8
Finite Multirate Elastic Adaptive Loss Models
In this chapter, the characteristics of the input traffic are the reverse of those in Chapter as far as the bandwidth requirement and allocation are concerned. We consider multirate loss models of quasi‐random arriving calls with fixed bandwidth requirements and elastic bandwidth allocation during service. The same traffic characteristics but of random arriving calls are considered in Chapter .
8.1 The Elastic Engset Multirate Loss Model
8.1.1 The Service System
In the elastic EnMLM (E‐EnMLM), we consider a single link of capacity ![]() b.u. that accommodates elastic calls of
b.u. that accommodates elastic calls of ![]() service classes. Calls of each service class
service classes. Calls of each service class ![]() come from a finite source population
come from a finite source population ![]() . The mean arrival rate of service‐class k idle sources is
. The mean arrival rate of service‐class k idle sources is ![]() , where
, where ![]() is the number of in‐service calls and
is the number of in‐service calls and ![]() is the arrival rate per idle source. The offered traffic‐load per idle source of service‐class k is
is the arrival rate per idle source. The offered traffic‐load per idle source of service‐class k is ![]() (in erl). Calls of service‐class k request
(in erl). Calls of service‐class k request ![]() b.u. (peak‐bandwidth requirement). To introduce bandwidth compression in the model, the occupied link bandwidth j can virtually exceed
b.u. (peak‐bandwidth requirement). To introduce bandwidth compression in the model, the occupied link bandwidth j can virtually exceed ![]() up to a limit of
up to a limit of ![]() b.u. Then the call admission is identical to the one presented in the case of the E‐EMLM (see Section 3.1.1).
b.u. Then the call admission is identical to the one presented in the case of the E‐EMLM (see Section 3.1.1).
Similarly, in terms of the system state‐space ![]() , the CAC is expressed as in the E‐EMLM (see Section 3.1.1). Hence, the TC probabilities of service‐class k are determined by the state space
, the CAC is expressed as in the E‐EMLM (see Section 3.1.1). Hence, the TC probabilities of service‐class k are determined by the state space ![]() :
:

where ![]() ,
, ![]() and
and ![]() .
.
The compression/expansion of bandwidth destroys reversibility in the E‐EnMLM and therefore no PFS exists (for ![]() ), a fact that makes (8.1) inefficient, as Example 8.1 shows.
), a fact that makes (8.1) inefficient, as Example 8.1 shows.
To circumvent the non‐reversibility problem in the E‐EnMLM, ![]() are replaced by the state‐dependent factors per service‐class k,
are replaced by the state‐dependent factors per service‐class k, ![]() , which have a similar role to
, which have a similar role to ![]() and lead to a reversible Markov chain [1,2]. Thus, the compressed bandwidth of a service‐class k call,
and lead to a reversible Markov chain [1,2]. Thus, the compressed bandwidth of a service‐class k call, ![]() , becomes
, becomes ![]() (which is (3.7)). To ensure reversibility,
(which is (3.7)). To ensure reversibility, ![]() have the form of (3.8), where
have the form of (3.8), where ![]() are given by (3.9).
are given by (3.9).
Example 8.2
Consider again Example 8.1 (![]() ).
).
- Draw the modified state transition diagram based on
 and determine the values of
and determine the values of  for each state
for each state  ).
). - Write the GB equations of the modified state transition diagram, and determine the values of
 and the TC probabilities of both service‐classes.
and the TC probabilities of both service‐classes.
- Figure 8.2 shows the modified state transition diagram of the system. The values of
 are identical to those presented in Table 3.2.
are identical to those presented in Table 3.2. - Based on Figure 8.2, we obtain the following 12 GB equations:

















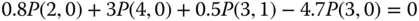




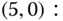

The solution of this linear system is:







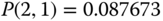

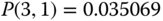


Based on the
 and ( 8.1), we obtain the approximate TC probabilities:
and ( 8.1), we obtain the approximate TC probabilities: (compare with the exact 0.1568)
(compare with the exact 0.1568)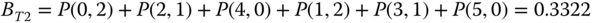
(compare with the exact 0.3291)
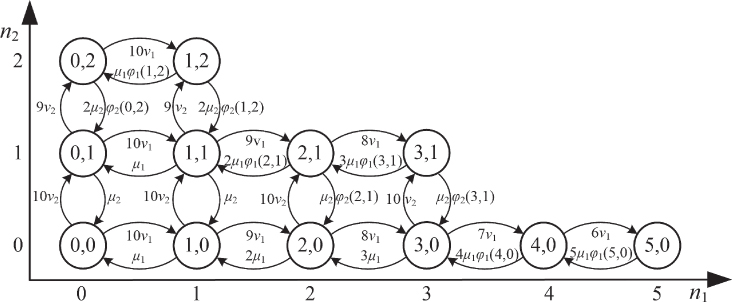
Figure 8.2 The state space  and the state transition diagram (Example 8.2).
and the state transition diagram (Example 8.2).
8.1.2 The Analytical Model
8.1.2.1 Steady State Probabilities
The GB equation (rate in = rate out) for state ![]() in the E‐EnMLM is given by:
in the E‐EnMLM is given by:

where ![]() are the probability distributions of the corresponding states
are the probability distributions of the corresponding states ![]() , respectively, which are defined as
, respectively, which are defined as ![]() and
and ![]() , while:
, while:  and
and  .
.
Assume now the existence of LB between adjacent states. Equations (8.3) and (8.4) are the detailed LB equations of the modified model (which is reversible):
for ![]() and
and ![]() .
.
Based on the LB assumption, the probability distribution ![]() has the solution:
has the solution:

where ![]() is the offered traffic‐load per idle source of service‐class k and
is the offered traffic‐load per idle source of service‐class k and ![]() is the normalization constant given by
is the normalization constant given by  .
.
Note that the probability distribution ![]() does not have a PFS due to the summation of (3.9) needed for the determination of
does not have a PFS due to the summation of (3.9) needed for the determination of ![]() . We now define
. We now define ![]() , as in (6.26).
, as in (6.26).
Consider now two different sets of macro‐states: (i) ![]() and (ii)
and (ii) ![]() . For the first set, no bandwidth compression takes place and
. For the first set, no bandwidth compression takes place and ![]() are determined by (6.27) [3]. For the second set, we substitute (3.8) in ( 8.3) to obtain:
are determined by (6.27) [3]. For the second set, we substitute (3.8) in ( 8.3) to obtain:
Multiplying both sides of (8.16) by ![]() and summing over
and summing over ![]() , we have:
, we have:

Equation (8.7), due to (3.9) is written as:

Summing both sides of (8.8) over ![]() and based on (6.26), we have:
and based on (6.26), we have:

or

The combination of (6.27) and (8.10) results in the recursive formula of the E‐EnMLM:

8.1.2.2 TC Probabilities, CBP, and Utilization
The following performance measures can be determined based on (8.11):
- The TC probabilities of service‐class k,
 , via:
(8.12)where
, via:
(8.12)where
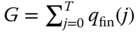 is the normalization constant.
is the normalization constant. - The CC probabilities (or CBP) of service‐class k,
 , via (8.12) but for a system with
, via (8.12) but for a system with  traffic sources.
traffic sources. - The link utilization,
 , via:
(8.13)
, via:
(8.13)
The determination of ![]() via ( 8.11) and consequently of all performance measures requires the (unknown) value of
via ( 8.11) and consequently of all performance measures requires the (unknown) value of ![]() (similar to what we have already seen for the proof of (6.27)). To circumvent the complex determination of
(similar to what we have already seen for the proof of (6.27)). To circumvent the complex determination of ![]() in each state
in each state ![]() via an equivalent stochastic system (as already described in Example 6.5), we adopt an approximate algorithm for the calculation of
via an equivalent stochastic system (as already described in Example 6.5), we adopt an approximate algorithm for the calculation of ![]() which is similar to the algorithm of Section 6.2.2.3.
which is similar to the algorithm of Section 6.2.2.3.
8.1.2.3 An Approximate Algorithm for the Determination of 
The algorithm comprises the following steps:
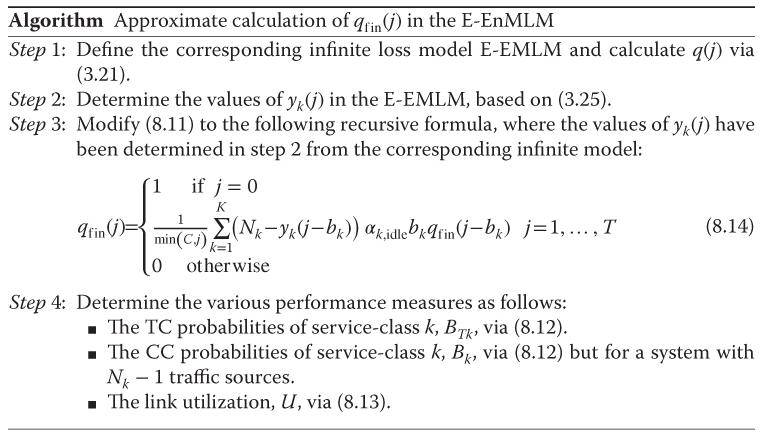
Example 8.3
Consider again Example 8.1 ![]() . Apply the algorithm of Section 8.1.2.3 for the determination of TC probabilities.
. Apply the algorithm of Section 8.1.2.3 for the determination of TC probabilities.
- Step 1: The corresponding infinite loss model (E‐EMLM) has the parameters
 erl. Based on (3.21), we have the following normalized values,
erl. Based on (3.21), we have the following normalized values, 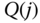 :
: 




- Step 2: Based on (3.25), we have for
 :
: 




- Step 3: Based on (8.14), we have the following normalized values of
 :
: 





