7
Finite Multirate Retry Threshold Loss Models
We consider multirate loss models of quasi‐random arriving calls with elastic bandwidth requirements and fixed bandwidth allocation during service. Calls may retry several times upon arrival (requiring less bandwidth each time) in order to be accepted for service. Alternatively, new calls may request less bandwidth according to the occupied link bandwidth indicated by threshold(s).
7.1 The Finite Single‐Retry Model
7.1.1 The Service System
In the finite single‐retry model (f‐SRM), a single link of capacity ![]() b.u. accommodates calls of
b.u. accommodates calls of ![]() service‐classes under the CS policy. Calls of service class
service‐classes under the CS policy. Calls of service class ![]() come from a finite source population
come from a finite source population ![]() . The mean arrival rate of service‐class
. The mean arrival rate of service‐class ![]() idle sources is given by
idle sources is given by ![]() , where
, where ![]() is the number of in‐service calls and
is the number of in‐service calls and ![]() is the arrival rate per idle source. The offered traffic‐load per idle source of service‐class
is the arrival rate per idle source. The offered traffic‐load per idle source of service‐class ![]() is given by
is given by ![]() (in erl). Note that if
(in erl). Note that if ![]() for
for ![]() , and the total offered traffic‐load remains constant, then the call arrival process is Poisson. A new call of service‐class
, and the total offered traffic‐load remains constant, then the call arrival process is Poisson. A new call of service‐class ![]() has a peak‐bandwidth requirement of
has a peak‐bandwidth requirement of ![]() b.u. and an exponentially distributed service time with mean
b.u. and an exponentially distributed service time with mean ![]() . If the initially required b.u. are not available in the link, the call is blocked and immediately retries to be connected in the system with
. If the initially required b.u. are not available in the link, the call is blocked and immediately retries to be connected in the system with ![]() b.u. while the mean of the new service time increases to
b.u. while the mean of the new service time increases to ![]() so that the product bandwidth requirement by service time remains constant [1]. If the
so that the product bandwidth requirement by service time remains constant [1]. If the ![]() b.u. are not available the call is blocked and lost. The CAC mechanism of a call of service‐class
b.u. are not available the call is blocked and lost. The CAC mechanism of a call of service‐class ![]() is identical to that of Figure 2.2 of the SRM, i.e., a new call of service‐class
is identical to that of Figure 2.2 of the SRM, i.e., a new call of service‐class ![]() is blocked with
is blocked with ![]() b.u. if
b.u. if ![]() and is accepted with
and is accepted with ![]() if
if ![]() , where
, where ![]() and
and ![]() are the in‐service calls of service‐class
are the in‐service calls of service‐class ![]() accepted with
accepted with ![]() b.u., respectively.
b.u., respectively.
The comparison of the f‐SRM with the EnMLM reveals similar differences to those described in Section 2.1.1 for the SRM and the EMLM.
7.1.2 The Analytical Model
7.1.2.1 Steady State Probabilities
To describe the analytical model in the steady state, let us concentrate on a single link of capacity C b.u. that accommodates only two service‐classes with the following traffic characteristics: ![]() . Blocked calls of service‐class 2 may retry with parameters
. Blocked calls of service‐class 2 may retry with parameters ![]() while blocked calls of service‐class 1 do not retry. Although the f‐SRM does not have a PFS, we assume that the LB equation (6.33), proposed in the EnMLM, does hold, that is [ 1]:
while blocked calls of service‐class 1 do not retry. Although the f‐SRM does not have a PFS, we assume that the LB equation (6.33), proposed in the EnMLM, does hold, that is [ 1]:
or, due to the fact that ![]() in the equivalent stochastic system:
in the equivalent stochastic system:
This assumption is important for the derivation of an approximate but recursive formula for the ![]() . If
. If ![]() , when a new call of service‐class 2 arrives in the system this call is blocked and retries to be connected with
, when a new call of service‐class 2 arrives in the system this call is blocked and retries to be connected with ![]() b.u. If
b.u. If ![]() , the retry call will be accepted in the system. To describe this situation we need an additional LB equation [ 1]:
, the retry call will be accepted in the system. To describe this situation we need an additional LB equation [ 1]:
where ![]() is the offered traffic‐load per idle source of service‐class 2 with
is the offered traffic‐load per idle source of service‐class 2 with ![]() , and
, and ![]() is the mean number of service‐class 2 calls accepted in state
is the mean number of service‐class 2 calls accepted in state ![]() with
with ![]() .
.
Multiplying (7.3) with ![]() , we have for
, we have for ![]() :
:
Multiplying both sides of (7.2) with ![]() , we have for
, we have for ![]() :
:

Adding (7.4) to (7.5), and since ![]() , we obtain:
, we obtain:

Apart from the assumption of the LB equation ( 7.3), another approximation is necessary for the recursive calculation of ![]() :
:
In (7.7), the value of ![]() is considered negligible compared to
is considered negligible compared to ![]() when
when ![]() . This is the migration approximation (see Section 2.1.2.1). Due to ( 7.7), equation ( 7.5) is written as (for
. This is the migration approximation (see Section 2.1.2.1). Due to ( 7.7), equation ( 7.5) is written as (for ![]() :
:
The combination of (7.6) and (7.8) gives an approximate formula for the determination of ![]() in the f‐SRM, assuming that only calls of service‐class 2 can retry [ 1]:
in the f‐SRM, assuming that only calls of service‐class 2 can retry [ 1]:

where ![]() , and
, and ![]() when
when ![]() (otherwise
(otherwise ![]() ).
).
The generalization of (7.9) in the case of ![]() service‐classes, where all service‐classes may retry, is as follows [ 1]:
service‐classes, where all service‐classes may retry, is as follows [ 1]:

where ![]() when
when ![]() (otherwise
(otherwise ![]() ).
).
Note that if ![]() , for
, for ![]() , and the total offered traffic‐load remains constant, then we have the recursion (2.10) of the SRM.
, and the total offered traffic‐load remains constant, then we have the recursion (2.10) of the SRM.
7.1.2.2 TC Probabilities, CBP, Utilization, and Mean Number of In‐service Calls
The following performance measures can be determined based on (7.10):
- The TC probabilities of service‐class k calls with
 b.u.,
b.u.,  , via (6.35).
, via (6.35). - The TC probabilities of service‐class k calls with
 b.u.,
b.u.,  , via:
(7.11)where
, via:
(7.11)where
 is the normalization constant.
is the normalization constant. - The CBP (or CC probabilities) of service‐class k calls with
 (without retrial),
(without retrial),  , via (6.35) but for a system with
, via (6.35) but for a system with  traffic sources.
traffic sources. - The CBP (or CC probabilities) of service‐class k calls with
 ,
,  , via (7.11) but for a system with
, via (7.11) but for a system with  traffic sources.
traffic sources. - The conditional TC probabilities of service‐class k retry calls given that they have been blocked with their initial bandwidth requirement
 , via:
(7.12)
, via:
(7.12)
- The link utilization,
 , via (6.36).
, via (6.36). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via (6.37), while the mean number of service‐class k calls with
, via (6.37), while the mean number of service‐class k calls with  given that the system state is
given that the system state is  , via (6.38).
, via (6.38). - The average number of service‐class k calls in the system accepted with
 ,
,  , via:
(7.13)where
, via:
(7.13)where
 is the average number of service‐class k calls with
is the average number of service‐class k calls with  given that the system state is
given that the system state is  , and is determined by:
(7.14)where
, and is determined by:
(7.14)where
 and
and  when
when  .
.
The determination of ![]() via ( 7.10), and consequently of all performance measures, requires the values of
via ( 7.10), and consequently of all performance measures, requires the values of ![]() and
and ![]() , which are unknown. In [ 1–3] give a method for the determination of
, which are unknown. In [ 1–3] give a method for the determination of ![]() and
and ![]() in each state
in each state ![]() via an equivalent stochastic system, with the same traffic parameters and the same set of states, as already described for the proof of (6.27) in the EnMLM. However, the state space determination of the equivalent system is complex, even for small capacity systems that serve many service‐classes with the ability to retry.
via an equivalent stochastic system, with the same traffic parameters and the same set of states, as already described for the proof of (6.27) in the EnMLM. However, the state space determination of the equivalent system is complex, even for small capacity systems that serve many service‐classes with the ability to retry.
Example 7.2
Consider a link of capacity ![]() b.u. and two service‐classes whose calls require
b.u. and two service‐classes whose calls require ![]() and
and ![]() b.u., respectively. The offered traffic load per idle source is
b.u., respectively. The offered traffic load per idle source is ![]() erl, while the number of sources is
erl, while the number of sources is ![]() . Blocked calls of service‐class 1 retry with reduced bandwidth,
. Blocked calls of service‐class 1 retry with reduced bandwidth, ![]() b.u., and increased offered traffic
b.u., and increased offered traffic ![]() erl, so that the total offered traffic load per idle source remains the same
erl, so that the total offered traffic load per idle source remains the same ![]() . Due to the migration approximation, retry calls of service‐class 1 are assumed to be negligible when the occupied link bandwidth
. Due to the migration approximation, retry calls of service‐class 1 are assumed to be negligible when the occupied link bandwidth ![]() . Taking into account the migration approximation assumption, the state space consists of eight states
. Taking into account the migration approximation assumption, the state space consists of eight states ![]() , presented in Table 7.1 together with the respective occupied link bandwidth
, presented in Table 7.1 together with the respective occupied link bandwidth ![]() and the blocking states
and the blocking states ![]() . According to Table 7.1, the values of
. According to Table 7.1, the values of ![]() appear more than once, and therefore it is impossible to use ( 7.10) directly for the calculation of
appear more than once, and therefore it is impossible to use ( 7.10) directly for the calculation of ![]() , e.g., the value
, e.g., the value ![]() corresponds to both
corresponds to both ![]() and
and ![]() . To overcome this, an equivalent stochastic system should be determined with the following three characteristics:
. To overcome this, an equivalent stochastic system should be determined with the following three characteristics:
- The states
 are the same as the initial system.
are the same as the initial system. - Each state
 has a unique occupied link‐bandwidth value.
has a unique occupied link‐bandwidth value. - The chosen values of
 , and
, and  of the equivalent system keep constant (as much as possible) the initial ratios of
of the equivalent system keep constant (as much as possible) the initial ratios of  .
.
In this example, an approximate solution to the initial system is ![]() , and
, and ![]() ; for these values we present in the last column of Table 7.1 the unique values of the equivalent occupied link bandwidth,
; for these values we present in the last column of Table 7.1 the unique values of the equivalent occupied link bandwidth, ![]() . The resultant TC probabilities are
. The resultant TC probabilities are ![]() , and
, and ![]() . Note that every system that is a multiple of
. Note that every system that is a multiple of ![]() , and
, and ![]() (e.g.,
(e.g., ![]() , and
, and ![]() ) gives exactly the same TC probabilities.
) gives exactly the same TC probabilities.
Table 7.1 State space, ![]() ,
, ![]() , and blocking states (Example 7.2).
, and blocking states (Example 7.2).
| 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 3 | 3000 | * | |||||
| 0 | 1 | 0 | 2 | 2000 | 1 | 0 | 1 | 4 | 4001 | * | * | ||||
| 0 | 2 | 0 | 4 | 4000 | * | * | 1 | 0 | 2 | 5 | 5002 | * | * | * | |
| 0 | 2 | 1 | 5 | 5001 | * | * | * | 1 | 1 | 0 | 5 | 5000 | * | * | * |
As already mentioned, the determination of an equivalent system is complex, especially when calls retry many times. To circumvent this problem we present, in the next section, the algorithm of Section 6.2.2.3 (initially proposed for the EnMLM) for the f‐SRM.
7.1.2.3 An Approximate Algorithm for the Determination of  in the f‐SRM
in the f‐SRM
Contrary to ( 7.10), which requires enumeration and processing of the state space, the algorithm presented herein is much simpler and easy to implement [4,5].

