CHAPTER 17
Local Network Security: Review Questions
Review the following summary points before proceeding to the “Review Questions” and “Exam Questions” sections at the end of this chapter to make sure you are comfortable with every concept. After completing the review, answer the review questions to verify your knowledge of the material covered in Part III.
Summary Points
- The most widely discussed hierarchical networking initiative is the open systems interconnection (OSI) model put forward by the International Standards Organization.
- Every networking course examines the OSI model in terms of what types of devices, protocols, and functions exist at each level. However, different cybersecurity challenges may be present at each level.
- Network topologies are Layer 1—physical or logical—connection strategies that fall into four basic types of configurations: star, bus, ring, and mesh.
- Most networks employ connectivity devices, such as hubs, switches, and routers, which alter the appearance of the actual connection scheme. Therefore, the logical topology will not match the appearance of the physical topology. The particulars of the connection scheme are hidden inside the connecting device.
- A network protocol is a set of rules that governs how communications are conducted across a network. In order for devices to communicate with each other on the network, they must all use the same network protocol.
- The most basic address in networking operations is the Media Access Control address (MAC address) that serves as a unique identifier for every device attached to a network. These addresses are typically assigned to the devices by their manufacturers and stored in their firmware.
- Two common types of attacks typically are aimed at the MAC layer of a network: MAC spoofing and MAC broadcast flooding.
- MAC spoofing involves changing the device’s MAC address to change its identity.
- A MAC broadcast flood attack can be launched against a Layer 2 device, such as a network switch, from a device connected to one of its ports. The attack software on the controlled device is designed to flood a high volume of different MAC addresses into the switch’s CAM table, causing it to fill up. When this state is reached, the switch will run out of room to map the new MAC addresses to its ports. Because all of the MAC addresses in the CAM are now new addresses that have not been mapped, the switch will be forced to broadcast all of the frames it receives to all of its ports.
- The TCP/IP (Transmission Control Protocol/Internet Protocol) suite of protocols form the most popular network protocol currently in use.
- With the proper tools, it is fairly easy to manipulate the IP headers of TCP/IP packets to falsify addresses to hide an attacker’s identity. This manipulation process is known as IP spoofing and is the basis for many types of network and internetwork attacks.
- A SYN flood that exploits the three-way handshake that TCP/IP employs to initiate connections between network nodes. In this type of attack, the attacker sends the SYN request to the server, but manipulates the handshake to either spoof a different IP address in the SYN packet or simply withhold the ACK packet from the server.
- An IP address is required to make a device a valid member of the Internet. This is how individual users are identified to receive file transfers, email, and file requests. Two versions of IP addressing are currently in use: IPv4 and IPv6. IPv4 is the internet protocol version typically referenced because it has been around longer and is simpler to understand.
- Sections of the network can be grouped together into subnets that share a range of IP addresses. A protective gateway is employed to act as an entry and exit point for the segmented subnet. These groups are referred to as intranets. An intranet requires that each segment have a protective gateway to act as an entry and exit point for the segment. In most cases, the gateway is a device called a router or a switch.
- Alongside TCP/IP being the dominant data packaging and transfer protocol suite, the Ethernet family of standards has become the dominant force in hardware and electrical signaling interfacing as well as for providing media access control.
- Under the Ethernet standard, information is collected into a package called a frame. An Ethernet frame brings together many pieces of information required to navigate a network: the source and destination MAC addresses, as well as the IP packet header and data. In addition, the Ethernet frame adds an error-checking and correcting section, which enables the receiver at the destination to check what it receives for correctness.
- The Ethernet protocol is classified as a bus topology that has been implemented across several different network media, including:
- Coaxial cable (IEEE 802.3 – 10BASE-2 or -5)
- Twisted-pair copper cable (IEEE 802.3 – 10/100/1000BASE-T)
- Fiber-optic cable (IEEE 802.3 – 10/100/1000BASE-Fx, Lx or Sx)
- Wireless RF (IEEE 802.11a-h)
- Network servers are specialized computers designed to operate efficiently in a multiuser, multiprocessor, multitasking environment.
