2
Multirate Retry Threshold Loss Models
We consider multirate loss models of random arriving calls with elastic bandwidth requirements and fixed bandwidth allocation during service. Calls may retry several times upon arrival (requiring less bandwidth each time) in order to be accepted for service. Alternatively, calls may request less bandwidth upon arrival, according to the occupied link bandwidth indicated by threshold(s).
2.1 The Single‐Retry Model
2.1.1 The Service System
In the single‐retry model (SRM), a link of capacity ![]() b.u. accommodates Poisson arriving calls of
b.u. accommodates Poisson arriving calls of ![]() service‐classes, under the CS policy. A new call of service‐class
service‐classes, under the CS policy. A new call of service‐class ![]() has a peak‐bandwidth requirement of
has a peak‐bandwidth requirement of ![]() b.u. and an exponentially distributed service time with mean
b.u. and an exponentially distributed service time with mean ![]() . If the initially required b.u. are not available in the link, the call is blocked, but immediately retries to be connected with bandwidth requirement
. If the initially required b.u. are not available in the link, the call is blocked, but immediately retries to be connected with bandwidth requirement ![]() b.u., while the mean of the new (exponentially distributed) service time increases to
b.u., while the mean of the new (exponentially distributed) service time increases to ![]() , so that the product bandwidth requirement by service time
, so that the product bandwidth requirement by service time ![]() remains constant [1,2]. If the
remains constant [1,2]. If the ![]() b.u. are not available, the call is blocked and lost (Figure 2.1). The CAC mechanism of a call of service‐class
b.u. are not available, the call is blocked and lost (Figure 2.1). The CAC mechanism of a call of service‐class ![]() is depicted in Figure 2.2. A new call of service‐class
is depicted in Figure 2.2. A new call of service‐class ![]() is blocked with
is blocked with ![]() b.u. if
b.u. if ![]() and is accepted with
and is accepted with ![]() b.u., if
b.u., if ![]() , where
, where ![]() and
and ![]() are the in‐service calls of service‐class
are the in‐service calls of service‐class ![]() (in the steady state of the system) accepted with
(in the steady state of the system) accepted with ![]() b.u., respectively. The comparison of the SRM with the EMLM reveals the following basic differences:
b.u., respectively. The comparison of the SRM with the EMLM reveals the following basic differences:
- (i) The steady state probabilities in the SRM do not have a PFS, since the notion of LB between adjacent states does not hold (see Example 2.1). Because of this, the unnormalized values of
 are determined via an approximate, but recursive, formula, as Section 2.1.2 shows.
are determined via an approximate, but recursive, formula, as Section 2.1.2 shows. - (ii) In the EMLM, the steady state vector of all in‐service calls of all service‐classes is
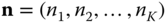 , while in the SRM the corresponding vector becomes
, while in the SRM the corresponding vector becomes  . This dimensionality increase means that only quite small problems can be solved exactly (see Example 2.1).
. This dimensionality increase means that only quite small problems can be solved exactly (see Example 2.1). - (iii) In the EMLM, the calculation of
 via the Kaufman–Roberts recursion (1.39) is insensitive to the service time distribution [3]. In the SRM, this insensitivity property does not hold. However, numerical examples in [ 2] show that the CBP obtained for various service time distributions are quite close.
via the Kaufman–Roberts recursion (1.39) is insensitive to the service time distribution [3]. In the SRM, this insensitivity property does not hold. However, numerical examples in [ 2] show that the CBP obtained for various service time distributions are quite close.

Figure 2.1 Service system of the SRM.

Figure 2.2 The CAC mechanism for a new call in the SRM.

Figure 2.3 The state space  (CS policy) and the state transition diagram (Example 2.1).
(CS policy) and the state transition diagram (Example 2.1).
2.1.2 The Analytical Model
2.1.2.1 Steady State Probabilities
To describe the analytical model in the steady state, let us concentrate on a single link of capacity ![]() b.u. that accommodates two service‐classes with the following traffic characteristics:
b.u. that accommodates two service‐classes with the following traffic characteristics: ![]() . Blocked calls of service‐class 2 can retry with parameters
. Blocked calls of service‐class 2 can retry with parameters ![]() , while blocked calls of service‐class 1 are not allowed to retry. Although the SRM does not have a PFS, we assume that the LB equation (1.51) proposed in the EMLM does hold, that is:
, while blocked calls of service‐class 1 are not allowed to retry. Although the SRM does not have a PFS, we assume that the LB equation (1.51) proposed in the EMLM does hold, that is:
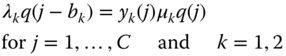
This assumption (approximation) is important for the derivation of an approximate but recursive formula for the calculation of ![]() . The aforementioned equation expresses the fact that no call blocking occurs in state
. The aforementioned equation expresses the fact that no call blocking occurs in state ![]() , if there are available
, if there are available ![]() b.u.
b.u. ![]() . If
. If ![]() , when a new call of service‐class 2 arrives in the system, then this call is blocked and retries to be connected with
, when a new call of service‐class 2 arrives in the system, then this call is blocked and retries to be connected with ![]() b.u. If
b.u. If ![]() , then, the retry call will be accepted in the system. To describe the latter case, we need an additional LB equation [ 2]:
, then, the retry call will be accepted in the system. To describe the latter case, we need an additional LB equation [ 2]:

where ![]() is the mean number of service‐class
is the mean number of service‐class ![]() calls accepted in the system with
calls accepted in the system with ![]() in state
in state ![]() .
.
Dividing (2.2) by ![]() and multiplying by
and multiplying by ![]() , we obtain [ 2]:
, we obtain [ 2]:

where ![]() is the offered traffic‐load of service‐class 2 calls with
is the offered traffic‐load of service‐class 2 calls with ![]() .
.
Equation (2.1) can be written as ![]() . Then, by multiplying both sides with
. Then, by multiplying both sides with ![]() and summing up for
and summing up for ![]() , we have:
, we have:

Adding (2.3) to (2.4), and since ![]() , we have:
, we have:

Apart from the assumption of the LB equation ( 2.1), another approximation is necessary for the recursive calculation of ![]() [ 2]:
[ 2]:

Equation (2.6) expresses the so‐called migration approximation [ 1, 2,4], according to which the number of calls accepted in the system with other than the maximum bandwidth requirement is negligible within a state space, called the migration space. In this space, the value of ![]() is negligible compared to
is negligible compared to ![]() when
when ![]() . For service‐class
. For service‐class ![]() (with
(with ![]() ):
):

Equation ( 2.4) due to ( 2.6) is written as:

The combination of (2.5) and (2.8) is achieved through the use of a binary parameter (![]() ), and gives an approximate but recursive formula for the determination of
), and gives an approximate but recursive formula for the determination of ![]() in the SRM, considering two service‐classes where only calls of service‐class 2 can retry [ 1, 2]:
in the SRM, considering two service‐classes where only calls of service‐class 2 can retry [ 1, 2]:
where ![]() , and
, and ![]() when
when ![]() (otherwise
(otherwise ![]() ).
).
The symbol ![]() is used to distinguish retry models, where only the migration approximation exists, from other models (e.g., thresholds models presented in Section 2.5) where the symbol
is used to distinguish retry models, where only the migration approximation exists, from other models (e.g., thresholds models presented in Section 2.5) where the symbol ![]() is used and additional approximations are considered.
is used and additional approximations are considered.
The generalization of (2.9) for ![]() service‐classes, where all service‐classes may retry, is as follows [ 2]:
service‐classes, where all service‐classes may retry, is as follows [ 2]:

where ![]() and
and ![]() when
when ![]() (otherwise
(otherwise ![]() ).
).
Note that the variable ![]() in (2.10) expresses the migration approximation, i.e., (2.7).
in (2.10) expresses the migration approximation, i.e., (2.7).
2.1.2.2 CBP, Utilization, and Mean Number of In‐service Calls
Having determined the unnormalized values of ![]() , we can calculate the following performance measures:
, we can calculate the following performance measures:
- The CBP of service‐class
 calls with
calls with  b.u. (i.e., the actual CBP of service‐class
b.u. (i.e., the actual CBP of service‐class  with retrial),
with retrial),  , via the following formula [ 2]:
(2.11)where
, via the following formula [ 2]:
(2.11)where
 is the normalization constant.
is the normalization constant. - The CBP of service‐class
 calls with
calls with  b.u. (i.e., the actual CBP of service‐class
b.u. (i.e., the actual CBP of service‐class  without retrial, or the retry probability in case of service‐class
without retrial, or the retry probability in case of service‐class  with retrial),
with retrial),  , via:
(2.12)
, via:
(2.12)
- The conditional CBP of service‐class
 retry calls given that they have been blocked with their initial bandwidth requirement
retry calls given that they have been blocked with their initial bandwidth requirement  , via:
(2.13)
, via:
(2.13)
- The link utilization,
 , via (1.54).
, via (1.54). - The mean number of service‐class k calls with
 b.u. in state
b.u. in state  , via:
(2.14)
, via:
(2.14)
- The mean number of service‐class
 calls with
calls with  b.u. in state
b.u. in state  , via:
(2.15)where
, via:
(2.15)where
 when
when  (otherwise
(otherwise  ).
). - The mean number of in‐service calls of service‐class k accepted in the system with
 , via:
(2.16)
, via:
(2.16)
- The mean number of in‐service calls of service‐class k accepted in the system with
 , via:
(2.17)
, via:
(2.17)
Example 2.2
In the system of Example 2.1 (![]() ):
):
- (a)Calculate the values of
 (link occupancy distribution) based on ( 2.10).
(link occupancy distribution) based on ( 2.10). - (b)Calculate the CBP of both service‐classes including the retry probability, as well as the conditional
 .
.
- (a) To determine the values of
 based on ( 2.10) (the unnormalized link occupancy distribution), starting with
based on ( 2.10) (the unnormalized link occupancy distribution), starting with  , we recursively calculate
, we recursively calculate 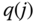 for
for  , while having
, while having  erl,
erl,  erl, and
erl, and  for
for  :
: 



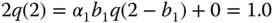










The normalization constant is
 .
.Thus:





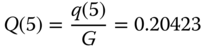
- (b)
 CBP of service‐class 1,
CBP of service‐class 1,  of service‐class 2, and
of service‐class 2, and  CBP of service‐class 2:
CBP of service‐class 2: 

(compare with the exact 0.20692) 

(compare with the exact 0.55226) 

(compare with the exact 0.37764) 

(compare with the exact 0.68380) It is apparent that even in small SRM examples the error introduced by the assumption of LB and the migration approximation is not significant.
2.2 The Single‐Retry Model under the BR Policy
2.2.1 The Service System
In the SRM under the BR policy (SRM/BR), ![]() b.u. are reserved to benefit calls of all other service‐classes apart from service‐class
b.u. are reserved to benefit calls of all other service‐classes apart from service‐class ![]() . The application of the BR policy in the SRM is similar to that of the EMLM/BR, as the following example shows.
. The application of the BR policy in the SRM is similar to that of the EMLM/BR, as the following example shows.
Example 2.3
Consider Example 2.1 (![]() ) and apply the BR parameters
) and apply the BR parameters ![]() b.u. and
b.u. and ![]() b.u. to the first and second service‐class, respectively.
b.u. to the first and second service‐class, respectively.
- (a)Explain the anticipated effect of these BR parameters on the CBP of both service‐classes.
- (b)Find the total number of permissible states
 and those adjacent states where the LB is destroyed due to the BR policy (justify your answer). Draw the state transition diagram. (Hint: elaborate on Figure 2.3).
and those adjacent states where the LB is destroyed due to the BR policy (justify your answer). Draw the state transition diagram. (Hint: elaborate on Figure 2.3). - (c)Calculate the state probabilities
 and the corresponding values of
and the corresponding values of  (link occupancy distribution) based on the GB equations.
(link occupancy distribution) based on the GB equations. - (d)Calculate the CBP of both service‐classes.
- (a)Since
 , and
, and  , while
, while  and
and  , we have that
, we have that  . This means that the CBP of the first service‐class becomes equal to the probability of retry of the second service‐class. Because of these BR parameters, there are 3 blocking states of the first service‐class, that is, more than the blocking states of the second service‐class, (retry) calls of which eventually require 2 b.u. In other words, the CBP of the first service‐class under this BR policy becomes worse than the CBP of the second service‐class.
. This means that the CBP of the first service‐class becomes equal to the probability of retry of the second service‐class. Because of these BR parameters, there are 3 blocking states of the first service‐class, that is, more than the blocking states of the second service‐class, (retry) calls of which eventually require 2 b.u. In other words, the CBP of the first service‐class under this BR policy becomes worse than the CBP of the second service‐class. - (b)
Elaborating on Figure 2.3, we find that we have to exclude two states, namely states
 and
and  . So, the total number of permissible states, of the form
. So, the total number of permissible states, of the form  , is 14, shown in Figure 2.4 together with the state transition diagram. Due to the BR policy, the LB is destroyed between adjacent states: (0,0,2) – (1,0,2), (0,1,0) – (1,1,0), (1,0,1) – (2,0,1), (1,1,0) – (2,1,0), and (2,0,1) – (3,0,1). We comment on the first pair (similar justifications exist for the other pairs and thus they are omitted).
, is 14, shown in Figure 2.4 together with the state transition diagram. Due to the BR policy, the LB is destroyed between adjacent states: (0,0,2) – (1,0,2), (0,1,0) – (1,1,0), (1,0,1) – (2,0,1), (1,1,0) – (2,1,0), and (2,0,1) – (3,0,1). We comment on the first pair (similar justifications exist for the other pairs and thus they are omitted).
- States: (0,0,2) – (1,0,2). Assuming that the system state is (0,0,2) when a new call of service‐class 1 arrives to the system. In this state, the total occupied bandwidth is
 b.u. Thus, the call cannot be accepted in the system because the free b.u. is reserved for calls of service‐class 2 (or think that service‐class 1 sees the system with capacity,
b.u. Thus, the call cannot be accepted in the system because the free b.u. is reserved for calls of service‐class 2 (or think that service‐class 1 sees the system with capacity,  b.u.).
b.u.).
- States: (0,0,2) – (1,0,2). Assuming that the system state is (0,0,2) when a new call of service‐class 1 arrives to the system. In this state, the total occupied bandwidth is
- (c) Based on the GB in each state, we write 14 GB equations:
















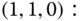











By replacing one GB equation, say (1,0,0), with the equation of the normalization condition
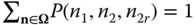 , the solution of the resultant linear system is:
, the solution of the resultant linear system is:













Based on the values of
 , we have:
, we have:


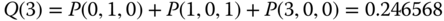


- (d) The CBP of service‐class 1 is given by:

The
 of service‐class 2 calls is given by:
of service‐class 2 calls is given by:
Finally, the CBP of service‐class 2 (calls with
 ), is given by:
), is given by:
We see that the BR policy has substantially increased
 (from 0.206923 in the SRM to 0.548536 in the SRM/BR) and as a result there is a decrease in
(from 0.206923 in the SRM to 0.548536 in the SRM/BR) and as a result there is a decrease in  (from 0.377639 in the SRM to 0.301968 in the SRM/BR).
(from 0.377639 in the SRM to 0.301968 in the SRM/BR).