Example 7.3
Consider again Example 7.1 ![]() . Apply the algorithm of Section 7.1.2.3 for the determination of TC probabilities.
. Apply the algorithm of Section 7.1.2.3 for the determination of TC probabilities.
- Step 1: The corresponding infinite loss model (SRM) is
 erl and
erl and  erl.
erl.
Based on (2.10), we have the following normalized values of
 :
:

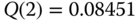



- Step 2:
Based on (2.14) and (2.15), we have:




















- Step 3:
Based on (7.15), we have the following normalized values of
 :
: 





- Step 4:
The approximate TC probabilities are:
 (compare with the exact 0.190881)
(compare with the exact 0.190881) (compare with the exact 0.540931)
(compare with the exact 0.540931) (compare with the exact 0.364034)
(compare with the exact 0.364034)
7.2 The Finite Single‐Retry Model under the BR Policy
7.2.1 The Service System
In the f‐SRM under the BR policy (f‐SRM/BR), ![]() b.u. are reserved to benefit calls of all other service‐classes apart from service‐class k. The application of the BR policy in the f‐SRM is similar to that of the SRM/BR as the following example shows.
b.u. are reserved to benefit calls of all other service‐classes apart from service‐class k. The application of the BR policy in the f‐SRM is similar to that of the SRM/BR as the following example shows.
Example 7.4
Consider again Example 7.1 ![]() and let the BR parameters
and let the BR parameters ![]() b.u. and
b.u. and ![]() b.u. so that
b.u. so that ![]() . In that case, equalization of TC probabilities is achieved between new calls of service‐class 1 and new (not retry) calls of service‐class 2.
. In that case, equalization of TC probabilities is achieved between new calls of service‐class 1 and new (not retry) calls of service‐class 2.
- Find the total number of permissible states
 and draw the state transition diagram.
and draw the state transition diagram. - Calculate the state probabilities
 and the corresponding values of
and the corresponding values of  .
. - Calculate the TC probabilities of both service‐classes, including the retry probability.
- There are 14 permissible states of the form
 . The state space
. The state space  and the state transition diagram are shown in Figure 7.2.
and the state transition diagram are shown in Figure 7.2. - Based on Figure 7.2, we obtain the following 14 GB equations:


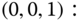








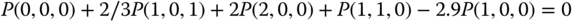
















The solution of this linear system is:














Then, based on the values of
 , we obtain the values of
, we obtain the values of  :
:





- The TC probabilities of service‐class 1,
 , are given by:
, are given by: 
(0.548536 in the SRM/BR, see Example 2.3) The
 of service‐class 2 calls,
of service‐class 2 calls,  , when they require
, when they require 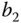 b.u., is:
b.u., is: (0.548536 in the SRM/BR)
(0.548536 in the SRM/BR)The TC probabilities of service‐class 2 calls,
 , when they require
, when they require 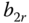 b.u., are:
b.u., are: (0.301968 in the SRM/BR)
(0.301968 in the SRM/BR)

Figure 7.2 The state space  and the state transition diagram (Example 7.4).
and the state transition diagram (Example 7.4).
7.2.2 The Analytical Model
7.2.2.1 Link Occupancy Distribution
In the f‐SRM/BR, the unnormalized values of ![]() can be calculated in an approximate way according to the Roberts method (see Section 1.3.2.2). Based on that method, we can either find an equivalent stochastic system (which is complex) [ 3] or apply an algorithm similar to the one presented in Section 7.1.2.3 . Due to its simplicity, the latter is adopted herein with the following modifications.
can be calculated in an approximate way according to the Roberts method (see Section 1.3.2.2). Based on that method, we can either find an equivalent stochastic system (which is complex) [ 3] or apply an algorithm similar to the one presented in Section 7.1.2.3 . Due to its simplicity, the latter is adopted herein with the following modifications.
7.2.2.2 TC Probabilities, CBP, Utilization, and Mean Number of In‐service Calls
The following performance measures can be determined based on (7.17):

- The TC probabilities of service‐class k calls with
 b.u.,
b.u.,  , via (6.42).
, via (6.42). - The TC probabilities of service‐class k calls with
 , via:
(7.18)
, via:
(7.18)
- The CC probabilities of service‐class k calls with
 (without retrial),
(without retrial),  , via (6.42) but for a system with
, via (6.42) but for a system with 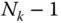 traffic sources.
traffic sources. - The CC probabilities of service‐class k calls with
 , via (7.18) but for a system with
, via (7.18) but for a system with  traffic sources.
traffic sources. - The conditional TC probabilities of service‐class k retry calls given that they have been blocked with their initial bandwidth requirement
 , via (7.12), while subtracting the BR parameter
, via (7.12), while subtracting the BR parameter  from both
from both  and
and  .
. - The link utilization,
 , via (6.36).
, via (6.36). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via (6.37) where
, via (6.37) where  is determined by:
(7.19)
is determined by:
(7.19)
- The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via (7.13) where
, via (7.13) where  is determined by:
(7.20)where
is determined by:
(7.20)where
 , and
, and  when
when  .
.
Example 7.5
Consider again Example 7.4 ![]() . Apply the algorithm of Section 7.2.2.1 for the determination of TC probabilities.
. Apply the algorithm of Section 7.2.2.1 for the determination of TC probabilities.
- Step 1: The corresponding infinite loss model (SRM/BR) is
 erl and
erl and  erl.
erl.
Based on (2.18), we have the following normalized values of
 :
:





- Step 2:
Based on (1.67) and (2.21), we have:




















- Step 3: Based on (7.17), we have the following normalized values of
 :
: 





The approximate TC probabilities are:
 (compare with the exact 0.539377)
(compare with the exact 0.539377) (compare with the exact 0.539377)
(compare with the exact 0.539377) (compare with the exact 0.285796)
(compare with the exact 0.285796)
7.3 The Finite Multi‐Retry Model
7.3.1 The Service System
In the finite multi‐retry model (f‐MRM), calls of service‐class k can retry more than once to be connected in the system [2– 5]. Let ![]() be the number of retrials for calls of service‐class k and assume that
be the number of retrials for calls of service‐class k and assume that ![]() , where
, where ![]() is the required bandwidth of a service‐class k call in the
is the required bandwidth of a service‐class k call in the ![]() th retry,
th retry, ![]() . Then a service‐class k call is accepted in the system with
. Then a service‐class k call is accepted in the system with ![]() b.u. if
b.u. if ![]() .
.
Example 7.6
Consider a link of ![]() b.u. The link accommodates quasi‐random arriving calls of two service‐classes. Calls of service‐class 1 require
b.u. The link accommodates quasi‐random arriving calls of two service‐classes. Calls of service‐class 1 require ![]() b.u. while calls of service‐class 2 require
b.u. while calls of service‐class 2 require ![]() . Blocked calls of service‐class 2 can retry two times with
. Blocked calls of service‐class 2 can retry two times with ![]() b.u. and
b.u. and ![]() b.u. Let the number of sources be
b.u. Let the number of sources be ![]() , the arrival rate per idle source be
, the arrival rate per idle source be ![]() and
and ![]() sec,
sec, ![]() sec, and
sec, and ![]() sec (in this example we do not assume that
sec (in this example we do not assume that ![]() ).
).
- Find the total number of permissible states
 and draw the state transition diagram.
and draw the state transition diagram. - Calculate the state probabilities
 and the corresponding values of
and the corresponding values of  based on the GB equations.
based on the GB equations. - Calculate the TC probabilities of both service‐classes, including the retry probabilities and the link utilization.
- Calculate the conditional TC probabilities of service‐class 2 retry calls with
 , given that they have been blocked with their initial bandwidth requirement,
, given that they have been blocked with their initial bandwidth requirement,  .
.
- The total number of permissible states of the form
 , is 14. They are shown in Figure 7.3 together with the state transition diagram.
, is 14. They are shown in Figure 7.3 together with the state transition diagram. - Based on Figure 7.3, the corresponding 14 GB equations are:



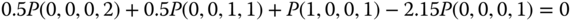








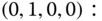



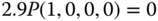












The solution of this linear system is:



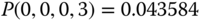





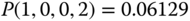




Based on the values of
 , we have:
, we have:








- The TC probabilities of service‐class 1 are given by:
 (0.545687 in the MRM, see Example 2.6)
(0.545687 in the MRM, see Example 2.6)The TC probability of the first retry of service‐class 2 is given by:
 (0.876443 in the MRM)
(0.876443 in the MRM)The TC probability of the second retry of service‐class 2, with
 b.u., is given by:
b.u., is given by: (0.725882 in the MRM)
(0.725882 in the MRM)The TC probability of service‐class 2, with
 b.u., is given by:
b.u., is given by: (0.545687 in the MRM)
(0.545687 in the MRM)The link utilization is determined by:
 b.u. (2.148 in the MRM)
b.u. (2.148 in the MRM) - The conditional TC probabilities of service‐class 2 retry calls with
 are given by:
are given by:  (0.62262 in the MRM).
(0.62262 in the MRM).

Figure 7.3 The state space  and the state transition diagram (Example 7.6).
and the state transition diagram (Example 7.6).
7.3.2 The Analytical Model
7.3.2.1 Steady State Probabilities
Following the analysis of Section 7.1.2.1, in the f‐MRM not only LB is assumed but also the migration approximation, that is, the mean number of service‐class k calls in state ![]() , accepted with
, accepted with ![]() b.u., is negligible when
b.u., is negligible when ![]() . This means that service‐class k calls with
. This means that service‐class k calls with ![]() are limited in the area
are limited in the area ![]() . The
. The ![]() are determined by [ 2]:
are determined by [ 2]:

where ![]() , and
, and ![]() when
when ![]() (otherwise
(otherwise ![]() ).
).
Note that if ![]() for
for ![]() , and the total offered traffic‐load remains constant, then we have the recursion (2.22) of the MRM [6]. In addition, if calls may retry only once, then the SRM results [ 6].
, and the total offered traffic‐load remains constant, then we have the recursion (2.22) of the MRM [6]. In addition, if calls may retry only once, then the SRM results [ 6].
7.3.2.2 TC Probabilities, CBP, Utilization, and Mean Number of In‐service Calls
The following performance measures can be determined based on (7.21):
- The TC probabilities of service‐class k calls with
 b.u.,
b.u.,  , via (6.35).
, via (6.35). - The TC probabilities of service‐class k calls with their last bandwidth requirement
 b.u.,
b.u.,  , via:
(7.22)where
, via:
(7.22)where
 is the normalization constant.
is the normalization constant. - The CC probabilities of service‐class k calls with
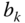 (without retrial),
(without retrial),  , via (6.35) but for a system with
, via (6.35) but for a system with  traffic sources.
traffic sources. - The CC probabilities of service‐class k calls with
 , via (7.22) but for a system with
, via (7.22) but for a system with  traffic sources.
traffic sources. - The conditional TC probabilities of service‐class k retry calls, while requesting
 b.u. given that they have been blocked with their initial bandwidth requirement
b.u. given that they have been blocked with their initial bandwidth requirement  , via:
(7.23)
, via:
(7.23)
- The link utilization,
 , via (6.36).
, via (6.36). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via (6.37), while the mean number of service‐class k calls with
, via (6.37), while the mean number of service‐class k calls with  given that the system state is
given that the system state is  , via (6.38).
, via (6.38). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via:
(7.24)where
, via:
(7.24)where
 is the average number of service‐class k calls with
is the average number of service‐class k calls with  given that the system state is
given that the system state is  , and is determined by:
(7.25)where
, and is determined by:
(7.25)where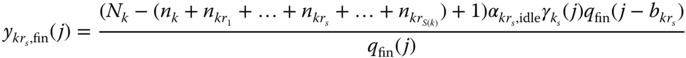
 , and
, and  when
when  (otherwise
(otherwise  ).
).
The determination of ![]() via ( 7.21), and consequently of all performance measures, requires the values of
via ( 7.21), and consequently of all performance measures, requires the values of ![]() and
and ![]() , which are unknown. In [ 2], there is a method for the determination of
, which are unknown. In [ 2], there is a method for the determination of ![]() and
and ![]() in each state
in each state ![]() via an equivalent stochastic system, with the same traffic parameters and the same set of states. However, since this method is complex, we adopt the algorithm of Section 7.3.2.3 (see below), which is similar to the algorithm of Section 7.1.2.3 of the f‐SRM.
via an equivalent stochastic system, with the same traffic parameters and the same set of states. However, since this method is complex, we adopt the algorithm of Section 7.3.2.3 (see below), which is similar to the algorithm of Section 7.1.2.3 of the f‐SRM.
7.3.2.3 An Approximate Algorithm for the Determination of  in the f‐MRM
in the f‐MRM
The algorithm for the calculation of ![]() in the f‐MRM can be described as follows [ 4, 5]:
in the f‐MRM can be described as follows [ 4, 5]:


Example 7.7
Consider again Example 7.6 (![]() ,
, ![]() ). Apply the algorithm of Section 7.3.2.3 for the determination of TC probabilities, including the retry probabilities and the link utilization.
). Apply the algorithm of Section 7.3.2.3 for the determination of TC probabilities, including the retry probabilities and the link utilization.
- Step 1: The corresponding infinite loss model (MRM) is
 erl,
erl,  erl,
erl,  erl,
erl,  erl.
erl.
Based on (2.22), we have the following normalized values of
 :
:



- Step 2:
Based on (2.14) and (2.25), we have:








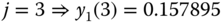



- Step 3:
Based on (7.26), we have the following normalized values of
 :
: 

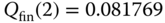

- Step 4: The approximate TC probabilities and retry probabilities are:
 (compare with the exact 0.5274)
(compare with the exact 0.5274) (compare with the exact 0.867574)
(compare with the exact 0.867574) (compare with the exact 0.709409)
(compare with the exact 0.709409) (compare with the exact 0.5274)
(compare with the exact 0.5274)The link utilization is determined by:
 b.u. (compare with the exact 2.104)
b.u. (compare with the exact 2.104)
7.4 The Finite Multi‐Retry Model under the BR Policy
7.4.1 The Service System
Compared to the f‐SRM/BR, in the f‐MRM under the BR policy (f‐MRM/BR), blocked calls of service‐class k can retry more than once to be connected in the system.
Example 7.8
Consider again Example 7.6 (![]() ,
, ![]() ) and let the BR parameters
) and let the BR parameters ![]() b.u. and
b.u. and ![]() b.u. so that
b.u. so that ![]() .
.
- Find the total number of permissible states
 and draw the state transition diagram.
and draw the state transition diagram. - Calculate the state probabilities
 and the corresponding values of
and the corresponding values of  based on the GB equations.
based on the GB equations. - Calculate the TC probabilities of both service‐classes, including the retry probabilities and the link utilization.
- The total number of permissible states of the form
 is 7. They are shown in Figure 7.4 together with the state transition diagram.
is 7. They are shown in Figure 7.4 together with the state transition diagram. - Based on Figure 7.4, the corresponding 7 GB equations are:










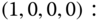


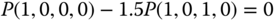
The solution of this linear system is:







Based on the values of
 , we have:
, we have:



- The TC probabilities of service‐class 1 are given by the formula:

(compare with the exact 0.819672 in the MRM/BR, see Example 2.8) The TC probabilities of service‐class 2, with
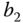 , are given by:
, are given by:
(compare with the exact 0.819672 in the MRM/BR) The TC probabilities of service‐class 2, with
 b.u., are given by:
b.u., are given by:
(compare with the exact 0.606557 in the MRM/BR) The TC probabilities of service‐class 2, with
 b.u., are given by:
b.u., are given by:
(compare with the exact 0.514754 in the MRM/BR) The link utilization is determined by:
 b.u. (compare with the exact 1.941 b.u. in the MRM/BR)
b.u. (compare with the exact 1.941 b.u. in the MRM/BR)

Figure 7.4 The state space  and the state transition diagram (Example 7.8).
and the state transition diagram (Example 7.8).
7.4.2 The Analytical Model
7.4.2.1 Link Occupancy Distribution
Based on the Roberts method and the algorithm of Section 7.2.2.1 of the f‐SRM/BR, the unnormalized values of the link occupancy distribution, ![]() , in the f‐MRM/BR can be determined by the following algorithm:
, in the f‐MRM/BR can be determined by the following algorithm:

7.4.2.2 TC Probabilities, CBP, Utilization, and Mean Number of In‐service Calls
The following performance measures can be determined based on (7.28):
- The TC probabilities of service‐class k calls with
 b.u.,
b.u., 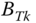 , via (6.42).
, via (6.42). - The TC probabilities of service‐class k calls with
 , via:
(7.29)
, via:
(7.29)
- The CC probabilities of service‐class k calls with
 (without retrial),
(without retrial),  , via (6.42) but for a system with
, via (6.42) but for a system with  traffic sources.
traffic sources. - The CC probabilities of service‐class k calls with
 , via (7.29) but for a system with
, via (7.29) but for a system with  traffic sources.
traffic sources. - The conditional TC probabilities of service‐class k retry calls, while requesting
 b.u. given that they have been blocked with their initial bandwidth requirement
b.u. given that they have been blocked with their initial bandwidth requirement  , via (7.23), while subtracting
, via (7.23), while subtracting  from both
from both  and
and  .
. - The link utilization,
 , via (6.36).
, via (6.36). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via (6.37) where
, via (6.37) where  is determined via (6.43).
is determined via (6.43). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via (7.24) where
, via (7.24) where  is determined by:
(7.30)
is determined by:
(7.30)
- where
 , and
, and  when
when  .
.
Example 7.9
Consider again Example 7.8 (![]() ,
, ![]() ). Apply the algorithm of Section 7.4.2.1 for the determination of TC and retry probabilities.
). Apply the algorithm of Section 7.4.2.1 for the determination of TC and retry probabilities.
- Step 1:
The corresponding infinite loss model (MRM/BR) is the following:
 erl,
erl,  erl,
erl,  erl. Based on (2.27) and since
erl. Based on (2.27) and since  and
and  for
for  , we have the following normalized values of
, we have the following normalized values of  :
: 
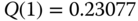

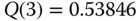
- Step 2:
Based on (1.67) and (2.30), we have:








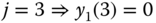



- Step 3: Based on (7.28), we have the following normalized values of
 :
: 



The approximate TC probabilities and retry probabilities are:
 (compare with the exact 0.814167)
(compare with the exact 0.814167) (compare with the exact 0.814167)
(compare with the exact 0.814167) (compare with the exact 0.597726)
(compare with the exact 0.597726) (compare with the exact 0.50153)
(compare with the exact 0.50153)
Example 7.10
Consider a link of capacity ![]() b.u. and
b.u. and ![]() service‐classes with
service‐classes with ![]() and
and ![]() b.u. The offered traffic‐loads are
b.u. The offered traffic‐loads are ![]() and
and ![]() erl. Blocked calls of service‐class 1 reduce their bandwidth requirement twice, from 10 to 8 and finally to 6 b.u. The corresponding retry offered traffic‐loads are
erl. Blocked calls of service‐class 1 reduce their bandwidth requirement twice, from 10 to 8 and finally to 6 b.u. The corresponding retry offered traffic‐loads are ![]() and
and ![]() erl. Blocked calls of service‐class 2 reduce their bandwidth once, from 7 to 4 b.u. The retry offered traffic‐load of service‐class 2 is
erl. Blocked calls of service‐class 2 reduce their bandwidth once, from 7 to 4 b.u. The retry offered traffic‐load of service‐class 2 is ![]() erl. The number of sources for both service‐classes is
erl. The number of sources for both service‐classes is ![]() . Based on the above, we have a f‐MRM system. The equivalent stochastic system used for the TC probabilities calculation is
. Based on the above, we have a f‐MRM system. The equivalent stochastic system used for the TC probabilities calculation is ![]() , and
, and ![]() . Table 7.2 shows the state space, which consists of 30 states.
. Table 7.2 shows the state space, which consists of 30 states.
Table 7.2 The state space, ![]() , and the blocking states (Example 7.10).
, and the blocking states (Example 7.10).
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | ||
| 0 | 1 | 0 | 0 | 0 | 7 | 7001 | ||
| 0 | 2 | 0 | 0 | 0 | 14 | 14002 | ||
| 0 | 3 | 0 | 0 | 0 | 21 | 21003 | ||
| 0 | 4 | 0 | 0 | 0 | 28 | 28004 | ||
| 0 | 5 | 0 | 0 | 0 | 35 | 35005 | ||
| 0 | 6 | 0 | 0 | 0 | 42 | 42006 | ||
| 0 | 6 | 1 | 0 | 0 | 50 | 50006 | * | * |
| 0 | 7 | 0 | 0 | 0 | 49 | 49007 | * | * |
| 1 | 0 | 0 | 0 | 0 | 10 | 10000 | ||
| 1 | 1 | 0 | 0 | 0 | 17 | 17001 | ||
| 1 | 2 | 0 | 0 | 0 | 24 | 24002 | ||
| 1 | 3 | 0 | 0 | 0 | 31 | 31003 | ||
| 1 | 4 | 0 | 0 | 0 | 38 | 38004 | ||
| 1 | 5 | 0 | 0 | 0 | 45 | 45005 | * | |
| 1 | 5 | 0 | 0 | 1 | 49 | 49005 | * | * |
| 2 | 0 | 0 | 0 | 0 | 20 | 20000 | ||
| 2 | 1 | 0 | 0 | 0 | 27 | 27001 | ||
| 2 | 2 | 0 | 0 | 0 | 34 | 34002 | ||
| 2 | 3 | 0 | 0 | 0 | 41 | 41003 | ||
| 2 | 3 | 1 | 0 | 0 | 49 | 49003 | * | * |
| 2 | 4 | 0 | 0 | 0 | 48 | 48004 | * | * |
| 3 | 0 | 0 | 0 | 0 | 30 | 30000 | ||
| 3 | 1 | 0 | 0 | 0 | 37 | 37001 | ||
| 3 | 2 | 0 | 0 | 0 | 44 | 44002 | ||
| 3 | 2 | 0 | 0 | 1 | 48 | 48002 | * | * |
| 3 | 2 | 0 | 1 | 0 | 50 | 50002 | * | * |
| 4 | 0 | 0 | 0 | 0 | 40 | 40000 | ||
| 4 | 1 | 0 | 0 | 0 | 47 | 47001 | * | * |
| 5 | 0 | 0 | 0 | 0 | 50 | 50000 | * | * |
The corresponding MRM system used for the calculation of ![]() and
and ![]() and consequently of TC probabilities (according to Section 7.3.2.3 ) is
and consequently of TC probabilities (according to Section 7.3.2.3 ) is ![]() . In Table 7.3, we present the analytical TC probabilities obtained from the equivalent stochastic system and the algorithm of Section 7.3.2.3 together with the corresponding simulation results. The latter are mean values of seven runs with 95% confidence interval. At each point (P) of Table 7.3 the values of
. In Table 7.3, we present the analytical TC probabilities obtained from the equivalent stochastic system and the algorithm of Section 7.3.2.3 together with the corresponding simulation results. The latter are mean values of seven runs with 95% confidence interval. At each point (P) of Table 7.3 the values of ![]() , and
, and ![]() are constant while those of
are constant while those of ![]() and
and ![]() are increased by
are increased by ![]() and
and ![]() , respectively (for
, respectively (for ![]() and
and ![]() erl). Based on Table 7.3, one observes that the algorithm of Section 7.3.2.3 gives almost the same results as the equivalent stochastic system method and satisfactory results compared to simulation.
erl). Based on Table 7.3, one observes that the algorithm of Section 7.3.2.3 gives almost the same results as the equivalent stochastic system method and satisfactory results compared to simulation.
Table 7.3 Analytical and simulation results of TC probabilities (Example 7.10).
| Equivalent stochastic system | Algorithm (Section 7.3.2.3 ) | Simulation | ||||
| P | ||||||
| 1 | 3.05 | 2.03 | 3.05 | 2.03 | 3.23 |
1.83 |
| 2 | 4.32 | 2.72 | 4.32 | 2.72 | 4.02 |
2.44 |
| 3 | 5.78 | 3.50 | 5.78 | 3.50 | 5.19 |
3.20 |
| 4 | 7.39 | 4.36 | 7.39 | 4.36 | 7.01 |
3.76 |
| 5 | 9.12 | 5.30 | 9.13 | 5.30 | 8.16 |
4.71 |
| 6 | 10.94 | 6.31 | 10.94 | 6.31 | 9.58 |
5.67 |
7.5 The Finite Single‐Threshold Model
7.5.1 The Service System
In the finite single‐threshold model (f‐STM), the requested b.u. and the corresponding service time of a new call are related to the occupied link bandwidth ![]() and a threshold
and a threshold ![]() . Specifically, the following CAC is applied. When
. Specifically, the following CAC is applied. When ![]() , then a new call of service‐class k is accepted in the system with its initial requirements
, then a new call of service‐class k is accepted in the system with its initial requirements ![]() . Otherwise, if
. Otherwise, if ![]() , the call tries to be connected in the system with
, the call tries to be connected in the system with ![]() , where
, where ![]() and
and ![]() , so that the product bandwidth requirement by service time remains constant. If the
, so that the product bandwidth requirement by service time remains constant. If the ![]() b.u. are not available the call is blocked and lost. The call arrival process is the quasi‐random, i.e., calls of service class
b.u. are not available the call is blocked and lost. The call arrival process is the quasi‐random, i.e., calls of service class ![]() come from a finite source population
come from a finite source population ![]() . By denoting as
. By denoting as ![]() the arrival rate per idle source of service‐class k, the offered traffic‐load per idle source is given by
the arrival rate per idle source of service‐class k, the offered traffic‐load per idle source is given by ![]() (in erl).
(in erl).
The comparison of the f‐STM with the f‐SRM reveals similar differences to those described in Section 2.5.1 for the STM and the SRM.
Example 7.11
Consider again Example 7.1 (![]() ) and let
) and let ![]() b.u.
b.u.
- Find the total number of permissible states
 , where
, where  is the number of service‐class 2 calls accepted in the system with
is the number of service‐class 2 calls accepted in the system with  b.u. Draw the state transition diagram.
b.u. Draw the state transition diagram. - Calculate the state probabilities
 and the corresponding values of
and the corresponding values of  based on the GB equations.
based on the GB equations. - Calculate the TC probabilities of both service‐classes and the link utilization.
- There are 16 permissible states of the form
 . The state space
. The state space  and the state transition diagram are shown in Figure 7.5.
and the state transition diagram are shown in Figure 7.5. - Based on Figure 7.5, we obtain the following 16 GB equations:

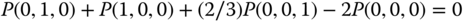










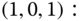
















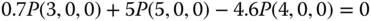


The solution of this linear system is:
















Then, based on the values of
 , we obtain the values of
, we obtain the values of  :
:





- The TC probabilities of service‐class 1,
 , are given by:
, are given by:  (0.165955 in the STM, see Example 2.11)
(0.165955 in the STM, see Example 2.11)The TC probabilities of service‐class 2 calls,
 , when they require
, when they require  b.u., are:
b.u., are: (0.382997 in the STM)
(0.382997 in the STM)The link utilization is determined by:
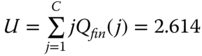 b.u. (2.685 in the STM)
b.u. (2.685 in the STM)

Figure 7.5 The state space  and the state transition diagram (Example 7.11).
and the state transition diagram (Example 7.11).
7.5.2 The Analytical Model
7.5.2.1 Steady State Probabilities
To derive a recursive formula for the calculation of ![]() , we concentrate on a single link of capacity
, we concentrate on a single link of capacity ![]() b.u. that accommodates two service‐classes with the following traffic characteristics:
b.u. that accommodates two service‐classes with the following traffic characteristics: ![]() . If
. If ![]() upon the arrival of a service‐class 2 call, then this call requests
upon the arrival of a service‐class 2 call, then this call requests ![]() b.u. and
b.u. and ![]() . No such option is considered for calls of service‐class 1.
. No such option is considered for calls of service‐class 1.
Although the f‐STM does not have a PFS, we assume that the LB equation (6.33) does hold for calls of service‐class 1, for ![]() :
:
or, due to the fact that in the equivalent stochastic system, ![]() :
:
For calls of service‐class 2, we assume the existence of LB between adjacent states:
where ![]() is the offered traffic‐load per idle source of service‐class 2 with
is the offered traffic‐load per idle source of service‐class 2 with ![]() and
and ![]() is the mean number of service‐class 2 calls accepted in the system with
is the mean number of service‐class 2 calls accepted in the system with ![]() in state
in state ![]() .
.
Equations (7.32)–(7.34) lead to the following system of equations:
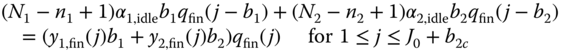


For (7.35), we adopt the (migration) approximation that the value of ![]() in state
in state ![]() is negligible when
is negligible when ![]() . For (7.37), we adopt the (upward migration) approximation that the value of
. For (7.37), we adopt the (upward migration) approximation that the value of ![]() in state
in state ![]() is negligible when
is negligible when ![]() . Based on these approximations, we have (for
. Based on these approximations, we have (for ![]() ):
):

where  , and
, and ![]() .
.
In the general case of ![]() service‐classes, the formula for
service‐classes, the formula for ![]() is the following [ 2]:
is the following [ 2]:

where  ,
, 
Note that if ![]() for
for ![]() , and the total offered traffic‐load remains constant, then we have the recursion (2.38) of the STM.
, and the total offered traffic‐load remains constant, then we have the recursion (2.38) of the STM.
7.5.2.2 TC Probabilities, CBP, Utilization, and Mean Number of In‐service Calls
The following performance measures can be determined based on (7.39):
- The TC probabilities of service‐class k calls with
 b.u.,
b.u.,  , via (6.35) (assuming that calls have no option for
, via (6.35) (assuming that calls have no option for  ).
). - The TC probabilities of service‐class k calls with
 b.u.,
b.u., 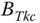 , via:
(7.40)where
, via:
(7.40)where
 is the normalization constant.
is the normalization constant. - The CBP (or CC probabilities) of service‐class k calls with
 (without the option of
(without the option of  ),
),  , via (6.35) but for a system with
, via (6.35) but for a system with  traffic sources.
traffic sources. - The CBP (or CC probabilities) of service‐class k calls with
 , via (7.40) but for a system with
, via (7.40) but for a system with  traffic sources.
traffic sources. - The conditional TC probabilities of service‐class k calls with
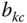 given that
given that  , via:
(7.41)
, via:
(7.41)
- The link utilization,
 , via (6.36).
, via (6.36). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u., 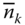 , via (6.37), while the mean number of service‐class k calls with
, via (6.37), while the mean number of service‐class k calls with  given that the system state is
given that the system state is  , via:
(7.42)
, via:
(7.42)
- The average number of service‐class
 calls in the system accepted with
calls in the system accepted with  b.u.,
b.u.,  , via:
(7.43)where
, via:
(7.43)where
 is the average number of service‐class k calls with
is the average number of service‐class k calls with  given that the system state is
given that the system state is  , and is determined by:
(7.44)
, and is determined by:
(7.44)
The determination of ![]() via ( 7.39), and consequently of all performance measures, requires the value of
via ( 7.39), and consequently of all performance measures, requires the value of ![]() and
and ![]() , which are unknown. In 2, 3, there is a method for the determination of
, which are unknown. In 2, 3, there is a method for the determination of ![]() and
and ![]() in state
in state ![]() via an equivalent stochastic system. However, the state space determination of the equivalent system can be complex (as in the case of the EnMLM and the f‐SRM) even for small capacity systems that serve many service‐classes.
via an equivalent stochastic system. However, the state space determination of the equivalent system can be complex (as in the case of the EnMLM and the f‐SRM) even for small capacity systems that serve many service‐classes.
Example 7.12
Consider Example 7.2 (![]() ) and let
) and let ![]() . Due to the migration approximation, calls of service‐class 1 with
. Due to the migration approximation, calls of service‐class 1 with ![]() are assumed to be negligible when
are assumed to be negligible when ![]() . In addition, due to the upward migration approximation, calls of service‐class 1 with
. In addition, due to the upward migration approximation, calls of service‐class 1 with ![]() are assumed to be negligible when
are assumed to be negligible when ![]() . Taking into account these approximations, the state space consists of 11 states
. Taking into account these approximations, the state space consists of 11 states ![]() , presented in Table 7.4 together with the respective occupied link bandwidth
, presented in Table 7.4 together with the respective occupied link bandwidth ![]() and the blocking states
and the blocking states ![]() . According to Table 7.4, the values of
. According to Table 7.4, the values of ![]() appear more than once, and therefore it is impossible to use directly ( 7.39) for the calculation of
appear more than once, and therefore it is impossible to use directly ( 7.39) for the calculation of ![]() . To overcome this, an equivalent stochastic system should be determined with the following three characteristics:
. To overcome this, an equivalent stochastic system should be determined with the following three characteristics:
- The states
 of the equivalent system are the same as the initial one.
of the equivalent system are the same as the initial one. - Each state
 of the equivalent system has a unique value for the occupied link bandwidth.
of the equivalent system has a unique value for the occupied link bandwidth. - The chosen values of
 , and
, and 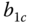 of the equivalent system keep constant (as much as possible) the initial ratios of
of the equivalent system keep constant (as much as possible) the initial ratios of  .
.
In this example, the values ![]() , and
, and ![]() are an approximate solution to the initial system; for these values we present in the last column of Table 7.4 the unique values of the equivalent occupied link bandwidth,
are an approximate solution to the initial system; for these values we present in the last column of Table 7.4 the unique values of the equivalent occupied link bandwidth, ![]() . The resultant TC probabilities are
. The resultant TC probabilities are ![]() % and
% and ![]() %.
%.
Table 7.4 The state space, ![]() , and the blocking states (Example 7.12).
, and the blocking states (Example 7.12).
| 0 | 0 | 0 | 0 | 0 | ||
| 0 | 1 | 0 | 2 | 2000 | ||
| 0 | 1 | 1 | 3 | 3001 | ||
| 0 | 1 | 2 | 4 | 4002 | * | |
| 0 | 1 | 3 | 5 | 5003 | * | * |
| 0 | 2 | 0 | 4 | 4000 | * | |
| 0 | 2 | 1 | 5 | 5001 | * | * |
| 1 | 0 | 0 | 3 | 3000 | ||
| 1 | 0 | 1 | 4 | 4001 | * | |
| 1 | 0 | 2 | 5 | 5002 | * | * |
| 1 | 1 | 0 | 5 | 5000 | * | * |
To circumvent the determination of an equivalent system, in the next section we modify the algorithm of Section 6.2.2.3 (initially proposed for the EnMLM) to fit to the f‐STM.
7.5.2.3 An Approximate Algorithm for the Determination of  in the f‐STM
in the f‐STM
Contrary to ( 7.39), which requires enumeration and processing of the state space, the algorithm presented herein is much simpler and easy to implement [ 5].