- Step 4: The approximate TC probabilities are:
 (compare with 0.17 in the E‐EMLM)
(compare with 0.17 in the E‐EMLM) (compare with 0.3604 in the E‐EMLM)
(compare with 0.3604 in the E‐EMLM)
8.2 The Elastic Engset Multirate Loss Model under the BR Policy
8.2.1 The Service System
We consider again the multiservice system of the E‐EnMLM and apply the BR policy (E‐EnMLM/BR). A new service‐class k call is accepted in the link if, after its acceptance, the occupied link bandwidth is ![]() , where
, where ![]() refers to the BR parameter used to benefit calls of other service‐classes apart from k (see also the EMLM/BR in Section 1.3.2).
refers to the BR parameter used to benefit calls of other service‐classes apart from k (see also the EMLM/BR in Section 1.3.2).
In terms of the system state‐space ![]() , the CAC is expressed as in the E‐EMLM/BR (see Section 3.2.1). Hence, the TC probabilities of service‐class k are determined by the state space
, the CAC is expressed as in the E‐EMLM/BR (see Section 3.2.1). Hence, the TC probabilities of service‐class k are determined by the state space ![]() :
:

where ![]() , and
, and ![]() .
.
Example 8.4
Consider again Example 8.1 ![]() . Assume that
. Assume that ![]() and
and ![]() b.u., so that
b.u., so that ![]() .
.
- Draw the complete state transition diagram of the system and determine the values of
 and
and  for each state
for each state  .
. - Write the GB equations, and determine the values of
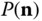 and the TC probabilities of both service‐classes.
and the TC probabilities of both service‐classes. - Draw the modified state transition diagram based on
 and determine the values of
and determine the values of  for each state
for each state  .
. - Write the GB equations of the modified state transition diagram, and determine the values of
 and the TC probabilities of both service‐classes.
and the TC probabilities of both service‐classes.
- Figure 8.3 shows the state space
 that consists of 11 permissible states
that consists of 11 permissible states  together with the complete state transition diagram of the system. The corresponding values of
together with the complete state transition diagram of the system. The corresponding values of  and
and  are exactly the same as those presented in Table 3.1 (ignore the last row) for the E‐EMLM.
are exactly the same as those presented in Table 3.1 (ignore the last row) for the E‐EMLM. - Based on Figure 8.3, we obtain the following 11 GB equations:






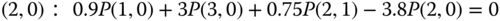




The solution of this linear system is:











Based on the values of
 and (8.15), we obtain the exact values of the TC probabilities:
and (8.15), we obtain the exact values of the TC probabilities:
(compare with 0.3234 in the E‐EMLM/BR) - Figure 8.4 shows the modified state transition diagram. The corresponding values of
 are exactly the same as those presented in Table 3.2 (ignore the last row) for the E‐EMLM.
are exactly the same as those presented in Table 3.2 (ignore the last row) for the E‐EMLM. - Based on Figure 8.4, we obtain the following 11 GB equations:











The solution of this linear system is:











Based on the values of
 and ( 8.15) we obtain the TC probabilities:
and ( 8.15) we obtain the TC probabilities:
which is quite close to the exact value of 0.30098.

Figure 8.3 The state space  and the state transition diagram (Example 8.4).
and the state transition diagram (Example 8.4).

Figure 8.4 The state space  and the modified state transition diagram (Example 8.4).
and the modified state transition diagram (Example 8.4).
8.2.2 The Analytical Model
8.2.2.1 Link Occupancy Distribution
In the E‐EnMLM/BR, the unnormalized values of ![]() can be calculated in an approximate way according to the Roberts method (see Section 1.3.2.2). Based on this, we can either find an equivalent stochastic system (requiring enumeration and processing of the state space) or apply the following algorithm (similar to that presented in Section 8.1.2.3 ):
can be calculated in an approximate way according to the Roberts method (see Section 1.3.2.2). Based on this, we can either find an equivalent stochastic system (requiring enumeration and processing of the state space) or apply the following algorithm (similar to that presented in Section 8.1.2.3 ):

Note that if ![]() for all
for all ![]() then the E‐EnMLM results. In addition, if
then the E‐EnMLM results. In addition, if ![]() , then we have the EnMLM.
, then we have the EnMLM.
8.2.2.2 TC Probabilities, CBP, and Utilization
The following performance measures can be determined based on (8.16):
- The TC probabilities of service‐class k,
 , via:
(8.17)where
, via:
(8.17)where
 is the normalization constant.
is the normalization constant. - The CBP (or CC probabilities) of service‐class k,
 , via (8.17) but for a system with
, via (8.17) but for a system with  traffic sources.
traffic sources. - The link utilization,
 , via (8.13).
, via (8.13).
Example 8.5
Consider again Example 8.4 ![]() . Apply the algorithm of Section 8.2.2.1 for the determination of TC probabilities.
. Apply the algorithm of Section 8.2.2.1 for the determination of TC probabilities.
- Step 1: The corresponding infinite loss model (E‐EMLM/BR) has the parameters
 ,
,  erl. Based on (3.34), we have the following values of
erl. Based on (3.34), we have the following values of  :
: 


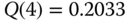

- Step 2: Based on (3.25), we have:















- Step 3: Based on (8.16), we have the
 , i.e., the normalized values of
, i.e., the normalized values of  :
: 