Figure 2.4 The state space  (BR policy) and the state transition diagram (Example 2.3).
(BR policy) and the state transition diagram (Example 2.3).
2.2.2 The Analytical Model
2.2.2.1 Steady State Probabilities
To calculate the link occupancy distribution in the steady state of the SRM/BR, we prefer the Roberts method to the Stasiak–Glabowski method. The latter is more complex compared to the Roberts method and does not provide more accurate results (compared to simulation) in retry loss models and threshold loss models (see Section 2.6, below) [5].
Based on the Roberts method, ( 2.10) takes the form [ 4]:

where ![]() ,
, ![]() , when
, when ![]() (otherwise
(otherwise ![]() ),
), ![]() is given by (1.65) and, similarly,
is given by (1.65) and, similarly, ![]() by:
by:

2.2.2.2 CBP, Utilization, and Mean Number of In‐service Calls
Based on (2.18) and (2.19), we can calculate the following performance measures:
- The CBP of service‐class
 calls with
calls with  b.u.,
b.u.,  , via the following formula [ 4]:
(2.20)where
, via the following formula [ 4]:
(2.20)where
 is the normalization constant.
is the normalization constant. - The CBP of service‐class
 calls with
calls with  b.u.,
b.u.,  (i.e., the actual CBP of service‐class
(i.e., the actual CBP of service‐class  without retrials, or retry probability in case of service‐class
without retrials, or retry probability in case of service‐class  with retrials), can be determined via (1.66), while the conditional CBP of service‐class
with retrials), can be determined via (1.66), while the conditional CBP of service‐class  retry calls given that they have been blocked with their initial bandwidth requirement
retry calls given that they have been blocked with their initial bandwidth requirement  , via (2.13), while subtracting
, via (2.13), while subtracting  from
from  and from
and from  .
. - The link utilization,
 , is given by (1.54).
, is given by (1.54). - The mean number of service‐class
 calls with
calls with  b.u. in state
b.u. in state  ,
,  , is given by (1.67), while the mean number of service‐class
, is given by (1.67), while the mean number of service‐class 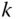 calls with
calls with  b.u. in state
b.u. in state  ,
,  , is given by:
(2.21)where
, is given by:
(2.21)where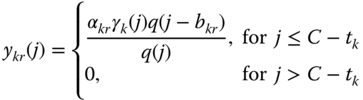
 when
when  (otherwise
(otherwise  ).
). - The mean number of in‐service calls of service‐class
 accepted in the system with
accepted in the system with  , is calculated by (2.16), while the mean number of in‐service calls of service‐class
, is calculated by (2.16), while the mean number of in‐service calls of service‐class  accepted in the system with
accepted in the system with  , by (2.17).
, by (2.17).
Example 2.4
In the system of Example 2.3 (![]() ):
):
- (a)Calculate the values of
 (link occupancy distribution) based on ( 2.18).
(link occupancy distribution) based on ( 2.18). - (b)Calculate the CBP of both service‐classes, including the retry probability. Compare with the exact results of Example 2.3.
- (a) To determine the state probability
 based on ( 2.18), we recursively calculate
based on ( 2.18), we recursively calculate  for
for  , starting with
, starting with  , while
, while  erl,
erl,  erl, and
erl, and  for
for  :
: 














The normalization constant is
 . Thus:
. Thus:





- As the following results reveal, the error introduced by the assumption of LB, the migration approximation, and the Roberts method is not significant, even in small SRM/BR examples.

(compare with the exact 0.548536) 
(due to the values of the BR parameters) 
(compare with the exact 0.301968)
Example 2.5
Consider a single link of capacity ![]() b.u. that accommodates calls of four different service‐classes with the following traffic characteristics:
b.u. that accommodates calls of four different service‐classes with the following traffic characteristics:
 ,
,  ,
,  ,
,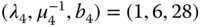 ,
,  , and
, and  .
.
That is, only calls of service‐class 4 have the ability to retry.
- (a)Present graphically the CBP of all service‐classes, including the retry probability and the conditional
 , as well as the link utilization, when assuming the SRM under the CS policy (no BR parameters). Compare the results with those obtained by the EMLM, assuming an increase of
, as well as the link utilization, when assuming the SRM under the CS policy (no BR parameters). Compare the results with those obtained by the EMLM, assuming an increase of  from 500 to 1000 b.u. in steps of 100 b.u. Provide simulation results for evaluation.
from 500 to 1000 b.u. in steps of 100 b.u. Provide simulation results for evaluation. - (b)Present graphically the equalized CBP of all service‐classes in the SRM/BR (i.e., under the BR policy) for the following set of BR parameters: Set 1
 b.u., which causes CBP equalization (the same increase of
b.u., which causes CBP equalization (the same increase of  , from 500 to 1000 b.u. in steps of 100 b.u., is assumed). For comparison, include the CBP obtained by the EMLM/BR while considering not only Set 1, but also the following set of BR parameters: Set 2
, from 500 to 1000 b.u. in steps of 100 b.u., is assumed). For comparison, include the CBP obtained by the EMLM/BR while considering not only Set 1, but also the following set of BR parameters: Set 2  .
. - (c)Comment on the results.
- Figure 2.5 presents the corresponding CBP of all service‐classes, including the retry probability and the conditional
 . Observe that
. Observe that  , since
, since  b.u. Because of this, we only present the values of
b.u. Because of this, we only present the values of  . In Table 2.1, we present the corresponding analytical and simulation CBP results for
. In Table 2.1, we present the corresponding analytical and simulation CBP results for  b.u. and
b.u. and  b.u. Simulation CBP results for the SRM are quite close to the analytical results, and therefore are not shown in Figure 2.5. Simulation results are based on SIMSCRIPT III [6], and are mean values of 12 runs with 95% confidence interval.
b.u. Simulation CBP results for the SRM are quite close to the analytical results, and therefore are not shown in Figure 2.5. Simulation results are based on SIMSCRIPT III [6], and are mean values of 12 runs with 95% confidence interval.
In Figure 2.6, we present the link utilization results for the EMLM and SRM; both models give almost the same results, a fact that is explained by the fact that the CBP decrease in service‐class 4 is accompanied by the CBP increase of the other service‐classes.
- Figure 2.7 presents the corresponding equalized CBP of all service‐classes for the SRM/BR and the EMLM/BR (set 1 and set 2). Simulation CBP results for the SRM/BR are quite close to the analytical results and, therefore, are omitted. As an example, we provide in Table 2.2 the corresponding analytical and simulation equalized CBP results for
 b.u. and
b.u. and  b.u.
b.u. - Apart from the fact that all CBP decrease when
 increases, we also see the following:
increases, we also see the following:
- According to Figure 2.5:
- The CBP of retry calls (i.e.,
 ) are much lower compared to the CBP obtained by the EMLM (i.e.,
) are much lower compared to the CBP obtained by the EMLM (i.e.,  ).
). - The fact that calls of service‐class 4 retry, increases the CBP of service‐classes 1, 2 and 3 in the SRM compared to the EMLM.
- The EMLM results fail to approximate the corresponding CBP results of the SRM.
- The CBP of retry calls (i.e.,
- Set 1 causes CBP equalization in the EMLM/BR among calls of the first three service‐classes, while Set 2 causes CBP equalization in the EMLM/BR of all service‐classes. According to Figure 2.7, the CBP obtained by the SRM/BR can be approximated by the EMLM/BR (Set 2), especially for high values of
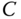 , while the CBP results of the EMLM/BR (Set 1) fail to approximate the corresponding results of the SRM/BR.
, while the CBP results of the EMLM/BR (Set 1) fail to approximate the corresponding results of the SRM/BR.
- According to Figure 2.5:
Table 2.1 CBP of Example 2.5 (SRM, ![]() b.u. and
b.u. and ![]() b.u.).
b.u.).
| CBP | Analytical results | Simulation results | Analytical results | Simulation results |
| 0.0479 | 0.0493 |
0.0004 | 0.0004 |
|
| 0.2997 | 0.2986 |
0.0031 | 0.0029 |
|
| 0.5089 | 0.5077 |
0.0063 | 0.0060 |
|
| 0.7360 | 0.7430 |
0.0128 | 0.0125 |
|
| 0.5089 | 0.5081 |
0.0063 | 0.0060 |
|
| 0.6914 | 0.6844 |
0.4955 | 0.4871 |
|
Table 2.2 CBP of Example 2.5 (SRM/BR, ![]() b.u. and
b.u. and ![]() b.u.).
b.u.).
| CBP | Analytical results | Simulation results | Analytical results | Simulation results |
| 0.3804 | 0.3825 |
0.00485 | 0.00485 |
|
| 0.3804 | 0.3826 |
0.00485 | 0.00486 |
|
| 0.3804 | 0.3824 |
0.00485 | 0.00485 |
|
| 0.3804 | 0.3825 |
0.00485 | 0.00487 |
|

Figure 2.5 CBP in the SRM and EMLM, for various values of  (Example 2.5).
(Example 2.5).

Figure 2.6 Link utilization in the SRM and EMLM (Example 2.5).

Figure 2.7 CBP in the SRM/BR and the EMLM/BR for various values of  (Example 2.5).
(Example 2.5).
2.3 The Multi‐Retry Model
2.3.1 The Service System
In the multi‐retry model (MRM), calls of service‐class ![]() can retry not only once, but several times, in order to be accepted in the system [ 1, 2]. Let
can retry not only once, but several times, in order to be accepted in the system [ 1, 2]. Let ![]() be the number of retrials for calls of service‐class
be the number of retrials for calls of service‐class ![]() , and assume that
, and assume that ![]() , where
, where ![]() is the required bandwidth of a service‐class
is the required bandwidth of a service‐class ![]() call in the
call in the ![]() retry,
retry, ![]() . Then a service‐class
. Then a service‐class ![]() call is accepted in the system with
call is accepted in the system with ![]() b.u. if
b.u. if ![]() . By definition,
. By definition, ![]() and
and ![]() .
.
Example 2.6
Consider a link of ![]() b.u. The link accommodates Poisson arriving calls of two service‐classes. Calls of service‐class 1 require
b.u. The link accommodates Poisson arriving calls of two service‐classes. Calls of service‐class 1 require ![]() b.u., while calls of service‐class 2 require
b.u., while calls of service‐class 2 require ![]() . Blocked calls of service‐class 2, in order to be accepted in the system, can immediately retry two times with
. Blocked calls of service‐class 2, in order to be accepted in the system, can immediately retry two times with ![]() b.u. and
b.u. and ![]() b.u. Let
b.u. Let ![]() calls/sec,
calls/sec, ![]() sec,
sec, ![]() sec, and
sec, and ![]() sec (in this example we do not assume that
sec (in this example we do not assume that ![]() ).
).
- (a)Find the total number of permissible states
 (state space
(state space  ) and draw the state transition diagram.
) and draw the state transition diagram. - (b)Calculate the state probabilities
 and the corresponding values of
and the corresponding values of  (link occupancy distribution) based on the GB equations.
(link occupancy distribution) based on the GB equations. - (c)Calculate the CBP of both service‐classes, including the retry probabilities and the link utilization.
- (d)Calculate the conditional CBP of service‐class 2 retry calls with
 given that they have been blocked with their initial bandwidth requirement,
given that they have been blocked with their initial bandwidth requirement,  .
.

Figure 2.8 The state space  (CS policy) and the state transition diagram (Example 2.6).
(CS policy) and the state transition diagram (Example 2.6).
- (a)The total number of permissible states, of the form
 , is 14. They are shown in Figure 2.8 together with the state transition diagram.
, is 14. They are shown in Figure 2.8 together with the state transition diagram. - (b) Based on Figure 2.8, the corresponding 14 GB equations are:




























By replacing the GB equation of (1,0,0,0) with the normalization condition
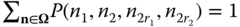 , the solution of this linear system is:
, the solution of this linear system is:













Based on the values of
 , we have:
, we have:
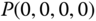
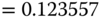










- (c) The CBP of service‐class 1 is given by:

The
 of service‐class 2 is given by:
of service‐class 2 is given by:
The
 of service‐class 2, is given by:
of service‐class 2, is given by:
The CBP of service‐class 2 is given by:

The link utilization is determined by:
 b.u.
b.u.Compare these results with the corresponding CBP and link utilization results in the case of the EMLM:
 b.u.
b.u. - (d) The conditional CBP of service‐class 2 retry calls with
 is given by:
is given by: 
2.3.2 The Analytical Model
2.3.2.1 Steady State Probabilities
Following the analysis of Section 2.1.2.1, we have to assume in the MRM the existence of both LB and the migration approximation. According to the migration approximation, the mean number of service‐class k calls in state ![]() ,
, ![]() , accepted with
, accepted with ![]() b.u., is negligible when
b.u., is negligible when ![]() , where
, where ![]() . This means that service‐class k calls with
. This means that service‐class k calls with ![]() are limited in the area
are limited in the area ![]() . Based on [1, 2], the unnormalized values of
. Based on [1, 2], the unnormalized values of ![]() can be determined by the following recursive formula:
can be determined by the following recursive formula:
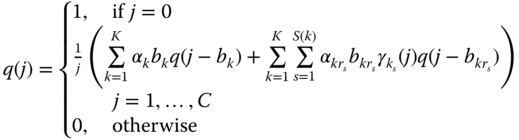
where ![]() when
when ![]() (otherwise
(otherwise ![]() ).
).
2.3.2.2 CBP, Utilization, and Mean Number of In‐service Calls
Having determined the unnormalized values of ![]() , we can determine the following performance measures:
, we can determine the following performance measures:
- The CBP of service‐class
 calls (with their last bandwidth requirement
calls (with their last bandwidth requirement  ),
),  , are determined as follows (if
, are determined as follows (if  is the normalization constant) [ 2]:
(2.23)
is the normalization constant) [ 2]:
(2.23)
- The
 of service‐class
of service‐class 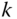 calls of
calls of  b.u.,
b.u.,  , is determined via (2.12), while the conditional probability of service‐class
, is determined via (2.12), while the conditional probability of service‐class  retry calls, requesting
retry calls, requesting  b.u. given that they have been blocked with their initial bandwidth requirement
b.u. given that they have been blocked with their initial bandwidth requirement  , is defined as:
(2.24)
, is defined as:
(2.24)
- The link utilization,
 , is given by (1.54).
, is given by (1.54). - The mean number of service‐class
 calls with
calls with  b.u. in state
b.u. in state  ,
,  , is given by (2.14), while the mean number of service‐class
, is given by (2.14), while the mean number of service‐class  calls with
calls with  b.u. in state
b.u. in state  ,
,  , is given by:
(2.25)where
, is given by:
(2.25)where
 when
when  (otherwise
(otherwise  ).
). - The mean number of in‐service calls of service‐class k accepted in the system with
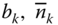 , is calculated by ( 2.16), while the mean number of in‐service calls of service‐class
, is calculated by ( 2.16), while the mean number of in‐service calls of service‐class  accepted in the system with
accepted in the system with  is determined by:
(2.26)
is determined by:
(2.26)
Example 2.7
In the system of Example 2.6 (![]() ):
):
- (a)Calculate the values of
 (link occupancy distribution) based on (2.22).
(link occupancy distribution) based on (2.22). - (b)Calculate the CBP of both service‐classes, including the retry probabilities, as well as the conditional
 .
. - (c)Repeat the previous calculations assuming that
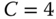 (instead of 3) b.u.
(instead of 3) b.u.
- (a) To determine the state probability
 based on ( 2.22), we recursively calculate
based on ( 2.22), we recursively calculate  for
for  , starting with
, starting with  , while
, while  erl,
erl,  erl,
erl, 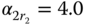 , and
, and  both for
both for  :
: 






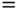



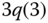




The normalization constant is
 . Thus:
. Thus:


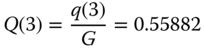
- (b)
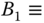 CBP of service‐class 1, and
CBP of service‐class 1, and  ,
, 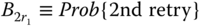 , and
, and  CBP of service‐class 2.
CBP of service‐class 2. 