Example 7.13
Consider again Example 7.11 (![]() ). Apply the algorithm of Section 7.5.2.3 for the determination of TC probabilities.
). Apply the algorithm of Section 7.5.2.3 for the determination of TC probabilities.
- Step 1:
The corresponding infinite loss model (STM) is
 . Based on (2.38), we have the following normalized values of
. Based on (2.38), we have the following normalized values of  :
: 





- Step 2:
Based on (2.41) and (2.42), we have:















- Step 3:
Based on (7.45), we have the following normalized values of
 :
: 





- Step 4:
The approximate TC probabilities are:
 (compare with the exact 0.152594)
(compare with the exact 0.152594) (compare with the exact 0.365804)
(compare with the exact 0.365804)
7.6 The Finite Single‐Threshold Model under the BR Policy
7.6.1 The Service System
In the f‐STM under the BR policy (f‐STM/BR), ![]() b.u. are reserved to benefit calls of all other service‐classes apart from service‐class k. The application of the BR policy in the f‐STM is similar to that of the STM/BR as the following example shows.
b.u. are reserved to benefit calls of all other service‐classes apart from service‐class k. The application of the BR policy in the f‐STM is similar to that of the STM/BR as the following example shows.
Example 7.14
Consider again Example 7.11 (![]() ) and let the BR parameters be
) and let the BR parameters be ![]() b.u. and
b.u. and ![]() b.u. so that
b.u. so that ![]() .
.
- Find the total number of permissible states
 , where
, where  is the number of service‐class 2 calls accepted in the system with
is the number of service‐class 2 calls accepted in the system with  b.u. Draw the state transition diagram.
b.u. Draw the state transition diagram. - Calculate the state probabilities
 and the corresponding values of
and the corresponding values of  based on the GB equations.
based on the GB equations. - Calculate the TC probabilities of both service‐classes and the link utilization.
- There are 13 permissible states of the form
 . The state space
. The state space  and the state transition diagram are shown in Figure 7.6.
and the state transition diagram are shown in Figure 7.6. - Based on Figure 7.6, we obtain the following 13 GB equations:

























The solution of this linear system is:











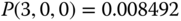

Then, based on the values of
 , we obtain the values of
, we obtain the values of  :
:





- The TC probabilities of service‐class 1,
 , are given by:
, are given by: 
(0.545538 in the STM/BR, see Example 2.13) The TC probabilities of service‐class 2 calls,
 , when they require
, when they require  b.u., are:
b.u., are: (0.313991 in the STM/BR)
(0.313991 in the STM/BR)The link utilization is determined by:
 b.u. (2.512 in the STM/BR)
b.u. (2.512 in the STM/BR)

Figure 7.6 The state space  and the state transition diagram (Example 7.14).
and the state transition diagram (Example 7.14).
7.6.2 The Analytical Model
7.6.2.1 Link Occupancy Distribution
In the f‐STM/BR, the unnormalized values of ![]() can be calculated in an approximate way according to the Roberts method. Based on that method, we apply an algorithm similar to the one presented in Section 7.5.2.3 , which is modified as follows:
can be calculated in an approximate way according to the Roberts method. Based on that method, we apply an algorithm similar to the one presented in Section 7.5.2.3 , which is modified as follows:

7.6.2.2 TC Probabilities, CBP, Utilization, and Mean Number of In‐service Calls
The following performance measures can be determined based on (7.48):
- The TC probabilities of service‐class k calls with
 b.u.,
b.u.,  , via (6.42).
, via (6.42). - The TC probabilities of service‐class k calls with
 , via:
(7.49)
, via:
(7.49)
- The CC probabilities of service‐class k calls with
 (without the option of
(without the option of 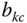 ),
),  , via (6.42) but for a system with
, via (6.42) but for a system with  traffic sources.
traffic sources. - The CC probabilities of service‐class k calls with
 , via (7.49) but for a system with
, via (7.49) but for a system with  traffic sources.
traffic sources. - The conditional TC probabilities of service‐class k calls with
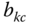 given that
given that  , via (7.41), while subtracting the BR parameter
, via (7.41), while subtracting the BR parameter  from
from  .
. - The link utilization,
 , via (6.36).
, via (6.36). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via (6.37) where
, via (6.37) where  is determined by:
(7.50)
is determined by:
(7.50)
- The average number of service‐class
 calls in the system accepted with
calls in the system accepted with  b.u.,
b.u.,  , via (7.43) where
, via (7.43) where  is determined by:
(7.51)
is determined by:
(7.51)
Example 7.15
Consider again Example 7.14 (![]() ). Apply the algorithm of Section 7.6.2.1 for the determination of TC probabilities.
). Apply the algorithm of Section 7.6.2.1 for the determination of TC probabilities.
- Step 1: The corresponding infinite loss model (STM/BR) is
 , and
, and  erl.
erl.
Based on (2.44), we have the following normalized values of
 :
:





- Step 2:
Based on (2.47) and (2.48), we have:















- Step 3: Based on (7.48), we have the following normalized values of
 :
: 





The approximate TC probabilities are:
 (compare with the exact 0.535982)
(compare with the exact 0.535982) (compare with the exact 0.295331)
(compare with the exact 0.295331)
7.7 The Finite Multi‐Threshold Model
7.7.1 The Service System
In the finite multi‐threshold model (f‐MTM), there exist ![]() different thresholds which are common to all service‐classes. A call of service‐class k with initial requirements
different thresholds which are common to all service‐classes. A call of service‐class k with initial requirements ![]() can use, depending on the occupied link bandwidth
can use, depending on the occupied link bandwidth ![]() , one of the
, one of the ![]() requirements
requirements ![]() , where the pair
, where the pair ![]() is used when
is used when ![]() , while
, while ![]() ). The maximum possible threshold is
). The maximum possible threshold is ![]() , while
, while ![]() . As far as the bandwidth requirements of a service‐class k call are concerned, we assume that they decrease as
. As far as the bandwidth requirements of a service‐class k call are concerned, we assume that they decrease as ![]() increases, i.e.,
increases, i.e., ![]() , while by definition
, while by definition ![]() .
.
7.7.2 The Analytical Model
7.7.2.1 Steady State Probabilities
To derive a recursive formula for the calculation of ![]() , the following LB equations are considered:
, the following LB equations are considered:

and
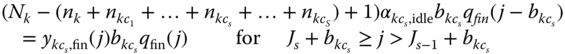
where ![]() is the number of in‐service calls of service‐class
is the number of in‐service calls of service‐class ![]() accepted in the system with
accepted in the system with ![]() b.u.,
b.u., ![]() and
and ![]() .
.
Similar to the analysis of the f‐STM and based on (7.52) and (7.53), we have the following recursive formula for the calculation of ![]() [ 5]:
[ 5]:

where 
 , and
, and ![]() .
.
Note that if ![]() for
for ![]() , and the total offered traffic‐load remains constant, then we have the recursion (2.51) of the MTM.
, and the total offered traffic‐load remains constant, then we have the recursion (2.51) of the MTM.
7.7.2.2 TC Probabilities, CBP, Utilization, and Mean Number of In‐service Calls
The following performance measures can be determined based on (7.54):
- The TC probabilities of service‐class k calls with
 b.u.,
b.u.,  , via (6.35).
, via (6.35). - The TC probabilities of service‐class k calls with their last bandwidth requirement
 b.u.,
b.u.,  , via:
(7.55)where
, via:
(7.55)where
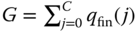 is the normalization constant.
is the normalization constant. - The CC probabilities of service‐class k calls with
 (without retrial),
(without retrial),  , via (6.35) but for a system with
, via (6.35) but for a system with  traffic sources.
traffic sources. - The CC probabilities of service‐class k calls with
 , via (7.55) but for a system with
, via (7.55) but for a system with  traffic sources.
traffic sources. - The conditional TC probabilities of service‐class k calls with
 b.u. given that
b.u. given that  , via:
(7.56)
, via:
(7.56)
- The link utilization,
 , via (6.36).
, via (6.36). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via (6.37), while the mean number of service‐class k calls with
, via (6.37), while the mean number of service‐class k calls with  given that the system state is
given that the system state is 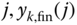 , via (7.42).
, via (7.42). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via:
(7.57)where
, via:
(7.57)where
 is the average number of service‐class k calls with
is the average number of service‐class k calls with  given that the system state is
given that the system state is  , and is determined by:
, and is determined by:

The determination of ![]() via ( 7.54), and consequently of all performance measures, requires the values of
via ( 7.54), and consequently of all performance measures, requires the values of ![]() and
and ![]() , which are unknown. To avoid the determination of an equivalent stochastic system we adopt the algorithm of Section 7.7.2.3 (see below), which is similar to the algorithm of Section 7.5.2.3 of the f‐STM.
, which are unknown. To avoid the determination of an equivalent stochastic system we adopt the algorithm of Section 7.7.2.3 (see below), which is similar to the algorithm of Section 7.5.2.3 of the f‐STM.
7.7.2.3 An Approximate Algorithm for the Determination of  in the f‐MTM
in the f‐MTM
The algorithm can be described by the following steps [ 5].