- While all servers perform the basic functions described so far, in practice servers may vary significantly in the primary application they are designed to perform for the network’s clients.
- Access to a server’s shared resources should be limited to users who have both a need and the proper authorization to gain such access. Care should be taken to make sure that unauthorized employees do not gain access to confidential materials.
- Network access to servers should typically be protected by one or more firewalls.
- Subnets or routers may be used to create a network segment for some network servers.
- Because servers are frequently used for user authentication, the server’s password should be hashed as a preventative measure. This is typically done by the operating system.
- In network environments, administrators are responsible for implementing the organization’s security policies. These policies should be designed to reflect the three objectives associated with the classical model of information security: confidentiality, integrity, and availability (CIA).
- The server admin is responsible for the design, implementation, and maintenance of the server computers, while the network administrator provides the same functions for the network and its media and connectivity devices.
- Division of administrative duties may also involve a special security administrator who is responsible for performing information security tasks for the servers, hosts, and connectivity devices in the network.
- Network administrators must have control over their physical server environment to provide a comprehensive security setting. This is accomplished by strictly limiting physical access to the servers—most commonly by placing them in protected server rooms that have automatic locks on the door and computer chassis.
- After the operating system and the desired applications have been installed, steps need to be taken to harden the security configuration of the entire server software environment. This involves closing as many known vulnerabilities, while still offering acceptable usability to the network’s users/customers.
- The Mandatory Access Control (MAC) system establishes which users or groups may access files, folders, and other resources.
- With Discretionary Access Control (DAC) strategies and configurations, the user has the discretion to decide who has access to their objects and to what extent.
- Nondiscretionary, Role-Based Access Control (RBAC) is based on job roles each user has within the organization.
- The domain’s server is responsible for maintaining an access control list (ACL) database that tracks each user account, including which group accounts they may be assigned to, as well as what rights and permission they have to different objects.
- In each strategy type, the principle of least privilege should be implemented when providing users with access to objects through rights and permissions assignments. Under this rule, each user is granted only the levels of access required to perform their job roles. This principle limits the damage that can be inflicted by a security breach to the initial task, process, or user.
- There are two classes of users in a network: administrators and users. These classes may also exist at two different levels: in local accounts databases located on the individual client devices and in network accounts databases located on network servers.
- Administrators create user and group accounts for network clients that include specific access rights and permissions to the network’s resources. Network users are allowed or denied access to read, modify, and examine files and folders based on the access control policy that has been established for them either as individuals or by their position in different network groups.
- An important part of an administrator’s tasks and the overall network security plan is auditing. Auditing is a preplanned monitoring method to evaluate or determine if problems exist within the area being evaluated or audited.
- Some firewalls, Intrusion Detection Systems, and auditing software can be configured to provide immediate alerts or notifications to administrators when unusual patterns or events are recognized.
- Auditing user privileges is a useful technique for identifying whether a user’s computer has picked up a virus that escalates the user’s privileges.
- Privilege escalation refers to users who are able to execute a program with embedded code that gives them administrative privileges after logging onto the server.
- Local host Intrusion Detection Systems have been the dominant implementation choice. However, similar systems are available for network-wide implementation. Ultimately, the most effective IDS/IDPS defense is a combination of the two types of systems working together in what are referred to as distributed IDS systems.
- Several vulnerability scanners are available to test the system and identify vulnerabilities and misconfigurations of computing devices in a network environment.
- When physical media leaves the confines of the private facility, the information they carry becomes vulnerable to interception and capture along their route or at the receiving port of the message.
- Fiber-optic cable provides a much more secure data-transmission medium than copper cable, because it cannot be tapped without physically breaking the conductor.
- The IEEE 802.11x wireless standards (also known as Wireless Fidelity or Wi-Fi) have gained wide acceptance as the preferred wireless networking technology for both business and residential network applications.
- Wired Equivalent Privacy (WEP) provides a basic encryption scheme for encrypting data transmissions and authenticating each computer on the network using a 128-bit mathematical key.
- The Wi-Fi Protected Access (WPA) standard adds improved data encryption, using Temporary Key Integrity Protocol (TKIP) and IEEE 802.1X Extensible Authentication Protocol (EAP) user authentication protocol to provide increased security. This combination requires users to employ usernames and passwords to access the network.