(compare with the exact 0.545687) 

(compare with the exact 0.876443) 

(compare with the exact 0.725882) 

(compare with the exact 0.545687) 
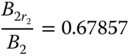
(compare with the exact 0.62262) In this very small example, the recursive formula ( 2.22) does not provide very good results compared to the exact results of Example 2.6. For an explanation, consider the effect of the migration approximation to the calculation of
 . The migration approximation assumes that service‐class 2 calls with
. The migration approximation assumes that service‐class 2 calls with  and
and  exist only when
exist only when 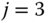 . However, we have already seen in Example 2.6 that
. However, we have already seen in Example 2.6 that  , when
, when  (states
(states  :
:  and
and  ), while
), while  , when
, when  (states
(states  ,
, 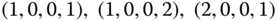 ).
). - (c) Since
 b.u., we have that
b.u., we have that  and
and  for
for  :
: 


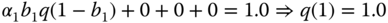
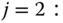












The normalization constant is
 . Thus:
. Thus:





(compare with the exact 0.416381) 
(compare with the exact 0.72426) 
(compare with the exact 0.59663) 
(compare with the exact 0.416381) 
(compare with the exact 0.57491) It is worth mentioning that the exact values require the knowledge of 25 steady state probabilities of the form
 . Of course, the increase of
. Of course, the increase of  results in a larger system (25 states vs 14 states when
results in a larger system (25 states vs 14 states when  ) in which the migration approximation introduces less error in the calculation of
) in which the migration approximation introduces less error in the calculation of 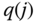 .
.
2.4 The Multi‐Retry Model under the BR Policy
2.4.1 The Service System
Obviously, in the MRM under the BR policy (MRM/BR), unlike the SRM/BR, blocked calls of service‐class ![]() can retry more than once to be connected in the system.
can retry more than once to be connected in the system.
Example 2.8
Consider the system of Example 2.6 (![]() ) under the BR policy with BR parameters
) under the BR policy with BR parameters ![]() b.u. and
b.u. and ![]() b.u. for the two service‐classes, respectively, so that
b.u. for the two service‐classes, respectively, so that ![]() . In that case, CBP of service‐class 1 calls is equalized with the
. In that case, CBP of service‐class 1 calls is equalized with the ![]() of calls of service‐class 2:
of calls of service‐class 2:
- (a)Find the total number of permissible states
 (state space
(state space  ) and draw the state transition diagram. (Hint: elaborate on Figure 2.8).
) and draw the state transition diagram. (Hint: elaborate on Figure 2.8). - (b)Calculate the state probabilities
 and the corresponding values of
and the corresponding values of 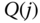 (link occupancy distribution) based on the GB equations.
(link occupancy distribution) based on the GB equations. - (c)Calculate the CBP of both service‐classes, including the probabilities of retry, and the link utilization.
- (a)The total number of permissible states, of the form
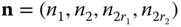 , is 7. They are shown in Figure 2.9 together with the state transition diagram.
, is 7. They are shown in Figure 2.9 together with the state transition diagram. - (b) Based on Figure 2.9, the corresponding 7 GB equations are:














By replacing the GB equation of
 with
with  , the solution of this linear system is:
, the solution of this linear system is: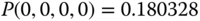






Based on the values of
 , we have:
, we have: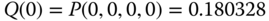



- (c) The CBP of service‐class 1 is given by:

(compare with 0.545687 in the MRM) The
 of service‐class 2 is given by:
of service‐class 2 is given by:
(compare with 0.876443 in the MRM) The
 of service‐class 2 is given by:
of service‐class 2 is given by:
(compare with 0.725882 in the MRM) The CBP of service‐class 2 is given by:

(compare with 0.545687 in the MRM) The link utilization is determined by:
 b.u.
b.u.(compare with 2.148 b.u. in the MRM)

Figure 2.9 The state space  (BR policy) and the state transition diagram (Example 2.8).
(BR policy) and the state transition diagram (Example 2.8).
2.4.2 The Analytical Model
2.4.2.1 Steady State Probabilities
Based on the Roberts method, we calculate the unnormalized link occupancy distribution in the steady state of the MRM/BR by modifying ( 2.22) as follows [ 4]:

where ![]() when
when ![]() (otherwise
(otherwise ![]() ), and
), and ![]() is given by (1.65) and, similarly,
is given by (1.65) and, similarly, ![]() by:
by:

2.4.2.2 CBP, Utilization, and Mean Number of In‐service Calls
Based on (2.27) and (2.28), we can determine the following performance measures:
- The CBP of service‐class
 calls with
calls with  b.u.,
b.u.,  , by the following formula [ 4]:
(2.29)where
, by the following formula [ 4]:
(2.29)where
 is the normalization constant.
is the normalization constant. - The CBP of service‐class
 calls with
calls with  b.u.,
b.u.,  , via (1.66).
, via (1.66). - The conditional CBP of service‐class
 retry calls, with
retry calls, with 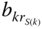 , given that they have been blocked with their initial bandwidth requirement
, given that they have been blocked with their initial bandwidth requirement  , via (2.24), while subtracting
, via (2.24), while subtracting  from
from  and from
and from  .
. - The link utilization,
 , via (1.54).
, via (1.54). - The mean number of service‐class
 calls with
calls with  b.u. in state
b.u. in state  ,
,  , via (1.67).
, via (1.67). - The mean number of service‐class
 calls with
calls with  b.u. in state
b.u. in state  ,
,  , via:
(2.30)where
, via:
(2.30)where
 when
when  (otherwise
(otherwise  ).
). - The mean number of in‐service calls of service‐class
 accepted with
accepted with  , via ( 2.16).
, via ( 2.16). - The mean number of in‐service calls of service‐class
 accepted in the system with
accepted in the system with  , via (2.26).
, via (2.26).
Example 2.9
In the system of Example 2.8 (![]() ):
):
- (a)Calculate the values of
 (link occupancy distribution) based on ( 2.27).
(link occupancy distribution) based on ( 2.27). - (b)Calculate the CBP of both service‐classes including the retry probabilities.
- (a) To determine the values of
 based on ( 2.27), we recursively calculate
based on ( 2.27), we recursively calculate  for
for  , starting with
, starting with  , while
, while  erl,
erl,  erl,
erl,  , and
, and  both for
both for  :
: 
 (due to the BR parameter
(due to the BR parameter  )
)

The normalization constant is
 . Thus,
. Thus,



- (b)
 CBP of service‐class 1
CBP of service‐class 1

 CBP of service‐class 2
CBP of service‐class 2
(compare with the exact 0.819672) 

(compare with the exact 0.606557) 
(compare with the exact 0.514754) In this very small example, ( 2.27) does not provide good results compared to the exact values of Example 2.8. This is because, the Roberts approximation (BR policy) and the migration approximation have additively introduced errors on the results. Fortunately, in larger examples (i.e., more realistic scenarios) the results provided by ( 2.27) are quite good compared to simulation [ 4]. To be more specific, in this example, the Roberts approximation ignores the transition from state
 to
to  for
for  . On the other hand, migration approximation ignores the existence of states
. On the other hand, migration approximation ignores the existence of states  and
and  , since
, since  and
and  when
when  .
.
Example 2.10
Consider a single link of capacity ![]() b.u. that accommodates calls of four different service‐classes with the following traffic characteristics:
b.u. that accommodates calls of four different service‐classes with the following traffic characteristics: ![]() ,
, ![]() , and
, and ![]() That is, only calls of service‐class 4 have the ability to retry four times; note that the product bandwidth by service time for service‐class 4 remains constant.
That is, only calls of service‐class 4 have the ability to retry four times; note that the product bandwidth by service time for service‐class 4 remains constant.
- (a)Present graphically the CBP of all service‐classes and compare them with those obtained by the EMLM and the SRM, assuming an increase of
 from 300 to 350 b.u. in steps of 10 b.u. For the SRM let
from 300 to 350 b.u. in steps of 10 b.u. For the SRM let  b.u. and
b.u. and  sec.
sec. - (b)Present graphically the equalized CBP of all service‐classes in the MRM/BR for the following set of BR parameters:
 , which causes CBP equalization (the same increase of
, which causes CBP equalization (the same increase of  , from 300 to 350 b.u. in steps of 10 b.u., is assumed). For comparison, include the equalized CBP obtained by the EMLM/BR, while considering the following set of BR parameters:
, from 300 to 350 b.u. in steps of 10 b.u., is assumed). For comparison, include the equalized CBP obtained by the EMLM/BR, while considering the following set of BR parameters:  .
. - (c)Comment on the results.
- Figure 2.10 presents the CBP of the first three service‐classes while Figure 2.11 presents the CBP of service‐class 4. Simulation CBP results for the MRM and the MRM/BR are quite close to the analytical results and therefore are omitted. As an example, we present in Table 2.3 the corresponding analytical and simulation CBP results for
 b.u. in the case of the MRM.
b.u. in the case of the MRM. - Figure 2.12 presents the CBP of the MRM/BR and the EMLM/BR for the various values of
 .
. - Apart from the fact that all CBP decrease when
 increases, we also see that:
increases, we also see that:
- According to Figures 2.10 and 2.11:
- The CBP of the first three service‐classes is better when calls of service‐class 4 retry only once (from
 to
to  b.u.) instead of four times. On the contrary, the CBP of service‐class 4 (not only
b.u.) instead of four times. On the contrary, the CBP of service‐class 4 (not only  but also
but also  ) is slightly better in the MRM than in the SRM. This behavior is expected since in the MRM blocked calls of service‐class 4 compete more times for the available link bandwidth than in the SRM.
) is slightly better in the MRM than in the SRM. This behavior is expected since in the MRM blocked calls of service‐class 4 compete more times for the available link bandwidth than in the SRM. - The EMLM results fail to approximate the corresponding CBP results of the MRM and SRM.
- The CBP of the first three service‐classes is better when calls of service‐class 4 retry only once (from
- According to Figure 2.12, the EMLM/BR results fail to approximate the corresponding results of the MRM/BR.
- According to Figures 2.10 and 2.11:
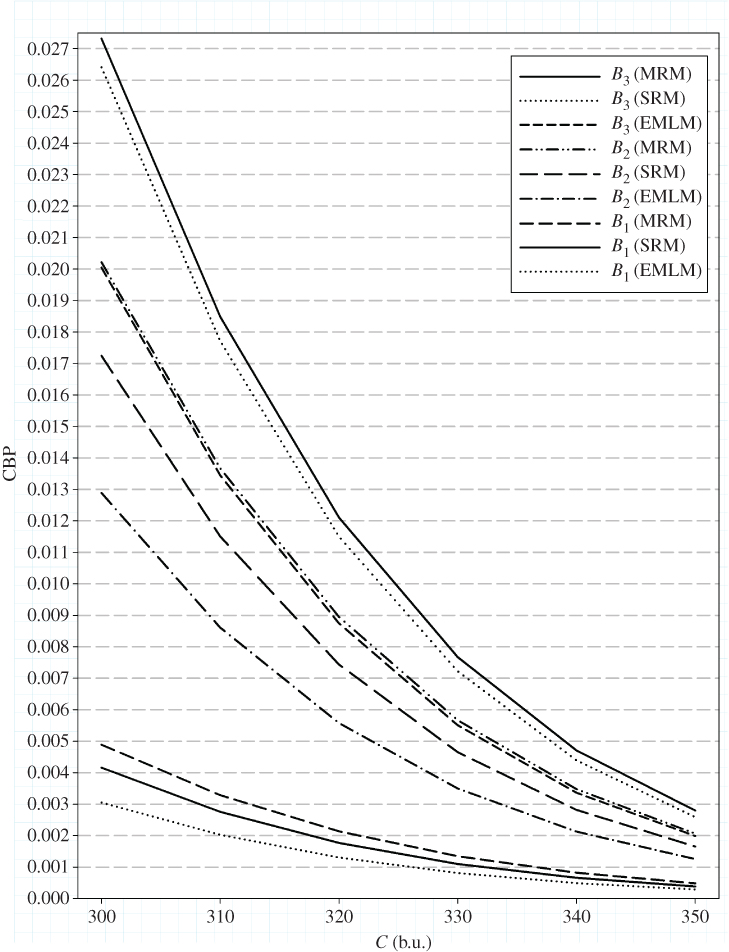
Figure 2.10 CBP of the first three service‐classes in the MRM, SRM, and EMLM for various values of  (Example 2.10) .
(Example 2.10) .

Figure 2.11 CBP of service‐class 4 in the MRM, SRM, and EMLM for various values of  (Example 2.10) .
(Example 2.10) .

Figure 2.12 Equalized CBP in the MRM/BR and EMLM/BR for various values of  (Example 2.10) .
(Example 2.10) .
Table 2.3 CBP of Example 2.10 (MRM, ![]() b.u.).
b.u.).
| CBP | Analytical results | Simulation results |
| 0.0049 | 0.0049 |
|
| 0.0202 | 0.0202 |
|
| 0.0273 | 0.0286 |
|
| 0.1161 | 0.1142 |
|
| 0.0349 | 0.0374 |
2.5 The Single‐Threshold Model
2.5.1 The Service System
In the single‐threshold model (STM), the requested b.u. and the corresponding service time of a new call are related to the value ![]() of the occupied link bandwidth (upon the new call arrival). More precisely, the following CAC is applied. When the value of
of the occupied link bandwidth (upon the new call arrival). More precisely, the following CAC is applied. When the value of ![]() is lower or equal to a threshold
is lower or equal to a threshold ![]() , then a new call of service‐class
, then a new call of service‐class ![]() is accepted in the system with its initial requirements
is accepted in the system with its initial requirements ![]() . Otherwise, if
. Otherwise, if ![]() , the call tries to be connected in the system with
, the call tries to be connected in the system with ![]() , where
, where ![]() and
and ![]() , so that the product bandwidth requirement by service time remains constant [ 1]. This means that, contrary to the SRM, a call does not have to be blocked in order to retry with lower bandwidth requirement. If the
, so that the product bandwidth requirement by service time remains constant [ 1]. This means that, contrary to the SRM, a call does not have to be blocked in order to retry with lower bandwidth requirement. If the ![]() b.u. are not available the call is blocked and lost.
b.u. are not available the call is blocked and lost.
The comparison of the STM with the SRM reveals the following basic similarities and differences:
- The steady state probabilities in the STM do not have a PFS, similar to the SRM (see Example 2.11). Thus, the unnormalized values of
 are determined via an approximate, but recursive, formula, as Section 2.5.2 shows.
are determined via an approximate, but recursive, formula, as Section 2.5.2 shows. - In the STM, the steady state vector of all in‐service calls of all service‐classes is
 . Although a similar vector is defined for the SRM, an SRM system and an STM system that accommodate the same service‐classes may have a different number of possible states, depending on the value of the threshold
. Although a similar vector is defined for the SRM, an SRM system and an STM system that accommodate the same service‐classes may have a different number of possible states, depending on the value of the threshold  .
. - The CBP results obtained in the STM are sensitive to the service time distribution [ 1].
- Setting the value of the threshold
 results in the same CBP for both the SRM and STM.
results in the same CBP for both the SRM and STM.
Example 2.11
Consider again Example 2.1 (![]() ) and let
) and let ![]() b.u.
b.u.
- (a)Assume that a new call of service‐class 2, having two possible bandwidth requirements
 , arrives to the system where the threshold principle is applied for CAC. Find the bandwidth requirement of that call depending on the value of
, arrives to the system where the threshold principle is applied for CAC. Find the bandwidth requirement of that call depending on the value of 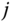 .
. - (b)Find the total number of permissible states
 , where
, where  is the number of service‐class 2 calls accepted in the system with
is the number of service‐class 2 calls accepted in the system with  b.u. Draw the state transition diagram.
b.u. Draw the state transition diagram. - (c)Find those adjacent states in which the LB is destroyed only due to the value of
 Compare with the SRM of Example 2.1.
Compare with the SRM of Example 2.1. - (d)Calculate the state probabilities
 and the corresponding values of
and the corresponding values of  (link occupancy distribution) based on the GB equations.
(link occupancy distribution) based on the GB equations. - (e)Calculate the CBP of both service‐classes and the link utilization.
- (f)Calculate the conditional CBP of service‐class 2 calls with
 , given that
, given that  .
.