- Step 4: The approximate TC probabilities are:
 (compare with 0.3171 in the E‐EMLM/BR).
(compare with 0.3171 in the E‐EMLM/BR).
8.3 The Elastic Adaptive Engset Multirate Loss Model
8.3.1 The Service System
In the elastic adaptive EnMLM (EA‐EnMLM), we consider a link of capacity ![]() b.u. that accommodates elastic and adaptive calls of
b.u. that accommodates elastic and adaptive calls of ![]() different service‐classes. Let
different service‐classes. Let ![]() and
and ![]() be the set of elastic and adaptive service‐classes
be the set of elastic and adaptive service‐classes ![]() , respectively. The call arrival process remains quasi‐random.
, respectively. The call arrival process remains quasi‐random.
The bandwidth compression/expansion mechanism and the CAC in the EA‐EnMLM are the same as those of the E‐EnMLM (Section 8.1.1). The only difference is in (3.3), which is applied only on elastic calls (the service time of adaptive calls is not altered).
Example 8.6
Consider again Example 8.1 ![]() and assume that calls of service‐class 2 are adaptive.
and assume that calls of service‐class 2 are adaptive.
- Draw the complete state transition diagram of the system and determine the values of j and
 for each state
for each state  .
. - Write the GB equations, and determine the values of
 and the exact TC probabilities of both service‐classes.
and the exact TC probabilities of both service‐classes.
- Figure 8.5 shows the state space
 that consists of 12 permissible states
that consists of 12 permissible states  together with the complete state transition diagram of the system. The values of
together with the complete state transition diagram of the system. The values of  and
and  are the same as those presented in Table 3.1.
are the same as those presented in Table 3.1. - Based on Figure 8.5, we obtain the following 12 GB equations:
























The solution of this linear system is:












Based on the values of
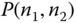 and ( 8.1), we determine the exact TC probabilities:
and ( 8.1), we determine the exact TC probabilities: (compare with 0.1568 of the E‐EMLM (Example 8.1))
(compare with 0.1568 of the E‐EMLM (Example 8.1))
(compare with 0.3291 of the E‐EMLM (Example 8.1)) The comparison between the TC probabilities obtained in the EA‐EnMLM and the E‐EnMLM reveals that the E‐EnMLM does not approximate the EA‐EnMLM. In addition, the TC probabilities of the EA‐EnMLM are lower, a fact that is expected since adaptive calls remain for less time in the system than the corresponding elastic calls.

Figure 8.5 The state space  and the state transition diagram (Example 8.6).
and the state transition diagram (Example 8.6).
To circumvent the non‐reversibility problem in the EA‐EnMLM, ![]() are replaced by the state‐dependent factors per service‐class k,
are replaced by the state‐dependent factors per service‐class k, ![]() , which have a similar role to
, which have a similar role to ![]() and lead to a reversible Markov chain [4]. Thus the compressed bandwidth of service‐class k calls is determined by (3.7), while the values of
and lead to a reversible Markov chain [4]. Thus the compressed bandwidth of service‐class k calls is determined by (3.7), while the values of ![]() and
and ![]() are given by (3.8) and (3.47), respectively.
are given by (3.8) and (3.47), respectively.
Example 8.7
Consider again Example 8.6 ![]() .
.
- Draw the modified state transition diagram based on
 and determine the values of
and determine the values of  for each state
for each state  .
. - Write the GB equations of the modified state transition diagram, and determine the values of
 and the TC probabilities of both service‐classes.
and the TC probabilities of both service‐classes.
- The graphical representation of the modified state transition diagram is identical to that of Figure 8.2. The values of
 are identical to those of Table 3.5 (for the EA‐EMLM).
are identical to those of Table 3.5 (for the EA‐EMLM). - Based on Figure 8.2 and Table 3.5, we obtain the following 12 GB equations:







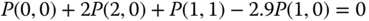








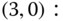



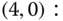



The solution of this linear system is:












Based on the values of
 and ( 8.1), we determine the TC probabilities:
and ( 8.1), we determine the TC probabilities: (compare with the exact 0.11232)
(compare with the exact 0.11232)
(compare with the exact 0.26442)
8.3.2 The Analytical Model
8.3.2.1 Steady State Probabilities
The GB equation (rate in = rate out) for state ![]() is given by (8.2) and the LB equations by ( 8.3) and ( 8.4).
is given by (8.2) and the LB equations by ( 8.3) and ( 8.4).
Similar to the E‐EnMLM, we consider two different sets of macro‐states: (i) ![]() and (ii)
and (ii) ![]() . For the first set, no bandwidth compression takes place and
. For the first set, no bandwidth compression takes place and ![]() are determined by (6.27) [ 4]. For the second set, we substitute (3.8) in ( 8.3) to have:
are determined by (6.27) [ 4]. For the second set, we substitute (3.8) in ( 8.3) to have:
Multiplying both sides of 8.18a by ![]() and summing over
and summing over ![]() , we have:
, we have:

Similarly, multiplying both sides of 8.18b by ![]() and
and ![]() , and summing over
, and summing over ![]() , we have:
, we have:

By adding (8.19) and (8.20), we obtain:

Based on (3.47), (8.21) is written as:

Summing both sides of (8.22) over ![]() and since
and since ![]() , we have:
, we have:

The combination of (6.27) and (8.23) results in the recursive formula of the EA‐EnMLM:
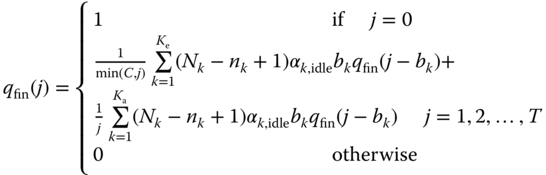
8.3.2.2 TC Probabilities, CBP, and Utilization
The following performance measures can be determined based on (8.24):
- The TC probabilities of service‐class k,
 , via ( 8.12).
, via ( 8.12). - The CBP (or CC probabilities) of service‐class k,
 , via ( 8.12) but for a system with
, via ( 8.12) but for a system with  traffic sources.
traffic sources. - The link utilization,
 , via ( 8.13).
, via ( 8.13).
The determination of ![]() via ( 8.24) and consequently of all performance measures requires the complex determination of the (unknown) value of
via ( 8.24) and consequently of all performance measures requires the complex determination of the (unknown) value of ![]() in each state j. To circumvent this, we adopt an approximate algorithm for the calculation of
in each state j. To circumvent this, we adopt an approximate algorithm for the calculation of ![]() which is similar to the algorithm of Section 8.1.2.3 .
which is similar to the algorithm of Section 8.1.2.3 .
8.3.2.3 An Approximate Algorithm for the Determination of 
The algorithm comprises the following steps:

Example 8.8
Consider again Example 8.6 ![]() . Apply the algorithm of Section 8.3.2.3 for the determination of TC probabilities.
. Apply the algorithm of Section 8.3.2.3 for the determination of TC probabilities.
- Step 1: The corresponding infinite loss model (EA‐EMLM) has the parameters
 erl.
erl.
Based on (3.57), we have the following values of
 :
:




- Step 2: Based on (3.58) and (3.59), we have:















- Step 3: Based on (8.25), we have the following values of
 :
: 





- Step 4: The approximate TC probabilities are:
 (compare with 0.12723 in the EA‐EMLM)
(compare with 0.12723 in the EA‐EMLM) (compare with 0.29844 in the EA‐EMLM)
(compare with 0.29844 in the EA‐EMLM)
8.4 The Elastic Adaptive Engset Multirate Loss Model under the BR Policy
8.4.1 The Service System
We now consider the multiservice system of the EA‐EnMLM under the BR policy (EA‐EnMLM/BR). A new service‐class k call is accepted in the link if, after its acceptance, the occupied link bandwidth ![]() , where
, where ![]() refers to the BR parameter used to benefit calls of other service‐classes apart from k.
refers to the BR parameter used to benefit calls of other service‐classes apart from k.
In terms of the system state‐space ![]() , the TC probabilities of service‐class k are determined according to ( 8.15).
, the TC probabilities of service‐class k are determined according to ( 8.15).
Example 8.9
Consider again Example 8.6 ![]() . Assume that
. Assume that ![]() and
and ![]() b.u., so that
b.u., so that ![]() .
.
- Draw the complete state transition diagram of the system and determine the values of j and
 for each state
for each state  .
. - Write the GB equations, and determine the values of
 and the TC probabilities of both service‐classes.
and the TC probabilities of both service‐classes. - Draw the modified state transition diagram based on
 and determine the values of
and determine the values of  for each state
for each state  .
. - Write the GB equations of the modified state transition diagram, and determine the values of
 and the TC probabilities of both service‐classes.
and the TC probabilities of both service‐classes.
- Figure 8.6 shows the state space
 that consists of 11 permissible states
that consists of 11 permissible states  together with the complete state transition diagram of the system. The corresponding values of
together with the complete state transition diagram of the system. The corresponding values of  and
and  are exactly the same as those presented in Table 3.1 (ignore the last row).
are exactly the same as those presented in Table 3.1 (ignore the last row). - Based on Figure 8.6, we obtain the following 11 GB equations:






















The solution of this linear system is:






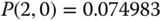




Then based on the values of
 and ( 8.15), we obtain the exact values of the TC probabilities:
and ( 8.15), we obtain the exact values of the TC probabilities:
(compare with 0.2674 in the EA‐EMLM/BR) - The graphical representation of the modified state transition diagram is identical to that of Figure 8.4. The corresponding values of
 are exactly the same as those presented in Table 3.5 (ignore the last row).
are exactly the same as those presented in Table 3.5 (ignore the last row). - Based on Figure 8.4 and Table 3.5, we obtain the following 11 GB equations:

















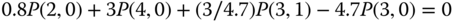




The solution of this linear system is:











Based on the
 and ( 8.15), we obtain the values of the TC probabilities:
and ( 8.15), we obtain the values of the TC probabilities:

Figure 8.6 The state space  and the state transition diagram (Example 8.9).
and the state transition diagram (Example 8.9).
8.4.2 The Analytical Model
8.4.2.1 Link Occupancy Distribution
In the EA‐EnMLM/BR, the unnormalized values of ![]() can be calculated in an approximate way according to the Roberts method. Based on this method, we can apply an algorithm similar to that presented in Section 8.3.2.3 , which is described by the following steps:
can be calculated in an approximate way according to the Roberts method. Based on this method, we can apply an algorithm similar to that presented in Section 8.3.2.3 , which is described by the following steps:

8.4.2.2 TC Probabilities, CBP, and Utilization
The following performance measures can be determined based on (8.26):
- The TC probabilities of service‐class k,
 , via ( 8.17).
, via ( 8.17). - The CBP (or CC probabilities) of service‐class k,
 , via ( 8.17) but for a system with
, via ( 8.17) but for a system with  traffic sources.
traffic sources. - The link utilization, U, via ( 8.13).
Example 8.10
Consider again Example 8.9 ![]() . Apply the algorithm of Section 8.4.2.1 for the determination of TC probabilities.
. Apply the algorithm of Section 8.4.2.1 for the determination of TC probabilities.
- Step 1: The corresponding infinite loss model (EA‐EMLM/BR) has the parameters
 erl.
erl.
Based on (3.60) we have the following values of
 :
: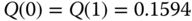




- Step 2: Based on (3.58) and (3.59), we have:









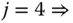





- Step 3: Based on (8.26), we have the following values of
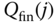 :
: 


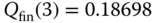


- Step 4: The approximate TC probabilities are:
 (compare with 0.256 in the EA‐EMLM/BR)
(compare with 0.256 in the EA‐EMLM/BR)
Example 8.11
Consider a link of capacity ![]() b.u. that accommodates calls of three service‐classes. The first two service‐classes are elastic, while the third service‐class is adaptive. The traffic characteristics of each service‐class of the EA‐EnMLM are:
b.u. that accommodates calls of three service‐classes. The first two service‐classes are elastic, while the third service‐class is adaptive. The traffic characteristics of each service‐class of the EA‐EnMLM are:
- Service‐class 1:


 b.u.
b.u. - Service‐class 2:


 b.u.
b.u. - Service‐class 3:


 b.u.
b.u.
In the case of the EA‐EMLM, the corresponding Poisson traffic loads are:
erl,
erl, and
erl.
Consider also two values of T: (i) ![]() b.u. and (ii)
b.u. and (ii) ![]() b.u.
b.u.
In the case of the EA‐EnMLM/BR model, let ![]() ,
, ![]() and
and ![]() in order to achieve TC probabilities equalization between calls of all service‐classes. Compare the TC probabilities of all service‐classes when
in order to achieve TC probabilities equalization between calls of all service‐classes. Compare the TC probabilities of all service‐classes when ![]() and
and ![]() increase in steps of 0.01 and 0.005 erl, respectively, while
increase in steps of 0.01 and 0.005 erl, respectively, while ![]() remains constant, from
remains constant, from ![]() up to
up to ![]() . In the case of the EA‐EMLM the last corresponding Poisson traffic loads are
. In the case of the EA‐EMLM the last corresponding Poisson traffic loads are ![]() , respectively. Also provide simulation results for the EA‐EnMLM and the EA‐EnMLM/ BR.
, respectively. Also provide simulation results for the EA‐EnMLM and the EA‐EnMLM/ BR.
Figures 8.7–8.8 present the analytical and the simulation TC probabilities of service‐class 1 for ![]() and
and ![]() b.u., respectively. To better compare the corresponding TC probabilities results (while having numerical values), we present in Tables 8.1 and 8.2, only for the first and last point, an excerpt of the results of Figures 8.7 and 8.8, respectively. Similarly, in Figures 8.9–8.10 and 8.11–8.12, we present the corresponding results for service‐classes 2 and 3. In the legend of all figures, the term
b.u., respectively. To better compare the corresponding TC probabilities results (while having numerical values), we present in Tables 8.1 and 8.2, only for the first and last point, an excerpt of the results of Figures 8.7 and 8.8, respectively. Similarly, in Figures 8.9–8.10 and 8.11–8.12, we present the corresponding results for service‐classes 2 and 3. In the legend of all figures, the term ![]() refers to the EA‐EMLM. Similarly, the term BR in all figures refers to the EA‐EnMLM/BR. Simulation results are based on SIMSCRIPT III and are mean values of six runs (no reliability ranges are shown). All figures show that:
refers to the EA‐EMLM. Similarly, the term BR in all figures refers to the EA‐EnMLM/BR. Simulation results are based on SIMSCRIPT III and are mean values of six runs (no reliability ranges are shown). All figures show that:
- Analytical and simulation results are very close to each other.
- The application of the compression/expansion mechanism reduces TC probabilities compared to those obtained when
 b.u. (compare, e.g., Figures 8.7– 8.8, Figures 8.9– 8.10, and Figures 8.11– 8.12).
b.u. (compare, e.g., Figures 8.7– 8.8, Figures 8.9– 8.10, and Figures 8.11– 8.12). - The co‐existence of the BR policy and the compression/expansion mechanism reduces TC probabilities compared to those obtained when
 b.u.
b.u. - The TC probabilities obtained by the EA‐EnMLM/BR and the EA‐EnMLM show that the BR policy favors calls of service‐class 3, as expected, and
- The results obtained by the EA‐EMLM fail to approximate the corresponding results obtained by the EA‐EnMLM.