- All the intelligent devices attached to the network must have a network interface adapter capable of physically connecting the device to the network transmission media.
- Switches collect MAC address information to keep track of the devices attached to them. As they interact with those devices, they record their MAC information in an onboard memory structure called a MAC address table.
- Switches can also be used to create logically secured Virtual Local Area Networks (VLANs)—a security topology that restricts visibility of network traffic by limiting the movement of network packets so that they only pass between designated ports.
- Unmanaged switches are Plug and Play (PnP) devices that do not include any options for user configuration.
- Managed switches are connectivity devices that have programmable management functions built into them that enable administrators to configure them for the specific network environment in which they will be used. As such, they provide some type of management console that the administrator can use to set parameters.
- Routers are network connectivity devices that forward network information in a manner similar to switches. However, unlike switches, routers can forward information across different network segments. This gives routers the ability to join different networks together through a process known as routing.
- Routers contain different sections of DRAM memory to hold message routing information and to buffer data flow between its ports.
The routing information is stored and updated in a logical memory table referred to as routing table.
- Routers communicate with other routers using a routing protocol to build and maintain their routing tables. These tables are used to record the best route between different network locations.
- A gateway is defined as a device that interfaces a network with another network that employs a different protocol. Recall that a protocol is a defined set of rules for carrying out communication between different devices or systems.
- A network bridge (or a network switch) bridges network segments together and forwards traffic from one network to another. Like the switch, a bridge uses MAC addresses to guide information to the correct ports.
- Most network connectivity devices possess some level of configuration possibilities. As such, their operation can be manipulated if their configuration parameters can be accessed. As with other types of network and computing devices, passwords should be employed to control access to the connectivity device’s configuration data whenever possible.
- Packet sniffing is the act of listening to packets as they move through a network. This activity is normally conducted using a network analyzer tool referred to as a packet sniffer. Attackers use these tools to listen to network traffic looking for items such as passwords and usernames sent across the network in a plaintext mode; they also listen for sensitive information such as credit card or other financial information they can hijack.
- Address Resolution Protocol (ARP) spoofing attacks send fake ARP messages to associate their MAC address with the IP address of another user. Once the association has been established, messages directed to that address will be diverted to the attacker. The attacker can then use information obtained from the intercepted messages to mount other types of attacks, such as DoS or man-in-the-middle attacks.
- A MAC broadcast flood attack can be launched against a Layer 2 device, such as a network switch, from a device connected to one of its ports. The attack software on the controlled device is designed to flood a high volume of different MAC addresses into the switch’s CAM table causing it to fill up. When this state is reached, the switch will run out of room to map the new MAC addresses to its ports. Because all of the MAC addresses in the CAM are now new addresses that have not been mapped, the switch will be forced to broadcast all of the frames it receives to all of its ports.
- Router flood attacks are designed to consume all, or a significant part, of the router’s resources, thereby rendering them nonfunctional. Router resources commonly targeted include onboard memory, processor operation, and internal bus bandwidth.
- In MAC duplicating attacks, also known as MAC cloning attacks, the attacker updates their own MAC address with the target’s MAC address. This will cause the switch to forward traffic to both locations.
- Switch-port-stealing attacks are designed to flood the switch with altered response packets. This will cause the switch to forward all traffic through the switch to the attacker’s location.
- Denial of Service (DoS) attacks are designed to overuse a host, server, or network resource to the point where it functionally ceases to provide services. Depending on the exact nature of the attack, the failure may be temporary or indefinite. Distributed Denial of Service (DDoS) attacks involve multiple remote systems being used to simultaneously amass the attack on the targeted resource.
- Spoofing attacks are based on changing a device’s MAC or IP address to change its apparent identity. Because a TCP/IP packet contains many different headers, attackers can create a TCP/IP packet and send its contents using a false source IP address. When the addressed recipient receives the message, the response generated would be sent to the spoofed address.