Figure 2.13 The state space  (CS policy) and the state transition diagram (Example 2.11).
(CS policy) and the state transition diagram (Example 2.11).
- (a)If
 i.e.,
i.e.,  or 1 at the time of arrival, then the call is accepted in the system with
or 1 at the time of arrival, then the call is accepted in the system with  b.u. Otherwise, if
b.u. Otherwise, if  , the call requests
, the call requests  b.u.; then, the call is accepted if
b.u.; then, the call is accepted if  or 3, while it is blocked and lost if
or 3, while it is blocked and lost if  or 5.
or 5. - (b)There are 16 permissible states, of the form
 . The state space
. The state space  and the state transition diagram are shown in Figure 2.13.
and the state transition diagram are shown in Figure 2.13. - (c)
Due to the selected value of
 , LB is destroyed between adjacent states:
, LB is destroyed between adjacent states:
- (0,0,1) and (0,1,1): When a new call of service‐class 2 arrives in the system and the state is (0,0,1) (which means
 ) then the call is accepted with
) then the call is accepted with 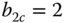 b.u. and the new state becomes (0,0,2) and not (0,1,1).
b.u. and the new state becomes (0,0,2) and not (0,1,1). - (2,0,0) and (2,1,0): Similarly, from state (2,0,0) the new state is (2,0,1), not (2,1,0).
- (0,0,1) and (0,1,1): When a new call of service‐class 2 arrives in the system and the state is (0,0,1) (which means
- (d) Based on the GB, the corresponding 16 GB equations are:




















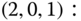











By replacing the GB equation of
 with the equation
with the equation  , the solution of this linear system is:
, the solution of this linear system is:















Based on the values of
 we have:
we have:





- (e) The CBP of service‐class 1 is given by:

(compare with 0.206923 in the SRM) The CBP of service‐class 2 is given by:

(compare with 0.377639 in the SRM) The link utilization is determined by:
 b.u.
b.u.(compare with 2.66 b.u. in the SRM) - (f) The conditional CBP of service‐class 2 calls with
 , given that
, given that  is:
is: 
2.5.2 The Analytical Model
2.5.2.1 Steady State Probabilities
Aiming at deriving a recursive formula for the calculation of ![]() (the unnormalized link occupancy distribution), we consider a link of capacity
(the unnormalized link occupancy distribution), we consider a link of capacity ![]() b.u. that accommodates calls of two service‐classes, whose initial bandwidth requirements are
b.u. that accommodates calls of two service‐classes, whose initial bandwidth requirements are ![]() and
and ![]() b.u., respectively. Calls of each service‐class arrive in the link according to a Poisson process with means
b.u., respectively. Calls of each service‐class arrive in the link according to a Poisson process with means ![]() and
and ![]() , and have exponentially distributed service times with means
, and have exponentially distributed service times with means ![]() and
and ![]() , respectively. If
, respectively. If ![]() upon the arrival of a service‐class 2 call, then this call requests from the system
upon the arrival of a service‐class 2 call, then this call requests from the system ![]() and
and ![]() . No such option is considered for calls of service‐class 1.
. No such option is considered for calls of service‐class 1.
Although the STM does not have a PFS, we assume that the LB equation (1.51) does hold for calls of service‐class 1, for ![]() :
:
For calls of service‐class 2, we assume the existence of LB between adjacent states that can be expressed as follows [ 2]:
where ![]() is the mean number of service‐class 2 calls with
is the mean number of service‐class 2 calls with ![]() in state
in state ![]() .
.
Equations (2.31)–(2.33) lead to the following system of equations [ 2]:
For (2.34), the following approximation is adopted: the value of ![]() in state
in state ![]() is negligible when
is negligible when ![]() . This approximation is similar to the migration approximation used in the SRM. For (2.36), the following approximation is applied: the value of
. This approximation is similar to the migration approximation used in the SRM. For (2.36), the following approximation is applied: the value of ![]() in state
in state ![]() is negligible when
is negligible when ![]() . This approximation is named the upward migration approximation and is different from the migration approximation since it considers negligible the population of calls with their initial bandwidth requirement [ 2]. The error introduced by the upward migration approximation in the calculation of
. This approximation is named the upward migration approximation and is different from the migration approximation since it considers negligible the population of calls with their initial bandwidth requirement [ 2]. The error introduced by the upward migration approximation in the calculation of ![]() can be higher than the corresponding error introduced by the migration approximation of the SRM, especially when the offered traffic‐load is light. In that case, it is highly probable that calls are accepted in the system with their initial bandwidth requirement [2].
can be higher than the corresponding error introduced by the migration approximation of the SRM, especially when the offered traffic‐load is light. In that case, it is highly probable that calls are accepted in the system with their initial bandwidth requirement [2].
Based on the above‐mentioned approximations, we have (for ![]() ):
):
where  ,
,  , and
, and ![]() .
.
Note that in (2.37), ![]() expresses the upward migration approximation and
expresses the upward migration approximation and ![]() expresses the migration approximation.
expresses the migration approximation.
In the general case of ![]() service‐classes, the approximate but recursive formula for
service‐classes, the approximate but recursive formula for ![]() is the following [ 2]:
is the following [ 2]:

where  ,
,  and
and ![]() .
.
2.5.2.2 CBP, Utilization, and Mean Number of In‐service Calls
Having determined the unnormalized values of ![]() , we can calculate the following performance measures:
, we can calculate the following performance measures:
- The CBP of service‐class
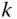 calls with
calls with  b.u.,
b.u.,  , via the following formula (if
, via the following formula (if  is the normalization constant) [ 2]:
(2.39)
is the normalization constant) [ 2]:
(2.39)
- The CBP of service‐class k calls with
 b.u. (assuming that they have no option for
b.u. (assuming that they have no option for  ),
),  , via ( 2.12).
, via ( 2.12). - The conditional CBP of service‐class
 calls with
calls with  given that
given that  , via:
(2.40)
, via:
(2.40)
Note that if
 , then (2.40) is identical to ( 2.13) of the SRM.
, then (2.40) is identical to ( 2.13) of the SRM. - The link utilization,
 , via (1.54).
, via (1.54). - The mean number of service‐class
 calls with
calls with  b.u. in state
b.u. in state  , via:
(2.41)
, via:
(2.41)
- The mean number of service‐class
 calls with
calls with  b.u. in state
b.u. in state  , via:
(2.42)
, via:
(2.42)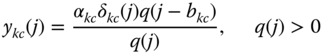
- The mean number of in‐service calls of service‐class k accepted in the system with
 ,
,  , via ( 2.16).
, via ( 2.16). - The mean number of in‐service calls of service‐class k accepted in the system with
 , via:
(2.43)
, via:
(2.43)
Example 2.12
In the system of Example 2.11 (![]() ):
):
- (a)Calculate the values of
 (link occupancy distribution) based on (2.38).
(link occupancy distribution) based on (2.38). - (b)Calculate the CBP of both service‐classes including the conditional
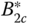 .
.
- (a) To determine the values of
 based on ( 2.38), we recursively calculate
based on ( 2.38), we recursively calculate  for
for  , starting with
, starting with  , while
, while  erl,
erl,  erl,
erl,  for
for  , and
, and  for
for  :
: 














The normalization constant is
 . Thus:
. Thus:





- (b) CBP and conditional

 (compare with the exact 0.165955)
(compare with the exact 0.165955)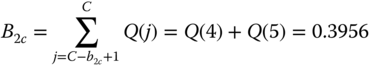 (compare with the exact 0.382997)
(compare with the exact 0.382997) (compare with the exact 0.53779)
(compare with the exact 0.53779)It is apparent that the error of the results in this small STM example is higher compared to the corresponding SRM example. This is due to the fact that in addition to the LB assumption and the migration approximation, which hold in the SRM, the upward migration approximation is introduced to the STM.
2.6 The Single‐Threshold Model under the BR Policy
2.6.1 The Service System
In the STM under the BR policy (STM/BR), ![]() b.u. are reserved to benefit calls of all other service‐classes apart from service‐class
b.u. are reserved to benefit calls of all other service‐classes apart from service‐class ![]() . The application of the BR policy in the STM is similar to that of the SRM/BR as the following example shows.
. The application of the BR policy in the STM is similar to that of the SRM/BR as the following example shows.
Example 2.13
Consider Example 2.3 (![]() ) and let
) and let ![]() b.u. This means that calls of service‐class 2 are accepted in the system with
b.u. This means that calls of service‐class 2 are accepted in the system with ![]() b.u. whenever
b.u. whenever ![]() .
.
- (a)Find the total number of permissible states
 (state space
(state space  ) and draw the state transition diagram. (Hint: elaborate on Figure 2.13).
) and draw the state transition diagram. (Hint: elaborate on Figure 2.13). - (b)Calculate the state probabilities
 and the corresponding values of
and the corresponding values of  (link occupancy distribution) based on the GB equations.
(link occupancy distribution) based on the GB equations. - (c)Calculate the CBP of both service‐classes.

Figure 2.14 The state space  (BR policy) and the state transition diagram (Example 2.13).
(BR policy) and the state transition diagram (Example 2.13).
- (a)Elaborating on Figure 2.13, we find that we have to exclude three states, namely the states (4,0,0), (5,0,0), and (2,1,0). Compared to the SRM/BR in Example 2.3 (Figure 2.4), we see that in this STM/BR example, state (2,1,0) is not a permissible state because it is accessible neither from state (1,1,0) due to the BR policy, nor from state (2,0,0) due to the threshold
 . States (4,0,0) and (5,0,0) are not permissible due to the BR policy. So, the total number of permissible states, of the form
. States (4,0,0) and (5,0,0) are not permissible due to the BR policy. So, the total number of permissible states, of the form  , is 13. They are shown in Figure 2.14 together with the state transition diagram.
, is 13. They are shown in Figure 2.14 together with the state transition diagram. - (b) Based on the GB in each state, we write 13 GB equations:



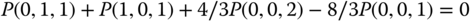






















By replacing the GB equation of (1,0,0) with the equation
 , the solution of this linear system is:
, the solution of this linear system is: 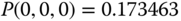
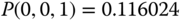


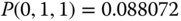








Based on the values of
 , we have:
, we have:

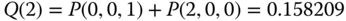



- (c) The CBP of service‐class 1 is given by:

(compare with 0.548536 in the SRM/BR) Finally, the CBP of service‐class 2 is given by:

(compare with 0.301968 in the SRM/BR)
2.6.2 The Analytical Model
2.6.2.1 Steady State Probabilities
Similar to the SRM/BR, we adopt the Roberts method for the calculation of ![]() in the STM/BR.
in the STM/BR.
Based on the Roberts method, ( 2.38) takes the form [ 4]:

where  ,
,  ,
, ![]() ,
, ![]() is given by (1.65), and
is given by (1.65), and

2.6.2.2 CBP, Utilization, and Mean Number of In‐service Calls
Based on (2.44) and (2.45), we can determine the following performance measures:
- The CBP of service‐class
 calls with
calls with  b.u.,
b.u.,  , via the formula [ 4]:
(2.46)where
, via the formula [ 4]:
(2.46)where
 is the normalization constant.
is the normalization constant. - The CBP of service‐class k calls with
 b.u.,
b.u.,  , via (1.66).
, via (1.66). - The conditional CBP of service‐class k calls with
 given that
given that  ,
,  , via ( 2.40), while subtracting the BR parameter
, via ( 2.40), while subtracting the BR parameter  from
from  .
. - The link utilization,
 , via (1.54).
, via (1.54). - The mean number of service‐class k calls with
 b.u. in state
b.u. in state 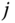 ,
,  , via:
(2.47)
, via:
(2.47)

- The mean number of service‐class k calls with
 b.u. in state
b.u. in state  ,
,  , via:
(2.48)where
, via:
(2.48)where
 .
. - The mean number of in‐service calls of service‐class k accepted in the system with
 , via ( 2.16).
, via ( 2.16). - The mean number of in‐service calls of service‐class k accepted in the system with
 , via (2.43).
, via (2.43).
Example 2.14
In the system of Example 2.13 (![]() ):
):
- (a)Calculate the values of
 (link occupancy distribution) based on ( 2.44).
(link occupancy distribution) based on ( 2.44). - (b)Calculate the CBP of both service‐classes including the conditional
 .
.
- (a) To determine the state probability
 based on ( 2.44) (the unnormalized link occupancy distribution), we recursively calculate
based on ( 2.44) (the unnormalized link occupancy distribution), we recursively calculate  for
for  , starting with
, starting with  , while
, while  erl,
erl,  erl,
erl,  for
for  , and
, and  for
for  :
: 














The normalization constant is
 . Thus:
. Thus:


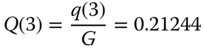


 (compare with the exact 0.545538)
(compare with the exact 0.545538) (compare with the exact 0.31399)
(compare with the exact 0.31399) (compare with the exact 0.44617)
(compare with the exact 0.44617)It is apparent that in this small STM/BR example the error introduced by the assumption of LB, the migration approximation, the upward migration approximation, and the introduction of the BR policy via the Roberts method is high, especially for
 .
.
Example 2.15
Consider a single link of capacity ![]() b.u. that accommodates calls of four different service‐classes with the following traffic characteristics:
b.u. that accommodates calls of four different service‐classes with the following traffic characteristics: ![]() ,
, ![]() ,
, ![]() ,
, ![]() ,
, ![]() , and
, and ![]() .
.
- (a)Present graphically the CBP of all service‐classes, including the conditional
 , for the STM under the CS policy (no BR parameters), when considering two different values of threshold,
, for the STM under the CS policy (no BR parameters), when considering two different values of threshold,  and
and  . Compare the results with those obtained by the SRM in Example 2.5 (or by the STM when
. Compare the results with those obtained by the SRM in Example 2.5 (or by the STM when  ), assuming an increase of
), assuming an increase of  from 500 to 1000 b.u. in steps of 100 b.u. Provide simulation results for evaluation.
from 500 to 1000 b.u. in steps of 100 b.u. Provide simulation results for evaluation. - (b)Present graphically the equalized CBP of all service‐classes, in the STM/BR, for the following BR parameters:
 , and
, and  b.u., which cause CBP equalization (the same increase of
b.u., which cause CBP equalization (the same increase of  , from 500 to 1000 b.u., is assumed). Consider both threshold values,
, from 500 to 1000 b.u., is assumed). Consider both threshold values,  and
and  .
.
- (a) Figure 2.15 presents in descending order the analytical CBP of service‐classes 1, 2 and 3, 4 (at the RHS and LHS, respectively). Simulation CBP results for the STM are close to the analytical results, especially when
 b.u., and therefore are not included in the figure. As an example, we present in Tables 2.4 and 2.5 the corresponding analytical and simulation CBP results, when
b.u., and therefore are not included in the figure. As an example, we present in Tables 2.4 and 2.5 the corresponding analytical and simulation CBP results, when  and
and  , respectively, for
, respectively, for  and
and  b.u. Simulation results are based on SIMSCRIPT III [ 6] and are mean values of 12 runs with 95% confidence interval. Note that in the case of
b.u. Simulation results are based on SIMSCRIPT III [ 6] and are mean values of 12 runs with 95% confidence interval. Note that in the case of  b.u., the offered traffic‐load is light and there is a difference between analytical and simulation results. This is because calls of service‐class 4 are mainly accepted in the system with their initial bandwidth requirement, a fact that is not taken into account in ( 2.38) due to the upward migration approximation.
b.u., the offered traffic‐load is light and there is a difference between analytical and simulation results. This is because calls of service‐class 4 are mainly accepted in the system with their initial bandwidth requirement, a fact that is not taken into account in ( 2.38) due to the upward migration approximation.
Based on Figure 2.15, we see that the increase of
 results in the substantial decrease of
results in the substantial decrease of  and a minor decrease in the CBP of the first three service‐classes. This was anticipated since calls of service‐class 4 use the
and a minor decrease in the CBP of the first three service‐classes. This was anticipated since calls of service‐class 4 use the 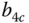 requirement more frequently compared to the SRM.
requirement more frequently compared to the SRM. - (b)Figure 2.16 presents the corresponding equalized CBP of all service‐classes for the STM/BR. For comparison we include the corresponding results of the SRM/BR. Simulation and analytical equalized CBP results are presented in Table 2.6 for
 , or
, or  b.u., and
b.u., and  . According to Figure 2.16, we see that (i) the equalized CBP decreases as
. According to Figure 2.16, we see that (i) the equalized CBP decreases as  increases and (ii) reducing the threshold
increases and (ii) reducing the threshold  results in the decrease (although slight) in the equalized CBP.
results in the decrease (although slight) in the equalized CBP.
Figure 2.15 Left: CBP of service‐classes 1, 2 in the STM and SRM versus various values of  . Right: The corresponding graphs for service‐classes 3, 4 (Example 2.15).
. Right: The corresponding graphs for service‐classes 3, 4 (Example 2.15).
Table 2.4 CBP of Example 2.15 (STM, ![]() or
or ![]() b.u., and
b.u., and ![]() ).
).
| CBP | Analytical results | Simulation results | Analytical results | Simulation results |
| 0.0474 | 0.0479 |
0.0003 | 0.00026 |
|
| 0.2953 | 0.2948 |
0.0025 | 0.0019 |
|
| 0.5086 | 0.5074 |
0.0054 | 0.0042 |
|
| 0.5361 | 0.5302 |
0.1579 | 0.1363 |
|
Table 2.5 CBP of Example 2.15 (STM, ![]() or
or ![]() b.u., and
b.u., and ![]() ).
).
| CBP | Analytical results | Simulation results | Analytical results | Simulation results |
| 0.0475 | 0.0480 |
0.0003 | 0.00017 |
|
| 0.2949 | 0.2948 |
0.0021 | 0.00137 |
|
| 0.5082 | 0.5074 |
0.0047 | 0.00297 |
|
| 0.5124 | 0.5113 |
0.0702 | 0.0511 |
|
Table 2.6 CBP of Example 2.15 (STM/BR, ![]() or
or ![]() b.u., and
b.u., and ![]() ).
).
| CBP | Analytical results | Simulation results | Analytical results | Simulation results |
| 0.3783 | 0.3799 |
0.00410 | 0.00332 |
|
| 0.3783 | 0.3799 |
0.00410 | 0.00333 |
|
| 0.3783 | 0.3799 |
0.00410 | 0.00332 |
|
| 0.3783 | 0.3799 |
0.00410 | 0.00333 |
|

Figure 2.16 CBP in the STM/BR and SRM/BR versus  and two values of
and two values of  (Example 2.15).
(Example 2.15).
2.7 The Multi‐Threshold Model
2.7.1 The Service System
In the multi‐threshold model (MTM), there exist ![]() different thresholds which are common to all service‐classes [ 1, 2]. A call of service‐class
different thresholds which are common to all service‐classes [ 1, 2]. A call of service‐class ![]() with initial requirements
with initial requirements ![]() can use, depending on the occupied link bandwidth, one of the
can use, depending on the occupied link bandwidth, one of the ![]() requirements
requirements ![]() , where the pair
, where the pair ![]() is used when
is used when ![]() (where
(where ![]() . The maximum possible threshold is
. The maximum possible threshold is ![]() , while
, while ![]() . As far as the bandwidth requirements of a service‐class
. As far as the bandwidth requirements of a service‐class ![]() call are concerned, we assume that they decrease as
call are concerned, we assume that they decrease as ![]() increases, i.e.,
increases, i.e., ![]() , while by definition
, while by definition ![]() (see Figure 2.17).
(see Figure 2.17).

Figure 2.17 The MTM principle of operation.
2.7.2 The Analytical Model
2.7.2.1 Steady State Probabilities
To describe the MTM in steady state, the following LB equations are considered:

and

where ![]() denotes the mean number of service‐class
denotes the mean number of service‐class ![]() calls, with
calls, with ![]() , in state
, in state ![]() .
.
Similar to the analysis of the STM and based on (2.49) and (2.50), we have the following recursive formula for the calculation of ![]() [ 1, 2]:
[ 1, 2]:

where 
 and
and ![]() .
.
Note that in (2.51), ![]() expresses the upward migration approximation, while
expresses the upward migration approximation, while ![]() expresses the migration approximation.
expresses the migration approximation.
2.7.2.2 CBP, Utilization, and Mean Number of In‐service Calls
Based on ( 2.51), we can determine the following performance measures:
- The CBP of service‐class
 calls with
calls with  b.u.,
b.u.,  , via the formula [ 2]:
(2.52)where
, via the formula [ 2]:
(2.52)where
 is the normalization constant.
is the normalization constant. - The CBP of service‐class
 calls with
calls with  b.u.,
b.u.,  , via (1.66).
, via (1.66). - The conditional CBP of service‐class
 calls with
calls with  given that
given that 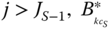 , via the formula:
(2.53)
, via the formula:
(2.53)
- The link utilization,
 , via (1.54).
, via (1.54). - The mean number of service‐class
 calls with
calls with 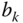 b.u. in state
b.u. in state  , via:
(2.54)where
, via:
(2.54)where

- The mean number of service‐class
 calls with
calls with 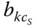 b.u. in state
b.u. in state  , via:
(2.55)where
, via:
(2.55)where
 .
. - The mean number of in‐service calls of service‐class
 accepted in the system with
accepted in the system with  , via ( 2.16).
, via ( 2.16). - The mean number of in‐service calls of service‐class
 accepted in the system with
accepted in the system with  , via:
(2.56)
, via:
(2.56)
2.8 The Multi‐Threshold Model under the BR Policy
2.8.1 The Service System
In the MTM under the BR policy (MTM/BR), ![]() b.u. are reserved to benefit calls of all other service‐classes apart from service‐class
b.u. are reserved to benefit calls of all other service‐classes apart from service‐class ![]() . The application of the BR policy in the MTM is similar to that of the MRM/BR.
. The application of the BR policy in the MTM is similar to that of the MRM/BR.
2.8.2 The Analytical Model
2.8.2.1 Steady State Probabilities
Similar to the MRM/BR, we adopt the Roberts method for the calculation of the unnormalized link occupancy distribution ![]() in the MTM/ BR.
in the MTM/ BR.
Based on the Roberts method, ( 2.51) takes the form [ 4]:

where 
 ,
, ![]() , and
, and

2.8.2.2 CBP, Utilization, and Mean Number of In‐service Calls
Based on (2.57) and (2.58), we can determine the following performance measures:
- The CBP of service‐class k calls with
 b.u.,
b.u.,  , via the formula [ 4]:
(2.59)where
, via the formula [ 4]:
(2.59)where
 is the normalization constant.
is the normalization constant. - The CBP of service‐class
 calls with
calls with  b.u.,
b.u.,  , via (1.66).
, via (1.66). - The conditional CBP of service‐class
 calls with
calls with  given that
given that  , via the formula:
(2.60)
, via the formula:
(2.60)
- The link utilization,
 , via (1.54).
, via (1.54). - The mean number of service‐class
 calls with
calls with  b.u. in state
b.u. in state  , via:
(2.61)where
, via:
(2.61)where

- The mean number of service‐class
 calls with
calls with  b.u. in state
b.u. in state  , via:
(2.62)where
, via:
(2.62)where
 .
. - The mean number of in‐service calls of service‐class
 accepted in the system with
accepted in the system with  , via ( 2.16).
, via ( 2.16). - The mean number of in‐service calls of service‐class
 accepted in the system with
accepted in the system with  , via (2.56).
, via (2.56).
Example 2.16
Consider again Example 2.10 (![]()
![]()
![]() , and
, and ![]() ). Calls of service‐class 4 reduce their bandwidth four times according to the following 12 sets of thresholds:
). Calls of service‐class 4 reduce their bandwidth four times according to the following 12 sets of thresholds:
| Set 1: | |
| Set 2: | |
| Set 3: | |
| Set 12: |
In the case of Set 1 the same CBP results are anticipated by the MRM and the MTM.
- Present graphically the CBP of all service‐classes
 for all sets of thresholds and
for all sets of thresholds and  b.u.
b.u. - Present graphically the equalized CBP of all service‐classes in the MTM/BR for all sets of thresholds and the following set of BR parameters:
 , which causes CBP equalization. Assume three values of
, which causes CBP equalization. Assume three values of  : 300, 310, and 320 b.u.
: 300, 310, and 320 b.u.
- In the LHS of Figure 2.18, we present the CBP of the first three service‐classes and in the RHS of the same figure the conditional CBP of service‐class 4. There, we see that decreasing the values of the thresholds results in the CBP decrease of all service‐classes. This is because calls of service‐class 4 use their initial bandwidth requirement less frequently,
 b.u.
b.u. - In Figure 2.19, we present the equalized CBP of all service‐classes. We see that decreasing the values of thresholds or increasing the capacity of the system results in the CBP decrease of all service‐classes. Note that when
 b.u., the MTM/BR results obtained for Set 1 coincide with the MRM/BR (Figure 2.12).
b.u., the MTM/BR results obtained for Set 1 coincide with the MRM/BR (Figure 2.12).

Figure 2.18 Left: CBP of service‐classes 1, 2, and 3 versus the sets of thresholds. Right: Conditional CBP of service‐class 4 versus the sets of thresholds (MTM) (Example 2.16).

Figure 2.19 Equalized CBP of all service‐classes versus the sets of thresholds (MTM/BR) (Example 2.16).
2.9 The Connection Dependent Threshold Model
2.9.1 The Service System
In the connection dependent threshold model (CDTM), bandwidth and service time requests depend on the total number ![]() of occupied b.u. of a link of capacity
of occupied b.u. of a link of capacity ![]() , as in the MTM. The only difference with the MTM is that different service‐classes may have different sets of thresholds. Specifically, we consider
, as in the MTM. The only difference with the MTM is that different service‐classes may have different sets of thresholds. Specifically, we consider ![]() service‐classes of Poisson arriving calls with mean arrival rates
service‐classes of Poisson arriving calls with mean arrival rates ![]() that require
that require ![]() b.u. per call and a mean service time
b.u. per call and a mean service time ![]() , exponentially distributed. Calls compete for the available bandwidth under the CS policy. The offered traffic‐load of calls of service‐class
, exponentially distributed. Calls compete for the available bandwidth under the CS policy. The offered traffic‐load of calls of service‐class ![]() is
is ![]() . Let
. Let ![]() , and
, and ![]() . Each arriving call of a service‐class
. Each arriving call of a service‐class ![]() may have
may have ![]() bandwidth and service‐time requirements, that is, one initial requirement with values
bandwidth and service‐time requirements, that is, one initial requirement with values ![]() and
and ![]() more requirements with values
more requirements with values ![]() , where
, where ![]() and
and ![]() , and
, and ![]() . The pair
. The pair ![]() is used when
is used when ![]() , where
, where ![]() and
and ![]() are two successive thresholds of service‐class
are two successive thresholds of service‐class ![]() , while
, while ![]() ; the highest possible threshold (other than
; the highest possible threshold (other than ![]() ) is
) is ![]() (see Figure 2.20). By convention,
(see Figure 2.20). By convention, ![]() and
and ![]() , while the pair
, while the pair ![]() is used when
is used when ![]() .
.

Figure 2.20 The CDTM principle of operation.
Example 2.17
As an application example of the CDTM, imagine a CPU (server in a LAN) exclusively devoted to video file format conversion (e.g., from AVI to DVD). The CPU collaborates with a CAC, which either accepts or denies conversion requests, depending on the current status and the processing capacity of the CPU (let it be 60 video frames/sec). We consider conversion requests for movies (service‐class 1), video clips (service‐class 2), and advertisements (short video clips, service‐class 3). Requests for movies are processed with a conversion rate of either 40 or 30 frames/sec, while requests for video clips are processed with a conversion rate of either 20 or 10 frames/sec, depending on the current CPU status, as Figure 2.21 shows. In Figure 2.21, the CPU together with the CAC is equivalent to a link of capacity ![]() b.u., considering that 1 b.u.= 10 frames/sec. Requests for advertisements are processed with a fixed conversion rate of 10 frames/sec. In order to determine the percentage of denied conversion requests per service‐class, we apply the CDTM with the following traffic and bandwidth requirements for each service‐class:
b.u., considering that 1 b.u.= 10 frames/sec. Requests for advertisements are processed with a fixed conversion rate of 10 frames/sec. In order to determine the percentage of denied conversion requests per service‐class, we apply the CDTM with the following traffic and bandwidth requirements for each service‐class: ![]() , and
, and ![]() , respectively. Furthermore,
, respectively. Furthermore, ![]() b.u.,
b.u., ![]() , and
, and ![]() , so that
, so that ![]() and
and ![]() .
.