Figure 8.7 TC probabilities for service‐class 1  b.u.) (Example 8.11).
b.u.) (Example 8.11).

Figure 8.8 TC probabilities for service‐class 1 ( b.u.) (Example 8.11).
b.u.) (Example 8.11).

Figure 8.9 TC probabilities for service‐class 2 (T = 90 b.u.) (Example 8.11) .

Figure 8.10 TC probabilities for service‐class 2 (T = 100 b.u.) (Example 8.11) .

Figure 8.11 TC probabilities for service‐class 3 (T = 90 b.u.) (Example 8.11) .

Figure 8.12 TC probabilities for service‐class 3 (T = 100 b.u.) (Example 8.11) .
Table 8.1 Excerpt of the results of Figure 8.7, when ![]() (Example 8.11).
(Example 8.11).
| ( |
( |
( |
( |
( |
|
| 0.02320 | 0.02153 | 0.00604 | 0.00420 | 0.00385 | |
| 0.15260 | 0.14692 | 0.05178 | 0.03822 | 0.03743 |
Table 8.2 Excerpt of the results of Figure 8.8, when ![]() (Example 8.11).
(Example 8.11).
| ( |
( |
( |
( |
( |
|
| 0.00704 | 0.00668 | 0.00215 | 0.00125 | 0.00117 | |
| 0.09760 | 0.09151 | 0.03716 | 0.02480 | 0.02367 |
8.5 Applications
Since the finite multirate elastic adaptive loss models are a combination of the loss models of Chapter 3 and the EnMLM of Chapter , the interested reader may refer to Sections 3.7 and 6.5 for possible applications.
In what follows, we continue the discussion started in Section 3.7 by considering the applicability of the models under SDN technology with the advanced 5G features of Cloud‐RAN (C‐RAN) and the self‐organizing network (SON). The latter enables more autonomous and automated cellular network planning, deployment, and optimization [6]. The considered reference architecture which is appropriate for the applicability of the models is presented in Figure 8.13.

Figure 8.13 The reference C‐RAN architecture.
This is in line with the C‐RAN architecture, although it can also support a more distributed, mobile edge computing (MEC)‐like functionality, by incorporating, e.g., the SON features. At the RAN level, the architecture includes an SDN controller (SDN‐C) and a virtual machine monitor (VMM) to enable NFV. Three main parts are distinguished: a pool of remote radio heads (RRHs), a pool of baseband units (BBUs), and the EPC. The RRHs are connected to the BBUs via the common public radio interface (CPRI) with a high‐capacity fronthaul. The BBUs form a centralized pool of data center resources (denoted as C‐BBU). The C‐BBU is connected to the EPC via the backhaul connection. To benefit from NFV, we consider virtualized BBU resources (V‐BBU) where the BBU functionality and services have been abstracted from the underlying infrastructure and virtualized in the form of VNFs [7]. To realize the virtualization, the VMM manages the execution of BBUs. Finally, the SDN‐C is responsible for routing decisions and configuring the packet forwarding elements [8]. Among the BBU functions that could be virtualized in the form of a VNF, we focus on the RRM, which is responsible for CAC and RRA. Various bandwidth/resource sharing policies such as the CS, the BR or the TH could be implemented at the RRM level and enable sharing of V‐BBU resources among the RRHs [9]. An analytical framework for the case where all RRHs in the C‐RAN form a single cluster can be found in [10]. The analysis for the multi‐cluster case is similar and is proposed in [11]. In both [ 10] and [ 11], the C‐RAN accommodates Poisson arriving calls of a single service‐class under the CS policy. Guidelines for the extension of the models of [ 10] and [ 11] in the case of multiple service‐classes are provided in [ 9]. These guidelines could be the springboard for the analysis of elastic adaptive service‐classes of random or quasi‐random input under the assumption that each RRH has ![]() subcarriers which can be virtually exceeded up to
subcarriers which can be virtually exceeded up to ![]() subcarriers. The latter is essential in order to include the compression/expansion mechanism for elastic adaptive calls.
subcarriers. The latter is essential in order to include the compression/expansion mechanism for elastic adaptive calls.
We continue with the use of SON technology for the implementation of bandwidth/resource sharing policies (and consequently of the multirate loss models). As an implementation example consider a virtualized RRM function in the C‐RAN of Figure 8.13. Traditionally, SON functions refer to self‐planning, self‐optimization, and self‐healing. Implementing the RRM function as a SON function would mainly target the self‐optimization objective, although this could also greatly facilitate the self‐planning objective. In particular, the goal of self‐optimization is as follows. During the cellular network operation, self‐optimization intends to improve the network performance or keep it at an acceptable level. The optimization could be performed in terms of QoS, coverage, and/or capacity improvements and is achieved by intelligently tuning various network settings of the BS as well as of the RRM function (e.g., CAC thresholds and RRA parameters). In the literature, the following architectural approaches for implementing the SON functions have been proposed [ 6]:
- Centralized SON (cSON): the SON functions are executed at the network management system (NMS) level or at the element management system (EMS) level. This will be particularly suitable for highly centralized C‐RAN solutions.
- Distributed SON (dSON): the SON functions are executed at the BS level. They can be implemented either within a BS or in a distributed manner among cooperating BSs. This is beneficial for scenarios that require pushing the network intelligence closer to MUs.
- Hybrid SON (hSON): a combination of cSON and dSON concepts (as shown in Figure 8.14). According to this approach, some SON functionality is distributed and executed at the BS level, whereas other SON functionality is centralized at the NMS or EMS level.