- Man-in-the-middle attacks involve an attacker creating links to two or more victims so they can intercept messages moving between them and insert new information into them before forwarding them. This is accomplished without either victim realizing the attacker is controlling the communications.
- Session replay attacks involve the attacker recording a sequence of IP packets or router commands, manipulating the data in them, and then reintroducing them to the router to gain access or cause undesirable actions to be performed.
- Rerouting attacks are enabled by an attacker gaining access to the routing tables in a network router and reconfiguring it to redirect IP packets to alternative locations. These types of attacks are prevented by using transmission protocols that require route authentication. They can also be thwarted by employing static routers.
- Masquerade attacks involve an attacker manipulating IP packets to create a false IP address so they can gain access to the network or inject false data into it.
- The main defense against IP spoofing attacks is a packet filtering device. Packet filtering is the process of passing or blocking network packets based on their source/destination addresses, logical ports, or protocols. Managed switches typically provide filtering configuration options for all of these elements.
Security Challenge Scenarios
NOW that you have read Chapters 11 through 16, it’s time to revisit the observations you made in Chapter 11. In the following section, complete the information requested and then compare this information to your original Chapter 11 assessments.
Local Network Security Scenario 1
Identify:______________________________________________
Protect: ______________________________________________
Detect: ______________________________________________
Respond: ______________________________________________
Recover: ______________________________________________
Local Network Security Scenario 2
Identify: ______________________________________________
Protect: ______________________________________________
Detect: ______________________________________________
Respond: ______________________________________________
Recover: ______________________________________________
Professional Feedback
In this section, you will compare your observations to those of a working security specialist—in this case, Philip Craig, the founder of BlackByte Cyber Security—to improve your understanding of cybersecurity.
The Insights of a Practicing Professional
Getting the opportunity to design an overall computing environment may be one of the most challenging, frustrating, and rewarding endeavors in your career. It will challenge both your technical and interpersonal skills, keep you bound up in detail after detail, and most importantly force you to learn an immense amount about the whole process from start to end. Whatever the environment, remember some key points:
- Function not feature
- Security over convenience
- Business before desire
Local Network Security Scenario 1
You have been tasked with making recommendation for equipping a new data network for a small, educational-content development company (fewer than 20 employees). The new company has outgrown its old network and computing equipment and wants to start out in the new facility with a network that meets their current needs.
Because their business is based on the creation of IP (intellectual property) in a market that is highly competitive, they have asked for equipment and configuration recommendations to establish the most secure physical networking environment they can afford.
In particular, the customer has asked that you provide comprehensive recommendations for implementing their server-related security policies and standards. Figure 17.1 provides an overview of the company’s electronic workflow structure.

FIGURE 17.1 The Company Layout
The company’s major functions can be organized as follows:
- Executive Staff: The executive staff conducts the following electronic activities:
- Conducts electronic banking activities via the Internet
- Administrative Staff: The administrative staff is involved in the following electronic functions:
- Managing a server-based accounting, warehousing, and inventory program
- Managing electronic employee payroll and timekeeping records
- Sales and Marketing Team: The sales and marketing personnel work in house and on the road as required to prospect for customers, interact with outside sales representatives, and make customer visits and presentations. They are involved in the following electronic activities:
- Handling incoming emails and customer sales calls
- Operating an outbound email contact manager
- Tracking customer interactions using a server-based customer management database program
- Interacting with the home office when traveling to retrieve documents, product updates, emails, and other communications
- Interacting with their Internet ISP and their internal content-development team to manage and update the company’s website.