Figure 2.21 The service system (Example 2.17).
2.9.2 The Analytical Model
2.9.2.1 Steady State Probabilities
Similar to the MTM, the CDTM has no PFS. To describe the CDTM in steady state, the following LB equations are assumed:


where ![]() denotes the mean number of service‐class
denotes the mean number of service‐class ![]() calls, with
calls, with ![]() , in state
, in state ![]() .
.
Formulas (2.63) and (2.64) are graphically presented in Figure 2.22.
Similar to the analysis of the MTM and based on ( 2.63) and ( 2.64), we have the following recursive formula for the calculation of ![]() [ 4]:
[ 4]:

where 
 and
and ![]() .
.
As a summary, in order to derive (2.65), the following assumptions (approximations) are necessary:
- (i) The assumption that the LB equations ( 2.63) and ( 2.64) do exist. This is the first source of error in ( 2.65).
- (ii)
 is assumed negligible (i.e., zero) outside
is assumed negligible (i.e., zero) outside  . This assumption is the migration approximation, and we name the state space in which
. This assumption is the migration approximation, and we name the state space in which  , the migration space
, the migration space  . Let us recall that in the migration space, calls accepted in the system with other than the maximum bandwidth requirement are negligible. This assumption is the second source of error in ( 2.65) and is represented by the variable
. Let us recall that in the migration space, calls accepted in the system with other than the maximum bandwidth requirement are negligible. This assumption is the second source of error in ( 2.65) and is represented by the variable  .
. - (iii)
 is assumed negligible (i.e., zero), if
is assumed negligible (i.e., zero), if  and
and  . This is the upward migration approximation, and we name the state space in which
. This is the upward migration approximation, and we name the state space in which  , the upward migration space. Let us recall that in the upward migration space, calls accepted in the system with their maximum bandwidth are negligible. This assumption is the third source of error in ( 2.65) and is represented by the variable
, the upward migration space. Let us recall that in the upward migration space, calls accepted in the system with their maximum bandwidth are negligible. This assumption is the third source of error in ( 2.65) and is represented by the variable  .
.
Note that in both (ii) and (iii), the values of ![]() and
and ![]() may not be negligible in the corresponding migration and upward migration spaces, respectively (see Example 2.18). The determination of these values can improve the accuracy of the CDTM, compared to simulation, but is beyond the scope of this book. The reader may refer to [7,8].
may not be negligible in the corresponding migration and upward migration spaces, respectively (see Example 2.18). The determination of these values can improve the accuracy of the CDTM, compared to simulation, but is beyond the scope of this book. The reader may refer to [7,8].
Example 2.18
Consider again Example 2.17 (![]() ). Calls of service‐class 1 behave as in the SRM due to the associated threshold parameter
). Calls of service‐class 1 behave as in the SRM due to the associated threshold parameter ![]() . Calls of service‐class 2 behave as in the STM due to the associated threshold parameter
. Calls of service‐class 2 behave as in the STM due to the associated threshold parameter ![]() . A migration space exists for calls of service‐class 1, while both migration and upward migration spaces exist for calls of service‐class 2. More precisely:
. A migration space exists for calls of service‐class 1, while both migration and upward migration spaces exist for calls of service‐class 2. More precisely:
 for
for  (migration space of service‐class 1)
(migration space of service‐class 1)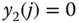 for
for  (upward migration space of service‐class 2)
(upward migration space of service‐class 2) for
for  (migration space of service‐class 2).
(migration space of service‐class 2).
In reality, however, the values of ![]() and
and ![]() may not be negligible. To illustrate this statement as well as the migration and upward migration spaces for Example 2.17, we present in Figure 2.23 an excerpt from the state transition diagram. In Figure 2.23, we give only the following specific state transitions. Assume that the system is in state
may not be negligible. To illustrate this statement as well as the migration and upward migration spaces for Example 2.17, we present in Figure 2.23 an excerpt from the state transition diagram. In Figure 2.23, we give only the following specific state transitions. Assume that the system is in state ![]() , servicing a call of service‐class 2 with bandwidth
, servicing a call of service‐class 2 with bandwidth ![]() , when a new call of service‐class 1 arrives. This call is accepted with its initial bandwidth
, when a new call of service‐class 1 arrives. This call is accepted with its initial bandwidth ![]() and the system passes to state
and the system passes to state ![]() , transferring to that state the call of service‐class 2 which is still in service. It is therefore apparent to expect that the average number of service‐class 2 calls in state
, transferring to that state the call of service‐class 2 which is still in service. It is therefore apparent to expect that the average number of service‐class 2 calls in state ![]() (which belongs to the upward migration space of service‐class 2), denoted as
(which belongs to the upward migration space of service‐class 2), denoted as ![]() , will not be zero. On the other hand, if the system is in state
, will not be zero. On the other hand, if the system is in state ![]() and a call of service‐class 3 (with
and a call of service‐class 3 (with ![]() ) leaves the system, then the system passes to state
) leaves the system, then the system passes to state ![]() and the population of service‐class 1 calls with
and the population of service‐class 1 calls with ![]() (if any) is transferred to
(if any) is transferred to ![]() . Thus, we also expect that the average number of service‐class 1 calls with
. Thus, we also expect that the average number of service‐class 1 calls with ![]() in state
in state ![]() (which belongs to the migration space of service‐class 1), denoted as
(which belongs to the migration space of service‐class 1), denoted as ![]() , will not be zero.
, will not be zero.

Figure 2.22 Graphical representation of the LB equations 2.63 (left) and 2.64 (right).

Figure 2.23 Migration and upward migration spaces (Example 2.18).
2.9.2.2 CBP, Utilization, and Mean Number of In‐service Calls
Based on ( 2.65), we can determine the following performance measures:
- The CBP of service‐class
 calls with
calls with  b.u.,
b.u.,  , via:
(2.66)where
, via:
(2.66)where
 is the normalization constant.
is the normalization constant. - The CBP of service‐class
 calls with
calls with  b.u.,
b.u.,  , via (1.66).
, via (1.66). - The conditional CBP of service‐class
 calls with
calls with  given that
given that  ,
,  , via:
(2.67)
, via:
(2.67)
- The link utilization,
 , via (1.54).
, via (1.54). - The mean number of service‐class
 calls with
calls with  b.u. in state
b.u. in state  , via:
(2.68)where
, via:
(2.68)where

- The mean number of service‐class
 calls with
calls with  b.u. in state
b.u. in state  ,
, 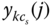 , via:
(2.69)
, via:
(2.69)
- The mean number of in‐service calls of service‐class
 accepted in the system with
accepted in the system with  , via ( 2.16).
, via ( 2.16). - The mean number of in‐service calls of service‐class
 accepted in the system with
accepted in the system with  , via ( 2.56).
, via ( 2.56).
Example 2.19
Consider a link of capacity ![]() b.u. in which calls of four service‐classes are accommodated. Calls of service‐classes 2, 3, and 4 can reduce their bandwidth requirements one, two, and three times, respectively. The traffic and bandwidth requirements of all service‐classes are the following:
b.u. in which calls of four service‐classes are accommodated. Calls of service‐classes 2, 3, and 4 can reduce their bandwidth requirements one, two, and three times, respectively. The traffic and bandwidth requirements of all service‐classes are the following:
 ,
, , and
, and  ,
,
where ![]() and
and ![]() are the vectors of the reduced bandwidth and increased service‐time of service‐class
are the vectors of the reduced bandwidth and increased service‐time of service‐class ![]() , respectively.
, respectively.
Use the following three sets of threshold parameters for service‐classes 2, 3, and 4:
| Set 1: | ||||||
| Set 2: | ||||||
| Set 3: |
By using Set 1, service‐classes 2, 3, and 4 behave according to the MRM. By using Set 2, service‐classes 2 and 3 behave according to the MRM, while service‐class 4 behaves according to the CDTM. By using Set 3, all service‐classes behave as in the CDTM. Provide CBP results of all service‐classes and compare them to the corresponding simulation results. Comment on the results.
In Tables 2.7–2.9 we present the analytical and the simulation CBP results for Sets 1–3, respectively, and for seven values of ![]() . Needless to say that the CBP of service‐classes 2, 3, and 4 are determined based on their last bandwidth requirement. Simulation results are mean values of 12 runs with 95% confidence interval.
. Needless to say that the CBP of service‐classes 2, 3, and 4 are determined based on their last bandwidth requirement. Simulation results are mean values of 12 runs with 95% confidence interval.
Each point P in the first column of Tables 2.7–2.9 corresponds to a vector ![]() . Point
. Point ![]() corresponds to
corresponds to ![]() . In the successive points the values of
. In the successive points the values of ![]() and
and ![]() are increased by 5 and 3, respectively, while
are increased by 5 and 3, respectively, while ![]() and
and ![]() remain constant. That is, point
remain constant. That is, point ![]() corresponds to
corresponds to ![]() and point
and point ![]() to
to ![]() . The analytical CBP results of service‐classes 2 and 3 coincide since both service‐classes have the same last bandwidth requirement (i.e., 4). This is validated from the simulation results. Based on Tables 2.7– 2.9, we see that:
. The analytical CBP results of service‐classes 2 and 3 coincide since both service‐classes have the same last bandwidth requirement (i.e., 4). This is validated from the simulation results. Based on Tables 2.7– 2.9, we see that:
- (i)Set 3 reduces the CBP of service‐classes 1, 2, and 3 more than the other two sets. On the contrary, Set 3 results in the CBP increase of service‐class 4. This is expected since calls of service‐classes 2 and 3 reduce their bandwidth faster by using Set 3. In addition, the arrival rate of service‐classes 1 and 2 increases, a fact that also affects negatively the CBP of service‐class 4.
- (ii)The analytical results of Set 1 are closer to simulation results, compared to the corresponding results of Sets 2 or 3, especially as the offered traffic load increases. This is because in Set 1, calls of service‐classes 2, 3, and 4 behave as in the MRM, so only the LB and the migration approximation add error in the analytical results. In Set 2, service‐class 4 behaves as in the CDTM, so an upward migration approximation error is added to the analytical results. Finally, in Set 3 calls of service‐classes 2, 3, and 4 behave as in the CDTM, a fact that increases the error introduced in the model.
Table 2.7 Analytical and simulation CBP results for Set 1 (Example 2.19).
| Analytical CBP (%) | Simulation CBP (%) | |||||||
| P | ||||||||
| 1 | 1.89 | 7.43 | 7.43 | 9.98 | 1.89 |
6.73 |
6.79 |
9.03 |
| 2 | 2.41 | 9.35 | 9.35 | 12.54 | 2.47 |
8.63 |
8.67 |
11.62 |
| 3 | 2.98 | 11.40 | 11.40 | 15.28 | 3.06 |
10.68 |
10.69 |
14.53 |
| 4 | 3.58 | 13.54 | 13.54 | 18.12 | 3.73 |
12.78 |
12.75 |
17.32 |
| 5 | 4.21 | 15.74 | 15.74 | 21.03 | 4.37 |
14.94 |
14.89 |
20.22 |
| 6 | 4.86 | 17.96 | 17.96 | 23.95 | 5.06 |
17.08 |
17.05 |
23.36 |
| 7 | 5.52 | 20.16 | 20.16 | 26.85 | 5.71 |
19.40 |
19.32 |
26.38 |
Table 2.8 Analytical and simulation CBP results for Set 2 (Example 2.19).
| Analytical CBP (%) | Simulation CBP (%) | |||||||
| P | ||||||||
| 1 | 1.68 | 6.53 | 6.53 | 9.49 | 1.56 |
5.69 |
5.70 |
7.90 |
| 2 | 2.19 | 8.42 | 8.42 | 12.17 | 2.13 |
7.62 |
7.62 |
10.68 |
| 3 | 2.76 | 10.47 | 10.47 | 15.07 | 2.75 |
9.70 |
9.72 |
13.68 |
| 4 | 3.38 | 12.63 | 12.63 | 18.10 | 3.44 |
11.95 |
11.96 |
16.91 |
| 5 | 4.03 | 14.86 | 14.86 | 21.20 | 4.14 |
14.23 |
14.23 |
20.20 |
| 6 | 4.70 | 17.12 | 17.12 | 24.31 | 4.90 |
16.56 |
16.55 |
23.47 |
| 7 | 5.39 | 19.37 | 19.37 | 27.39 | 5.64 |
18.85 |
18.86 |
26.79 |
Table 2.9 Analytical and simulation CBP results for Set 3 (Example 2.19).
| Analytical CBP (%) | Simulation CBP (%) | |||||||
| P | ||||||||
| 1 | 0.95 | 4.01 | 4.01 | 8.21 | 0.51 |
2.15 |
2.12 |
4.28 |
| 2 | 1.35 | 5.70 | 5.70 | 11.47 | 1.00 |
4.11 |
4.10 |
8.15 |
| 3 | 1.82 | 7.66 | 7.66 | 15.15 | 1.61 |
6.41 |
6.47 |
12.64 |
| 4 | 2.35 | 9.80 | 9.80 | 19.07 | 2.23 |
8.79 |
8.87 |
17.34 |
| 5 | 2.91 | 12.06 | 12.06 | 23.11 | 2.90 |
11.49 |
11.42 |
21.71 |
| 6 | 3.50 | 14.39 | 14.39 | 27.14 | 3.42 |
13.78 |
13.73 |
26.00 |
| 7 | 4.12 | 16.73 | 16.73 | 31.08 | 4.19 |
16.18 |
16.13 |
30.34 |
2.10 The Connection Dependent Threshold Model under the BR Policy
2.10.1 The Service System
In the CDTM under the BR policy (CDTM/BR), ![]() b.u. are reserved to benefit calls of all other service‐classes apart from service‐class
b.u. are reserved to benefit calls of all other service‐classes apart from service‐class ![]() . The application of the BR policy in the CDTM is similar to that of the MTM/BR.
. The application of the BR policy in the CDTM is similar to that of the MTM/BR.
2.10.2 The Analytical Model
2.10.2.1 Link Occupancy Distribution
Similar to the MTM/BR, we adopt the Roberts method for the calculation of ![]() in the CDTM/BR. Based on the Roberts method, ( 2.65) takes the form [ 4]:
in the CDTM/BR. Based on the Roberts method, ( 2.65) takes the form [ 4]:

where 

 and
and ![]() .
.
2.10.2.2 CBP, Utilization, and Mean Number of In‐service Calls
Based on (2.70), we can determine the following performance measures:
- The CBP of service‐class k calls with
 b.u.,
b.u.,  , as follows [ 4]:
(2.71)where
, as follows [ 4]:
(2.71)where
 is the normalization constant.
is the normalization constant. - The CBP of service‐class
 calls with
calls with  b.u.,
b.u.,  , via (1.66).
, via (1.66). - The conditional CBP of service‐class
 calls with
calls with  given that
given that  , via:
(2.72)
, via:
(2.72)
- The link utilization,
 , via (1.54).
, via (1.54). - The mean number of service‐class
 calls with
calls with  b.u. in state
b.u. in state  , via:
(2.73)where
, via:
(2.73)where

- The mean number of service‐class
 calls with
calls with  b.u. in state
b.u. in state  , via:
(2.74)where
, via:
(2.74)where
 .
. - The mean number of in‐service calls of service‐class
 accepted in the system with
accepted in the system with  , via ( 2.16).
, via ( 2.16). - The mean number of in‐service calls of service‐class
 accepted in the system with
accepted in the system with  , via ( 2.56).
, via ( 2.56).
Example 2.20
Consider four service‐classes of Poisson arriving calls with the following traffic characteristics: ![]() , and
, and ![]() . Calls are accommodated by a link of capacity
. Calls are accommodated by a link of capacity ![]() b.u. under the BR policy. Calls of service‐classes 3 and 4 may reduce their bandwidth, upon their arrival, according to the thresholds of Figure 2.24. Choose the BR parameters so that CBP are equalized among all service‐classes. Calculate the equalized CBP and compare them to the corresponding simulation results when the offered traffic‐load increases from the initial value to
b.u. under the BR policy. Calls of service‐classes 3 and 4 may reduce their bandwidth, upon their arrival, according to the thresholds of Figure 2.24. Choose the BR parameters so that CBP are equalized among all service‐classes. Calculate the equalized CBP and compare them to the corresponding simulation results when the offered traffic‐load increases from the initial value to ![]() , and
, and ![]() in six equal steps.
in six equal steps.