Figure 8.14 Enabling a hybrid SON.
Policies such as the CS, BR or the TH (described in this book), although they can be used under all three approaches, may have most benefit under the hSON. Focusing on SON's self‐optimization function, we consider the optimization of CAC. The CAC function (part of the dSON) admits or rejects a call, while the cSON function performs the selection of the optimization parameters for the CAC algorithm. These parameters are, for example, the BR parameters. In fact, the BR parameters can be used not only for CAC, but also for determining the allocated bandwidth to calls of each service‐class. When the cSON selects the CAC optimization parameters, it considers the overall resource utilization in the cell, the QoS requirements of already accepted calls, and the requirements of the new call. According to the selected bandwidth/resource sharing policy (e.g., the BR policy), its corresponding parameters (e.g., the BR parameters) are sent from the cSON to the dSON/RRM. The cSON sends an updated set of parameters if any changes in the performance guarantees are required (e.g., different acceptable levels of CBP). In the simplified case (e.g., when operating under tight resource or energy constraints) only the current values of the parameters are sent to the dSON/RRM. In particular, the cSON determines the configuration parameters based on a number of objectives (e.g., acceptable CBP). The dSON at the RAN receives the configuration parameters and acts accordingly (e.g., rejects connection requests that do not conform to the specified parameters). If the measurements reported from the dSON to the cSON violate the objectives (e.g., the CBP for a particular service is too high), the cSON will re‐calculate and send updated configuration parameters to the dSON. This approach can result in a more autonomous and automated cellular network functionality and enables simpler and faster decision‐making and operation.
8.6 Further Reading
Similar to the previous section, the interested reader may refer to the corresponding sections of Chapter 3 (Section 3.8) and Chapter 6 (Section 6.6) in order to study possible extensions of these models.
References
- 1 V. Koukoulidis, A Characterization of Reversible Markov Processes with Applications to Shared‐Resource Environments, PhD thesis, Concordia University, Montreal, Canada, April 1993.
- 2 V. Iversen, Reversible fair scheduling: The teletraffic theory revisited. Proceedings of the 20th International Teletraffic Congress, LNCS 4516, pp. 1135–1148, Ottawa, Canada, June 2007.
- 3 G. Stamatelos and J. Hayes, Admission control techniques with application to broadband networks. Computer Communications, 17(9):663–673, September 1994.
- 4 I. Moscholios, J. Vardakas, M. Logothetis and M. Koukias, A quasi‐random multirate loss model supporting elastic and adaptive traffic. Proceedings of the 4th International Conference on Emerging Network Intelligence, EMERGING 2012, Barcelona, Spain, September 2012.
- 5 I. Moscholios, J. Vardakas, M. Logothetis and M. Koukias, A quasi‐random multirate loss model supporting elastic and adaptive traffic under the bandwidth reservation policy. International Journal on Advances in Networks and Services, 6(3&4):163–174, December 2013.
- 6 Self‐Organizing Networks (SON); Concepts and Requirements (Release 12), document 3GPP 32.500 v12.1.0, September 2014.
- 7 Network Function Virtualisation (NFV); Management and Orchestration, document ETSI GS NFV‐MAN 001 (V1.1.1), December 2014.
- 8 T. Chen, M. Matinmikko, X. Chen, X. Zhou, and P. Ahokangas, Software defined mobile networks: Concept, survey, and research directions. IEEE Communications Magazine, 53(11):126–133, November 2015.
- 9 I. Moscholios, V. Vassilakis, M. Logothetis and A. Boucouvalas, State‐dependent bandwidth sharing policies for wireless multirate loss networks. IEEE Transactions on Wireless Communications, 16(8):5481–5497, August 2017.
- 10 J. Liu, S. Zhou, J. Gong, Z. Niu, and S. Xu, On the statistical multiplexing gain of virtual base station pools. Proceedings of IEEE Globecom, Austin, TX, USA, December 2014
- 11 J. Liu, S. Zhou, J. Gong, Z. Niu, and S. Xu, Statistical multiplexing gain analysis of heterogeneous virtual base station pools in cloud radio access networks. IEEE Transactions on Wireless Communications, 15(8):5681–5694, August 2016.