- Content Development Team: This team consists of writers, editors, and artists. Some of these workers are located in the company facility, some live and work remotely and never physically access the facilities, and others combine in-house work with telecommuting so they are in the office one or two days per week. Their electronic activities include the following:
- Creating text and graphic content on local machines, but they need to share that information among the team members as freely as possible
- Conducting web-based and hands-on research on technical products within a lab environment
- Customer Support Team: These technicians are dedicated to handling customers’ technical support calls, testing failure reports, and creating new or updated content for any errors or omissions in the IP. They also arrange and track replacement and update products that must be delivered to the customers. Their electronic activities include the following:
- Interacting with the customer management program to review past customer interactions and creating service records of problem calls and resolution actions
- Interacting with the content development team to share content problems reported by customers and offering rough revision materials as required
- Warehouse and Shipping Team: These workers are involved in the receiving, inventory tracking, storage of, and shipping of products. These employees have the following electronic activities associated with their jobs:
- Interacting with the warehouse and inventory portion of the company’s accounting software to update and track product receiving and shipping, as well as current inventory levels
- Interacting via Internet with Federal Express, United Parcel Service, and over-the-road trucking companies to schedule and track shipments
With this scenario in mind, provide suggestions as to how you would implement their server functions and what security measures should be set in place to provide security for their corporate resources. Recommendations should include, but are not limited to, physically securing the server and server room, establishing policies to protect the company’s intellectual property and personal information, and establishing procedures for maintaining the company’s servers.
There are six major departments within the organization. Initially mapping them to a basic role profile that can be implemented by a number of domain controllers (Microsoft, Linux, etc.) is important.
- Executive
- Administrative
- Sales/marketing
- Content development
- Customer support
- Warehouse
The existing functions are initially provided by the scenario, so a role-based access program will provide sufficient operational (and security) access controls for them:
- Electronic banking (A)
- Accounting (B)
- Warehouse inventory (C)
- Payroll and timekeeping (D)
- Customer-contact management system (E)
- Company website management (F)
- Content creation/management (G)
- Functional test lab (H)
- Website access (research, email, and so on) (I)
Building role-based access controls is a two-step process. The domain controllers can allow/disallow access to the application, and the application itself can be discriminant of users and privileges. This multi-authentication approach is a good idea. With such a small company, however, there may not be a domain controller, so you’ll have to take that into consideration.
With 20 people or so in the company, a central server (and backup preferably off-site) will provide good functionality. Your initial role-based architecture might look like Figure 17.2 (with the capital letters representing the application function).

FIGURE 17.2 Role-Based Architecture
Usually, almost everyone in the company will need to access the Internet. In reality, giving access to online email, banking, and a few Internet-surfing liberties won’t be a burden to your network or your computing platforms. What it can do, however, is challenge productivity! To help prevent employee slacking, disallow excessive content streaming (music services, Amazon Prime video, and so on) that can disrupt your business.
Now that you generally have a role-based, electronically enabled user policy, you can determine how the application itself will provide the separation of roles and duties necessary to maintain the operational integrity of the software systems deployed. As an example, everyone in the timekeeping system would need to input their time but not be able to access or report anyone else’s. The “timekeeper,” however, would need to have access to those higher-level functions of the payroll software. What you’re trying to avoid is the warehouse being able to access the customer contact database.
Proprietary information and intellectual property are main concerns in this scenario. The role-based access-control methodology will extend into these concerns. The objectives are to limit access to the information, keep it from leaving the company, and ensure that your employees understand that there are serious ramifications if they themselves compromise it. A good document management plan, policy, and procedures will provide a sound basis to protect this information. Some basic principles include keeping the company proprietary and intellectual information inside the system. Don’t let employees take it home on a thumb drive, don’t email it all over the company, and don’t let just anyone access it. Consider the loosely managed environment shown in Figure 17.3.
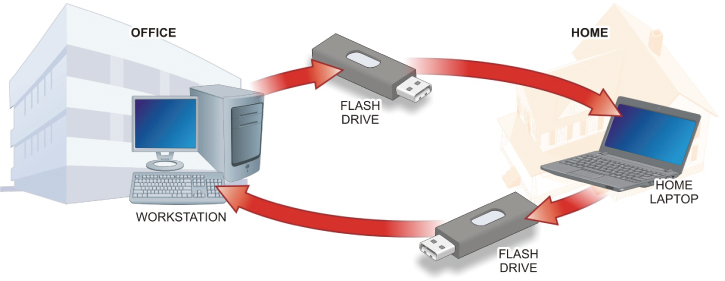
FIGURE 17.3 Loosely Managed Environment
Just a simple “I’ll get this done tonight!” scenario will significantly compromise your files or data. In the worst case, data comes off the work computer, onto a removable device, to a laptop, to a home network (or computer if it has the larger screen you want to use), back onto the laptop, and back to the office computer. From a security perspective, this is a nightmare! From a file or data perspective, the sheep have left the pen! Remember, this is a worst case; it can be argued that the employee has malware/antivirus protection, the file is deleted (even wiped) on all devices, and further it is checked before it is put back on the network. Would everyone really take the time to do all of these tasks? Even with these protections, your files have left the premises. This is not what you want to have happen.