Figure 2.24 Thresholds and bandwidth requirements of service‐classes 3 and 4 (Example 2.20).
Since ![]() , and
, and ![]() b.u., we choose the BR parameters that achieve CBP equalization as follows:
b.u., we choose the BR parameters that achieve CBP equalization as follows: ![]() , and
, and ![]() . Then,
. Then, ![]() . Table 2.10 shows the analytical and simulation CBPs for the seven different sets of offered traffic‐load. Simulation CBP results are very close to the analytical equalized CBP results and validate the CTDM.
. Table 2.10 shows the analytical and simulation CBPs for the seven different sets of offered traffic‐load. Simulation CBP results are very close to the analytical equalized CBP results and validate the CTDM.
Table 2.10 Equalized CBP for Example 2.20.
| Equalized | Simulation CBP (%) | ||||
| (erl) | CBP (%) | ||||
| (100, 12.0, 12.0, 1.0) | 4.19 | 3.36 |
3.36 |
3.35 |
3.32 |
| (110, 13.2, 13.2, 1.1) | 8.64 | 7.61 |
7.60 |
7.61 |
7.63 |
| (120, 14.4, 14.4, 1.2) | 13.85 | 13.11 |
13.11 |
13.08 |
13.10 |
| (130, 15.6, 15.6, 1.3) | 19.11 | 18.57 |
18.54 |
18.56 |
18.52 |
| (140, 16.8, 16.8, 1.4) | 24.07 | 23.68 |
23.70 |
23.70 |
23.71 |
| (150, 18.0, 18.0, 1.5) | 28.62 | 28.43 |
28.43 |
28.44 |
28.45 |
| (160, 19.2, 19.2, 1.6) | 32.75 | 32.58 |
32.60 |
32.57 |
32.59 |
2.11 Applications
We concentrate only on the CDTM since it comprises the retry and threshold models. The initial motivation for the CDTM was the available bit rate (ABR) service of asynchronous transfer mode (ATM) networks. The ABR service is a purely elastic service in which the notion of equivalent bandwidth is not well applicable (i.e., the ABR service cannot be considered a stream service having its average bandwidth per call, as constant rate). Therefore, a different model to the EMLM is needed, and this is the CDTM because it sufficiently models an elastic call at its set‐up phase (but not during the entire call duration) by adequately setting the threshold parameters. Thus, the CDTM is applicable to any elastic service at the call set‐up phase, as long as it is not a bandwidth hungry application wasting all the available bandwidth. For this reason, a threshold scheme must be applied (e.g., Figure 2.20). The logic behind the threshold scheme is that even if the available bandwidth of a link is large enough, a CAC does not always waste it on one call only, but saves a part of it for sharing with the next calls.
The minimum and the maximum bandwidth requirements of an elastic call are important CDTM parameters for the CBP calculation no matter what the thresholds are. The minimum bandwidth requirement is critical for the CBP value. If the minimum required bandwidth is zero, an elastic call should wait for any available bandwidth to start servicing. If the network (CAC) ignores the details of bandwidth requirements (i.e., the threshold scheme) of an elastic call, the assigned bandwidth will not meet the real needs of the call and the CBP calculation will not be accurate. Suppose, for instance, that an elastic call has the following thresholds scheme in a transmission link with bandwidth capacity of 19.2 Mbps: maximum rate of 1.536 Mbps for available link bandwidth at least 6.4 Mbps (first threshold at ![]() Mbps), rate of 768 kbps for available link bandwidth at least 3.2 Mbps at least (second threshold at
Mbps), rate of 768 kbps for available link bandwidth at least 3.2 Mbps at least (second threshold at ![]() Mbps), and minimum rate of 384 kbps for available link bandwidth less than 3.2 Mbps (third threshold at 19.2 Mbps, or at
Mbps), and minimum rate of 384 kbps for available link bandwidth less than 3.2 Mbps (third threshold at 19.2 Mbps, or at ![]() Mbps). Assume that the CAC knows only the minimum and maximum resource requirements of this elastic call, and offers to it (a) 700 kbps or (b) 1.536 Mbps when the available bandwidth is 4.0 Mbps at least in both cases. In the first case, the holding time will be estimated incorrectly (by taking into account 768 kbps instead of 700 kbps), while in the second case, although the holding time will be estimated correctly, the threshold scheme has been violated, therefore the CBP through the CDTM cannot be accurate. As far as the number of thresholds between the minimum and the maximum bandwidth requirements is concerned, several values exist since bandwidth is quantized and provided as a group of b.u. (trunks). So, in a realistic network environment the number of thresholds is manageable.
Mbps). Assume that the CAC knows only the minimum and maximum resource requirements of this elastic call, and offers to it (a) 700 kbps or (b) 1.536 Mbps when the available bandwidth is 4.0 Mbps at least in both cases. In the first case, the holding time will be estimated incorrectly (by taking into account 768 kbps instead of 700 kbps), while in the second case, although the holding time will be estimated correctly, the threshold scheme has been violated, therefore the CBP through the CDTM cannot be accurate. As far as the number of thresholds between the minimum and the maximum bandwidth requirements is concerned, several values exist since bandwidth is quantized and provided as a group of b.u. (trunks). So, in a realistic network environment the number of thresholds is manageable.
In what follows, we concentrate on the applicability of the CDTM to WCDMA networks. We have skipped straightforward applications, albeit some of them are very interesting, such as the application of the CDTM on smart grid, for a fine control of energy consumption [9].
Applicability of the CDTM to WCDMA Networks
The CDTM can be applied to WCDMA networks (in the uplink) in a similar way to the EMLM. A single BS controlling a cell can be modeled as a system of certain bandwidth capacity. The b.u. can be an equivalent bandwidth defined by the load factor introduced, for instance, by a lower rate service‐class (e.g., voice). The load factor is determined by the signal‐to‐noise ratio (SNR), data rate, and activity factor (probability that a call is active – transmits) of the associated service‐class. As far as the inter‐cell interference is concerned, it is assumed log‐normally distributed1 and independent of the cell load. A call is accepted for service as long as there are enough resources available in the cell. The CAC policy is based on the estimation of the increase in the total interference (intra‐ and inter‐cell interference plus thermal noise) caused by the acceptance of new calls. After call acceptance, the SNR of all in‐service calls deteriorates; because of this, WCDMA systems usually have no hard limits on call capacity. A call should not be accepted if it increases the noise of all in‐service calls above a tolerable level. Poisson arriving calls to a cell may have several contingency resource/QoS requirements.
Let us consider that the QoS offered to each service‐class ![]() belongs to one out of
belongs to one out of ![]() alternative QoS levels, which depend on the occupied cell resources. In what follows, a service‐class
alternative QoS levels, which depend on the occupied cell resources. In what follows, a service‐class ![]() call of QoS level
call of QoS level ![]() is referred to as service‐class
is referred to as service‐class ![]() call. A service‐class
call. A service‐class ![]() call is characterized by the following QoS parameters: (i)
call is characterized by the following QoS parameters: (i) ![]() , transmission bit rate, (ii)
, transmission bit rate, (ii) ![]() , mean service time (exponentially distributed), and (iii)
, mean service time (exponentially distributed), and (iii) ![]() , BER parameter.
, BER parameter.
The application of the CDTM for the call‐level performance evaluation of WCDMA networks is necessary when assuming that a WCDMA cell accommodates not only stream service‐classes but also elastic service‐classes, which are associated with individual sets of thresholds (indicating the occupied cell resources). A variation of an elastic service‐class is an adaptive service‐class, in which calls may reduce their resources/bandwidth, but their service time is kept fixed. We can therefore consider three types of service‐classes:
- Stream type: service‐classes that have only one QoS level (
 ).
). - Elastic type: service‐classes that have more than one QoS level (
 ) and the call's mean service time strongly depends on the QoS level (it holds:
) and the call's mean service time strongly depends on the QoS level (it holds: 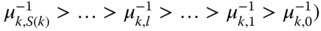 .
. - Adaptive type: service‐classes that have more than one QoS level (
 ) and the call's mean service time is the same for all QoS levels (it holds:
) and the call's mean service time is the same for all QoS levels (it holds:  .
.
Upon their arrival, elastic or adaptive calls select one resource requirement according to an associated threshold scheme; a resource requirement is not altered during the service‐time. For example, a QoS level can be assigned to an elastic service‐class ![]() call at the arrival time and is based on the occupied system resources (cell load
call at the arrival time and is based on the occupied system resources (cell load ![]() ), which is indicated through thresholds. The thresholds of an elastic service‐class
), which is indicated through thresholds. The thresholds of an elastic service‐class ![]() are denoted by
are denoted by ![]() . The QoS level assignment is performed as follows. If
. The QoS level assignment is performed as follows. If ![]() , then the elastic call is assigned the first QoS level
, then the elastic call is assigned the first QoS level ![]() and occupies
and occupies ![]() system resources for an exponentially distributed service time with mean
system resources for an exponentially distributed service time with mean ![]() . The symbol
. The symbol ![]() comes from the load factor (see 2.78). If
comes from the load factor (see 2.78). If ![]() , then the call is assigned to the second QoS level and occupies
, then the call is assigned to the second QoS level and occupies ![]() resources for an exponentially distributed service‐time with mean
resources for an exponentially distributed service‐time with mean ![]() , and so on. Finally, if
, and so on. Finally, if ![]() , then the call is assigned to the
, then the call is assigned to the ![]() QoS level and occupies
QoS level and occupies ![]() resources for an exponentially distributed service time with mean
resources for an exponentially distributed service time with mean ![]() . We assume that an elastic call has a certain amount of data to transmit. Therefore, a call's service time should be conversely proportional to the allocated resources. For this reason, the mean call service times,
. We assume that an elastic call has a certain amount of data to transmit. Therefore, a call's service time should be conversely proportional to the allocated resources. For this reason, the mean call service times, ![]() , are chosen so that the product
, are chosen so that the product ![]() remains constant for every QoS level
remains constant for every QoS level ![]() . As far as the offered traffic‐load of service‐class
. As far as the offered traffic‐load of service‐class ![]() calls is concerned, it is defined as
calls is concerned, it is defined as ![]() .
.
Interference and Call Admission Control
We assume perfect power control, i.e., at the BS, the same amount of power, ![]() , is received from each service‐class
, is received from each service‐class ![]() call. Since in WCDMA systems all users transmit within the same frequency band, a single user sees the signals generated by all other users as interference. Intra‐cell interference,
call. Since in WCDMA systems all users transmit within the same frequency band, a single user sees the signals generated by all other users as interference. Intra‐cell interference, ![]() , is caused by users of the cell and inter‐cell interference,
, is caused by users of the cell and inter‐cell interference, ![]() , is caused by users of the neighbouring cells. An amount of power
, is caused by users of the neighbouring cells. An amount of power ![]() is due to thermal noise in the cell and corresponds to the intra‐cell interference when the cell is empty.
is due to thermal noise in the cell and corresponds to the intra‐cell interference when the cell is empty.
The CAC is performed by measuring the noise rise, ![]() , which is defined as the ratio of the total received power at the BS,
, which is defined as the ratio of the total received power at the BS, ![]() , to the thermal noise power,
, to the thermal noise power, ![]() :
:

When a new call arrives, the CAC estimates the noise rise and if it exceeds a maximum value, ![]() , the new call is blocked and lost.
, the new call is blocked and lost.
Load factor and cell load
The cell load, ![]() , is defined as the ratio of the received power from all active users to the total received power:
, is defined as the ratio of the received power from all active users to the total received power:

From (2.75) and (2.76), the relation between the noise rise and the cell load is:
The maximum value of the cell load, ![]() , is the cell load which corresponds to the maximum noise rise,
, is the cell load which corresponds to the maximum noise rise, ![]() 2:
2: ![]() .
.
The resource/bandwidth requirement of a service‐class ![]() call is expressed by the load factor,
call is expressed by the load factor, ![]() [10]:
[10]:

where ![]() is the chip rate of the WCDMA carrier.
is the chip rate of the WCDMA carrier.
The cell load ![]() can be written as the sum of the intra‐cell load,
can be written as the sum of the intra‐cell load, ![]() (cell load derived from the active users of the reference cell), and the inter‐cell load,
(cell load derived from the active users of the reference cell), and the inter‐cell load, ![]() (cell load derived from the active users of the neighbouring cells), i.e.,
(cell load derived from the active users of the neighbouring cells), i.e., ![]() . The values of
. The values of ![]() and
and ![]() are given by 2.79 and 2.80, respectively:
are given by 2.79 and 2.80, respectively:

where ![]() is the number of active users of service‐class
is the number of active users of service‐class ![]() , while
, while

For a new service‐class ![]() call acceptance, the following condition must hold in the BS:
call acceptance, the following condition must hold in the BS:
That is, an arriving call with resource requirement ![]() is accepted in the cell if and only if, after its acceptance, the cell load remains below
is accepted in the cell if and only if, after its acceptance, the cell load remains below ![]() .
.
Local Blocking Probabilities
Due to (2.81), the probability that a new service‐class ![]() call is blocked when arriving at an instant with intra‐cell load,
call is blocked when arriving at an instant with intra‐cell load, ![]() , is called the local blocking probability (LBP),
, is called the local blocking probability (LBP), ![]() , and can be calculated by (based on ( 2.78)–( 2.80)):
, and can be calculated by (based on ( 2.78)–( 2.80)):
In ( 2.80), the ![]() can be modelled as a lognormal random variable (with parameters mean
can be modelled as a lognormal random variable (with parameters mean ![]() and variance
and variance ![]() ), which is independent of the intra‐cell interference. Hence, the mean,
), which is independent of the intra‐cell interference. Hence, the mean, ![]() , and the variance,
, and the variance, ![]() , of
, of ![]() are calculated by:
are calculated by:
Consequently, because of ( 2.80), the inter‐cell load, ![]() , will also be a lognormal random variable. Its mean,
, will also be a lognormal random variable. Its mean, ![]() , and variance,
, and variance, ![]() , are calculated as follows:
, are calculated as follows:
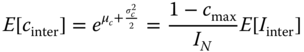

where the parameters ![]() and
and ![]() can be determined by solving (2.85) and (2.86):
can be determined by solving (2.85) and (2.86):

where ![]() is the coefficient of variation.
is the coefficient of variation.
Thus, (2.82) can be rewritten as:
The RHS of (2.89), is the cumulative distribution function (CDF) of ![]() . It is denoted by
. It is denoted by ![]() and can be calculated from:
and can be calculated from:

where ![]() is the well‐known error function.
is the well‐known error function.
Hence, if we substitute ![]() into (2.90), from ( 2.89) we can calculate the LBP of service‐class
into (2.90), from ( 2.89) we can calculate the LBP of service‐class ![]() calls as follows:
calls as follows:

Parameters' Discretization
To apply the CDTM in WCDMA systems, parameters' discretization is required. It is achieved by the introduction of a basic cell load unit ![]() (e.g., granularity of
(e.g., granularity of ![]() , used in Example 2.23). The CDTM parameters of system capacity, the total number of occupied b.u. in the system, the assigned number of b.u. to an in‐service call, and a bandwidth threshold are obtained by discretizing the cell load, the maximum cell load, the load factor, and the resource threshold, respectively:
, used in Example 2.23). The CDTM parameters of system capacity, the total number of occupied b.u. in the system, the assigned number of b.u. to an in‐service call, and a bandwidth threshold are obtained by discretizing the cell load, the maximum cell load, the load factor, and the resource threshold, respectively:

Incorporating the User Activity and LBP
The user activity is described by the activity factor, ![]() , which represents the fraction of the active period of a service‐class
, which represents the fraction of the active period of a service‐class ![]() call/user over the entire service time (
call/user over the entire service time (![]() ). In the CDTM, we consider that calls are active during the entire service time and we do not distinguish active users from passive users. However, in WCDMA systems it is essential to consider such a distinction because passive users do not consume any system resources. Hence, a system state
). In the CDTM, we consider that calls are active during the entire service time and we do not distinguish active users from passive users. However, in WCDMA systems it is essential to consider such a distinction because passive users do not consume any system resources. Hence, a system state ![]() does not represent the total number of occupied b.u. Instead, it represents the total number of b.u. that would be occupied if all (mobile) users were active. Let
does not represent the total number of occupied b.u. Instead, it represents the total number of b.u. that would be occupied if all (mobile) users were active. Let ![]() denote the total number of occupied b.u. at an instant. In the CDTM,
denote the total number of occupied b.u. at an instant. In the CDTM, ![]() is always equal to
is always equal to ![]() , while in WCDMA networks we have
, while in WCDMA networks we have ![]() . When all users are passive,
. When all users are passive, ![]() , while
, while ![]() when all users are active.
when all users are active.
The bandwidth occupancy, ![]() , is defined as the conditional probability that
, is defined as the conditional probability that ![]() b.u. are occupied in state
b.u. are occupied in state ![]() and, for user activity
and, for user activity ![]() , it can be calculated recursively by:
, it can be calculated recursively by:

where ![]() is the highest reachable system state,
is the highest reachable system state, ![]() for
for ![]() , and
, and ![]() is called resource/bandwidth share and denotes the proportion of the total occupied resources,
is called resource/bandwidth share and denotes the proportion of the total occupied resources, ![]() , from service‐class
, from service‐class ![]() calls (see (2.95)).
calls (see (2.95)).
In WCDMA systems, due to the intra‐/inter‐cell interference, blocking of a service‐class ![]() call may occur at any state
call may occur at any state ![]() with a probability
with a probability ![]() . This probability, called the local blocking factor (LBF), is calculated by summing over
. This probability, called the local blocking factor (LBF), is calculated by summing over ![]() the LBP multiplied by the corresponding bandwidth occupancies:
the LBP multiplied by the corresponding bandwidth occupancies:

where for ![]() use (2.91) with
use (2.91) with ![]() . Note that when
. Note that when ![]() ,
, ![]() (since in this case
(since in this case ![]() and
and ![]() ).
).
The service‐class ![]() bandwidth share in state
bandwidth share in state ![]() (requiring
(requiring ![]() b.u.) is derived assuming LB between adjacent systems states, while incorporating the LBF and the parameter delta (indicating the upward migration and migration approximations):
b.u.) is derived assuming LB between adjacent systems states, while incorporating the LBF and the parameter delta (indicating the upward migration and migration approximations):

where ![]() , while for
, while for ![]() :
:

Example 2.21
In Figure 2.25 we show how we can recursively determine the bandwidth occupancy (2.93). Consider a system with ![]() service‐classes and a single QoS level per service‐class (i.e.,
service‐classes and a single QoS level per service‐class (i.e., ![]() ), while
), while ![]() b.u. A dashed line shows the arrival of a passive user, while a solid line represents the arrival of an active user. Starting from state
b.u. A dashed line shows the arrival of a passive user, while a solid line represents the arrival of an active user. Starting from state ![]() , four possibilities exist:
, four possibilities exist:

Figure 2.25 Recurrent determination of the resource share (Example 2.21).
- (i)A passive user of service‐class 1 is accepted in the system with probability
 and the system passes to state
and the system passes to state  .
. - (ii)A passive user of service‐class 2 is accepted in the system with probability
 and the system passes to state
and the system passes to state  .
. - (iii)An active user of service‐class 1 is accepted in the system with probability
 and the system passes to state
and the system passes to state  .
. - (iv)An active user of service‐class 2 is accepted in the system with probability
 and the system passes to state
and the system passes to state  .
.
Then, ![]() is determined from
is determined from ![]() and
and ![]() :
:
![]() .
.
Example 2.22
Thanks to discretization, we can continue presenting a WCDMA cell in terms of the CDTM. Let us consider a link of capacity ![]() b.u. accommodating
b.u. accommodating ![]() service‐classes. Calls of service‐class 1 require 1 b.u. without any threshold. Service‐class 2 has one threshold,
service‐classes. Calls of service‐class 1 require 1 b.u. without any threshold. Service‐class 2 has one threshold, ![]() , and two contingency bandwidth requirements,
, and two contingency bandwidth requirements, ![]() and
and ![]() , while service‐class 3 has two thresholds,
, while service‐class 3 has two thresholds, ![]() and
and ![]() , and three contingency bandwidth requirements,
, and three contingency bandwidth requirements, ![]() , and
, and ![]() . In this specific example, a call is blocked and lost whenever the link bandwidth is fully occupied because the minimum bandwidth per call requirement of all three service‐classes is 1. If we apply this threshold scheme to a WCDMA system, due to the existence of local blocking, there are no pure blocking and non‐blocking states, but blocking of a service‐class
. In this specific example, a call is blocked and lost whenever the link bandwidth is fully occupied because the minimum bandwidth per call requirement of all three service‐classes is 1. If we apply this threshold scheme to a WCDMA system, due to the existence of local blocking, there are no pure blocking and non‐blocking states, but blocking of a service‐class ![]() call may occur in any state
call may occur in any state ![]() with probability
with probability ![]() (LBF). In Figure 2.26 we show the (macro‐) state transition diagram of this example for service‐class 2. Observe that in the Markov chain of this system, due to the local blocking, the transition rates from lower states to higher are reduced by the factor
(LBF). In Figure 2.26 we show the (macro‐) state transition diagram of this example for service‐class 2. Observe that in the Markov chain of this system, due to the local blocking, the transition rates from lower states to higher are reduced by the factor ![]() . A more important difference is that the system state
. A more important difference is that the system state ![]() can exceed
can exceed ![]() . The maximum value of
. The maximum value of ![]() is denoted by
is denoted by ![]() and is the state at which
and is the state at which ![]() approach 1. In other words, the higher states are unreachable due to severe local blocking. This fact shows that WCDMA systems may have no hard limit on the system capacity and therefore we talk about soft capacity. The Markov chain of Figure 2.26 does not have a PFS (all arrows are valid, ignore the Xs on the arrows for the moment) due to the existence of different contingency bandwidth requirements (as in the CDTM) and the local blocking; they both destroy the local balance between adjacent system states.
approach 1. In other words, the higher states are unreachable due to severe local blocking. This fact shows that WCDMA systems may have no hard limit on the system capacity and therefore we talk about soft capacity. The Markov chain of Figure 2.26 does not have a PFS (all arrows are valid, ignore the Xs on the arrows for the moment) due to the existence of different contingency bandwidth requirements (as in the CDTM) and the local blocking; they both destroy the local balance between adjacent system states.
For LB, the Markov chain must be transformed to a reversible Markov chain (represented in Figure 2.26 when ignoring the arrows bearing an X) by taking into account the migration and upward migration approximation (Figure 2.27).
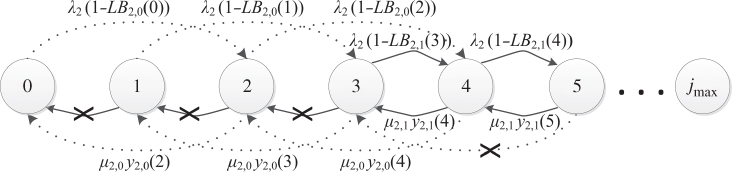
Figure 2.26 Excerpt of the state transition diagram (Example 2.22).

Figure 2.27 Migration and upward migration space (Example 2.22).
State Probabilities and CBP
The state probabilities are given by:

for ![]() and
and ![]() for
for ![]() , with
, with ![]() .
.
The CBP of service‐class ![]() can be calculated by adding all the state probabilities multiplied by the corresponding LBFs:
can be calculated by adding all the state probabilities multiplied by the corresponding LBFs:

Due to the contingency bandwidth requirements, ![]() , we need also to sum over
, we need also to sum over ![]() in specific areas defined by thresholds. This is done with the aid of the parameter gamma:
in specific areas defined by thresholds. This is done with the aid of the parameter gamma:

Example 2.23
A WCDMA cell of ![]() , with
, with ![]() mW, suffering
mW, suffering ![]() mW and
mW and ![]() , supports
, supports ![]() elastic service‐classes having
elastic service‐classes having ![]() kbps, and
kbps, and ![]() or
or ![]() erl. Table 2.11 contains the CBP results.
erl. Table 2.11 contains the CBP results.
Table 2.11 Various parameters and CBP results of Example 2.23.
| Service‐class 1 | Service‐class 2 | |||
| Activity factor | 1 | 0.7 | ||
| 4 dB | 3 dB | |||
| Traffic load | 4 erl | 8 erl | 1 erl | 2 erl |
| CBP (EMLM) | 0.9052% | 5.1663% | 1.1131% | 6.8848% |
| CBP (CDTM) | 0.9% | 4.5441% | 1.0978% | 5.9980% |
2.12 Further Reading
Extensions of the retry or thresholds models are categorized in wired [11–18], wireless [19–21], and optical networks [22]. In [ 11], the threshold models are extended to include BPP traffic. The CBP calculations are based either on recursive formulas or on convolution algorithms. In [12] and [13], the single threshold of the STM is replaced by two thresholds. When a new call finds the occupied link bandwidth above a threshold, it can be accepted in the link with its lower bandwidth requirement (similar to the STM). When the occupied link bandwidth becomes less than the second threshold then an in‐service call (accepted with its lower bandwidth requirement) can increase its bandwidth to its peak‐bandwidth requirement. In [14] and [15], the CDTM is extended to allow call bandwidth compression/expansion of in‐service calls with [ 15] or without [ 14] the existence of the BR policy (more on the subject of bandwidth compression/expansion and Poisson arriving calls can be found in Chapters and ). In [16– 18], a variant of the SRM/STM is proposed. Specifically, some service‐classes are characterized cooperative and the rest non‐cooperative. Users from a cooperative service‐class can retry with a certain probability to be connected in the system with reduced bandwidth when blocked with their initial peak‐bandwidth and the total occupied bandwidth of the system is below a threshold. This behavior increases the QoS perceived by other users. In [ 19], the threshold models are extended to include the CBP calculation in the uplink of a UMTS network. To this end, the notion of local (soft) blocking is incorporated in the model. The latter means that a call may be blocked in any state of the system if its acceptance violates the QoS, in terms of noise, of all in‐service calls (see also [23–26]). In [20], the threshold models are extended for the call‐level analysis of the Iub interface in UMTS networks. In [ 21], a multi‐threshold teletraffic model for heterogeneous CDMA networks is proposed. The model enables QoS differentiation of handover traffic when elastic and adaptive service‐classes are present. Furthermore, an applicability framework is proposed that takes into account advances in Cloud‐RAN and self‐organizing network (SON) technologies. In [ 22], the CDTM is extended for the calculation of connection failure probabilities (due to unavailability of a wavelength) and CBP (due to the restricted bandwidth capacity of a wavelength) in hybrid TDM‐WDM PONs with DWA.
References
- 1 J. Kaufman, Blocking in a completely shared resource environment with state dependent resource and residency requirements. Proceedings of IEEE INFOCOM'92, Florence, Italy, 4–8 May 1992, pp. 2224–2232.
- 2 J. Kaufman, Blocking with retrials in a completely shared resource environment. North‐Holland, Performance Evaluation, 15(2):99–113, June 1992.
- 3 J. Kaufman, Blocking in a shared resource environment. IEEE Transactions on Communications, 29(10):1474–1481, October 1981.
- 4 I. Moscholios, M. Logothetis and G. Kokkinakis, Connection dependent threshold model: A generalization of the Erlang multiple rate loss model. Performance Evaluation, 48(1–4):177–200, May 2002.
- 5 I. Moscholios, M. Logothetis and T. Liokos, QoS equalization in the connection dependent threshold model. Proceedings of the Communication Systems, Networks and Digital Signal Processing Conference, CSNDSP 2002, Staffordshire, UK, 15–17 July 2002, pp. 442–445.
- 6 SIMSCRIPT III, http://www.simscript.com/.
- 7 M. Logothetis, I. Moscholios and G. Kokkinakis, Improvement of the connection dependent threshold model with the aid of reverse transition rates. 12th GI/ITG Conference on Measuring, Modelling and Evaluation of Computer and Comummunication Systems (MMB) and 3rd Polish‐German Teletraffic Symposium (PGTS), MMB&PGTS 2004, Dresden, Germany, 12–15 September 2004.
- 8 M. Logothetis, I. Moscholios and G. Kokkinakis, New connection dependent threshold model – A generalization of the Erlang multirate loss model. Mediterranean Journal of Electronics and Communications, 3(4):126–137, October 2007.
- 9 J. Vardakas, I. Zenginis, and M. Oikonomakou, Peak demand reduction through demand control: A mathematical analysis, Proceedings of the IEICE ICTF 2016, Patras, 6–8 July 2016.
- 10 V. Vassilakis, G. Kallos, I. Moscholios and M. Logothetis, An analytical model for elastic service‐classes in W‐CDMA networks, in Heterogenenous Networks, Vol. II ‐ Performance Analysis & Applications, D.SEA.6.1.6: Part of Final Deliverables of NoE Euro‐NGI to EC, River Publishers, pp. 277–299, 2009.
- 11 M. Glabowski, A. Kaliszan and M. Stasiak, Modeling product‐form state dependent systems with BPP traffic. Performance Evaluation, 67(3):174–197, March 2010.
- 12 M. Sobieraj, M. Stasiak, J. Weissenberg and P. Zwierzykowski, Analytical model fo the single threshold mechanism with hysteresis for multi‐service networks, IEICE Transactions on Communications, E95‐B(1):120–132, January 2012.
- 13 M. Sobieraj, M. Stasiak and P. Zwierzykowski, Model of the threshold mechanism with double hysteresis for multi‐service networks, in Computer Networks, CN 2012, A. Kwicien, P. Gaj and P. Stera (eds), Communications in Computer and Information Science, Vol. 291, Springer, Berlin, 2012.
- 14 V. Vassilakis, I. Moscholios and M. Logothetis, Call‐level performance modeling of elastic and adaptive service‐classes. Proceedings of the ICC, Glasgow, UK, June 2007.
- 15 V. Vassilakis, I. Moscholios and M. Logothetis, The extended connection‐dependent threshold model for call‐level performance analysis of multi‐rate loss systems under the bandwidth reservation policy. International Journal of Communication Systems, 25(7):849–873, July 2012.
- 16 S. Miyata, K. Yamaoka and H. Kinoshita, Optimal threshold characteristics of call admission control by considering cooperative behavior of users (loss model). Proceedings of the IEEE PACRIM, Victoria, Canada, August 2013.
- 17 S. Miyata, K. Yamaoka and H. Kinoshita, Optimal threshold configuration methods for flow admission control with cooperative users. IEICE Transactions on Communications, E97‐B(12):2706–2719, December 2014.
- 18 I. Moscholios, M. Logothetis and S. Shioda, Performance evaluation of multirate loss systems supporting cooperative users with a probabilistic behavior. IEICE Transactions on Communications, E100‐B(10):1778–1788, October 2017.
- 19 L. Popova and W. Koch, Analytical performance evaluation of mixed services with variable data rates for the uplink of UMTS. Proceedings of ISWCS'06, Valencia, Spain, September 2006.
- 20 D. Parniewicz, M. Stasiak, and P. Zwierzykowski, Multicast connections in mobile networks with embedded threshold mechanism, in Computer Networks, CN 2011, A. Kwicien, P. Gaj and P. Stera (eds), Communications in Computer and Information Science, Vol. 160, Springer, Berlin, 2011.
- 21 V. Vassilakis, I. Moscholios and M. Logothetis, Quality of service differentiation of elastic and adaptive services in CDMA networks: A mathematical modelling approach. Wireless Networks, 24(4):1279–1295, May 2018.
- 22 J. Vardakas, V. Vassilakis and M. Logothetis, Blocking analysis in hybrid TDM‐WDM PONs supporting elastic traffic. Proceedings of AICT, Athens, Greece, June 2008.
- 23 D. Staehle and A. Mäder, An analytic approximation of the uplink capacity in a UMTS network with heterogeneous traffic. Proceedings of the 18th International Teletraffic Congress, Berlin, September 2003.
- 24 V. Iversen, V. Benetis, N. Ha, and S. Stepanov, Evaluation of multi‐service CDMA networks with soft blocking. Proceedings of the ITC Specialist Seminar, pp. 223–227, Antwerp, August/September 2004.
- 25 V. Iversen, Evaluation of multi‐service CDMA networks with soft blocking. Proceedings of the 3rd Conference on Smart Spaces, ruSMART 2010, and 10th International Conference, NEW2AN 2010, St. Petersburg, Russia, August 2010.
- 26 I. Moscholios, G. Kallos, V. Vassilakis, M. Logothetis and M. Koukias, Congestion probabilities in W‐CDMA networks supporting calls of finite sources. Proceedings of HETNETs, Ilkley, West Yorkshire, UK, November 2013.
