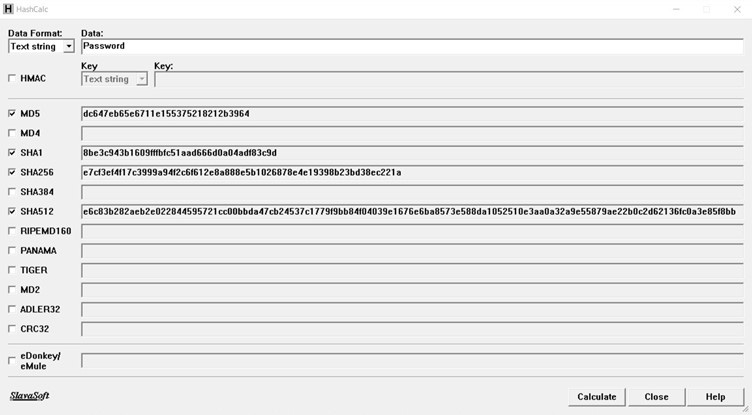
Figure 2.27 – Hashcalc generates hash codes for given plain text input using multiple algorithms
Password files will store encrypted passwords without storing human-readable plain text passwords. If the passwords are not encrypted, attackers can see the communication in plain text. As an example, when you communicate using http or ftp kinds of protocols, they don’t encrypt the communication, and attackers can easily intercept the passwords in plain text.
As an example, I’m using a Joomla CMS-hosted web application that is hosted without a digital certificate, which is a provided web service through http:

Figure 2.28 – Joomla web application backend without https
Whenever a user tries to access this web application backend, credentials are sent to the server as plain text. Let’s see what we can see when Wireshark is running on the network:

Figure 2.29 – Wireshark captured the web application credentials
The list is as follows:
- Malware – Attackers can use malicious code to compromise the systems; malware can take over systems, exploit vulnerabilities, and even create backdoors once infected.
- Password attacks – Attackers use several types of password attacks including dictionary attacks, brute force attacks, keylogger attacks, credential stuffing attacks, and password spraying attacks. Implementing MFA, conditional access, and hardened password policies can prevent these types of attacks.
- Castle security implementation – Castle security implementation is something like the security arrangements in the castles in the olden days. In castle security, total strength is given to the castle perimeter to protect the castle. Rigorous checking is carried out at the gate and any entity that goes through the gate is typically treated as trustworthy. Even older system implementations have the highest attention given to protecting the perimeter. Most of the appliances were implemented at the perimeter such as firewalls, intrusion detection system/intrusion prevention system (IDS/IPS), and security information and event management (SIEM) solutions. But this will not protect against attacks from insiders. Currently, the accepted implementation is known as zero trust. When implementing zero trust, no assumptions are made based on the location or access requests; all requests will be verified before providing access.
- Default configurations and passwords – Many devices implemented today come with default passwords. Often, administrators don’t change them. This leads attackers to locate the devices connected to the internet quite easily and access them using default passwords. If you visit https://datarecovery.com/rd/default-passwords/ and https://www.cirt.net/passwords, you can find a long list of default passwords to many systems.
If you search for any appliance on https://www.shodan.io/, you can find real devices connected to the internet. Let’s search for Hikvision:

Figure 2.30 – Shodan shows internet-connected Hikvision devices
When you click on any of the devices, it will take the admin login to the device. Most of the devices can be accessed with the default passwords that we discussed earlier. Once attackers gain access to the device, they can monitor, make changes to the device, and even forward ports to existing devices that are connected to internal networks.
Zombies and botnets
Bots is simply the short name for robots, which refer to automated programs or scripts. Once infected, your system will become a compromised host that can be controlled by the attacker, known as a zombie. Infected machines can be remotely controlled by attackers. Even though it’s a tiny program or script, by combining thousands of them, attackers can often bring down large systems using distributed denial-of-service (DDoS) attacks. A large number of bots is referred to as a botnet. Often, these scripts are infected in your browsers, programs, and even devices.
Summary
In this chapter, we discussed why attackers are interested in your privacy and the benefits for attackers from an attacker’s point of view.
We discussed the ways that attackers use stolen data for their benefit, and how we can protect our data using technical, procedural, and physical access controls. We discussed why recovering and mitigating vulnerabilities are critical as the vulnerabilities can be used to exploit systems. When vulnerabilities are not present, attackers can create some. We looked at how the reduction of the attack surface can impact potential attacks. Overexposure increases the attack surface. Attackers use different entry points to access systems using various technologies. Bots are small programs or scripts that can infect your system and compromise the system.
In the next chapter, we will learn how attackers reveal the privacy of individuals and companies.