The potential solutions are abundantly more secure. As an example, you could implement the simple, cost-effective solution discussed here:
Assume that the employee needs to be off-site for some reason. You want to accomplish the following:
- Keep the file(s) on the premises.
- Keep the development/work environment on the premises.
- Maintain positive control of both while the work is being completed.
This means you need to extend the desktop in a secure fashion. As shown in Figure 17.4, we usually accomplish this with a simple VPN connection back into the office and extend the remote desktop (RDP) session to the employee’s workstation. This approach doesn’t provide absolute security. It is, however, a much stronger approach than the original and can offer accountability (logging) as well. Remote access is a very effective and productive method in current business practices, and it can be very secure as well.

FIGURE 17.4 Maintaining Control
There are other options to remotely operate. From GotoMyPC software to full-blown Citrix desktop virtualization, people are working remotely extensively. For a 20-person company, some simple solutions such as a properly configured VPN and RDP connections can offer ways to be productive remotely.
With the need for remote connectivity—and for that fact, any connectivity—and keeping files and data (especially that which is proprietary) safe comes the need to discuss how to build a safe and secure environment for our electronic files and data. Keeping all of the company business within the physical walls (even virtual walls) of the company goes a long way toward securing that data. To do so, you can implement a simple communications policy that prohibits emailing files and data when unnecessary, especially internally. Email has become the de facto file repository.
Using email as a file cabinet is easy because attachments are surrounded by the context of the message containing the attachment. But now it sits on the email server—forever! Instead of allowing it to sit, you can file share to an individual on the network file server, and then email them the link to the file with instructions to “track changes” or “save a revision with your initials.” Now, you have an access record on the file server, and the data will remain on the servers. You can allow a working directory on a locally controlled office computer, but by practice and policy, you should always instruct employees to put the file back on the server and remove any local copies.
Most small networks like the size we’re talking about will tolerate simply opening and manipulating the file directly from the file server, so no local copy is necessary. Encryption techniques are extensive! Trying to address them here would consume a lot of space, so we’ll keep it simple. Use encryption when it makes sense. If you have highly proprietary documents, then encrypt them and add the public keys only to those documents that absolutely require it. Always use a master public key in addition to individual keys, as shown in Figure 17.5. This will ensure that the company owner always has access to any encrypted information. You can implement simple, electronic-auditing techniques to collect information on what files have whose key associated with them.

FIGURE 17.5 The Master Key
Now that you understand the basic architecture, you can start to focus on the different requirements for deployment. When you’re deploying your resources (that is, hardware, networks, monitors, storage arrays, and so on), there are many novel methods from which to choose nowadays. Let’s leverage a scaled approach. This means that the warehouse won’t get a 30-inch monitor, and the administrative folks won’t get dual screens. As the old saying goes, “the right tool for the right job.”
When it comes to personal computers and servers, there are some pretty simple principles to control costs and maintain capability. Only buy what you need for the job. As a small company, you wouldn’t want to hinder your employee performance with cheap or underpowered equipment. It is the same for very large companies. Can you imagine buying six-thousand PCs all with CD-ROMs? How many times do you actually need a CD-ROM? Maybe buy one or two USB CD-RWs and fetch them from the cabinet when you need them. The same applies for other peripherals. The literal piles of equipment discarded at some companies, quite a bit of it with little actual use, can be amazing.
Let’s look at the small, cost-effective system shown in Figure 17.6. It should meet all of the needs listed in the scenario, but you may consider adjusting for your budget simply because you would like a more commercial approach. The actual networking equipment is not shown, but it is implied that there will, at a minimum, be an outward-facing firewall, a managed switch, unmanaged switches, and the router(s) needed for internal and external access.