7.8 The Finite Multi‐Threshold Model under the BR Policy
7.8.1 The Service System
In the f‐MTM under the BR policy (f‐MTM/BR), ![]() b.u. are reserved to benefit calls of all other service‐classes apart from service‐class k. The application of the BR policy in the f‐MTM/BR is similar to that of the f‐MRM/BR.
b.u. are reserved to benefit calls of all other service‐classes apart from service‐class k. The application of the BR policy in the f‐MTM/BR is similar to that of the f‐MRM/BR.
7.8.2 The Analytical Model
7.8.2.1 Link Occupancy Distribution
Based on the Roberts method and the algorithm of Section 7.6.2.1 of the f‐STM/BR, the unnormalized values of the link occupancy distribution, ![]() , in the f‐MTM/BR can be determined as follows:
, in the f‐MTM/BR can be determined as follows:


7.8.2.2 TC Probabilities, CBP, Utilization and Mean Number of In‐service Calls
Based on (7.61) and (2.58), we can determine the following performance measures:
- The TC probabilities of service‐class k calls with
 b.u.,
b.u.,  , via (6.42).
, via (6.42). - The TC probabilities of service‐class k calls with
 , via:
(7.62)
, via:
(7.62)
- The CC probabilities of service‐class k calls with
 (without the option of
(without the option of  , via (6.42) but for a system with
, via (6.42) but for a system with  traffic sources.
traffic sources. - The CC probabilities of service‐class k calls with with
 , via (7.62) but for a system with
, via (7.62) but for a system with  traffic sources.
traffic sources. - The conditional TC probabilities of service‐class k calls with
 b.u. given that
b.u. given that  , via (7.56), while subtracting the BR parameter
, via (7.56), while subtracting the BR parameter  from
from  .
. - The link utilization,
 , via (6.36).
, via (6.36). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via (6.37) where
, via (6.37) where  is determined by (7.50).
is determined by (7.50). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via (7.57) where
, via (7.57) where 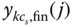 is determined by:
(7.63)
is determined by:
(7.63)
7.9 The Finite Connection Dependent Threshold Model
7.9.1 The Service System
In the finite CDTM (f‐CDTM), the difference compared to the f‐MTM is that different service‐classes may have different sets of thresholds. Each arriving call of a service‐class k may have ![]() bandwidth and service‐time requirements, that is, one initial requirement with values
bandwidth and service‐time requirements, that is, one initial requirement with values ![]() and
and ![]() more requirements with values
more requirements with values ![]() , where
, where ![]() ,
, ![]() and
and ![]() . The pair
. The pair ![]() is used when
is used when ![]() , where
, where ![]() and
and ![]() are two successive thresholds of service‐class k, while
are two successive thresholds of service‐class k, while ![]() ; the highest possible threshold (other than
; the highest possible threshold (other than ![]() ) is
) is ![]() . By convention,
. By convention, ![]() and
and ![]() , while the pair
, while the pair ![]() is used when
is used when ![]() .
.
7.9.2 The Analytical Model
7.9.2.1 Steady State Probabilities
Similar to the analysis of the f‐MTM and based on ( 7.54), we have the following recursive formula for the calculation of ![]() [ 5]:
[ 5]:

where  ,
,  , and
, and ![]() .
.
Note that if ![]() for
for ![]() , and the total offered traffic‐load remains constant, then we have the recursion (2.65) of the CDTM.
, and the total offered traffic‐load remains constant, then we have the recursion (2.65) of the CDTM.
7.9.2.2 TC Probabilities, CBP, Utilization, and Mean Number of In‐service Calls
The following performance measures can be determined based on (7.64):
- The TC probabilities of service‐class k calls with
 b.u.,
b.u.,  , via (6.35).
, via (6.35). - The TC probabilities of service‐class k calls with their last bandwidth requirement
 b.u.,
b.u.,  , via:
(7.65)where
, via:
(7.65)where
 is the normalization constant.
is the normalization constant. - The CC probabilities of service‐class k calls with
 (without retrial),
(without retrial),  , via (6.35) but for a system with
, via (6.35) but for a system with  traffic sources.
traffic sources. - The CC probabilities of service‐class k calls with
 , via (7.65) but for a system with
, via (7.65) but for a system with  traffic sources.
traffic sources. - The conditional TC probabilities of service‐class k calls with
 b.u. given that
b.u. given that  , via:
(7.66)
, via:
(7.66)
- The link utilization,
 , via (6.36).
, via (6.36). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via (6.37), while the mean number of service‐class k calls with
, via (6.37), while the mean number of service‐class k calls with  given that the system state is
given that the system state is  , via ( 7.42).
, via ( 7.42). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via ( 7.57), while the average number of service‐class k calls with
, via ( 7.57), while the average number of service‐class k calls with  given that the system state is
given that the system state is  , via:
(7.67)
, via:
(7.67)
The calculation of
 via ( 7.64), and consequently of all performance measures, requires the determination of an equivalent stochastic system. To avoid it, we adopt the algorithm of Section 7.9.2.3 (see below), which is similar to the algorithm of Section 7.7.2.3 of the f‐MTM.
via ( 7.64), and consequently of all performance measures, requires the determination of an equivalent stochastic system. To avoid it, we adopt the algorithm of Section 7.9.2.3 (see below), which is similar to the algorithm of Section 7.7.2.3 of the f‐MTM.
7.9.2.3 An Approximate Algorithm for the Determination of  in the f‐CDTM
in the f‐CDTM
The algorithm can be described by the following steps [ 5]:


Example 7.16
Consider again Example 7.10 (![]() ). The values of
). The values of ![]() and
and ![]() are used when
are used when ![]() and
and ![]() , respectively. Similarly, the value of
, respectively. Similarly, the value of ![]() is used when
is used when ![]() . The equivalent stochastic system used for the TC calculation in this f‐CDTM example is
. The equivalent stochastic system used for the TC calculation in this f‐CDTM example is ![]() . We consider three sets of
. We consider three sets of ![]() : (i)
: (i) ![]() , (ii)
, (ii) ![]() , and (iii)
, and (iii) ![]() . Table 7.5 shows the various sets of
. Table 7.5 shows the various sets of ![]() and the corresponding offered traffic‐loads, while Table 7.6 shows the state space, which consists of 53 states. The corresponding CDTM system used in the algorithm of Section 7.9.2.3 is
and the corresponding offered traffic‐loads, while Table 7.6 shows the state space, which consists of 53 states. The corresponding CDTM system used in the algorithm of Section 7.9.2.3 is ![]() . For the three different sets of
. For the three different sets of ![]() , we present in Tables 7.7–7.9 the analytical TC probabilities obtained via the equivalent stochastic system and the algorithm of Section 7.9.2.3 together with the corresponding simulation results. At each point (P) of Tables 7.7– 7.9, we assume that the values of
, we present in Tables 7.7–7.9 the analytical TC probabilities obtained via the equivalent stochastic system and the algorithm of Section 7.9.2.3 together with the corresponding simulation results. At each point (P) of Tables 7.7– 7.9, we assume that the values of ![]() , and
, and ![]() are constant while those of
are constant while those of ![]() and
and ![]() are increased by 0.4/
are increased by 0.4/![]() and 0.7/
and 0.7/![]() , respectively, i.e., point 1 is
, respectively, i.e., point 1 is ![]() , while point 6 is
, while point 6 is ![]() ,
, ![]() .
.
According to Tables 7.7– 7.9, the analytical TC probabilities obtained via the algorithm of Section 7.9.2.3 are closer to the simulation results (mean values of 7 runs with 95% confidence interval) than the corresponding results obtained by the equivalent stochastic system.
Table 7.5 Sets of sources and offered traffic‐loads per idle source (Example 7.16).
| Number of sources | |||||
Table 7.6 The state space, ![]() , and the blocking states (Example 7.16).
, and the blocking states (Example 7.16).
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | ||
| 0 | 1 | 0 | 0 | 0 | 7 | 7001 | ||
| 0 | 2 | 0 | 0 | 0 | 14 | 14002 | ||
| 0 | 3 | 0 | 0 | 0 | 21 | 21003 | ||
| 0 | 4 | 0 | 0 | 0 | 28 | 28004 | ||
| 0 | 5 | 0 | 0 | 0 | 35 | 35005 | ||
| 0 | 5 | 1 | 0 | 0 | 43 | 43005 | ||
| 0 | 5 | 1 | 0 | 1 | 47 | 47010 | * | * |
| 0 | 5 | 1 | 1 | 0 | 49 | 49005 | * | * |
| 0 | 6 | 0 | 0 | 0 | 42 | 42006 | ||
| 0 | 6 | 0 | 0 | 1 | 46 | 46011 | * | |
| 0 | 6 | 0 | 0 | 2 | 50 | 50016 | * | * |
| 0 | 6 | 0 | 1 | 0 | 48 | 48006 | * | * |
| 1 | 0 | 0 | 0 | 0 | 10 | 10000 | ||
| 1 | 1 | 0 | 0 | 0 | 17 | 17001 | ||
| 1 | 2 | 0 | 0 | 0 | 24 | 24002 | ||
| 1 | 3 | 0 | 0 | 0 | 31 | 31003 | ||
| 1 | 3 | 1 | 0 | 0 | 39 | 39003 | ||
| 1 | 3 | 1 | 0 | 1 | 43 | 43008 | ||
| 1 | 3 | 1 | 0 | 2 | 47 | 47013 | * | * |
| 1 | 3 | 1 | 1 | 0 | 45 | 45003 | * | |
| 1 | 3 | 1 | 1 | 1 | 49 | 49008 | * | * |
| 1 | 4 | 0 | 0 | 0 | 38 | 38004 | ||
| 1 | 4 | 0 | 0 | 1 | 42 | 42009 | ||
| 1 | 4 | 0 | 0 | 2 | 46 | 46014 | * | |
| 1 | 4 | 0 | 0 | 3 | 50 | 50019 | * | * |
| 1 | 4 | 0 | 1 | 0 | 44 | 44004 | ||
| 1 | 4 | 0 | 1 | 1 | 48 | 48009 | * | * |
| 1 | 4 | 0 | 2 | 0 | 50 | 50004 | * | * |
| 2 | 0 | 0 | 0 | 0 | 20 | 20000 | ||
| 2 | 1 | 0 | 0 | 0 | 27 | 27001 | ||
| 2 | 2 | 0 | 0 | 0 | 34 | 34002 | ||
| 2 | 2 | 1 | 0 | 0 | 42 | 42002 | ||
| 2 | 2 | 1 | 0 | 1 | 46 | 46007 | * | |
| 2 | 2 | 1 | 0 | 2 | 50 | 50012 | * | * |
| 2 | 2 | 1 | 1 | 0 | 48 | 48002 | * | * |
| 2 | 3 | 0 | 0 | 0 | 41 | 41003 | ||
| 2 | 3 | 0 | 0 | 1 | 45 | 45008 | * | |
| 2 | 3 | 0 | 0 | 2 | 49 | 49013 | * | * |
| 2 | 3 | 0 | 1 | 0 | 47 | 47003 | * | * |
| 3 | 0 | 0 | 0 | 0 | 30 | 30000 | ||
| 3 | 1 | 0 | 0 | 0 | 37 | 37001 | ||
| 3 | 1 | 0 | 1 | 0 | 43 | 43001 | ||
| 3 | 1 | 0 | 2 | 0 | 49 | 49001 | * | * |
| 3 | 1 | 0 | 1 | 1 | 47 | 47006 | * | * |
| 3 | 2 | 0 | 0 | 0 | 44 | 44002 | ||
| 3 | 2 | 0 | 0 | 1 | 48 | 48007 | * | * |
| 3 | 2 | 0 | 1 | 0 | 50 | 50002 | * | * |
| 4 | 0 | 0 | 0 | 0 | 40 | 40000 | ||
| 4 | 0 | 0 | 0 | 1 | 44 | 44005 | ||
| 4 | 0 | 0 | 0 | 2 | 48 | 48010 | * | * |
| 4 | 0 | 0 | 1 | 0 | 46 | 46000 | * | |
| 4 | 0 | 0 | 1 | 1 | 50 | 50005 | * | * |
Table 7.7 Analytical and simulation results of the TC probabilities (![]() ) (Example 7.16).
) (Example 7.16).
| Equivalent stochastic system | Algorithm (Section 7.9.2.3 ) | Simulation | ||||
| P | ||||||
| 1 | 1.96 | 1.07 | 1.57 | 0.98 | 1.57 |
0.82 |
| 2 | 2.78 | 1.52 | 2.18 | 1.37 | 2.17 |
1.17 |
| 3 | 3.76 | 2.05 | 2.92 | 1.83 | 2.97 |
1.53 |
| 4 | 4.90 | 2.66 | 3.77 | 2.35 | 4.07 |
1.93 |
| 5 | 6.19 | 3.34 | 4.73 | 2.91 | 4.96 |
2.36 |
| 6 | 7.63 | 4.09 | 5.78 | 3.50 | 5.96 |
2.95 |
Table 7.8 Analytical and simulation results of the TC probabilities (![]() ) (Example 7.16).
) (Example 7.16).
| Equivalent stochastic system | Algorithm (Section 7.9.2.3 ) | Simulation | ||||
| P | ||||||
| 1 | 4.02 | 2.23 | 3.70 | 2.06 | 3.00 |
1.77 |
| 2 | 5.89 | 3.25 | 5.45 | 3.00 | 4.27 |
2.67 |
| 3 | 8.18 | 4.48 | 7.61 | 4.13 | 6.11 |
3.79 |
| 4 | 10.86 | 5.92 | 10.15 | 5.45 | 8.06 |
5.20 |
| 5 | 13.87 | 7.52 | 13.00 | 6.93 | 10.03 |
6.83 |
| 6 | 17.12 | 9.27 | 16.12 | 8.55 | 12.56 |
8.27 |
Table 7.9 Analytical and simulation results of the TC probabilities (![]() ) (Example 7.16).
) (Example 7.16).
| Equivalent stochastic system | Algorithm (Section 7.9.2.3 ) | Simulation | ||||
| P | ||||||
| 1 | 4.62 | 2.57 | 4.41 | 2.43 | 3.74 |
2.17 |
| 2 | 6.82 | 3.76 | 6.56 | 3.58 | 5.18 |
3.40 |
| 3 | 9.50 | 5.21 | 9.20 | 4.97 | 7.54 |
4.62 |
| 4 | 12.62 | 6.88 | 12.29 | 6.60 | 9.72 |
6.31 |
| 5 | 16.09 | 8.76 | 15.74 | 8.43 | 11.78 |
8.40 |
| 6 | 19.80 | 10.78 | 19.45 | 10.43 | 14.03 |
10.49 |
7.10 The Finite Connection Dependent Threshold Model under the BR Policy
7.10.1 The Service System
In the f‐CDTM under the BR policy (f‐CDTM/BR), ![]() b.u. are reserved to benefit calls of all other service‐classes apart from service‐class k. The application of the BR policy in the f‐CDTM/BR is similar to that of the f‐MTM/BR.
b.u. are reserved to benefit calls of all other service‐classes apart from service‐class k. The application of the BR policy in the f‐CDTM/BR is similar to that of the f‐MTM/BR.
7.10.2 The Analytical Model
7.10.2.1 Link Occupancy Distribution
Based on the Roberts method and the algorithm of Section 7.8.2.1 of the f‐MTM/BR, the unnormalized values of the link occupancy distribution, ![]() , in the f‐CDTM/BR can be determined as follows:
, in the f‐CDTM/BR can be determined as follows:
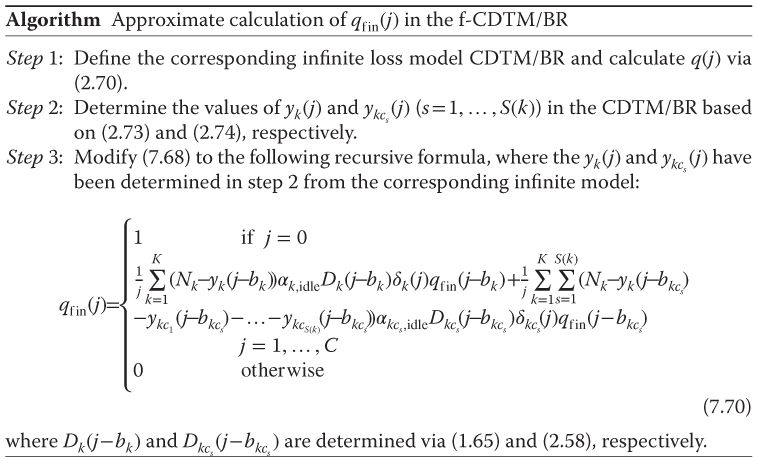
7.10.2.2 TC Probabilities, CBP, Utilization, and Mean Number of In‐service Calls
Based on (7.70) and (2.58), we can determine the following performance measures:
- The TC probabilities of service‐class k calls with
 b.u.,
b.u.,  , via (6.42).
, via (6.42). - The TC probabilities of service‐class k calls with
 , via:
(7.71)
, via:
(7.71)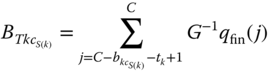
- The CC probabilities of service‐class k calls with
 (without the option of
(without the option of  , via (6.42) but for a system with
, via (6.42) but for a system with  traffic sources.
traffic sources. - The CC probabilities of service‐class k calls with with
 , via (7.71) but for a system with
, via (7.71) but for a system with  traffic sources.
traffic sources. - The conditional TC probabilities of service‐class k calls with
 b.u. given that
b.u. given that  , via (7.66), while subtracting the BR parameter
, via (7.66), while subtracting the BR parameter  from
from  .
. - The link utilization,
 , via (6.36).
, via (6.36). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via (6.37) where
, via (6.37) where  is determined by (7.46).
is determined by (7.46). - The average number of service‐class k calls in the system accepted with
 b.u.,
b.u.,  , via ( 7.57) where
, via ( 7.57) where  is determined by:
(7.72)
is determined by:
(7.72)
7.11 Applications
Since the finite multirate retry‐threshold loss models are a combination of the retry‐threshold loss models of Chapter 2 and the EnMLM of Chapter , the interested reader may refer to Sections 2.11 and 6.5 for possible applications.
7.12 Further Reading
Similar to the previous section, the interested reader may refer to the corresponding section of Chapter 2 (Section 2.12) and Chapter 6 (Section 6.6). In addition to these sections, interesting extensions of the f‐CDTM have been proposed in [7,8], for WCDMA networks. Compared to [ 7], in [ 8], a CAC distinguishes handover traffic from new traffic. More precisely, when the cell load is above a predefined threshold, handover calls are allowed to reduce their bandwidth requirements in order to avoid blocking.
References
- 1 G. Stamatelos and V. Koukoulidis, Reservation‐based bandwidth allocation in a radio ATM network. IEEE/ACM Transactions on Networking, 5(3):420–428, June 1997.
- 2 I. Moscholios, M. Logothetis and P. Nikolaropoulos, Engset multi‐rate state‐dependent loss models. Performance Evaluation, 59(2–3):247–277, February 2005.
- 3 I. Moscholios and M. Logothetis, Engset multirate state‐dependent loss models with QoS guarantee. International Journal of Communication Systems, 19(1):67–93, February 2006.
- 4 I. Moscholios, M. Logothetis and G. Kokkinakis, A simplified blocking probability calculation in the retry loss models for finite sources. Proceedings of Communication Systems, Networks and Digital Signal Processing – 5th CSNDSP, Patras, Greece, July 2006.
- 5 I. Moscholios, M. Logothetis and G. Kokkinakis, On the calculation of blocking probabilities in the multirate state‐dependent loss models for finite sources. Mediterranean Journal of Computers and Networks, 3(3):100–109, July 2007.
- 6 J. Kaufman, Blocking with retrials in a completely shared resource environment. Performance Evaluation, 15(2):99–113, June 1992.
- 7 V. Vassilakis, G. Kallos, I. Moscholios and M. Logothetis, Call‐level analysis of W‐CDMA networks supporting elastic services of finite population. IEEE ICC 2008, Beijing, China, May 2008.
- 8 V. Vassilakis, I. Moscholios, J. Vardakas and M. Logothetis, Handoff modeling in cellular CDMA with finite sources and state‐dependent bandwidth requirements. Proceedings of IEEE CAMAD 2014, Athens, Greece, December 2014.