FIGURE 17.6 Suggested Network
It should be no surprise that this looks like almost any other computer network on the planet. After all, there’s only so much you can do with what you have. The difference is that you will implement the following:
- Implement a strict role-based authority and authentication policy and enforcement strategy.
- Implement a strict keep-it-here policy for company sensitive information. After all, it is the reason you have your job.
- Design a document management system (including policy) that encourages good utilization of the file server, including file/data access permissions, encryption, auditing, and good work-flow to maintain a tidy source of your company information.
- Make prudent choices for equipment procurement and use. If you don’t need it, don’t buy it. If you do need it, can you share a resource?
Review Questions
The following questions test your knowledge of the material presented in Part III.
- ____________is a set of rules that governs how communications are conducted across a network. In order for devices to communicate with each other on the network, they must all use the same network protocol.
- At what layer of the OSI networking model do MAC addresses work?
- ____________involves sending so many requests to a server or network connectivity device that its ability to handle these requests is reached, causing it to stop supplying service due to its lack of resources to handle the volume.
- What three steps should be performed after the operating system has been installed, updated, and patched?
- Under what access control strategy does the system establish which users or groups may access files, folders, and other resources?
- Administrators use ____________ to collectively deal with user accounts that have common needs.
- Describe the two major components of an auditing system.
- ____________are database-driven tools designed to search computers for known vulnerabilities that have been identified and added to the database.
- What security advantage does fiber-optic cabling have over copper cabling media?
- At what level of the OSI model do network switches primarily operate?
- In what type of attack does the attacker send fake ARP messages to associate their MAC address with the IP address of another user?
- How does a SYN flood attack work?
- Which device typically marks the boundary of an intranet segment?
- ____________ is the process of passing or blocking network packets based on their source/destination addresses, logical ports, or protocols.
- Which type of device is considered the main defense against IP spoofing attacks?
Answer: A The data link layer is involved in controlling how the data is packaged and moved between communication points. At this layer, the data is formatted into frames suited for transmission. Components at this level also add error detection and correction functions to the frames, as well as media access protocols and specific information about transmission to specific nodes on the same network segment.
Answer: C IPv6 addresses are typically written in the form of hexadecimal digits, separated by colons (
Answer: D Proxy servers act as intermediaries between network computers and the Internet.
Answer: C RAS (Remote Access System) servers allow clients to dial in to a computer from a remote site, even if they are not connected to a LAN.
Answer: A Packet sniffing attacks are normally conducted using a network analyzer tool referred to as a packet sniffer, to listen to network traffic looking for items such as passwords and usernames sent across the network in a plaintext mode, or sensitive information such as credit card or other financial information they can hijack.
Answer: B In a MAC duplicating or MAC cloning attack, the attacker updates their own MAC address with the target’s MAC address. This will cause the switch to forward traffic to both locations.
Answer: C Although WEP is a strong encryption method, serious attackers can crack it. This has led the wireless industry to create a stronger Wi-Fi Protected Access (WPA) standard. WPA adds improved data encryption, using Temporary Key Integrity Protocol (TKIP) and IEEE 802.1X Extensible Authentication Protocol (EAP) user authentication protocol to provide increased security.
Answer: D Daemon is a standard, default user/group that has privilege to execute daemon programs (background processes) that run without direction from the user.
Answer: B, D Managed switches typically offer DHCP snooping and Dynamic ARP Inspection (DAI) configuration options that are designed to thwart MITM attacks. DHCP snooping is used to filter and block ingress (incoming) DHCP server messages and builds an IP-to-MAC address database. DAI uses the DHCP snooping database to check and validate ARP requests to prevent ARP spoofing attacks.
Answer: A All security efforts begin at the physical access level. If an unauthorized person can gain physical access to the network servers, media, or connectivity devices, then there is no security.
Exam Questions
10000111.10001011.01001001.00110110
191.254.0.0
2001:0db8:00a7:0051:4dc1:635b:0000.2ffe:
13:A2:00:40:6B:8E:662001: 0db8:00a7:0051:4dc1:635b:0000:2ffe).
